Verification of the Certificate Using the BLS Signature Scheme
Info: 9901 words (40 pages) Dissertation
Published: 16th Dec 2019
Tagged: Computer Science
1 INTRODUCTION
1.1 Introduction to MANETs
MANET known as Mobile Ad-Hoc Network is a self-organised, dynamic and infrastructure less network. MANET consists of mobile nodes that roam freely, every node has its own range of signal communication, other nodes within the range can interact and exchange messages. New nodes join and some other nodes may leave or some nodes fail to connect as they move out of the MANET network range.
The nodes in MANET are energy constrained, i.e., nodes are battery powered devices. There are many security threats to MANETS such as Denial of Service, Eavesdropping, Interception and Routing Attacks.
From the very beginning, the use of MANETS has been appealing to both military and civilian applications. MANETS are also characterized by being bandwidth and energy constrained.
As an example of MANET, let us consider multiplayer computer games. With the increasing number of mobile devices, multiplayer games are getting very popular. In such games, the set of players is changing during the games, the players can join or leave the game at any time, there are different teams, etc. In some of them, the decision about the player admission or game strategy is taken only when a certain number of members agree. Some transmitted information has to be protected (encrypted) against other players or teams.
MANETS are a kind of Wireless ad-hoc networks (WANET) that usually has a routable networking environment on top of a Link Layer ad hoc network. MANETS consist of a peer-to-peer, self-forming, self-healing network.
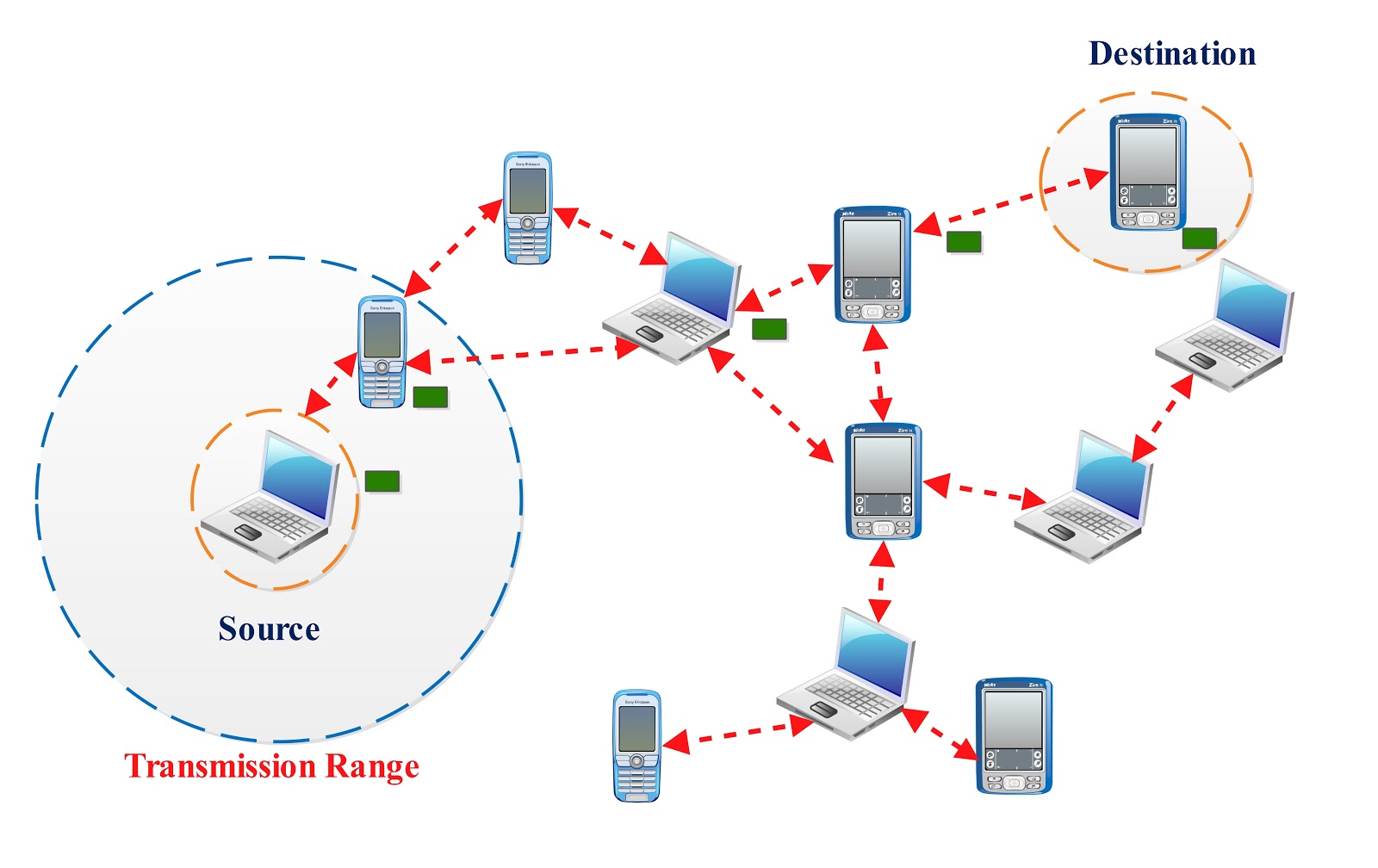
Figure 1.1.a : Mobile ad-hoc network
1.2 Types of MANETs
- Vehicular ad-hoc networks (VANETs) are used for communication between vehicles and road side equipment. Intelligent vehicular ad-hoc networks(InVANETs) are a kind of artificial intelligence that helps vehicles to behave in intelligent manners during vehicle-to-vehicle collisions and accidents.
- Smart phone ad-hoc networks (SPANs) leverage the existing hardware (primarily Bluetooth and Wifi) in commercially available smart phones to create peer-to-peer networks without relying on cellular carrier networks, wireless access points, or traditional network infrastructure. SPANs support multi-hop relays and there is no notion of a group leader so peers can join and leave at will without destroying the network.
- Internet-based mobile ad-hoc networks (iMANETs) are ad hoc networks that link mobile nodes and fixed Internet-gateway nodes.
- Military or Tactical MANETs are used by military units with emphasis on security, range and integration with existing systems.
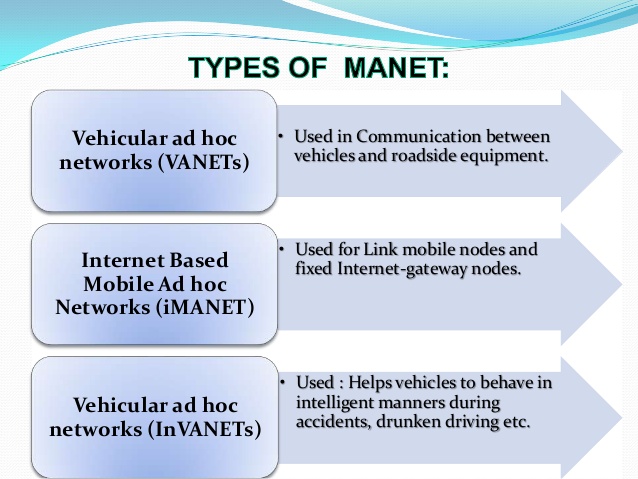
Figure 1.2.a : Types of Mobile ad-hoc networks
1.3 Applications of MANET
With the increase of portable devices as well as progress in wireless communication, ad-hoc networking is gaining importance with the increasing number of widespread applications in the commercial, Military and private sectors. Mobile Ad-Hoc networks allow users to access and exchange information regardless of their geographic position or proximity to infrastructure. In contrast to infrastructure networks, all nodes in MANETs are mobile and their connections are dynamic. Unlike other mobile networks, MANETs do not require a fixed infrastructure. This offers advantageous decentralized character to network. Decentralization makes the networks more flexible and more robust.
- Military Sector: Military equipment now routinely contains some sort of computer equipment. Ad-Hoc networking would allow the military to take advantage of commonplace technology to maintain an information network between soldiers, vehicles and military information headquarters. The basic techniques of ad hoc network came from this field.
- Data Networks: A commercial application for MANETs includes ubiquitous computing. By allowing computers to forward data for others, data networks may be extended far beyond the usual reach of installed infrastructure. Networks may be made more widely available and easier to use.
- Low Level: Appropriate low level application might be in home networks where devices can communicate directly to exchange information. Similarly, in other civilian environments like taxi cab, sports stadium, boat and small aircraft, mobile ad hoc communications will have many applications.
- Sensor Networks: This technology is a network composed of a very large number of small sensors. These can be used to detect any number of properties of an area. Examples include temperature, pressure, toxins, pollutions etc. The capabilities of each sensor are very limited, and each must rely on others in order to forward the data to a central computer. Individual sensors are limited in their computing ability and are prone to failure and loss. Mobile ad-hoc sensor networks could be the key to future homeland security.
1.4 Challenges in MANET
A. Autonomous: No centralized administration entity is available to manage the operation of the different mobile nodes.
B. Dynamic Topology: Nodes are mobile and can be connected dynamically in an arbitrary manner. Links of the network vary timely and are based on the proximity of one node to another node.
C. Device Discovery: Identifying relevant newly moved in nodes and informing about their existence need dynamic update to facilitate automatic optimal route selection.
D. Bandwidth Optimization: Wireless links have significantly lower capacity than the wired links. Routing protocols in wireless networks always use the bandwidth in an optimal manner by keeping the overhead as low as possible. The limited transmission range also imposes a constraint on routing protocols in maintaining the topological information. Especially in MANETS due to frequent changes in topology, maintaining the topological information at all nodes involves more control overhead which, results in turn in more bandwidth wastage.
E. Limited Resources: Mobile nodes rely on battery power, which is a scarce resource. Also, storage capacity and power are severely limited.
F. Scalability: Scalability can be broadly defined as whether the network is able to provide an acceptable level of service even in the presence of a large number of nodes.
G. Limited Physical Security: Mobility implies higher security risks such as peer-to-peer network architecture or s shared wireless medium accessible to both legitimate network users and malicious attackers. Eavesdropping, spoofing, denial of service attacks should be considered.
H. Infrastructure-less and self-operated: Self-healing feature demands MANET should realign itself to blanket any node moving out of its range.
I. Poor Transmission Quality: This is an inherent problem of wireless communication caused by several error sources that result in degradation of the received signal.
J. Ad Hoc Addressing: Challenges in standard addressing scheme to be implemented.
K. Network Configuration: The whole MANET infrastructure is dynamic and is the reason for dynamic connection and disconnection of the variable links.
L. Topology Maintenance: Updating information of dynamic links among nodes in MANETS is a major challenge.
1.5 Attacks on MANET
Securing wireless ad-hoc networks is a highly challenging issue. Understanding possible form of attacks is always the first step towards developing a good security solution. Security of communication in MANET is important for secure transmission of information. Absence of any central co-ordination mechanism and shared wireless medium makes MANET more vulnerable to digital or cyber- attacks than wired network there a number of attacks that affect MANET.
An honest node can also be compromised if it is under the control of the attacker. As the network comprises of layers of protocols, the attacks are specific to a layer and the security should also be implemented in the corresponding layer. These attacks can be classified as:
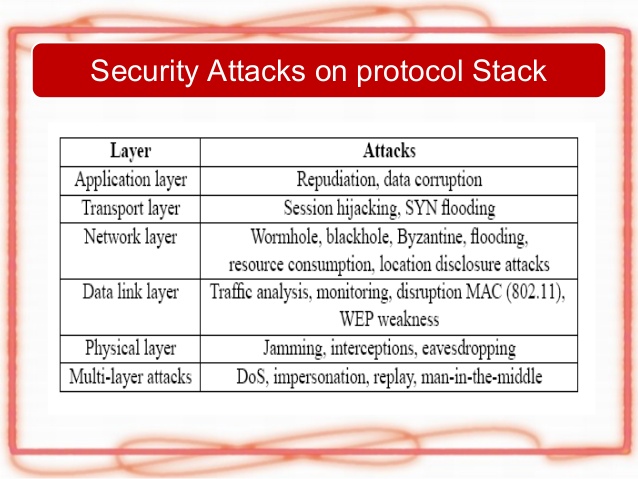
Figure 1.5.a : MANET Layer specific attacks
Attacks on Mobile Ad-Hoc networks (MANETs) can be classified into following two categories:
1) Passive Attack
2) Active Attack
1.5.1 Passive Attack:
In this type of attack, the intruder only performs some kind of monitoring on certain connections to get information about the traffic without injecting any fake information. This type of attack serves the attacker to gain information and makes the footprint of the invaded network in order to apply the attack successfully. The types of passive attack are eavesdropping, traffic analysis and snooping.
- Eavesdropping: This is a passive attack. The node simply observes the confidential information. This information can later be used by the malicious node. The secret information like location, public key, private key, password etc. can be fetched by the eavesdropper.
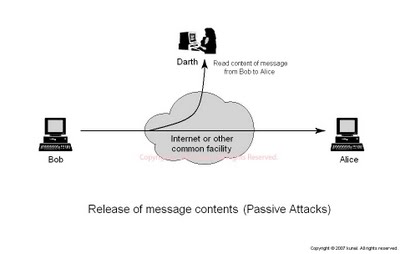
Figure 1.5.1.a: Eavesdropping
- Traffic Analysis: In MANETs the data packets as well as the traffic pattern, both are important for adversaries. For example, confidential information about network topology can be derived by analysing traffic patterns. Traffic analysis can also be conducted as active attack by destroying nodes, which simulates self-organization in the network, and valuable data about the topology can be gathered.
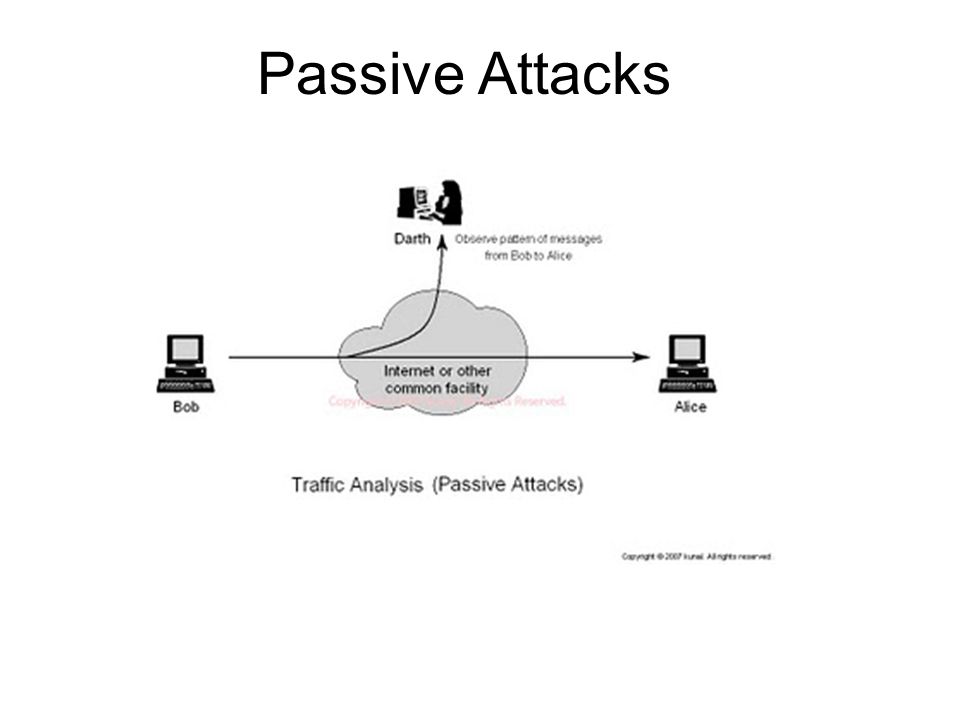
Figure 1.5.1.b Traffic Analysis
- Snooping: Snooping is unauthorized access to another person’s data. It is similar to Eavesdropping but is not necessarily limited to gaining access to data during its transmission. Snooping can include casual observance of an e-mail that appears on another’s computer screen or watching someone else typing. More sophisticated snooping uses software programs to remotely monitor activity on a computer or network device. Malicious hackers (crackers) frequently use snooping techniques to monitor key strokes, capture passwords and login information and to intercept e-mail and other private communications and data transmissions. Corporations sometimes snoop on employees legitimately to monitor their use of business computers and track internet usage. Governments may snoop on individuals to collect information and prevent crime and terrorism. Although snooping has a negative aspect in general but in computer technology snooping can refer to any program or utility that performs a monitoring function.
1.5.2 Active Attack:
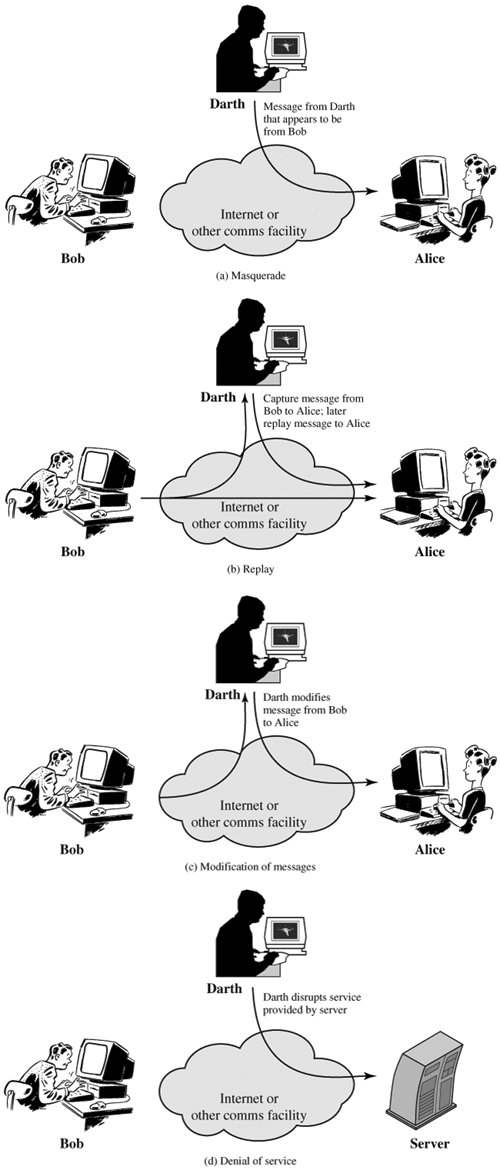
In this type of attack, the intruder performs an effective violation on either the network resources or the data transmitted. This is done by International Journal on New Computer Architectures and their Applications causing routing disruption, network resources depletion, and node breaking. In the following are the types of active attacks over MANET and how the attacker’s threat can be performed:
- Flooding Attack: In flooding attack, attacker exhausts the network resources, such as bandwidth and to consume a node’s resources, such as computational and battery power or to disrupt the routing operation to cause severe degradation in network performance. For example, in AODV protocol, a malicious node can send a large number of RREQs in a short period to a destination node that does not exist in the network. Because no one will reply to the RREQs, these RREQs will flood the whole network. As a result, all of the node battery power, as well as network bandwidth will be consumed and could lead to denial-of-service.
- Black hole Attack: Route discovery process in AODV is vulnerable to black hole attack. The mechanism, that is, any intermediate node may respond to RREQ message if it has a fresh enough route, devised to reduce routing delay, is used by the malicious node to compromise the system. In this attack, when a malicious node listens to a route request packet in the network, it responds with the claim of having the shortest and the freshest route to the destination node even if no such route exists. As a result, the malicious node easily misroute network traffic to it and then drop the packets transitory to it.
- Wormhole Attack: In a wormhole attack, an attacker receives packets at one point in the network, “tunnels” them into another point in the network, and then replays them into the network from that point. Routing can be disrupted when routing control message are tunnelled. This tunnel between two colluding attacks is known as wormhole. In DSR, AODV, this attack could prevent discovery of any routes and may create a wormhole even for packet not addressed to itself because of broadcasting. Wormholes are hard to detect.
- Gray hole attack: This attack is also known as routing misbehaviour attack which leads to dropping of messages. Gray hole attack has two phases. In the first phase the node advertise itself as having a valid route to destination while in second phase, nodes drops intercepted packets with a certain probability.
- Link spoofing attack: In a link spoofing attack, a malicious node advertises fake links with non-neighbours to disrupt routing operations. For example, in the OLSR protocol, an attacker can advertise a fake link with a target’s two hop neighbours. This causes the target node to select the malicious node to be its MPR. As an MPR node, a malicious node can then manipulate data or routing traffic. For example, modifying or dropping the routing traffic or performing other types of DoS attacks.
- Malicious code attacks: Malicious code attacks include viruses, worms, spywares and trojan horses, can attack both operating system and user application. Repudiation attacks: Repudiation refers to a denial of participation in all or part of the communication. Many of encryption mechanisms and firewalls used at different layer are not sufficient for packet security. Application layer firewalls may take into account in order to provide security to packets against many attacks. For example, spyware detection software has been developed in order to monitor mission critical services.
- Session Hijacking: Attacker in session hijacking takes the advantage to exploits the unprotected session after its initial setup. In this attack, the attacker spoofs the victim’s nodes IP address, finds the correct sequence number i.e., expected by the target and then launches various DoS attacks. In session hijacking, the malicious nodes tries to collect secure data (passwords, secret keys, logos, names etc.) and other information from nodes. Session hijacking attacks are also known as address attack which make effect on OLSR protocol. The TCP-ACK storm problem may occur when malicious node launches a TCP session hijacking attack.
- SYN Flooding Attack: The SYN Flooding attacks are the type of Denial of Service (DoS) attacks, in which the attacker creates a large number of half opened TCP connections with victim node. These half opened connections are never complete the handshake to fully open the connection.
- Denial of service attack: Denial of service attacks are aimed at complete disruption of routing information and therefore the whole operation of ad-hoc network.
- Jamming: Jamming is a special class of DoS attacks which are initiated by malicious node after determining the frequency of communication. In this type of attack, the jammer transmits signals along with security threats. Jamming attacks also prevent the reception of legitimate packets.
- Traffic monitoring and analysis: Traffic monitoring and analysis can be deployed to identify the communication parties and functionalities, which could provide information to launch further attacks. Since these attacks are not specific to the MANET, other wireless networks, such as the cellular network, satellite network and WLAN also suffer from these potential vulnerabilities.
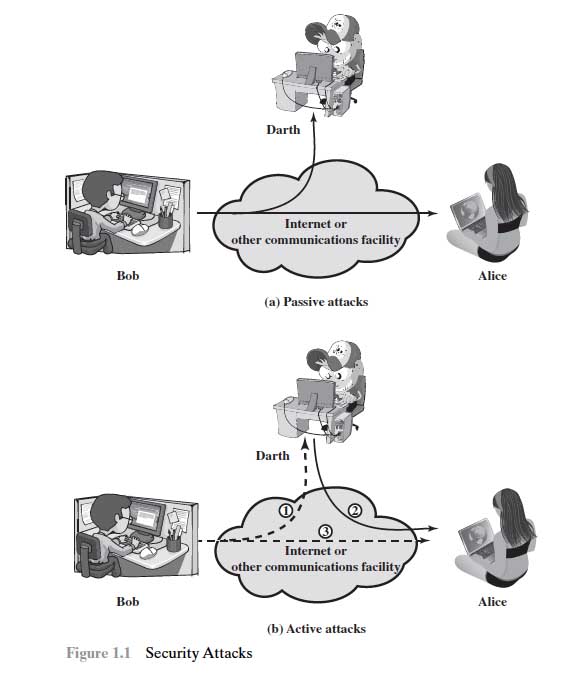
Figure 1.5.2.a : Active and Passive Attacks
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Computer Science"
Computer science is the study of computer systems, computing technologies, data, data structures and algorithms. Computer science provides essential skills and knowledge for a wide range of computing and computer-related professions.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




