Developing Trust Models for Cloud Computing
Info: 11320 words (45 pages) Dissertation
Published: 11th Dec 2019
Tagged: TechnologyComputing
Chapter 1- INTRODUCTION
1.1 Background
From the past few years, cloud computing has turned out to be component of competitive market. Most of the organizations make use of cloud computing to an extent. While cloud computing services is expanding and achieving popularity, people are dread to use cloud services which is still a broad issue. Different issues are recognized in literature; two of the major ones are trust and security. Since its beginning, security risks has gained attention in the context of cloud computing. To improve the security strength of service provider or service, various tools and protocols are always in need.
In the cloud computing environment, Service providers provide users with various services. However, these services comes with certain features, specifications, methods of gaining security. Some service target on secure network while other services focuses on reliable access to data and service through encryption. Nature of technologies adopted by different service providers differ from each other to gain security. A customer can request a service based on level of security provided and user requirement. Now the challenge comes when analyzing a specific service based on its different security properties. The important challenge is to trust a cloud service provider based on its security. One can do that by creating a model in which confidence can be taken as a trust value. This report builds such a framework where user can get the best service provider according to his requirements.
Thesis introduces a trust framework that the user can use to identify the best service provider based on the needs of the user. Also user is authenticated when he wants to use services. Due to this trust worthiness of both the sides is verified and then only user can upload his data on the cloud. We can also give feedback about the service providers that can be used as one of the parameters while evaluating service provider. Best service provider is selected based on user requirements and the rating which the previous user has given to the system. Then after the suitable provider is identified, files are securely uploaded on the cloud. This preserves the security and reliability of data. User is also verified by using the encryption and decryption techniques due to which false user is not able to take part in the whole process.
1.2 Outline of Cloud Computing
A computing base which consists of collection of interdependent computing nodes, hardware, servers as well as applications and services which are allocated to different users is Cloud Computing. It promises to deliver secure, reliable, fault-less, scalable, and firm services, infrastructures to the cloud users. They have the aim of providing unlimited virtually storage and computing, and not disclosing the complexity of large distributed computing from users. Internet or other private networks or their combination are used as a means for delivering services. Depending upon their capability, availability, Quality of Service requirements, cloud services are accessed through these networks.
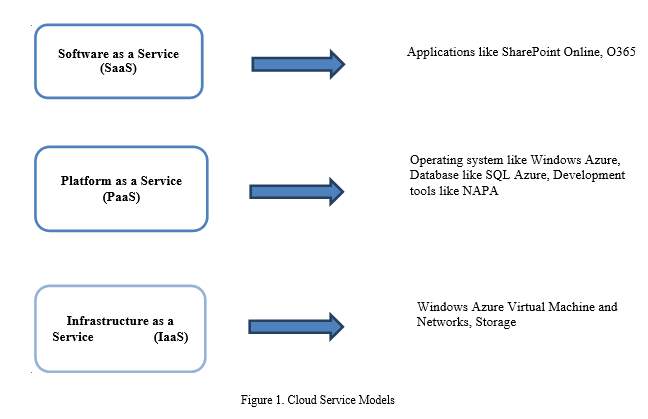
There are three types of service models in Cloud computing paradigm: Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS).
- In Software as a Service (SaaS) model, a software application runs on the cloud infrastructure and it serves multiple end users. Google Apps is one of the examples. Google calendar is another example that gives cooperation on applications like project management etc. through internet.
- In Platform as a Service (PaaS) model, the customer has the liberty to create and host his own applications which run on the cloud infrastructure. Heroku, Google App Engine are some of the examples of PaaS.
- In Infrastructure as a Service (IaaS) model, hardware resources like servers, data space, network accessories etc. are made available to customers. Amazon Web Service (AWS) and Microsoft Azure are the examples of IaaS. Examples of Amazon are Simple Storage Service, Elastic Compute Cloud (EC2).
1.3 Characteristics
Cloud computing serves as a virtual repository of resources which can be utilized by a number of users simultaneously through the complex network of the internet. Cloud computing enables the user to take advantage of the high computational power and high storage capacity at minimum cost. The goal of cloud computing industry is to fully utilize cloud infrastructure with minimum cost and maximum profit. The remote use of leased computation power and data repositories has been noticed as a new trend among IT users. Cloud computing provides a dynamic and scalable computing infrastructure for such users. Services on the cloud facilitate individuals as well as business enterprises to use software and hardware resources which are managed and maintained by third parties at physically remote locations.
Since 2007, cloud computing has been started and it’s expanding very robustly. It has different characteristics that influences people to use cloud computing paradigm. Few of them are discussed below:
- Self-service on-demand: It is a popular feature in which user can make use of resources as needed anytime. It helps users to perform tasks like managing, building, scheduling and deploying. The customer should be able to utilize the resources as and when they are needed without any permission from cloud provider. This helps user in making better decisions.
- Ever present access to network: Since the services are accessible via browser, it is accessible from anywhere across the world and from any gadget that assists web interface. Similar to web service, even cloud service is accessible.
- Resource pooling independent of location: Resources are shared or pooled to fulfill a large number of customers. It uses the concept of multi-tenancy where various resources are dynamically allocated and deallocated on demand. User is unaware of resource location.
- Flexible scaling: It is totally scalable. Facilities like memory, computational power and others can be scaled i.e. increased or decreased according to user needs.
- Service specific billing: Cloud computing does not possess any advance cost. It is totally dependent on the usage. Depending upon the resources used, customer is billed. This helps out user to track their use and automatically assists to reduce cost. Cloud computing makes it possible that information collected regarding billing to be transparent and it is easily available to user.
The above mentioned features of cloud computing forces various users and organizations to use this platform.
- Cloud Environment Security
According to the type of models like PaaS, SaaS, or IaaS the cloud provider builds, utilizes and manages the application, resources and services in a cloud computing environment. The properties which make effective use of already available resources are virtualization and software multitenancy. Due to virtualization single data center, server, operating system arranges various users. Because of resource sharing concept millions of users are helped by cloud providers. Resource management, communication, data security for virtualization are few of the security factors in cloud paradigm. The significant types of threats are picturized by following figure and explained below:
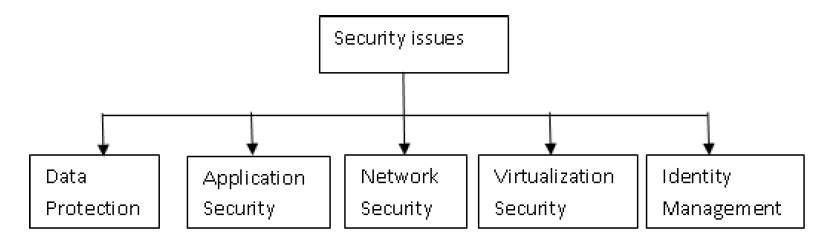
Figure 2. Categorization of Security
Each of these issues are currently active sectors of research and technology in CC context. Lots of analysis is done for this issues. Huge research is proceeding in this area to address this parameters. Multiple solutions or results exist and many more are yet to come. By keeping this in mind, thesis has highlighted some of the techniques related to security factor.
- Network Security:
Depending upon the deployment pattern, a cloud computing can be of type private or public. In cloud scenario, from remote locations applications and services are accessible. Security challenges which are significant are uninterrupted availability of service without any disturbance because of network issues like Denial of service attacks or other attacks.
- Data Protection:
Everybody knows that in cloud computing data is shared among multiple users at any point of time or everywhere. Under service provider’s control, information is stored safely and processed in an environment which is shared one. Data may be interfered by any suspicious entity. The factors which make data protection and privacy important in cloud environment are administrative issues and lack of transparency about data location. Therefore key issues regarding data protection includes integrity, confidentiality and availability of data.
- Identity Management:
During the time of registration identities are created for cloud services to access it. So using that particular identity each user alone can access a cloud service. Uncertified access to services and applications is one of the crucial issue. A fake user can act as an official user and get access to cloud service. Due to this problem is created for authorized users as service is unavailable for them. It could also happen that data usage boundary is crossed by that user. This could be like performing any task which is not maintained by access control for particular application or entry to protected area. Hence, for both user and service provider identity management is an important issue in CC.
- Application Security:
Various security issues comes into play when dealing with application software being developed or running. Considering provider’s side, application that is running from faraway must be from trustworthy provider and that too without any threats. Major threats for application security are availability, openness and flexible anywhere. Another factor that is also very important is data integrity as they are executed from remote locations.
- Virtualization Security:
Due to the introduction of virtualization concept many new attacks came into existence through management and other elements. Man-in the middle attack comes during sharing of resources between Virtual Machines (VMs) through multi tenancy at the authorization time of service. There is no consistent way to check the security of virtual applications. In cloud environment, VMs are formed and returned back as when needed. Due to this reverting nature of VMs, it is difficult to gain a reliable security. So that leads to another issue during the usage of cloud resources.
Features of virtualization, multitenant and openness of cloud computing bring potential security issues to cloud services such as unreliability, insecurity, and inconsistency. The security issue is an important aspect of cloud computing which cannot be ignored. Access control is one of the most important measures to ensure the security of cloud computing. Early access control technology can not only ensure normal access requirements of valid users, prevent invasions of unauthorized users, but it can also solve security problems caused by valid user’s misoperation. Cloud computing environment is a typical distributed environment; hence the distribution, dynamism and anonymity of information resources and services are remarkable features of cloud computing environment [3].
Therefore, the traditional centralized access control model has apparently cannot satisfy the security requirements of cloud computing. The implementation of access control in cloud computing environment will face a series of challenges. In cloud computing, researchers are more concerned about how to implement access control polices through unconventional ways. In 1996, Blaze M proposed the concept of trust management and for the first time applied trust mechanism to the technical field, providing a new way of solving security problems in cloud computing environment. On the basis of trust management, trust mechanism will be introduced into access control area and trust will be redefined and calculated. Due to the dynamic characteristic of the trust, trust computing is a major difficulty [4].
Authors discussed that trust and security are one of the obstacles for acquiring cloud computing. Service Level Agreements (SLAs) are inappropriate for establishing trust between cloud providers and consumers due to its inconsistent and unclear subsections. One way to achieve trustworthiness of services can be done by using consumer’s feedback. Researchers have identified the importance of trust management based on collected feedbacks from users. There are various issues of trust management in cloud computing which are as follows:
- User’s privacy
Privacy issues are raised while adopting cloud environment. Dynamic interaction of consumer with the cloud provider may consist of sensitive data. There are various chances of leaking sensitive information such as behavioral information (interest of a user, with whom user interacted, etc.) or address and phone number. Thus services which involve such data should strictly maintain consumer’s privacy.
- Cloud service protection
Cloud services experience attacks from its users are not the unusual one. By creating several accounts or misleading feedbacks, services are getting affected. However, detection of such behavior is not so easy. Firstly new user joins the cloud and suddenly old user leaves it. This dynamism makes it very difficult to identify malicious behavior. Secondly, users may have multiple accounts for particular service that makes it even more difficult. At last, we can detect exactly at what time when such behavior occurs.
- Trust management service’s availability
For effective trust management, trust service provides an interface between cloud services and users. But assurance of availability of this is a challenging problem because of the infinite number of users and dynamic nature of the cloud. Thus, trust management service should be highly scalable and adaptive to be useful in cloud environments [5].
Cloud Service Certification (CSC) is the other way for establishing trust and increasing the transparency of cloud. Various CSC has evolved such as Euro Cloud Star Audit or CSA STAR. This CSC ensures the high level of security for a particular period of time like one to three years. However, a cloud is an ever-changing environment that may put these certifications in trouble. If configuration changes occur then CSC may not meet the required criteria. Thus continuous auditing of CSC is required to assure secure, transparent cloud service and to establish trustworthy CSC [6].
- Problem Statement
The issues of trust, security and privacy exist from the development of Internet. The main reason why they are extensively spoken these days is because of one thing i.e. Cloud Computing. It has become the hot topic in research and consumer area. Any organization or user that stores the data in cloud is worried about the risk of whether their data will be safe or not. Hence it is important for both user and provider to have mutual trust such that provider assures that data won’t be insecure. Thus, there is need of developing trust models.
- Motivation
A lot of people have been talking about cloud computing. It is the current trend that has been used widely all over the world. Various advantages are present of cloud computing. They are:
- Ubiquitous network access
- Pay per use
- On demand self-service
- Research Gap Identified
- There is need to increase trust results accuracy by combining trust management techniques such as recommendation and reputation.
- Another gap can be performance optimization of trust management service for better results.
- By using conceptual architecture, technical implementation is not provided. Only broad outline is given.
- To address current issues and gaps in cloud computing, researchers believe that continuous auditing of cloud services is one of the best possible way.
- Objective
- The objective is to establish trust among users so that people will use cloud computing effectively and efficiently.
- To identify attributes for trust management in cloud computing.
- To implement a trust based protocol that runs between user and cloud provider.
1.9 Basic Terms
- Federated cloud:
The deployment and management of multiple internal and external cloud computing services to fulfill business needs is the federated cloud. It is also known as cloud federation. Federation is nothing but the combination of several smaller parts that perform a common action. Federated cloud is the union of infrastructure, software and platform services from different networks that can be accessible by user via the internet. It is facilitated through network gateways which connect private, public clouds and community clouds creating a hybrid cloud environment. Federated cloud rely on physical data centers. Federation of cloud resources allows user to select best service provider in terms of cost, flexibility and availability of services to satisfy the particular business requirement. It also makes it possible to distribute workloads around the globe, implement security models for user access and move data between networks.
- Trust in cloud service:
Cloud Computing has become very popular nowadays because consumer can use the cloud services at a very low cost. It has opened up new challenges by introducing various type of trust scenario. Today, problem of trusting cloud computing is main concern for most organizations. The gap between innovation and adoption is so large that cloud consumers don’t fully trust this new way of computing. Trust is one of the most demanding thing in the world of cloud computing. The distributed nature of cloud services introduces various factors like security, privacy. Maintaining user’s privacy is not an easy task because of the data involved in it. One of the main problems is protection of cloud services. Due to the dynamic nature of cloud environment, it is difficult to manage trust among users. Building a mutual relationship between cloud and user is the key to achieve users trust.
- Believability of provider:
Cloud service providers (CSP) are companies that provides services, business applications and infrastructure in the cloud. Cloud services are hosted in a data center which can be accessed by individuals through network connectivity. Benefit of using CSP is scalability and efficiency. Rather than companies building their own infrastructure, services can be purchased from CSP which offer services. Various services by CSPs are Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS). Nowadays many CSPs are concentrating on providing high levels of security and service. IaaS and PaaS generally come with performance guarantees. As CSP hosts applications and data storage, customers must be assured that their data will remain secured and data center where applications are hosted fulfill certain requirements. SSAE16 and ISO are some of the certifications for data centers that provides levels of security, safety, reliability and availability.
- SLA based trust:
Cloud computing is a technology where platform, software, infrastructure and storage can be delivered as a service on the basis of pay per use concept. But for critical applications and sensitive data cloud providers must be chosen based on level of trustworthiness. Service level agreement (SLA) is the official commitment that happens between customer and service provider. This can be legally binding informal or formal contract depending on the situation. Aspects like availability, quality are agreed between user and provider. The most important component of SLA is that services should be offered to user as mentioned in contract. In pervasive computing, trust management is an issue where providers and customers are distributed across domains. A well-defined SLA includes components as type of service to be provided, steps for reporting issue with the service, monitoring process, service’s desired performance level, reliability and responsiveness, repercussions for service provider for not meeting its commitment etc.
- Reputation based trust:
In reputation based trust models, the connection between consumer and provider is established by calculating trust index obtained from neighboring entities. This involves infinite transactions. Due to reputation based trust model users are able to select trustworthy provider. Also there is elimination of false feedback to protect provider’s trust index. Cloud Armor is a reputation based framework that offers functionalities to deliver trust as a service which includes 1) robust and adaptive credibility model for measuring credibility of feedbacks to safeguard services from malicious users, 2) a protocol to prove credibility of feedbacks and preserve user’s privacy and 3) availability model. Reputation information can be useful for predicting future behavior of entities and estimating the trustworthiness.
- AES Algorithm
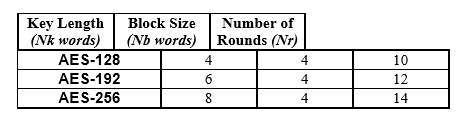
Figure 3. AES
Algorithm Functions, Symbols and Parameters:
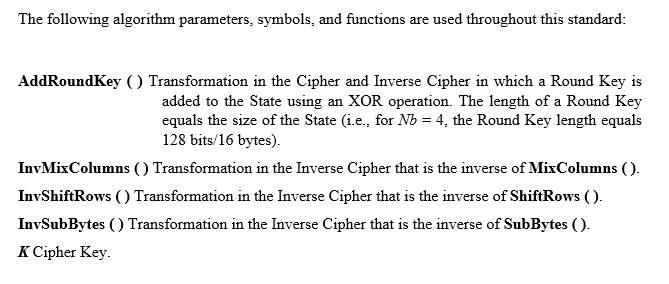

Figure 4. Pseudo code for the Cipher
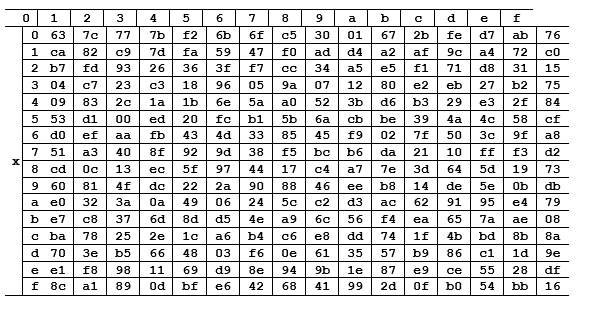
Figure 5. S-box
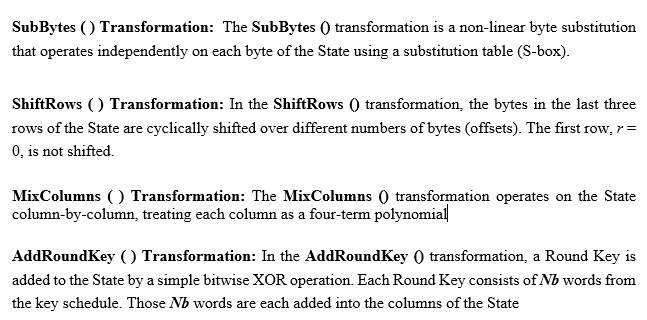
- ECC (Elliptic Curve Cryptography) Encryption
For implementation of public key cryptography, another method that can be used is ECC algorithm. This algorithm works on conversion of big integer to integer and again from integer to big integer. ECC does not work for image files. We have to use Blowfish algorithm for image encryption. ECC works for pdf and text files.
Following is the sample code of ECC encryption algorithm. We will get the basic idea of how it works.

- DES (Data Encryption Standard) Algorithm
DES is a symmetric- key approach for data encryption. As the DES operates by using the similar key for encrypting and decrypting a message, so both the receiver and sender must have and use the same private key. Over the years, this techniques has been replaced by more secure AES algorithm.
This standard follows a Block Cipher, that means a key and algorithm are applied to a block of data concurrently rather than one bit at a time. DES organizes it into 64-bit blocks for encrypting a plain text message. By using permutation and substitution, each block is enciphered using secret key into a cipher text of 64-bit. This whole process can run in four various modes and involves 16 rounds. Decryption is just opposite to this, following same steps but in reverse order in which keys are applied.
- RSA Algorithm
RSA stands for Rivest, Shamir, and Adelman who are the inventors of the technique. RSA is extensively used for securing sensitive data, specifically when data is being sent on unconfident network like internet and it is used for public-key encryption. This method of cryptography uses two different keys, one private and one public. The private key must be kept secretly whereas public key can be shared with others. In this, both private and public keys can encrypt the data or message; the opposite key from one that is used to encrypt data is used to decrypt the data. Due to this mechanism, RSA has become the mostly used asymmetric algorithm. It has several advantages like integrity, confidentiality, and so on.
For deduction of RSA keys it requires huge amount of time and processing power. Netscape Navigator and Microsoft Internet Explorer are the software products built from it.
Chapter 2 – LITERATURE REVIEW
2.1 Trust evaluation mechanism
Mohan K et al (2016) proposed a new trust evaluation scheme that is based on fuzzy logic inference system for health care system. The trustworthiness of cloud providers is evaluated in the proposed work. Due to this model, some cloud service providers are filtered for any user based on some parameters. Experiments are conducted using these parameters and compared with previous method [7].
Mohan, K., and M. Aramudhan (2016) proposed cloud broker architecture in which various health providers are integrated together to form a group that fulfills the requirements of users and provides quality of service to all users. Various trust mechanisms are computed to ensure privacy and security of users. Attributes are used to calculate the trust value of health provider. Then based on that value selection is proposed. A new mechanism Patient Turned Queuing Scheduling (PTQS) is used to resolve the starvation [8].
Noor, Talal H., et al. (2016) have designed and implemented a technique called Cloud Armor, a trust management framework which provides a set of functionalities to deliver trust as a service. Two models are introduced: Credibility model and availability model. It mainly focuses on taking user feedbacks on cloud services [5].
Jameel, Hassan, et al. (2005) presented a trust model based on vectors of trust values. Evaluation of trust depends on the suggestion of peer entities. A method for handling false recommendations is also presented [9].
A Comprehensive and Adaptive Trust (CAT) model is proposed for large-scale P2P networks based on human psychological behavior by Li, Xiao-Yong, and Xiao-Lin Gui (2009). The simulation results show that model has remarkable enhancements as compared to existing ones [10].
2.2 Cloud Service Certification(CSC) and Security module
Sebastian Lins et al. (2016) ensured that Cloud Service Certification (CSC) assures a high level of security. Continuous auditing of certain criteria should be done to achieve reliable and secure cloud services. They have proposed a continuous auditing architecture and discussed various advantages and challenges [6].
Seol, Jinho, et al. (2015) introduces secure cloud architecture which also involves hardware security module that separates user data from cloud administrators. Hardware security module provides with required security by exposing certain interfaces to cloud administrators. Due to this administrators are protected from affecting the security of vulnerable management systems [11].
Mohammadnia, Hamzeh, and Hassan Shakeri (2014) suggested a novel model for cloud job distribution which makes better decisions for job switching and rescaling a construction for security management [12].
Hassan Takabi et al. (2010) talks about the reevaluation of security and privacy issues in clouds. Many modifications in existing solutions and newer solutions are urgently needed to make sure that cloud computing benefits are fully adopted [13].
Rizwana Shaikh and M. Sasikumar (2015) analyzes and measures a service based on security is a challenge. This paper presents such measurement by using trust model. Model measures the strength of security and computes trust value [14].
Jong P. Yoon and Z.Chen (2010) proposed a new security technique to enable multifactor access control and to manage various deployment models where system sessions and users network may vary. Privilege chains are build using metadata of resources and access policies. This paper verifies trustiness of cloud resources [15].
Alsharif Mohamed Y. Ahmed and Depei Qian (2013) have proposed an architecture and solution of trust management and security for distributed systems that uses cloud computing. Optimization is done which includes encryption, virtual personal networks and multi-paths transmission that enhances security and trust [16].
- Mutual trust
Lin, Guoyuan, et al. (2014) discusses main factor for the security of Cloud computing is the access control. By using the traditional model the issues of vulnerability and uncertainty are not solved. A mutual trust between user and cloud is the key to implement various access control method. Mutual Trust Based Access Control (MTBAC) model is proposed here. This model considers both user’s trust and node’s credibility. By implementing a model in cloud environment security problems are solved [3].
Tan, WenAn, et al. (2014) have discussed the problem of workflow scheduling (WFS) in the cloud environment. A trust oriented WFS model is proposed in this paper. A cloud service selection algorithm is designed. Proposed algorithm consists of trust metric that involves recommendation trust and direct trust. By adjusting weights of different criteria, results show that proposed method is effective [17].
Li, Xiaoyong, et al. (2015) proposed a new scheme called service operator aware trust scheme (SOTS) for resource matchmaking across multiple clouds. A middleware framework for trust management is designed that reduces user load. An adaptive approach is introduced that overcomes the limitations of traditional schemes. By using SOTS, useful resources can be provided to users in a multi-cloud environment [18].
Noor, Talal H., et al. (2016) have mainly discussed various challenges that are involved in managing trust in the cloud environment. It says that cloud computing is a promising technology but due to lack of trust management it is hindering in the market. Proposed framework can help various researchers to develop solutions to these problems [19].
Manchala, Daniel W. (2000) introduces the concept of trust and develops models that can use these parameters to verify e-commerce transactions in a way to be able to satisfy the requirement of mutual trust. By verifying transactions, we can avoid unnecessary costs of each transaction [20].
- Cloud Service Provider
Barsoum, Ayad, and Anwar Hasan (2013) proposed a cloud-based storage scheme that gives benefits to data owner by facilities provided by Cloud Service Provider (CSP). This helps to build indirect trust between them. They have justified the performance through analysis and implementation on Amazon platform have been done [21].
Baranwal, Gaurav and Deo Prakash Vidyarthi (2014) proposed a paper in which QoS metrics are identified and defined in such a way that cloud provider and user both can convey their offers and expectations respectively through quantified form is proposed. Here a flexible and dynamic framework is proposed using Ranked Voting Method that takes input as user requirements and gives output as best provider. Due to this proposed work, customers are able to understand provider easily and also providers can advertise their service in a better way [22].
Li, Xiaoyong, and Junping Du (2013) have presented an adaptive trust management model called Cloud-Trust for evaluating cloud service based on various trust attributes. Two types of modeling tools (rough set and induced order weighted averaging (IOWA)) are combined and applied to knowledge discovery and data mining. Rough sets discover knowledge and IOWA aggregate trust degree which gives better performance [23].
- User Trust
Rashidi, Ahmad, and Naser Movahhedinia (2012) discuss eight parameters which are thought to be important have been extracted, motivated by the need of user trust. Eight theoretical views of trust have been synthesized and a model is developed for consumer trust. The model is analyzed and effects of these elements are investigated and described. Results of this paper could be a hint for recognizing parameters affecting users trust [24].
Ahmad, Shakeel, et al. (2012) presented a research paper in which advantages and disadvantages are evaluated for users. In three turns new trust model is proposed. At first turn user must be contented with earlier experience of provider, at second turn user must be known about SLA, cloud computing, advantages, and disadvantages etc. Due to satisfaction at second turn now provider can be considered as reliable. At third turn, the user can trust that reliable provider [25].
Li, Xiaoyong, et al. (2015) presented T-broker, a trust-aware service brokering system for matching multiple cloud services to fulfill user requests is presented in this paper. Results show that T-broker gives the good outcome in many cases and proposed work is robust [26].
Khan, Khaled M., and Qutaibah Malluhi (2010) suggests emerging technologies that can be helpful to address the challenges of trust in cloud computing were discussed. Thus, more consumer control of processes and data and better transparency must be offered by cloud providers to regain user’s trust [27].
- Public cloud
Xue, Kaiping, and Peilin Hong (2014) proposed a dynamic secure group sharing framework for public cloud computing environment is proposed. The privilege can be granted only to some specific members based on proxy signature, session keys are protected and all the sharing files are securely stored in cloud servers. They have used an enhanced TGDH scheme to dynamically update group key pair when group members are joining or leaving the group. Even if all the group members are not together online, still their scheme works well. While providing forward and backward secrecy, digital envelopes should be updated that can delegate overhead to servers without revealing any information. The analysis shows that proposed scheme can achieve lower complexity and overhead [28].
- Reputation Management
Zhu, Chunsheng, et al. (2015) discusses that for cloud providers and sensor network providers, authentication, as well as trust and reputation calculation and management, are the two critical issues. In order to fill this gap, this paper proposed an authenticated trust and reputation calculation and management (ATRCM) system for CC-WSN integration. Proposed system achieves following three functions: 1) calculating and managing trust as well as the reputation of CSP and SNP; 2) authenticating SNP and CSP to avoid malicious attacks; 3) helping the user to choose the desirable provider based on authenticity, attribute requirement and cost, reputation and trust of CSP and SNP. System analysis shows that system is secure against attacks such as collusion, good mouthing and so on [29].
Shen, Haiying, and Guoxin Liu (2014) for collaborative cloud computing have proposed an integrated resource management platform called Harmony. This platform includes three components to increase mutual interactions for trustworthy and efficient sharing among clouds. Integrated reputation/resource component collects and provides information about resources available and provider’s reputation. Multi-QoS oriented resource selection component assist users to choose the provider which offer highest QoS. Price assisted reputation/resource control component gives incentives for nodes to offer high QoS. It also helps providers to keep their reputations high and avoid being overloaded. Simulation experiments on PlanetLab prove the effectiveness of various Harmony components and performance is better than previous ones. Results also show that Harmony achieves balanced load distribution, high scalability in large CCC environment [30].
Xiong, Li, and Ling Liu (2004) proposed PeerTrust, reputation-based trust framework that includes consistent adaptive trust model for comparing and quantifying trustworthiness of peers based on transaction feedback system. Paper also includes strategies for implementing the model in the decentralized P2P environment [31].
- SLA Based Trust Management
Balachandra Reddy Kandukuri et al. (2009) talks about present SLA discuss only services provided and waivers. Paper conveys that waivers have to be made according to business type done by the customer. Also, SLA should discuss legal actions that can be taken when services are misused [32].
Sheikh Mahbub Habib et al. (2011) talks about how customers are not sure whether they can select trustworthy cloud provider based on its SLA. To help customers for identifying they have proposed a multi-faceted Trust Management(TM) system framework. It helps to find the suitable provider by considering various attributes [33].
2.9 Trust Relationships and Actions based Trust Evaluation
Kouatli, Issam (2016) investigated trust relationship for cloud computing environment. A survey was conducted in which security, data protection, and ethics were the most important variables. Observational and data analysis was carried out and as a result, IT managerial guideline was proposed [34].
This paper presents a complete approach to trust management based on simple language for describing trust relationships and actions. It also narrates a prototype implementation of new trust system called as PolicyMaker which will make easier the development of security features in network services [4].
- Fuzzy Sets and Fuzzy logic
Xiaodong Sun et al. (2011) introduces trust management model which is based on fuzzy set theory and named as TMFC. This model is for cloud users who are making a decision to use services of providers by giving trust evaluation sets and building trust relationship [35].
- Service based Trust Evaluation
On the basis of existing methods, Zhi-Yong, Yu, et al. (2015) proposed a service trust evaluation method which is based on the weighted multi-attribute cloud. Time decay factor was introduced to show the timeliness of trust. This method can improve the success rate of service interaction was proven by experimental results [36]
Noor, Talal H., et al. (2013) presents an overview of cloud service models and surveys main techniques that support trust management of services in cloud environments. A generic framework is presented which assesses existing research prototypes and related areas [37].
Kantarci, Burak, and Hussein T. Mouftah (2014) have developed the model called Sensing as a Service (SaaS) that gives access to IoT. Trustworthy Sensing for Crowd Management (TSCM) is proposed, a cloud platform that confirms the presence of users who are willing to join by giving their data on social networks. Trustworthiness of users is updated by cloud [38].
- Other Methods for evaluation of trust
Chunxiao Li et al. (2012) proposed virtualization architecture to make sure a secure virtual machine (VM) environment under an untrusted OS. This includes secure runtime execution environment, secondary storage, and network interface. Implementation of runtime environment was done in Xen virtualization system. Using proposed architecture, even under an untrusted management OS, a trusted computing environment can be built for VM that needs top security level with minimal performance penalties [39].
Monir, Merrihan B., et al. (2015) presented current trust management techniques related to the performance of cloud providers considering aspects like security, privacy, user feedback, credibility, etc [40].
Sunyaev, Ali and Stephan Schneider (2013) mainly concentrates on how to address the lack of trust, acceptance, and transparency in cloud services [41].
Ko, Ryan KL, et al. (2011) talks about challenges and key issues for achieving trusted cloud through detective controls and presents TrustCloud that focuses accountability through policy-based and technical approaches [42].
In this paper, authors have mostly tried to focus on vital or prime trust, privacy and security issues in present existing cloud computing scenario. This also have helped users to identify real and unreal threats associated with their usage. These are the some issues that this paper have highlighted: (1) analyzing the method that may be used to remove these security, privacy, trust etc. issues and thus offering a reliable, trustworthy, safe cloud computing scenario; and (2) observing the issues related to trust, security that causes threats in existing CC environments[6].
A comparison of cloud computing is done with pervasive and service computing in this research paper. Till now all these computing models are actively studied by both research and industry people. They have built up a subjective comparison among them with the help of computer architecture model which has three features: storage, input/output and calculation. Finally comparison results are assessed and a series of questions have been put forward for future work [7].
For SaaS service providers, this paper presented a framework and model to fulfill customers by borrowing cloud resources from various IaaS service providers. By maximizing user satisfaction and minimizing cost, it proposed three inventive scheduling algorithms and admission control for making profit to maximum. It also shows effectiveness of proposed model through evaluation by changing provider and user side parameters to determine which solution is best in which condition [8].
For inter-cloud system, researchers have proposed a reputation-based trust system in distributed environment. Each cloud is able to make self-governing decision because of trust value location is at different levels of cloud for assurance of cloud. They have simulated the performance of the presented work. Excluding trust management, other attacks such as giving false ratings and some critical attacks can degrade the whole process [9].
A model is proposed in this paper to rank candidates in a favored election. This model is an extension to the recently presented model for ranking entities. It can be useful for both efficient and inefficient candidates by considering only few constraints. There are some techniques which are beneficial for decreasing complexity of model by acquiring some of the results through assessment [10].
A Cloud Sustainability Dashboard is proposed to examine and understand sustainability of cloud. This dashboard models and evaluates the overall effect of services which are organized by cloud. They utilize their approach to assess sustainability of open source CC environment i.e. Open Cirrus [11].
Researchers have presented an architecture for allocation of resources inside the cloud for market. For dealing with services they have also put forward the idea of creation of cloud exchange. Also some platforms have been discussed. Basically they have shown cloud efforts from market point of view for creation of another party to disclose developing potential for successful acceptance of CC [12].
A research paper was proposed where they have surveyed voting data according to ranking and its analysis was done with the help of Data Envelopment Analysis. They observed that existing systems have some faults so they have made correction to it. Calculation cost is the advantage of system [13].
Authors have given the outline of Cloud Computing (CC) describing what exactly CC is about and what are facilities provided by providers at current. From customer’s point of view, they have mentioned benefits and some threats that are associated with CC. They have also pointed out certain challenges regarding SLA, security etc. Trust is significant factor so based on trust some challenges are outlined [14].
Service Measurement Index, a framework has been developed by team globally. This framework consists of some measures that are useful for comparing non-cloud and cloud services. It includes various parameters that are tested and documented. 51 attributes are present in this paper [15].
Table 1 Summary of different papers regarding trust in cloud computing
| Sr. No. | Author Name | Year | Title | Cloud User Trust | Cloud Provider Trust | Model | Implementation Details | Parameters used by Authors |
| 1. | Noor Talal H., et al. | 2016 | CloudArmor: Supporting reputation-based trust management for cloud services | No | Yes | Credibility
Availability |
Each model is Tested against the collusion and Sybil attacks. | Robustness,
Accuracy |
| 2. | Lins Sebastian et. al | 2015 | Trust is Good, Control is Better: Creating Secure Clouds by Continuous Auditing | Yes | No | Continuous Auditing | Auditors are assigned. Accordingly auditors adjust their auditing reports. Trustworthiness of the provider is based on the auditing report. | Cloud Computing characteristic, Architecture changes,
Environment threats |
| 3. | Seol Jinho, et al. | 2015 | A trusted IaaS environment with hardware security module. | Yes | No | Threat Model | Provides an extra security layer for guest users to protect against attacks from malicious admin and a system architecture which gives following functionality :
Interface Isolation, Secure Connection, Secure Storage, Secure Management |
Security |
| 4. | Tan WenAn, et al. | 2014 | A trust service-oriented scheduling model for workflow applications in cloud computing. | No | Yes | Trust Service-Oriented workflow scheduling | Trust is calculated using trust metric consist of Direct trust and Recommendation trust.
According to direct and recommendation trust weight are assigned |
Reliability |
| 5. | Li Xiaoyong, et al | 2015 | Service operator-aware trust scheme for resource matchmaking across multiple clouds | No | Yes | Entropy based Adaptive trust evaluation module | The Real-time Trust Degree (RTD) is calculated. RTD is generated when user and system interacts. Weights are calculated based on the information entropy. | Service operators (CPU Frequency, memory size, network bandwidth etc.) |
| 6. | Barsoum Ayad, and Anwar Hasan. | 2013 | Enabling dynamic data and indirect mutual trust for cloud computing storage systems. | Yes | Yes | Each trusted user is given a key to access the encrypted data. For this purpose bENC, lazy revocation, key rotation encryption techniques are used. | Data integrity,
Data Access |
|
| 7. | Li Xiaoyong, and Junping Du. | 2013 | Adaptive and attribute-based trust model for service level agreement guarantee in cloud computing. | No | Yes | Adaptive Trust Management Model | Trust is calculated by user.
User records its own data accordingly decides whether the service provider is trust worthy or not. |
Data |
| 8. | Kantarci Burak, and Hussein T. Mouftah | 2014 | Trustworthy sensing for public safety in cloud-centric internet of things. | Yes | No | Trustworthy sensing for crowd management | Trustworthiness of user is calculated over sensed data it sent. Outlier detection algorithm is used to check whether data is altered if yes then trustworthiness of user is reduced | Sensed Data |
| 9. | Noor Talal H., et al | 2016 | Managing Trust in the Cloud: State of the Art and Research Challenges | No | Yes | Trust Managem-ent Analytical Framework | Mainly three modules:
1) Trust Feedback sharing: In this user give feedback about the service provider 2) Trust Assessment: System response to the quires of customers 3) Trust result Distribution |
Feedback data. |
Summary of Review Papers
This is the summary of various papers that have been taken for research work. This will help others to build their proposed solution for the future work. In one of the paper researchers have proposed the tinny application concept for customized applications. Due to this, organization can move towards cloud computing by saving cost and getting advantages of cloud computing. However many firms are not moving towards cloud due to the main issue which is Trust. One trust model is proposed by which users and providers both are transparent to each other. This is the reason for developing trust on both sides. A framework is proposed is some paper in which QoS metrics are defined to measure cloud services and Ranked Voting method is used to find best cloud provider. This paper have just given the framework model. The future work will be implementation of this framework. Now this one will be one of the challenges to execute the idea proposed in the paper.
A cloud-based storage scheme is developed that supports outsourcing of dynamic data, where user is capable of not only accessing and archiving data by provider but also scaling and updating data. Scheme ensures that users receive the most recent version of outsourced data. In case of any dispute, a Trusted Third Party recognizes the dishonest party. Investigation was done when overheads were added due to incorporating scheme for static data. Future work of one of the papers suggest that proposed system TSCM can be utilized in disaster management or malicious users may use crowdsourcing to confuse emergency forces. This increases community resilience against such situation. Also combination of TSCM with other trust models can increase its efficiency. So this can be used as one of the key point for further research work. A secure virtualization architecture was proposed in an untrusted management OS. Performance evaluation shows that overhead is due to building of domain, restoring and saving operations that occurs very rarely at very low frequency during life cycle of DomU. A slowdown of 1.06 percent remains every time. So this can be the future scope of area for researchers where this small slowdown can be eliminated. In one of the research paper, for trustworthy resource matchmaking across multiple clouds SOTS is proposed. Results shows that it works good in many cases. But there are some open issues that can be applied to this scheme. First of all we can integrate this scheme with reputation management to deal with user’s feedback issue. Secondly, assessing the security levels of resource can be another challenging direction. At last, we can evaluate the proposed scheme in larger scale multiple cloud environment. So all these can be a great help for authors to start their future work. Cloud-Trust is one model that gives very good results in many cases but there are some improvements and unresolved issues that can be applied to current model. Distributed data sharing and remote computing are main areas today so we can implement and evaluate this model on various cloud systems which can be done for further research. Another issue to be addressed in future research is how to motivate or encourage users to submit their feedback to trust engine.
In one of the research works T-broker system was proposed. They have mentioned some of the future aspects that will be useful for research. One of the aspect was how to perfectly calculate trust value of resources with only few monitored evidence reports and how to encourage users to submit feedbacks to trust measurement engine. Other aspect was to implement system on multiple cloud system. One paper suggests that further work should concentrate on auditing methodologies related to cloud computing context mainly focusing on cloud service characteristics. Also one should find out how uniquely CC characteristics influence auditing. Then methodologies need to be implemented to prove their economic applicability in CC environments.
Chapter 3- METHODOLOGY
3.1 Gaps identified from existing systems
In cloud computing condition, just when the security and unwavering quality of both parties are guaranteed, information security can be adequately ensured amid communications amongst clients and the Cloud. In this way, assembling a shared trust connection amongst clients and cloud stage is the way to execute new sorts of get to control technique in cloud computing condition.
3.2 Ranking of Cloud Service Providers
Ranked voting method is used in this work for finding a best service provider. In this technique, voter ranks alternatives by the order of preference. For finding an efficient provider, there is a big list of parameters or metrics. So cloud providers will be candidates for them and each metric will be voter. Hence this is the preparation of ranked voting data set. A lot of research work is done to analyze ranked voting data. One of them is DEA (Data Envelopment Analysis). But DEA results into more than one efficient candidate. Few techniques are proposed to eliminate these candidates. Due to this, order of preference can be changed because of presence of inefficient candidate. A naïve method has been introduced by Hiroaki Ishii and Tsuneshi Obata that does not use information related to inefficient candidate to eliminate efficient candidate which is given by DEA. Therefore, the same method is considered by proposed work to identify best provider for customer.
3.3 Idea of the System
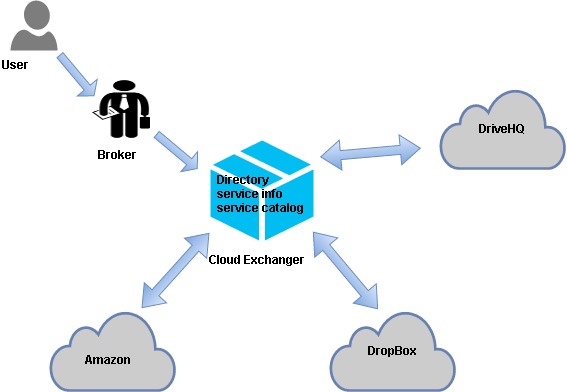
Figure 6. Overview of the system
3.3 Proposed Solution
Proposed model take both user’s behavior trust and best cloud services into consideration. Mutual trust between users and cloud service nodes are ensured through trust mechanism. Only trusted users have access to the Cloud, and simultaneously users can select the most credible cloud service. Finally, a trust based access control model is proposed. This model not only considers user’s behavior trust and ensure that user’s access request poses no malicious threat to cloud server, it also takes cloud service credibility into account.
The proposed work adopted Ranked Voting system to formulate best provider selection problem and developed a flexible framework for selection of a best provider which can be used for different applications with different QoS requirement. User can make their own voter list as per its requirement. A set of rules is defined to compare QoS values even though they may be of different value types. Depending upon the requirements, broker will calculate best cloud for user.
 Architecture:
Architecture:
Figure 7. Conceptual View of proposed framework
Modules:
- Broker
- Cloud Exchanger
- Service Provider
Broker:
Cloud broker takes details of requirement of user and details of service provider from directory and analyze them using proposed framework in order to choose a best provider.
Cloud Exchanger:
User, cloud providers, broker and cloud coordinator are brought together by a central coordinator called as Cloud Exchanger. It contains directory to provide information to broker about Cloud services.
Service Provider:
Service log and catalogue both are provided by service provider. It also updates both periodically.
To select the best cloud service provider the broker will consider the QoS metrics such as the average rating, average capacity and finally calculate the rank of the service providers. Based on the result the broker will send the best cloud service provider to the user. To maintain the two way trust authentication the selected cloud Service provider will authenticate the user by sending an encrypted content and the corresponding secret key to decrypt the content. If the user is authorized he/she will get the encrypted content and the secret key to his attached email id to the application. Once the user got the encrypted content and the key he has to decrypt the content and the send the decrypted data to the corresponding cloud service provider if the data sent by the user is matching the data which is sent by the cloud service provider then the cloud service provider will accept the request from the user and stores his file in the cloud.
Algorithm:
- Calculate average capacity
Average Capacity=C1+C2+…+Cnn
Where C1, C2, Cn are capacities of the cloud provider
N is number of cloud provider’s instances
- Calculate average cost
Average Cost=c1+c2+…+cnn
Where c1, c2, cn are cost of the cloud provider
N is number of cloud provider’s instances
- Calculate average rating and calculate ranks for the cloud provider.
Ranks of the cloud provider can be calculated using below formula
Ranking=Average Rating*Average Cost
- Calculate the best cloud based on ranks.
“Lower the ranking best is the cloud provider”.
- Upload files to secured cloud
- Authenticate user by sending encrypted content and secret key.
3.4 System Requirements
Hardware requirement:
- System: Intel(R) Core (TM) i5 CPU 1.70GHz (64-bit operating system)
- Hard Disk: 40 GB
- RAM: 512 Mb
Software requirement:
- Windows 2010
- Java/J2EEE
- Eclipse Luna
Chapter 4- RESULTS
The clouds which are considered in this paper are: Amazon, Drivehq and Dropbox. Broker calculates best cloud for user by calculating rating and cost. In cloud exchanger, you can view the directory. Then user gives its requirements by filling catalog form which correspond to respective clouds. Various parameters are present like cost, capacity, OS which user can give according to his preference. After signing in, browse any text file to be uploaded. Then request will go to broker and it will calculate best cloud and sends back to user. Now cloud will authenticate user by sending him encrypted content and key to corresponding email. If it matches, then cloud will accept the request from user.
Figure 8. Broker
Figure 9. Cloud Exchanger
Figure 10. Amazon
Figure 11. Drive HQ
Figure 12. Dropbox
Figure 13. Sign in
Figure 14. Register Form
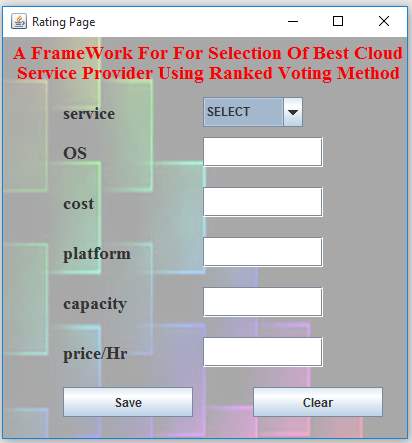
Figure 15. User Requirements Form
Figure 3 depicts that system takes requirements from user by considering parameters like type of service, operating system, cost, platform, capacity, price per hour. These requirements are then send to broker for further process.
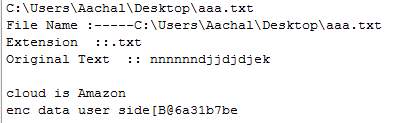
Figure 16. Best Cloud as Output
Figure 4 shows the result as best cloud obtained after the entire process is completed. As we can see here it is showing Amazon as best cloud provider after we have uploaded text file.
Figure 17. Feedback
Analysis:
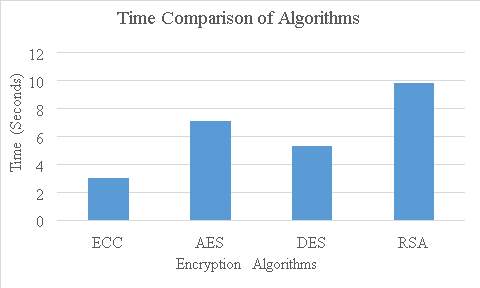
Figure 18. Encryption Algorithm Comparison
The above chart shows the time taken by the various encryption algorithm to encrypt text file. Here we had used ECC algorithm. Above graph shows that ECC takes less time than any other encryption algorithm.
Chapter 5- CONCLUSION AND FUTURE WORK
Cloud computing offers resources on the basis of pay per use. This has led to increase in the number of customers who use cloud services which in turn has increased the growth of CC market .So a big confusion is created for the selection of best service provider as the various providers are available in the market. Proposed work gives the solution to this problem in an efficient manner. User just have to give its requirements and this framework will automatically find and provide best provider to user. User don’t have to look in market to find different offers and compare it. This also helps providers to be visible in CC environment.
Future work will be to combine novel trust management techniques such as recommendation with this system to enhance system’s performance. Another focus of research work will be on performance optimization.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Computing"
Computing is a term that describes the use of computers to process information. Key aspects of Computing are hardware, software, and processing through algorithms.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




