Cybersecurity: Analysis of Issues and Threats
Info: 4693 words (19 pages) Dissertation
Published: 21st Oct 2021
Tagged: Cyber Security
ABSTRACT
Cybersecurity has gained considerable attention in last decade due to its ability to secure government’s data against expanding cyber threats. However, as Information Technology is advancing, so are the issues and threats to cybersecurity. Cybersecurity is still struggling to address multi-dimensional Cyberattacks which are gaining upper hand due to its ever-increasing sophistication. Hence, there is a need to be aware of the importance of issues and threats to cybersecurity. For a future researcher, new learner or IT professional it is imperative for them to analyse the questions like: what kind of enemies’ cybersecurity is fighting? how are the enemies motivated? what kind of techniques are they using to attack the vulnerable areas of cybersecurity? A list of articles is collated and analysed to know the answers of these imperative questions to have a clear understanding about various issues and threats to cybersecurity. So, the main aim of this paper is to analyse and highlight on all issues and threats on cybersecurity for a clear and comprehensive understanding of cyberattack. This is an attempt to influence the approach for future researchers and security professionals to address issues and threats related to cybersecurity.
Keywords: Cybersecurity, Cyberattack, Cybercrime, Cyber-threat
INTRODUCTION
As the world in terms of IT is evolving, so are the imminent threats to governing bodies in cyberspace. From the data theft incident of 22 million federal employees that happened in the US in 2015, it would appear that cybersecurity of even the superpower countries is vulnerable (Fonseca & Rosen, 2017). On the same context, as per the cost statistics report from Ponemon Institute (as cited in Karakoç, 2017), the average cost of cybercrime per company in the U.S. is shockingly $17,360,000. The government’s cybersecurity in most countries is still struggling to battle with underlying factors of cyberattack, as there are no silver bullets to quell cyberattack due to its disseminating nature (Clark & Hakim, 2017).
The problem related to cybersecurity is global in nature as it depends on technology, culture, economy and political shifts (Ulsch & Ulsch, 2014). Furthermore, the factors relating to issues and threats vary in specificity and extent (Viano, 2017). This scattered, vague, partial or sometimes exhaustive information about cybersecurity and factors relating to the cyber attack in different resource types (like EBook, Journal, Web page, Thesis or Conference Proceedings) could be overwhelming for upcoming researchers, IT professionals or new readers. The idea voiced by Dahbur, Bashabsheh, and Bashabsheh (2017), that stressed on more research and awareness to address cybersecurity issues and threats really motivated me to analyse the cybersecurity in a systematic manner. This academic research essay aims to analyse and highlight on various types of issues and threats to cybersecurity for quick, easy and comprehensive understanding of cyberattack, which could effectively be helpful for upcoming researchers and tech professionals.
This paper is designed as follows: first, in methodology, main terms and concepts are defined. Then there is an explanation of identification and filtering procedures for articles. The articles are then segregated based on different concepts, themes or topics. Findings showcase various critical avenues that need to be addressed with cybersecurity. Then based on findings, the articles are discussed and analysed pointing out implications, followed by gaps identified. Finally, we conclude the paper with observations, limitations and future research directions.
METHODOLOGY
To have a systematic understanding of the issues and threats on cybersecurity, first, the main topic or terms are defined to have a concise idea. Then 5 different concepts, themes or topics are formulated as this is directly related to issues and threats to cybersecurity. Articles are then searched and identified from the search engines and segregated based on these topics. From these findings, different articles are then examined and analysed and then discussed based on similarities, differences, implications, new ideas or gaps found. Then based on discussion conclusion is drawn with mention of limitations and areas identified for future research. Figure1 gives clear idea of the methodology process:
Defining main topic and concepts
Findings
Identification and Extraction
Categorization
Discussion
Conclusion
Figure1: Methodology process
Defining main topic and concepts
Cybersecurity: an Organizational resource to protect from cyber-attack (Alexander & Panguluri, 2017).
Cyberattack: Unintentional or unauthorized access, use, manipulation, interruption, or destruction of electronic information and/or the electronic and physical infrastructure used to process, communicate, and store that information (White, 2017).
Since the aim of this literature review is to reveal and exhibit various issues and threats related to cybersecurity, so the above main topic is formulated into different concepts, topics or key variables, in order cover the whole breadth and scope of the topic. An idea inspired from Klubeck (2015), which uses “Five Whys” and “Getting to root questions” techniques to come up with key metrics, formulated and defined below concepts or topics (Sutton, 2017):
- Cyberattack Types: different kinds of cyber-attacks.
- Cyberattack Actors: individuals or groups who implement cyber-attack.
- Cyberattack Tools: methods or technology used to implement cyber-attack.
- Cyberattack Motivations: the reasons that drive someone to action the cyber-attack.
- Cyberattack Impact: results or effects of cyber-attack.
Identification and Extraction
To filter out articles related to issues and threats to cybersecurity, databases ProQuest, ABI/INFORM, IEEE Xplore, SpringerLink, Safari O’ Reilly and ACM Digital Library were used. As shown in Figure 2, in the search engines, keywords like “Cybersecurity”, “Cyberattack”, “Cyber-threat” and “Cybercrime” (both in singular and plural) were applied. This also included searching by separating a word into two (“Cyber attack”, “Cyber security” etc.). Most recent and updated article had to be chosen to have better and revised ideas and concepts about the evolving topic (here, Cybersecurity).
Articles were excluded if found to be duplicate or were written in a language other than English. The articles were also excluded if it explicitly discussed cybersecurity specific to a particular area (e.g. Small organisations, cryptography, vehicle navigation, Airforce etc).
Initially, 35 articles were extracted from the databases (Journal=11; EBook= 7; Newspaper= 1; Thesis= 5; Conference proceeding= 6; Web Page= 5). After the full text review, it was identified that 19 articles were not relevant, so resulting 15 articles (Journal=3; EBook= 4; Thesis= 2; Conference proceeding= 4; Web Page= 2) were used for data analysis.
Keywords:
Cybersecurity, Cyberattack, Cybercrime, Cyber-threat
Database:
ProQuest, ABI/INFORM, IEEE Xplore, SpringerLink, Safari O’ Reilly, ACM Digital Library
Internet:

Excluded based on duplicates and scope
Journal:3 | EBook: 4 | Thesis: 2 | Conference proceeding: 4 | Web Page: 2 |
Total articles = 15
Journal:11 | EBook: 7 | Newspaper: 1 | Thesis: 5 | Conference proceeding: 6 Web Page: 5 |
Total articles = 35
Figure 2: Extraction process
Categorization
To analyse different articles by comparing and contrasting, the articles are categorized based on the above concepts. Concept matrix table in Fig 3 shows the bulk of these comparisons. Furthermore, the above main concepts are subdivided into subthemes to examine the topic in a detailed manner.
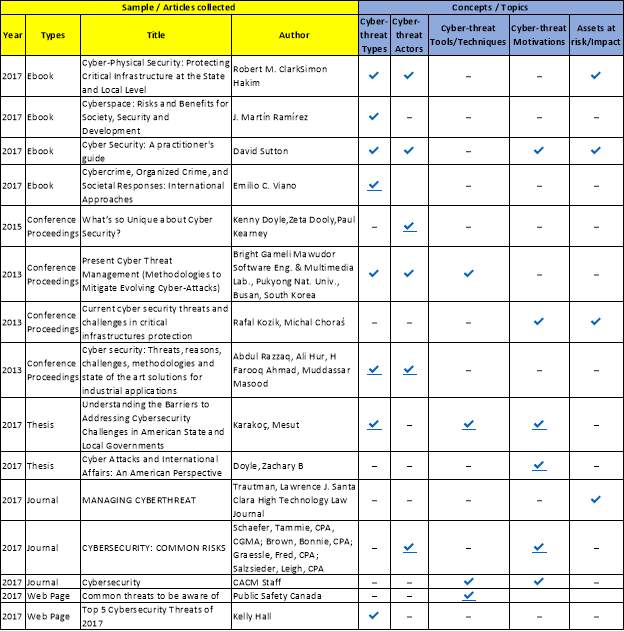
Fig 3: Concept matrix table
FINDINGS
In the next section, we examine the findings based on different variables under the main concepts (Types, Actors, Tools, Motivations and Impact).
Findings based on Cyberattack Types
The first key area of this review requires highlighting different types of attack in the cyberspace. From the report by White (2017), the types of cybercrime are spread across the topic of Hacking and Hacktivism. Most common acts like cyber vandalism, cyber theft, web jacking, cyber terrorism and cyber trespassing are covered within the topic. However, investigating report from Mawudor (2013) is limited it to Advanced Persistent Threat, which involves individual or groups from foreign agencies or crime syndicates that exploits vulnerabilities in web server. It may have been more detailed with more segregation to cover a wide range of cyber threats.
The report by Razzaq, Hur, Ahmad, and Masood (2013) did exactly in their study where a range of cyber threats was listed including software piracy, Industrial espionage, child pornography, cyber contraband, spam, denial of service attack (DoS) and distributed denial of service attack (DDoS). One of the key highlights is the rare Zero-day attack, that has a deep impact on network and is publicly not known (Karakoç, 2017; Mawudor, 2013), this calls attention to have an unwavering focus on threats that propagate in stealth mode.
Findings based on Cyberattack Actors
Identifying the real enemies behind these cyber-attacks is as important as identifying the types of cyber issues. In the pivotal study, Sutton (2017) illustrates a list of individuals or groups that implement the cyber-attacks, these are: script kiddies – inexperienced individual who attacks soft targets; hacktivists – they primarily defame organizations website; lone wolves – newcomers in hacking who learn and implement hacking by exploring blogs or social media; investigative journalists; minor criminals; organised criminals; terrorists ; insiders – employees working within an organization and security agencies. On the contrary, Mawudor (2013) and K. Doyle, Dooly, and Kearney (2015) showcase a generic approach in categorising threat actors like device, applications, human, criminal hackers, state-sponsored hacker groups and insider threat.
One of the significant fact presented by Schaefer, Brown, Graessle, and Salzsieder (2017) is that “according to cybersecurity experts, there are likely at least 80 million internal cybersecurity attacks a year—and that number is probably much higher because many internal attacks go unreported” (p.57). This emphasizes to target and prioritize internal cyber threats more as compared to external factors.
Findings based on Cyberattack Tools
In one of the pivotal reports, Mawudor (2013) and Sutton (2017) pointed technology related cyberattack tools like Website cloning, Email attachment and Compression (rar) Files and Application Installers. Surprisingly, there is a list of hacking tools like Kali Linux, John the Ripper, Nmap, Wireshark etc which are readily available online like play tools for free, this considerably raises the attack bar on cybersecurity. This also reveals that browsing, downloading or clicking on untrusted source could compromise credentials on the internet.
This is further complemented by Karakoç (2017), that focuses on non-technical cyberattack tools like Software engineering, Phishing and Ransomware. McQuade study of software engineering (as cited in Karakoç, 2017) highlights that cybercriminal uses his or her psychological manipulation ability to control a victim and retrieve sensitive information about individual or organisation. Phishing is another deceiving technique that uses a fake email to retrieve username and password from the victim (Karakoç, 2017). According to Mehmood (as cited in Karakoç, 2017) Ransomware is a blackmail technique to unlock the computer or server, in return for some payment. This implies that human factor is one of the weak links and is one of the contributors to vulnerabilities of cybersecurity.
Findings based on Cyberattack Motivations
There is always a driving force that motivates one’s action and cyberattack is no exception. Most often cyberattack can be attributed to financial gain (Schaefer et al., 2017; Sutton, 2017), however, there are other factors like revenge or malicious damage, espionage, intellectual property theft and investigative journalism (Sutton, 2017).
Kozik and Choraś (2013) and Karakoç (2017) stress on unemployment, poverty and social status, as a motivating factor which suggests the need for effective employment and economic policy. On the contrary, Z. B. Doyle (2017) argues motivation to be religious, ethnic cleansing and border conflicts which implies that such factors can be global, social and sensitive in nature.
Furthermore, driving force can also be internal which can be illustrated by CACM Staff (2017) which makes a very valid point that with more sophistication of technology and rise of data in the computer, there is an elevation of cyber attacks.
Findings based on Cyberattack Impact
It is really unimaginable and unfathomable to grasp devastation caused by a cyber attack on power grids or energy plants of the state. From the compelling report by Kozik and Choraś (2013), the statistics clearly implies that critical infrastructure like Energy, Water, Government, Healthcare, IT, Nuclear, Chemical, Transportation, Dams, Communications and Bank are at vulnerable ends.
Although no justification or evidence is provided in the report by Sutton (2017) on the list of critical sectors impacted, Clark and Hakim (2017) and Trautman (2017) gives an influential details on the real-life cyberattack incidents like compromise of US Department of Defence in 2008, data stealing from NASA systems in the US in 2012, medical record breach at Utah Department of Health (USA) in 2012 etc. This reveals that such impact has far-reaching ends, it is not only limited to financial or data loss but impacts economy, environment, reputation, physical and human lives.
DISCUSSION
Examination and findings on the above articles highlight various issues and threats related to cybersecurity. As Ramírez and García-Segura (2017) point out, there is a multiple and far-reaching spectrum of activities under cybercrime relating to cybersecurity, at one end the crimes are related to personal or corporate breaches. At the other end of the spectrum are crimes like spam, hacking and denial of service that disrupts the performance of the internet, and midway along the spectrum is transaction-based crimes like fraud, piracy and money laundering. This implies that there are multiple avenues of cyber attack, and techniques used by the attackers are widespread.
The findings show that identifying different types of cyberattack is one of the first and critical aspects while focussing on cybersecurity. In order to make cybersecurity more robust, the security professionals should not only focus on the mainstream threats, but also on the rare cyberattack (e.g. Zero-day attack, APT) that penetrate in the network immediately as vulnerabilities are found and are hidden. Additionally, articles also reveal that internal threats within an organization could be far more damaging as the internal associate knows where all the sensitive data is located and can exploit it at any time. Cyber threat not only has the potential to affect the technologies of cybersecurity but can also deceive and manipulate human minds. On the one hand, cybercriminals use tools and technologies which are far more superior and sophisticated. On the other hand, they use human vulnerabilities as a tool to attain their malicious intent.
The article also illustrates that even though we try to keep a check on technology and human factor, the threat to cybersecurity becomes far more convoluted and alarming when the motivation for cyberattack becomes religious and ethnic driven. Furthermore, there is also an evidence-based study that shows the impact on cybersecurity is rampant and global in nature, as it affects different sectors of nation’s economy.
Based on examination of the findings of issues and threats to cybersecurity, following gaps were identified:
- It’s noted that most of the previous studies primarily focus on a theory-based approach to highlight a list of threats to cybersecurity but fails to discuss on a quantitative level. With precise data figures in hand, it might help the readers to prioritize the threats and could be a motivating factor for creating awareness about cybersecurity.
- As compared to other areas, motivations and tools used for cyberattack are the areas which are not explored exhaustively by the previous study. It’s not sure if this can be attributed to secrecy in sharing this sensitive information (particularly tool related) or biased opinion among the researcher to regard it as low priority threat.
- Under the main concept of cyberattack types, very less number of articles reflects on the topics like cyberbullying, child pornography, zero-day attack, Advanced Persistent Threat (APT) and environmental threats. However less evident, in terms of frequency and occurrence these have a high degree of sensitivity and implications far-more damaging because above factors could cost human lives.
CONCLUSION
This academic research essay aimed at highlighting various issues and threats to cybersecurity which was based on different vantage points provided by 15 relevant articles. The presented study provides different avenues and dimensions of cyberattack which can impact cybersecurity. Due to multifaceted nature of cyber-attack as observed from the above findings, the resources (people, process and technology) in cybersecurity must be dynamic and organized. Despite the aim to make an effective and solid contributing academic literature review, certain limitations should be considered. First, as articles chosen are English language only and limited search engines are used to extract the articles, the scope of the findings are small. Second, due to evolving nature of the topic, we have selected only the recent articles (here, 2013 to 2017). Third, due to the small sample size collected, the findings are limited. Fourth, the approach used for selecting the article is subjective in nature. Nevertheless, these constraints don’t lessen the quality of the study and findings. We propose that further studies in the less researched area, like cyberattack tools and motivations involved in the cyber threat, have plenty of opportunities to expand. More quantitative approach-based examination of various factors would gain new insights and analyse the criticality of the cyber attack factors based on priority. Thereby, we contribute this paper to proliferating research and inquisitive people who are doing further research and investigating more on issues and threats to cybersecurity.
REFERENCES
Alexander, R. D., & Panguluri, S. (2017). Cyber-Physical Security : Protecting Critical Infrastructure at the State and Local Level. In Cybersecurity Terminology and Frameworks (pp. 19-47). Retrieved from https://link-springer-com.helicon.vuw.ac.nz/content/pdf/10.1007%2F978-3-319-32824-9_2.pdf doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-32824-9
CACM Staff. (2017). Cybersecurity. Communications of the ACM, 60(4), 20-21. doi:https://dl-acm-org.helicon.vuw.ac.nz/citation.cfm?doid=3069398.3051455
Clark, R. M., & Hakim, S. (2017). Cyber-Physical Security Protecting Critical Infrastructure at the State and Local Level. In Protecting Critical Infrastructure at the State, Provincial, and Local Level: Issues in Cyber-Physical Security (pp. 1-17). Retrieved from https://link-springer-com.helicon.vuw.ac.nz/content/pdf/10.1007%2F978-3-319-32824-9_1.pdf doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-32824-9
Dahbur, K., Bashabsheh, Z., & Bashabsheh, D. (2017). Assessment of Security Awareness: A Qualitative and Quantitative Study. International Management Review, 13(1), 37-58,101-102. doi:https://search-proquest-com.helicon.vuw.ac.nz/docview/1881414624?accountid=14782
Doyle, K., Dooly, Z., & Kearney, P. (2015). What’s so Unique about Cyber Security? Retrieved from https://link-springer-com.helicon.vuw.ac.nz/chapter/10.1007%2F978-3-319-25360-2_11
Doyle, Z. B. (2017). Cyber Attacks and International Affairs: An American Perspective. (Masters’ Thesis), Retrieved from https://search-proquest-com.helicon.vuw.ac.nz/docview/1891352488?accountid=14782
Fonseca, B., & Rosen, J. D. (2017). The New US Security Agenda. In Cybersecurity in the US: Major Trends and Challenges. doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-50194-9_4
Karakoç, M. (2017). Understanding the Barriers to Addressing Cybersecurity Challenges in American State and Local Governments. (Masters’ Thesis), Retrieved from https://search-proquest-com.helicon.vuw.ac.nz/docview/2001286247?accountid=14782
Klubeck, M. (2015). Planning and Designing Effective Metrics. In Designing and Documenting Your Metrics (pp. 25-58). Retrieved from https://link-springer-com.helicon.vuw.ac.nz/content/pdf/10.1007%2F978-1-4842-0826-7_3.pdf doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-1-4842-0826-7
Kozik, R., & Choraś, M. (2013). Current cyber security threats and challenges in critical infrastructures protection. Paper presented at the Informatics and Applications (ICIA),2013 Second International Conference, Lodz. Retrieved from https://ieeexplore-ieee-org.helicon.vuw.ac.nz/xpls/icp.jsp?arnumber=6650236
Mawudor, B. G. (2013). Present Cyber Threat Management (Methodologies to Mitigate Evolving Cyber-Attacks). Paper presented at the Information Security (Asia JCIS), 2013 Eighth Asia Joint Conference, Seoul, South Korea. Retrieved from https://ieeexplore-ieee-org.helicon.vuw.ac.nz/document/6621661/
Ramírez, J. M., & García-Segura, L. A. (2017). Cyberspace : Risks and Benefits for Society, Security and Development. In Some Criminal Aspects of Cybersecurity (pp. 141-151). doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-54975-0
Razzaq, A., Hur, A., Ahmad, H. F., & Masood, M. (2013). Cyber security: Threats, reasons, challenges, methodologies and state of the art solutions for industrial applications. Paper presented at the Autonomous Decentralized Systems (ISADS), 2013 IEEE Eleventh International Symposium, Mexico City, Mexico. Retrieved from https://ieeexplore-ieee-org.helicon.vuw.ac.nz/xpls/icp.jsp?arnumber=6513420
Schaefer, T., Brown, B., Graessle, F., & Salzsieder, L. (2017). CYBERSECURITY: COMMON RISKS. Strategic Finance, 99(5), 54-61. doi:https://search-proquest-com.helicon.vuw.ac.nz/docview/1960925772?accountid=14782
Sutton, D. (2017). Cyber Security: A practitioner’s guide. In Cybercrime: Cyber Threats. Retrieved from https://www.safaribooksonline.com/library/view/cyber-security-a/9781780173405/15_chapter05.xhtml#h22
Trautman, L. J. (2017). MANAGING CYBERTHREAT. Santa Clara High Technology Law Journal, 33(2), 230-287. doi:https://search-proquest-com.helicon.vuw.ac.nz/docview/1878757850?accountid=14782
Ulsch, M., & Ulsch, N. M. (2014). Cyber Threat! : How to Manage the Growing Risk of Cyber Attacks. In Introduction: What Every Current and Future Senior Executive Must Know about the Cyber Threat: A Perfect Digital Storm Is Forming (pp. 25-33). Retrieved from https://ebookcentral.proquest.com/lib/vuw/reader.action?docID=1742833&query=
Viano, E. C. (2017). Cybercrime, Organized Crime, and Societal Responses: International Approaches. In Cybercrime: Definition, Typology, and Criminalization (pp. 3-22). Retrieved from https://link-springer-com.helicon.vuw.ac.nz/content/pdf/10.1007%2F978-3-319-44501-4_1.pdf doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-44501-4
White, S. J. (2017). Cyber-Physical Security Protecting Critical Infrastructure at the State and Local Level. In Assessing Cyber Threats and Solutions for Municipalities (pp. 49-65). Retrieved from https://link-springer-com.helicon.vuw.ac.nz/content/pdf/10.1007%2F978-3-319-32824-9_3.pdf doi:https://doi-org.helicon.vuw.ac.nz/10.1007/978-3-319-32824-9
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




