Role of Cloud Computing in Cyber Resilience
Info: 9219 words (37 pages) Dissertation
Published: 9th Dec 2019
Tagged: Computer ScienceCyber Security
Table of Contents
Research Problem and Discussion
Introduction
Cloud computing is being acclaimed as the penultimate answer for the issues of indeterminate traffic spikes, figuring over-burdens, and conceivably costly interests in equipment for information handling and reinforcements. Although the general idea of cloud computing return to the 1950’s, the services of cloud computing primarily became available in the early 2000’s specifically focused at large organizations. Since then, the cloud computing services are spread to small and medium size businesses along with consumers. Cloud computing can conceivably change the IT business, making both programming and infrastructure significantly more alluring as administrations, by reshaping the manner in which equipment is planned and bought. Cloud computing is a computing model to enhance the present utilization and conveyance show for IT administrations in view of the Internet, by accommodating progressively scalable and frequently virtualized assets over the Internet.
The term cloud computing is not new and can be thought of as an expansion of how we utilize the Internet. Infact, the term cloud is likewise used to represent the Internet. The principle thought of cloud computing is to outsource the administration and conveyance of software and hardware assets to outsider organizations (cloud providers), which have some expertise in that specific administration and can give much better nature of administration at bring down expenses in an advantageous manner. For instance, now an organization can buy the access of hardware assets as indicated by its real requests and without forthright expenses. On the off chance that the demand diminishes, the organization can diminish the measure of remote equipment assets for which it is paying. On the off chance that interest expands, the organization can without much of a stretch modify the assets to the interest. An organization data can be stored in a different country where governing laws might be different from expectations of the company.
In today’s world, the global enterprises collect and analyze huge volumes of data like never before. They are utilizing this data for their intense growth, innovation and collaboration. The technological innovations such as cloud computing, the internet of everything (IoE), mobile computing are speeding the pace of change and they’re quickly getting to be a need for any organization that looks to stay aggressive in the interconnected worldwide business biological system. Indeed, even as organizations put resources into and advantage from the technological advances of digitization, they are encountering an orderly increase in cyber security dangers. Profitable data is shared freely and as often as possible, and the defenselessness of that data to theft, destruction, or change by malicious actors persistently increments.
Cyber resilience is the capacity to plan for and adjust to changing threat conditions while withstanding and quickly recouping from attacks to infrastructure accessibility. Cyber resilience ideas give setting to executing a risk management strategy. For sure, cyber resilience is about overseeing threats: recognizing occasions that may occur, surveying that they are so prone to occur and what affect they may have, and choosing what moves to make. Cyber resilience guarantees that administrations can keep on being accessible and work without being risked, regardless of whether by digital dangers or by the effect of normal and man-made disasters. Digital continuity is one means by which an organization can build up its strength. Its objective is to keep up digital administrations and data applicable for the working for those administrations, regardless to any incompatible changes or interferences. Digital continuity is around information technology system capacity to keep conveying as proposed, regardless of whether digital security is failing or has failed.
Review of literature
The expanding interest for adaptability and scalability in progressively obtaining and releasing processing assets in a practical and device independent way, and ease in facilitating applications without the weight of installation and support, has brought about a wide reception of the cloud computing. While the advantages are many, this computing process is as yet powerless against countless disappointments; as a result, clients have turned out to be progressively worried about the reliability and accessibility of cloud computing administrations. Resilience fill in as a successful way to address clients’ reliability and accessibility concerns. In this paper, we propose to describe the role of cloud computing in cyber resilience. There are intermittent disappointments due to typical cyber attacks, we will examine the impacts of disappointments on clients’ applications and looking over adaptation of cloud computing in cyber resilience to various cyber attacks relating to each class of disappointments.
Cyber resilience can best be comprehended as an association’s abilities and capacities for readiness, reaction, and reuse even with a cyber risk. For any level of organization this incorporates processes that empower solidness, guarantee recovery and help reestablish their administrations quickly. At the end of the day, for all the organizations cyber resilience guarantees that its administrations can keep on being accessible and work without being imperiled, regardless of whether by cyber threats or by the effect of regular and synthetic disasters. Cyber resilience ought to be considered with regards to complex frameworks that include physical and data as well as intellectual and social spaces (Smith, 2005).
With regards to constant adjustment and reinvention, most of the organizations experience around the world has demonstrated that cloud computing can be a practicable and significant instrument for cyber resilience. For instance, a key element of cloud computing is the sort of geographic failover capacity that could shield basic administrations from the outcomes of a noteworthy emergency, e.g. a natural disaster, critical failure of infrastructure or a huge attack. In addition, cloud services can give huge levels of computing power effectively on request, implying that government departments and offices can utilize these services as bomb over for their own frameworks as and when required.
Further, the unpredictability, outrageous vulnerability, and quick development of potential cyber threats leaves risk assessment endeavors simply more unfit to enough address cyber security worries for basic infrastructural frameworks. Thus, the conventional methodology of solidifying of cyber frameworks against recognized dangers has ended up being unimaginable. The main genuine resistance that cybersecurity experts could take to solidify frameworks from the large number of potential digital dangers would incorporate the preclusion of cyber frameworks from getting to the web. Along these lines, similarly that biological frameworks create invulnerability as an approach to react to infections and different attacks, so excessively should cyber systems adjust, making it impossible to everchanging dangers that keep on attacking crucial system works, and to skip over from the impacts of the attacks (Linkov, 2013). Consequently, cyber resilience alludes to the capacity of the framework to plan, absorb, recover and adjust to adverse impacts, particularly those related with cyber attacks.
Nonetheless, to guarantee that cloud computing can be utilized for cyber resilience, many existing authoritative and approach systems require a survey, which is probably going to be unpredictable and will distinguish issues of discussion, for example, what sort of information is permitted to be exchanged crosswise over national borders.
Research Problem and Discussion
Society is progressively dependent upon perplexing and interconnected cyber frameworks to direct everyday life exercises. From individual back to overseeing defense abilities to controlling a tremendous web of aircraft traffic, cyber data frameworks and programming bundles have turned out to be coordinated at for all intents and purposes at all levels of individual and aggregate action. While such coordination has been met with tremendous increments in productivity of administration conveyance, it has additionally been liable to a differing assortment of threats from evil programmers, gatherings, and even state government bodies. Such cyber threats have moved after some time to influence different digital functionalities, for example, with Direct Denial of Service (DDoS), information robbery, changes to information code, infection through PC infection, and numerous others.
Attacking targets have turned out to be similarly different, running from people to global
organizations and national government offices. At the individual level, a large number of individual information records including credit card data and government recognizable proof is stolen every day – disturbing the lives of numerous people and creating billions of dollars in misrepresentation or different misfortunes. At the corporate level, hacking endeavors focused at the Sony Corporation, Equifax, and other likewise estimated associations exhibit the potential for programmers to pick up section to delicate data put away in organization databases, and possibly affect the security of a millions of users. Finally, state-based cyber dangers emerge from singular programmers and other huge states alike, for example, with every day interruption endeavors that happen inside the Department of Defense. While numerous cyber dangers are foiled, many can correct enduring and across the board harm as far as security, money related misfortunes, social issue, and different concerns. In warfare, cyber threats may soon end up one of the primary factors that choose whether a war is won or lost (Kott, 2015).
While conventional risk assessment involves a count of result of threats, vulnerabilities, and ramifications for hazards and their ensuing exposures, risk assessment ends up constrained in the cybersecurity field as methodologies are expected to address threats and vulnerabilities that end up coordinated inside a wide assortment of reliant computing frameworks and going with the architecture (DiMase, 2015) (Ganin, 2017). For very complex and interconnected frameworks, it turns out to be restrictively hard to direct a risk assessment that enough records for the potential falling impacts that could happen through a blackout or misfortune overflowing into different systems. Given the fast advancement of threats to digital frameworks, new management approaches are required that location hazard over every single related space of cyber systems (Linkov I. , 2013).
Cyber resilience guarantees that system recovery happens by considering interconnected hardware, software and detecting parts of cyber foundation. It is in this manner establish a bridge between managing tasks of the system while guaranteeing mission execution. Resilience has roots in numerous controls and incorporates environmental, social, psychological, organizational, and engineering points of view and definitions. Resilience engineering, for instance, has been characterized as “the capacity of systems to envision and adjust to the potential for surprise and failure,” and has been related with a move in safety paradigm recognizing that system adapting is essential when avoidance is unimaginable (Hollnagel, 2006).
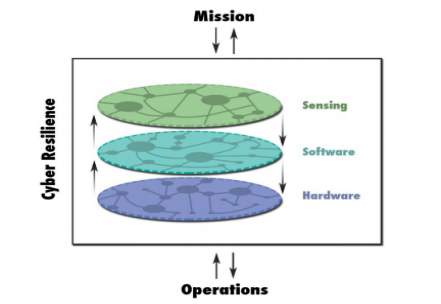
Fig: The cyber resilience domains includes sensing hardware and software components
Resilience is frequently mistaken or conflated for a few other related but unique ideas. These comprises of risk, strength, and security. A “Risk” is the probability of a threat operator exploiting the helplessness and the relating business effect. If risk is overseen fittingly, system achieves condition of security or vigor. Security, robustness and threats are associated, they are centered around keeping system from debasing and keeping usefulness inside satisfactory level when the threat occurs. Resilience is an altogether different idea. Oxford characterizes it as “the ability to recover rapidly from challenges.” Resilience assessment along these lines begins with the suspicion that system is influenced, usefulness is weakened and is centered around assessment of recovery speed.
The key segments of cyber risk are moderately well known. The probability of a successful cyber attack can be exactly estimated and evaluated with a level of exactness from known attributes of a network or system (Leslie, 2017). Since cyber threats are hard to measure, current endeavors move from evaluating risk in particular units (like probability of failure) towards risk-based decision making utilizing multi-criteria decision analysis (Ganin, 2017). Not at all like the idea of resilience, the idea of risk does not answer the inquiries of how well the system can retain a cyber assault, or how rapidly and how totally the systems can recover from a cyber assault. At whatever point risks are distinguished and moves made to decrease chance, there still stays remaining danger. As such, resilience appraisal and administration are, to some extent, a push to address that staying known, yet unmitigated, risk and in addition upgrade the general capacity of the framework to react to obscure or rising dangers.
Traditional risk assessment is engaging for cyber risk administration because of the quantitative nature and the single risk esteem that is yield. These qualities make chance edges simple to formalize in arrangement reports and to manage in a predictable way at the government level. In any case, quantitative risk assessment ordinarily includes measurement of the probability of an occurrence of events and vulnerability to the event. Rising cyber realities and advancements are giving new dangers indeterminate force and recurrence and the vulnerabilities and results as far as the degree of setbacks, financial misfortunes, time delays, or different harms are not yet completely comprehended or displayed. Thus, risk calculations turn out to be more dubious and produce expensive arrangements since various, frequently theoretical, risk situations could point to numerous vulnerabilities and disastrous system failures that are excessively expensive to moderate, assimilate, or recover. Besides, clients and different stakeholders may have inclinations for tolerating some loss in execution of one part in the system over any debasement in another part (Bostick, 2017). One result can be noteworthy financing spent in manners that don’t line up with stakeholders, bringing about disappointment with execution, notwithstanding the cost, or even case that meddles with the risk decrease efforts.
Each entity, organization, association, or state is liable to pressures got from occasions, changes, and episodes that happen in their condition. These circumstances of stress are new difficulties whose goals will influence the working of the association until the point that the circumstance can be overseen through robotization. With regards to the security of associations, the pressure circumstance being referred to requires a response that includes another emphasis on the security program all through the association. Organizations must recognize resources with the best esteem and set up another model of security administration that unifies, with a specialist security group, the supervision of all cybersecurity endeavors all through the organization. It is here that the leader of this group picks up visibility and participates in the decision making of the association, framing some portion of the official group.
The Evolution of cyberthreats
Cybercrime is an appealing and profoundly lucrative business. Attackers have more and preferable assets available to them over any other time in recent memory — both specialized and financial. This enables them to grow progressively complex attacks. This outcomes in more unpredictable and more unique dangers, notwithstanding a more prominent number of assaults.
Equifax, CCleaner, WPA2, Vault7, CIA, KRACK, NSA… these are only a couple of the primary characters of the business cybersecurity scene of late months. They were the heroes of huge contaminations, information burglary, ransomware assaults, hacked applications used to dispatch assaults against a nation or complete focused on assaults against extensive organizations, or endeavor vulnerabilities influencing billions of gadgets.
The devastation that followed from three ongoing occasions must be mulled over. From 2011 to 2014, the Dragonfly cyber undercover work aggregate reliably stood out as truly newsworthy, quickly growing its exercises and endangering the North American and European vitality segment. Dragonfly exploited two major parts of a pernicious program, to be specific remote access devices, accessing and controlling contaminated PCs.
In 2017, there were two assaults that emerged particularly for the effect and harm they caused: WannaCry and GoldenEye/NotPetya.
WannaCry showed up in May, spreading and wreaking devastation on corporate systems around the globe, turned out to be one of the biggest assaults ever. Despite the fact that we have seen considerably more great assaults before, (for example, Blaster or SQLSlammer, to name only two), at any rate as far as number of casualties and rate of spread, in all actuality the harm they caused was simply insurance. In any case, WannaCry is a ransomware with arrange worm usefulness, so every contaminated PC wound up with its reports being commandeered.
Goldeneye/NotPetya was the second assault with the best repercussion of the year, as a post-quake tremor of the seismic tremor that was WannaCry. In spite of the way that its casualties were at first constrained to a particular land region (Ukraine), it wound up influencing organizations in more than 60 nations.
The attack, precisely arranged, was done through an extremely prevalent bookkeeping application among organizations in Ukraine, M.E.Doc. The attackers bargained the server updates of said programming, so that every one of the PCs with M.E.Doc introduced could be contaminated in a flash and consequently. Notwithstanding encoding the records, if the signed in client had chairman authorizations, the malware went for the MBR (Master Boot Record) of the hard circle. At first it was by all accounts a ransomware in the vein of WannaCry, yet in the wake of investigating it altogether it turned out to be certain that its creators did not plan to let the delivered information to be recuperated. Days after the fact, the Ukrainian government transparently blamed Russia of being behind the assault.
Also, in the field of cybersecurity, 2018 proved unable have begun off more regrettable: the security imperfection found in Intel, AMD and ARM processors was fatal genuine. This structural outline disappointment, went with by mistakes in the working framework, dropped like a bomb in the innovation area, and all worked with time as the opponent to close the holes when conceivable
The flaw, utilized by the Meltdown expolit in Intel designs, is particularly basic from the point
of perspective of touchy information exfiltration — data for example, qualifications, messages, photographs and other records — permitting the assailant, through a malevolent process that keeps running at the client level on the PC or server, to peruse the memory of other forms, including favored procedures of the working framework piece.
Both household clients and essentially all organizations are influenced, since Specter follows up on PCs, workstations, Android telephones and on-commence servers and Cloud servers. The more basic the data being taken care of, the more noteworthy the danger of being the objective of an assault utilizing this instrument. What’s more, there are bounty more genuine cases coming to the monsters of various segments. For instance, Apple, which was gotten in the crossfire of captures made in China of 22 individuals who supposedly trafficked with organization information. All markers point to an inside activity, since a portion of the prisoners worked for organizations subcontracted by Apple and approached the trafficked information.
HBO has likewise endured a few cyberattacks as of late. In one of them, servers were endangered by taking complete scenes not however debuted from various TV arrangement, as well as inward data.
Challenges for organizations to become cyber-resilient
Each and every entity, organization, association, or state is liable to pressures got from occasions, changes, and occurrences that happen in their condition. These circumstances of stress are new difficulties whose goals will influence the working of the association until the point that the circumstance can be overseen through automation.
With regards to the security of associations, the pressure circumstance being referred to requires a response that includes another attention on the security program all through the association. Organizations must recognize resources with the best esteem and set up another model of security administration that brings together, with a specialist security group, the supervision of all cybersecurity endeavors all through
the organization. It is here that the leader of this group picks up perceivability and partakes in the basic leadership of the association, framing some portion of the official group.
More Threats, Higher Intensity:
In the United States, the Comprehensive National Cybersecurity Initiative (CNCI) was propelled with the Bush Administration in January 2008. This activity acquainted a separated methodology with distinguishing existing and developing cybersecurity dangers, finding and blocking existing vulnerabilities, and gaining from performers attempting to access government data frameworks. President Obama issued an announcement that “cyberthreats are a standout amongst the most genuine monetary and national security challenges we look as a country” and that “the financial success of the United States in the 21st century will depend on cybersecurity.”
Components of cyber resilience
- Readiness. To get ready for long haul readiness, an organization must distinguish resources, survey and oversee framework risk, create capacities to react to and recover from interruptions, and put resources into research, training, and practices that add to long haul cyber resilience objectives.
- Response. Utilizing the plans and techniques set up amid the readiness stage, resilient elements keep on working amid an emergency and bounce back rapidly. A strong response is likewise versatile and adaptable: improving amid an emergency is a key component of resilience.
- Reinvention: Gaining from and enhancing existing plans and techniques is a sign of cyber resilience. After an emergency has passed, analysis is vital: recognizing what was successful and where the response was risky; building up an arrangement for development.
Approaches to Improving Cyber Resilience
Resilience of a framework, a system or an association is impacted by various components, in a complex and regularly opposing way. In this section, we think about a portion of these components, and how they can be overseen or abused keeping in mind the end goal to improve the resilience.
Manage Complexity: Resilience of a framework or system depends extraordinarily on unpredictability of connections inside the framework (Kott A. &., 2014). In his spearheading work, (Perrow, 1984) clarifies that cataclysmic disappointments of frameworks rise up out of high unpredictability of connections which prompt cooperation’s that the systems architect can’t envision and make preparations for. System Resilience safety measures can be crushed by concealed ways, immense to the designer because the connections are so various, heterogeneous, and frequently certain. This issue is especially imperative in multi-kind systems, which are systems that consolidate a few unmistakable sorts – systems of physical assets, correspondence systems, data systems, and social and psychological systems. When we consider a whole multi-class arrange—and not only one of the heterogeneous, single-classification sub-organizes that contain the entire – we see unmistakably many-sided quality of the ways interfacing the system’s components.
Of specific significance are those ways inside the framework that are not perceived or grasped by the designer. Without a doubt, the designer can generally devise a system to keep an propagation of disappointment through the connections that are self-evident. Many, anyway are not self-evident, either in light of the fact that there are just an excessive number of ways to consider – and the numbers quickly increment once we understand that the ways between components of a correspondence framework, for instance, may likewise go through a social or a data arrange—or on the grounds that the connections are certain and inconspicuous. Unobtrusive criticism connections may prompt a disappointment in hierarchical decision making.
To improve resilience, now and again, the designer of the system can utilize more prominent unpredictability of associations between two components of the frameworks by expanding repetition of its functions. Also, as the number and heterogeneity of connections develop, they offer the specialists (or other dynamic instruments) inside the system more chances to recover the system’s execution. This operator might have the capacity to utilize extra connects to more components with a specific end goal to reconnect the system, to discover substitution assets, and eventually to reestablish its capacities.
Chose Topology: Quite separated from many-sided quality, the decision of proper topology of the framework or system can enhance resilience. Much earlier research tended to the crucial vulnerabilities of various systems as an element of their topological properties. Quite compelling has been the arrangement of properties of systems as per their hub degree conveyance. While a few systems, (for example, remote and work systems) are genuinely homogeneous and take after an exponential hub degree circulation, others, called without scale systems, (for example, the Web or the power-framework), offer noteworthy skew in hub degrees, depicted by a power-law. It is outstanding that without scale charts are substantially more vigorous to arbitrary hub disappointments (blunders) than diagrams with an exponential degree dispersion, yet that these sans scale charts are progressively more defenseless against focused assaults (in particular, expulsion of high-degree hubs). In this book, the part by Moore and Cho investigates the job of
topology and techniques to investigate the impact of topology on resilience; and the section by Kotenko et al shows topology-based strategies in examination of digital assault spread and the effect on resilience.
Include Resources: extra assets in a system can help enhance strength. For instance, adding ability to hubs in a power age and dissemination system may lessen probability of falling disappointments and accelerate the administration rebuilding. Including neighborhood stockpiling and impacting the conveyance of hubs of various capacities in a system likewise prompts enhanced resilience to the detriment of extra assets. Strength might be enhanced by adding different useful abilities to every hub (as a rule inferring the requirement for extra assets), by preparing more information sources
Outline for Reversibility: Components of the framework ought to be composed in a way that enables them to return to an experimental mode when fizzled or bargained. This implies a few things: (1) the segment in the fizzled mode ought not make any further damage itself or different segments of framework or condition; (2) it ought to be conceivable to invert the condition of the part during the time spent recouping the framework. This is on account of a few disappointments, for example, physical breakage and human misfortunes are frequently irreversible or costly to cure
Control Propagation: To improve the framework’s capacity to assimilate the effect of a digital
trade off, the designer should prepare for fell disappointments. Such disappointments are no independent in that one triggers another. A system that is inclined to expansive “domino impacts” will probably maintain extreme harm because of even unassuming aggravations, which fundamentally restrains the degree inside which proficient assimilation and recuperation (and consequently strong activity) stays conceivable. Hence, the conditions or connections between hubs should outlined, at whatever point conceivable, in a way that limits the probability that a disappointment proliferates from effectively starting with one hub then onto the next. In a perfect world, connections should both inactively and effectively sift through the spread of disappointment.
Provide Buffering: In information and product stream arranges, the capacity of the system is to offer its customers access to an arrangement of conveyed things. In such systems, supports (e.g., reserving, nearby capacity) establish a versatility instrument that forestalls the requirement for proceeded with access to the first source. Should the first source wind up inaccessible, one can change to a nearby provider. Subsequently, neighborhood access can be guaranteed in spite of interference of the worldwide supply arrange insofar as access to a nearby reserve (cushion) is accessible
Prepare Active Agents: Active specialists – human or fake – ought to be accessible to take dynamic measures to retain, recover and adjust. Keeping in mind the end goal to be compelling in doing as such, the operators must have plans, procedures and readiness. Where fitting and important, human administrators or clients of the framework should assume the job of dynamic resilience specialists. Wherever conceivable, be that as it may, the originator of the framework ought to consider bringing into the framework an arrangement of counterfeit halfway self-sufficient canny operators that can direct the ingestion and recuperation activities, in a self-sufficient way. Keeping in mind the end goal to play out the ingest and recuperate activities in nearness of the enemy malware conveyed on the inviting framework, the counterfeit operator frequently needs to take damaging activities, such as erasing or isolating certain product. Such damaging activities are precisely controlled by the proper standards of commitment. Engineers of the specialist should endeavor to outline its activities and arranging ability to limit the related hazard. This hazard must be adjusted against the annihilation caused by the foe if the specialist’s move isn’t made. Since the foe and its malware realize that the operator exists and is probably going to be available on the framework, the malware looks to discover and obliterate the specialist. Along these lines, the specialist has procedures and systems for keeping up a level of stealth, cover and camouflage. All the more for the most part, the specialist takes estimates that decrease the likelihood that the malware will recognize the specialist. The operator is aware of the need to practice self-safeguarding and self-protection.
Direct Analysis: As noted in a few places in this area, all resilience-upgrading measures and actin can likewise cause un-foreseen impacts prompting decrease in resilience. Subsequently, thorough, high-constancy examination is an absolute necessity. A resilience-improving measure ought not be planned or presented without a fitting investigation that is fit for uncovering potential negative effects and fundamental impacts (Kott A. , 2017). Similar explanatory investigations ought to be led with and without the proposed measure. High-constancy investigation is especially suitable.
Cloud Computing benefits
With regards to ceaseless adjustment and reinvention, our experience working close by associations and governments around the globe has demonstrated that cloud computing can be a practicable and important instrument for cyber resilience. For instance, a key element of cloud computing is the sort of geographic failover capacity that could shield basic administrations from the results of a noteworthy attack, e.g. a natural disaster, a basic system failure or a noteworthy attack. Besides, cloud administrations can give gigantic levels of processing power adequately on request, implying that administration divisions and organizations can utilize these administrations as flop over for their own frameworks as and when required. Since certain administration information and administrations are probably going to be in especially appeal amid times of emergency, the exceedingly versatile nature of cloud computing implies systems supporting these administrations are more averse to crash, even under curiously overwhelming utilization prerequisites.
Moreover, cloud vendors perceive that trust is a central piece of their plan of action and do their highest to keep it. In the meantime, they work on a scale that expects them to plan and manufacture their frameworks in view of the presumption that anything that can turn out badly will turn out badly, e.g. hateful users will exist, user workloads will in some cases be tainted with malware, or physical machines, organize gadgets, and storage clusters will come up short. Suppliers in this manner need to keep up entire control of the environment and authorize best practices and secure defaults for tenants. The huge pool of customers can likewise work to the advantage of security, as it permits cloud suppliers to search for security insight over their entire condition, which is considerably bigger than a normal organization’s conventional on-premises framework. This information can be utilized by enormous information security-knowledge frameworks to find malware and organize interruption endeavors far and wide. The quicker such threats are recognized, the better shot there is of ceasing malware before it contaminates a cloud supplier’s customer.
A viable and cyber resilient flexible execution of cloud computing administrations requires public sector elements to adjust a forward-inclining innovation pose that will guarantee an attitude that is ceaselessly watchful for security upgrades. To do as such organizations must consider the following activities:
- Conduct a threat investigation
- Characterize and organize critical services
- Set cyber resilience goals and objectives
- Implement pilot activities to test set up technical and policy prerequisites for utilization of cloud
- Define roles and obligations and determine assets required
- Conduct regular audits of the policies and process set up
The role of cloud computing in cyber resilience is an ongoing thought for most of the organizations. However, governments are progressively taking new advancements and, in a few nations, numerous taxpayer supported organizations currently exist principally or just in digital format. These administrations can frequently be critical exclusively to the working of the state, locale or city yet in addition to citizens ability to practice their rights and satisfy their duties. Keeping up those computerized administrations, particularly in an emergency, has required new risk administration considering and operational practices for governments. As a result, administrations of all sizes are currently swinging to adoption of cloud computing in cyber resilience and are looking at the role that cloud computing can play.
The practical benefits of cloud computing for Resilience
As their tasks turn out to be more information driven, governments and public division associations must guarantee that their administrations and information are as resilient as could be expected under the circumstances, and that they can be reestablished rapidly in the midst of emergency. Cloud can encourage this, supporting existing ways to deal with strength and progression while likewise giving new alternatives because of its distribution, scalability, security and cost-viability.
Geographical Distribution
A key element of cloud is the geographic failover capacity that could secure basic
administrations from the results of a noteworthy emergency, e.g. a natural disaster, a basic infrastructure failure or a huge attack. Anyway, not all states, areas or urban communities are presented to similar dangers. If such dangers are a part of a government’s more extensive risk evaluations, at that point the case for cloud in support of resilience is especially strong.
Most risks, e.g. earth quakes or flooding have a tendency to be gathered in specific areas or geographies. Significant cloud vendors, however, regularly run various datacenters over a sites, states and landmasses, and repeat customer information in at least two areas. This enables them to give powerful administration levels and information resilience despite geologically engaged dangers. In addition, with data center information, management and backup, data recovery considering neighborhood disturbances can be quicker and simpler. If an association loses access to its on-premises servers in an emergency, cloud suppliers can keep on defending information and bolster basic taxpayer supported organizations. Indeed, many cloud vendors back their affirmations of information accessibility by offering a service level agreement that provides 99.9 percent uptime to their customers.
Case Study – Cloud Resilience in Hong Kong:
Since 2016 Microsoft has offered a cloud solution committed to cyber resilience in Hong Kong. The arrangement is a partnership with NTT Communications and influences their Enterprise Cloud administrations and ICT foundation and Microsoft’s Azure cloud and ExpressRoute private passage, which guarantees that client information does not go over the open web. It is assessed that the expense of the offer is around 55% that of a self-manufactured, back-up arrangement.
Scalability: Cloud services can give giant levels of computing power adequately on request, implying that government offices and organizations can utilize these services as flop over for their very own systems as and when required. Taking full favorable position of this would however, require the pertinent government system to keep up dynamic contracts with cloud service providers and to keep a skeleton-version of the infrastructure running in the cloud. This would have funding suggestions.
Since certain government information and services are probably going to be in demand amid times of emergency, the exceptionally scalable and “elastic” nature of cloud computing implies systems supporting these services are more averse to crash, even under surprisingly overwhelming utilization necessities. The Organization of Economic Cooperation and Development (OECD) has noticed that the “elasticity” of cloud processing is one of its incredible quality.
Security: Cloud providers perceive that trust is a key piece of their plan of action and do their highest to keep it. In the meantime, they work on a scale that expects them to outline and construct their systems based on assumption that anything that can turn out badly will turn out badly, e.g. hateful users will exist, client remaining tasks at hand will in some cases be tainted with malware, or physical machines, network gadgets, and storage arrays will fail. Cloud providers in this manner need to keep up total control of the environment and authorize best practices and secure defaults for tenants.
The substantial pool of clients can likewise work to the advantage of security, as it permits cloud suppliers to search for security knowledge over their entire condition, which is much bigger than a normal company’s customary on-premises infrastructure. This information can be utilized by big data security-insight frameworks to find malware and arrange interruption endeavors far and wide. The quicker such dangers are recognized, the better possibility there is of ceasing malware before it contaminates a cloud supplier’s customer. It is vital to recognize that most innovation suppliers have embraced a “cloud first” approach. Thus, most of the advancement is conveyed in the cloud and just later converted into on-premises arrangements.
Cost Effectiveness: Most business cloud services are accessible on an as-utilized, pay-as-you-go or subscription basis. This implies data can be put away and anchored utilizing the most recent software and hardware; something that would have cost thousands of dollars in the past is currently given at a small amount of the expense. Moreover, as the assets are elastically provisioned, they can rapidly scale, and associations will pay for computing assets just when they require them. This can be especially useful for government capacities for example, preparing tax forms or conveying snow removal hardware that experience unsurprising spikes in utilization and limit.
Policy Foundations needed for use of cloud resilience and continuity
While there gives an impression of being practical case for the utilization of cloud benefits in digital continuity and disaster recovery plans, generally couple of governments have formal strategies that empower its utilization. Infact, many have strategies set up that could make it troublesome for government offices and organizations to exploit the cloud’s geological conveyance, scalability and cost-effectiveness.
In the meantime, ways to deal with the utilization of cloud in cloud resilience designs that suit one state may not suit another. This might be because of varying geopolitical substances, national infrastructures or usual way of doing things. Varying physical topographical areas may likewise bring natural factors that influence the pertinence or feasibility of utilizing cloud innovation, while contrasting levels of specialized capacity may likewise make a few alternatives less functional.
Strategy and legitimate difficulties may likewise emerge. The degree for dependence on cloud in coherence and flexibility anticipates any nation, area or city will rely upon their lawful structures, their hazard administration approach and their assessment of the risk scene. In general, the national lawful structure is probably going to decide a great part of the setting for territorial or city levels of government. The issues to be tended to could incorporate open segment acquisition and use rules, security models and structures, and examining.
Research Contribution and Future Work
Considering this complex and genuine display, in what manner can organizations intent to ensure their advantages in the most productive way imaginable accomplish this more versatile, mind boggling and cooperative methodology in their battle?
Cybersecurity ought to be dealt with as an issue of corporate hazard administration, not as an issue inserted in IT. The key components of its administration include:
- Prioritizing the most significant resources of the association.
- Prioritizing, knowing and comprehension the most important foes and dangers for each association.
- Knowing and executing the best barriers against present and potential dangers.
- Being set up for a moment when foes can sidestep all security advancements and identifying them, containing them and helping their activities as quickly as time permits to limit corporate harm.
- Adopting an emergency position which persistently what’s more, effectively looks for dangers, and identifying defenseless focuses that can later be utilized by danger on-screen characters to diminish the assault surface.
- Managing at the corporate level any correspondence of a break.
- Defining and continually executing activities to limit chance and reinitiate the cycle of persistent change in the administration of corporate security
Adaption is essential as the association’s procedures, innovations, devices and security administrations ought to be evaluated and balanced as dangers develop in a procedure of consistent change in light of carefulness. Being versatile suggests that this adjustment must be done in the base time interim, at the most extreme speed, even continuously.
Organizations must search out and relieve their risks at all levels. Making a total record all things considered, from information to applications, and checking all activities that are completed with them is a process that is long and monotonous, yet important. Organizations must exploit the apparatuses and administrations that computerize these undertakings of profiling, listing, and checking their advantages (people, information, framework) for aversion or potentially early recognition of enemies.
Associations need to comprehend and embrace the “resilience cycle” process, which will help security groups to persistently expand on the experience of blocked or potentially recognized dangers.
This necessitates they learn and adjust to the key periods of flexibility:
- In the pre-occurrence stage, through the capacity to more likely anticipate and oppose dangers, including cutting edge innovations that distinguish known and obscure or zero-day malware.
- During its execution, by responding rapidly with identification, control and reaction to sudden occasions that undermine the association to limit its effect on business; taking preferred standpoint of the new standards that emerge because of the checking and perceivability abilities that Endpoint Detection and Response (EDR) arrangements give.
Governments, regardless of their size or area, will at some point or another experience an emergency including digital resilience and advanced coherence. Resilience and progression will be imperative not just with regards to emergencies straightforwardly influencing an association, yet in addition when managing the swells and insurance impacts that influence our universally reliant digital foundation and frameworks. Regardless of whether it is by thinking about cloud relocation for more prominent digital resilience, or focusing on advanced coherence for taxpayer driven organizations, governments and open area associations when all is said in done should see distributed computing as a vital device in shoring up their emergency administration designs and abilities.
In any case, to guarantee that distributed computing can utilized for digital resilience, many existing administrative and approach systems require an audit, which is probably going to be intricate and will distinguish issues of debate, for example, what sort of information is permitted to be exchanged crosswise over national outskirts. In any case, the reward for states, locales and urban areas that grasp the digital resilience prospects managed by distributed computing and conquer the arrangement and specialized difficulties confronted won’t be constrained to defending the operability and progression of their basic capacities and administrations. The more extensive chances of the innovation for open and private
divisions, from government organizations to fire up business people, will be all the simpler to grasp because of the strong lawful and arrangement system that will result from this procedure.
One of the significant difficulties to building a viable long-haul cyber resilience system and usage plan is precisely portraying and measuring the center abilities required. Drawing vigorously on the Threat and Hazard Identification and Risk Assessment Guide distributed by the US Federal Emergency Management Agency (FEMA), five key advances are prescribed to that fundamental procedure:
1. Distinguish key threats and evaluate their effect on basic frameworks and capacities.
2. Group and organize basic administrations.
3. Set cyber resilience objectives and targets.
4. Develop cyber resilience results and distinguish and test abilities.
5. Characterize jobs and duties and decide assets required.
Understanding cyberthreats and assessing their probability can be dangerous. There are numerous pernicious on-screen characters, thought processes and assault vectors. A few assaults may essentially be preludes to other people. The intricate connections between frameworks may offer ascent to unforeseen falling impacts more extreme than the harm initially proposed by the programmer. At last, the nature of the harm may not be quickly self-evident, for instance the exfiltration of information from touchy frameworks or considerably more lamentably modification of basic information.
Organizing which basic administrations and touchy data to secure includes extreme
exchange offs. Recognizing all administrations and resources as high need isn’t down to earth, so it is important to characterize and actualize an unmistakable system for ordering information and administrations (counting those worked by outsiders) as high, medium, or low effect. The National Institute of Standards and Technology (NIST) offers one such structure: Standards for Security Categorization of Federal Information and Information Systems.10 Once benefits are grouped, organizing them must be grounded in a strong comprehension of the inward workings of each administration and how it is associated with and subject to different administrations. The NIST Framework for Protecting Critical Infrastructure Cybersecurity is a definitive asset that can help with settling on hazard-based security choices.
Before objectives and targets can be set, key partners must have a clear and regular comprehension of their vision for cyber resilience, one that reflects societal qualities, conventions, and legitimate standards. This is the establishment for what will be a community-oriented exertion to set objectives that portray an abnormal state wanted result or ability and supporting targets. It is basic these objectives and goals are sufficiently adaptable to oblige inescapable changes in administrative association and in innovation. Cyberattacks, catastrophic events and such don’t cause issues only for IT divisions. They can make political and social agitation by physically wrecking equipment and information. In this way, any resilience system needs to determine its coveted results, and afterward distinguish the abilities important to react to recognized dangers and effectively convey those results.
References:
Bostick, T. P. (2017). Enabling stakeholder involvement in coastal disaster resilience planning.
Cisco. (2016). Retrieved from Cyber Resilience: Safeguarding the Digital Organization: https://www.cisco.com/c/dam/en_us/about/doing_business/trust-center/docs/cisco-cyber-resilience-safeguarding-digital-org-wp.pdf
DiMase, D. (2015). Systems engineering framework for cyber physical security and resilience.
Essential role of cloud computing in cyber resilience and digital continuity. (n.d.). Retrieved from Microsoft: https://www.microsoft.com/en-us/cybersecurity/content-hub/essential-role-of-cloud-computing-in-cyber-resilience-and-digital-continuity
Ganin, A. (2017). Multicriteria decision framework for cybersecurity risk assessment and management.
Hollnagel, E. W. (2006). Resilience engineering: Concepts and precepts. Aldershot: Ashgate.
Kott, A. &. (2014). Resiliency and robustness of complex systems and networks. Adaptive Dynamic and Resilient Systems.
Kott, A. (2006). Information warfare and organizational decision-making. Artech House, Boston.
Kott, A. (2015). Will cybersecurity dictate the outcome of future wars.
Kott, A. (2017). Assessing mission impact of cyberattacks.
Leslie, N. O. (2017). Measurable resilience for actionable policy. The Journal of Defense Modeling and Simulation, 49-63.
Linkov, I. (2013). Measurable resilience for actionable policy. Environmental Science and Technology.
Linkov, I. E. (2013). Measurable resilience for actionable policy. Environmental Science and Technology.
Perrow, C. (1984). Normal accidents: Living with high risk technologies. Princeton University Press.
Smith, E. A. (2005). Effects based operations; Applying network centric warfare in peace, crisis,. Office of the Assistant Secretary of defence, Washington DC.
Vacca, J. R. (2013). Cyber Security and IT Infrastructure Protection. Elsevier Science, Syngress.
Vacca, J. R. (2017). Cloud Computing Security. Taylor & Francis Group.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




