Integrated Examination System
Info: 12025 words (48 pages) Dissertation
Published: 11th Dec 2019
Tagged: Information Technology
Chapter 1 – Project Introduction
1.1 Introduction
An integrated system in information technology and software engineering has a meaning where two or more system combine to produce one piece of artefact, as System Integration (SI) explains in this review, so those system or subsystems can share features and communicate with each other. The IES software is integrating with an examination system that is related to the exam board institution as they provide with exam rule and regulation and the education organisation where they provide the student data. The integrated examination system (IES) will offer each student with the facility to have all the formatting tools to write their answers and to have a feature where the system can support in understanding of the questions so it can be answered in a correct way. This accessibility is very useful for special needs candidates as it can help them understand in a more effective way especially when they have difficulties in understanding the questions; they may not be able read the question or possibly misread the question due to their condition such as Dyslexia. The IES will have a PDF import which can be set up very easily by any of the administrator staff members. The main reason to have this PDF input is to have a flexibility in preparing a local application testing system which means whenever a staff member wants to assign a test to the class or have an exam session of any subject all they need to do is just import the list of exam papers that the teacher has prepared for each individual student.1.2 Problem Statement
The project idea originated during Shahzad’s industrial placement year as one of his responsibility was to set a restriction on the computer to block out all the computer stock applications so to do this he was tasked to set group policies on student laptops so they are ready for examination. The problem occurred when the volume of laptops increased which required more staffs to complete a single task. The issue that the technicians had to achieve the task is that there were some programs which couldn’t be controlled by Group Policies or by User Account rights. Therefore, they had to uninstall them one by one. What Shahzad recommended to them was that they find a software which restricts the students from accessing pre-installed windows programs, however after researching they couldn’t find any program that fulfils our needs, the big reason being that whichever one they look at it is poorly designed and had an exit feature that lets the user close the application and the user could use the internet alongside using the software which they didn’t want. The software program should fulfil the term and conditions requirements from Joint Council for Qualifications (JCQ CIC). The key features of this software program are that it records each candidate's question answer record and activities while using the software and to submits that collected data and keep save it after submission.1.3 Aim & Objectives
Aim of developing the Integrated Examination System (IES) software program is to support information communication technology (ICT) management team in the educational organisations, so that they don't have to spend a lot of time to setting up a computer machine individually in the event of an exam session or any computerised classroom test. In addition to avoid discrimination of each individual student who is taking the test at the time. The student will be welcomed by a split screen once they launch the program which is split into two sections where one section they will see the PDF import and another will be a typewriter document where they can type the answers. During the period of the use of the system all the key commands will be stored in a log file which then will be submitted alongside the submission of the paper. this Information will be very useful when coming to marking the paper as it tracks all the key commands and user activities during that period.1.4 Minimum requirements
By the end of this project all the minimum set of implementations will be:- A fully functioning two Window Presentation Framework applications one for student and one for staff members with usable user interface.
- Have a functionality so application can communicate with each other.
- Allow the student application to be able to import text.
1.5 Extensions
If time allows, there are many extensions to the application which would be desired to be included, but are not necessary for the final piece of project outcome.- A tutorial element of any problem solution, is not only provide training to the end user for the use of product, but also inadvertently educating the user with core functionality of software solutions.
- The project structure can be modified to the web-services.
- On the server side the application can send multiple messages to the client side simultaneously alongside the files and same the time.
1.6 Deliverables
- The main deliverables to have a Finnish application using the WPF platform both server side and Client side TCP/ IP, Protocol Technologies as this is the minimum requirements after the project
- this project is that it should have a completion off the communication between the two applications also can voice type the answers on the client side of the application.
1.7 Evaluation criteria
To demonstrate this software artefact, University student and staff’s member requested to use the software artefact, who attract some interest in productivity software and they will be asked to spend some time using the software in its state at the time to use the application without any assistances After a user evaluation, will be followed by a short questionnaire, comparing the two solutions, and the level of difficulty they experienced.1.8 Relevance to University Degree
This project is developed in reflection from Task-Based Software Engineering(COSE50584) and Concurrent Network Applications(CESCOM10104-5) modules, as part of my Software Engineering(G600) degree using the techniques, skills, and programming criteria from them. By following the modules learning materials which supported to create structure the code, formatting, creating functions and objects; as well as rearranging software application in an object-oriented trend. Alongside the Networking experience gained in my industrial placement year, guided me with coming up with this software application artefact. Also, how to manage with issues based on common bugs and features. Thus, applying best-practice to come up with solutions and by dividing tasks to milestones and priorities. Another module called Object-Oriented Application Engineering Programming (COSE50582) was used during the development process of outcome the object-oriented trend and design patterns as mentioned before. Overall, studying this Software Engineering degree, I have built a lot of skills in programming and handling problem solving issues in a logical and methodical manner in projects. As well as gaining confidence while working outside in the industrial.1.9 Research Areas
To develop this integrated system for exams these are the following research method that this review will look in to:- System Integration
- Current examination systems
- Cheating issues aspect
- System Security
- Technology Usage
Chapter 2 – Background Research
2.1 Research Introduction
In these current days where technology is rapidly perceiving the human life with no exceptions of education world, particularly implementation of secure examination system is a very demanding topic and issues that should be addressed in the by developing a secure examination system. During the exam, teachers provide the system that is website application and secure network design which can prevent cheating by examinee and examine both in aspect of cheating and security prevention. As everyone knows that education was initially handled manually by doing written exam and now has been replaced by a more digital examination system to be more accurate and efficient. This is a better way to mark and monitor exams with no human errors. As there are many human errors that can take place in exams and after the exams. The point of the software interface is to make it easier to mark, view and monitor exams. This will reduce any kind of mistake that occurs in the exam hall or when marking. Security is a very major issue when it comes to integrated system for exam such as therefore the exam organisers in the institution must take care of the personal details that are written when taking an exam, the existence of security hole allows someone to access the system by illegally stealing exam questions and answers, making changes to existing value, or other type of modifications. (Abdul Wahid, 2015) Organisers should separate the correct information like answers and make sure they don’t mix with any other information from the exam. If they move the exam onto digital instead of written, it would decrease any wasted time which is done by a normal written exam. For example, after the test has ended the papers need to be collected and put to the assigned teacher, there could be a possibility that the papers get muddled up and it would cause some students to have an irrelevant and unqualified grade. To reduce the chances of this the ICT technicians should move the test onto a digital system. This would make it 99% impossible to have an error. The chances are slim for a computer to make a mistake but a human error of course everyone makes mistakes. So, that’s why creating this software has many benefits with very little resolvable impacts. Which is cheating, there is a high possibility people can cheat as there are new ways invented every day. The chances of someone passing when cheating is 0.1% as complete word for word answers with references are automatically defined as copied as torrents or malware software tend to use the host’s IP address this makes it able to connect to the internet and retrieve answers. When it does this the system security software recalls information on browsing activity or surfing activity throughout the system. If any activity is found that is not from the system software itself then the software detects it and defines it as a false entry and stops any functions from happening from that host IP, which would block the system which the cheating client is working from revealing the person who has been cheating. Efficiency is the key to this software as it provides maximum work in a slow amount of time and efforts. Efficiency is needed because the more accurate the software is in presenting the data and sending the data to an examiner who can mark the paper without error.2.2 System Integration (SI)
As the integration is a key aspect of this IES project and for the outside industries software system that use SI technology, SI is a modular approach for building systems and SI process has always been at the near-end of the development cycle (Techopedia, 2017) because integration refers to the practice of combining individually tested software components into an integrated whole (Carnegie Mellon University , 2012). In recently year, As the technology is growing the concept of SI is moving away to service-oriented and cloud-based architecture (Mann, 2012). The reason for this is that enterprise software development industries is looking for light weighted infrastructure as they need to support more complex integrated problem.2.2.1 Integration Architecture
An integration architecture is a general pattern that serves as a blueprint to define the basic layout of an integrated system (Ng, 1991). The architectures general strategy is of system decomposition, data storage, and communications as (ISAZADEH, 2004) says, and there are two main issues that can occur when developing an integrated system, the issues are communication and handing data in the system, these issues can be resolved in the large-scale emprise application system by following basic type of software integration architectures which are as follow (ISAZADEH, 2004):- Message-passing systems – is a communication system which send messages between compounds, system and subsystem.
- Channel-based systems- is where an active component of the system uses a channel communicates with each other’s.
- Systems with central repository – is a database source as that the main integrating root.
- Object-oriented systems –is used to show reusability of those system components and make the software more efficient.
2.3 Existing Solution
2.3.1 Content Management Systems
There are many content management systems(CMS) such as Moodle, Webct, Blackboard and many more in house based software systems and hosted via internet (Sarrayrih, M., and Ilyas, M. 2013). As the definition of CMS explained by (Rouse, 2016) that it is a set of software application which are used to create and manage digital content and CMS are predictably used in enterprise content management (ECM). These CMS are not widely used for online examination due to security vulnerability concerns as (Abdul Wahid, 2015) said. The only disadvantage of CMS is the security strength as the software has many uses that are over the internet which can be a security issue but as some websites are monitored they are protected. And ICT technician know this as there is a green lock on some websites which show that the site is protected. When examination takes place online there are remote controlled by an examiner which show that they are not abusing or either not taking part correctly. However, these systems are not entirely used for online exams there are also used for access module materials for example Staffordshire University have has given access to Blackboard where they can see materials such as lecture Slides, Notes and Marking criteria, with this type of functionality the student a chance to open those materials simultaneously with that exam on aside. This Integrated Examination System (IES) on the hand is all offline based in limited to what should and should not be accessed.2.3.2 Blackboard
Blackboard Learn is an online learning management system where students can take their exams, submit assignments also review any learning materials per their education organisation administrators. They have a similar system to well-known products such as Moodle, Sakai and Desire2Learn. The system is a web application which provides a secure and safe online environment where people can complete their desired courses. Blackboard Learn is made up of various factors. It can be installed on windows machine and uses an internet information services(IIS) web server specifically designed for Blackboard Learn. When used on the web it runs through Tomcat; which is a web container running on Java Server Pages. Blackboard Learn also has a collaboration server which is essentially a text based environment. This allows users to have an interaction. Blackboard Learn also has various server architectures which support the system to be utilised by any user. The IES uses a similar architecture to Blackboard Learn as it consists of server and client side communication however it does not have database at this stage but can be modified or converted with a database in future implementation. (Patterson, 2013)2.4 Security
There are many ways which are used to cheat in online exams. Many which consist of browsing the internet, asking fellow students. These are some of the many way which are used to cheat this can cause people to have an advantage to other students. This is a major concern. More ways include devices which makes students able to call over the room another examinee and trade answers. Another way is connecting a local storage or reading a tutorial that already on the system. All these ways have cures as they can be configured by network settings also external software’s which control the pc system. There are ways were the online based exams can prevent cheating problems one which is by using squid 3 proxy configurations as it prevents the examinees to use search engines or any other facilities of the Internet, according to (Cluskey Jr., et al., 2011) exam organisers should facilitate on the computer machines with Responds Lockdown type internet browser to prevent accessing other website, however many of these browsers can be bypassed so it’s not an efficient way. Nevertheless, the proxy system as this paragraph talked about at the start of this topic if that is set up and configured correctly the education organisation won’t need to use or invest in internet browsers. The way proxy system works is that when the proxy servers enabled only the online examination system server IP can accessed and all the other DNS cannot.2.5 Assessment Criteria’s
There are four main type of assessments testing criteria as stated below. And each of these criteria’s can take advantage of the examination system in any academic organisation sector whether it is secondary school or university standard exams. System like Surpass Paper+ which are offered to build assessment to assess the candidate.2.5.1 Formative Testing
Formative testing is widely used to gauge student learning during the lesson times. It is mainly used to assess students in classrooms to find how they are progressing with the learning material that have been taught to them. These types of tests are usually set as homework’s which students can do at their individual time and seek help from their parents if required. The tests sometime are required researching on topic that they are learning to build up the base for the learner so they can find advance learning material to understand easily. The tests are usually done on Microsoft word processor if they are writing essay type of document or any other Microsoft Office software which ever they find the need of to complete that specific task, so for formative testing the examination system cannot be utilised as it is not an appropriate tool to use because it is not a proper academic exam.2.5.2 Benchmark Testing
Benchmark testing is for checking if the student has mastered a unit of content that have been taught in the classrooms, this type of tests usually focus on a section of the material that they have been recently studying. These assessments have been designed so the teacher can analysis the student understanding of what they have been teaching. So, Benchmark testing is done by either computer or paper based exams. The tests are taken around the end of the term, so examination software systems are on a high demand at that time if the exam is planned to take place on a computer machine Instead of paper based.2.5.3 Summative Testing
Summative testing is similar as benchmark testing but the difference is that instead of testing student on a specific unit as benchmark testing talks about in this Assessment criteria section, Summative Testing cumulatively tests everything that the student has been taught throughout the year (O'Malley, n.d.). The test is given to all the student in the same process as everyone in the classroom, school or state so everyone has an equal opportunity to demonstrate what they know that what they can do. Examination software systems can be used in two assessment criteria’s which are benchmark testing and summative testing Because the tests can be taken on computer, As the student just types instead of writing on a paper if they are not assessed on handwriting skills. By taking the exam on a computer system it can Benefits tutors to mark the exams document and give feedback to the students via emails or face to face in the classrooms at school.2.6 Data Collection
Qualitative and quantitative data collection tools are utilized to measure the qualitative and quantitative dimensions of correct data. Explanations related to the development processes of these data collection tools and their validity and reliability stages are presented below. Things such as Writing Quantity Formulas which counts the number of syllables per word. (Yuan, 2004) Also, Language accuracy scale this was used in the evaluation of texts in terms of accuracy. It has 10 levels ranging from 0-9. Each level has a mark for spelling, punctuation and grammar. For example, the level of determines how many more marks the software can add to the examinee’s marks.2.7 Special Arrangement in assessments
A special arrangement is arranged by the Education institutions should make for a candidate before their exam or any assessments. These arrangements are only given with evidence of the candidate's disability or any temporary injuries which then can affect the learner's. Access arrangements support candidates without changing the actual assessment criteria. These arrangements fall into two categories; one provides methods with delegated Centres and another to require JCQ CIC awarding body approval. When Awarding Bodies will comply it will require Equality Act 2010 duty to make a reasonable adjustment. (Joint Council for Qualifications, 2016)2.8 Exam board organisation arrangements
The Joint Council for Qualifications (JCQ CIC) is an organisation which is a member of AQA, CCEA, City & Guilds, OCR, Pearson, SQA and WJEC awarding bodies and deals with vocational issues. The institution supports learners in England, Scotland, Wales and Northern Ireland to achieve and progress in their studies. (Joint Council for Qualifications, 2016) Reasonable adjustment depends on several factors of that the individual learner by understanding their needs and requirement, an adjustment can’t be made if it is not reasonable and involves: • Unreasonable costs • Timeframes • Affects the security • Integrity A reasonable adjustment may be unique for a specific individual candidate; therefore, it may not be included in the Access Arrangement Approval.2.8.1 Joint Council for Qualifications regulations
These regulations have been established to ensure that the integrity and security of the examination/assessment system is maintained at all times and is not brought into disrepute. Centre’s must conduct examinations and assessments in accordance with these regulations and, where relevant, the JCQ publications (Joint Council for Qualifications, 2016): • Access Arrangements and Reasonable Adjustments; • Instructions for conducting controlled assessments; • Instructions for conducting coursework; • Instructions for conducting examinations; • Instructions for conducting non-examination assessments; and • Suspected Malpractice in Examinations and Assessments – Policies and Procedures. 2.8.1.1 A Centre will have confirmed its readiness to adhere to these regulations when first registered as an approved Centre. All heads of Centre’s will be required to confirm, on an annual basis, that they are both aware of and adhering to the latest version of these regulations. A head of Centre cannot delegate this responsibility to a member of the senior leadership team or the examinations officer. 2.8.1.3 The head of Centre is the head of a school, the principal of a college or the chief officer of an institution which is approved by one or more of the awarding bodies as an examination/ assessment Centre. The head of Centre is responsible to the awarding bodies for making sure all examinations/assessments are conducted according to the instructions, and the qualification specifications issued by the awarding bodies. The head of Centre may not appoint themselves as the examinations officer. 2.8.1.4 The examinations officer or quality assurance coordinator is the person appointed by a head of Centre to act on behalf of the Centre in matters relating to the administration of awarding body examinations and assessments. 2.8.1.5 These general regulations apply to the following qualifications:- AEA, AQA Level 3 Technical qualifications, BTEC, Cambridge Nationals,
- Cambridge Technical, Edexcel Awards, Edexcel Certificates,
- Edexcel International GCSE, ELC, FSMQ, GCE, GCSE, OCR Level 3 Certificates and Projects (including the Extended Project).
- This document may also apply to other qualifications as specified by an awarding body.
- The relationship between Centre’s and awarding bodies;
- The responsibilities of awarding bodies in providing administrative, subject-specific assessment and quality assurance support for Centre’s.
- The responsibilities of Centre’s during preparations for examinations/assessments and post-examination/assessment activities;
- Obligations arising from current data protection, equality and freedom of information legislation.
2.10 Cheating using Online Examination Systems
Cheating has various problems over network, using an online examinations system it uses socket programming to determine the function and abilities of monitoring a proxy. Thus, analysing the data packet, the source address and the destination address. The things that can be gained are the content of the data packet. Based on filtrating rules, once the system find any illegal data packet, the link will be cut and a warning message will be sent to the examiner. Or the computer will be isolated to reject any illegal link (Cluskey Jr., et al., 2011). In this way, cheats can be prevented to some extent. But on the other hand, it is very passive. Only when examiner implements the operation which is not allowed, can illegal information be identified and intercepted. Besides, if the rules are revised or changed illegally, the examination will get out of control. Per these two negative factors, examiners know that using monitoring proxy to prevent cheating is not enough. (Carroll, 2015) (Murphy & Zwieback, 2005) have proposed that with content separating, ventures can fundamentally lessen the spam assault, confine access to improper Sites, and secure against some malware dangers. Like system sifting, content separating must be actualized in both inbound and outbound headings. For the staff working in an association, their parts and obligations regarding framework taking care of must be obviously characterized so they can be considered dependable in instances of security break. In mixed assaults, the pernicious code is produced and can take many structures also, assault the PC framework in various diverse courses, even through a direct physical assault on switches and servers in intrigue with a work force of the association. It can influence a few territories of the system all the while and can play out extra system assaults, for example, refusal administrations against different frameworks. Once inside the system, this can spread to the whole arrange from shared circles to inward Web servers. The previously mentioned dangers are likewise called physical security openings, which should be stopped by utilizing security arrangement. Security and honesty of a mechanized framework are the principle issues in an Internet-based networked environment. In a network, distinctive methodologies, that is, cryptography, digital mark and firewall, are connected to make the framework secure. Yet at the same time there exist numerous security dangers, for example, snooping, wiretapping, parodying, login assault, coordinate information get to, malicious document execution, denial of administration, and framework data spillage (Abdul Wahid, 2015). Henriksson et al. (2006) partitioned the variables that impact the quality of open area data on Websites to six noteworthy classifications: security and privacy, usability, content, services, citizen participation, and features. Wimmer and Bredow (2001) proposed an all-encompassing idea that incorporates security perspectives from the key level down to the information and data level with a specific end goal to address diverse security angles. Their all-encompassing methodology comprises of four layers: vital, handle level, cooperation, and data. Reena Sethi (2006) has directed a study on the effect of ICT appropriation in the vehicle area in an Indian setting. The overview revealed that 22% of open respondents did not utilize the Internet in view of the absence of trust, and 32% workers were not positive about working hostile to infection programs/firewalls.2.11 Human-Computer Interaction (HCI)
HCI is a research study that originated in the early 1980s primarily as a specialty area in computer science embracing human factors engineering. The study lights up on how humans interact with computers and to what extents computer are useful in human interaction teams. Since 1980, HCI has expanded rapidly targeting especially professionals in many regulations approaches (Carroll, 2015). In late 1970s, the usage of computer was very limited as human only interacted with it who were in that profession or liked to use with it as a hobby. HCI relates to many topic studies and has a lot of content covering many aspects of them so covering everything is not essential in this project dissertation. Therefore, in this project research Shahzad will going into end-user development, user-interface and visual representation.2.11.1 End-User Development
End-User Development (EUD) is “a set of methods, techniques and tools that allow users of software systems, who are acting as non-professional software developers, at some point to create, modify, or extend a software artefact” (Henry Lieberman, 2006). Developing an application with EUD gives users more flexibility to use the software according to the user real time needs, as it allows users to customise their user interface, add or remove any other software system features. The reason that EUD is important as explained by (Scaffidi, 2011)is because a user prospective can change at any time during the period of user using that specific software application. Therefore, according to the application that is been developed it is sometime essential for the developer to provide some tuning tool to keep the user active e.g. Most development IDE software’s style configuration are set as a defaults white theme colour contrast However, after using that default theme for some long-term hours of use the bright theme can harm the user eyes, so they might not feel comfortable using the software. Therefore, implementing EUD is a good practise to help the user personalise the theme or any customisable functionality at any time while utilising the software application.2.11.2 User-Interface
This is a very important (Paterno, 2013) part for the adoption of user interface when developing software artefact now days. It provides facilities and easy access to navigate around the application and to see context of the application some are narrated below.- Technology-related aspects
- User-related aspects
- Environment- related aspects
- Social aspects
2.11.3 Visual Representation
Making a meaningful software application for a user requires understanding visual representation, thus, to understand Visual Representation they are its most useful principle which support developer in the creativity skill area when developing screen designs and graphical user interface (GUI). “These principles have been developed and elaborated within whole fields of study and professional skill - typography, cartography, engineering and architectural draughting, art criticism and semiotics.” (Blackwell, 2017). Typography and text Computers were originally made to make daily lifestyle tasks easier. Typography is essentially the style and appearance of text e.g. Font size, Font style. It is essential in a user-interface especially in IES as the product as different accessibilities to improve user experience. It is user-friendly which means it can be used by anyone with no operational knowledge. “Conventions of typography and graphic design help us to interpret that text as if it were on a page, and human readers benefit from many centuries of refinement in text document design.” (Blackwell, 2017) Icons and symbols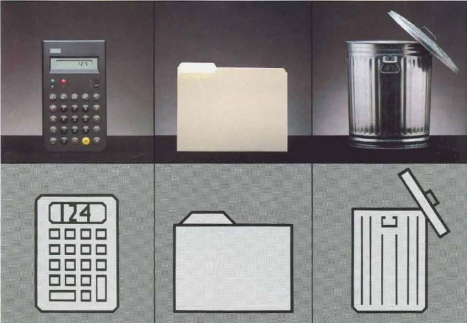 Symbols are frequently used to indicate everyday objects such as a punctuation. As the resolution of computers increased the detail of symbols improved providing easier. Icons are seen easier to interpret as maybe the icons are pictorial giving literate children and speakers of a foreign language an easier understanding of what the specific icon stands for. As illustrated by (Blackwell, 2017) Macintosh used a folder symbol which symbolized a briefcase however the symbol was more of a handle. This gives the impression, anyone could carry any files they wanted, that a briefcase gives the idea of safety and storage.
Figure 2a – (Blackwell, 2017) Presents Life objects generated in symbols
These icons are going to be used in IES to give the user an easier interaction so it doesn’t cause the user any stress regarding the navigation; these icons provide a subtle impression of action behind the icon. For example, a microphone indicates voice recognition.
Symbols are frequently used to indicate everyday objects such as a punctuation. As the resolution of computers increased the detail of symbols improved providing easier. Icons are seen easier to interpret as maybe the icons are pictorial giving literate children and speakers of a foreign language an easier understanding of what the specific icon stands for. As illustrated by (Blackwell, 2017) Macintosh used a folder symbol which symbolized a briefcase however the symbol was more of a handle. This gives the impression, anyone could carry any files they wanted, that a briefcase gives the idea of safety and storage.
Figure 2a – (Blackwell, 2017) Presents Life objects generated in symbols
These icons are going to be used in IES to give the user an easier interaction so it doesn’t cause the user any stress regarding the navigation; these icons provide a subtle impression of action behind the icon. For example, a microphone indicates voice recognition.
2.12 Technologies
2.12.1 TCP/IP Communication
TCP/IP, Transmission Control Protocol/Internet Protocol, is a collection of communications protocols used to interconnect network devices on the Internet. The initial idea behind TCP/IP is that a global communication over a network. TCP consists of various features from protocol standards to high level protocols for consistence. Open protocol standards are freely accessible and were created independently. It is operative offline and in the use of internet. It is mostly ideal for combining different components may they be hardware or software. Independence from physical hardware allows TCP to manage different networks with could be running over Ethernet, DSL (digital subscriber line) connection, a dial up line, optical network and overall any kind of physical transmission. A common addressing scheme allows any TCP device to address a device in the network. This network could be as big as a global network. And lastly the high-level protocol which is used mostly in user services and is very consistent. (Hunt, 2002) TCP Services TCP Client A TCP client requests data from an internet resource using TCP. As established earlier TCP is needed to connect to other devices on the same network however big the network may be. The TCP Client then creates another component called a socket. A socket is the endpoint of bi-directional communications between two processes over a network (Kanjilal, 2015) then using a socket it then requests and receives data via TCP. To create a connection with TCP you must be aware of the network devices’ address and the port allocated to the server. Port numbers are defined by Internet Assigned Number Authority(IANA) this is where common port services are found. If commonly used ports are not on this list then they are in the major ranges from 1,024 to 65,535. (Microsoft Organisation, 2017) Relation to IES2.12 Low-Level Hooks
Hooks is primarily known as a mechanism in which an application can intercept events, involving a various number of examples. Such as, messages, mouse actions and keystrokes. (Microsoft, n.d.) A function that effectively evaluates an event is known as a hook procedure which in many cases is used; a hook procedure can be represented on every specific event it receives, later modifying or discarding the event. This hooking procedure is required for this project to minimise the control of the desktop and the different commands on the keyboard that restrict the user, that prevent cheating of some sort. However, this hooking process is a low-level programming technology, which means it can change the computer machines registry files, keeping in mind that the computer will be harmed as the settings cannot be reverted without the permission of the administrator or any Information Technology skilled staff. The following are examples of the desired implementation features:- Group policy set-up
- Window applications restrictions
- Task menu restrictions
- Spell check restrictions
- Execution restrictions
2.13 Software Testing
Software testing is a process which is used to executing a software application to find bug also used to validate and verify a specific software product, so that it meets the client’s given development milestone. Software Testing lifecycle activities depends on what software development methodologies approach has been chosen, the most common software development lifecycle is Waterfall model however in recent year many organisations are starting to use Agile models.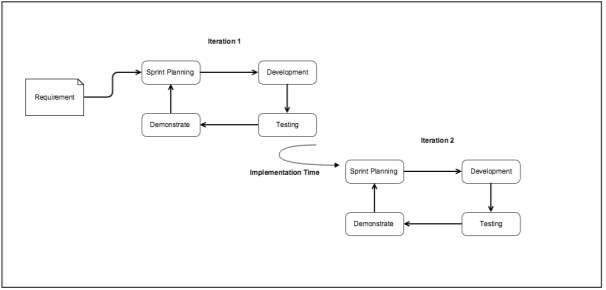 Figure 1 - Agile Model Lifecycle
Advantage of Agile Model are that customer are satisfaction rapidly, because of continuous delivery of useful software and working software are frequently.
Software testing fall into the following stages:
Figure 1 - Agile Model Lifecycle
Advantage of Agile Model are that customer are satisfaction rapidly, because of continuous delivery of useful software and working software are frequently.
Software testing fall into the following stages:
2.13.1 State Testing
Is a test which is carried out during the verification process as the developer writes the source code. Static testing is also a cost-efficient way for businesses.2.13.2 Dynamic Testing
This testing stages implementation is done when the software code is executed to demonstrate the result of running tests. And It is done during validation process. And there are many different types of testing available such as the most well-known are:- Unit testing
- Integration testing
- System testing
- Mock Testing
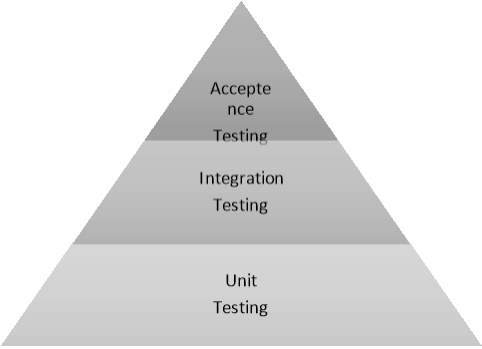 This type of testing encourages developers to modify a piece of feature from the code without having the concerns to break the whole code structure. Once all the unit tests are completed and passed in the “most efficient and error-free manner possible” (Rouse, 2017), A integration test can be run to evaluate the components of the application. The pyramid shaped diagram (Figure 2.13a) represents all the testing layers’ process that occurs when implementing on unit testing.
Figure 2.13a – Testing Layers
2.13.4 Integration tests
Integration Testing is defined as “Integration tests differ from unit tests in that (integrated Test) the code under test is not isolated. Integration tests are written by developers or testers. They run in a unit testing framework” by (Microsoft, 2017).
2.13.5 Acceptance tests
Acceptance Testing is defined as “Acceptance tests consist of multiple steps that represent realistic usage scenarios of the application as a whole. These tests verify that an application meets the needs of the intended users. Their scope includes usability, functional correctness, and performance. Generally, test engineers create these tests”. (Microsoft, 2017)
This testing layer process will be done for each sprint while testing the source code functionality.
This type of testing encourages developers to modify a piece of feature from the code without having the concerns to break the whole code structure. Once all the unit tests are completed and passed in the “most efficient and error-free manner possible” (Rouse, 2017), A integration test can be run to evaluate the components of the application. The pyramid shaped diagram (Figure 2.13a) represents all the testing layers’ process that occurs when implementing on unit testing.
Figure 2.13a – Testing Layers
2.13.4 Integration tests
Integration Testing is defined as “Integration tests differ from unit tests in that (integrated Test) the code under test is not isolated. Integration tests are written by developers or testers. They run in a unit testing framework” by (Microsoft, 2017).
2.13.5 Acceptance tests
Acceptance Testing is defined as “Acceptance tests consist of multiple steps that represent realistic usage scenarios of the application as a whole. These tests verify that an application meets the needs of the intended users. Their scope includes usability, functional correctness, and performance. Generally, test engineers create these tests”. (Microsoft, 2017)
This testing layer process will be done for each sprint while testing the source code functionality.
| Unit Testing Tool | Available as |
| MS Unit | Build-in IDE |
| N unit | Third-party |
| MB Unit | Third-party |
| xUnit.Net | Third-party |
2.13.6 Implementing Unit Testing
To implement on this test to show unit testing in this IES software application and any other software project, the project owner had to first create:- Add a unit test to the project
- Decorate the class the contains test methods with TestClass attributes
- Decorate the Test Method with TestMethod attribute
- Finding bugs early during the development stages, after the product owner made change in the line of code, the developer can run a unit test immediately on the local machine. And see if the code failed or passed the test and know where the bugs were found if failed. In the industrial organisations, if the project did not have unit testing then the developer may have to deploy the to the Quality Assurance (QA) servers and the tester then may or not have detected the bug.
- One is that the end user is might not be able fully utilise the applications feature
- Two to fix the issue it might take a lot of time for the organisation to resolve the issue as it has been found late in the development lifecycle.
- Unit testing also makes complex code easier to understand as if the code which is written a long time ago, it is unlikely to be understand what that code means. Thus, if the developer has done a Unit test around that code it is relatively easy to understand as the developer has ran those unit tests.
- Also, very beneficial as it saves a lot of development time and makes it easier to refactor when needed to do so.
2.14 Agile Methodology
NEED TO FINISHChapter 3 – Project Management
3.1 Introduction
This chapter is about outline the key milestone and overall structure of the projects, including how the IES was planned to be developed and when client interaction took place.3.2 Project Milestone
Integrated examination system (IES) Project can be split up into distinct milestone, which can also be checked for completion- Research, planning and scoping
- Create and Build the interface for the Administrator and the Student
- Build the server interface for connection
- Execute the full system test on the IES once completed
- Write the project report outline the project as whole in detail including the user guide etc. (see detail in sprint 1)
3.3 Gantt chart
To make sure the delivery of the project as mentioned above in section and ensure the project on track, the Gantt chart below is created in figure 3a.| Month |
Oct
|
Oct
|
Nov
|
Nov
|
Nov
|
Nov
|
Dec
|
Dec
|
Dec
|
Jan
|
Jan
|
Jan
|
Jan
|
Feb
|
Feb
|
Feb
|
Feb
|
Mar
|
Mar
|
Mar
|
Mar
|
Apr
|
Apr
|
Apr
|
Apr
|
| Week |
1
|
2
|
3
|
4
|
5
|
6
|
7
|
8
|
9
|
10
|
11
|
12
|
13
|
14
|
15
|
16
|
17
|
18
|
19
|
20
|
21
|
22
|
23
|
24
|
25
|
| Task | |||||||||||||||||||||||||
| Research & Planning | |||||||||||||||||||||||||
| Gathering Inf. | |||||||||||||||||||||||||
| Confirm Project backlog | |||||||||||||||||||||||||
| Review Sprint 1 | |||||||||||||||||||||||||
| Sprint 2 | |||||||||||||||||||||||||
| Sprint 3 | |||||||||||||||||||||||||
| System Testing | |||||||||||||||||||||||||
| Client Demonstration | |||||||||||||||||||||||||
| Report write Up | |||||||||||||||||||||||||
| Proof reading & submission | |||||||||||||||||||||||||
| Hand over Project | |||||||||||||||||||||||||
| Break | Active work on the project |
3.4 Development Tools Used
From the very start of the project it was chosen that this IES software application will be write in Windows Presentation Framework in C-Sharp(C#) programming language, this was mainly due to the compatibility factors in many Education organisation the they are on older system window system however,3.6 Sprint Milestone
NEED TO FINISHChapter 4
Developments & Implementations
4.1 Project Backlog
A Project Backlog is an important fragment of a project which follows an Agile approach as mentioned in Chapter 3 while developing projects. The Project Backlog supports the developer to prioritise the requirements of the project.4.2 Sprint 1
4.2.1 Focus
Sprint 1 started with the Sprint Planning meeting with the superior, where Shahzad decided to focus on collecting development tools to achieve the milestones and start building the foundation of the product which are as follow:- Creating a user interface design for student’s interaction which will be the Client-side
- Create a field so that the student can type their answers
- Save the input data to a selected directory
- Import voice typing feature using Microsoft speech API
- Load a test pdf file on the UI
- Make TCP/IP connection to interact with student user interface as a TCP Clients
- Create a TCP/IP server application so it looks for TCP Clients
- Send test data to TCP Clients
- Record client hostname and IP address
4.3.1 User Interface(UI) Design
Client-side The first sprint started off planning the design of the user interface as a draft paper drawing as seen in Appendix A for the client-side. This interface design was decided due to the necessity of the system for student interaction. The following user interface design in figure 4a was then implemented as a wireframe: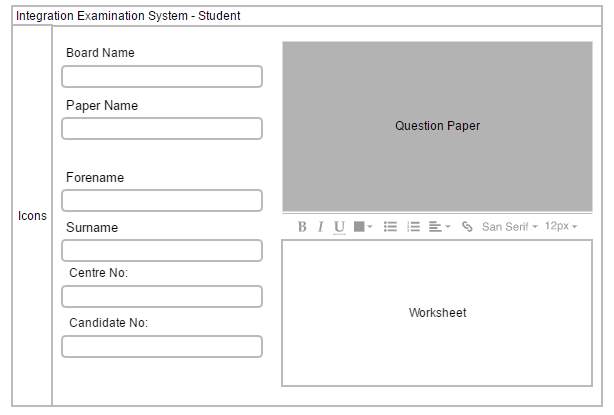 Figure 4a – IES UI Wireframe called IES-Student
After the wireframe decision was made the product owner started to put that plan through development stage using Windows Presentation Framework(WPF) in Microsoft Visual Studio 2015 integrated development environment (IDE). Once the project was ready in Microsoft Visual Studio IDE the second step was to use the available component tools provided by the IDE and create IES-Student interface.
The WPF component tools that the product owner utilized was as follow:
Figure 4a – IES UI Wireframe called IES-Student
After the wireframe decision was made the product owner started to put that plan through development stage using Windows Presentation Framework(WPF) in Microsoft Visual Studio 2015 integrated development environment (IDE). Once the project was ready in Microsoft Visual Studio IDE the second step was to use the available component tools provided by the IDE and create IES-Student interface.
The WPF component tools that the product owner utilized was as follow:
- Textbox
- Button
- Label
- RichTextBox
- Web Browser
 Figure 4b - The editing the XAML files where design code is placed when developing in WPF
After the solution was found for the responsive issue the UI was structured into three different categories. Category first was is where the navigation functionality lies. The second category is where user details will be assigned. This is where the student will write their candidate number and exam board or centre id. The third category is split into rows. Row 1 is where the question paper is presented, the second row is for formatting tools. This provides interaction to row 3 where the work sheet or where the student is supposed to type.
Icons
As this IES software project is targeting students, the user interface needs to be clear, precise and meaningful for students in any age to easily interpret the application. In IES, the icons used in this project are unique as they give a direct impression of the action behind the icon. For example, the submission icon it has the icon of a folder and an arrow pointing inwards providing the thought that this is the button that is used to submit. This has a very universal understanding and is also self-explanatory for anyone to use this.
Figure 4b - The editing the XAML files where design code is placed when developing in WPF
After the solution was found for the responsive issue the UI was structured into three different categories. Category first was is where the navigation functionality lies. The second category is where user details will be assigned. This is where the student will write their candidate number and exam board or centre id. The third category is split into rows. Row 1 is where the question paper is presented, the second row is for formatting tools. This provides interaction to row 3 where the work sheet or where the student is supposed to type.
Icons
As this IES software project is targeting students, the user interface needs to be clear, precise and meaningful for students in any age to easily interpret the application. In IES, the icons used in this project are unique as they give a direct impression of the action behind the icon. For example, the submission icon it has the icon of a folder and an arrow pointing inwards providing the thought that this is the button that is used to submit. This has a very universal understanding and is also self-explanatory for anyone to use this.
| Navigation toolbar icons | ||
 |
Submit button | Folder with arrow gives impression of putting the users work inside this folder |
 |
Speech/Voice Recognition button | Microphone icon represents that the user may use voice to text functionality as this is a quicker way rather than typing. The reason behind the colour red is that it gives a vibrant thought that the user could use speech if this function is enabled. |
 |
Start Exam button | This button provides the user with the intention that the user needs to start the exam paper via this icon. It has a similar colour to the toolbar. |
 The IES program also consists of basic formatting tools such as bold, italic, underline, undo and redo as stated in Figure 4c.
Figure 4c- Formatting Tool
Summary
To finish off the sprint, a Sprint Retrospective meeting was organised and product iteration demonstration with the Product Owner, this is where the questions are raised regarding how the sprint cycle carried out to be. Overall the first sprint was successful in many ways such as the design factor and the initial code behind the work. After one that occurred in the design layout implementation, these were resolved later. The feedback after the retrospective meeting was positive, the user was very intrigued with the idea and positive comments were also mentioned. The hardcode was also up to the standard than they had in mind. The structure of the design was easily accessible as the buttons on the navigation bar were vibrant and not being an eyesore to the user.
This was tested by the user and the product owner seemed very impressed with the accomplishment in the sprint and hinted towards the fact that the project was heading in the direction that the product owner was aiming for. However, the sprint did come with some challenges as stated before the getting used to the code but after thorough research it got easier to interact with that desired section of knowledge. As the sprint progressed familiarity grew increasing confidence in completing the task. Another way that needed to be adapted was having a plan set out of the whole sprint beforehand thus making it easier to come up with the final design.
The IES program also consists of basic formatting tools such as bold, italic, underline, undo and redo as stated in Figure 4c.
Figure 4c- Formatting Tool
Summary
To finish off the sprint, a Sprint Retrospective meeting was organised and product iteration demonstration with the Product Owner, this is where the questions are raised regarding how the sprint cycle carried out to be. Overall the first sprint was successful in many ways such as the design factor and the initial code behind the work. After one that occurred in the design layout implementation, these were resolved later. The feedback after the retrospective meeting was positive, the user was very intrigued with the idea and positive comments were also mentioned. The hardcode was also up to the standard than they had in mind. The structure of the design was easily accessible as the buttons on the navigation bar were vibrant and not being an eyesore to the user.
This was tested by the user and the product owner seemed very impressed with the accomplishment in the sprint and hinted towards the fact that the project was heading in the direction that the product owner was aiming for. However, the sprint did come with some challenges as stated before the getting used to the code but after thorough research it got easier to interact with that desired section of knowledge. As the sprint progressed familiarity grew increasing confidence in completing the task. Another way that needed to be adapted was having a plan set out of the whole sprint beforehand thus making it easier to come up with the final design.
4.3 Sprint 2
4.4 Sprint 3
NEED TO FINISH4.5 Sprint 4
NEED TO FINISHChapter 5 – Testing & evaluation
5.1 Introduction
5.2 Conclusion of Project
Conclusion (NEED TO FINISH)
To conclude my software should have types of information and communications technology features as discussed above are not finite or fixed categories. Indeed, there are other ways of organizing a discussion around the aspects and varieties of ICT. In addition, one could argue that there is some overlap between the categories; for example, software programs with design characteristics that would enable them to be used as tutor or exploratory programs, or as tutor and diagnostic programs. The use of mean’s four types of learning with technology plus assessment and management purposes was used simply as an organizational device within which broad issues of ICT and SEN might be considered. Providing access to technology to schools is not the same as making sure every learner has access. Access might require adaptations to accommodate different learners. In addition, these adaptations might involve one or more of the types of learning with technology discussed above are right to point out that ICT is not a single entity but refers to a set of technologies. Moreover, ICT offers distinct opportunities and challenges to learners with disabilities and special educational needs. The challenges include the adaptations that may have to be made for learners to acquire or use the tools of technology. The opportunities lie in the way that technology can then be used to perfect the effects of what would otherwise create a barrier to learning or participation in an interactive activity. A study took place in Finland to assess student characterises expertise in computing sector in secondary school, Figure 1, Represents results in scores which indication the expertise of a student using ICT in school and college, and how advance they learn. This result outcome from a study that was examined how each student interact with ICT and notice their expertise on how advance they can understand. The data of this study consisted of ICT-related activities and task, self-evaluation questionnaires, interest in ICT, and classroom observations. (Liisa Ilomäki, 2007)5.3 Future strategy & Personal Reflection
NEED TO FINISHBibliography
Abdul Wahid, Y. S. M., 2015. Toward Constructing a Secure Online Examination System. 08-10 Jan. Carnegie Mellon University , 2012. SOFTWARE SYSTEM INTEGRATION. [Online] Available at: http://www.sei.cmu.edu/productlines/frame_report/softwareSI.htm [Accessed 2017]. Carroll, J. M., 2015. The Encyclopedia of Human-Computer Interaction, 2nd Ed. Cluskey Jr., G. R., Ehlen, C. R. & Raiborn, M. H., 2011. Thwarting online exam cheating without proctor supervision. Journal of Academic & Business Ethics, July, Volume 4, p. 1. Henry Lieberman, F. P. M. K. A. V. W., 2006. END-USER DEVELOPMENT: AN EMERGING PARADIGM. ISAZADEH, A., 2004. SOFTWARE ENGINEERING: INTEGRATION. Applied and Computational Mathematics, 3(1), pp. 56-66. Joint Council for Qualifications, 2016. Access Arrangements, Reasonable Adjustments and Special Consideration - JCQ Joint Council for Qualifications. [Online] Available at: http://www.jcq.org.uk/exams-office/access-arrangements-and-special-consideration Liisa Ilomäki, P. R., 2007. Intensive use of ICT in school: Developing differences in students’ ICT expertise. January, 48(1), pp. 116-136. Mann, S., 2012. Guide to integration architecture. [Online] Available at: http://searchmicroservices.techtarget.com/feature/Guide-to-integration-architecture Mohammad A Sarrayrih, M. I., 2013. Challenges of Online Exam, Performances and problems for Online University Exam. 10(1), pp. 439-443. Murphy, J. & Zwieback, w. D., 2005. Managing Emerging Security Threats. [Online] Available at: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.102.7018&rep=rep1&type=pdf [Accessed 2017]. Ng, W. R. a. P. A., 1991. Some thoughts on systems integration: A conceptual framework. Journal of Systems Integration, 1(1), pp. 97-114. O'Malley, K., n.d. 4 Common Types of Tests Teachers Give (and Why). [Online] Available at: https://www.noodle.com/articles/4-types-of-tests-teachers-give-and-why [Accessed 27 Oct 2015]. Open University, 2004. ICT and special educational needs. s.l.:s.n. Rouse, M., 2016. Content Management System (CMS). [Online] Available at: http://searchcontentmanagement.techtarget.com/definition/content-management-system-CMS [Accessed 2017]. Techopedia, 2017. System Integration (SI). [Online] Available at: https://www.techopedia.com/definition/9614/system-integration-si [Accessed 25 January 2017]. Yuan, R. E. a. F., 2004. THE EFFECTS OF PLANNING ON FLUENCY, COMPLEXITY, AND ACCURACY IN SECOND LANGUAGE NARRATIVE WRITING. March, 26(1), pp. 59-84.Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Technology"
Information Technology refers to the use or study of computers to receive, store, and send data. Information Technology is a term that is usually used in a business context, with members of the IT team providing effective solutions that contribute to the success of the business.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




