Web Architecture Components to Further Web Functionality
Info: 7742 words (31 pages) Dissertation
Published: 10th Dec 2019
Tagged: Computer ScienceInternet
The Technical Stuff – How the internet works
Contents
P1 – Outline the web architecture and components which enable internet and web functionality.
How do we connect to the internet?
P2 – Explain the client-side and server-side factors that influence the performance of a website.
Client-side/server-side performance issues
P3 – Explain the security risks and protection mechanisms involved in website performance.
M1 – Explaining the role of web architecture in website communications
D1 – Explain the role of TCP/IP protocol and how it links to application layer protocols
Internet layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model
Transport layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model
Application layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model
Task 1
P1 – Outline the web architecture and components which enable internet and web functionality.
Introduction
The internet is used by many people around the world which help to perform many everyday tasks. It’s used to distribute and retrieve information across to many people digital as it’s more efficient as doing this process physically in real life. The internet could be used for revision, reading news articles, listening to music and watching videos. There are many tasks that can be achieved when using the internet. Most internet users don’t know how internet works briefly in depth, but have sufficient knowledge on the surface knowing how to use the internet. Most internet users don’t need to know how the internet works except if they’re working for companies that maintain the functionality and access to the internet.
This report will cover how verbally and visually how the internet works, describing the algorithms and components that make the internet work. How web servers have conflicts and the different issues that arise and how they can be fixed. Then an in-depth description that explains the role of web architecture in website communications.
What is the internet?
The internet is the different varied sized networks that are connected by using cables, phone lines, satellites and wireless connections to send and receive data. It provides a sufficient variety of information to retrieve and facilities of communication which we use to complete to tasks more efficiently. The internet has existed since 1969 when two scientists at UCLA connected two computers together and the workstations had the ability to communicate with each other. In 1983, ARPANET adapted the TCP/IP protocol to the internet to which manages the transmission of data, this would invent the modern version of the internet. In 1993, the Tim-Berners Lee invented the World Wide Web (WWW) which has increased the internet’s popularity. This is the aspect of the internet that we use the most through a web browser.
How do we connect to the internet?
A connection to the internet can be established by subscribing to an Internet Service Provider (ISP) and you’ll receive a router or a modem that gives a computer system an IP Address to allow the computer system to connect the internet. There are three different types of connections to the internet. The Asymmetric Digital Subscriber Line uses a frequency spectrum which receives internet through a phone line. A dial-up service which uses a modem to receive internet from telephone line connected to a bigger computer network. A cable connection which uses a router to receive internet from a coaxial cable, a router is used to receive access from a cable underground to get an internet connection. The router can be connected to a computer system by using an Ethernet cable or using the provided login details to allow wireless electronic devices to receive internet access. In exceptional cases.
What is a DNS?
The Domain Name System/Server (DNS) is used translate alphabetical characters which make up to the domain name, which is primarily located in the middle of a Uniform Resource Locator. To convert it into the Internet Protocol Address to allow the user to establish a connection to access the website. Domain Name System/Server are primarily stored at an Internet Service Provider, as if a user didn’t have one they would always have to manually add new domains with their Internet Protocol Address.
The process of the Domain Name System/Server. The user would send a request to the ISP to access www.google.com. Then the Internet Service Provider should have the Internet Protocol Address of the domain, then an established connection can be made to access the website. The domain name of Uniform Resource Locator is linked to an Internet Protocol Address (216.58.206.68). A Domain Name System/Server can be updated if nobody has requested to visit the website before, an Internet Service Provider (ISP) will go to Nominet, which every website has a domain registered to their web server to find the Internet Protocol address (IP) of the domain. Then the computer system stores the Internet Protocol address (IP) related to the domain in the DNS client of the computer system.


DNS Server/System
Internet Service Provider
www.google.com
Nominet
What is an IP Address?
An Internal Protocol address (IP) is a group of four integers separated by full stops (e.g. 128.56.78.91.). The minimum to maximum interval of the integer the Internet Protocol address (IP) is 0-225. This applies each of the four integers in the Internet Protocol Address, the result is that there are limited Internet Protocol addresses (IP) left. This produces the unique identifier of an individual computer system to allow to establish a connection with the internet. Internet Protocol Addresses (IP) are given to you by your Internet Service Provider (ISP) specifically in the router, the hardware given to you by the Internet Service Provider to connect to the internet.
There are two different types of Internet Protocol addresses, external and internal. An external Internet Protocol address (IP) is the public variation of an Internet Protocol Address that every other user outside your local network can perceive while connected onto the internet. This uniquely identifies a network with one or more electronic devices that have an established internet connection. An internal Internet Protocol address in basic terms is an Internet Protocol address (IP) in an Internet Protocol Address (IP). This is used to identify the electronic devices connected to one router individually. An internal Protocol Address could be e.g. 192.168.0.1 of and a computer system and for a smart phone it could be 192.168.0.2. There are connected to the same router and in the same network. 192.168.0.1 and 192.168.0.2 are common formations because there are linked to the external Internet Protocol addresses (IP) which are unique identifiers, making the internal Internet Protocol addresses unique from an aspect. Without Internal Internet Protocol addresses, only one electronic device could connected to a router.
Internal IP addresses
192.168.1.1
External IP Address
128.56.78.91






Internet
Workstation
Router
192.168.1.2
Workstation
Internet Service Provider
Workstation
192.168.1.3
.
TCP/IP
The Transmission Control Protocol/Internet Protocol (TCP/IP) is basically a collection of different protocols. This branch of protocols is basically used to allow communication between different computers on the internet. The Transmission Mission Protocol (TCP) deals with the established connection between two workstations as the Internet Protocol (IP) deals with the distribution of packets.
Web Server
A web server is combination of physical hardware and software that processes website requests via Hyper Text Transfer Protocol (HTTP) though the World Wide Web, the most popular section of the Internet used. Web servers are used to store website’s as they have a high storage capacity to store many different websites simultaneously. An news distribution service need a vast amount of web servers to accommodate new web pages with new products to sell as well as old web pages which are archived to be viewed again by the client. A web server’s hardware would need to have very powerful components to handle operations such as one’s I have listed above. The software should automatically have the ability to handle operations such as handling web requests. This prevents the web server administrator from doing this manually.
P2 – Explain the client-side and server-side factors that influence the performance of a website.
Client-side/server-side performance issues
Client-side issues
Client issues when connecting to the server can range from a slow connection, old/slow equipment or old software.
A slow connection from the client-side can increase the request-response cycle between and client and server. When requesting a web-page there are usually no problems, except that when loading it will take longer as packets as lost and the router has to keep sending more packets until the request is complete. However, once the request is complete and the web-page is loaded for the user. It may load a 400 error that relates to “NOT FOUND-CLIENT FAILURE” As some packets may be lost as they’ve haven’t destination in time.
Old/slow equipment of a computer system has an impact on the performance when in the process of the request/response cycle between a client and a server. The components of the computer may be obsolete and incompatible with the processes used today. This is because the equipment that is old isn’t supported by the latest software related to the internet. As a result it takes a long time load the web-page or doesn’t load at all giving the user an error. If the equipment is slow then it will take longer to load a website because the equipment is limited to resources that perform a task, which is considered to be slow.
Old software can have an impact on the performance when in the process of a request/response cycle. This occurrence is usually way as most software in the present has the ability to automatically update itself, display efficiency to the user as well as creating efficiency for the user. Old software doesn’t have the bug fixes and new features that allow for an efficient connection between a server and client. If software is outdated it will either load errors or outdated versions of websites, which have no new features.
Server-side issues
A server may have insufficient resources to complete request/response cycle efficiently. As a singular machine may be running multiple websites at once. One of the reasons that sit affects performance is because the server prolongs the duration as they’re trying to locate which website needs to loaded as well as the specific page (primarily the index) that has been requested. This makes the process of the cycle slower causing more complex errors that the average user doesn’t understand and know how to fix.
A server may have network issues that prolongs the process of the request/response cycle due to t its slow performance because of this factor stated above. In the network of web servers, the hardware may be failing such as the Ethernet cables. The connections between the servers are a necessity for a big website to load a very-specific web page according to the user’s expectations. It would take longer for data to be retrieved and sent to user, because of hardware problems. As well as problems server crashes can occur if it doesn’t have the capacity to allocate the packets being sent and received.
Task 2
P3 – Explain the security risks and protection mechanisms involved in website performance.
Introduction
Web servers can be compromised by different threats can have an impact on the server’s performance as well as creating setbacks on the hardware on the server. These threats are Distributed Denial of Service (DDOS), Cross-side scripting (XSS), Website Poisoning (Drive by download), SQL Injection, Hacking, Data Theft and Brute/Force Dictionary Attack. These are the most common threats to web-servers on the internet.
Distributed Denial of Service
Distributed Denial of Service is an attack on a web-server to make it unavailable by overwhelming it with useless traffic from different workstations. It could be simple as sending multiple requests that the web-server doesn’t have the capacity to handle it and can crash and be down for a certain duration. It’s more difficult to prevent this attack as the traffic is coming from multiple workstations, which could be located in different locations around the world. There are different types of Distributed Denial of Service attacks (DDOS): Bandwidth, Application and Traffic Attacks. Data Theft is an effect of Distributed Denial of Service attacks are they’re becoming more advanced.
Cross-side scripting
Cross-Side Scripting (XSS) attacks are injections of malicious scripts from the client’s side that are can be viewed on the website by other users. This can be prevented implementing a mechanism that preventing using form inserting client-side scripts, this could be as simple as blocking the permissions to use to the client-side web editor.
Website Poisoning
Website poisoning or Drive-by-download is where malicious code is injected into the website and forces the client to download malicious files that infect their computer system. This is usually displayed as a popup that could state “Your PC has a virus, press this button to download an anti-virus.” Ironically, you would be downloading a virus to your computer. Presently, you can download an anti-virus which has internet security such as Norton to protect your from this blacklisted algorithm. The anti-virus will block access to the website once a threat like this has been detected or block the threat, so you can use the site smoothly.
SQL Injection
An SQL Injection is where malicious code is injected into poorly-scripted database that is purposefully used for exploitation of the information in the database. This is done by exploiting a vulnerability of an application to trick the database to running a backend command or query to retrieve vital information such as bank details, which is an example of data theft. A firewall can prevent an SQL Injection attack, as it can detect an external Internal Protocol Address and block the connection to the database for instance.
Hacking
Hacking is the blacklisted practices that are against the Data Protection Act of 1998 to mainly gaining access to unauthorised data. In a scenario of a web server, hacking could range from injecting a Remote Access Trojan (RAT) for backdoor access for to gain administrator permissions to corrupting files vital for the network to function. Hacking can be prevented by updating the server software such as Apache, mainly security updates that prevent hackers from finding new algorithms through bugs and errors for their own personal gain.
Brute Force/Dictionary Attack
Brute force is method that generates possible candidates of characters linked together that are possible matches to the encrypted statement (e.g password) in attempt to being retrieved, for purposes to unlock a system for beneficial purposes (e.g accessing somebody’s account). This can be prevented on when a hacker is attempting to gain internal permissions by logging in to an administrator’s account; the website should have an algorithm that gives the client 3 attempts to access the account. If they failed the account will be locked and can only be unlocked with another client with greater permissions.
Careless users
Careless users that have authority in accordance with a web-server should be encouraged to produce a strong password attached their account. Especially a password that appears to be an encrypted piece of data. This strong password should consist of upper case and lower case characters. As well as numbers and symbols. For authorities users there should be a length check validation method, which should be at the minimum of 16 and beyond. This is to protect data that is unauthorised for public view. A character check validation method would work effectively, as in the password there should be at least one of each data type consisted in the password (integer, upper and lower characters, symbols).
M1 – Explaining the role of web architecture in website communications
The internet has a web architecture that is different fundamental processes that are linked together that allow us to access the internet as a whole and the World Wide Web (WWW) through an internet browser on the surface of the internet. There are two different methods that we can use to retrieve our results on the Internet. You can either use the search engine to enter what you want to retrieve, the general results that are linked to the keywords that you’ve entered into the search engine, through the Internet Browser. Or you can enter a Uniform Resource Locator (URL) of a website into the search bar of most internet browsers to specifically retrieve a particular website and the web page too. These methods will be explained below including the mechanisms and algorithms that have embedded purposes that contribute to the purpose of the functionality of the internet. The internet has affected the physical attributes of business as most people find it more convenient to access the internet and use it for general purposes. Instead of visiting business’s in person. To use their services that they provide.
When the web browser application is launched by the user on their operating system. The user can access the internet because they’re connected to broadband, which provides them with an Internet Service Provider (ISP) which allows access to the internet in some circumstances through and Asymmetric Digital Subscriber Line (ADSL). Most users would have a subscription plan that makes it compulsory to pay a fee monthly to use the broadband services .The preferred search engine is displayed on the user’s monitor, it uses the protocol Hyper Text Transfer Protocol Secure (HTTPS) for a secure connection and to load the fundamental website code Hyper Text Mark-up Language (HTML) of the search engine. They have the option to either use the search bar or the Uniform Resource Locator bar (URL). Most users prefer to use the search bar to enter keywords that are specific to what websites their looking for. The user decides to use the search engine to enter the keywords ‘Spotify’.
If the user wanted to access the site directly they have to enter the Uniform Resource Locator. The Uniform Resource Locator (URL) is broken down into 4 parts. The protocol (https), host (.www), domain name (Spotify) and the extension (.com). This type of protocol is used to retrieve the data that make ups the website being access. The Host is the World Wide Web (WWW) that all website addresses use. The World Wide Web (WWW) is the surface of the internet we access on a daily-basis. It’s the information that contains web resources and web documents. Every website that can be accessed via the internet browser uses the host of the World Wide Web (WWW). The Domain name is the combination of characters and numbers that is another identifier that relates the Internet Protocol (IP) Address of a website. Without this we would have to access a website through its Internet Protocol (IP) Address directly. Finally, the extension is to identify where the domain was registered. The .com extension is a general extension that then automatically identifies where the domain name was registered, by changing it .co.uk. When the Uniform Resource Locator (URL) is entered into the search bar. However, some websites use direct extensions that relate to where the domain was registered. Primarily, most websites made in a specific country want to register their domain in that country. The entity that allows this to happen is called a Domain Name Registrar. A Domain Name Registrar is a company that registers domain names, they can make reservations for taken domain names to prevent plagiarism and for other reasons specified. Domain Name Registrar can also register extensions too such as .com, co.uk and other extensions specified to certain countries such as .cz for the Czech Republic. This commercial entity can also register official domain extensions such as .gov for websites owned by the government.
https://www.spotify.com/uk/
1.Protocol 3.Domain Name
2. Host 4.Extension
- 2. 3. 4.
The Transmission Control Protocol/Internet Protocol (TCP/IP) is the suite of all the protocols related to the internet. This Transmission Control Protocol (TCP) allows data transmission through packets that are distributed to the server as form of a request. The Internet Protocol (IP) is a protocol that has fundamental communications in the Internet protocol for using data to relay across different network boundaries. The Internet Protocol (IP) address is the unique identifier to establish a connection to the internet, a Personal Area Network (PAN) of devices would all share the same Public Internet Protocol (IP) Address which mostly IPV4. IPV4 addresses are the current Internet Protocol (IP) addresses we use today. They comprise of 4 integers separated by dots, ranging from the intervals randomly from 0-255. A user would use have Internet Protocol (IP) address that is assigned to their Internet Service Provider (ISP), for security purposes to monitor internet activity and the permissions to distinguished from other users, so different electronic devices and systems can connect.
Packets are small units of data that are decalibrated when in the process of being sent through a packet-switched network that is sent from the source to the destination, then they’re calibrated form the file of data. Packets could simple as a request and response to a server. A favoured example would be downloading a file onto computer system. As packets are sent as request to the web-server to retrieve the external file from the web server by downloading it. The file that is in the process of downloading is decalibrated of packets. Then the fastest route is determined by the server to transfer the packets to another network (primarily a Personal Area Network). Then once the packets are received by the other network the process of calibration is the file being downloaded. Once all the packets have calibrated, technically the file would be downloaded.
To receive a response of the results, which in terms for the user the website or webpage is launched for them to display .The HTTP/HTTPS protocol loads the fundamental HTML basis code of the webpage that has results related to the keywords ‘Spotify’. The Domain Name System/Server (DNS) is used to decode the domain of the Uniform Resource Locator (URL) of that webpage to retrieve the Internet Protocol (IP) address by decoding to the domain to find the Internet Protocol Address (IP). Then the user can access the webpage overall as Internet Service Provider.
Then the user would enter an input to click on the primary result which loads the Spotify Website. The user wants to download the Spotify desktop application onto their hard drive of their computer system to use for the entertainment purposes. When the user goes through all the processes that the ‘Spotify’ Website requires they have the rights to download the file. The protocol that is used to is File Transfer Protocol (FTP). This protocol is the standardised network protocol used to transfer files from either to servers to hosts. The units of data are in the form in packets are sent directly to the destination or to the user retrieving the file. The more sophisticated and secure version of File Transfer Protocol (FTP) is the Secure File Transfer Protocol (SFTP).
The Secure File Transfer Protocol (SFTP) was introduced to the 1990s. However, instead of using text-based data that the File Transfer Protocol (FTP) uses, packet-based data is used for operations that the protocol offers. The SSH protocol is inherently secure and used in the Secure File Transfer Protocol (SFTP). The Secure File Transfer Protocol uses the main connection for file transfers not opening a separate for file transfer to take place. On the website when downloading “Spotify” This can be done on the website instead of separate web page being to download the executable file. Secure File Transfer Protocol has more additional information attached to the website. Such as the permissions, date, time, size of the file. This is can accommodate for most files presently used to today, as all have these properties such as executable file with Spotify. File Transfer Protocol (FTP) doesn’t have these features. Overall, this protocol is faster, has more features and accommodates for variants of digital data that needs to be transfer. There is a chance that the Secure File Transfer Protocol (SFTP) was used in the operations of download the executable “Spotify” file.
Once this user download and installs Spotify, they may want to message their friend to make recommendations to the application. They may use electronic mail (e-mail). They may access an email distribution service Google Mail. Google Mail and other services use a protocol called Simple Mail Transfer Protocol (SMTP). Simple Mail Transfer Protocol (SMTP) is a protocol attributed to the TCP/IP protocol, which allows recipients on electronic mail (e-mail) distributing services to send and receive electronic mail (e-mail) over the internet. The protocols Post Office Protocol (POP3) and Internet Message Access Protocol (IMAP) are additionally used and contribute to delivering high-quality electronic mail (e-mail) services. Post Office Protocol (POP3) is used to allow electronic mail (e-mail) client downloads such as word document attachment to an e-mail. A user could attach a self-made notepad manual that is related to “Spotify” then send it along with a message to their friend. Internet Message Access Protocol (IMAP). It’s a protocol that saves distributed electronic mail from a recipient into an inbox of an electronic mail (e-mail) distributing service such as Google Mail. It requires more computer resources for functionality of this protocol to be sufficient. It mainly uses the port 143. To be used with a firewall. When a user sends a message to his friend who’s the recipient that message can be saved into their friend’s inbox, for them to review later. If this protocol wasn’t implemented. The electronic mail could be and received by the server as form of a useless request, so the electronic mail isn’t saved.
D1 – Explain the role of TCP/IP protocol and how it links to application layer protocols
Introduction
The Transmission Control Protocol/Internet Protocol (TCP/IP) is the suite of all the protocols related to the internet. The Transmission Control/Internet Protocol is mainly a combination of the Transmission Control Protocol and the Internet Protocol (TCP/IP). This Transmission Control Protocol (TCP) allows data transmission through packets that are distributed to the server as form of a request. However, the Internet Protocol (IP) is a protocol that has fundamental communications in the Internet protocol suite for relaying data across different boundaries of networks. The Internet Protocol (IP) controls the destination and how the packets are going to reach that destination. Transmission Control Protocol (TCP) makes sure that there is an established connection, to allow networks to interconnect and make a connection. It makes the internet what it is. Transmission Control Protocol (TCP) has the function to also make sure that packets can be resent as well as checking individual packets making sure that they don’t contain any errors. Previously, it didn’t provide connectivity but the Transmission Control Protocol (TCP) allow this function to work. The Internet Protocol (IP) give’s an electronic device an Internet Protocol (IP) Address that is either ipv4 or ipv6. The Internet Protocol (IP) address is the unique identifier to establish a connection to the internet, a Personal Area Network (PAN) of devices would all share the same Public Internet Protocol (IP) Address which mostly IPV4. This is because IPV4 addresses are becoming obsoleted and outdated. IPV4 addresses are the current Internet Protocol (IP) addresses we use today. They comprise of 4 integers separated by dots, ranging from the intervals randomly from 0-255.However, they’re running out and current technology still uses them. In the future Internet Service Providers will transfer to using IPv6 addresses primarily. These mechanisms contribute to the functionality of the Internet Protocol (IP).
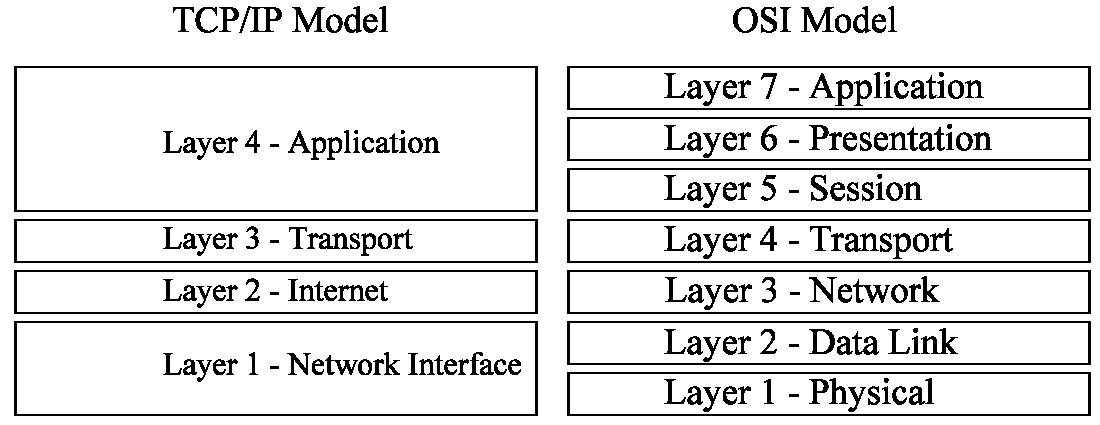
Transmission Control Protocol/Internet Protocol (TCP/IP) has a model which is related to the Open Systems Interconnection model (OSI). The Open Systems Interconnection model is a diagram that was designed by the Organisation for Standardization (OSI). The diagram describes the 7 different layers that create internet. As the first layer identifies the simple and physical structures. Then the 7th layer describes the applications that are used to access the internet. The Transmission Control Protocol/Internet Protocol (TCP/IP) model is a generalised diagram that groups the 7 layers of the Open Systems Interconnection models into different groups which are equivalent to 4 layers. That relate to the similar layers that have different embedded purposes that explain the general purpose of each of those 4 layers. These models are very similar are may be compared in manner that allows them to be relate to each other.

Network Interface/Network Access of the Transmission Control Protocol/Internet Protocol (TCP/IP) model – It consists of the 2 lower layers of the Open Systems Interconnection model (OSI). The Physical Layer and then the Data Link layer (layer 1 and 2 of OSI). The physical layer defines the characteristics of the hardware on the network. This it allow different hardware to be distinguished for different tasks and procedures that need to take out for a network to function correctly. The layer above which is the Data Link Layer, handles the transfer of data between the media of network. This allow users on a network to distribute data between each other, for example this could be simple as sending images between one people.
In general, this is lowest level layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model. This layer is responsible for attaching Internet Protocol addresses (IP) to Media Access Control addresses (MAC). To network individual computer systems to the same network. From physical hardware responsible and for encapsulation of Internet Protocol packets for data transmission, so they’re grouped together to prevent data from being missing. Then it uses protocols related to Transmission Control Protocol/Internet Protocol for the distribution of physical data. The Network Interface layer allows you to connect to different interfaces of network such as Wi-Fi or Ethernet.
Internet layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model– The internet layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model comprises of only layer 3 from the Open Systems Interconnection model (OSI), which the network layer. It’s responsible for managing data addressing and the delivery of data between networks. It’s responsible for forwarding packets by routing them to different routers. Routing is a process towards the selection of where traffic needs to be directed between pathways of routers from different networks, despite them being a Local Area Network (LAN), Wide Area Network (WAN) or a Personal Area Network (PAN).
In general, the internet layer has a packet construct uses the Internet Protocol (IP) and the addressing mechanism to deliver packets from a source to a destination. The Internet Protocol address (IP), it mainly the IPV4 of the Internet Protocol address (IP) to forward packets to different devices. They use other protocols too, IPV6 which is the more advanced version of an Internet Protocol address (IP) just to address different systems that share the same IPV4 address. This layer uses the Internet Control Message Protocol (ICMP), this is to send message errors to a user operating on a network. To allow users to see errors when sending and receiving requests to access different networks, servers or devices. Address Resolution Protocol (ARP) which is used to map IPV4 Internet Protocol addresses to Media Access Control addresses (MAC). This is to individually identify each electronic device physically, this is for individual identification of hardware. These are the protocols that are all used in the Internet layer.

Transport layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model – The transport layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) ensures that sufficient data transmission has been initiated. The transport layer receives data from the application layer and turns them into packets. However, if they’re any errors with packets they are sent in the form they’re in. Then the data sent be will corrupted but computer system will warn you if this takes place.
The protocols associated with this layer are the Transmission Control Protocol (TCP), which ensure that there is reliable communication of data being delivered correctly. However, the User Datagram Protocol isn’t as dynamic as the Transmission Control Protocol (TCP), it can complete operations that this layer requires to complete. It doesn’t carry them to a high standard. Only small devices use User Datagram Protocol (UDP) to transmit. The User Datagram Protocol doesn’t have the ability to establish or verify connections between distributing and receiving hosts. The User Datagram Protocol can sort out packets too but not as well as the Transmission Control Protocol (TCP). These protocols that are included in the Open Systems Interconnection model (OSI) are linked together to contribute to the similar purpose of functionality that the Transport Layer of the Transmission Control Protocol/Internet Protocol model (TCP/IP).
Application layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model – The application layer is responsible for providing networking services to applications that related to the use of internet or used to access the internet. The services that are there work with the transport layer to send and receive data. Different protocols exist to contribute to that .For example electronic mail (e-mail) distributing services such as Google Mail use the protocols File Transfer Protocol (FTP) this protocol is used to transfer files from either to servers to hosts, Simple Mail Transfer Protocol (SMTP) which allows recipients on electronic mail (e-mail) distributing services to send and receive electronic mail (e-mail) over the internet and Post Office Protocol (POP3) which allows an electronic mail (e-mail) distributing service to save electronic mail into inboxes. The Domain Name Server/System (DNS) works with this layer too .These protocols contribute to the functionality of this service works and how it offers service to users. As electronic mail (e-mail) takes advantage of the request and response to work in favour as the data being equivalent to messages that humans could interpret, that could acquire different features.
However, there are 3 layers from the Open System Interconnection model (OSI). That relate to the Transmission Control Protocol (TCP). The session layer which manages and terminates connections between systems, this is required to enable a network to be efficient. The presentation layer makes sure data can be interpreted by the user despite being in form of packets prior. On a website you may see English Characters but they’re representation of the assigned binary numbers. The application layer contains a variety of communication services and programs that every can use. An internet browser would relate to the OSI application very well as it’s a good example.
Harvard References
- Techtargetcom. 2017. SearchExchange. [Online]. [5 November 2017]. Available from: http://searchexchange.techtarget.com/definition/SMTP
- Southrivertechcom. 2017. Southrivertechcom. [Online]. [5 November 2017]. Available from: https://southrivertech.com/whats-difference-ftp-sftp-ftps/
- Techtargetcom. 2017. SearchExchange. [Online]. [5 November 2017]. Available from: http://searchexchange.techtarget.com/definition/SMTP
- Martin knafve. 2017. Hmailservercom. [Online]. [5 November 2017]. Available from: https://www.hmailserver.com/documentation/v5.6/?page=whatis_pop3imapsmtpc
- Oraclecom. 2017. Oraclecom. [Online]. [5 November 2017]. Available from: https://docs.oracle.com/cd/E23823_01/html/816-4554/ipov-6.html
- Sqaorguk. 2017. Sqaorguk. [Online]. [5 November 2017]. Available from: https://www.sqa.org.uk/e-learning/HardOSEss04CD/page_06.htm
- Getcybersafegcca. 2017. Getcybersafegcca. [Online]. [5 November 2017]. Available from: https://www.getcybersafe.gc.ca/cnt/rsks/cmmn-thrts-en.aspx
- Wikipediaorg. 2017. Wikipediaorg. [Online]. [5 November 2017]. Available from: https://en.wikipedia.org/wiki/Rootkit
- W3org. 2017. W3org. [Online]. [5 November 2017]. Available from: http://www.w3.org/standards/webarch/
- Techopediacom. 2017. Techopediacom. [Online]. [5 November 2017]. Available from: https://www.techopedia.com/definition/30409/website-architecture
- Godaddycom. 2017. Godaddycom. [Online]. [5 November 2017]. Available from: https://uk.godaddy.com/help/what-is-dns-665 https://technet.microsoft.com/en-
- Homebtcom. 2017. BTcom. [Online]. [5 November 2017]. Available from: http://home.bt.com/tech-gadgets/internet/websites/what-is-internet-11364190069786
- Britannicacom. 2017. Encyclopedia Britannica. [Online]. [5 November 2017]. Available from: https://www.britannica.com/technology/Internet
- Webopediacom. 2017. Webopediacom. [Online]. [5 November 2017]. Available from: https://www.webopedia.com/DidYouKnow/Internet/ipv6_ipv4_difference.html
- Tavis, J. 2017. Webmasterviewcom. [Online]. [5 November 2017]. Available from: http://www.webmasterview.com/2011/03/server-security-threats/
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Internet"
The Internet is a worldwide network that connects computers from around the world. Anybody with an Internet connection can interact and communicate with others from across the globe.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please: