Recency, Frequency and Monetary Information Mining
Info: 11928 words (48 pages) Dissertation
Published: 16th Dec 2019
Tagged: Information Technology
1.INTRODUCTION
RFM remains for Recency, Frequency and Monetary esteem. RFM investigation is a promoting procedure utilized for dissecting client conduct, for example, how as of late a client has acquired (Recency), how frequently the client buys (recurrence), and how much the client burns through (financial). It is a helpful strategy to enhance client division by partitioning clients into different gatherings for future personalization benefits and to recognize clients who will probably react to advancements. Lately, information mining applications in view of RFM ideas have additionally been proposed for various zones, for example, for the PC security (Kim et al., 2010), for car industry (Chan, 2008) and for the gadgets business (Chiu et al., 2009).
Research instances of information mining with RFM factors incorporate distinctive information mining methods, for example, neuralnetwork and choice tree (Olson et al., 2009), harsh set hypothesis (Cheng and Chen, 2009), self sorting out guide (Li et al., 2008), CHAID (McCarty and Hastak, 2007), hereditary calculation (Chan, 2008) and consecutive example mining (Chen et al., 2009; Liu et al., 2009). Mix of RFM investigation and information mining systems gives valuable data to present and new clients.
Classification rules found from client statistic factors and RFM factors gives helpful learning to directors to foresee future client conduct, for example, how as of late the client will likely buy, how frequently the client will buy, and what will the estimation of his/her buys. Affiliation administer mining in view of RFM measures breaks down the connections of item properties and clients’ commitments/loyalties to give a superior suggestion to fulfill clients’ needs.
Recency = 10 – the quantity of months that have gone since the client last obtained
Recurrence = number of buys over the most recent a year (greatest of 10)
Money related = estimation of the most noteworthy request from a given client (benchmarked against $10k)
On the other hand, one can make classes for each trait. For example, the Recency quality may be broken into three classifications: clients with buys inside the most recent 90 days; in the vicinity of 91 and 365 days; and longer than 365 days. Such classes might be landed at by applying business standards, or utilizing an information mining procedure, for example, http://en.wikipedia.org/wiki/CHAIDCHAID, to discover significant breaks.
Once every one of the traits has fitting classes characterized, fragments are made from the convergence of the qualities. In the event that there were three classifications for each property, at that point the subsequent grid would have twenty-seven conceivable blends (one surely understood business approach utilizes five canisters for every qualities, which yields 125 fragments). Organizations may likewise choose to fall certain subsegments, if the degrees show up too little to be in any way valuable. The subsequent sections can be requested from most important (most noteworthy recency, recurrence, and esteem) to minimum profitable (least recency, recurrence, and esteem). Recognizing the most important RFM portions can profit by chance connections in the information utilized for this investigation. Hence, it is profoundly prescribed that another arrangement of information be utilized to approve the aftereffects of the RFM division process.
Promoters of this method bring up that it has the ethicalness of straightforwardness: no particular measurable programming is required, and the outcomes are promptly comprehended by representatives. Without other focusing on procedures, it can give a lift accordingly rates for advancements.
RFD – Recency, Frequency, Duration is a changed variant of RFM examination that can be utilized to break down customer conduct of viewership/readership/surfing focused business items. (For instance, measure of time spent by surfers)
RFE – Recency, Frequency and Engagement is a more extensive form of the RFD investigation, where Engagement can be characterized to incorporate visit length, pages per visit or other such measurements. It can be utilized to break down buyer conduct of viewership/readership/surfing focused business items.
The objectives of the analysis were to:
- Identify patterns of migration from RFM cell to cell over time.
- Determine the extent to which customer migration patterns fell into discernible clusters
- Identify investment and marketing strategies appropriate to each migration cluster.
- Assess the effectiveness of RFM migration vs. other segmentation and targeting strategies available for marketing promotions.
1.1PURPOSE OF THE PROJECT
The primary reason for setting up this record is to give a general understanding in analysis and necessities of the current framework or circumstance and for deciding the working qualities of the framework.
By this RFM
- model we can divide the customers based on RFM.
- Because of this RFM model we can give more advantages for permanent customer.
1.2PROBLEMS IN EXISTING SYSTEM
The main problem in the existing system is for every user we are giving the same discount. But there is no special discount for the regular consumers and also there is no separate discount for the high paid customers.
In the existing system, all the customers who purchase the products in a particular website are treated universally equal with respect to providing discounts and coupons.
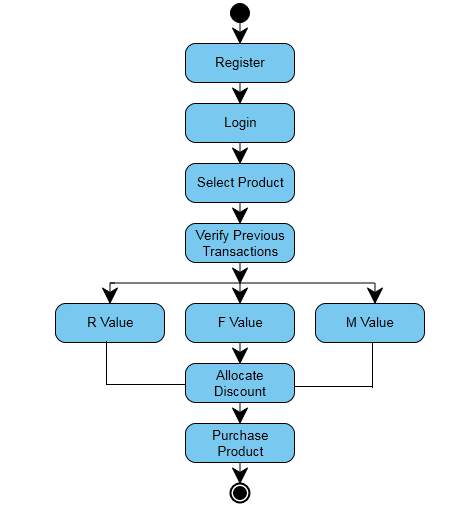
In the existing system, there are some faults regarding the categorization of the customers whereas in the proposed system, customers are categorized into eight segments considering their ‘R’,’F’,’M’ values.
- PROPOSED SYSTEM
Coordination of RFM examination and information mining procedures gives helpful data to present and new clients. Grouping in view of RFM characteristics gives more behavioral information of clients’ genuine showcasing levels than other bunch investigations. Arrangement rules found from client statistic factors and RFM factors gives helpful learning to directors to foresee future client conduct, for example, how as of late the client will presumably buy, how frequently the client will buy, and what will the estimation of his/her buys. Affiliation lead mining in view of RFM measures dissects the connections of item properties and clients’ commitments/loyalties to give a superior proposal to fulfill clients’ needs.
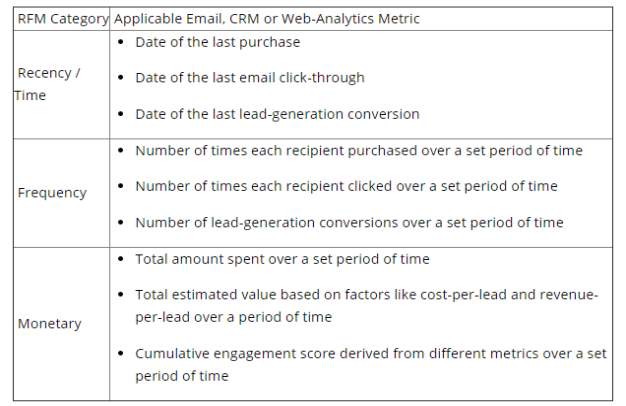
Table 1: RFM Based Relationship
- . SCOPE OF THE PROJECT
RFM (recency, recurrence, money related) investigation is a showcasing method used to decide quantitatively which clients are the best ones by looking at how as of late a client has acquired (recency), how frequently they buy (recurrence), and how much the client burns through (fiscal). RFM investigation depends on the promoting maxim that “80% of your business originates from 20% of your clients.”
For over 30 years, coordinate mailing advertisers for non-benefit associations have utilized a casual RFM investigation to focus on their mailings to clients well on the way to make gifts. The thinking behind RFM was basic: individuals who gave used to probably give once more. With the approach of http://whatis.techtarget.com/test/Quiz-E-mail-Marketing-and-the-Spam-Probleme-mail advertising efforts and http://searchcrm.techtarget.com/definition/CRMcustomer relationship administration programming, RFM appraisals have turned into an essential instrument.
- SOFTWARE REQUIREMENT SPECIFICATIONS
2.1. REQUIREMENTS SPECIFICATION DOCUMENT
A Software requirements specification (SRS), is a requirements specification for a software system, is a complete description of the behavior of a system to be developed and may include a set of use cases that describe interactions the user will have with the software. In addition it also contains one of the nonfunctional requirements. Non-functional requirements impose constraints on the design or implementation
The Requirements are broadly divided into two groups:
Functional requirements
Non-functional requirements
2.1.1. FUNCTIONAL REQUIREMENTS
Functional requirements consist of the following
- Registering the user
- Selecting the product
- User going for the purchase
- Calculating the discount based on RFM
2.1.2NON-FUNCTIONAL REQUIREMENTS
The non-functional requirements consist of:
Analysis and Design
The Analysis of the system is done in each and every phase. Designs are developed by using Android concept which includes the user interface, which consists of buttons, text view, listview and spinner, etc.
Maintainability
Every one of the modules must be plainly separate to enable diverse UIs to be produced in future. Through keen and powerful programming designing, all means of the product improvement process will be all around archived to guarantee practicality of the item for the duration of its life time. All advancement will be furnished with great documentation
Execution
The reaction time, usage and throughput conduct of the framework. Care is taken in order to guarantee a framework with relatively elite.
Ease of use
The convenience and preparing the end clients of the framework is ease of use. Framework ought to have characteristics like-learning capacity, effectiveness, influence, control. The fundamental point of the undertaking is to build the extent of page originator to outline a page and to diminish the adjust of the software engineer.
Modifiability : The simplicity with which a product framework can oblige changes to its product is modifiability. Our task is effectively versatile for changes that is valuable for the application to withstand the necessities of the clients.
Portability:The capacity of the framework to keep running under various figuring situations. Nature writes can be either equipment or programming, yet is generally a mix of two.
Reusability
The degree to which existing application can be reused in new application. Our application can be reused various circumstances with no specialized challenges.
Security
The variables that shield the product from unplanned or malevolent access, utilize, adjustment, annihilation, or divulgence. Security can be guaranteed as the undertaking includes verifying the clients.
2.2.SOFTWARE REQUIREMENTS
- Java 7.0
- Net Beans
- J2EE
- MySQL 5.5
- Apache tomcat 7.0
2.3.HARDWARE REQUIREMENTS
- Pentium 4 Processor
- Minimum 1 GB RAM
- 80 GB HDD
- Internet connectivity
3.SYSTEMARCHITECTURE
ARCHITECTURE DIAGRAM:
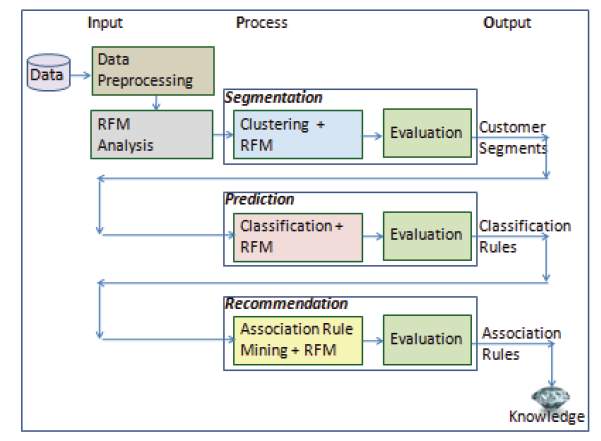
- MODULES OF THE SYSTEM
MODULE-1(User Verification)
Description and priority
User enters username and password and gets validation with the database. The module-1 has first and high priority. If it was a new user then user has to register.The first module deals with Registration and login validation. The registration details are stored in the database and whenever the user logs in, the user credentials are retrieved to check whether the user is an authorized user or not.
MODULE-2 (Consumer Selection Process)
Description:
In this module user after login into the system he can view the products available for consumers to purchase. User/Consumer can select the product he needed.
MODULE-3(Estimation of Recncy)
Description:
Recency(R) can be calculated by the formulae, present purchase date-previous purchase date. Rating for the ‘R’ value is given as the following,
| Present-Previous purchase date(in hours) | Rating |
| 0 | 5 |
| 1 | 4 |
| 2 | 3 |
| 3 | 2 |
| >=4 | 1 |
Table 2:Estimation of Recency
MODULE-4 (Frequency Calculation)
Description:
Frequency(F) can be calculated by the formulae,Max no of purchases among all customers/time.
For example: if we consider 10 as Max no of purchases and time as 5 days then we get, Frequency as 2 then the rating is given as,
| Frequency | Rating |
| >=10 | 5 |
| 8 | 4 |
| 6 | 3 |
| 4 | 2 |
| 2 | 1 |
Table:3:Frequency Calculation
MODULE-5 (Finding Of Monetary)
Description:
Monetary value(M) can be calculated as,Find the sum of all the purchases made by the customer. Find the maximum value among the sum of customers. Max.sum of monetary values/time
For example: if we consider 10,000 as Max. Sum of purchases and time as 5 days then we get, monetary value as 2000 then the rating is given as,
| Monetary value | Rating |
| >=10000 | 5 |
| 8000 | 4 |
| 6000 | 3 |
| 4000 | 2 |
| 2000 | 1 |
Table 4: Finding Of Monetary
MODULE-6 (Consumer Clusterring)
Description:
Clients with a general high RFM score speak to the best clients. Clients who have a high general RFM score however a recurrence score of 1 are new clients. The organization can give exceptional offers to these clients keeping in mind the end goal to expand their visits. RFM score can be investigated together with the items they buy to configuration very focused on offers for every client segment.
| RFM Pattern | Customer type |
| R>=3,F>=3,M>=3 | Best |
| R>=3,F<3,M>=3 | Valuable |
| R>=3,F>=3,M<3 | Shopper |
| R>=3,F<3,M<3 | First Time |
| R<3,F>=3,M>=3 | Churn |
| R<3,F>=3,M<3 | Frequent |
| R<3,F<3,M>=3 | Spenders |
| R<3,F<3,M<3 | Uncertain |
Table 5:Consumer ClusterringDiscount is decides by organization.
4.SYSTEM DESIGN
4.1.INTRODUCTION:-
Programming configuration sits at the specialized bit of the product designing procedure and is connected paying little mind to the improvement worldview and zone of use. Configuration is the initial phase in the advancement stage for any designed item or framework.
The’s architect will likely deliver a model or portrayal of an element that will later be constructed. Starting, once framework necessity have been determined and dissected, framework configuration is the first of the three specialized exercises – outline, code and test that is required to fabricate and confirm programming.
The significance can be expressed with a solitary word “Quality”. Configuration is where quality is cultivated in programming improvement. Configuration gives us portrayals of programming that can evaluate for quality. Configuration is the main way that we can precisely make an interpretation of a client’s view into a completed programming item or framework. Programming configuration fills in as an establishment for all the product building steps that take after. Without a solid outline we chance building a precarious framework – one that will be hard to test, one whose quality can’t be evaluated until the last stage.
Amid plan, dynamic refinement of information structure, program structure, and procedural points of interest are created checked on and recorded. Framework configuration can be seen from either specialized or venture administration point of view.
From the specialized perspective, plan is involved four exercises – engineering outline, information structure plan, interface plan and procedural outline.
4.2. E-R DIAGRAMS:
- The connection upon the framework is structure through an applied ER-Diagram, which indicates the existential elements as well as the standard relations through which the framework exists and the cardinalities that are essential for the framework state to proceed.
- The element Relationship Diagram (ERD) delineates the connection between the information objects. The ERD is the documentation that is utilized to lead the date demonstrating movement the traits of every datum protest noted is the ERD can be portrayed leave an information question portrayals.
- The arrangement of essential segments that are distinguished by the ERD are
- Information objectRelationships
- AttributesVarious kinds of pointers.
- The main role of the ERD is to speak to information objects and their connections.The set of primary components that are identified by the ERD are
Data object Relationships
Attributes Various types of indicators.
The primary purpose of the ERD is to represent data objects and their relationships.
4.3. UML DIAGRAMS:-
Unified Modeling Language (UML)
- The Unified Modeling Language (UML) is one of the most exiting tools in the world of system development.
- The Brought together displaying Language permits the product designer to express an investigation show utilizing the demonstrating documentation that is represented by an arrangement of syntactic semantic and down to earth rules.
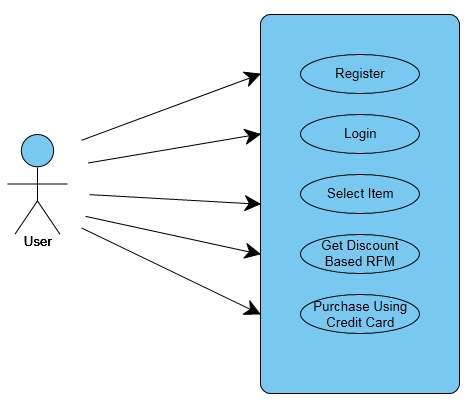
4.3.1 USE CASE DIAGRAM:
- An utilization case chart at its least difficult is a portrayal of a client’s connection with the framework that demonstrates the connection between the client and the distinctive http://en.wikipedia.org/wiki/Use_Caseuse casesin which the client is included. An utilization case chart can recognize the diverse kinds of clients of a framework and the distinctive utilize cases and will frequently be joined by different sorts of graphs as well.
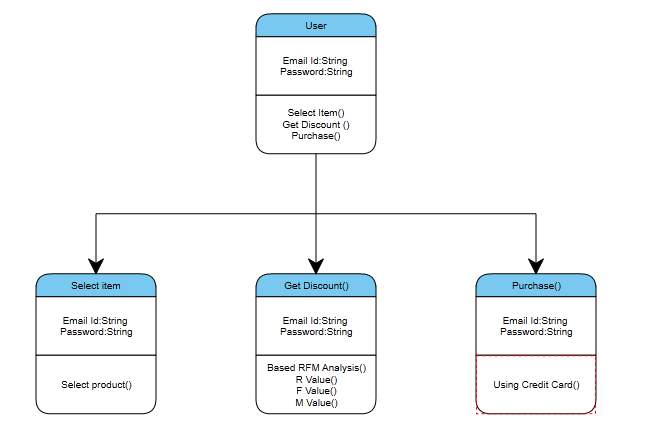
4.3.2. CLASS DIAGRAM:
- A class is a classification or gathering of things that have comparative qualities and regular conduct a rectangle is a icon that represents a class. It is divided into three areas the upper most area contains the name, the middle area holds the Attributes and the lower area shows the operations.
- A class diagram consists of a number of these rectangle connected by the lines that show the classes relate to one another. Class diagrams describe the structure of the system. Class charts depict the structure of the framework. Classes are reflection that determines the regular structure and conduct of set of items.
- Class charts depict the framework as far as items, classes, properties, activities and their affiliations
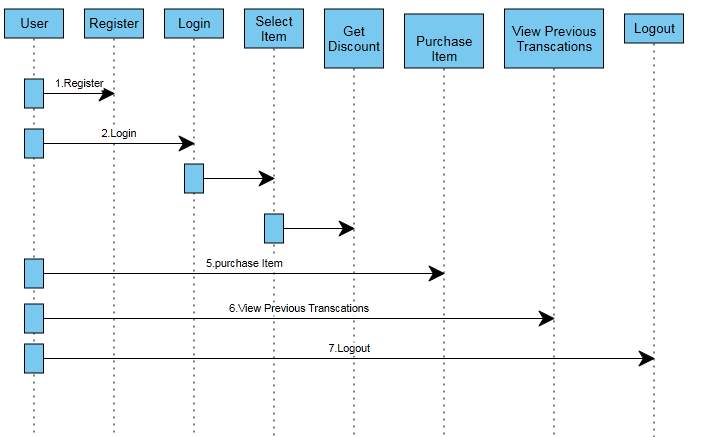
4.3.3. SEQUENCE DIAGRAM:
- The Sequence diagram shows then time based dynamics of the interaction. grouping graph comprises of articles spoke to in the typical route as named rectangles (with underline messages), messages spoke to as strong line bolts and time spoke to as vertical movement.
- For the most part these are utilized to formalize the conduct of the framework and to imagine the correspondence among the items, they are helpful for distinguishing extra protests that take part in the utilization cases. A succession chart speaks to the connection that happen among these articles.
State Diagram:
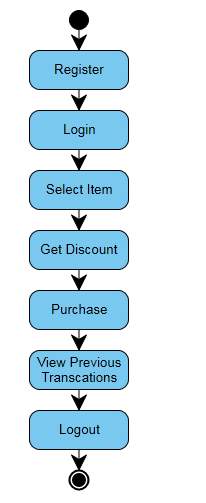
4.3.4 ACTIVITY DIAGRAM
Activity diagrams are graphical representations of workflows of stepwise activities and actions with support for choice, iteration and concurrency. In the Demonstrating Language, action graphs are planned to display both computational and hierarchical procedures (i.e. work processes). Action charts demonstrate the general stream of control.
Action graphs are built from a predetermined number of shapes, associated with bolts.
The most vital shape composes:
adjusted rectangles speak to activities;
jewels speak to choices;
bars speak to the begin (split) or end (join) of simultaneous exercises;
a dark circle speaks to the begin (introductory state) of the work process;
A surrounded dark circle speaks to the end (last state).
5. TECHNOLOGIES / PLATFORMS USED
5.1 JAVA
Why Java?
The Java programming dialect is an abnormal state dialect that can be portrayed by the majority of the accompanying trendy expressions:
|
|
|
|
|
|
|
|
|
|
Every one of the previous popular expressions is clarified in The Java Language Environment , a white paper composed by James Gosling and Henry McGilton.
In the Java programming dialect, all source code is first composed in plain content documents finishing with the .java augmentation. Those source records are then ordered into .class documents by the javac compiler. A .class record does not contain code that is local to your processor; it rather contains bytecodes — the machine dialect of the Java Virtual Machine http://java.sun.com/docs/books/instructional
exercise/getStarted/introduction/definition.html1 (Java VM). The java launcher instrument at that point runs your application with a case of the Java Virtual Machine.
An outline of the product improvement process.
Since the Java VM is accessible on a wide range of working frameworks, the same .class records are equipped for running on Microsoft Windows, the Solaris TM Operating System (Solaris OS), Linux, or Mac OS. Some virtual machines, for example, thehttp://java.sun.com/items/hotspot/Java Hotspot virtual machine, play out extra strides at runtime to give your application an execution help. This incorporates different assignments, for example, discovering execution bottlenecks and recompiling (to local code) as often as possible utilized segments of code.
What is Java EE?
Java EE (Enterprise Edition) is a broadly utilized stage containing an arrangement of facilitated advances that fundamentally decrease the cost and unpredictability ofdeveloping, conveying, and overseeing multi-level, server-driven applications. Java EE expands upon the Java SE stage and gives an arrangement of APIs (application programming interfaces) for creating and running versatile, hearty, adaptable, solid and secure server-side applications.Some of the key segments of Java EE include:
Endeavor JavaBeans (EJB): an oversaw, server-side segment engineering used to embody the business rationale of an application. EJB innovation empowers quick and rearranged advancement of appropriated, value-based, secure and versatile applications in view of Java innovation.
Java Persistence API (JPA): a system that enables engineers to oversee information utilizing object-social mapping (ORM) in applications based on the Java Platform.
5.2. SERVLETS:
Servlets give a part based, stage free strategy for building Web-based applications, without the execution restrictions of CGI programs. Servlets approach the whole group of Java APIs, including the JDBC API to get to big business databases.
Java Servlets are programs that keep running on a Web or Application server and go about as a center layer between a solicitations originating from a Web program or other HTTP customer and databases or applications on the HTTP server.Using Servlets, you can gather enter from clients through website page frames, display records from a database or another source, and make site pages progressively.
Servlets can be made utilizing thejavax.servlet and javax.servlet.httppackages, which are a standard piece of the Java’s endeavor release, an extended variant of the Java class library that backings substantial scale improvement projects.These classes execute the Java Servlet and JSP details. At the season of composing this instructional exercise, the variants are Java Servlet 2.5 and JSP 2.1.
5.3 JDBC:
Origin of JDBC
JDBC is not a new query language. It is a simply a java object interface (communication) to SQL. Our applications use JDBC to forward SQL statements to a DBMX. We compose SQL articulations in a java program to perform database inquiries and updates. We can consider JDBC only a java SQL wrapper. JDBC does not upgrade or decrease the energy of SQL. It’s essentially an instrument for submitting SQL proclamations. JDC can deal with effortlessly the controls like associating with a database, recovering question comes about, conferring or rolling back transactions.
JDBC is based on the X/Open SQL CLI (Call Level Interface), which is also the basis for Microsoft’s ODBC interface. The CLI is not a new query language. It is simply a procedural interface to SQL.
JDBC Drivers
JDBC drivers are either immediate or ODBC connected direct driver sits over the DBMS’s local interface. For instance, Symantec gives guide drivers to Oracle 7.X utilizing ODBC. IBM additionally gives a local JDBC driver to its DB2 items coordinate means no exchanges will be done between a JDBC program and the database. This will be speedier and utilized as a part of continuous condition.
Rather than coordinate drivers, spanned drivers are based on the highest point of existing ODBC drivers. JDBC is made after ODBC. Thusly, there exists an interpretation between these the two conventions. These kinds of extension drivers are moderate in correspondence. Java Soft and Intersolve give JDBC to ODBC connect drivers that make it less demanding to decipher amongst JDBC and the different ODBC drivers. Therefore, the JDBC applications, we compose are ensured to be convenient crosswise over multi seller DBMS. That is, a JDBC program is both stage autonomous and information base-free.
Every one of the classes and interfaces required for composing a JDBC program are incorporated into java.sql bundle. The java.sql bundle is provided with the center jdk programming itself. JDBC drivers give usage to these classes and interfaces of java.sql bundle. The other obligation of drivers is to keep up exchange unwavering quality. The drivers must give the required synchronization assurance.
Java Database Connectivity (JDBC)
JDBC is an arrangement of classes and Interface utilized to connect to a database utilizing applications created in Java dialect. To get an association with the database, a Driver, which is the usage of JDBC API stacked. This driver is utilized to make a Statement, which is a question used to execute SQL inquiries. Aftereffect of an announcement is put away as ResultSet.
JDBC remains for Java Database Connectivity, which is a standard Java API for database-autonomous availability between the Java programming dialect and an extensive variety of databases.
The JDBC library incorporates APIs for every one of the assignments specified beneath that are usually connected with database utilization.
Making an association with a database.
Making SQL or MySQL proclamations.
Executing SQL or MySQL questions in the database.
Review and Modifying the subsequent records.
5.4. JSP:
Java Server Pages (JSP) is a server-side programming technology that enables the creation of dynamic, platform-independent method for building Web-based applications. JSP approach the whole group of Java APIs, including the JDBC API to get to big business databases. This instructional exercise will show you how to utilize Java Server Pages to build up your web applications in basic and simple advances.
A JavaServer Pages segment is a sort of Java servlet that is intended to satisfy the part of a UI for a Java web application. Web engineers compose JSPs as content records that join HTML or XHTML code, XML components, and inserted JSP activities and orders. Utilizing JSP, you can gather include from clients through page frames, display records from a database or another source, and make website pages powerfully.
JSP labels can be utilized for an assortment of purposes, for example, recovering data from a database or enrolling client inclinations, getting to JavaBeans parts, passing control amongst pages and sharing data between demands, pages etc.
JSP Processing: The accompanying advances clarify how the web server makes the site page utilizing JSP:
Similarly as with a typical page, your program sends a HTTP ask for to the web server.
The web server perceives that the HTTP ask for will be for a JSP page and advances it to a JSP motor. This is finished by utilizing the URL or JSP page which closes with .jspinstead of .html.
The JSP motor loads the JSP page from circle and changes over it into a servlet content. This change is exceptionally straightforward in which all format content is changed over to println( ) articulations and all JSP components are changed over to Java code that executes the comparing dynamic conduct of the page.
The JSP motor incorporates the servlet into an executable class and advances the first demand to a servlet motor.
A piece of the web server called the servlet motor loads the Servlet class and executes it. Amid execution, the servlet produces a yield in HTML arrange, which the servlet motor goes to the web server inside a HTTP reaction.
The web server advances the HTTP reaction to your program as far as static HTML content.
At long last web program handles the progressively created HTML page inside the HTTP reaction precisely as though it were a static page.
APACHE TOMCAT:
Apache Tomcat is an open-source web server and servlet container developed by the Apache Software Foundation (ASF). Tomcat implements several Java EE specifications including Java Servlet, JavaServer Pages (JSP), Java EL, and WebSocket, and provides a “pure Java” HTTP web server environment for Java code to run in.
Apache is created and kept up by an open group of engineers under the sponsorship of the Apache Software Foundation, discharged under the http://en.wikipedia.org/wiki/Apache_LicenseApache License 2.0 permit, and is http://en.wikipedia.org/wiki/Open-source_softwareopen-source programming.
Catalina is Tomcat’s http://en.wikipedia.org/wiki/Web_containerservlet container.Catalina actualizes http://en.wikipedia.org/wiki/Sun_MicrosystemsSun Microsystems’ determinations for http://en.wikipedia.org/wiki/Java_servletservlet and http://en.wikipedia.org/wiki/JavaServer_PagesJava Server Pages (JSP). In Tomcat, a Realm component speaks to a “database” of usernames, passwords, and parts (like Unix gatherings) doled out to those clients. Diverse executions of Realm enable Catalina to be incorporated into conditions where such verification data is now being made and kept up, and after that utilization that data to actualize Container Managed Security as depicted in the Servlet Specification.
JavaScript and Ajax Development
JavaScript is a question situated scripting dialect principally utilized as a part of customer side interfaces for web applications. Ajax (Asynchronous JavaScript and XML) is a Web 2.0 system that enables changes to happen in a page without the need to play out a page invigorate. JavaScript toolboxs can be utilized to actualize Ajax-empowered parts and usefulness in website pages.
5.6 MySQL:
MySQL, the most prevalent Open Source SQL database administration framework, is created, conveyed, and upheld by Oracle Corporation. The MySQL Web website (http://www.mysql.com/) gives the most recent data about MySQL programming.
MySQL is a database administration framework. A database is an organized accumulation of information. It might be anything from a straightforward shopping rundown to a photo exhibition or the huge measures of data in a corporate system. To include, access, and process information put away in a PC database, you require a database administration framework, for example, MySQL Server. Since PCs are great at dealing with a lot of information, database administration frameworks assume a focal part in registering, as independent utilities, or as parts of different applications.
MySQL databases are social. A social database stores information in discrete tables as opposed to putting every one of the information in one major storeroom. The database structures are sorted out into physical documents streamlined for speed. The coherent model, with articles, for example, databases, tables, perspectives, lines, and sections, offers an adaptable programming condition. You set up rules administering the connections between various information fields, for example, balanced, one-to-many, extraordinary, required or discretionary, and “pointers” between various tables. The database upholds these tenets, so that with a very much planned database, your application never observes conflicting, copy, vagrant, outdated, or missing information.
The SQL part of “MySQL” remains for “Organized Query Language”. SQL is the most widely recognized institutionalized dialect used to get to databases. Contingent upon your programming condition, you may enter SQL straightforwardly (for instance, to create reports), insert SQL articulations into code written in another dialect, or utilize a dialect particular API that shrouds the SQL linguistic structure.
MySQL programming is Open Source. Open Source implies that it is feasible for anybody to utilize and change the product. Anyone can download the MySQL programming from the Internet and utilize it without paying anything. On the off chance that you wish, you may contemplate the source code and change it to suit your necessities. The MySQL programming utilizes the GPL
The MySQL Database Server is quick, dependable, adaptable, and simple to utilize. In the event that that is the thing that you are searching for, you should try it out. MySQL Server can run easily on a work area or PC, close by your different applications, web servers, et cetera, requiring practically zero consideration. In the event that you devote a whole machine to MySQL, you can modify the settings to exploit all the memory, CPU power, and I/O limit accessible.
MySQL can likewise scale up to bunches of machines, arranged together. You can discover an execution correlation of MySQL Server with other database chiefs on our benchmark page.
MySQL Server was initially created to deal with vast databases considerably quicker than existing arrangements and has been effectively utilized as a part of very requesting generation conditions for quite a while. Albeit under steady improvement, MySQL Server today offers a rich and helpful arrangement of capacities. Its availability, speed, and security make MySQL Server profoundly suited for getting to databases on the Internet.
MySQL Server works in customer/server or inserted frameworks. The MySQL Database Software is a customer/server framework that comprises of a multi-strung SQL server that backings diverse backends, a few distinctive customer projects and libraries, authoritative devices, and an extensive variety of use programming interfaces (APIs).
We additionally give MySQL Server as an implanted multi-strung library that you can connect into your application to get a littler, speedier, simpler to-oversee independent item.
A lot of contributed MySQL programming is accessible. MySQL Server has a commonsense arrangement of highlights created in close participation with our clients. It is likely that your most loved application or dialect underpins the MySQL Database Server.
5.7. NET BEANS:
NetBeans is a http://en.wikipedia.org/wiki/Software_developmentsoftware improvement stage written in http://en.wikipedia.org/wiki/Java_(programming_language)Java. The NetBeans http://en.wikipedia.org/wiki/Platform_(computing)Platform enables applications to be created from an arrangement of particular http://en.wikipedia.org/wiki/Software_componentsoftware segments called modules. Applications in light of the NetBeans Platform, including the NetBeans http://en.wikipedia.org/wiki/Integrated_development_environmentintegrated advancement condition (IDE), can be reached out by http://en.wikipedia.org/wiki/Third_party_developerthird party designers.
NetBeans IDE 6.8 is the primary IDE to give finish support of Java EE 6 and the http://en.wikipedia.org/wiki/GlassFish” o “GlassFishGlassFish Enterprise Server v3. Designers facilitating their open-source extends on http://en.wikipedia.org/wiki/Project_Kenaikenai.com moreover advantage from texting and issue following incorporation and route right in the IDE, bolster for web application advancement with PHP 5.3 and the Symfony structure, and enhanced code fruition, layouting, indications and route in JavaFXprojects.NetBeans IDE 6.9, discharged in June 2010, included help for http://en.wikipedia.org/wiki/OSGi” o “OSGiOSGi, http://en.wikipedia.org/wiki/Spring_FrameworkSpring Framework 3.0, Java EE reliance infusion (JSR-299), http://en.wikipedia.org/wiki/Zend_Framework” o “Zend FrameworkZend Framework for http://en.wikipedia.org/wiki/PHPPHP, and less demanding code route, (for example, “Is Overridden/Implemented” comments), organizing, insights, and refactoring over a few dialects.
http://en.wikipedia.org/wiki/Software_frameworkFramework for rearranging the improvement of http://en.wikipedia.org/wiki/Java_SwingJava Swing work area applications.The NetBeans IDE package for Java SE contains what is expected to begin creating NetBeans modules and NetBeans Platform based applications; no extra SDK is required.Applications can introduce modules powerfully. Any application can incorporate the Update Center module to enable clients of the application to download http://en.wikipedia.org/wiki/Digital_signaturedigitally marked overhauls and new highlights specifically into the running application. Reinstalling an update or another discharge does not drive clients to download the whole application once more.
The stage offers reusable administrations normal to work area applications, enabling engineers to center around the rationale particular to their application. Among the highlights of the stage are:
UI administration (e.g. menus and toolbars)
Client settings administration
Capacity administration (sparing and stacking any sort of information)
Window administration
NetBeans IDE is a free, open-source, cross-stage IDE with worked in-bolster for Java Programming Language
6. TESTING
6.1 Presentation:
Programming testing is a basic component of programming quality confirmation and speaks to a definitive audit of determination, plan and coding. The expanding perceivability of programming as a framework component and orderly expenses related with a product disappointment are persuading factors for we arranged, through testing. Testing is the way toward executing a program with the goal of finding a mistake. The plan of tests for programming and other built items can be as trying as the underlying outline of the item itself.
There of essentially two sorts of testing approaches.
One is Black-Box testing – the specifiedfunctionthataproducthasbeen planned toperform,tests can be conductedthatdemonstrateeachfunctionisfully worked.
TheotherisWhite-Boxtesting – knowingtheinternalworkingsoftheproduct,testscanbeconductedtoensurethattheinternal activity oftheproductperforms accordingtospecifications andallinternalcomponentshavebeenadequately worked out.
White boxandBlack boxtestingmethods have been utilized to test this package.The whole loopconstructshave been tried for their limit and middle of the road conditions. Thetest information was designedwith aviewtocheckfor allthe conditions and logicaldecisions.Errorhandlinghasbeentakencareof bytheuseofexceptionhandlers.
6.2 STRATEGIES:
Testing is an arrangement of exercises that can be arranged in cutting edge and directed systematically.A procedure for programming testing must settlement low-level tests that are important to check that a little source code section has been accurately executed and in addition abnormal state tests that approve real framework capacities against client prerequisites.
Programming testing is one component of confirmation and validation.Verification alludes to the arrangement of exercises that guarantee that product accurately actualizes as particular function.Validation alludes to an alternate arrangement of exercises that guarantee that the product that has been constructed is traceable to client necessities.
The fundamental goal of programming is trying to reveal errors.To satisfy this goal, a progression of test steps unit, coordination, approval and framework tests are arranged and executed.Each test step is refined through a progression of precise test system that aid the outline of test cases.With each testing venture, the level of reflection with which programming is considered is expanded.
Testing is the best way to guarantee the nature of programming and it is an umbrella action instead of a different stage. This is an action to be preformed in parallel with the product exertion and one that comprises of its own periods of investigation, outline, usage, execution and support.
6.3 UNIT TESTING
This testing strategy considers a module as single unit and checks the unit at interfaces and speaks with different modules instead of diving into points of interest at proclamation level. Here the module will be dealt with as a discovery, which will take some information and produce output.Outputs for a given arrangement of info blend are pre-ascertained and are created by the module.
6.4 SYSTEM TESTING:
Here all the pre tried individual modules will be amassed to make the bigger framework and tests are completed at framework level to ensure that all modules are working in synchronous with each other.This testing approach helps in ensuring that all modules whichare running flawlessly when checked independently are likewise running in union with different modules.
6.5 INTEGRATED TESTING:
Testing is a noteworthy quality control measure utilized amid programming development.Its fundamental capacity is to recognize errors.Sub capacities when joined may not deliver than it is desired.Global information structures can speak to the problems.Integrated testing is a methodical system for building the program structure while leading the tests. To reveal mistakes that are related with interfacing the goal is to influence unit to test modules and manufactured a program structure that has been identified by design.In a non – incremental mix every one of the modules are consolidated ahead of time and the program is tried as a whole.Here blunders will show up in an unending circle work. In incremental testing the program is built and tried in little fragments where the blunders are segregated and redressed.
Distinctive incremental combination methodologies are top – down mix, base – up incorporation, relapse testing.
6.6 TOP-DOWN INTEGRATION TEST
Modules are coordinated by moving downwards through the control chain of importance starting with fundamental program.The subordinate modules are consolidated into structure in either an expansiveness first way or profundity first manner.This process is done in five stages:
Fundamental control module is utilized as a test pilot and steps are substituted or all modules specifically to primary program.
Contingent upon the mix approach chose subordinate is supplanted at once with genuine modules.
Tests are directed.
On consummation of each arrangement of tests another stub is supplanted with the genuine module
Relapse testing might be led to guarantee trha5t new mistakes have not been presented. This procedure ceaseless from stage 2 until the point that whole program structure is reached.Intop down combination technique basic leadership happens at upper levels in the chain of command and is experienced first.If significant control issues do exists early acknowledgments is basic.
On the off chance that profundity first mix is chosen an entire capacity of the product might be executed and illustrated.
A few issues happen when preparing at low levels in progressive system is required to enough test upper level strides to supplant low-level modules toward the start of the best down testing. So no information streams upward in the program structure.
6.7 BOTTOM-UP INTEGRATION TEST
It starts development and testing with nuclear modules.As modules are incorporated from the base up, preparing prerequisite for modules subordinate to a given levelis constantly accessible and requirement for stubs is eliminated.The following advances executes this methodology.
Low-level modules are consolidated in to bunches that play out a particular programming sub work.
A driver is composed to facilitate experiment info and yield.
Bunch is tried.
Drivers are evacuated and moving upward in program structure joins groups.
Reconciliation moves upward, the requirement for partitioned tester’s sores. On the off chance that the best levels of program structures are incorporated best down, the quantity of drivers can be decreased significantly and coordination of groups is incredibly streamlined.
6.8 TESTING
Each time another module is included as a piece of combination as the product changes. Relapse testing is a really that guarantees changes that don’t present unintended conduct as extra blunders.
Relapse testing possibly led physically by executing a subset of all experiments or utilizing mechanized catch play back apparatuses empowers the product architect to catch the experiment and results for ensuing playback and compression.The relapse suit contains distinctive classes of experiments.
6.9. IMPLEMENTATION
Implementation is the process of converting a new or revised system design into operational one.
There are three kinds of Implementation:
Usage of a PC framework to supplant a manual system.The issues experienced are changing over records, preparing clients, and confirming printouts for respectability.
Usage of another PC framework to supplant a current one.This is normally a troublesome conversion.If not legitimately arranged there can be numerous issues.
Execution of an adjusted application to supplant a current one utilizing the same computer.This sort of transformation is moderately simple to deal with, gave there are no significant changes in the records.
Implementation in Generic tool project is done in all modules. In the first module User level identification is done. In this module every user is identified whether they are genuine one or not to access the database and also generates the session for the user. Illegal use of any form is strictly avoided. In the Table creation module, the tables are created with user specified fields and user can create many tables at a time. They may specify conditions, constraints and calculations in creation of tables. The Generic code maintains the user requirements throughout the project.
In Updating module user can update or delete or Insert the new record into the database. This is very important module in Generic code project. User has to specify the field value in the form then the Generic tool automatically gives whole filed values for that particular record. In Reporting module user can get the reports from the database in 2Dimentional or 3Dimensional view. User has to select the table and specify the condition then the report will be generated for the user.
6.10 TEST CASES:
| Test Cases | Expected Output | Actual Output | Low Priority | High Priority |
| User Registration page. | User Entered details in registration page. | User entereddetails in registration page successfully. |
———— |
Yes |
| User login Page. | User entered username and password to login. | User entered login details successfully. |
———— |
Yes |
| View Product | User view products after login only. | User viewed product details successfully after login. |
———— |
Yes |
| Show discount. | When we clicked on product show discount. | By clicking on product it will show discount | —————- | Yes |
| Calculate discount | Discount should be calculated by the parameters RFM . | Discounts are calculated by using RFM values. | ————– | Yes |
| Key Sent to mail. | Credit Code Key Sent to Mail. | Key Successfully send to mail. | ————– | Yes |
| Credit card Check . | Transaction should complete after entering correct key only | Transaction Completed Successfully After Entering The security Key. | ————– | Yes |
| Wrong Key Credit Check. | Transaction Failed By Entering Invalid/wrong key. | Transaction Failed due to invalid key. | ————– | Yes |
6.11 Screen Shots:
Home screen:
Register page:
Login page:
Login Success user page;
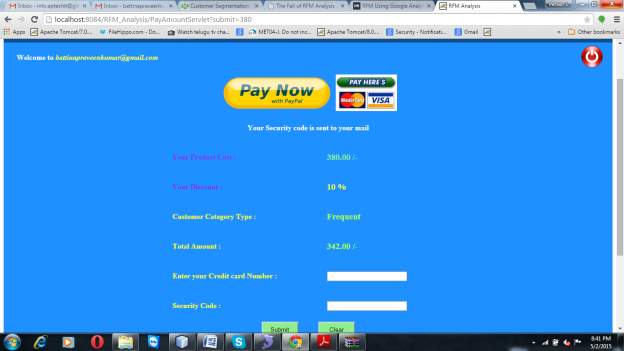
Transaction page:
Transaction failed:
6.12 Project Code:
Database Code:
packagecom.ep;
import java.sql.*;
public class DbConnection {
static Connection con;
public static Connection getConnections() {
try {
Class.forName(“com.mysql.jdbc.Driver”);
con =DriverManager.getConnection (“jdbc:mysql://localhost:3306/RFM”,”root”,”inetsolv”);
} catch (Exception e) {
e.printStackTrace();
}
return con;
}
}
Login Code:
packagecom.ep;
importjava.io.IOException;
importjava.io.PrintWriter;
importjava.sql.Connection;
importjava.sql.PreparedStatement;
importjava.sql.ResultSet;
importjavax.servlet.RequestDispatcher;
importjavax.servlet.ServletException;
importjavax.servlet.annotation.WebServlet;
importjavax.servlet.http.HttpServlet;
importjavax.servlet.http.HttpServletRequest;
importjavax.servlet.http.HttpServletResponse;
importjavax.servlet.http.HttpSession;
@WebServlet(name = “LoginCheckServlet”, urlPatterns = {“/LoginCheckServlet”})
public class LoginCheckServlet extends HttpServlet {
protected void processRequest(HttpServletRequest request, HttpServletResponse response) {
try {
String username = request.getParameter(“uname”);
String password = request.getParameter(“pwd”);
Connection con = DbConnection.getConnections();
HttpSession session = request.getSession(true);
session.setAttribute(“user”, username);
String q = “select * from register where mail=? and pwd=?”;
PreparedStatementpstmt = con.prepareStatement(q);
pstmt.setString(1, username);
pstmt.setString(2, password);
ResultSetrs = pstmt.executeQuery();
if (rs.next()) {
RequestDispatcher dispatcher = request.getRequestDispatcher(“SuccessLogin.jsp”);
dispatcher.forward(request, response);
} else {
RequestDispatcher dispatcher = request.getRequestDispatcher(“FailureLogin.jsp”);
dispatcher.forward(request, response);
}
} catch (Exception e) {
e.printStackTrace();
} finally {
}
}
RFM Analysis code:
packagecom.ep;
importjava.io.IOException;
importjava.sql.Connection;
importjava.sql.PreparedStatement;
importjava.sql.ResultSet;
importjava.util.Calendar;
importjava.util.Date;
importjava.util.GregorianCalendar;
importjava.util.Random;
importjavax.servlet.RequestDispatcher;
importjavax.servlet.ServletException;
importjavax.servlet.annotation.WebServlet;
importjavax.servlet.http.HttpServlet;
importjavax.servlet.http.HttpServletRequest;
importjavax.servlet.http.HttpServletResponse;
importjavax.servlet.http.HttpSession;
@WebServlet(name = “PayAmountServlet”, urlPatterns = {“/PayAmountServlet”})
public class PayAmountServlet extends HttpServlet {
protected void processRequest(HttpServletRequest request, HttpServletResponse response) {
try {
HttpSession session = request.getSession(true);
String user = (String) session.getAttribute(“user”);
String cost = request.getParameter(“submit”);
Integer cossst = Integer.parseInt(cost);
session.setAttribute(“cost”, cost);
//to get last purchase
Connection con = DbConnection.getConnections();
PreparedStatementpstmt = con.prepareStatement(“select * from purchase where user=?”);
pstmt.setString(1, user);
ResultSetrs = pstmt.executeQuery();
int day = 0;
int month = 0;
int year = 0;
if (rs.next()) {
rs.last();
day = rs.getInt(“day”);
month = rs.getInt(“month”);
year = rs.getInt(“year”);
}
intday_p, month_p, year_p;
GregorianCalendar date = new GregorianCalendar();
day_p = date.get(Calendar.DAY_OF_MONTH);
month_p = date.get(Calendar.MONTH);
year_p = date.get(Calendar.YEAR);
Calendar c1 = Calendar.getInstance();
c1.set(year, month, day);
Calendar c2 = Calendar.getInstance();
c2.set(year_p, month_p, day_p);
Date d1 = c1.getTime();
Date d2 = c2.getTime();
long diff = d2.getTime() – d1.getTime();
int noofdays1 = (int) (diff/(1000 * 24 * 60 * 60));
intnoofdays = noofdays1 – 1;
System.out.println(“noofdays: ” + noofdays);
//calculate R value
int R = 0;
if (noofdays == 1) {
R = 5;
}
if (noofdays == 2) {
R = 4;
}
if (noofdays == 3) {
R = 3;
}
if (noofdays == 5) {
R = 2;
} else {
R = 1;
}
//calculate F
int F = 1;
int count = 0;
PreparedStatementpstm = con.prepareStatement(“SELECT COUNT(*) FROM purchase where user=?”);
pstm.setString(1, user);
ResultSetrsf = pstmt.executeQuery();
while (rsf.next()) {
count++;
}
if (count == 1) {
F = 1;
}
if (count == 2) {
F = 2;
}
if (count == 3) {
F = 3;
}
if (count == 4) {
F = 4;
}
if (count >= 5) {
F = 5;
}
//Calculate M
intspentcost = 0;
int M = 1;
PreparedStatement pstmt1 = con.prepareStatement(“select cost from amount where user=? “);
pstmt1.setString(1, user);
ResultSet rs1 = pstmt1.executeQuery();
if (rs1.next()) {
spentcost = rs1.getInt(“cost”);
}
if (spentcost>= 1000) {
M = 1;
}
if (spentcost>= 3000) {
M = 2;
}
if (spentcost>= 5000) {
M = 3;
}
if (spentcost>= 20000) {
M = 4;
}
if (spentcost>= 50000) {
M = 5;
}
int discount = 0;
if (R >= 3 && F >= 3 && M >= 3) {
System.out.println(“1 st REM For loop”);
discount = 35;
}
if (R >= 3 && F < 3 && M >= 3) {
System.out.println(“30 st REM For loop”);
discount = 30;
}
if (R >= 3 && F >= 3 && M < 3) {
System.out.println(“25 st REM For loop”);
discount = 25;
}
if (R >= 3 && F < 3 && M < 3) {
System.out.println(“20 st REM For loop”);
discount = 20;
}
if (R < 3 && F >= 3 && M >= 3) {
System.out.println(“15 st REM For loop”);
discount = 15;
}
if (R < 3 && F >= 3 && M < 3) {
System.out.println(“10 st REM For loop”);
discount = 10;
}
if (R < 3 && F < 3 && M >= 3) {
System.out.println(“5 st REM For loop”);
discount = 5;
}
if (R < 3 && F < 3 && M < 3) {
System.out.println(“2 nd REM For loop”);
discount = 0;
}
session.setAttribute(“discounta”, discount);
Integer buy_cost = 0;
Integer buy_cost1 = 0;
if (discount != 0) {
buy_cost = discount * cossst;
System.out.println(“buy_cost:” + buy_cost);
buy_cost1 = buy_cost / 100;
cossst =cossst-buy_cost1;
}
session.setAttribute(“buy_cost1”, cossst);
System.out.println(“R:” + R);
System.out.println(“F:” + F);
System.out.println(“M:” + M);
System.out.println(“discount:” + discount);
String coupen1 = user.substring(0, 2);
Random num = new Random();
int coupen2 = num.nextInt();
int code1 = Math.abs(coupen2);
String coupen3 = Integer.toString(coupen2);
String code = coupen1 + “” + code1;
session.setAttribute(“sscode”, code);
SMTPSendmsg = new SMTPSend();
msg.msgsend(user, code);
RequestDispatcherrd = request.getRequestDispatcher(“payment.jsp”);
rd.forward(request, response);
} catch (Exception e) {
e.printStackTrace();
} finally {
}
7. CONCLUSION
This part proposes a novel three-advance approach which utilizes RFM investigation in three information mining assignments: grouping, order and affiliation administer mining, connected in a steady progression. Initially, client sections with comparative RFM esteems are recognized to have the capacity to embrace distinctive showcasing techniques for various client fragments. Besides, grouping rules are found utilizing statistic factors (age, sex, instruction level and so forth.) and RFM estimations of client sections to foresee future client practices and to target client profiles all the more obviously.
Thirdly, affiliation rules are found to distinguish the relationship between client portions, client profiles and item things bought, and thusly to suggest items with related rankings, which brings about better consumer loyalty and strategically pitching. Information Oriented Applications in Data Mining This part displays fusing RFM investigation into information mining systems to give showcase knowledge. It intends to bring consideration of information mineworkers and advertisers to the significance and favorable circumstances of utilizing RFM examination in information mining. So as to assess the proposed display and exactly exhibit the advantages of utilizing this model in coordinate showcasing, a contextual investigation was done utilizing the datasets gathered inside two years time span by a games store in Turkey through its web based business site.
8. REFERENCES
Arthur, D. and Vassilvitskii, S K-Means++ The benefits of cautious seeding, Proceedings of ACM-SIAM Symposium on Discrete Algorithms, pp. 1027-1035, ISBN:978-0898716245, New Orleans, January 2007, Society for Industrial and Applied Mathematics, USA.
Blattberg, R.C.; Kim, B-D. and Neslin, S.A..Database Marketing: Analyzing and Managing Customers, Chapter 12, pp. 323-337, Springer, ISBN: 978-0387725789, New York,USA.
Bult, J. R. and Wansbeek, T. Ideal choice for post office based mail, Marketing Science, Vol. 14, No. 4, (Fall 1995) 378-394, ISSN:0732-2399. Chan, C.C.H. (2008). Shrewd esteem based client division technique for battle administration: A contextual investigation of car retailer, Expert Systems with Applications, Vol. 34, No. 4, (May 2008) 2754-2762, ISSN:0957-4174.
Chen, M.; Chiu, A. and Chang, H. (2005). Mining changes in client conduct in retail advertising, Expert Systems with Applications, Vol. 28, No. 4, (May 2005) 773-781, ISSN:0957-4174
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Technology"
Information Technology refers to the use or study of computers to receive, store, and send data. Information Technology is a term that is usually used in a business context, with members of the IT team providing effective solutions that contribute to the success of the business.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




