Security Challenges in Cloud Computing
Info: 7273 words (29 pages) Dissertation
Published: 24th Jan 2022
Tagged: Cyber SecuritySecurityComputing
Abstract
You’re probably utilizing cloud right now, even if you don’t recognize it. If you are using an app to send an email, editing documents, watching movies, listening to music, playing games, or storing pictures and other files, it’s likely that cloud computing services are making it all possible behind the scenes. Cloud provides storage and access for data over the internet instead of our computer’s hard drive. It can be defined as a ‘pay-as-per-you-use model for enabling suitable, on-demand network access to a shared group of computing resources that can be rapidly provisioned and released with nominal amounts of management effort or service provider interactions. Though there are numerous services offered by cloud, most of them fall under one of the following three categories: Software-as-a-service (SaaS)-offers software applications, on demand and typically on a subscription basis. Platform-as-a-service (PaaS)-supplies on-demand environment for developing, testing, delivering, and managing software applications. Last but, not the least, with Infrastructure-as-a-service (IaaS), you rent servers, virtual machines (VMs), storage, networks, and operating systems.
Great visions are getting built, as the vast possibilities of cloud computing are being realized. From tiny start-ups to Multinational Corporations, government agencies to non-profits, everyone is leveraging the technology for all sorts of reasons. Although the value created by Cloud is very high, security is one of the major factors that hampers its growth. Some of these security challenges include data storage security, data transmission security, application security and security related to third-part resources. The goal of this study report is to provide a comprehensive overview of the security issues arising from the usage of cloud and a few counter measures to those challenges in the world of cloud computing.
Index Terms: cloud, cloud computing, security, challenges, technology.
1. INTRODUCTION
Along with the rapid development of information technology, all the organisations are seeking unique ways of driving their businesses forward, and the responsibility to manage these increasing demands are now placed on computer networks to provide competitive edge and create new opportunities at reduced cost with efficient service. This has accelerated all the business and technological initiatives that promise to provide these services at comparably low infrastructure and operating costs. A fine example to this scenario is the rapid growth of cloud computing.
Cloud Computing, often referred to as simply “the cloud”, is a distributed architecture that centralizes server resources on a scalable platform, enabling ubiquitous access to configurable resources and services. It provides storage and access for data over the internet instead of our computer’s hard drive. Leveraging the Internet, it provides unparalleled and distributed services based on virtualization and service-oriented architecture. Cloud is not another recent technology, but rather it can be described as a delivery model for information services using existing technologies. It does an excellent job in reducing the time spent on IT infrastructure and maintenance. Cloud presents itself as a ubiquitous, dynamically scalable and on-demand model, that can be purchased on a ‘pay-as-you-go’ basis without any prior subscription or under/over provisioning[1].
1.1 AIMS AND OBJECTIVES
This study report aims at identifying the possible security challenges for Cloud computing and some of the possible solutions for these challenges identified through literature reviews.
2. TYPES OF CLOUD
2.1 SERVICE BASED MODELS
There are three delivery models that cloud utilizes to provide different types of services are delivered to the end user. All the services offered by cloud fall under one of these following three categories. They are SaaS, PaaS and IaaS which provide software, application platform, and infrastructure resources as services to the consumer. These models also place a different level of security requirement in the cloud environment. Among all the three services, IaaS is considered as the foundation of all cloud services, with PaaS and SaaS built upon it. With this, several tremendous capabilities are inherited[2].
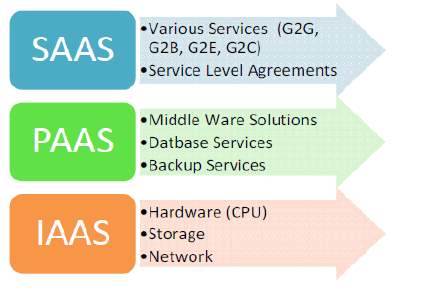
2.1.1 Software as a Service
(SaaS) is an excellent software deployment model where apps are hosted remotely, by the application or service provider, thus providing the capability to the service subscribers to access provider’s applications running on a cloud infrastructure. Here, the service providers control the entire application and the Customer just pays to use it through a web API This model offers the customers with significant benefits, such as enhanced operational efficiency and reduced costs. SaaS has emerged rapidly as the dominant delivery model for meeting the requirements of various IT enterprise services. Though the success of SaaS seems to be incredible, many enterprises are still not sure with this model due to lack of clarity in the way their data is secured. However, to ensure that their customers are fearless about the application security, vendors must address these issues from time to time.
2.1.2 Platform as a Service
(PaaS) is another model that is just above IaaS in the stack and it abstracts everything up to OS, middleware, etc. PaaS offers an integrated development environment (with a set of tools) that a developer can cherish to build their applications without having to worry about what is going on underneath the service, and still has the control over his/her application.
Here the service offered is a complete software development lifecycle management, from planning to design to developing applications to deployment to testing to maintenance. Everything else that runs in the background is abstracted away from the “view” of the developers. Google’s App Engine, a service that allows developers to build programs on Google’s infrastructure, is a perfect example of PaaS. The dark side of PaaS is that, these advantages itself can be helpful for a hacker to leverage the PaaS cloud infrastructure.
2.1.3 Infrastructure as a Service
(IaaS), cuts down the efforts put by developers in deploying applications. Here, a virtual machine is offered as a service and this machine can hold anything that the developer wants it hold. This way, instead of spending huge amounts on own data centers or managing customized hosting services and then hiring operations staff to get it going, one can focus on building a beautiful application, get a virtual server running in minutes and pay only for the resources used. In short, IaaS has enabled numerous organizations to focus on their core competencies without worrying much about the set up and management of the infrastructure. The best part of the service is that it allows the consumers to automatically grow or shrink the number of virtual machines running at any given time to accommodate the changes in their requirements and demands. Although the cloud has a compelling value proposition in terms of cost, the security provided for the applications still do not seem to be in a great state.
2.2 LOCATION BASED MODELS
Apart from the services offered, cloud computing can also be described based on the location of the cloud. Any deployment model would fall under one of the following four categories.
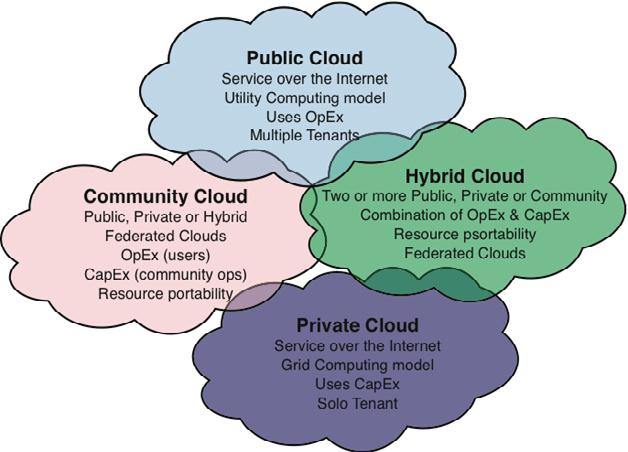
2.2.1 Public Cloud
Public Cloud is defined as a type of hosting, where services are delivered over a network for public use. These clouds are great for organizations that requires the management of host and various applications that users use. Here, customers are not aware of the location of the infrastructure and have zero physical control over it. Whereas, the cost is usually shared among all the users or is in the form of a pay per user policy. Since public clouds use shared resources, they do excel mostly in the performance metric, but are also most vulnerable to numerous attacks.
2.2.2 Private Cloud
Private Cloud refers to the cloud infrastructure that is solely utilized by a single organization and is not shared with others. It can be hosted either internally or externally, thus giving organizations a good amount of control over security and data which is safeguarded by a security system. This model is apt for organizations that have huge demand for management, security, and uptime requirements. Although the security and control level are highest while using a private network, the cost reduction can still be minimal, if the organization requires to invest in an on-premise cloud infrastructure.
2.2.3 Hybrid cloud
Hybrid Cloud of course, refers to the use of both private and public clouds, depending on their purpose. This model is tremendous when scalability, flexibility and security are taken into consideration. Resources here, are managed and can be provided either internally or through the help of external providers. An example of hybrid cloud can be seen in action, when an organization uses public cloud to interact with their customers, but also keeping their data secured through a private cloud. Though the model uses both public and private clouds, they can remain separate entities, thus adding to the beauty of the model.
2.2.4 Community Cloud
Community Cloud refers to an infrastructure that is mutually shared between multiple organizations that belong to a single community cloud at banks, government in a country, or trading firms are some of the best examples for community cloud model implementation. Here, the factors like privacy, performance, and security are usually shared by the community members. The model is managed and hosted either internally or through the help of a third-party provider, thus making it apt for organizations that work on joint ventures that need centralized cloud computing ability for managing, building, and executing their projects[3].
3. ARCHITECTURE OF CLOUD COMPUTING
Cloud computing system is composed of two sides. These two sides are known as the Front End and the Back End, and they are connected to each other usually through the internet. Here, the front end represents the user side and back end acts as the “cloud” section of the system. The client’s computer, along with the application required to access the cloud computing system forms the front end. This end is an interface that is visible to all the computer users or clients through their web-enabled client devices. But there is no rule, that all cloud computing systems would use the same user interface. Whereas the back end of the system is where, various computers, servers and data storage systems that create the “cloud” of computing services reside. Also, there exists a central server that takes care of system administration, traffic monitoring and client demands to ensure everything is running in an efficient and smooth manner. Apart from this, it adheres to a set of rules called protocol and makes use of a Cloud middleware.
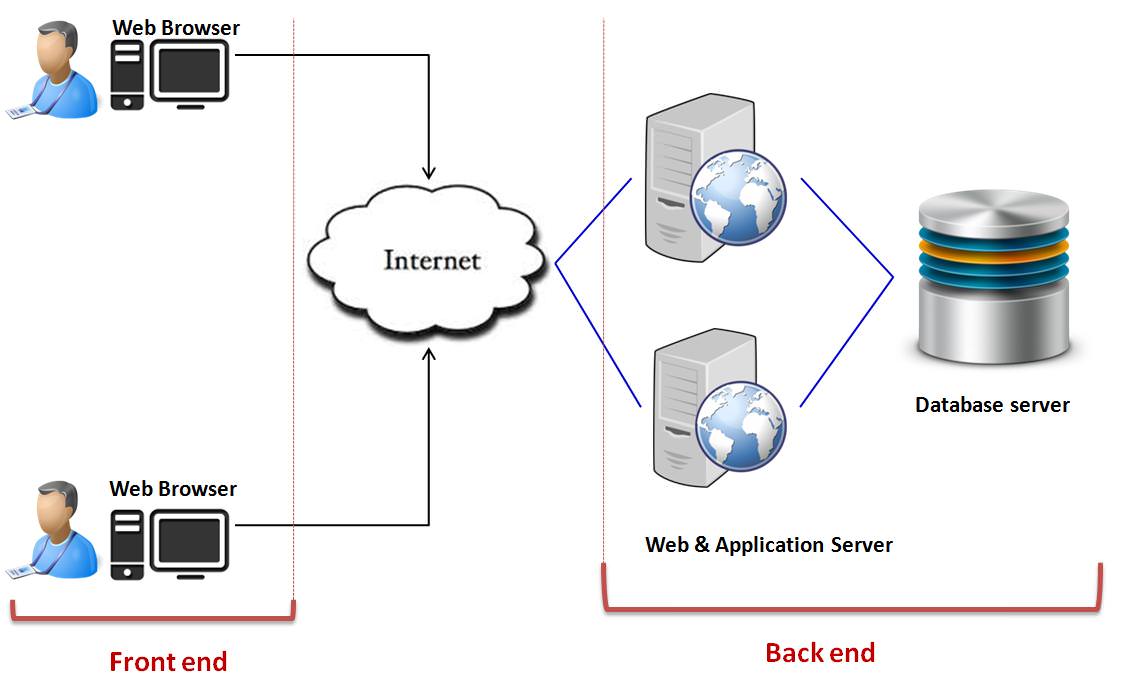
The middleware software of cloud, also known as the cloud OS, does a tremendous job in managing and controlling numerous services. Amazon EC2 – Elastic Cloud Compute forms the best example for Clouds middleware. The operating system on a bare metal server, also known as a hypervisor, utilizes various well-defined protocols, thus allowing multiple guest virtual machines to run concurrently. It the hypervisor that guides the communication between its containers and the connected world. Hypervisors use the server virtualization methodology that bypasses some of the physical limitations which stand-alone servers can face. Through the concept of virtualization, a physical server can be tricked into thinking, that it is also a part of a multiple server environment. With the increase in the numbers of services hosted by a cloud computing provider, the demands of increasing traffic and compute loads must be anticipated and accommodated. To maintain and protect the client’s data efficiently, a cloud architecture must have greater redundancy for locally hosted systems. Through the copies generated by this redundancy, the central server can jump in and access backup images to quickly retrieve and restore the required data.
When a simplified vision of cloud computing architecture, is considered, then the following steps take place in the background: First, A service request is sent by the client, which then is taken as an input to find the appropriate resources. Once all the appropriate computing resources are found then the client request gets executed and the results for the service are sent back to the clients.
3.1 KEY CHARACTERISTICS OF CLOUD
3.1.1 Broad network access
Capabilities of cloud are available all over the network and are accessed through standard mechanisms by numerous heterogeneous thin and thick client platforms such as mobile phones, laptops, and PDAs. Cloud computing provides the ability to massively scale bandwidth and storage space.
3.1.2 On demand services
Email, applications, network, or server service are some of the services that are provided without requiring human interaction with each service provider. Amazon (AWS), Microsoft, Google, IBM and Salesforce.com, and NASDAQ are some of the major Cloud services, providing on-demand services.
3.1.3 Resource pooling
Computing resources are pooled together using multiple-tenant model, to serve multiple consumers with various physical and virtual resources dynamically assigned and reassigned with respect to consumer demands. These resources include processing, storage, memory, virtual machines, and network bandwidth. The pooling together of the resource builds economies of scale (Gartner).
3.1.4 Measured service
Often, the usage of cloud computing resources can be measured, controlled, and reported, thus providing transparency for both, provider, and consumer who has utilized the service. There also exists a metering capability that enables to control and optimize the utilization of resources. This characteristic is visible in utility companies that sell power to subscribers, and telephone companies that sell voice and data services, IT services, data center hosting, etc. At the end of the day, you pay for what you have utilized. The more you use, the higher you pay.
3.1.5 Rapid elasticity
Cloud services are elastically provisioned to provide quick scale out and are rapidly released to provide quick scale in. Using this, users can dynamically increase or decrease their capabilities as required. Scaling up and down of a tenant’s resources provides a good opportunity for other tenants in utilizing the previously assigned resources of tenant’s. To the consumer, these provisioning capabilities often seem to be unlimited, and can be bought in any amounts, at any time.
3.1.6 Multi Tenacity
Cloud is based on a model, where resources are shared at the network level, host level and the application level. Multi-tenancy, as the term implies, refers to dealing with multiple tenants of the cloud living and sharing with other tenants the provider’s infrastructures, including computational resources, storage, services, and applications. Using multitenancy, clouds provide simultaneous and secure hosting of services for various customers utilizing a single set of cloud infrastructure resources. This unique feature of resource sharing in clouds, allows cloud providers to control the utilization of resources more efficiently by partitioning a virtualized infrastructure among multiple customers.
4. SECURITY CHALLENGES OF CLOUD COMPUTING
Tremendous amount of organizations, both small and large are embracing public and private cloud computing at a rapid pace. According to a research conducted, it was shown that almost one-third of all the organizations have been utilizing the public and private cloud infrastructures for more than three years now, and more than half of all the organizations have their production workload all on the cloud. Even though, the concept of cloud computing is far above than just a physical or virtual server, which transforms into a different cybersecurity model, but gradually, all these differences lead towards a wide range of security issues.
Environments in cloud are multidomain environments in which each domain may utilize different requirements in terms of security, privacy, trust and employ various mechanisms and methodologies that are potential enough. These domains will be able to represent services that are individually enabled or any other components belonging to the infrastructure. Service-oriented architectures form a relevant technology that facilitates these multidomain formations through service composition and orchestration. Although cloud helps organizations accomplish more by breaking the physical bonds between users and the infrastructure, there exists several security threats that must be overcome to gain benefits from this rapid growing computing paradigm. Enterprises are no longer sitting and wondering if they should take up the risk of migrating their applications and data to the cloud. Instead they are doing it, but security still pertains to be a serious concern. The first step in minimizing risk in the cloud is to identify the top security threats.
All the security concerns associated with cloud computing fall into any of the two broad categories: challenges faced by cloud providers and challenges faced by their customers. However, the responsibility to stay secure is shared. It is the responsibility of the provider to ensure that their infrastructure is secure and that their clients’ data is protected in all the possible means, while the user is in charge to fortify their application and use efficient authentication measures. Security and privacy form two of the major concerns in cloud computing. In the world of cloud computing, the user accesses computing power that exceeds the one contained within their physical world, through a virtual environment. To gain access to this virtual environment the user has to transfer data through the cloud, thus giving birth to numerous security breaches.
4.1. DATA LEAKS
A data leak also referred to as data breach is the release of confidential and private data to an untrusted/unauthenticated environment. Some of the challenges in cloud are also prevalent in traditional corporate networks, but since the data stored on cloud servers is huge, providers usually get to be the victims of these attacks. Here the damage severity is directly proportional to the sensitivity of the data that is exposed. It gets worst when financial data gets leaked, but breaches that involve information regarding health, trade secrets, and intellectual property can be even more devastating. Because, when a data breach takes place, it is not only the customers who suffer, companies also may incur huge fines, or they may even face severe criminal charges.
Apart from the huge costs that rack up due to breach investigations, brand damage and loss of business can also have their own indirect impacts on the organization for years. In a public cloud, where you are sharing resources with other organizations, government could get a “reasonable cause” to seize your assets if another company has violated the law. This way you may put your data at the risk of seizure, just because you are sharing the environment in the cloud. Though cloud providers deploy security controls which protect their environments, it is the responsibility of the organizations to protect their own data in the cloud. Thus, the following question pertains: “Is the cloud inherently less safe, with all the sensitive data being stored online?”
4.2. POOR AUTHENTICATION
There are numerous attacks that result from broken authentication standards. Most of the organizations have a hard time with their identity management system that tries to allocate permissions according to the user’s work role. Sometimes, they even forget to release user access when the job function changes or when the user leaves the organization. Usually developers tend to embed credentials and cryptographic keys in source code and leave them in repositories such as GitHub which is a publicly faced environment. But it is very important for the keys to be appropriately protected, along with a well-secured public key infrastructure. These keys also need to be rotated periodically, thus making it harder for the attackers to use them without authorization. Organizations should understand and be aware of all the security measures the providers use to protect the identity data. Multifactor authentication techniques like one-time passwords and phone-based authentication should be encouraged as these make it difficult for hackers to log in with any stolen credentials.
4.3 LOSS OF DATA
As the cloud got matured over the years, example of cloud providers losing data have become extremely rare. But the attacks to permanently delete cloud data and harm businesses are still prevalent, thus making cloud data centers vulnerable to natural disasters as any other facility. A malicious attack, a natural disaster, or a wipe by the service provider can erase the data on the cloud. For a business that do not have any kind of recovery plan, loosing data can be a devastating event. A best example to this is when Google lost has data when lightning struck its power grid for about four times. To secure your data is to carefully review your provider’s back up procedures as they are highly dependent on physical storage locations, physical disasters, and physical access. The task of protecting the data from data losses is not solely imposed on the cloud service provider only. If a customer encrypts the data and sends it to the cloud, then the burden of protecting the key is on the customer, because once the key is lost, all the data associated with it is also lost.
Backing up data every day and off-site storage remains an important aspect with cloud environments. There are certain compliance policies that specify the amount of time, for which companies should retain their audit records and other related documents. Losing such data may result in some serious regulatory consequences. A few protection rules treat data destruction and corruption of personal data as data leaks, thus requiring suitable notifications. Thus, it is always important to know the rules to stay away from trouble.
4.4 SYSTEM VULNERABILITIES
We have already learnt that; cloud security is a shared burden between the client and the provider. This relationship between client and provider demands the client to take certain preventative actions in ensuring that the data always stays protected. The essential point is that clients and providers, both have shared responsibilities, and omitting one of the two may result in vulnerabilities. System vulnerabilities, exploitable bugs in programs, are not any new terms, but today, they’ve grown into a bigger problem with the rapid growth of multitenancy in cloud computing. Multiple companies share memory, databases, and various other resources with one another, creating a larger scope for new attack surfaces.
Fortunately, some of the basic practices can be used to mitigate these vulnerabilities. Some of these best practices are regular vulnerability scanning, quick patch management, and rapid follow-up on reported system threats. According to the Cloud Security Alliance, the costs incurred in mitigating these system vulnerabilities “are small when compared to other IT expenditures.” Yes, the expense of getting IT processes in place to discover and develop repair mechanisms is relatively small compared to a huge potential damage. Thus, it is considered as a best practice for all the regulated industries to build a patch as quickly as possible.
4.5 DENIAL OF SERVICE ATTACKS
We have heard of numerous cyberattacks, that establish a long-term impact and hack into sensitive information. But denial of service assaults is an exception from these. Though, they do not attempt to disturb the security perimeter, they make your services unavailable to legitimate users, by overloading your servers. However, in few scenarios, Denial of Service is also utilized for other malicious activities, and to put down security measures such as application firewalls.
Though these attacks have been existing for years, they’ve gained prominence again and thanks to cloud computing this time. These attacks affect availability, which means, systems slowly get to a crawl state or simply time out. They consume huge amounts of processing power, making it impossible to respond to any other valid and authenticated requests. Apart from the DDoS attacks, organizations should be aware of various asymmetric and application-level DoS attacks, that target web servers and databases. This attack is like being caught in a rush-hour traffic gridlock, where there is nothing that you can do, but just wait. The providers can efficiently handle DoS attacks rather than their customers. This is because, the strategy here is to mitigate the attack before it occurs, and administrators will have access to those resources whenever they require them.
4.6 CLOUD ABUSES
With cloud based services, it is possible for both small and multinational companies to host vast amounts of data easily. Bu this unprecedented storage capacity provided by cloud has also allowed both hackers and unauthorized users to easily host and spread malware, and illegal software. These services can be misused to support nefarious activities, such as breaking an encryption key to launch an attack. Some other despicable attacks including DDoS, sending spam, and phishing emails are also made easy for hackers.
These attacks may also include sharing of pirated software, videos, music, or books, and depending on the damage incurred, huge fines may be imposed. Service providers need to learn about the various types of abuses and offer tools for customers accordingly, to control the health of their cloud. Although customers do not form the direct victims here, they may have to suffer from service availability issues and data losses. Therefore, customers should always ensure that their providers offer a security mechanism that repots abuses.
4.7 API INSECURITY
The opportunity to customize cloud experience according to their needs is provided to users, by the help of Application programming interfaces. Although API’s seem to be of great use, they can be a huge threat to cloud security because of their very own customizable nature. This is because, along with the customization feature, they also provide the customers with authentication and access provision. Companies like Google, Facebook, YouTube, and various others provide programmers numerous tools that help in building their programs in such a way, that they can even integrate their applications with other highly demanded software’s.
Although this benefits programmers and businesses, it also gives birth to several security risks that lie in the communication that takes place between multiple applications. they also leave exploitable security risks. Weak APIs push organizations to be the victims for numerous security issues related to confidentiality, integrity, availability, and accountability.
4.8 HIJACKING OF ACCOUNTS
Along with the existence of Phishing, fraud, and software exploitation, implementation of cloud services has opened a new dimension to the set of threats, because with account hijacking attackers can participate in several illegal activities including manipulating transactions, and modifying sensitive data. This even leads to use of cloud application by the attackers for launching their devastating attacks.
Thank to hijacking; attackers can now use your credentials to access your sensitive data stored on the cloud. These methods also include scripting bugs and reusing passwords to steal sensitive data. This way, they can even misuse and manipulate the original data for their own benefits. Another best example of hijacking includes, Man in The Cloud Attack – the latest trending threat that involves the hijacking of user tokens which cloud platforms provide to verify authenticated users. To minimize these, companies must ensure that the data credentials are not shared between users and services, and should utilize multifactor authentication mechanisms. Thus, our end goal should always deal with the protection of account credentials from being hijacked.
4.9 INSIDER ATTACKS
Sometimes an attack may come from within our own organization. The threat coming from inside has many shades: it may be a current or former employee, a system administrator, or even a business partner in the worst case. The agenda behind these threats range from stealing data for profits to brutal revenges. Usually with cloud, the insider may either destroy the whole infrastructure & services or even steal, manipulate, and misuse data for profits. Systems that are solely dependent on the cloud service providers for security, have higher chances of getting attacked by these insiders. Though these kinds of attacks seem to take place very rarely, they still exist in few scenarios.
Also in few cases, it is easy to misconstrue a genuine entity as a “malicious” insider. For example, when a network administrator accidentally copies a sensitive database to a server that is publicly accessible, this is just an accident that can be misconstrued as an attack. Thus, it is recommended, that every organization implements logging, monitoring, and auditing services in the most efficient manner possible.
4.10 POOR DILIGENCE
Until now, most of the issues that we’ve learnt about are all technical in nature. However, this threat arises when an organization is not clear about any of its policies, resources, and methodologies for the cloud. Organizations that leverage the cloud without a complete understanding of its environment and the risks associated with it, may encounter numerous technical, financial, and legal risks.
In some cases, organizations are not aware of the provider’s liability in case of any data loss activity. This is because, they fail to scrutinize the contract efficiently. Also, poor diligence results in numerous risks, when organizations migrate to cloud without a proper understanding of all the services that it provides. Thus, it is highly recommended for any company to do an intensive research on all the benefits, before simply subscribing to the cloud.
4.11 PACKET SNIFFING
Packet sniffing is one of the various network attacks that allows an attacker to access your files and other information. The following attack gets activated when the filter to stop host machines from viewing the data traffic is turned off. This way, the attacker will be able to view the data across the network. Implementation of Sniffing can be done locally, or on the server or a router that is connected to a network. This can also include a software that listens to any network device for interesting packets. When software goes through a packet with required criteria, it automatically logs it into a log file. Usually interesting packets are the ones that include words like “login” or “password” or “credentials”. Most of the cloud service providers still do not provide any kind of strong protection against one customer from attempting to view another’s data. Thus, encrypting sensitive traffic should be used as a standard practice to avoid these attacks as much as possible.
4.12 MALWARE INJECTION
Malware injection refers to a type of attack, where a piece of code is injected into the cloud, and this embedded code tricks the cloud and starts to act as Software as a Service. If this event takes place successfully, the cloud system automatically redirects even the legit user requests to the injected malware. Once after it gains proper access to the cloud, it starts to steal data and misuse it. This way, the attackers are gain control over the data without any valid authentication. Due to rapid growth of these attacks, Malware Injects have become one of the major security concerns in the field of cloud computing systems.
4.13 PORT SCANNING
A malicious technique that identifies open, closed, and filtered ports on a system in cloud environment is referred to as Port Scanning. In this, intruders seize sensitive data with the help of any open ports available. These ports include services that are running on a system, IP and MAC addresses, gateway, and fire-wall rules. When the Subscriber allows the traffic to flow from any source to a specific port, then that port gets vulnerable to a port scan. This is because, a port is a place where information goes into and out of the computer, and so the port scanning will then be able to identify the open doors to that computer. Also, there is no way to stop these attacks while you are using the Internet, because communicating with an internet server opens a port your computer. In cloud computing, the attacker attacks the services by discovering open ports on which these services are currently running.
5. EFFECTIVE COUNTER MEASURES AND PREVENTION MECHANISMS
Like the way in which we secure a conventional IT environment, both cloud provider and the client need to implement an approach that addresses security in a comprehensive manner, incorporating access management, perimeter security and threat management, encryption, (DDoS) mitigation, privacy, and compliance management. Especially in a shared environment, elements related to identity and access management should be given a lot of importance, because in these environments data is stored and accessed by multiple clients. Numerous standards, procedures, and practices are required to be implemented for mitigating the probability of security threats in the field of cloud computing. These standards and measures ensure privacy and security of confidential information in a cloud environment. Reducing the above studied threats result in a secure environment for both, users, as well as the providers of cloud. A basic philosophy of security includes having different layers of defense, a concept also known as defense in depth. This mechanism utilizes the concept of overlapping systems which is designed to provide consistent security even if one of the systems fail. An example to this a security system working in a team with the intrusion detection system (IDS). The mechanism, Defense in depth has high success rate in providing security, because, in this scenario, neither there is a single point of failure nor a single-entry vector where the attack can take place.
Success in cloud computing depends upon many factors. Cloud providers should be a position to provide an effective solution to their customers that can sustain any number of malicious threats using methods such as multifactor authentication, activity monitoring, regular testing etc. To satisfy on security requirements and address the security issues as analyzed above, we can summarize some of the best practices in mitigating the cloud.
5.1 BREACH RESPONSES
There are some best practices to avoid data breaches in cloud. Breach response plan is one of the best solutions as it helps in triggering a quick notification to data breaches and thus reduce the amount of harm. It contains steps involving notification of the concerned agency who could contain the breach. Also conducting periodic checks will allow the security team to have a control on the network. Breaches can be avoided by classifying data and keeping track of its movement within the organizational network. Always remember to cut down on all the files and folders before revealing a storage equipment. Consistently review and restrict downloads that may serve as an allegiance to the attackers. In the end, always place encryption as your last defense technique for cybercriminals. When all other attempts fail to protect your data, encryption is every organization’s last hope to the hacker’s game of breaches.
5.2 SPECIALIZED ON PREMISE EQUIPEMNT STRATEGIES
Given that DDoS attacks are becoming very common, this is one of the best protection mechanisms against those. Here, instead of relying on existing firewalls, enterprises purchase and deploy dedicated mitigation appliances that sit on the data centers in front of the routers and are particularly designed to detect any malicious traffic. We can get away from DoS even by utilizing Internet Service Providers that implement mitigation facilities. One of the simplest defense mechanism against DDoS is to ensure that there is an excess of bandwidth, but it can be expensive at times. Scanning the systems regularly for vulnerabilities, setting up of intrusion detection systems, maintaining backup of internet connection, configuring firewalls in a secure fashion, and regularly updating the old software patches are some of the best practices to prevent and fightback DoS attacks in the field of cloud computing.
5.3 BUILD A LAYERED DEFENCE MECHANISM
Always ensure to place restrictions on the IP addresses that can access the application. This way, threats like account hijacking can be reduced. There are various tools that specify allowable IP ranges, thus allowing users to access the application only through those networks and VPN’s. It is also recommended for companies, to set up a protocol that prevents sharing account credentials between other employees and services. Another mandatory aspect is to implement a strong multifactor authentication mechanism that requires users to enter dynamic one-time passwords, delivered to them via SMS, token generators, biometrics, or any other secure schemes. Though all these techniques help in mitigating risks, encryption is best technique to prevent hijacking attacks. Therefore, always make sure to encrypt data before sending it to the cloud; this protects the data even if a breach occurs. For ultimate protection plan, ensure to place the encrypted key nowhere close to the encrypted data. Taking advantage of the cloud begins with managing the security threats associated with it. This leads to the process of pursuing a multi-layered security approach that protects your data all the time.
5.4 DUE DILIGENCE & PRIVATE SOLUTIONS
Organizations should possess a clear set of goals in mind and get a thorough understanding of all benefits and risks involved with Cloud Computing, before directly jumping to it. Security concerns are common, whenever the outside world has our data. For example, a hypervisor refers to a virtual machine manager that allows multiple systems to share a single host. Now, your service provider can provide your organization with some virtual systems on the same hypervisor that is shared with the virtual systems of other customers as well. In other words, the hardware resources utilized by your systems are also utilized by company’s systems. This process of sharing resources may be a good option for less critical systems, but this is not an apt model for systems that are referred to as highly critical. Thus, consumers need to understand the risks involved with sharing technologies and must perform activities related to due diligence covering risk assessment and risk management, application and data security, network configuration and security. Conducting due diligence helps organizations in understanding the various risks of adopting cloud technology and provides organizations with a second chance to obtain a better understanding of their capacity and consumption needs.
5.5 SAVE THE DATA
We have in the above section, how compromising on sensitive data caused due to deletion, modification, and storage of data on unreliable medium, can lead to a dreadful threat. Fortunately, there are some emerging efforts in the industry to prevent these attacks and save our data from permanent losses. One of these techniques is to enforce a strong API security. This way, the attackers are less likely to steal our data. Strong authentications and secure validation processes are to be implemented to avoid any cloud abuses. Securing the data with SSL encryption techniques, regularly checking the data integrity, and exploring the collection plans and back up plans of the provider are some of the additional processes that must be implemented to prevent data from getting lost.
5.6 SECURE NETWORKING
It is important to prevent damages caused by various attacks like SQL Injections, malware injections, Man in the cloud attacks, packet sniffing, and XSS attacks. For example, various filtering techniques can be utilized to detect and avoid the SQL injection attacks. Techniques like Active Content Filtering, Content Based Data Leakage Prevention Technology, can be used to prevent XSS attacks. Apart from these, there is a malicious sniffing detection platform that is based on address resolution protocol and roundtrip time, and this platform can detect a sniffing system running on a network. In most of the cases, the security measures implemented in a private network also apply to the private cloud, but in case of a public cloud implementation, the network topology should be changed to implement the security features.
6. CONCLUSIONS
Security concerns in cloud computing is an active area of research and experimentation. Lots of researches are going on, to address various security threats like network security, data protection, insider attacks and isolation of resources. While cloud computing offers several benefits, people have different perceptions about cloud computing. Some argue that cloud to be an unsafe place. Finally, one of the major drawbacks of the Cloud is that, here the customers must trust their providers with sensitive, and potentially damaging information from a legal standpoint. In this paper, we have provided a telling overview of security threats in the field of cloud computing. Also, we have provided the reader with some effective countermeasures, and prevention mechanisms to overcome these attacks and get the most out of a secure cloud.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Computing"
Computing is a term that describes the use of computers to process information. Key aspects of Computing are hardware, software, and processing through algorithms.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




