Network Scanning Methods and Protecting Organisation Network
Info: 7745 words (31 pages) Dissertation
Published: 10th Dec 2019
Table of Contents
1.4.Uploading to external services
3. Conclusion & Recommendation (indicate what you learned on your own)
1. Introduction
This outlines the analysis on the organizations network, which concludes if any data was leaked and the possible data exfiltration methods that were used by the threat actor, further indicating how the port scans originated from the gateway machine, which clients machines were scanned within the internal network and the ports that were targeted. Furthermore, stating the clients and how they were identified, due to the reported potential data leak on the organizations network and referring to the PCAP file provided on data captured going to the gateway from the external scada Network.
As network security has become an important issue because; of the exponential growth of cyber criminals. The analysis will provide solutions on protecting the organisations network, how to detect advanced targeted attacks and providing actionable threat information. There are many systems and tools which used for protecting the network such as IDS, firewall, network security scanning etc. The network security scanning method can be used for protecting the system and also can be used for destroy system by the threat actor; it can have both bad and good effects on the system. Network scanning methods provides assessment and analysis for vulnerabilities on network system allowing for proactive protection of the organizations network. The network administrator uses it to detect some dangerous backdoor and some weaknesses and revise it to avoid the system being damaged.
2. Data Exfiltration Analysis
Internal threats to data are one of the highest ranked fears of executives in organizations. Organizations depend on a wide spectrum of communication that includes face to face meeting, online meetings, everyday data generated by departments etc. The amount of information that organizations produce in the information age is staggering and protecting that data is one of the most critical aspects of cybersecurity. It is very difficult and complex to conclude what information is leaving an organization legitimately and which information is because of malicious data exfiltration.
The case we are analysing contains several indicators of malicious intent that require further analysis and investigation to determine what the root cause is and what the intent is.
These indicators include:
- ICMP Packet size that are of varying length and sizes.
- ICMP Packets with completely out of s
- ICMP communication between 2 IPs but that contains information about other IP networks.
- ARP packets between the same 2 IPs that occur late in the packet transmission indicating possible timeouts and network reconnection by unknown entities or devices.
- A TTL value that is part of the same sequence of packets but does not decrease to indicate legitimate movement of packets through the network.
These indicators on the face of the Wireshark capture give enough pause to warrant further investigation of the traffic and indicate an initial intent of malicious behaviour.
The premise of the investigation through the rest of the report will work on the premise that there were bad actors involved and that there is a legitimate threat to the organization. The analysis will concentrate on finding evidence to prove or disprove if there was any data exfiltrated from the organization.
Since the External SCADA network is part of the organization. There is also a presumption that the threat actor is most likely internal to the organization.
We will start by looking at the first 4 ICMP packets and determining a baseline of malicious activity in the network.
2.1. Packet 1 to 15
Initial analysis of the first four (4) packets indicate that the entity 172.1.1.2(Address: PcsCompu_a1:20:9d (08:00:27:a1:20:9d)) initiated an ICMP request to the entity 172.1.1.1 (Address: PcsCompu_01:9e:aa (08:00:27:01:9e:aa)). This looks normal on its face but there is a mismatch between the size of the request and reply packet. Entity 172.1.1.2 (Referred to as Host A) and 172.1.1.1 (Referred to as Host B) have a huge disparity in packet sizes that are part of the same sequence and an unchanged ICMP packet should at least be the same size in both the request and the reply.
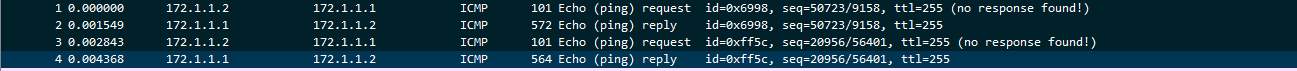
Packet 1 (request) is 101 bytes whereas packet 2 (reply) is 572. This prompted further analysis and further investigation at the content of the bigger packets as they are most likely to contain data indicative to what we need to look for.
A closer look at the packets indicated that there was indeed data transmitted through the ICMP request. The ICMP packet contained an HTTP request to a site called icanhazip.com.
The fact that there was data hidden in the packet indicate that there was an attempt at obfuscation of data travelling through the organizations network and this clearly indicate possible malicious activities. This finding has raised the status of possible bad actors from a maybe to a definite possibility.
Further investigation on the other packets involved shows a response from the same site that contains more data.
Packet 1:
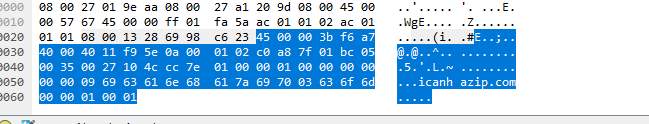
Packet 2:
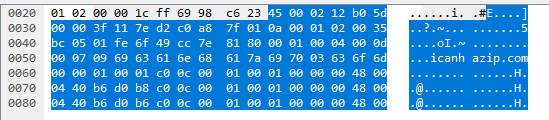
Packet 3:
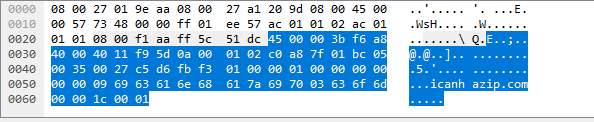
Packet 4:
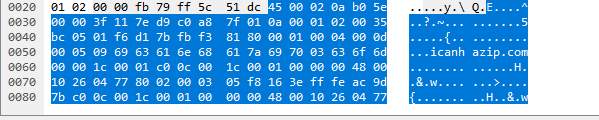
Icanhazip.com is a website that finds your public IP from anywhere. This website provides a similar service to whatsmyip.com. By default, this may show either an IPv4 address or if on an IPv6 enabled network will show your IPv6 address. Rackspace employee Major Hayden runs icanhazip.com as a service to the general internet community. You can force viewing either IPv4 or IPv6 by using the following URLs:
Further investigation of the subsequent packets 5 to 15 indicate that the entity on “Host A” further attempted and succeeded in querying the icanhazip.com website for a public IP and there was a response for the IP:
Packet 8
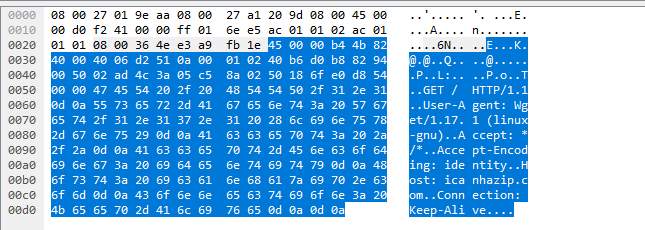
Packet 10:
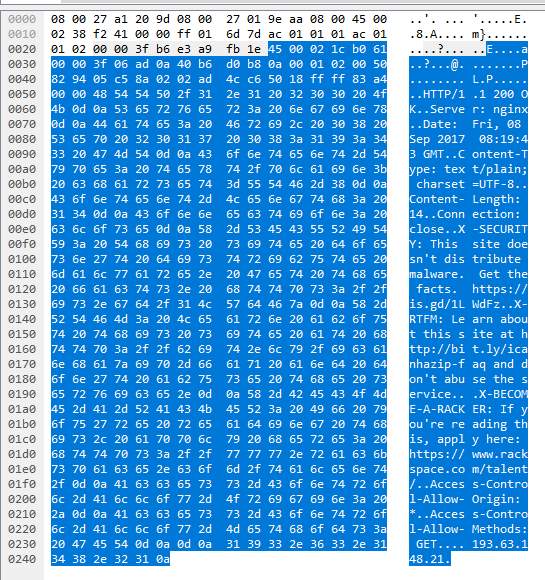
The above images provide the following information:
- The end computer is a Linux machine and the connection to icanhazip.com was made through wget command.
- The public IP 193.63.148.21 was retrieved from the icanhazip.com website.
- Date of GET request: 08 September 2017 at 08:19:43
The returned IP was further investigated with ping.eu and resolved to the following:
j124-me.comp.glam.ac.uk
Our initial investigation into the identity of “Host A”, the initiator of the packets has revealed that we are looking for an endpoint with the following details:
Hostname: j124-me.comp.glam.ac.uk
Physical address: 08:00:27:a1:20:9d
Public IP: 193.63.148.21
Below we will be investigating further to understand what the entity at that host was attempting to do and what possible malicious activities they have undertaken.
The analysis of Packets 49 to 62 shows another request to the icanhazip.com using the same host. A root server b.root-servers.net was queried through the request. The authoritative name servers that serve the DNS root zone, commonly known as the “root servers”, are a network of hundreds of servers in many countries around the world.
The b root server sits at the following IP:
|
|
|
- e.root-servers.net 192.203.230.10, 2001:500:a8::e NASA (Ames Research Center)
The above 2 root servers were used in the icanhazip.com website query.
- Packet 63 to 143
Another ARP request is made between packet 63 and packet 66.
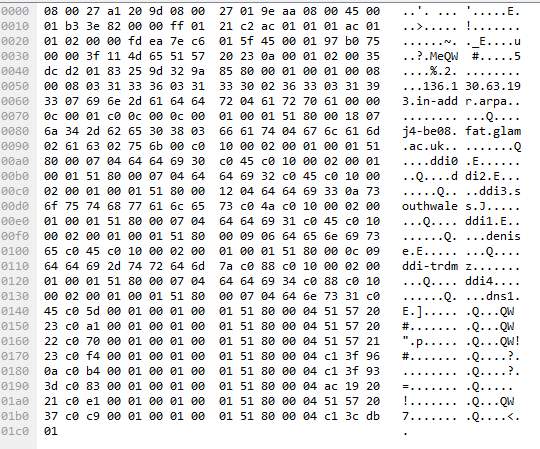
The following information is discovered from the ARP packet as seen in the image above.
IP: 193.63.130.136
Hostname: j4-be08.fat.glam.ac.uk
The same DNS servers used in the previous ARP request were used in the ARP request seen here.
The name Denise also appears in both ARP queries. This probably warrants further investigation to figure out if it is a compromised username or not.
The combination of the two ARP requests clearly indicates a reconnaissance pattern that is used in information gathering during a hacking attempt.
We are now going to analyse the two public IPs that were targeted.
193.63.130.135 and 193.63.130.136
The domain name fat.glam.ac.uk is an alias for djangoss.isd.glam.ac.uk.
djangoss.isd.glam.ac.uk has address 81.87.32.151 browsing to djangoss.isd.glam.ac.uk redirects to the following website. http://sasstaff.southwales.ac.uk/
We can then assume that the actor was trying to access this internal website that is used by the University of South Wales.
At first glance the university website is running on port 80 which is not secure and there is no HTTPS running on it. This makes our suspicion more that this was targeted by hackers.
This is also shown as evident by packet 107 which indicates that the southwales.ac.uk websites was accessed.
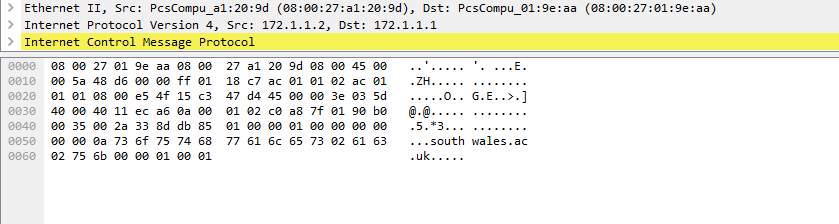
Since this an internal site. It should have been accessed by the entity that is coming from an external network.
There is also clear indication of trying to access emails.
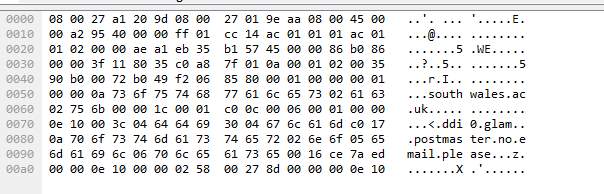
2.4. ARP Request
RFC 903 suggests a method for workstations to dynamically find their protocol address e.g., their Internet Address), when they know only their hardware address (e.g., their attached physical network address). ARP (Address Resolution Protocol) is used to resolve an IP address to a MAC address. The IP address is the logical address of the host, and the MAC address is the address of the actual, physical NIC of the host.
Malicious activities such as hacking have an established process that is usually followed. Hackers can use ARP (Address Resolution Protocol) running on your network to make their systems appear as your system or another authorized host on your network. A usual hacking attempt might involve the following steps or a general deviation of the below:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
Evidence presented 2.1 indicate signs of reconnaissance which is usually done to discover what networks are on the network. The attempt by host J124-me to find its own public IP is an attempt at finding out the public subnet of the network and using it to discover hosts that are publicly available.
As part of the reconnaissance, the next step is usually an active search of hosts and ARP is a great protocol to use for the attempt.
The next packets in the Wireshark capture indicated that host J124-me initiated an ARP request to the default gateway. An analysis of subsequent packets indicates that they then attempted to resolve a few addresses and hostnames.
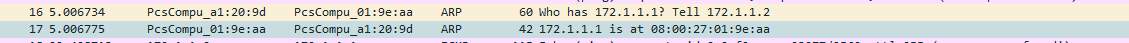
Further investigate of the packet 18 indicates that an ARP request was made for the following address:
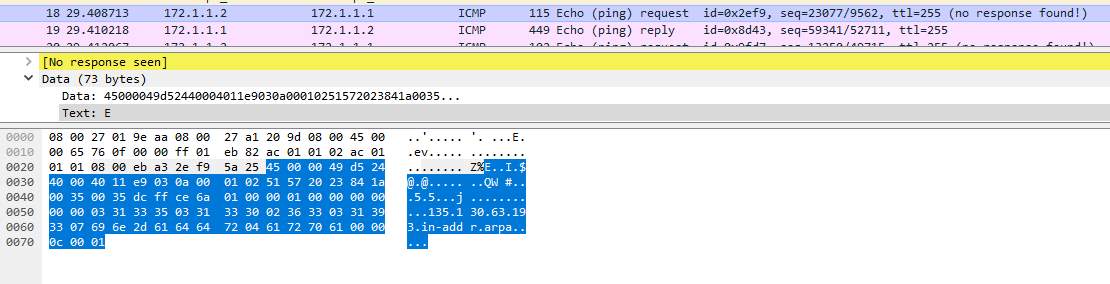
IP: 193.63.130.135
Hostname: j4-be07.fat.glam.ac.uk
The network diagram for the organization indicates that the subnet for that IP belongs to the internal network. The above clearly indicates host identification for the possibility of malicious attack.
The below reply was returned to the ARP request.
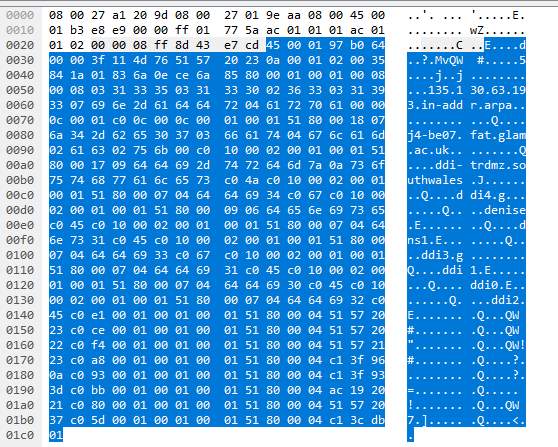
The following DNS servers were discovered to be used through the packet.
- Ns1.glam.ac.uk with IP 81.87.32.1
- Ddi1.glam.ac.uk with IP 81.87.32.34
- Ddi2.glam.ac.uk with IP 81.87.32.35
- Ddi0.glam.ac.uk with IP 81.87.32.35
- Ddi3.glam.ac.uk, No IP resolution found
- Ddi4.glam.ac.uk, no IP resolution found
Again, the above information indicates clearly a reconnaissance pattern of traffic. This is indicated using ARP to find a specific host using its IP address and finding out its hostname.
2.5. Inbound & Outbound Emails
Threat actors can use emails by sending malicious email attachments, to transmit sensitive data from secure computer systems to themselves or to other insecure private systems. They transmit sensitive data as plain text in an email or text message, or attached as a file, to exfiltrate the contents of organization emails, databases, images, and source code.
Many drafts emails are saved to the cloud, so it isn’t enough to check for sensitive data when the message is sent. If a threat actor has outside access to targets email or other messaging service that supports saved drafts, they can use this feature for exfiltration. Therefore is very essential prevent sending messages over insecure channels, such as using http instead of https, it is advisable that companies uses https for their websites to prevent data exfiltration, and to alert the IT security staff of such attempts. The security team retain a log of addresses used to send email, what devices emails are sent from, and the addresses of recipients. These will help the security team to identify the nature and scope of data exfiltration events.
2.6. Uploading to external services
Uploading data such as pdf files, images or files to external services involves downloading sensitive data to local infrastructure, which could lead to data exfiltration. The actor can then upload sensitive data to a possible attacker through a web browser client or to any other unmonitored software. The organisations data can be exposed to services such as web sites like a social network, websites without HTTPS, where the actor could accidentally upload the wrong images or paste the wrong text. Sophisticated threat actors may be able to pass small amounts of sensitive data, like user credentials or encryption keys, as URL parameters to specialized web applications.
2.7. ICMP and ICMP tunnelling
On first glance at the wireshark output, it is evident that ICMP was used as the protocol for possible malicious activities. A look at the packet length in the Figure below indicate that the method used was ICMP tunneling. In packet 1 we have a source address 172.1.1.2; this is the address of the gateway or host that composed the ICMP message, which passed through the gateway. The destination address of the gateway or host to which the message should was sent is 172.1.1.1; allow it is not clearly stated to whom the IP belong, because they are not in the IP range of the SCADA external neither in the internal network. The figure above shows a wireshark capture of traffic between two machines with the IPs of 172.1.1.1 and 172.1.1.2.
A quick scan of the wireshark output and the network diagram in the Figure below shows that one of the machines involved is the Gateway of the organizations network. A look at the diagram also indicates that host machines on the SCADA network should only have IP ranges of 172.1.1.100 to 172.1.1.200.
There is currently no information on which machine has the IP 172.1.1.2 which initiated the traffic and who it belongs to. The targeted clients on the internal network are within?
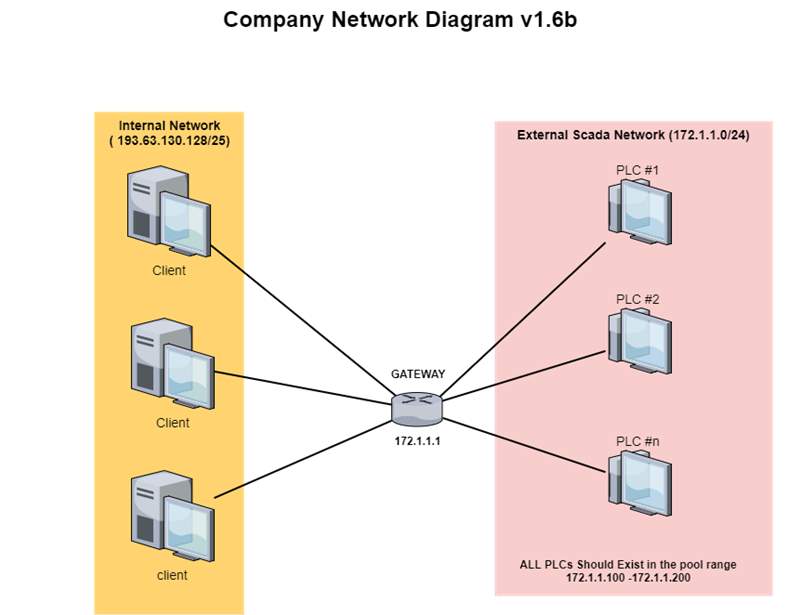
The packet analysis shows a protocol Internet Control Message Protocol (ICMP) which equals IP protocol of value 1; ICMP messages are sent using the basic IP header. ICMP protocols are used for diagnostic purposes and it is part of internet protocol suite, defined in RFC792. Any field labelled “unused” is reserved for later extensions and must be zero when sent, but receivers should not use these fields, except to include them in the checksum, length of internet header and data in octets is 87 (https://www.ietf.org/rfc/rfc792.txt, no date).
The time to live from the network analysis equals 255 in seconds; as this field is decremented at each machine in which the datagram is passes, the value in this field should be at least as great as the number of gateways which this datagram will pass through. The icmp protocol is internet protocol version 4, with an internet header length of 32-bit words.
The source threat actor initiated communications using ICMP echo request (ping) packets (type 8), whereas the proxy used echo reply packets (type 0). This was captured by icmptunnel, encapsulated in an ICMP reply packet and send back to the client threat actor, icmptunnelling works by creating a virtual tunnel interface. The user traffic on the client machine is routed to tun0; icmptunnel schedules to listen from this interface for targeted IP packets. These packets are encapsulated in an ICMP echo packet the payload of the ICMP packet is nothing but the original IP packet. The ICMP packet generated from the tunnelling is sent outside the threat actor machine, through to the proxy server and through to restricted internet connection, which leads to exposure of sensitive information such operating systems etc. (https://github.com/DhavalKapil/icmptunnel, no date).
The proxy server receives these RFC792 ICMP protocol packets and translates the original IP packet and retransmits the packets onto the internet after implementing IP masquerading, using false identity external to the computer system. Hence, the target gateway believes that its own proxy server is making the request; whereby the target then responds back to the proxy server with an IP packet (https://github.com/DhavalKapil/icmptunnel, no date).
On the client side, the IP packet is retrieved from the payload of the ICMP reply packet and injected in tun0. The threat actor’s user applications read from this virtual interface to retrieve the proper IP packet. The source IP address that is originating from the SCADA network can be obfuscated because the network is most likely using NATing through the gateway. This allows the attacker to hide their identity on the attack. NAT does not provide security, it merely allows many private IPv4 address to use one public IPv4 address. It is not a reliable security mechanism and it can be used as a method to obfuscate internal addresses to attackers. But I still would not define it as reliable security layer.
Ping tunneling often referred to as ICMP tunnelling, is another method threat actors use to exfiltrate data that allows which allows them to reliably tunnel TCP connections to a remote host using ICMP echo request and reply packets, this is commonly known as ping requests and replies. The target allows incoming ICMP packets, if it sends back a reply. There is a proxy, client and destination with ICMP packets, and the proxy is the endpoint for our ping packets, the computer that we send the ping packets to. The client is the threat attacker’s computer we’re they are initiating connections from or surfing the net from, and the destination is the computer of the network we are targeting, we would normally be trying to access over TCP such as a web site or an SSH server somewhere. However, there are a number of situations where ping tunnel can fail, in cases where outgoing and incoming ping is not allowed, or filtered by a gateway somewhere along the way (http://www.admin-magazine.com/Articles/Arp-Cache-Poisoning-and-Packet-Sniffing, no date)
2.8. ARP Protocol
It is evident that ARP broadcast was used as the protocol for possible malicious activities. ARP packets were sent to their destination port by MAC address. Referring to RFC826, arp broadcast requires the systems on the network maintain a table associating ports to their associating MAC addresses. Relating to the network diagram in this network environment, one can find ways to sniff other devices’ packets. One such way is to spoof the MAC address and poison the ARP table. Since ARP keeps no state information, the ARP cache can be overwritten. The threat actor a broadcast message asking who has 172.1.1.2 to obtain the target hardware’s MAC address, the target replies to the threat actor with a message telling them the targets MAC address of 172.1.1.2.
Arp cache poisoning puts the attacker in position to intercept communications between the two computers. Computer A within the internal network believes it is communicating with Computer B within the same internal network, but because of the poisoned Arp table, the communication actually goes to the attacker’s computer. The attacker can then either respond to Host A by pretending to be Host B, or simply forward the packets to its intended destination, but only after the packet information is captured and logged for later use by the attacker. Likewise, the response from Computer B can be captured and logged by the attacker, who has also used Arp poisoning to make Computer B think the attacker’s computer is Computer A. This type of attack is known as Man in the Middle attack (http://www.admin-magazine.com/Articles/Arp-Cache-Poisoning-and-Packet-Sniffing, 2017).
ARP traffic does not necessarily need to be sent before any ICMP traffic, although it can be done, the host machine can adapt IP-to-MAC mapping, then inserts it into an ARP table for some period of time. Therefore, the host machine will check this ARP table for such a mapping first and only then send out an ARP if there is no entry (Networkengineering.stackexchange.com, 2017)
If the host A has no entry for host B’s IP address in the ARP table. Host A will have to ping Host B the traffic exchange is like this:
Host A Host B
ARP_Request —>
<— ARP_Reply
ICMP_Echo —>
<— ICMP_Echo_Reply
2.9. DNS Tunnelling
As the packet analysis shows that there is certain evidence of DNS servers as they are commonly used in most systems. DNS Tunnelling (DNS) services are used in every network with general purpose use of internet services. DNS is therefore a convenient target for threat actors to misuse. The threat actor used DNS tunnelling to try misusing the system. With DNS tunnelling the threat actor, used other protocol such as ARP to tunnel through the DNS, to accomplish data exfiltration or to tunnel any internet protocol IP traffic on the system.
DNS tunnelling includes a domain controller, a subdomain, a server side component, and client side component and data encoded in DNS payloads. The information of the controlled domain is used to define the target name server for that targeted specific domain and subdomain.
DNS tunneling is a data exfiltration method, which is a substantial threat to organizations. The two main threats to DNS tunneling are command and control of compromised endpoints and data exfiltration, which threat actors can misuse to gain access to the organisations sensitive data. Command and control for attackers can go to the extent of allowing for full remote access to a targeted endpoint. Attackers can accomplish DNS tunnelling through netcat like capability with some DNS tunneling utilities or via any remote access application over a full IP tunnel. DNS tunneling provides a vulnerability channel for data exfiltration and malicious activities which is a great threat to the organisation. Although inefficient for data transfer DNS tunneling can be used to easily exfiltrate high value data such as password hashes or sensitive documents. Therefore need to be closely monitored; DNS tunneling can be used to leak large amounts of data given enough time. However this threat can be minimised, threats can be mitigated using payload analysis and traffic analysis detection techniques, but cannot be totally eliminated (Van Dyke, 2008).
https://www.sans.org/reading-room/whitepapers/dns/detecting-dns-tunneling-34152
3. Port Scanning Methods
One of the common methods to determine if the network has been compromised is to scan the organisations network to see if there are any open ports which are open to determine they are vulnerable to intrusion. Port scanning methods were used by the attacker as the port scans originated from the company’s gateway between the Internal Network and the Scada Network. A port scanner scans a host or a range of hosts to determine what ports are open and what service is running on them. In most cases, the attacker will conduct port scanning at the start of an attack, to map the interesting hosts. Port scans help the attacker to find out which ports are running which server; the threat actor targets the system with a collection of exploits for the targeted clients. The attacker will do their homework, by mapping the network to get their way around to get an idea of what type of services are offered and what operating systems are in use.
The network security has become an important issue because of the exponential growth of Internet. There are many system and tools which used for protecting the network such as IDS, firewall, network security scanning and so on. Therefore, network security scanning can be used for protecting system and also can be used for destroy system by the intruder. It provides assessment and analysis for vulnerabilities on network system and it can get the proactive protection (https://www.auditmypc.com/port-scanning.asp, no date).
The system administrator can use it to detect some dangerous backdoor and some weaknesses and revise it before the system is damaged. Port scanning is one of the most popular and important probing tools used by intruder. The weakness may be introduced by the error configuration or worse programming. When an intruder wants to get the permissions of the network system, he must get the information of system which can provide him the entry of system and he will discover weaknesses in the services and operating system of a remote host. The attacker wants to know what operating systems they are used, what hosts are up and what TCP/UDP ports are open. The simplest security scan is the ping scan which let you to detect which computers are online (http://etutorials.org/Networking/network+security+assessment/Chapter+4.+IP+Network+Scanning/4.2+TCP+Port+Scanning/, no date)
3.1. NMAP
Nmap is one of the best port scanners used, it runs on just about every operating system, is very versatile and has many features including OS fingerprinting, service version scanning and stealth scanning. Another popular scanner is superscan, which is only for the windows platform. Run a scan of the ports, and try pOf, or NMAP to run a port scan. This will show you the ports that are open on the machine, the Operating System, and can even tell you what type of firewall or router they are using so you can plan a course of action. You can activate operating systems detection in NMAP by using the -O switch (SearchNetworking, 2017).
Nmap is a utility for port scanning and it’s character is to provide a more comprehensive method of scanning and to detect the remote operating system using protocol fingerprint. It supports the wide range of protocols such as UDP, TCP, connect (), TCP SYN, ftp proxy, ICMP, FIN, ACK sweep and Null scan (SearchNetworking, 2017).
The aim of port scanning is to find some open ports in the remote host. It is very useful to get more information from the remote host because the port is connected to the special network server such as WEB server, FTP server and Email server and so on. The TCP and UDP protocol need the port to communicate on the Internet and each port is a number who identify different kinds of server. Port numbers start at 0 and go up to 65535 and the numbers in the lower ranges are used for common Internet protocols. Port scanning can find out which ports are open, which are closed, and which are filtered. There are many methods which can be used port scanning. A common way is to send protocol packet to the remote port and get the result packet from the remote machine. The result can identify the status of the remote machine port. For example, if you send a SYN packet to a remote open port, the remote host will respond back with a SYN+ACK packet. If the port is closed, the remote host will respond back with a RST packet. It uses the TCP protocol procedure which has more steps of communication between two hosts. UDP and ICMP also can be used for port scanning. Nmap is a most popular port scanner. Port scanning has different scanning methods open scanning, half-open scanning and stealth scanning. The open scanning use the three-way TCP/IP handshake mechanism and it can finish a whole network connection. The half-open scanning doesn’t finish the whole connection progress and it can avoid the IDS. The example of half-open scanning is SYN scanning. The open canning can produce more log information and can be detected easily but it is fast and can get correct result. The stealth canning can avoid the IDS and firewall but it maybe gets the error result because of the network configuration. Port scanning has other new ways such as slow scans, cooperative scans and organized scans which can’t be detected easily. The slow scan run at a very low speed and the cooperative scan make a series of ports from different sources. The method of FIN scan is to send a TCP FIN packet and if a RST packet is got, the remote port is closed. If the port is not closed, the remote machine doesn’t respond. So the FIN scan can tell us if the port is closed. The TCP scanning can be realized by third-party machine such as FTP bounce scanning and proxy bounce scanning. UDP port scanning use the UDP protocol and it send UDP packet which can contain zero bytes data. If the remote host responds with an ICMP port unreachable error packet, the remote port is closed. If the remote port is open, the respond will be different with the remote application program. The network administrator should shut down unnecessary ports in order to protect your network system. The necessary open port also can be camouflaged and the attacker cannot distinguish the real open port (TechTarget, 2000-2017)
As the system offers TCP or UDP services will have an open port for that service. For example, if you’re serving up Web pages, you’ll likely have TCP port 80 open. FTP is TCP port 20/21, Telnet is TCP 23; SNMP is UDP port 161 and so on (TechTarget, 2000- 2017)
3.2. Vulnerability scanners
Once vulnerability scanners have identified which services are running which services, it checks the system against a large database of known vulnerabilities and then prepares a report on the security holes that are found. The software can be updated to scan for the latest security holes (TechTarget, 2000-2017).
3.3. SSH
It is not evident if there is an SSH server on the network but they are widely available for most used operating systems, but however it is a good security measure, open port 22 is usually evidence of an secure shell (SSH) service running on the target, which can sometimes be brute forced. Referring to RFC4251, Secure Shell (SSH) is a protocol that provides authentication, encryption and data integrity to secure network communications. The importance of secure shell in an organisation is because it allows for following capabilities: a secure command-shell, secure file transfer, and remote access to a variety of TCP/IP applications via a secure tunnel (Van Dyke, 2008). Secure Shell offers a good solution for the problem of securing data sent over a public network, but it can be brute forced.
3.4. Port Numbers
Port numbers is one of the first things threat actors try to figure out during before an attack. Service names and port numbers are used to distinguish between different services that run over transport protocols such as TCP, UDP. Service names are assigned on a first-come first served basis, according to the RFC6335.
Port numbers are assigned according to a certain range, based on three ranges: system ports 0-1023, user ports 1024-49151, and the dynamic and private Ports 49152-65535; they all have different uses as described in RFC6335. User ports are assigned by the IANA organisation using the “IETF Review” process, as outlined by the RFC6335. Dynamic Ports are not assigned. There is a certain procedure followed to name port numbers, based on RFC6335 (IANA, 2017).
3.5. Port Forwarding
Port forwarding is a good network security measure tool that can provide security to TCP/IP applications including e-mail and in-house applications. Port forwarding, can be referred to as tunnelling, however it has disadvantages as well, it allows data from normally unsecured TCP/IP applications to be secured. After setting up port forwarding, SSH will then reroute traffic from the target client and sends it across the encrypted channel, and delivers it to the server on the other side of the threat actor. Threat actors can send data over a single multiplexed channel, eradicating the need to open additional vulnerable ports on a firewall or router (Van Dyke, 2008).
3.6. Proxy Forwarding
Proxy forwarding goes with Secure Shell (SSH) connection protocol as it allows for proxy forwarding of other protocols such as SMTP, and HTTP. This may be a concern for network administrators who wish to control the access of certain applications by users located outside of their physical location. Essentially, the forwarding of these protocols may violate site- specific security policies, as they may be undetectably tunnelled through a firewall. Implementers should provide an administrative mechanism to control the proxy forwarding functionality so that site-specific security policies may be upheld.
In addition, a reverse proxy forwarding functionality is available, which, again, can be used to bypass firewall controls. As indicated above, end-point security is assumed during proxy forwarding operations. Failure of end-point security will compromise all data passed over proxy forwarding (Van Dyke, 2008).
3.7. General network tools
The attacker used basic general network tools to attempt penetrating the network. At the beginning of most attacks the actors uses the basic network tools available with most operating systems. The attacker queried the “who has” databases for information on the target, most probably using whois.sc website. After that, the threat actor can use “nslookup” to understand if he can transfer the whole contents of the DNS. The threat actor might also be able to figure what different systems do based on their DNS name; for example, sqlserver would most likely be a database server. The threat actor uses another network tool traceroute which will be discussed in the topic below, which allows the threat actor to figure out the structure of the network and ping to check which hosts are alive, unless if there is a firewall in place that blocks ping requests and traceroute packets (TechTarget, 2000-2017).
Virus Total
Due to the conclusion that this is a malicious attack. by running the .cap file through Virus Total to discover if there were any payloads in the packets: Here are the results.
Basic Properties
MD5
e79b704c9a9fc7adff3b87569f383cc3
SHA-1
6858b299e11a810dbdab62bae2a5c18c2430103e
File Type
Network capture
Magic
tcpdump capture file (little-endian) – version 2.4 (Ethernet, capture length 262144)
SSDeep
768:6o5MCGLQo2eTb/QQhGUPDwlqeyVllgFYGA/aVh:6LOo2g/AYDYqNlgFLA/gh
TRiD
TCPDUMP’s style capture (little-endian) (100%)
File Size
35.44 KB
PCAP Network Trace Info
Overview
Capture Duration
108.990934 seconds
Data Size
33 kB
End Time
2017-09-08 10:21:54
File Encapsulation
Ethernet
File Type
pcap
Number of Packets
149
Start Time
2017-09-08 10:20:05
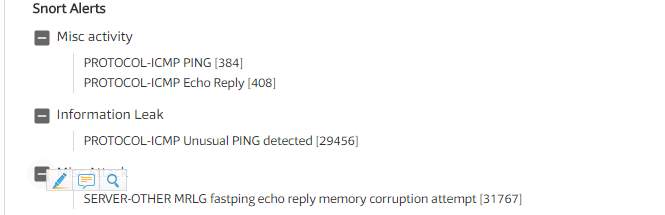
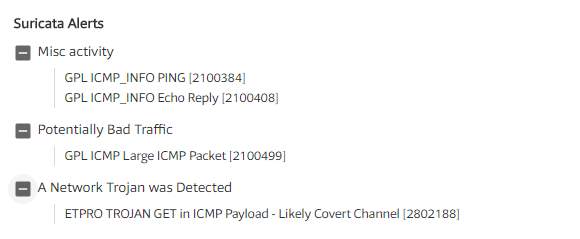
There was clearly malicious payloads in the traffic that was used to circumvent security.
ETPRO TROJAN GET is a Locky ransomware payload.
“
Locky is ransomware malware released in 2016.it is delivered by email (that was allegedly an invoice requiring payment) with an attached Microsoft Word document that contains malicious macros. When the user opens the document, it appears to be full of garbage, and it includes the phrase “Enable macro if data encoding is incorrect,” a social engineering technique. If the user does enable macros, the macros then save and run a binary file that downloads the actual encryption trojan, which will encrypt all files that match extensions. Filenames are converted to a unique 16 letter and number combination with the. locky file extension. After encryption, a message (displayed on the user’s desktop) instructs them to download the Tor browser and visit a specific criminal-operated Web site for further information. The Web site contain instructions that demand a payment of between 0.5 and 1 bitcoin (as of early November of 2017, one bitcoin varies in value between $7,000 and $8,000 via a bitcoin exchange). Since the criminals possess the private key and the remote servers are controlled by them, the victims are motivated to pay to decrypt their files” (Wikipedia)
Data security is sub sequential as, IP address on the network is a potential entry point for threat actors, and many unsophisticated networked solutions cannot distinguish between “good” and “bad” traffic. In the area of data security risk mitigation, there are guidelines to assist them in the form of data-security standards. There is more broad extensive knowledge on the topic of network security.
It is pretty evident that the network was not secure and a potential target for malicious activity.
The website was running on an unsecure port that was a potential for data exfiltration.
The bad actor managed to get access to the webserver and exfiltrate information through the website.
A few recommendations:
- Disable ICMP as it was the base protocol used for the data exfiltration that took place.
- Implement an Intrusion Prevention System to detect malicious behaviour.
- Implement HTTPS as the protocol for the website to counter unencrypted communication, as its currently using HTTP only.
2. References
1. VanDyke (2008)Electric, S. (no date) ‘firewall configuration to allow client -server comms’ [Accessed: 13 October 2017].
2. IANA (2017) Service Name and Trasport Protocol Port Number Registry [Accessed: 13 October 2017].
3. ‘icmptunnel by DhavalKapil’ (no date) (Accessed: 13 July 2011) [Accessed: 18 October 2017].
4. ‘Network security, lesson 2 Common security measures’ (no date) [Accessed: 25 October 2017].
5. admin magazine. (no date) arp cache poisoning. [ONLINE] Available at: http://www.admin-magazine.com/Articles/Arp-Cache-Poisoning-and-Packet-Sniffing. [Accessed 18 November 2017].
6. R. Marchany, ‘Higher Education: Open and Secure?’ (2014) ‘InfoSec Reading Room’ [Accessed: 14 November 2017].
7. VanDyke (2008) ‘White Paper An Overview of the Secure Shell ( SSH )’ [Accessed: 16 November 2011].
8. ‘What is the default TTL value – 58345 – The Cisco Learning Network’ (no date) [Accessed: 17 November 2017]
9. Nmap.org/. (no date). nmap.org. [ONLINE] Available at: http://www.nmap.org [Accessed 19 November 2017].
10. ‘What is traceroute? – Definition from WhatIs.com’ (no date). Available at: http://searchcio-midmarket.techtarget.com/definition/traceroute [Accessed: 18 November 2017].
11. Networkengineering.stackexchange.com. (2017). stack exchange. [ONLINE] Available at: https://networkengineering.stackexchange.com/questions/20813/what-is-first-arp-vs-icmp. [Accessed 17 November 2017].
12. Etutorials.org. (no date). Network Security assessment. [ONLINE] Available at: http://etutorials.org/Networking/network+security+assessment/Chapter+4.+IP+Network+Scanning/4.2+TCP+Port+Scanning/. [Accessed 17 November 2017].
13. TechTarget. (2017). Search Networking. [ONLINE] Available at: http://searchnetworking.techtarget.com/tutorial/Network-security-lesson-2-Common-security-measures. [Accessed 19 November 2017].
5. Bibliograpghy
1. www.iana.org (no date) ‘service name and trasport port number registry’.
2. (www.iana.org, no date)(‘Port and Firewalls’, 2015)(Joe Touch and Kumiko Ono, 2012)(R. Marchany, 2014)(IANA, 2017)(‘What is the default TTL value – 58345 – The Cisco Learning Network’, no date)(‘What is traceroute? – Definition from WhatIs.com’, no date)(Kajay, 1996)(‘icmptunnel by DhavalKapil’, no date)(‘Network security, lesson 2 Common security measures’, no date)(Electric, no date)(Pfleeger, no date)(Msdn.micosoft.com, 2013)
4. Pfleeger, C. P. (no date) ‘security in computing’ (Accessed: 10 November 2017).
5. Kajay, M. E. (1996) Enterprise security: protecting Information Assets. Mc Graw-Hills (Accessed: 20 October 2017).
6. Msdn.micosoft.com (2013) ‘obtaining data from the local computer (windows)’ (Accessed: 25 October 2017).
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Technology"
Information Technology refers to the use or study of computers to receive, store, and send data. Information Technology is a term that is usually used in a business context, with members of the IT team providing effective solutions that contribute to the success of the business.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




