Mitigating the Risk of Phishing Attacks
Info: 15279 words (61 pages) Dissertation
Published: 17th Nov 2021
Abstract
Phishing is a form of cyber attack where the attacker spoof emails and use fraudulent websites to deceive online users into giving out their confidential information.
This dissertation looked at the phishing as a whole and examined various stakeholders and the countermeasures that they recommend to be implemented.
Our methodology was a combination of quantitative and qualitative analysis. Research data was gathered from literature review, an online survey and an expert interview. Semi structured interviews were conducted first to get the expert opinion on both the current and the future of phishing and the countermeasures that should be adopted. Analysis from the interviews led to 6 key findings and 5 recommendations for improving phishing attacks countermeasures.
An online user survey was then conducted to get users feedback on the online security perceptions, how to avoid phishing attacks and how they react to various phishing mitigation means.
The results from the interviews showed varied opinions from the experts, they held different opinions in regards to user education and technical solutions as a means to mitigate phishing attacks while on the other hand those that were surveyed appeared to be more concerned about protecting themselves online but at the same time they are not taking online security as their primary task, also they were being hindered by a lack of understanding about phishing and how to mitigate it.
The results went on to suggest that despite education materials drastically reducing the user’s tendency for falling for phishing attacks, some of them are more confusing rather than providing solutions, hence much more effort on the stakeholders is still needed in order to polish the anti-phishing mechanisms.
Click to expand Table of Contents
CONTENTS
1 INTRODUCTION………………………………………………………………….7
1.1 Problem and Context ………………………………………………………….7
1.2 Aim………………………………………………………………………………..8
1.3 Objectives………………………………………………………………………..8
2 LITERATURE REVIEW………………………………………………………..9
2.1 What is Phishing……………………………………………………….………..9
2.2 Understanding Phishing attacks………………………………………………12
2.3 Why users fall for phishing…………………………………………………….15
2.4 Phishing Mitigation……………………………………………………………16
2.4.1 Technical Approach…………………………………………………………..16
2.4.2 User Education……………………………………………………………….19
3 RESEARCH METHODOLOGY………………………………………………….22
3.1 Methods…………………………………………………………………………23
3.2.1 Interview………………………………………………………………………..23
3.2.1.0 Recruitment of participants………………………………………….…23
3.2.1.1 Interview protocol…………………………………………………………..23
3.2.2 Survey……………………………………………………………………….24
3.2.2.0 User data…………………………………………………………………….24
3.2.2.1 content of the survey…………………………………………………….24
3.2.2.2 Sampling used………………………………………………………..……..25
3.3 Disadvantages of the methodology…………………………………………26
4 RESULTS AND FINDINGS FROM EXPERT INTERVIEWS………………..26
4.1 Stakeholders incentives to mitigate phishing…………………………..……27
4.2 Expert recommendations…………………………………………………..28
4.3 Why users fall for phishing…………………………………………………30
4.4 Who should protect users against phishing?…………………………………32
4.5 users reaction existing anti-phishing methods……………………………….33
4.6 How users make decisions on whether websites or emails are genuine or not
4.7 Technical method of mitigating phishing……………………………………….34
4.8 Anti-phishing educational…………………………………………………….….35
4.9 User education Versus Technical solutions…………………………………….36
4.10 How to improve existing anti-phishing methods……………………………..36
5 RESULTS AND FINDINGS FROM USER SURVEYED……………….……..38
5.2 Online security perceptions…………………………………………………..38
5.3 How to avoid phishing………………………………………………………..39
5.4 Protections against phishing………………………………………………….41
6 CONCLUSIONS AND FUTURE WORK…………………………………….42
7 REFERENCE……………………………………………………………………43
8 APPENDIX………………………………………………………………………48
1. Introduction
Advancements in information technology has led to the evolution of digital era making it more effective and easy for people. People can now sell and buy goods, do banking activities and participate in political activities as well for example online elections. When it comes to communication, you no longer need a computer to send and receive an email, you can just use your smartphone which is more portable and an internet connection.
However the advancements in Information technology has been a double edged sword, with the ever increasing accessibility of the internet, people tend to share information about themselves and as a consequence, it has made it easier to access someones personal and confidential information. This is an opportunity that has well been exploited by cyber criminals who manipulate and exploit consumers financial data such as usernames, passwords, card numbers and other valuable financial information and in this way, cyber criminals are able to compose personalized attacks to persuade the intended victim to grant their malicious requests.
One of those major types of cyber crime is called Phishing.
Phishing is a social engineering form of attack where the attacker spoof emails with the aim of tricking people into sharing the confidential data. Most of the time the target victims perceive these emails to be coming from trusted people but in real sense these emails come from con artists, (Jasan Hong, 2012). Instead of targeting directly the systems used by these victims, phishing attacks target directly the people using the systems and it bypasses the majority of the organization security measures installed and as (Michael Workman,2008) put it, persuasion technique makes users engage in emotions like excitement and fear in order to divert their attention. This persuasive influence may be delivered through a phone call, a private message or an email as a means of distracting the victims decision.
1.1 Problem Statement
Various solutions have to control phishing attacks have been proposed however there is no solution that we can say is a “silver bullet” against phishing attacks, hence phishing has become a more common measure to commit e-crime.
Every time academic researchers come up with ways of detecting and preventing phishing, phishers changer their strategies by exploiting the various vulnerabilities found in the currently implemented solutions.
According to the Anti-Phishing Work group (APWG), the reason why phishing has become so rampant is because it’s easy. 460,000 unique phishing websites were observed, this is a record that had never been experienced before.
In 2016 from January to June there was an increase in the number of phishing website that were created with January standing at 86,557, February 79,259, March 123555, April 158,900, May 148,200 and June 158,800.
Out of this observation , the APWG found that retail industry was the most hit by phishing attacks, which was far much ahead of other industries with a standing of 43%, while the least hit was the government which stands at 1%(Anti-Phishing Work Group, 2016).
Financial Fraud Action which coordinates fraud prevention for the UK Financial sector states that that there has been steady drop in the number of phishing websites that mostly target the UK bank and building societies between the period of 2012 and 2016, where 2012 the record stood at 256,641. The figure went down to 14673 in 2016. This drop is closely attributed to customers using antivirus software and other packages that are provided by the bank. One reason for this being the technological fire that has been employed by the banks. Despite this, clearly there is a substantial increased number of phishing activities that is carried out.
Presently, close to 50% of these phishing attacks have been directed to either the financial sector or the retail ( Anti-phishing Work Group, 2016) but there is eminent risk that phishing will also target the single sign-on that is going to lay every users online identity details open to phishing if a more secure means is not found soon enough (Lance James, 2013).
1.2 Aim
The main aim of this dissertation is to identify the approaches that can be used to mitigate phishing attacks so as to enable information integrity, availability and confidentiality.
1.3 Objectives
- Analysis of the Phishing attacks and how an attacker could use this attack to exploit online users.
- Critically analyze why online users fall for phishing.
- Provide guidance to stakeholders on how to mitigate the phishing threat.
- Define recommendations and further work. The recommendations will be used to know where the scope of this study could be extended.
2.0 Literature Review
In order to meet the research aim, it is necessary that we first understand what is meant by the term phishing, explore the damage it can do to various institutions and how it can be mititgated.
2.1 What is Phishing?
The internet has brought convenience to many online users in terms of exchange of information, but at the same time it has also provided many a perfect platform for cyber criminal activities.
The attack platform has changed from computer systems to humans and this has increased the barriers of technological impacts of the crime . One example of human centered attack is phishing.
According to (Jansson K, and Rossouw von Solms,2013), phishing is a kind of social engineering that aims at gaining an online user’s trust through impersonating legitimate institutions. It resembles the fundamental principle of “fishing” in a physical world, but now instead of luring fish, human beings are lured using authentic looking emails and websites.
Various definitions of phishing exists however, according to Oxford dictionary:
“It is a fraudulent way of sending emails that purport to come from trusted companies with the aim of inducing people to reveal their personal and confidential information like credit card numbers, passwords, etc ”.
Before having a deeper understanding of how and why phishing attacks work and how to mitigate them, lets first explore some of the definitions existing. Due to its constantly evolving nature , currently there is no universal definition.
In Phishing attacks, the attacker deceives the victim to reveal his/her private and confidential information. The technique employed usually involves an email and or a website that is similar to the legitimate email and website (Gregg Tally, Roshan Thomas and Tom Van Vleck,2004).
According to (Lance James,2005) Phishing is an online activity done by sending forged emails to users falsely imitating a legitimate and authentic institution in order to disclose their confidential information.
A standard definition should be applied to most of the phishing activities taking place currently and therefore the definition according to (Lastdgrager,2014) would be; “Phishing is a deception act that is able to scalable and the attacker use impersonation to obtain confidential information from the victim.”
Considering the fact that phishing is a process, a taxonomy should be in place to make sense out of the complex nature of the attackers by mapping out the attack life cycle (Wetzel,2005).
The taxonomy is as follows:
Planning – Attackers first decide on their target and the kind of information they plan to steal.
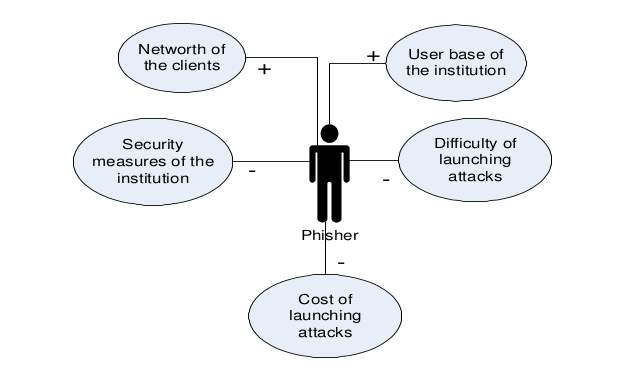
Fig 2.1 A model of phishers decision process
The users base of the institution – a higher institution user based will translate into a higher number of phishing emails.(Franklin J, Perrig A, Paxon V and Savage, 2014) states that averagely in every US household there are 6 credit cards and their insurance is concentrated around 5 banks there is an approximately 15 – 45% chance that these households will receive a phishing email from these 5 banks however (SC Media,2017) states that this rule does not apply to, attackers with specific victim information.
The net worth of clients – A higher clients’ net worth will translate into a higher return on an attack hence phishers tend to target victims with higher net worth.
Security Measures that are implemented by the Organization – organization with stronger security measures are much harder for phishing attacker to penetrate. Ways through which an attacker can learn about an organization’s preparedness is through publicly available information and previous attack experience.
Credential value - more valuable credentials invites frequent attacks. As at now small and medium business accounts are for sale in the internet black market. While on the other hand ,credit card numbers have become cheap, meaning that attacks that target these accounts will be on the rise.
Setup
Attacker will set up an infrastructure after deciding on a target and one of the key points here is that these phishers heavily rely on hackers when they want to launch large scale attack and they will go to greater heights to make sure they remain stealth and undetectable. To that point they exploit register with weak security loopholes and also operate from countries with weak law enforcement resources and also these phishers make use of proxies to hide their location(Franklin J, Perrig A, Paxon V and Savage, 2014).
According to (SC Media, 2017) Botnets are very critical tools used to launch and cover up the attacks. These botnets are configured as proxies so as to hide the phishing trail, making it difficult to investigate.
Attack
After the tools have been set up, an attack is launched through various vectors. The most common vectors are email and websites.
Email - spammers first send phishing emails using spam relays anonymous mailer, and botnets (Xing S, 2012). When the packets arrive at the ISP gateways these email packets are put together, then the gateway filters them after which the mail transfer agent moves them to storage.
When users log in to their email accounts, the mail client connect them to the mail storage through users ISP and then download the mail to their personal machine. On the other hand if the user mail client is also a web client, then it connects directly to the mail storage and retrieves the emails through web interface.
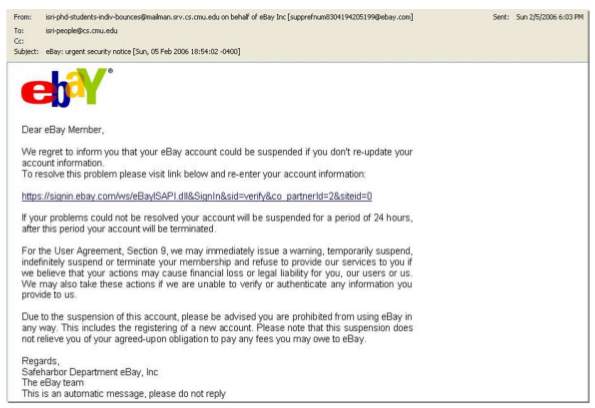
Fig 2. A Phishing email from eBay that is requesting their users to log into their account and update it. It also warns the user of account suspension if he/she fails to do so. The email and the website URL are spoofed.
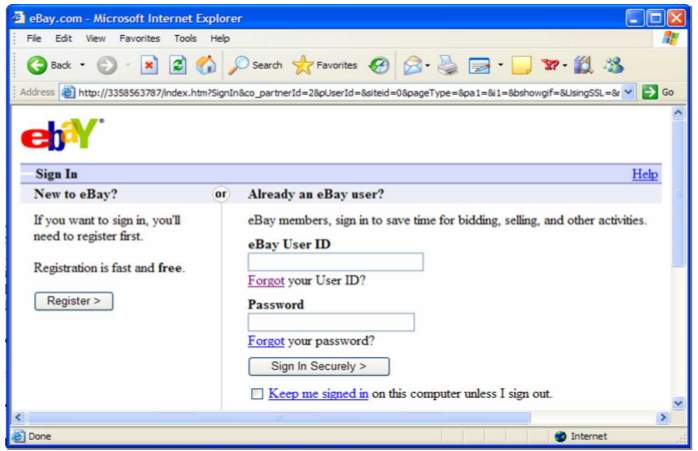
Fig 2.5 This is an example of a phishing website that users see when they click on an email link
2.2 Understanding Phishing Attacks
(Schneier B,2006)observed that methods of attacking a computer network can be seen in terms of increasing abstraction and sophistication.
Many of the real attacks are exploiting psychology as much as technology and according to Schneier, the traditional wave of attacks were physical in nature, they targeted computers, the network devices and the wires between them with a goal of disrupting the flow of information.
Then came came the second wave that consisted of syntactic attacks targeting the vulnerabilities in the network protocols, software implementations or the encryption algorithms. The third wave comprised of semantic attacks which focused on how human beings assign meaning to various content.
(Richard Siedzik, 2011) goes further to state that people always want to believe what they see in print and unlike the other two waves of attack, the solutions to semantic attacks lies somewhere other than “in the math”.
Phishing is a type of a semantic attack hence trying to make computer systems robust enough is not sufficient enough to solve the phishing attacks because phishing attacks do not exploit system bugs. Furthermore, phishing deceives users into interacting with the message from the attacker on their own computer systems. Successful attacks highly depend on the level of discrepancy between how a user perceives a communication, for example a web page or an email message and the communication’s actual effect. (Rachna Dahmija, J.D. Tygar and Marti Hearst,2010) goes on to state that for a phishing attack to be successful, it should not only present a high credibility email and web presence to the victim, they must also create a very impressive presence that will cause the victim to fail to recognize the security tools that have been installed on the web browser.
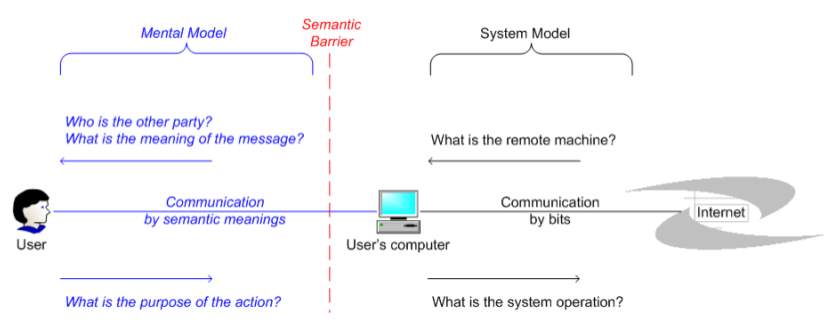
Fig 2.9 Semantic barrier between a user and his/her computer
The figure above shows how a typical internet communication takes place. When human beings play a role in the communication process then just protecting the system model is not enough because the message being communicated depends not only on the exchanged bits but also on the semantic meaning derived from the bits and according to (Richard Siedzik, 2011), success in any phishing attack shows that humans are not always assigning proper semantic meaning to their online interactions.
2.3 Why Users fall for Phishing
Phishing is a type of semantic attack and other than exploiting system vulnerabilities, it takes advantage of the human interaction with the computers.
(Schneier B., 2000) goes on to state that this type of attack takes advantage of the fact that users usually trust email addresses and websites on the basis of surface signs, but these signs give little meaning when it comes to trust information (Rachna Dahmija, J.D. Tygar and Marti Hearst,2010) hence users fall for phishing not because of technological failure but rather because of poor online decisions they make(Kumaguru Ponnurangam,2009).
Various theories have been proposed to explain why users fall for phishing attacks.
Trust and Authority – Human beings have been designed to inwardly trust authorities. From the dawn of the ancestors society has been built to trust and obey authority figures from parents to school teachers, Rock stars or a political leader(Don Mosley,2011).
When daddy yells, “Bring that newspaper.!”, the kid’s body muscles move even before taking time to think on how to respond. When a victim receives an email marked as “High priority” with some consequences attached to it if the victim does not perform certain actions , it is engaging same authority response mechanism we have been obeying for thousands of years.
Our social-economic culture has made us trust the validity of certain institutions. Most of us will not hesitate to deposit money at a certain bank because it has been there for years, we will walk into a huge mall with a large banner “Best Buy” to buy a new electronic instead of the guy selling electronics out of his van in an abandoned building.
According to (Markus et al,2010) we cannot determine the validity of any business transaction without verbal, physical and visual clues and this is the major cornerstone of email advertising. If an email resembles some official correspondence, then there is a very good chance that you will open it. According to bounded rationality, (Slovic,1987) states that, users make decisions based on the information they have at their disposal. People will make a decision on the risk on the basis of the foreseen seriousness of the consequences and if there is no foreseen risk then there is no calculation that are made. (Dhamija, Tygar and Hearst,2012) did a study on how online users fall for phishing attacks and some of the major observations that informed most of the users decisions included:
- “If the URL loos suspicious, I wont trust it”
- “When I see the website verisign, I will certainly believe its not phishing”
- “I hate statements like, this message is authentic”
However Markus et al states that those points outlines above only describe the ability of the users rather than their habits.
Some of the online users believe that the already existing online security is stronger, they despise having an interruption on their task base activity because they become fatigued by the warning messages. But according to (Dhamija and Dusseault,2008) one of the reasons for this fatigue is because the warning messages are presented in a confusing way and some of the user education is also too complex to understand for some of the users who have no technical background.
(Kumaguru, Cranor and Hong, 2009) goes on to state that many users not only know about the security indicators but also that these indicators get spoofed by the phishing attackers. A research that was done by (Furnell, 2015) indicated that while most of the online users recognize terms like hackers and viruses, only about 68% claimed to know what exactly phishing was, out of this percentage that ha heard about about phishing, some understood it incorrectly as they thought it is referring to the topic of the message and not the message intention.
In addition to that, users don’t take internet security as a primary activity and hence they don’t look out for the online threats in the first place(Anandpara and Roinestad,2007). There is also a growing complexity of the phishing attacks based on the knowledge that the phishing attackers gather on how users react to most of the phishing attacks and the phishers build up on this.
2.4 Phishing Mitigation
Numerous mitigation methods exists and according to Purkait who conducted an extensive research in 2012 about the Phishing attacks countermeasures suggests that phishing detection can be classified into 2 types:
- User education
- Technical approach
2.4.1 Technical Approach
(Wilson and Argles,2011) did a survey on anti-phishing measures and states that some of the technical anti-phishing measures include content based filtering and blacklisting.
In content based filtering, the contents of the email is examined for matching malicious URL (Hossain Shahriar, Tulin and Victor Clincy,2015) goes further to state that this technique can be used to determine the source of the email hence help in decreasing the attacks to a greater length.
Attackers usually send bulk emails to mark potential victims, the emails contain fake source address and routing information and according to (Ammar and Atawneh,2013) this has been made possible due to the vulnerabilities that exists in the SMTP protocol making the email seem like they are coming from legitimate entities hence the attacker remain undetected.
Anti-phishing filtering mostly supplements the traditional spam filtering techniques and as (Robin Van Meteren,2000) put it, filtering systems classifies unseen content into a positive class C(relevant to the user) or into a negative class -C (irrelevant to the user). These principles help in classifying the content into either benign of suspicious content hence prevent user computers from being compromised by malicious emails(Australian Signals Directorate,2017).
Some of the anti-spam filtering techniques include:
- Disallowing contents that cannot be inspected, for example, Zip files and RAR and also inspecting the passphrases-protected archives.
- Decline incoming emails having the organizations domain as the sender but don’t originate from the servers that are approved by the organization.
- A content disarming and reconstruction software can be used to sanitize email attachments, this software replaces the attachments with a new file that contains the same content without any malicious content.
- Quarantine hyperlinks and emails attachments from service providers that provide email addresses to anonymous users since attackers most of the times use such emails because they lack attribution (Australian Signals Directorate,2017).
One of the instant means of blocking malicious content online is blacklisting. This approach uses a reputation intelligence to block malicious content. It is more economical because it does away with any further need for an in depth analysis and it is done before any policy based analysis is done. It can be done both manually and automatically, with a manual blacklisting being prone to less false positives(Wilson and Argles, 2011) because according to (Downs, Holbrook and Cranor, 2015) Heuristic techniques looking out for phishing like behaviors have a higher rate of false positives as well as easy for the attackers to bypass.
One of the ways to blacklist is to use access control lists (ACLs) to filter by restricting traffic from certain IP addresses however (Wilson and Argles, 2011) states that these ACLs have a wider scope that are more complex and unable to automatically update using dynamic feeds.
An earlier research carried out by (Gutek and Bikson, 1984) suggests that 90% of most of the system failures resulted from human/social aspects and not technology and phishing is that threat with a human cause rather than a technical one. (Downs, Holbrook and Cranor, 2015).
According to (Kumaguru, Cranor and Hong,2012), technical approaches that are implemented at the toolbar are complicated as users find it difficult to interpret the information displayed on the toolbar hence they ignore the toolbar warnings.
(Miller and Garfinkel, 2014) did an evaluation on the toolbar and found out that most of them are ineffective. A simulation of 5 phishing attacks and 3 toolbar found that many users chose to ignore the warnings given on the toolbar because one of the main indicator that the users depended upon was the visual appearance of the website.
On the other hand many of the website owners have poor and inconsistent security practices, for example, some of them do not use SSL(Secure socket layer). On the other hand (Wu et al, 2013) did a study which showed that having a printed tutorial on how to use toolbar information reduced to a greater length the users tendency of falling for phishing. In their recommendation they suggested that interruptions that are active such as pop ups that are timed to interrupt dangerous actions are effective more than the toolbar. They recommended that warnings should have alternative paths as well instead of just suggesting non continuation of the action.
According to (Egelman and Hong,2014) users are more likely to pay attention to active rather than passive warnings and even when users pay attention to browser warnings on phishing attacks, users would still believe that emails containing those phishing links were genuine because even if users recognize the warnings, most of the times they fail to read them hence (Egelman and Hong,2014) recommend that serious warnings should be designed differently from other browser warnings. They suggest that effective warnings should be able to interrupt a user’s primary task and provide a clear choice on what to do next but one of the provided choices should not allow the user to ignore the warning. (Dhamija et al,2012) however states that even when users are presented with options, they fail to read an immediately click OK, hence an improved user interface guideline on website security should be designed because currently most of the security features are confusing and misleading.
Additional devices should be introduced, for example, mobile devices used in encrypting passwords before being entered into the authentication page by the user, an approach that will render the password useless to the attacker. Although this approach can be subject to other forms of attacks like session hijacking, the session can be managed from a peripheral device that will be able to bypass any malicious content already in the computer. (Welgold and Hitgen,2011) goes on to state that although this approach still depends on the user who is not to be tricked by phishing messages, It will help in improving security.
2.4.2 User Education
Users are more likely to fall for phishing attacks because of the sensitive trust decisions that they have to make when conducting online activities. Psychologists have the opinion that when under stress, most of the people do not look back and reflect on the options they got before they make a decision.
Studies have shown that people under such circumstances do not consider all the possible solutions and hence fail to make rational decisions(Keinan, G., 1987). During this time, people assess individual options rather than comparing them to others and taking the first solution that works(Klein, G., 1999).
- According to researchers, user education in the context of online security is difficult because:
- Users always take security as a secondary task.
- Users are not motivated to read online privacy and security policies.
One of the most important issues with user education is knowledge retention, the extent to which the audience will be able to remember the lessons over a longer period of time . According to (P. Kumaguru, Y. Rhee and S. Sheng, 2008) retention is an indication of the effectiveness of the training and this is true both for the traditional as well as alternative methods of great user awareness.
In order to maximize this effectiveness,(Anandpara et al, 2007) states that the following learning science principles should be followed.
To learn by doing – According to the theory of cognition and learning, knowledge and skills can only be acquired and strengthened through practice, hence users learn by clicking the phishing emails then user education materials are presented when the user falls for phishing.
Immediate feedback – According to (Anderson, J. R., 1993) immediate feedback to learners improves the learning efficiency and provides guidance towards the correct behavior. (Anandpara et al, 2007) goes on to state that feedback is provided to the user through the interventions brought after a user clicks on a phishing link.
The principle of Contiguity – (Myers, R. E. and Anderson, R. B., 1992) states that a computer aided instruction effectiveness will increase when pictures and words are presented in a contiguous manner rather than being isolated from one another, for example, in one of the experiments, students learning about lighting storms had a good performance when pictures and words were close to each other.
(Kumaguru et al,2012) goes on to state that when users receive such training they were less likely to fall for phishing emails. The effectiveness of the training would increase when the users received the training twice.
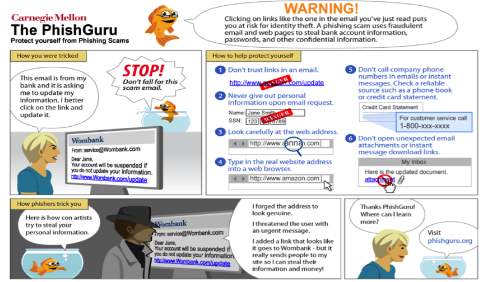
Fig. 3.3 Phishing training
‘Phishguru’ Is an online security training system teaches users on how not to be deceived by phishers by using simulated phish attacks. According to (Kumaguru et al, 2012) Phishguru provides more effective training than the traditional methods because it’s designed to be more engaging.
The principle of personalization – According to (Myers, 2001), Conversational styles improves learning more than the formal styles. People tend to understand instruction materials more when they are presented in such a way that the learners feel like he/she is part of the conversation.
(Myers, R. E. and Anderson, R. B., 1992) goes on to state that conversations are enhanced when “I”, “We”, “Me”, “My”, “You” and “Your” are used.
The argument of whether anti-phishing education is effective or not is out of context because according to (Wilson and Argles, 2011) current education material do notrelate to familiar scenario that a user can understand. (Kumaguru et al, 2012) goes on to state that the learning materials can be more effective when they are related to real world scenarios. In order to write a successful training, (Parsons, McCormac and Fergason, 2013) states that it has to be personal , contextual and meaningful because evidence is suggesting that training is more likely to be successful when the subject is of relevance to users.
The principle of Story based agent environment – An agent can be a character that can help in guiding learners in the learning process. The character or characters can either be visual or verbal, real or cartoon like characters. According to (Moreno, R., Myers, R. E. and Lester, J. C., 2001) when an agent is used in a story based learning content,learning will be enhanced. People put more efforts in understanding a learning material when an agent is there to guide them in the learning process
(Myers, 2001). The learning will be enhanced further if the learning materials are within the story context. Stories stimulate a learners cognitive process because they organize events in a framework that is meaningful.
Before 2012, studies that were done to check the effectiveness of the existing anti-phishing material found out that users were able to identify fraudulent websites after training but the primary confusion was on interpreting the long URL’S and (Miller and Garfinkel, 2011) suggested that URL information and domain names to be part of the training as well. They go on to state that its ineffective when the training only focuses on the website content and the design when checking for the authenticity because in the likelihood of a phishing attack using a Man in the middle attack, the content of the website or the design cannot help in mitigating the risk of phishing.
On the other hand other researchers have argued that education is ineffective and according to (Niesel, 2011), education does not work and that technological improvement is the most necessary requirement in protecting users against phishing because education is unrealistic.(Schneier, 2006) goes on to state that educating the user is futile and would be better if it is replaced with an improve technology. On the other hand (Ranum, 2014) argues that the most effective learning tools are pain and humiliation and the moment people feel that way, they will be motivated to find better ways of mitigating phishing attacks hence people should be left to learn from their mistakes.
(Anandpara, 2007) asks a question on why there is a large volume of anti-phishing materials yet phishing still continues to claim victims. These researchers carried out tests that came to a conclusion that most of the anti-phishing materials tests fear instead of ability to spot phishing. They go on to state that these anti-phishing test remove the natural contexts and introduce artificial ones that only impacts on the test takers judgment where the users were not aware that they were under assessment to recognize phishing but they know they were under observation.
These researchers therefore recommend that the security industry researchers need to continue with the research to make education on phishing more fun, engaging and changing with the times so as to make users engage with it. Secondly, they should invest on the social networking websites which can be able to educate users on how to make good trust decisions when they are confronted with phishing.
3.0 Research Methodology
The main aim of this research was to investigate on why people still fall for phishing attacks and how to mitigate them. The first step was to conduct a literature review after which, expert interviews were done followed by user surveys to discover both expert and user opinion on phishing.
Opinions on both the users and expert were gathered, users were asked questions relating to their experiences with phishing and their preferred sources of avoiding phishing . The intention of this was to have views on why users fall for phishing and how to mitigate the attacks.
In a social science methodology, pattern may vary according to the source, for example in this report 3 patterns have been identified by (Baroudi and Orlikowski, 1991) and they are: positivism, interpretive studies and critical studies. Although all of this three paradigms could offer an insight, positivism is the most dominant.
- Positivism is defined as trying out a theory so as to describe an event in a more factual and objective manner(Baroudi and Orlikowski, 1991). And according to (Staub, Boudreau and Grefen, 2012) positivism defines a theory as something that can be empirically falsified.
- On the other hand interpretive studies try to reject the factual and objective idea and attempt instead to have an understanding of phenomena from the meaning that is assigned to it by the participants.
- While Critical studies brings out the assumptions that have been assumed by highlighting the deep seated contradictions(Baroudi and Orlikowski, 1991).
The main aim of the dissertation is to investigate and improve anti-phishing activities and not to test phishing theories. The approach that will be adopted by this research work will not heavily rely on the positivist approach because in seeking to examine user interaction with phishing attacks and the anti-phishing measures, the approach has to be critical in nature because critical approach allows for a certain level of victimization which other approaches like interpretive studies and positivism do not.
According to (Myers, 2011) there has been a discussion on whether these three approaches no matter how philosophically distinct they may be can overlap in some way in practice, however (Stahl,2012) states that one of the main advantage of the critical approach is that it seeks to overturn oppression and that this approach strives to make the affected party be in a position to take part in a discourse hence understanding better a users experience and giving more information on phishing that will seek to include rather than exclude.
3.1 Methods
When seeking to enlarge the phishing body of knowledge and also meet the practical concerns that surround phishing, an interview and a survey approach using a mixed approach.
Mixed approach according to (Roselyn Cameron,2015), collects, analyze and interpret quantitative and qualitative data that investigate the same phenomenon.
It is premised on the assumption that a combination of both qualitative and quantitative approach will bring a better understanding of a research problem.
(Baroudi and Orlikowski, 1991) states that several factors influence why a research approach is chosen. One of our research objective was the need to use the expert opinion from the interviews to confirm the issues that were identified during the literature review, introduce some of the issues that were forgotten by the researcher and in order to facilitate user survey by using both qualitative and quantitative approach with users in order to confirm the expert view.
The other reason was the context within which a researcher is trained and the chosen approach itself. This research will not use the collected data to test and revise any theory on phishing but rather illuminate the data. Meaning that the approach taken while questioning was inductive with evidence that led to the theory and not deductive where the theory shaped the questions.
3.1.1 Interview
3.1.1.1 Recruitment of Participants
The experts were mainly recruited from our own and friends’ network of contacts. They were candidates from different organizations working at different levels in the company in order to get varied opinions.
A total of seven experts who were either responsible for or had knowledge of in terms of the operation or policy decision with regards to the malware prevention in the company were contacted with an aim of securing between four to five interviews.
Three of the interviews were done on phone and the remaining two through email in accordance with the Leeds Beckett University guidance on ethics. The interviewees consisted of one network security engineer, a security consultant, a technology company representative and two bank representatives.
3.1.1.2 Interview Protocol
Semi structured interview protocol was adopted. This protocol allowed the researcher to ask structured questions that enabled a comparison between different respondents while at the same time giving the interviewer a chance to explore explore specific areas of relevance to each of the interviewee (Rosenthal, R. and Rosnow, R., 2012 ).
The interview was began by asking each of the experts their backgrounds and their responsibilities in the company. The researcher then asked some open ended questions on phishing and how they impacted on them personally and their organizations, the loses, the current and future state of phishing and lastly, to what extent they though the countermeasures were effective. The experts were then asked to give a set of recommendations which at the end the experts were asked to give feedback on them and provide additional recommendations.
The interviewees were first asked about some of the stereotypes about phishing attacks and their opinion on why most online users fall for phishing attacks. The main intention of these two questions was to raise any existing preconception that might have influenced subsequent answers. After this, they were asked about how their responsibilities of protecting online users, how it can be shared so as to strike a balance between education and technology. This was done so as to investigate some of the tension that exists between education and technological approach to mitigating phishing attacks as was evident in the literature review. They were lastly asked to provide a summary on phishing and how it is evolving.
3.1.2 Survey
3.1.2.1 User Data
Data was gathered using Smart Survey. This process allowed for the respondent to remain anonymous, this is important because they were being asked to respond honestly on their online behavior.
3.1.2.2 Content of the Survey
The survey had closed ended and open ended questions. The questions in the survey were greatly influenced by the questions that were identified during the literature review and also from the expert opinions that were gathered earlier. For the purposes of comparison between users and experts opinions, the questions below were examined :
- How do users respond to phishing?
- What are users experience with the anti-phishing education?
- Online and offline user security attitude and who has the responsibility of protecting the user from phishing attacks?
3.1.2.3 Sampling used
Sampling involves selecting a subset of a whole population and the main reason why it is done so is because of cost.
To obtain a good representative of sample of computer users is impractical within the constraints of a project and hence we used a simple random sample where all samples had an equal chance of being selected. This was like drawing 3 names from a hat that had all the students names in the class, any of these names had an equal chance of being chosen.
In our approach links were posted on on facebook and other social media networks.
A decision to participate or not to participate in an online survey depends on a number of factors, from the selected persons’ social environment to household structure, household characteristics like the social demographic characters and psychological predispositions, the interviewer’s characteristics and the interviewer – interviewee interaction and so generally speaking, these are some of the reasons that may be connected with their refusal (Natalja Menold and Cornelia Zuell, 2011).
These factors will communicate the importance of any survey topic, the incentives and the interview length. Regarding the household characteristics, some of the participants fail to respond because they think its a “waste of their time” or an “invasion on their privacy”.
According to (John Cornish, 2002) response problems in surveys are experienced when the questionnaires are not adequately prepared and or the samples refuse to respond. This is a reflection that an unsuccessful attempt to get information from eligible samples has occurred. (Oracle, 2012) goes further to state that people are most likely not to respond to a survey when the person conducting the survey has been unable to make contact with the selected group and particularly if the survey is compulsory, hence the contact level in a survey influences the quality of information. On the other hand as well, once a contact has been established, chances are that some of the participants will still refuse to cooperate.
Non response from survey participants has several effects on the results of the statistics by contributing to a variance increase in sampling because the size of the sample will decline from the original one and this brings about biases when there are differences between those who responded and those who did not. The second bias will result from the different population size between those that participated and those that did not participate, this is referred to as under-coverage bias.
3.3 Disadvantages of the Chosen methods
While open questions might have richer response while at the same time allow for new topics too be raised, the respondents may find them to be much of a hard work because they are cahllenging to interpret.
Closed ended questions on the other hand can be simple to analyze however they offer little clarity that that would reflect on the respondents experience hence missing the opportunity to discover the issues that were not considered by the researcher(Dawson, 2007).
It was challenging due to the topic, to come up with survey questions and not to use emotive words and or appear to be bias however due to the fact that it was an online survey helped reduce that factor. On the other hand some of the points appeared to be ambiguous because the survey had not been tested on a representative sample of the intended audience, for example a number of the respondents never understood the meaning of phishing as it was presented in the survey.
For the semi-structured interview method, one of the main disadvantages is that it can be too restrictive even though its considered to be less restrictive than an interview that is fully structured. It involves asking the all the experts the same questions and this reduced the opportunity to tailor the interview to an individual level.
On the other hand some of the interviewees who accepted the interview invitation, failed to turn up or canceled the appointment and according to (Dawson, 2007), this is one of the main challenges in academic interviews as the interviewees fail to identify any benefits to them in participating in the interview and sometime also, they worry about the breach of their anonymity.
4.0 RESULTS AN FINDINGS FROM EXPERT INTERVIEW
| CATEGORIES | FINDINGS |
| An evolving threat |
|
| What stakeholders should do to mitigate phishing |
|
| Law enforcement and education |
|
The evolution of phishing has been more organized and targeted, and it is being used as a gateway to other cyber crime attacks.
The experts interviewed were first asked to define phishing attacks and their trends and a major observation that they all made was that, phishing is becoming more and more organized.
“These are criminal gangs whose main aim is to perpetrate fraud, gone are the days of the teenage hackers, these are organized criminal gangs that have both a business and a contingency plan. What we have come to see is that these gangs are not only involved in one crime but they commit others as well.
One of the well known gangs is the ‘Rock Fish Group’ consisting of phishers from Europe and some of the researcher has claim that close to 90% of the 1 million URL his group was processing in 2012 has some characteristics of Rock Fish in them” (Male, Network security Engineer).
All the experts were in agreement that phishing has evolved to become more effective and has become a challenge for the spam filters to detect and an example can be drawn from the recent attempted attacks on various executives. According to a research that was carried out by Indiana State University, 16% of the participants fell for the regular phishing emails while 72% fell for the spear phishing emails(Jogatic, T. N., Jakobson, M. and Menczer, F., 2012).
4.1 Stakeholders Incentives to mitigate phishing
When the experts were asked on how phishing impacts their organizations, the responses they gave provided an insight into what motivates the organizations into fighting phishing attacks.
One of the reasons that was found was that most of them are motivated to invest in protecting their resources against phishing after suffering losses from the attacks but according to some of the evidence, not all of these victims have put up that investment.
(Female, Security consultant) stated that many of the medium organizations that had consulted her earlier did not have any phishing strategy because they had never been victims and if by any chance they could have fell victims, they could have lost a lot of money. Reputation is another factor and most of the organizations especially the financial ones were spending much more money in anti-phishing campaigns because they were positioning their banking services as one of the safest in the region.
Most of the ISPs have an incentive when their email systems are targeted because these attacks seeks to compromise customers web-mail account hosted by the ISPs, these attackers use them as spam mail attacks and the ISPs motivation is to ensure that a proper flow of mail services and avoid email servers from being blacklisted.
(Male, Bank Representative) went further to state that fixing an infected computer can be costly and most of the banks need a re-installation of their operating systems. Internet registrars have been lagging behind in the fight against phishing ans according to the bank representative, these registrars are not motivated in fighting phishing as the same phishers still pay them to register their phishing domains but (Male, Network Security Engineer) disagreed by stating that phishers are now using fake credit card details when registering their domains.
4.2 Expert Recommendation
R1. Academic Researchers and regulators need to have more investigations on incentives.
From the findings some of the stakeholders are not well equipped to protect themselves against online attacks like phishing, hence lacking the burden of proof on their shoulders would amount to very less in the fight against phishing and on the other hand internet service providers who are well placed to clean the affected machines are not motivated to do so therefore a further research is needed to come up with incentive models.
Web application vendors, Operating systems vendors, Browser vendors and ISPs are some of the key stakeholders with influence over the phishing attacks.
(Male, Technology Company representative) states that the vendors and the service providers are in the best position to fight against these attacks. For example operating systems security has a greater effect on the general security and the expert had kind words for the Microsoft for putting efforts in trying to harden their operating systems but still added that more needs to be done. Browsers are a very strategic position in fighting phishing, because first, browsers can warn users. A study conducted in 2014 showed that Firefox was able to present phishing warning effectively.
Attackers are fast losing the war on the email attack because many users are now running both spam and virus filtering and so many of the attackers have resorted to sending the users a URL to redirect them to fake websites containing malware (Egelman, S. and Hong, J. 2014).
R2: Operating system vendors should secure the operating systems by implementing the sure coding, improving the default security by building an anti malware capability into their operating systems and doing vulnerability patching.
Host files need to be protected by Microsoft and other operating system as done by the anti-virus software in order to prevent various online attacks (Zone alarm, 2016). Operating system should also constantly be patched to provide strong defense, however one of the disadvantage of patching is that the distribution of patch will give the criminals information on the vulnerabilities being patched, (Egelman, S. and Hong, J. 2014).
R3: web application security should be improved and equipped with the application fixing capabilities.
More than 70% of phishing websites are either hosted on free websites or hacked ones. SQL injections, Cross Site Scripting (XSS) and other vulnerabilities have made these websites prime targets for these attackers. (Male, Security Consultant) proposed that technical organizations like the anti-phishing work group (ASP) should be producing a list of regular basis of the frequent hacked sites and notify the operators of their vulnerabilities.
If these systems are compromised due to lack of technical skills, then a way should be provided to provide education resources and training so as to help secure these applications. Another way is to encourage the hosting service providers to run intrusion detection and intrusions prevention on these applications they are hosting and also scan for other malicious web pages that have been created for phishing attacks.
R4: Improving the performance of the integrated web browsers by the web browser vendor to provide anti-phishing warning with the aim of catching close to 90% of the phishing URL’s within a few hours after they are published online.
Currently the browser integrated warning is only catching between 40 and 60% of the phishing URLs within three hours after they are launched (Sheng Wadman and Waner Cranor, 2013).
(Moore Clayton, 2014) states that one of the ways of improving blacklisting is by gathering collecting phishing feeds from multiple sources so as to maximize coverage, but many of the browser vendors are still not motivated enough to implement some of these heuristic methods because they fear that they could attract a lot of false positives which in turn could expose the vendor to costly lawsuits.
R5: researchers to focus more on heuristic methods that minimize false positives.
There exists a lot of false positives in most of the current anti-phishing heuristic methodologies(Moore Clayton, 2014). However in order to have a better use of these heuristic methods there should be very low false positives. But with billions of visited websites everyday even 1% of false positive would mean that millions of web pages are labeled falsely hence for heuristic method to be implemented, false positive level should be close to zero ( Sheng Wardman and Waner Cranor, 2013).
4.3 Why Users Fall For Phishing
Stereotypical Victims
Stereotypical victims do not exist and as (APWG, 2012) put it, users are very busy to even stop and think about the risk of phishing for a second. (Anderson, R. 2014) adds that it’s very difficult to come up with a clear view of who falls for phishing attacks because most of the time the victims are not honest mostly because of the embarrassment on what happened, additionally even experts fall victims of phishing attacks
There is no single profile of phishing victims because everybody is vulnerable, and if you just hit them at the right point, anyone can be a victim (Anderson, R. 2014), however some of the experts who were interviewed raised the stereotype of those who were computer illiterate as the major one.
(Female, Security Consultant) stated that there is a category of those without any mental picture of what is happening behind the computer screens despite having knowledge of the existence of both the hackers and viruses.Those who are uneducated and haven’t been sensitized on the risk of responding to malicious emails, and are not computer savvy as well,are not able to detect any malicious content.
User Ignorance
In the literature review both lack of awareness and technical expertise were flagged as some of the reasons for falling for phishing (Anandpara and Roinestad, 2007). (Male, Network Security Engineer, July 2017)said in regards to the ever growing number of phishing victims that,
“if someone believes that there exists some £25 million that is waiting or him/her if he/she sends £25 thousand, frankly then he/she must be stupid and deserves what happens to him/her’’
However this expert related this to lack of mental framework on phishing and went further to state that “How did you come to know that this was right by just reading it on the Wikipedia?, what cross reference did you use?”
The kid will not understand what you are talking about because he/she has not been taught about that. Education is key to most of these attacks. People fail to recognize an obviously looking malicious email hence user education should be continually done.
Carelessness
(Holbrook and Crainor, 2012) found out that some of the online users do not just care about protecting their data, that is why ultimately, it’s users who are responsible for the their downward spiral.
(Female, Bank Representative) said that many of the people are yet to understand how the internet is insecure and it is only when they will be attacked that they will start to accept the impact of the threat.
Security as a secondary task
One of the main reasons for the carelessness was that security was mainly seen as a subordinate to the main task at hand(Anapandara and Roinestad, 2007), most of the time users are undertaking their normal tasks which distracts them from any other awareness.
“When someone opens their inbox there is a lot of emails for example when I go through my inbox, they are so many and most of the times I even wonder what to do with them, do I respond, hold it for later response or just ditch it? Then something comes up demanding my immediate judgment, but that judgment could be the wrong one as well, hence, there is just a certain aspect of the busy nature of our lives” (Male, Network Security Engineer)
People are more used to typing in username and passwords which has made them respond to any username and password request. If you were walking around Beckett pack then someone approaches you and tells you that he/she would like to see your credit card, you would definitely not give it out, but in another instance where you are web browsing and a prompt comes and asks for your username and password, you will happily give it out.
Skills of the Phisher
Despite the lack of awareness, being too busy or any other personal matters, users also have to deal with attacks attempts that are made by skilled and convincing attackers (Anandpara and Roinestad, 2007).
(Female, Bank Representative) said that looking at most of the websites nowadays, they look so genuine and maybe its only the security experts who can pinpoint the difference, because any other person would just accept that the website presented before him/her is genuine. Phishing email intentions is to make the victim act , they are never simple notification, their main motive is to direct someone to some site where they can capture their credentials, most of the time your account will be subjected to some conditions, for example, its a call to undertake some action that is connected to you getting a refund or to keep your account up to date or just something that is of importance to you as a user.
(Male, Bank Representative) stated that banks usually warn their customers to look out for the padlock in the address bar, not to click a link you have not seen before. But Fraudsters have realized that users do not take the warnings from the bank into account and for that they have continued to evolve their phishing site and make them appear more genuine which has made it a challenge for anyone trying to differentiate between a malicious and a genuine site or email. (Anandara and Roinestad, 2007). We are having a new technology and the cyber criminals will also evolve it and change the messaging making it to appear as if it’s coming from a genuine site, for example bank. (Male, Network Security Engineer) stated that:
“ It’s very challenging and even some people in our security industry sometimes are not sure when they see an email, whether it’s coming from a source that is credible or not”.
There has been a development towards the attacks which cannot be detected by just visual detection, these forms of advanced attacks makes it challenging to spot any difference.
4.4. Who Should Protect The User Against Phishing
Before coming up with the best way to mitigate phishing attacks it is important to put into consideration as to whether successful phishing attacks are asocial failure or a technical failure. If its technical failure, the user who usually don’t care about phishing is at risk whereas if its social then governance and regulations may be of help (Wilson and Argles, 2011)
Most of the experts interviewed emphasized that phishing is just another form of fraud manifestation, and one of the guys said that, phishing idea is like a guy who knocks at an old lady’s door and charge her £10000 for fixing her roof.
In some sense, the main issue here is is not technology but humans, they are the weakest lisnk in the security chain. To put phishing into its context, it is the the current weakest link in the internet and as you continue using email, there still exist a huge opportunity for the cyber criminals to exploit that interface, it will never go away (Egleman S and Hong, J. 2014)
Most of the time the impression given is of a powerless user, if not ‘stupid’ who hide behind solutions or at the mercy of a skillful fraudster, and because of this the whole society is having a responsibility of protecting the online users.
Being stupid enough to believe that there is a £25,000,000 that is waiting for you in the bank if you send £25000, then honestly you deserve what befalls you. Same problem became witnessed when the phones became introduced and as it is said, it takes a while for the mores to get settled. This idea is of the same nature as that guy who knocks on the old lady’s door and charges £10 to fix the roof. It’s challenging to question, but ultimately the answer lies in the user education.
4.5 Users Reaction To Existing Anti-Phishing Methods
It’s largely assumed that those who care to remain safe online behave differently from those who don’t. According to the literature review research users care less about their online security. (Anti-phishing Work Group, 2016).
The interviewees as well had the same thought that users never take online security seriously, this can be evidenced by the lack of real world consequences for users who fall victims.
According to (Andy Patrizio, 2012) users feel the pain and some of them decent protective measures that they think will be an obstacle when they carry out their activities online. (Xing, S., 2010) goes further to state that without the users interest to protect themselves, technological solutions may achieve so little, technology will only take you as far. Anti malware and antivirus software protect computer systems but when each time you are prompted with the “update antivirus” and you click ignore or remind me later, then ultimately its human who is causing his/her downfall. There was a general agreement that young users were more security aware but didn’t care much about their privacy which is a weak link that the phishers could exploit.
4.6 How users make decisions on whether a site is genuine or noticing
As discussed previously in the literature review, users are either not aware or don’t care much or are just too focused on their main task at hand and pay minimal attention to security online. Most of the time they depend on gut feelings or other ways like spelling errors. (Furnell, s, 2015).
“some users ask themselves, how do I know whether a site is genuine or not genuine? I don’t, and do I have to care ? Probably not, because my credit card is only used for online shopping and if the site turns out to be fake, then it doesn’t really matter to me, it’s my bank’s problem to deal with not me” (Male, Bank Representative).
Traditionally, users have always been told to look out for site errors like graphics and poor language like spelling mistakes but that is not the case now as the phishers are evolving to become more skilled and evasive. Problem arises now when users no longer know what to look out for as the attack indicators, they now depend on the source of the email and or the site certificate to make the decision, however those two mean absolutely nothing to most of the users. Due to this lack of of adequate mental framework to decide, they now resort to believing whatever it is that they are told (Male, Bank Representative).
(Furnell, S,. 2015) goes on to state that new technologies have even gone ahead to make the situation more worse and even though the current smart phones may present partial solution to this problem, it makes things harder for the user as well.
4.7 How to mitigate phishing Technically
Technology today has saved many people for example, some of the large corporations like banks have implemented immediate email response for suspected attacks.
In the UK for example, this immediate email response has been facilitated by the banking sector structure. The UK in particular, there is a good number of retail banks that are very well organized and are doing pretty good job in watching out for phishing emails, so many sites have been taken down (Wilson and Argles, 2011).
“Personally I believe that we can overcome this challenge we are facing today because we got all the building blocks and honestly there is no need for any new technology, on the other hand education alone is also not enough. The reality is that, all the technology stakeholders should design an anti-phishing system that can be used by everyone and that could greatly reduce the chance of any phishing attacks, however commercial interest and complex legislative processes will hinder that from happening. It would be a big challenge just to roll out one global anti-phishing system without facing the legislative challenges from different countries but speaking from a technical point of view, it’s something that could be solved quickly, if the various industry players and the governments are willing to invest and also agree to overcome certain liberty issues, then to a greater extent we could do away with phishing attacks” (Male, Network Security Engineer).
Another potential solution is the use of smart phones, although according to (Furnell, S., 2015) they have problems of their own, people are now looking forward to having a mobile phone as one of the technical solutions, and with the ever increasing smart phones processing power, we will soon start seeing smart phones based solutions so long as you are using a smart phone. Institutions like banks have to move away from the use of passwords and usernames as well.
Technical solutions can only take you as far, but if the online attitude of the user is not sufficient, then they will continue to be victims regardless of the technology being implemented.
In the end there should be a combination of technology with risk management for the internet, one of the interviewees felt that some of the users activity are too risky to be done online.
He went further to state that, a more risk based approach should be implemented, it’s a challenging one because no one manages risks appropriately. This approach means that you will not allow people do a certain thing s online.
4.8 Anti-Phishing Education
A lot of questions have been raised about the efficiency of anti-phishing education (Kumaguru,P.,Cranshaw., and Hong J.,2015), (Wilson and Argles,2011) (Anandpara and Roinesta,2007) and some of hence questions featured during the interview.
Irrespective of the already discussed technical solutions, we can not ignore the role that is played by education in mitigating the risk of phishing attacks.
“The problems faced by the users will not go away overnight, hence it is very vital to continue educating them” (Male, Bank Representative).
Most of the experts agreed that user education should be started at an early age, and this education could be accommodated in the school lessons on the internet security.
(Female, Bank Representative) stated that looking at the current school curriculum , there is a national curriculum that touched on how to use online environment like the internet and that is the best way to educate this new generation.
“When growing up, there was this Delloite promotional video on online security, it was not technologically heavy, it had a story on how organizations get compromised and end up loosing customers privacy and information. Something that Is dramatized like the Delloite security promotional video would resonate better than just warning about phishing” (Female, Bank Representative).
According to (Liu, W., X., Deng and G., Huang, 2011) when doing an online campaign, try and strike a balance between the message itself and getting it across so that people can really understand what you are putting forward.As time pass by people are becoming more aware, when someone gets a message and and passes it on to other two people, the viral spread is a very powerful thing. There are social networks like the twitter and facebook which different organizations can use as well to educate their customers.
4.9 User Education Versus Technical solutions
Most of the experts had the thought that both technology and education had their disadvantages, not only because of the user weakness but also because of the solutions like the technology approaches which were slow in being adopted. On the other hand, education alone cannot be enough to mitigate phishing.
It is very difficult to have people’s attention hence making educations a challenge. Its only easy to educate users about online fraud and how to protect themselves when they have been victims of fraud, but just in a normal day to day, it is very challenging to educate them and that is why technical solutions comes in as a supplement.
(Female, Security Consultant) stated that technology alone is inadequate, to find the right approach is a challenge and whether or not these challenges can only be addressed by technology or education awareness, is uncertain, ultimately the solution lies with the education, but I also technology has played a major role in trying to solve the problem and there are numerous tools out there that would try to help. Hence the answer therefore seems to be the combination of both of them.
4.10. How to improve the existing Anti-phishing Methods
Apart from the technological challenges like false positives and false negatives, human interface also hinder technological solutions to phishing.
Humans have always been the weakest link in the online fraud, for example, you can install an antivirus and a malware protection, but as many people do each time when prompted with the “New updates available”, they either ignore it or click on remind me later because they dont want to be interrupted (Wilson and Argles, 2011).
Another problem with technical solution is that, some of the technical indicators for example in the browsers are offering more confusion than any tangible help, hence users are being trained in looking out for visual indicator which in the end will mean nothing to them.
With the ever advancing phishers skills that leaves the anti-phishing technology to ever catch up, the organizational ability to justify their investment and deployment controls in anti-phishing can only mean one thing that there they are at least two steps behind the phishers.
According to those interviewed, there are organizations that have tried to come up with initiatives to mitigate phishing, for example UK banking industry. Most of these banking institutions have their own campaigns on Radio and TVs, newspapers, social media and other media outlets, their main aim is of educate the users about awareness on phishing and it’s telltale signs. Banks have their web pages on security where anyone can go and look for information in regards to these attacks.
Academic researchers are also researching on the online behavior of the phishing attacks victims and use the findings as basis in coming up with anti-phishing strategy. Several consumer websites exists where people can go and read a very detailed information about phishing.
From a general point of view, the anti-phishing measures have concentrated more on the financial sector but according to (Information Security Magazine, 2012) there might be other sectors that are facing the same risks but have not been put on the spotlight. For example, it’s very rare to see an educational awareness campaign on the healthcare industry. Electronic health records have exploded and many doctors can now track their patients online, but there hasn’t been any recorded notice or circular from a doctor telling his/her patient not to type his/her credentials in some of the web logins, or to be on the watch because someone may try to phish their confidential data and commit fraud by impersonating the patient and receiving services not eligible for.
Several suggestions were raised during the interview on how phishing could be tackled better:
- Anti-phishing education should start early in life and should be made simple.
- It’s beneficial for the industry players to corporate on phishing education
- Government and law enforcement should be involved with more emphasis on arrest
- More clarity needs to be put on security indicator and how reliable they are
- All operating systems should implement DNS security
- A risk management approach should be adopted on any activity done online
- Users should be motivated to pay more attention to privacy
In conclusion, despite some of the interviewees having their doubts on users being able to mitigate phishing, there was one thing that they all agreed on, that the combination of both technical and educational approach was key to stopping the phishing attacks.
5.0 Findings From User Survey
Although the age factor was not featured in-depth in the literature review, the result from survey has largely reflected students and professionals with three quarter of the respondents being below 35years.
The question on gender was introduced for purposes of filtering. The result came back with an imbalance with over 70% being male while the rest were female. This imbalance was expected given the platform on which the survey was conducted.
Question 3 on computer knowledge level was used to examine whether a higher computer level co-related with higher security awareness. The bulk of the responses came from people with medium or higher computer knowledge.
5.1. Online Security Perception
The respondents were asked how concerned they felt about online cyber crime, they were then asked if they have been a victim of phishing. The respondents were neither very high nor very low worried, although the very low were twice the number of the very high worried.
The level of computer knowledge affected the level of concern, as the computer level of knowledge grew, there was a significant decline in the level of worry as well which was a reflection of a greater confidence in their ability to spot online scam like phishing, as pointed out by (Furnell, S., 2015).
“being a savvy user, I always look out for scams, this has enabled me to feel secure and avoid most of the cyber crime”– female 23-35.
More than 50% of the respondent population had lost money through the phishing attacks and to no surprise at all, those who had lost money through this kind o f attacks have become more concerned about cyber crime which has confirmed some of the experts opinion that people learn through experience.
On the issue of whether people stop to read security awareness messages when doing other online activities can be drawn from the expert interviews and the literature interview which found out that users do not take security as their primary task and from the survey it was found that more than half of those who responded never stop to read these security messages. On the other hand it could also be concluded that some of the users have a feeling that after reading these security messages like once or twice or even a couple of times then that is enough but they do not know that phishing is so dynamic and keeps changing form and it is important to keep up to date with the latest security measures.
Close to 5% of the respondents claimed that they had never read these security messages. From the survey, it was found that the rate of reading security messages drops with the level of concern about the cyber crime. About 22% of the respondents who had never read these security messages had a very high level of concern about phishing which could be translated that they are non readers or maybe they did not care that much about these attacks.
Some good number of the respondents take no precaution to protect themselves against the phishing attacks or felt that they already knew how to protect themselves or maybe they prefer other protection sources.
Generally the concern level about online security was higher than expected from the survey result, however that concern doesn’t translate into users reading security warnings while they are carrying out their online activities.
5.2 How to avoid phishing
Here, the respondents were asked whether they have seen or read any of the anti-phishing education materials, whether it was easy to understandand if at all it changed their online behavior thereafter.
75% of those who responded had had access to anti-phishing materials, which means that 25% of those who responded had no memory of having read or seeing an anti-phishing material. While 73% having read the anti-phishing messages from the various websites they had visited, 29% hot the security messages from friends and relatives which enforced the view of the role of social context in regards to anti-phishing campaign.
Most of the people (close to 85%) of the respondents were of the opinion that most of the material out there about phishing were of the right level while another 1% found it to be too challenging, but from the various open ended questions that were asked, there was a view that most of the users still lack an understanding of what really phishing is and how best they can protect themselves.
“From all the sources that I have read the anti-phishing messages, they tend to say the same thing and that makes it boring” male 30-35
In terms of the anti-phishing material impact, 34% of the respondents changed their online behavior with the help of these materials, the most likely to change were women according to the statistics that was gathered, but from a general point of view, most respondents were already satisfied with how they conducted themselves onlie.
“I will put a ‘NO’ to that question because I feel like my online practices have already improved. The anti-phishing materials that I read are all talking about the same things and I feel like there is nothing new that am going to learn, they repeat the same old information” female 26-35
“I am saying ‘NO’ I don’t have to change my behavior, I am security conscious anda careful online user already” female 20-25
Information and suggestions from family and friends were one of the most effective means of making people change their online behavior as compared to other official sources like banks.
“Most people don’t like reading security information from various organizations , but if they hear the same information from a relative or a friend, they will listen” male 30-35
But contrary to that, most of the respondents cited official sources like banks as their most preferred sources of the online security information.
“I get most of my information about phishing and other online scams from official sources like banks and other financial institutions” female 30-35, female 20-25, male 20- 25.
The age group between 18-25 showed a higher level of interest in facebook, twitter and other social media platforms as their preferred channels.
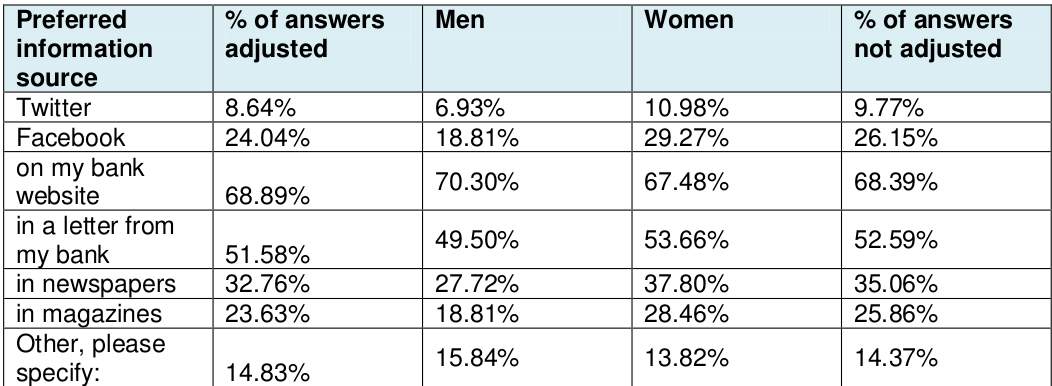
Preferred channel for anti-phishing education
5.3 Protection against phishing attacks
Anti-phishing mechanisms include HTTPs indicators in the address bar, only logging in to trusted websites, not opening unsolicited mails, not clicking on suspicious links , using spam filters, using bookmarks or typing in URLs, antivirus software or using firewalls.
Antivirus software which was the most popular had only a total of 39% mentioning it as their means of online protection. Generally, there were no indicators whether people who use toolbar for example take heed of the warnings, and whether those who checked out for certificates even knew what to look out for.
From the literature review, it was discovered how users deal with emails, where they focus more on the content of the email rather than the security indicators, one of the possible mitigation for this is users deciding to see who the sender of the email is and whether they trust them and was expecting an email from them but this exposes the users to numerous threats from emails that are full of malware.
“I do not always click on emails that I do not recognize their source ” Female 20-25
Another aspect was the intention of the email, how well it was written and whether the user felt that it looked legitimate. However, with the increasing level of sophistication by the phishers by using logos and HTML formatting, it’s very difficult to know whether an email is fake or not.
The next question was asking about the strategies that the user use to decide on whether a site is genuine or not. How well known the site came top with majority of the respondents saying that they only access well known sites but this is not a good strategy as it is always the well known sites that get spoofed by phishers.
Majority of the respondents understand that that they should be looking out for security indicators on the websites however some of them just feel comfortable with being told that the site is secure without any verification however this could be exploited by the attackers by posting security messages on the phishing websites.
Most of the respondents felt that they were putting in enough effort in protecting themselves online but very few really exhibited strong strategy.
6.0 CONCLUSION AND FUTURE WORK
The aim of dissertation was to investigate how phishing attack could be mitigated, so as to enable companies and people to uphold information integrity, confidentiality and availability.
As phishing and other online crimes continue to evolve, interest of phishing stakeholders, expert recommendations and survey result have been put into consideration.
Despite some of the experts having a dissenting opinion on the effectiveness of user education, studies have shown that well designed education material could mitigate between 40 – 50% of the current phishing attacks. These studies have shown that user education is very effective but education alone will not be able to stop these attacks for example, according to (Moore, T., and Clayton, R., 2013) up to 61% of the US online users have had access to anti-phishing education material but still the attacks are on the rise. The major task now is for all the stakeholders to bring on board the remaining 39% who have not had access to these materials. But according to (Ammar Almomani and Samer Atawneh, 2013), even with the best user education material on phishing, users still fall for close to 30% of the phishing attacks even after training hence to make it more effective, it should be complemented with other countermeasures like technical measures.
Operating systems should be secured by implementing secure code and doing vulnerability patching practices, also anti-malware should be built into these operating systems in order to enhance their default security.
Web browser vendors on the other hand should raise the standards of the browsers with anti-phishing warning capabilities so as to be able to detect up to 80% of the malicious content within a short period of time after being published. Internet service providers and other technical vendors should design better technical means for detecting botnets, how to take control of compromised machines and recover them.
From the studies there are 2 areas of study that needs further findings, one is about users and the other one is about the phishing solutions.
Users who responded to the survey appeared to be more confused and couldn’t really differentiate between phishing attacks and other forms of cyber attack, one of the areas that was raised in the literature review but not well addressed was how education materials should be designed, one of those who participated in the interview talked about trust, some of users talked about checking the website certificate but there was little or no evidence that they really had knowledge of what website certificates even meant. A further study should be carried out to discover what types of threat the users are aware of and how they rank them. It would be interesting as well to find out through other means other than user survey the level of honesty the users have about their online behavior.
Some of the researchers claim that personality has a great impact on managing phishing where fast decision makers are more likely to fall for phishing attacks. A better solution would be one that focuses on both the strategies being employed by the key players such as banks and other financial institutions.
To conclude, this dissertation has brought some interesting opinions about the objectives that were set out for example, opinions on user behavior, their attitude and their reaction towards anti-phishing materials, from these discussions, an interest for a further work has been left.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




