Information System Outsourcing and Ethics
Info: 7023 words (28 pages) Dissertation
Published: 9th Dec 2019
Tagged: Information SystemsOutsourcing
ORGANISATIONAL CULTURE
Table of Contents
Task 1: Assessment of Information System Outsourcing
Task 2: Situations of Information systems and ethics
Task 3: Discussion on Security is a business issue
Task 4: Explanation of Enterprise System
Task 5: Explanation of Business Process Analysis
Task 1: Assessment of Information System Outsourcing
Outsourcing of information technology is primarily done to achieve high levels of efficiency within an organization. However, if an organization is not careful then, outsourcing can cause irreparable damage to the company, which can be fatal for its survival. There are five to six main areas, which an organization should focus upon before outsourcing its information security. According to Coltman et al. (2015), cost efficiency is the primary focus of the companies when they are looking for outsourcing. In most cases, a prime reason for outsourcing is to increase the profit margins and reduce operational costs of the company. However, the core activities of the company should never be outsourced. These core activities require specialized skills and knowledge and outsourcing would mere fear of losing the competitive advantage in the market.
Companies these days have to be extra cautious about their reputation especially in the times when social media can make or break company reputation. According to Caldwell, (2013), it has become mandatory that companies continuously focus upon innovating new techniques and improves the quality of its product as per the needs and requirements of its customer base. If outsourcing is done in a correct manner, then customer stickiness with the company increases. For instance, call center executives belong to third-party payroll. However, if outsourcing is done efficiently, then the customers can feel the same comfort as talking to the executive as talking to any of the company staffs. Inefficient outsourcing can be fatal to company reputation.
Figure 1: Risks of IS outsourcing
(Source: as influenced by Harmon, 2014)
In the modern competitive environment, innovation is the key to success. A business will want to increase its competitive advantage by improving product quality and innovating new products and introduce it in the market. However, in most cases, due to certain business constraints, innovation is outsourced to the third party. Thus, businesses should focus on outsourcing innovation to companies that they trust. Successful innovation can lead to competitive advantage in emerging markets, which means a huge increase in profit margins. However, the reverse will have a fatal impact on profit margins as well as its market reputation. Further, once the innovation is outsourced, the companies might not be able to innovate anything in the future. They may not update themselves with the new technological advances that have taken place in recent times.
Outsourcing can bring with itself the risk of loss of business. The service provider is encountering the customer base of the client company. Thus in the case in the near future if there is a change in the mind of the client company to shift its outsourcing then it will be important for the later to keep its customer data safe from unauthorized access. According to Gholami et al. (2013), there is always a risk of the third party company to not meet the quality standards as desired by the client company. In certain cases like in banking or other financial institutions, when IS or information system is outsourced, the customers may not be met or dealt properly by third-party staffs because the later might not really understand what the requirement is. Firms should constantly update their outsourcing partners about the desired standard of work that it expects, and proper monitoring of the third party staffs are important to maintain the expected level of efficiency. According to Gorla & Somers (2014), outsourcing partners are not strategic partners of the companies. If a company makes a profit, then there is no direct benefit of the outsourcing partners.
When companies enter into a contract with their outsourcing partners, there might be some hidden costs, which the companies shout, keep in mind. According to Hammer (2015), there are mainly three to four types of hidden costs. Transition cost is one of the most common hidden costs that companies procure due to outsourcing. Sometimes the vendor might have technical skills and advice that are required to carry out the tasks. Thus, the principal company has to train the third party staffs to ensure that proper implementation of the tasks is carried out. Another form of hidden cost is the transition cost when the contract expires. The company might choose to perform the tasks internally or change its vendor (Nibusinessinfo.co.uk, 2018).
Finally and most importantly, principle companies should always keep in mind the threats of data and security breach when outsourcing information systems. A particular company may render services to many of its direct competitors. Thus outsourcing information systems can develop a risk of breach of confidentiality. According to Nickerson, Varshney & Muntermann (2013), sensitive information if leaked before the competitors will lead to serious injuries to the competitive advantage of the companies. Thus, companies should be extra cautious about this factor. Outsourcing can hamper staff accountability and lead to loss of staff morale. Companies might be challenged by the problem of low-efficiency levels due to the ambiguity of staff accountability. Those professionals who are transferred from principle to Vendor Company may feel offended. They may feel that they are not good enough to be retained back in the company.
Task 2: Situations of Information systems and ethics
The information system has been one of the primary reasons for the financial success of several businesses across the globe. Some companies like Google, Yahoo, Facebook, and eBay among others would not have existed if information system were not invented. However, along with certain benefits, one major problem that has cropped up during this time is the problem of security and protection against information breach. There are about 10 to 15 top ranking companies across the globe that has faced breach of data in the past 6 to 7 years. The numbers are on the increase (Cmu.edu, 2016).
One of the most striking examples of information breach in recent times was that of Yahoo. In 2016, the search engine giant announced that back in 2014 it has been victim to data breaches where a group of hackers hacked sensitive data of more than 500 million users. These data consisted of sensitive information like name, contact details, email id and date of birth. In December 2016, it was further revealed that about 1 billion accounts were hacked in the year 2013. One of the biggest ethical issues that were faced by Yahoo or rather Altaba was that it failed to inform its investors about the data breach. Eventually, Yahoo had to pay a fine of $35 million to US Securities and Exchange Commission. Data breaches can have great financial and legal implications and not informing the investors about the breach is an ethical issue from yahoo’s end (Ncbi.nlm.nih.gov, 2018).
| Company | Ethical and security issues |
| Yahoo |
|
| JPMorgan and Chase |
|
| eBay |
|
Table 1: Information systems and ethics breach
(Source: As influenced by Perloth, 2016)
In 2014, one of the largest banks in USA JP Morgan and Chase was a victim of hackers hacking customer information of over 76 million customers and 7 million small businesses. Sensitive details like customer name email id, date of birth and contact details all were hacked. The hackers also gained access to 90 of the bank’s servers, which could have resulted in the transfer of funds from customer accounts, and unauthorized use of net banking and credit cards. Further, money-laundering charges against the hackers were also on the role. JP Morgan and Chase spend about $250 million dollars each year to protect its servers and systems from being hacked. However, it failed to upgrade its system to two-factor authentication.
Two-factor authentication not only requires a password but also asked for a one-time password to be sent to customer’s mobile number to gain access to net banking (Ncbi.nlm.nih.gov, 2018). This facility was lacking in JP Morgan Chase systems. According to Perloth (2016), the hackers could have been caught much before them gaining access to 90 servers of the bank if the bank had they made a simple security fix when user credentials of one of their staffs were compromised. JPMorgan declared that there was no monetary loss to any of its customers. However, the hackers were just one step away from doing the same. Phishing and unauthorized use of credit, debit cards can be fatal to customer’s financial security.
e-Bay is another auction giant that faced data breach issues in May 2014. Hackers breached in company systems and hacked personal information like name email id and date of birth of more than 145 million users. According to Kelly (2014), eBay claimed that the debit or credit card and account information could not be hacked because they were saved separately. However, eBay was criticized for its failure to upgrade its systems for safe and secure usage. Further, it was not able to implement the password renewal process efficiently. The users were not communicated about its breach of personal data. These are certainly ethical issues, which have hampered company reputation in the market.
Thus, to conclude an ethical code of conduct must be created to guide the companies in case they face a data breach. Most of the companies especially the financial institutions deal with the monetary aspects of its customers. Thus if they fail to abide by the code of conduct, it may lead to fatal consequences for its customers. Along with customers, the other stakeholders like investors and financiers should be informed about the breach (Perloth, Corkery & Goldstein, 2014).
Task 3: Discussion on Security is a business issue
With the lines between work and play blurring them due to advancement in technology, it has become more apparent that security maintenance is not just an issue of the information technology department. Data or information acts as a business enabler allowing organizations to undertake productivity and operations as well. Security needs to be seen as a task of minimizing risks for an organization. Translation of business requirements into all forms of security configuration can grant access to a better two-way communication process. Security helps a business to develop critical functions and treat potential risk as important aspects of successful business performance.
Gone are the days, when cybersecurity headaches would be moved on to It departments. This is because of the digitization of business. For instance, in Telstra’s cybersecurity report, it is shown that 59% of Asian organizations a business-interrupting security breaches at least once a month. Protection of such risks requires a business to think of protection hacks not only as a business risk but act accordingly as well. The marketing team deals with probably the greatest amount of data than any other department. Hence, a breach of this data can result in blockages for marketing operation thereby creating issues for company sales and promotions.
In this contemporary world of business, it has been observed that most of the business organizations are relies on technology and it increases the chances of losing essential information of very high. As influenced by Harmon (2014), security issues of a business organization that involves in security breaches, malicious attacks for instance integration of viruses in computer system along with hacking that steals essential information and so on. It has been observed that not only both Government and Non-government organizations are dependable to cellular phones, voice mail system, and many more other latest technological innovations in order to maintain their work process better way.
Even for that purpose, most of the organization stores their all information regarding their business activities, information regarding business properties, customer’s information, and information regarding business associates, business transactions and so on. However, this increasing dependency on electronic products and raising incidents regarding security issues of business organizations create doubts among the customers. As influenced by Jeston (2014), most of the business organizations face issues regarding their strategies of maintaining security and privacy of essential business information. In recent times, due to these security issues, it has been observed that the number of identity theft has also started to grow gradually.
Figure 2: Alignments of IT and Business Issue
(Source: as influenced by Keyte & Locher, 2016)
Although most of time security issues are considered a technological issue that can create a huge effect in the infrastructure in today’s communication system, however; at the same time business organizations are going to be affected by this issue in this present era. As influenced by Keyte & Locher (2016), most of the business partners, vendors along with several business suppliers are using a respective network, in order to avail the facility of getting accessed of required business information easily. This facility creates chances among criminals through breaching the security of that network along with discloses all the confidential information and even steals them also. As influenced by Laudon & Laudon (2015), generally, cybercriminal attempts to steal and disclose confidential information in order to gain financially. For that purpose, it is required to protect confidential data from the persons that do not have the power of legitimate and authorization access.
Nowadays, most of the business organization has their own private networks that are used by their employees in order to do their work. In this situation, it has been observed that the security regarding information technology has not possessed highly advanced architect of network infrastructure. As influenced by Agostinho et al. (2016), weak network infrastructure can increase the possibilities of information hacking in a business organization. In this context, the integration regarding information security for a business organization can minimize the chances of data loss along with decreases the chances of data modification in unexpected ways. For that purpose, most of the time, it has been observed that there are issues regarding integration in data protection and making balances through satisfying the customers demand regarding the security of information technology in a business organization.
In addition to that, it has been observed that most of the business employees have made they’re unauthorized accessed at the time of doing work through their personal devices such as mobile phone. As influenced by Babnik et al. (2014), using unauthorized access can create the chances of saving business data, and that leads to possibilities of infected by malware, finally can reach to the cybercriminals also. In addition to that, despite security protection in a business organization, CryptoWall can still increase the chances of getting affected by malware. As influenced by Barton et al. (2016), CryptoWall is nothing but an external security threat for an organization that tracks the users to open an infected email. In this context, it is required to establish a clear and effective communication among business associates, employees of the organizations in order to establish the culture of security awareness.
Similarly, appointing experienced social engineers will be helpful for an organization in order to minimize the risk of security issues. Apart from that, ensure proper control regarding user activity can help to decreases the chances of transactions errors along with digital identity theft. For that purpose, it is required for a business organization to give responsibility to the experienced person that is responsible for payment run, maintaining bank details, transactions of a business organization.
Hence, it can be said that in order to avoid issues regarding security, a business organization needs to write down their security policies in a detailed and explained way. In addition to that, it is required to implement security policies in an easy way that can be helpful for all users and along with that many mutual networks, scanning is required. This can help in identifying security along vulnerability issues of the network, and proper implementation strategies can help to overcome those issues.
Task 4: Explanation of Enterprise System
In this contemporary business world, Enterprise System has gained its importance in order to manage and evaluate business operations efficiently. It also helps a business organization to solve their most complex business easily with the help enterprise system. As influenced by Gatzert & Martin (2015), the enterprise system is nothing but a huge number of applications that comes within a software package and help a business organization in data analysis, business process along with maintaining the information flow efficiently. It has been observed that with the help of enterprise system, an organization can monitor several departments of an organization and identifies problems easily. In this context, it can be said that using enterprise system has helped Nestle organization to make improvements in their efficiency in the workflow.
One of the renowned company for candy making, Nestle was able to increase their business easily with the implementation of the enterprise system in their business organization. In the year 2000, with the implementation of the enterprise system in Nestle organization has helped not only make better work efficiency regarding finance, production management, procurement, demand planning and much more. As influenced by Gonzalez, Llopis & Gasco (2013), an enterprise system can assist an organization to build a business plan along with a budget that is going to be required for future for a business organization. In addition to that, it can assist in decreasing the supply order at a minimum rate. As influenced by Gurung & Prater (2017), an enterprise system can help to review the production and delivery system efficiently through the organizing process properly.
On the other hand, it has been observed that enterprise system has Nestle organization through re-engineering the work process and make improvements in supply chain management of the organization. As influenced by Han & Mithas (2013), enterprise system not only helps to identify problems regarding supply chain management by identifying the problems but along with that it helps in resolving those issues also. It has been observed that with the help of the enterprise system, an organization can avoid the delays regarding the rollout of the project and assist in focusing business strategies instead of logistics. Enterprise system has helped Nestle organization to identify other supplies in order to implement new strategies for business developments. It can be said that enterprise system has helped Nestle organization to make replacements of old supplies for new orders.
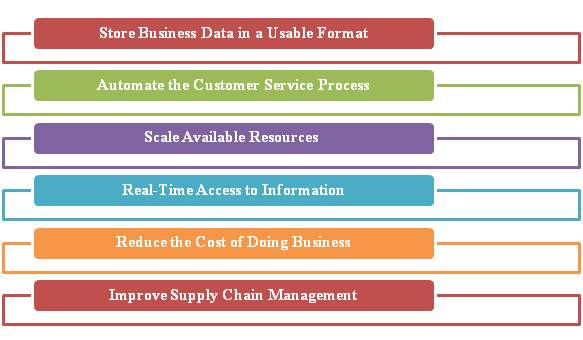
Figure 3: Values of Enterprise Systems
(Source: as influenced by Lambert & Davidson, 2013)
In addition to that, the enterprise system helps to manage the supply chain management of an organization most efficient way. As influenced by Kolb & Reichert (2013), with the help of enterprise system, an organization can handle supply chain management through focusing the overall needs of a business. In this context, Nestle organization has become benefited through the enterprise system by managing the overall manufacturing costs of their products. In that situation, the enterprise system has played an important to store a huge amount of data that can be utilized in a usable format for the further business purpose. As influenced by Lambert & Davidson (2013), it is essential to store and retrieve those stored data easily at the time of requirement for a global organization. It has been observed that business data that are stored usable format can assist an organization to provide the required information in front of their customers as well as business associates also.
Apart from that, the satisfying customer is essential for a business organization to make improvements in their business. In this context, Nestle organization has adopted a customer service process that is automated for their employees. As influenced by Min et al. (2016), automated customer service process of enterprise system can assist an organization to maintain efficiency regarding their customer service process and maintain their works regarding back office efficiently. It has been observed that the automation system of customer service can not only help to save time in satisfying their issues, however, in addition to that helps in forecasting new products also. In addition to that, a business organization can able to access their required any time they want. As influenced by Niu et al. (2014), enterprise system provides an organization the facility of accessing real-time information that can assist them in improving the business process of an organization easily.
It has been observed that using an enterprise system in a business organization can assist in reducing cost in several sectors, for instance, inventory control, budget regarding customer service and much more. As influenced by Nofal & Yusof (2013), an enterprise system can help to make changes regarding the cost of inventory that can create a huge impact on the bottom line of a business organization. In addition to that, the enterprise system helps in strategizing the way new business strategy can be implemented for a business organization. It has been observed that using an enterprise system can assist in finding new resources in order to implement a new business plan effectively. Even, the enterprise system ensures the regulatory compliance for an organization. As influenced by Rosemann & vom Brocke (2015), information regarding an organization’s business activities, assets along with properties are collected with the help of automated means that are stored in an enterprise system and present in front of investors easily.
In this context, LG, one of the renowned multinational electronic company has able t make improvements in their business process management regarding Human Resource, self-implementation of self-service services for their employees and so on. In addition to that enterprise system has provided them the benefits of a centrally managed single system that helped them to make improvements in the business by making it standardized. As influenced by Sarno, Pamungkas, & Sunaryono (2015), improvements in a business process can assist a business organization to improve work productivity and work efficiency throughout the organization. Apart from that, the system has helped LG to find and implement new business practices for their betterment in an organization. It has been observed that centralized control in HR process was able to make localized changes in a flexible way. In addition to that enterprise system provides the facility for reporting in real time for higher authorities of a business organization. This real-time reporting facility can guide them in order to form new business objectives and track its progress.
Task 5: Explanation of Business Process Analysis
Business Process Analysis or BPA has gained its importance in an organization, in order to develop and maintain work efficiency along with effectiveness in business operations. As influenced by Tjader et al. (2014), with the help of business process analysis, an organization can exchange business information, documents, and the process that is involved at the time of doing business. It has been observed that most the public sector uses the BPA that helps them not only for their business goals but guide them in identifying business problems and fix them. As influenced by Zott & Amit (2013), business process analyses provide recommendations to an organization regarding the core process of the business based on the data collection.
It has been observed most of the business organization uses this BPA system in order to provide better training to their new employees to become accustomed to their current business process. As influenced by Sarno, Pamungkas, & Sunaryono (2015), better training process can help new employees to improve their work productivity in an organization. In this context, it can be said that BPA has used by UN/CEFACT or the United Nations Centre for Trade Facilitation and Electronic Business. BPA has assisted the organization to make a proper process through clear documentation and identify process inefficiencies. As influenced by Han & Mithas (2013), through identifying inefficiencies can help an organization to make strategies in order to overcome obstacles. Apart from that, through robust data, an organization can monitor the way business process is performing.
In addition to that, it has been observed that some business organizations also use Business Process Modeling along with BPA system in order to improve the efficiency in the workflow of the business organization. As influenced by Niu et al. (2014), with the help of business process modeling, an organization can represent an illustration of a business process of that organization and make alignment their business strategies to their business operations. Although, Flowcharts, Petri-Nets can help to make illustrations of the business process, however, in addition to that several software are also available for doing that illustration a more easy way.
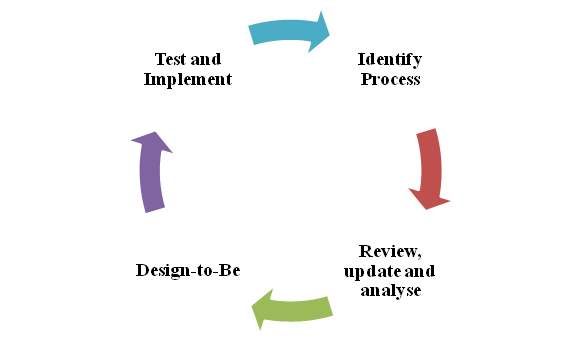
Figure 4: Business Process Framework
(Source: Created by author)
As influenced by Tjader et al. (2014), using business modeling tools can help to simulate the workflow of an organization before implementing it into actions. Several ways exist that can help a business organization to make improvements in their business process modeling. Design To-Be Process, Model that is based on the existing process, identification of efficiencies along with potential improvements is some of the popular ways that can guide a business organization.
It has observed that the BPA system determines birth the success and failures of business. For that purpose, it is required to satisfy the requirements of the projects and analyses the project vision along with its objectives in order to make proper development in a business process system. As influenced by Lambert & Davidson (2013), in order to make developments in a system through business process analysis, it is required for an organization to review the business goals that can help them to reach their business goals. In this context, it has been observed that BPA has played an essential role in order to implement changes in the present core business process of an organization.
It has been observed that ISD or Information System development along with BPR activities and technological implementation of the workflow are all the aspects of the system development process for a business organization. These systems aspects along with the conceptual process of business analysis are essential for a business organization in order to make improvements in the business process operations systems. As influenced by Kolb & Reichert (2013), with the help of business process analysis, an organization can not only identifies the conceptual business process but along with creates an impact on them. In this context, support regarding production along with employees of the organization is some of the aspects that are not affected by these production aspects.
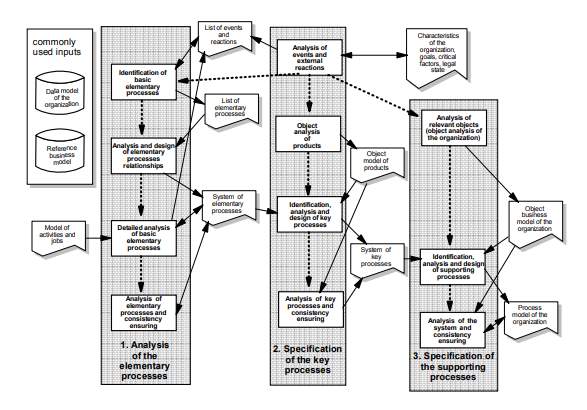
Figure 5: Role of Business Process Analysis in Information System Development
(Source: as influenced by Rosemann & vom Brocke, 2015)
In addition to that, with the help of the business process model, a system encapsulates the data that they store in IS or Information System and implement actions based on that data that turns into a process. As influenced by Rosemann & vom Brocke (2015), the conceptual model regarding business process analysis assists the ISD through providing the required information in order to establish the structures regarding interface functions properly. In this context, it can be said this information regarding the structure of interface functions are in the form of business products along with business activities along with information regarding present structures of business products; business activities are also identified. It has been observed that most of the ISD analysis systems are performed worth the collaboration with BPA system of a business organization. As influenced by Sarno, Pamungkas, & Sunaryono (2015), in order to solve a complex process, most of the business organization breaks their process of business analysis into several sub-processes that help the system to monitor the processing system efficiently.
In order to make developments in the system based on the business analysis process, it is required to make a blueprint in order to make efficiency in the workflow. Process Design, Process in action along with Process Implementation and Process evaluation are some of the steps that can help a system to make developments. As influenced by Niu et al. (2014), in order to solve an issue regarding business a system has been developed with the help of technical expertise of an organization along with the guidance of business analyst. In the technical spec phrase, the system has been developed that has much more details regarding that specific business issue and finds a way that can be implemented in order to solve that issue.
In addition to that, BPR or business process re-engineering system can assist a lot in order to make improvements in the business analysis process. Business reengineering process can help to identify and eliminate the process that is not required for a business organization (as influenced by Lambert & Davidson, 2013). In order to solve a business by making developments in the system, it is required to have user acceptance by making it user-friendly.
Reference List
Books
Harmon, P. (2014). Business process change. Massachusetts, United States: Morgan Kaufmann.
Jeston, J. (2014). Business process management. Abingdon, UK: Routledge.
Keyte, B., & Locher, D. A. (2016). The complete lean enterprise: Value stream mapping for administrative and office processes. Florida, United States: Productivity Press.
Laudon, K. C., & Laudon, J. P. (2015). Management information systems (Vol. 8). New Jersey, United States: Prentice Hall.
Journals
Agostinho, C., Ducq, Y., Zacharewicz, G., Sarraipa, J., Lampathaki, F., Poler, R., & Jardim-Goncalves, R. (2016). Towards a sustainable interoperability in networked enterprise information systems: trends of knowledge and model-driven technology. Computers in Industry, 79, 64-76.
Babnik, K., Breznik, K., Dermol, V., & Trunk Širca, N. (2014). The mission statement: organizational culture perspective. Industrial Management & Data Systems, 114(4), 612-627.
Barton, K. A., Tejay, G., Lane, M., & Terrell, S. (2016). Information system security commitment: A study of external influences on senior management. Computers & Security, 59, 9-25.
Gatzert, N., & Martin, M. (2015). Determinants and value of enterprise risk management: empirical evidence from the literature. Risk Management and Insurance Review, 18(1), 29-53.
Gonzalez, R., Llopis, J., & Gasco, J. (2013). Information systems offshore outsourcing: managerial conclusions from the academic research. International Entrepreneurship and Management Journal, 9(2), 229-259.
Gurung, A., & Prater, E. (2017). A research framework for the impact of cultural differences on IT outsourcing. In Global Sourcing of Services: Strategies, Issues, and Challenges (pp. 49-82).
Han, K., & Mithas, S. (2013). Information technology outsourcing and non-IT operating costs: An empirical investigation. Mis Quarterly, 37(1).
Kolb, J., & Reichert, M. (2013). A flexible approach for abstracting and personalizing large business process models. ACM SIGAPP Applied Computing Review, 13(1), 6-18.
Lambert, S. C., & Davidson, R. A. (2013). Applications of the business model in studies of enterprise success, innovation, and classification: An analysis of empirical research from 1996 to 2010. European Management Journal, 31(6), 668-681.
Min, H., Joo, S. J., & Nicolas-Rocca, T. S. (2016). Information system outsourcing and its impact on supply chain performances. International Journal of Logistics Systems and Management, 24(4), 409-425.
Niu, N., Da Xu, L., Cheng, J. R. C., & Niu, Z. (2014). Analysis of architecturally significant requirements for enterprise systems. IEEE Systems Journal, 8(3), 850-857.
Nofal, M. I., & Yusof, Z. M. (2013). Integration of business intelligence and enterprise resource planning within organizations. Procedia Technology, 11, 658-665.
Rosemann, M., & vom Brocke, J. (2015). The six core elements of business process management. In Handbook on business process management 1 (pp. 105-122). Springer, Berlin, Heidelberg.
Sarno, R., Pamungkas, E. W., & Sunaryono, D. (2015, May). Business process composition based on meta-models. In Intelligent Technology and Its Applications (ISITIA), 2015 International Seminar on (pp. 315-318). IEEE.
Tjader, Y., May, J. H., Shang, J., Vargas, L. G., & Gao, N. (2014). Firm-level outsourcing decision making: A balanced scorecard-based analytic network process model. International Journal of Production Economics, 147, 614-623.
Zott, C., & Amit, R. (2013). The business model: A theoretically anchored robust construct for strategic analysis. Strategic Organization, 11(4), 403-411.
Online articles
Caldwell, T. (2013). Plugging the cyber-security skills gap. Computer Fraud & Security, 2013(7), 5-10. Retrieved on 8th October from https://www.sciencedirect.com/science/article/pii/S1361372313700629
Coltman, T., Tallon, P., Sharma, R., & Queiroz, M. (2015). Strategic IT alignment: twenty-five years on. Retrieved on 8th October from https://link.springer.com/article/10.1057/jit.2014.35
Gholami, R., Sulaiman, A. B., Ramayah, T., & Molla, A. (2013). Senior managers’ perception of green information systems (IS) adoption and environmental performance: Results from a field survey. Information & Management, 50(7), 431-438. . Retrieved on 8th October from https://www.sciencedirect.com/science/article/abs/pii/S0378720613000724
Gorla, N., & Somers, T. M. (2014). The impact of IT outsourcing on information systems success. Information & Management, 51(3), 320-335. Retrieved on 8th October from https://www.sciencedirect.com/science/article/abs/pii/S0378720614000020
Hammer, M. (2015). What is business process management?. In Handbook on business process management 1 (pp. 3-16). Springer, Berlin, Heidelberg. Retrieved on 8th October from https://link.springer.com/chapter/10.1007/978-3-642-45100-3_1
Nickerson, R. C., Varshney, U., & Muntermann, J. (2013). A method for taxonomy development and its application in information systems. European Journal of Information Systems, 22(3), 336-359. Retrieved on 8th October from https://www.tandfonline.com/doi/abs/10.1057/ejis.2012.26
Newspaper Article
Kelly, G. (2014, 21 May). eBay Suffers Massive Security Breach, All Users Must Change Their Passwords. Forbes [Online] Retrieved on 7th October 2018 from https://www.forbes.com/sites/gordonkelly/2014/05/21/ebay-suffers-massive-security-breach-all-users-must-their-change-passwords/#76c68d4a7492
Perloth, N. (2016, 22 Sep). Yahoo Said Hackers Stole Data on 500 Million Users in 2014. New York Times. [Online] Retrieved on 8th October 2018 from https://www.nytimes.com/2016/09/23/technology/yahoo-hackers.html
Perloth, N., Corkery, M. & Goldstein, M. (2014, 22 Dec). Neglected Server Provided Entry for JPMorgan Hackers. New York Times. [Online] Retrieved on 8th October 2018 from https://dealbook.nytimes.com/2014/12/22/entry-point-of-jpmorgan-data-breach-is-identified/
Website
Cmu.edu (2016) Guidelines for Data Protection – Information System Security Retrieved on 8th October from https://www.cmu.edu/iso/governance/guidelines/data-protection/information-system.html
Ncbi.nlm.nih.gov (2018) The Pros and Cons of Outsourcing Information Technology Retrieved on 8th October from https://www.ncbi.nlm.nih.gov/pmc/articles/PMC2793990/
Nibusinessinfo.co.uk (2018) Outsourcing Advantages and disadvantages of outsourcing Retrieved on 8th October from https://www.nibusinessinfo.co.uk/content/advantages-and-disadvantages-outsourcing
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Outsourcing"
Outsourcing is a business practice, often undertaken as a cost cutting exercise, whereby a third-party is hired to perform tasks or a specific activity that would traditionally be performed by an employee of the hirer.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




