Human Factor and Countermeasures in Small and Medium Enterprise (SME)
Info: 10092 words (40 pages) Dissertation
Published: 9th Dec 2019
Tagged: Business
Human factor and countermeasures in Small and Medium Enterprise (SME)
1.2 Description of the case company
2 RESEARCH QUESTIONS AND METHODOLOGY
3.1 What is Information Security?
3.3 Conventional Threats vs Internal Threats
3.4 Small and medium enterprise information security
3.5 End user security behavior
3.6 End user countermeasures perception
4.1 Internal threat within DeltaGric
4.3 Relations between countermeasures and security behavior
5.2 The case company IT infrastructure
5.3 Interviews / Analysis of questionnaire
5.4 Observation / Summary on the results of data collection
6.2 Information system security regulations
6.3 Training awareness and reinforcement
6.4 Formal process of reward and deterrence
6.6 Identification, Authentication, and Access Control
6.6.1 Identification and Authentication
SYMBOLS AND ABBREVIATIONS
ISRB IS Security Risk-Taking Behavior
IS Information Security
SME Small and Medium Enterprise
IA Information Assurance
SAP
OSS Open Source Software
ERP Enterprise Resource Planning
IT Information Technology
ISO Information Security Officer
E-mail Electronic Mail
NHIS National Health Insurance Scheme
IDPS Intrusion Detection and Prevention Systems
1 INTRODUCTION
The background and motivation of this research are presented in this chapter. In addition, the brief description of the case company is discussed. Further, the research objectives are described
1.1 Background and Motivation
In recent times, it is very rare to find people who will disagree about the fact that information technology is pivotal to the way businesses are run today. In the digital information age which we now live in, organizations are seeking to use automation by way of Information Technology to process information to better serve their customers and support their missions, goals, and objectives. Unfortunately, not everyone wants to use this advancement for the greater good. Some persons have different motivations that are not in keeping with the use of Information Technology within the confines of proper ethical and sometimes even legal conduct. So, even though the use of IT offers so many advantages to organizations, there are numerous inherent risks that must be mitigated to successfully use IT as an extender or enhancer of services.
Information assets, knowledge assets, and information capital all provide value to organizations (Berzkalne, & Zelgalve, 2014). Information is one of the most valuable assets of an organization (Van Niekerk & Von Solms, 2010) therefore, security of such asset is important to every organisation. The technical parts of information security (hereinafter IS) have been in the spotlight for quite a while; this has also gained spotlight attention over the past decade, but the attention has focused more on the external threat forgetting that the breach by an insider who can be a former or current employee, business partner, or a client can even be more damaging to their information asset. Statistics to internal threat has been all but pleasant to many organisations, in 2016 Cyber Security Intelligence Index (CSI), IBM discovered that 60% of all attacks were carried out by insiders. Of these attacks, three-quarters involved malicious intent, and one-quarter involved inadvertent actors. Price water cooper (PwC 2014) also noted that about one-third (32%) of respondents to PwC’s 2014 US State of Cybercrime Survey said insider crimes are costlier or damaging than those committed by external adversaries, yet less than half (49%) say they have implemented a plan to deal with internal threats. Furthermore, Africa’s two largest economies, South Africa, and Nigeria, are estimated to be losing $5130m annually due to data breach (McAfee 2016), and the rate of data breaches in south Africa increased by 15% in the first half of 2016 (Gemalto’s breach level Index 2016).
By and large, hardware and software cannot be secured alone by just upgrades and/or running patches as there could be a myriad of other issues that could affect the integrity of software or hardware components e.g. O-day vulnerabilities, misconfiguration as well as peculiar open source vulnerabilities. Internal threat to information security cannot be limited to malicious insiders (employee, ex-employee, client, or partner) who wishes to steal organisation information for personal gains but also includes employee ignorance, employee carelessness, and error. As prevention techniques also get advanced, hackers are becoming more innovative with the way they conduct their attack. The last decade has seen a shift in traditional hacking methodology from software or hardware hacks to newer and innovative ways of exploiting the vulnerabilities that come because of being human, new methods of using phishing or vishing, social engineering by deception and exploiting the naivety or trust of human beings are now being added to the attack methodology, making hacking more lethal and by extension, its consequences graver for organizations and/or individuals that fall prey. Therefore, it stands to a reason that organizations need to protect their information resources (Okere, van Niekerk, & Carroll, 2012).
Furthermore, IS has become a top interest and of the utmost importance for everyday consumers and businesses, with the widespread incidence of data breaches via the internet and via internal ways i.e. social engineering, phishing, etc. Small and medium scale enterprises (hereinafter SME) must comprehend the significance of data security and find the means to protect the privacy of their respective organizations, staffs, and clients not only from the technical parts of information security threats but also from a neglected internal threat such as social engineering. Therefore, this research will be undertaken to explore internal information security threats SME’s face and proffer countermeasures, particularly in the case company.
The research is commissioned by Tunde Ogunkoya, the case company will find this research work useful in terms of recommendations and consultation on the potential threat to their organization.
1.2 Description of the case company
This section presents the background of the case company. Furthermore, the current business challenges of the case company are discussed.
DeltaGRiC is a leading Applications Security consultant, whose aim is to help African businesses running of Open Source Applications, SAP, and PeopleSoft Enterprise applications to mitigate cyber-security risks and compliance violation.
DeltaGRiC’s niche proposition is SAP Vulnerability Assessment & Penetration Testing plus SAP Forensics and Open Source Vulnerability Assessment.
DeltaGRiC focuses on 3 major aspects:
- Applications Consulting: Assist organizations to choose and implement the type of software they need to automate their business-critical processes based on their budget, business needs or requirements as well as their technological landscape/technological roadmap.
- Open Source Software Compositional Analysis (to cater to three things in software build)
- Security Risk mitigation,
- Legal Risk Mitigation because of the OSS license in use,
- Operational Risk Management because of the age of the OSS component in use, Number of commit and number of contribution)
- The third thing we do is to manage Security risks on Tier 1 Applications like SAP and Oracle (Vulnerability Assessment and Penetration testing). (Tunde 2017a)
1.3 Research objectives
The main objective of this research work is to analyze the internal security threats in the case company and to propose recommendations on how to tackle them. Furthermore, it will also look at the human factor within internal information security chain which is most times giving less attention unlike the external threat and proffer countermeasures in mitigating internal threats in SME’s.
1.4 Structure of thesis
The thesis will be divided into six chapters. Chapter 1, Introduction to the research work, the case company and the research objectives will be talked about. In Chapter 2, the research scope and the research questions will be discussed. In addition, Chapter 2 discusses and provides arguments for the research methodology. Subsequently, Chapter 3 presents the theoretical framework developed based on literature review to answer the research questions. Chapter 4 is devoted to analyzing the empirical data from the interviews and the questionnaire to understand the company’s perception of internal threat. In Chapter 5, contains data analysis for case study based on the theoretical framework and empirical data. And Finally, Chapter 6 concludes this research, discusses the results of this work, and suggests directions for further research.
2 RESEARCH QUESTIONS AND METHODOLOGY
This chapter focuses on the research questions and research methodologies. Four research questions are discussed to accomplish the objectives of the research work. Finally, the research methods used in this research work is presented.
2.1 Research Questions
Four research questions are presented and described to achieve the objectives of this research work. The research questions are as follows:
- How do current security practices and employees’ behavior affect the internal security of the case company?
Employees’ run the day to day activity of a company, therefore this research question will help to understand how security practices and employee behavior affect the internal security of the case company.
- What kind of security management practices should be developed to improve the internal security in the case company?
This research would analyze the business scenario and the current security management practices been used by the case company. The findings will therefore be used to proffer new security management practices or update the current existing on to the current day best practices.
- What kind of employee training on security does the case company need to implement?
In other to protect the organization from any form of breach, it is important for the organization to have in place a proper security awareness initiative which is not limited to classroom style training sessions, security awareness website(s), helpful hints via e-mail, or even posters. These methods can help ensure employees have a solid understanding of company security policy, procedure, and best practices.
- How can ICT solutions assist in implementing the security measures?
This research question aims to show the importance of ICT in implementing security measures in the case company.
2.2 Research Methodology
The purpose of this research is to identify internal information security threats SME’s face and proffer countermeasures to help minimize or stop the threats,
we choose to use a mixed research method because we need to get information from the human point of view and use external experience on IT security topics and this could be done by reading literature related to our study.
If we use only a questionnaire, we would only obtain knowledge about human behavior and their risks but we will not obtain knowledge about up-to-date information on current threats and best methods to reduce this risk, only by using this mixed method we can identify potentially dangerous behavior in users from the user observation process and identify this behavior in recommendations from other authors in prominent literature.
3 INFORMATION SECURITY
This chaptercontains literature review about information security, information security within SME, internal threat, countermeasures, and human perception behavior. Various research paper reviews and analyses show the importance of internal threat within SME and the relations between countermeasures for internal risk minimization or mitigation and human perceptionand behavior.
3.1 What is Information Security?
Information security is the control of information asset and resources from unauthorized access, disclosure, modification, destruction, or disruption. Moreover, information security is defined as the preservation of confidentiality, integrity, and availability of information as well as the inclusion of other properties such as authenticity, accountability, denial, and reliability (ISO/IEC, 17799: 2005). Furthermore, Whitman and Mattord 2008 defined information security as the protection of information and its critical elements, including the systems and hardware that use, store, and transmit that information (Whitman and Mattord 2008). In other for an organization to adequately protect its information assets, employees, and operations the organization as to put in place multiple layers of security which includes physical, operational, information etc. and all this work hand in hand in case of a breach from one sector or the security chain in the protection of the organization assets.
3.2 The CIA TRIAD
There are various explanation of information security models and the oldest or most recognized one is the CIA triad or CIA triangle which is used for IA (Information Assurance). (Gibson, 2011; Andress 2011, 2014; Corey, 2015). The CIA triad consists of confidentiality, integrity, and availability, and it is designed to guide information security policies within an organization.
Confidentiality
Information
Security
Integrity Availability
Figure 1 CIA TRIAD
3.2.1 Confidentiality
Confidentiality is the ability to hide information from unauthorized personnel. Haughn, & Gibilisco, 2014 defined confidentiality as a set rule that limits people’s access to information. It is feasibly the most obvious part of the CIA triad with regards to security; but correspondingly, confidentiality is the most attacked of the CIA triad and it is vulnerable to various types of attacks; some been snooping and traffic analysis. Snooping basically means the unauthorized access to or interception of vital information. This can happen when a file containing confidential information is been transmitted via e-mail. While traffic analysis ensures that certain information can be gotten through the observing of online traffic which can reveal the sender or receiver e-mail address and nature of transaction can also be deduced (Forouzan, 2014: 417). In ensuring confidentiality cryptography and encryption methods are an example of an attempt to ensure data transferred from one computer to another are done privately.
3.2.2 Integrity
Integrity is the ability to prevent data from being changed in an unauthorized manner. Andress, 2011. The integrity of information is vulnerable to modification, masquerading, replaying, and repudiation. (Forouzan, 2014: 418). The breach of the integrity of a file is noticeable when unauthorized changes is detected either in its size or by means of the file’s hash value. (A hash value is the use of a specific algorithm that evaluates the bit in the file and calculates a single representative number called a hash value). The file can be said to have been compromised if the hashing algorithm varies from the original hash value (Whiteman & Mattord, 2008:7). Information is a very important part of any organization or an individual therefore security of its integrity is of utmost importance. I.e. the case of the recent ransomware hack of the NHIS in the United Kingdom, if by chance a patient’s medical report has been altered then the wrong treatment maybe prescribed to such person, thus causing a potential fatal outcome. Furthermore, it is important for organizations or individuals to always have backup for their documents to allow them quick recovery when a data breach or loss has occurred. In addition, integrity of a document or file is kept in place when backup as been made. Corey (2015).
3.2.3 Availability
It is important to ensure that the information concerned is readily accessible to the authorized viewer always. White & Mattord, (2008) defines availability as access to information which is unobstructed, uninhibited and in a functional format. Denial of service (DoS) attack is an example of attack that leads to the unavailability of a website, this happens when large amount of traffic is sent to it causing it to crash (Minnaar, 2014: 133).
3.3 Conventional Threats vs Internal Threats
Conventional security threats are does intended to attack security vulnerabilities in organization’s devices which are connected to the outside world via the internet, devices if where or are properly configured and kept up to date are safe.
Figure 2 shows examples of conventional security threats.
Denial of service(DoS)
Buffer overflow attacks
Identity theft
Eavesdropping
IP Spoofing
Conventional Threats
Figure 2
Internal threats or insider threat as become more popular after the popular case of Edward Snowden and it has become a major source of concern for many organizations in protecting their information asset from the insider threat as many of the organizations as focused more on dealing with the external threat. SEI-CERT (2012) defines internal threat as a malicious insider threat who is a current or former employee, contractor, or other business partner who has or had access to the organizations network, system or data and they intentionally or non-intentionally misuse their access and causes breach to the organizations confidentiality, integrity, and availability. Internal threat can be categorized into three types the Negligent insider (The employee who has erroneously exposed organization information), The Malicious insider (The disgruntled employee who has intentionally exposed organization information), and the compromised Insider (The employee whose access credentials have been compromised by an attacker). Internal threats can affect all types of organizations large or small firms and it can cause significant damage to the affected organization. Silowash et al (2012).
Many SMEs have failed to acknowledge that the threat of an attack from the inside is real and substantial as many still employ based on trust in case of the case company and no proper policies in place to checkmate such threats. In 2011 a Cybersecurity Watch Survey was conducted by the U.S. Secret Service, the CERT Insider Threat Center, CSO Magazine, and Deloitte, and they found that in cases where respondents could identify the perpetrator of an electronic
crime, 21% were committed by insiders (SEI 2011). In addition, 43% of respondents had experienced at least one malicious, deliberate insider incident in the previous year. The survey also revealed that 46% of the respondents thought that damage caused by insider attacks was more severe than damage from outsider attacks. Researchers have various opinion on what is considered as internal threat, some see internal threat as a malicious internet content, others see it as the attack of physical network i.e. server rooms, network points etc. most common crimes by insiders where unauthorized access to or use of corporate information, unintentional exposure of private or sensitive data, virus worms, or other malicious code, and theft of intellectual property (IP). (SEI 2011). Dhillion,2001 also found out in his research that majority of breaches come from the insider that have subverted internal countermeasures. Some examples of internal threat attacks are shown below in figure 3
Fraud
Social Engineering
Spyware
Hardware Theft
Ransomware
Internal Threats
Figure 3
3.4 Small and medium enterprise information security
SMEs are susceptible to attacks, some SMEs do not pay the proper attention to this threat and some do not recognize the severity of this threats. SME is a major contributor to economic growth and development around the world, in South Africa SMEs make up about 91% of formalized businesses and provides roughly 34% of GDP (The banking association South Africa). Nevertheless, due to the advantages of IT, SMEs have been adopting the use of IT applications to support their businesses, but the formulation of information security management practices are primarily developed for bigger enterprises leaving out SMEs and making them prone to attack.
Ironically, the unique nature in which SMEs do their business as kept them out of the information security management approach creation and warranted customized approaches for various SMEs. Furthermore, Many SME’s have been on the reactive side rather than been proactive when it comes to information security, a survey by Ernst & Young 2014, states that 53% of organizations claim that one of the main causes of difficulty in information security is lack of experience and capable resources. Chavis, Klapper, and Love (2010) also states that finance is one of the major constraints of SMEs.
Tawileh et al (2007) state that human factor presence complicates information security issues even more. But Gupta & Hammond (2005) thinks that disgruntled employee could be even the source of attack against information assets, they notice that limited financial resources and expertise within SME can lead to lack of policies and procedures within the organization and that can raise the risk of insider attacks.
Some researchers review efficiency of information security countermeasures within SME, one of the Gupta & Hammond (2005) major findings was that SME quite often chooses to use technologies for security risk minimization that are not very effective for their environment, therefore could cause even more serious risks. This finding also shows the main problem area of this thesis.
3.5 End user security behavior
Information security is a major concern for SMEs, yet the responsibility of employees in maintaining information security is frequently neglected.
Various research scholars and information security practitioners have expressed concern over employees’ IS security behavior (ISRB) (D’Arcy et al. 2014, Guo et al. 2011, Willison & Warkentin 2013).
Internal security breach most times will not be possible if employee security behavior is top notch, therefore, it is important to understand what influences employee security behavior.
Employees can negatively affect information security intentionally or unintentionally. (Tunde, 2017b) Behavioral studies regarding IS security has been emphasized in recent years (D’Arcy et al. 2009, Mishra & Dhillon 2006, Puhakainen & Siponen 2010, Siponen & Vance 2010, Vroom & von Solms 2004). The three main IS issues that came up in all their researches in the context of an organization included: security awareness (training/education), IS misuse/abuse, and security policy compliance.
Various studies have focused on the individual in other to identify the factors that motivate their security behavior i.e. intentions and attitudes.
Sommestad et al. (2014). focus on the individual to identify that beliefs (perceived behavioral control, threat appraisal, descriptive norm, response efficacy) and values (perceived value congruence, perceived legitimacy, information security awareness), play a critical role for user compliance with security policies. They also suggest that rewards and punishments are poor predictors of compliance.
Lebek et al. (2014) through a literature review, found that the constructs of Theory of Reasoned Action (TRA)/Theory of Planned Behavior (TPB) are good predictors of the intention to comply with the ISP. They also found that organizational commitment, perceived effectiveness of the employee’s actions and technology awareness can also influence users’ intention to comply.
To oversee internal security threat, we must understand how organizations practices can influence employee behavior. The factors that influence employee behavior is divided into two groups. Understanding what the organization expects from them is in the first group while the second group consists of factors influencing employee willingness to behave within the accepted organizational norms. Leach (2003)
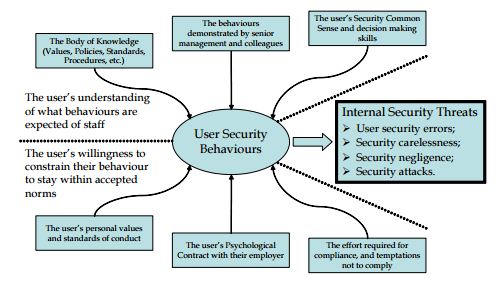
Figure 4 Factors influencing user security behavior. Adopted from Leach (2003)
3.6 End user countermeasures perception
4 HUMAN FACTOR IN INFORMATION SECURITY
4.1 Internal threat within DeltaGric
After evaluation of various literature’s, and interaction with the thesis commissioner the following attributes were identified within the case company’s information security:
- Employees lack knowledge of insider threats and risks
- The company has limited resources in place to manage security
- Priority is placed on other subjects rather than the information asset of the company
- Lack of understanding of the grave danger insider threat poses
- No confidentiality policy in place, rather they act on employee psychological test to determine their loyalty.
4.2 Human factor
Humans are a very important aspect of information security in every organization in developing and deploying, establishing, and enforcing effective security policies and procedures. The human factor can be of positive or negative effect to the security of information assets in an organization. Humans have constantly been tagged as the weakest link in information security. The human factor in information security system is any breach caused by an intentional or non-intentional act of an employee to disclosing organization information to some unauthorized personnel. Internal threat to a business is the human element (Node4, 2016). Hackers go from small to win big, larger organizations are sometimes hard to penetrate by hacker’s due to their considerable investment in information security and employee education but their partnership with SME organizations who have not given the best attention to information security and employee awareness to information security makes them also prone to attacks or data theft.
In 2014 95% of all security incidents involved human error (IBM 2014), 65% of human error was recorded by Node4 (Node4 research, 2016) and in a similar survey in 2016, 35% of current employees are the source of security incidents in organizations (PwC, 2016).
The human factor is one of the most significant vulnerabilities in organizations yet it is the most ignored, many SMEs think the protection of their confidentiality, integrity and availability assets lie solely on the protection of their technical aspects and paying less attention to managing the human element of the organization. Additionally, it is difficult to design an effective information security policy without first understanding the reason for compliance and non-compliance of information security polices by employees.
4.3 Relations between countermeasures and security behavior
Due to the findings from the literature review in answering the research questions, the following was detected in the relationship between internal threats, human factor, employee security behavior and countermeasures.
To reduce the internal threat, various security countermeasures are being implemented and maintained but the way employees understand these countermeasures influences their behavior is not always clear.
Figure 5 below shows the relationship between security behavior, human factor, internal threat, and countermeasures.
Information security internal threat


Information security countermeasure

Human Factor
Security Behavior

Figure 5: Relationship between security behavior, human factor, internal threat, and countermeasures.
5 EMPIRICAL DATA
The framework for this chapter is derived from the literature review from above. The literature helped to understand the problem and guided data gathering and analysis. The framework describes two variables and how they are related. End user countermeasure perception and information security countermeasures to minimize or mitigate internal threats. The relation between these two variables will be used to answer the research questions.
So, this research was carried out in two phases: in the first phase, information
countermeasures were identified and analyzed. In the second phase, the human perception of those countermeasures was analyzed. The theoretical framework shows that there are various countermeasures that influence user information security behavior and further empirical study should be performed to prove the negative/positive influence.
5.1 CASE STUDY
DeltaGRiC is an Applications Security consultant company, whose aim is to help African businesses running of Open Source Applications, SAP, and PeopleSoft Enterprise applications to mitigate cyber-security risks and compliance violation. DeltaGRiC’s niche proposition is SAP Vulnerability Assessment & Penetration Testing plus SAP Forensics and Open Source Vulnerability Assessment. The organization is based in Sandton South Africa, with over 50 employees with 15 of them with the IT department and one person assigned to the responsibility of information security.
DeltaGric has not officially recorded any malicious information security incident performed by an insider in their organization. However, there have been few employee errors that could have put the organization in a vulnerable state but due to prompt and continuous testing, it was been discovered. (Tunde, 2017)
5.2 The case company IT infrastructure
The case company DeltaGRiC – Sandton South Africa has its own enterprise resource planning (hereinafter ERP) system. The ERP system was adopted by the case company as a business management software, because It is easy to use and highly effective software to fulfil the business demand for the company. (Tunde 2017c*)
The case company operate a hybrid Infrastructure environment where some solutions are deployed in the cloud and some hosted internally in our in-house data center. e.g. our Moodle LMS platform is hosted internally.
The ERP – Odoo is hosted on the Odoo cloud by a Tier 4 cloud datacenter provider. The mobile device management solution of the case company is hosted on a cloud service provided by google and the antivirus/antimalware systems are deployed on individual machines which in turn is synchronized with the management center server within the in-house server.
5.3 Interviews / Analysis of questionnaire
In-depth qualitative interviews were conducted in this research in other to obtain and truly investigate the interviewee’s perspective and viewpoints about the research topic. The interview procedure was semi-structured in style to keep the interview open-ended and allow the interviewee the freedom of expression. The interview was conducted in two divides, one was a skype interview with the head of the IT department since he has an extensive and broad knowledge of IT infrastructure as well as business processes in the case company and second was an email interview with member of the staff of the case company. The transcripts of the interviews are displayed in Appendix 1 and Appendix 2 respectively. The following sub-sections discusses the main point of the interviews.
5.4 Observation / Summary on the results of data collection
The results of the interviews and questionnaire helped us to understand more on the case company, their perception on how the information security of the organization is been managed. It was seen that the case company did not have proper policies (i.e. confidentiality policy, security policy, etc.) in place to checkmate internal threats within the organization. Thus, information security policy can be adopted by the case company to help employees understand the do’s and don’ts of the company.
6 Countermeasures
As an SME, it is important to curve out countermeasures that is compatible with the organization and the countermeasure approach should be ISO/IEC 27001 compliance to enable a smooth running of the organization. In curving out countermeasures to protecting DeltaGRiC’s assets from internal attacks it is important to identify and classify what the assets are and what control measures are currently in place to protect those assets. The company assets and current control measures in the case company have been identified in the chapter 4.1 and after careful observation, we propose the following solutions in no order as countermeasures to mitigating internal threat within the case company and other SME organizations.
6.1 Confidentiality agreement
A confidentiality agreement is one of the important measures of mitigating internal threats posed by employees in SMEs. DeltaGRiC currently does not have a confidentiality agreement in place at the time of this research work. Current members of staff have been employed based on self-recognition and culture breed (Tunde, 2017) which is not a safe for the organization.
DeltaGRiC should have a confidentiality agreement in place, current employees, outsourced employees, and future employees should be given this contracts at the time of employment. The agreement will describe what type of information is considered confidential and what the consequences of violating such agreement is/are. The document can be a single page document which is readable, clear and important areas are pointed out.
6.2 Information system security regulations
An information system security regulation/ policy should be created according to the south African legislation requirements, which should include management, operational, Technical policies, and all other acceptable use of DeltaGRiC’s assets. This document must be giving to all employees, who must acknowledge they have read, understood, and will comply with it the set rules.
The document should contain the following to help minimize and mitigate against internal threat:
DeltaGRiC staffs must respect the confidentiality and integrity of any of the organizations information system, be familiar with the information-system security policies and procedures, and report any security weaknesses or breaches in DeltaGRiC’s information systems to their direct superior or head of IT department.
Members of staff shall respect security controls for DeltaGRiC information systems and not attempt to or circumvent those controls. Staffs shall not access or attempt to access any company information system without authorization from CSO. Users shall refrain from activities that intentionally or inadvertently disrupt, impair, or undermine the performance of DeltaGRiC information systems. These activities include the following, but are not limited to it:
- Intentionally causing physical or logical damage to a DeltaGRiC owned information system or resource
- Downloading computer viruses or malware or otherwise introducing malicious code into a DeltaGRiC information system
- Using Internet-based proxy servers or anonymizers, or any other tool, device or action that makes Internet activity untraceable, to bypass Web-filtering security mechanisms established on DeltaGRiC information systems;
- Downloading, installing, or running security programs or utilities that reveal weaknesses in the security of a DeltaGRiC information system, including but not limited to password cracking programs, network reconnaissance and discovery applications, key loggers, packet sniffers, network mapping tools, and port scanners, without prior approval from CSO; or
- Consuming excessive bandwidth through actions including but not limited to placing a program in an endless loop, printing excessive amounts of paper, and sending chain letters and unsolicited mass emails. Files and other content downloaded from the Internet, including but not limited to non-standard shareware, free software, peer-to-peer software, and information-sharing software, is subject to prior approval from CSO in writing. This approval may be conditioned upon CSO checking the downloaded files or content for viruses, trojans, malware, or other potentially malicious content. Users shall refrain from divulging to unauthorized persons any details regarding DeltaGRiC information systems or architecture unless previously authorized. The use of passwords to access DeltaGRiC information systems and DeltaGRiC-approved mobile communications devices is for the protection of the company, and not any user. Users shall take reasonable steps to prevent the disclosure of their usernames, passwords, security tokens, or other similar information to unauthorized users. Users shall not use cloud or Internet-based hosting services to store or share DeltaGRiC data unless specifically approved by CSO, and acquired through terms that include the requirement for compliance with security standards in south Africa.
- Users shall take all steps necessary to completely logoff or other termination procedures when finished using any DeltaGRiC information system. At a minimum, users should take such steps to logoff of terminate from a DeltaGRiC Information system at the end or every workday.
- Users of DeltaGRiC-approved mobile communications devices shall ensure that precautions are taken to prevent theft or loss. Unattended DeltaGRiC mobile communications devices shall be physically secured (e.g., locked in an office, desk drawer or filing cabinet; attached to a desk or cabinet by a cable lock system) when unattended. Any user must immediately report to CSO any loss or theft of any mobile communications device containing any information from DeltaGRiC information system.
- Users shall not connect personally-owned, or other non-company owned, equipment or devices, including, but not limited to, USB or other storage or memory devices, iPads or iPods, PDAs, tablets, BlackBerry devices, mobile phones, or cameras, to the company network infrastructure in any manner without proper approval. These devices should not be connected to DeltaGRiC’s systems for purposes of charging power, transferring personal audio, video, or images as non-company owned electronic devices may introduce unnecessary risk to DeltaGRiC’s systems and data. Remote access to DeltaGRiC’s information systems using a personally-owned fixed device or mobile communications device shall only be permissible through CSO provided and supported remote access software applications, protocols, delivery mechanisms, and if necessary, CSO provided and supported anti-virus software.
- Users with remote access shall ensure that their personally-owned fixed device or mobile communication device remotely connected to a DeltaGRiC information system is only connected to legitimately secure networks, such as a personally-owned home network under complete control of the user, or a validated provider network, and that their fixed device or mobile communications device maintains basic security controls (e.g., password protection) to prevent unauthorized access to all DeltaGRiC information systems. The method of storing information on a personally-owned fixed device or mobile communications device shall comply with DIT information-system security requirements. Users shall immediately report the loss of any personally-owned fixed device or mobile communications device used to access County information systems to DIT. In the event of a lost or stolen device, DeltaGRiC reserves the right to clear its data from the device by any available technical means.
6.3 Training awareness and reinforcement
As agreed by the commissioner of this research work, the full-time employee is trained by DeltaGric and the outsourced employees by their employee which could cause an internal threat within the organization due to lack of cooperation. Therefore, an information security awareness and training program should be incorporated as part of the DeltaGRiC’s training and education programs for employees and third-party users of the organization’s network on issues related to vulnerabilities and cyber-security breach risks associated with information technology, and the importance and methods of protecting company information and information systems. Security awareness should be continually emphasized, reinforced, updated, and validated. The ISO should develop and maintain a communications process for notifying users of new information system security related issues and concerns specific to the organization and of general interest. ISO should always make sure that new staff or users of their network participate in an approved Information Technology and Information Security Awareness orientation training class within 90 days of being granted access to any DeltaGRiC information systems. Members of staff and third-party agents should get proper training and be made to sign acknowledgment letter indicating they have read and understood the organization’s security policies
6.4 Formal process of reward and deterrence
Process of reward is a motivational way of keeping employees happy, diligent to their work and loyal to the organization, while deterrence will keep employees in check in cases of negligence to company policies. Therefore, DeltaGRiC should have a formal reward process that evaluates employees, though the reward process does not evaluate information security behavior, but only overall employee work performance. DeltaGRiC should also implement methods of detecting unacceptable behavior and should have a well-established process of investigation and punishment. After proper investigation, depending on the gravity of the offense the employee found wanting can be reprimanded or even fired. The process and the result of unacceptable behavior are visible for other employees so it also serves as a preventive mechanism.
6.5 Security policy
Today, one of the biggest challenges organizations face when trying to protect themselves from both internal and external threats is the little or no existence of security policy. Security is an integral part of information security, and in case of DeltaGRiC it has failed to put down a writing policy which defines what their sensitive information is, who can have access to it and under what circumstances can these assets be accessed by a member of staff.
6.6 Identification, Authentication, and Access Control
6.6.1 Identification and Authentication
DeltaGric information systems should enforce complex requirements for all employee, administrative, third party and system account passwords. DeltaGRiC should ensure a minimum of 6 characters, to include numbers, uppercase and lowercase letters, and special characters. All employees, administrative and third party should password as a confidential information and should be encrypted in storage and transmission. The reuse of passwords should be minimized or prohibited and passwords should have a minimum and maximum lifetime restrictions. DeltaGRiC information systems, including but not limited to, databases, operating systems, applications, and file systems, should require authentication before been accessed. User and System Identification, including administrator, system or service accounts, and network device Identification, should have a private authenticator assigned to it. Password policy should be taking into consideration in creating default passwords and it should be changed immediately upon first logon. In the event the integrity breach of a password, or suspected of compromise, the password should be immediately changed and ISO notified. DeltaGRiC’s information system users should properly protect their authentication credentials from unauthorized disclosure or modification. DeltaGRiC’s information systems should obscure the display of passwords or other authentication information during the authentication process to ensure the confidentiality of the information from unauthorized use.
6.6.2 Access Control
Data and system owners shall implement operational procedures and technical controls to ensure access to Fairfax County Government information and systems is based upon the principle of least privilege and an authorized need to know and access. The principle of least privilege, providing only the access necessary to perform assigned duties, shall be implemented to ensure the confidentiality, integrity, and availability of Fairfax County Government information systems and data. Fairfax County information systems shall display a warning banner which identifies the system as a County-owned system, that access is limited only to authorized individuals for approved purposes, that all activity is subject to monitoring, and access indicates acknowledgment of these conditions. County information systems shall initiate a session lock or timeout after a threshold of inactivity has been exceeded. Session locks shall remain enabled until the user again authenticates to the specific system or application. Formal approval, usage restrictions, security standards, and deployment guidance shall be implemented prior to authorizing mobile devices to access County information or systems. Fairfax County Government shall monitor for unauthorized connections of mobile devices to County information systems and enforce protection and standard requirements for approved mobile device connections. Fairfax County Government Information systems shall uniquely identify and authenticate general users, privileged or administrative users, processes, and systems. Fairfax County Government public-facing resources (i.e. published via the Website) which may host privacy-related information systems shall uniquely identify and authenticate external users. Authorization to create a user ID and password must be received from a designated approval authority. Requests for user, administrative, and system access must be approved according to formal access request procedures. Remote access to Fairfax County information resources shall be capable only through approved and encrypted remote access implementations to ensure the confidentiality and integrity of remote access sessions. Fairfax County shall monitor for unauthorized remote access and violations of usage restrictions. DIT may confine wireless communications to organization-controlled boundaries and monitor for unauthorized wireless connections. DIT shall scan for unauthorized wireless access points and take appropriate action if an unauthorized connection is discovered. ISO shall disable internal wireless networking capabilities embedded within information systems or components when not intended for use in mission or business functions.
6.7 Passwords and Passphrases
DeltaGRiC information systems should enforce complexity requirements for all user, administrative, and system account passwords. Staffs should ensure to use a minimum of 6 characters when creating passwords, to include uppercase letters, lowercase letters, numbers, and special characters when technically feasible for the system. DeltaGRiC information system users should properly protect passwords from unauthorized disclosure or modification. Passwords should not be shared with anyone internal or external to the organization. Users are required to maintain password secrecy. Passwords should not be written down or stored in an unapproved retrieval system without proper security controls. Users should not reveal their passwords in either electronic or verbal communications.
Passwords should be changed immediately if the integrity of the password has been or is suspected to have been compromised and ISO should be notified. Passwords for all general user and administrative accounts should be changed every 90 days, and password reuse minimized according to system specifications. System and service accounts must comply with the same requirements unless specifically approved through the formal exception process.
6.8 Intrusion Detection and Prevention Systems (IDPS)
DeltaGRiC should utilize multiple types of Intrusion Detection and Prevention Systems (hereinafter IDPS) technologies to achieve in-depth detection and prevention of malicious attacks. DeltaGRiC’s IDPS can use operating system configurations that minimize the possibility of exploitation, unauthorized access, and system vulnerabilities. IDPS operating systems should be current, patched, and configured according to industry best practices and County System Hardening Standards. IDPS signature releases and software should be kept current as to add new IDPS functionality, new detection capabilities, or refine existing detection capabilities. IDPS administrators should maintain and use individual accounts and passwords to authenticate to the devices in accordance with access management and password policies. DeltaGRiC IDPS should be planned and deployed based on regulatory requirements and infrastructure of organizations networks and should maximize the analysis of traffic transmitted and received. Alert and notification functions for indications of intrusive activity from IDPS devices shall be enabled and monitored by information security personnel daily. Suspected and confirmed instances of intrusions shall be immediately reported to ISO.
6.9 Maintenance of System and Data
The confidentiality, integrity, and availability of DeltaGRiC’s information can be sustained through information system maintenance policies and procedures for systems installed on-site, at remote sites, or through remote third-party processes. DeltaGRiC should make sure that no unauthorized personnel do any maintenance work on their behalf and all maintenance work assigned to some authorized personnel must be supervised not just a member of staff but a staff with a technical knowledge of the maintenance work been done.
DeltaGRiC must ensure that all maintenance done on their behalf is kept on record i.e. date when such maintenance is done, name of the person doing the maintenance, what was maintained, removed, or replaced. System functionality, security controls, and approved baselines must be tested and validated after maintenance or repair to be able to detect if there has been any breach in company’s security.
7 CONCLUSION
BIBLIOGRAPHY
George, Sillowash, et al. Common-Sense Guide to Mitigating Insider Threats 4th Edition. Pittsburgh, 2012.
Forouzan, B. 2014. Foundations of computer science (3rd edition). Hampshire: Cengage Learning.
CERT Insider Threat, https://www.cert.org/insider-threat/
Unintentional Insider Threats: The Non-Malicious Within, https://www.cert.org/blogs/insiderthreat/post.cfm?EntryID=169
Corey, R. 2015. What is the CIA triad? Confidentiality, Integrity, availabilty https://www.cybrary.it/2015/06/what-is-the-cia-triad-confidentiality-integrity-and-availability/ (retrived: 6 May 2017).
Gibson, D. 2011. Understanding the security triad: Confidentiality. 27 May.
http://www.pearsonitcertification.com/articles/article.aspx?p=1708668 (retrived: 6 May 2017).
Andress, j. 2014. The basics of information security: Understanding the fundamentals of InfoSec in theory and practice (2nd edition). Massachusetts: Elsevier.
ISO/IEC. 2005. International Standard iso/iec 17799:2005. Information technology security techniques: Code of practice for information security management. Geneva: ISO Copyright Office.
Ponemon Institute, LLC. (2013, May 28). 2013 Cost of data breech: Global analysis. Retrieved from http://www.ponemon.org/library/2013-cost-of-data-breach-global-analysis
http://www.banking.org.za/what-we-do/sme/sme-enterprise
Michael E. Whitman and Herbert J. Mattord (2008). Principles of Information Security, Thomson Course Technology.
Andress, J. 2011. The Basics of Information Security. Waltham, USA: Elsevier.
Ernst & Young: Get Ahead of Cybercrime: EY’s Global Information Security Survey – 2014. www.ey.com/Publication/vwLUAssets/EY-global-information-security-survey-2014/$FILE/EY-global-information-security-survey-3014.pdf
Chavis, Larry W. and Klapper, Leora F. and Love, Inessa, Access to Bank Financing and New Investment: Evidence from Europe (April 10, 2010). THE ECONOMICS OF SMALL BUSINESSES: AN INTERNATIONAL PERSPECTIVE, Giorgio Calcagnini and Ilario Favaretto, eds., Springer Publishing, 2010. Available at SSRN: https://ssrn.com/abstract=1677453
http://f.datasrvr.com/fr1/516/11618/BakerHostetler_2016_Data_Security_Incident_Response_Report.pdf
Sommestad, T., Hallberg, J., Lundholm, K., Bengtsson, J.: Variables influencing information
security policy compliance: a systematic review of quantitative studies. Inf. Manage.
Comput. Secur. 22(1), 42–75 (2014)
Pahnila, S., Karjalainen, M., Siponen, M.: Information security behavior: towards
multi-stage models. In: PACIS (2013)
Lebek, B., Uffen, J., Neumann, M., Hohler, B., Breitner, H.M.: Information security
awareness and behavior: a theory-based literature review. Manage. Res. Rev. 37(12), 1049–
1092 (2014)
Okere, I., van Niekerk, J., & Carroll, M. (2012). Assessing information security culture: A
critical analysis of current approaches. In Information Security for South Africa (ISSA),
2012 (pp. 1–8). doi:10.1109/ISSA.2012.6320442
Van Niekerk, J. F., & Von Solms, R. (2010). Information security culture: A management
perspective. Computers & Security, 29(4), 476–486. doi:10.1016/j.cose.2009.10.005
D’Arcy J, Herath T & Shoss MK (2014) Understanding employee responses to stressful
information security requirements: a coping perspective. Journal of Management
Information Systems 31(2): 285–318.
Guo KH, Yuan Y, Archer NP & Connelly CE (2011) Understanding nonmalicious security
violations in the workplace: a composite behavior model. Journal of Management
Information Systems 28(2): 203–236.
Willison R & Warkentin M (2013) Beyond deterrence: an expanded view of employee
computer abuse. MIS Quarterly 37(1): 1–20.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Business"
The term Business relates to commercial or industrial activities undertaken to realise a profit including producing or trading in products (goods or services). A general business studies degree could cover subjects such as accounting, finance, management and increasingly, entrepreneurship.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




