ABSTRACT
Context: This project puts to test the following hypothesis, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. The role of web services is currently a broad aspect in research, academia and e-commerce. This is for example, numerous services such as, email, storage and cloud all falls under web-based services. Often web services comprise of a Service Level agreement (SLA), by standards defining services on offer inclusive of their characteristics. However, current SLA is more centred on Quality of Service (QoS), adversely resulting in lacking a vast content of other crucial security concerns.
Aims and Objectives: Aim to study in-depth, existing SLA standards such as WS-Agreement and WSLA, examining the possibility of extending them to incorporate other security concerns (crucial elements) such as confidentiality and integrity.
Methods: Section of the project focuseson proposal for a solution that will extent SLA security concerns, with the aim to improve the current state and bridge security gaps for other overlooked security elements such as confidentiality and integrity among others. A project proposal is derived from a combination of results obtained from internet users’ survey and existing literature on SLA security concerns.
Findings/Results: Revealed that a significant number of internet users are aware of existence of security concerns despite high dependency on the internet. Security concerns in Web-based services and SLA were also identified through literature review. The results of which is a clear indication that mitigation of security issues is a battle yet to be won regardless of the subject being widely explored in research community.
Conclusion and future work: Like Web Services, Service Level Agreements are faced with security challenges. This depend on the parameters on which the Service Level Agreement offers. Currently more focus has been found to be on Quality of Service. Therefore, the project is in appeal to Web Services providers and consumers to include other security concerns such as confidentiality and integrity. This is in anticipation for enhanced security in SLA through adoption of lacking parameters. Future recommendations are to review the new SLA to, identify strengths and weaknesses as well as adaptation to future requirements and contingency planning for possible dysfunctions.
Key words: Web-based service, Service Level Agreement (SLA), security concerns, Quality of Service (QoS), confidentiality, integrity
Table of Contents
CHARPTER 1: INTRODUCTION
1.1 Study Title: Analysing security in Service Level Agreement (SLA)
1.2 Motivation and Background
1.3 Concept of security concerns in SLA
1.4 Problem and hypothesis analysis
1.5 Aims
1.6 Objectives
1.7 Research Questions (RQs)
1.8 Relevance and Significance
1.9 Overview of the project structure
CHAPTER 2: LITERATURE REVIEW
2.1 Definition of Web Services
2.1.2 Web Services architecture
Figure 1. Web services architecture
Web Services Architecture roles
How a Web Service Architecture Operates
2.2 Understanding Service Level Agreements (Answers to Research Questions)
Figure 2: SLA Lifecycle
2.3 Linking SLA to Web Services and addressing security issues
Figure 2. Interoperability in web services
2.4 Existing Service Level Agreements
CHAPTER 3: PROPOSED SOLUTION
Table 1. Questionnaire results
Table 2. Question 1 data analysis
Chart 1: Question 1 results
Table 3. Question 2 data analysis
Chart 2: Question 2 results
Table 4. Question 3 data analysis
Chart 3: Question 3 results
Table 5. Question 4 data analysis
Chart 4: Question 4 results
Table 6. Question 5 data analysis
Chart 5: Question 5 results
Table 7. Question 6 data analysis
Chart 5: Question 6 results
Table 8. Question 7 data analysis
Chart 6: Question 7 results
Table 9. Question 8 data analysis
Chart 7: Question 8 results
Table 10. Question 9 data analysis
Chart 8: Question 9 results
Table11. Question 10 data analysis
Chart 9: Question 10 results
Table 12. Question 11 data analysis
Chart 10: Question 11 results
Table 13. Question 12 data analysis
Chart 11: Question 12 results
Table 14. Question 13 data analysis
Chart 12: Question 13 results
3.4 Problem Requirements
3.4.1 Requirements definitions for SLA
SLA Measurable requirements (Qualities)
SLA unmeasurable requirements (Qualities)
3.5 Design and Development
3.5.1 Proposed solution: An Approach to Secure Service Level Agreements
SLA Security management
CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
4.1 Evaluation
4.1.2 Advantages
4.1.3 Proposed solution limitations
CHAPTER 5: EVALUATION, CONCLUSION AND FUTURE WORK
5.1 Conclusions
5.2 future work
Appendix 1: Analyzing security in Service Level Agreement questionnaire based Survey
Appendix 2: Survey respondent Consent
Appendix 3: Records of monthly supervision meetings
November Report
December Report
January Report
February Report
March Report
Appendix 4: Report Structure Documentation
CHARPTER 1: INTRODUCTION
Chapter overview
This chapter introduces the project giving an insight to its hypothesis, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. Security concerns are at the core of the discussions in the study. Focus is more directed to lack of security concerns in Service Level agreement (SLA) such as, confidentiality and integrity, and their role in SLA. The role of web services in today’s internet paradigm and SLA security concerns are to be explored in elaboration to the hypothesis. Study title, motivation and background, concept of security in SLA an insight to the problem and hypothesis analysis, research aims and objectives, research questions, relevance and significance will be included. Finally, in conclusion to the chapter is an overview of the project structure.
- Study Title: Analysing security in Service Level Agreement (SLA)
Security concerns are remaining a huge focus on today’s internet paradigm (Aljazzaf et al, 2010; Toms, 2004; Wang and
Vassileva, 2007; Zhou et al 2014). This is for example in widely deployed/distributed computing services of huge importance to the current internet paradigm. For instance, cloud computing, email, storage, all falling under web-based services (Toms 2004). “Web Services” can be defined as systems using Extensible Mark-up Language (XML) in communicating among distributed computing environments (Park et al 2007; Zhou et al, 2013). Latest businesses are now functioning globally through exploitation of web services by distribution of their applications (Frankova 2010). Web services researchers have a more focus on security research on establishing safety regulations for services (JIANG et al 2016; Park et al 2007). Often exploitation of web services comes with a regulatory agreement between themselves and consumers on what services they offer and any consequences because of breach (Meland et al 2012). An example of web services security regulations is a Service Level Agreement (SLA). SLAs has a relationship regulatory role between the providers and consumers (Meland et al 2012). This project is going to focus on analysing Service Level Agreement security concerns beyond Quality of Service (QoS), which is currently the focus of SLA, lacking other crucial security concerns such as confidentiality and integrity (Zhou et al 2014). In addition to the analysis of SLA, a proposal will be made to extend security concerns in SLA to include confidentiality and integrity as crucial aspects in security. Three objectives are to be satisfied as follows;
- Explore and elaborate the project hypothesis. An in-depth research is taken to understand parameters in Service Level Agreement with the motivation/view to establish other security concerns differing from Quality of Service (QoS). Example security concerns of main interest in the project are confidentiality and integrity.
- Investigate most challenging SLA security concerns and suggest why the focus seems to be currently on Quality of Service rather than other security concerns which have a great potential to tarnish the image of the service provider with possibility of facing lawsuits resulted through security breach scandals.
- Based on the study findings, will make a proposal for a solution to extend security concerns in SLA to include confidentiality and integrity.
- Motivation and Background
Web-based services are among widely distributed and dominant technology on the internet, with many diversified services (JIANG et al 2016; Masood and Java 2015; Toms 2004). Such is a dilemma for consumers in terms of making a choice as all equally functional, possibly differing in cost, quality and security (Zhou et al 2014). They are featured with “self-contained and self-descriptive” applications composed of modules that are invokable on the internet once deployed. Currently, web-based services are the most favourable medium for exchanging information (Toms 2004). These modular applications (self-contained units) are platform independent (Tidwell 2000; Zhou et al 2014). Web services operate on a Service Oriented Architecture (SOA) (Park et al 2007; Zhou et al, 2013). For instance, research by Zhou et al, 2014, identified majority studies to have a significant concentration on Quality of Service aspects not fully addressing security concerns. Cloud computing is also vastly growing providing Infrastructure, Software or platform as a service. All either exposing or consuming Web Services from another platform or Infrastructure. Consequently, results in complex interaction management, adversely making it difficult to manage the security aspect of things (Baun et al. 2011; Deshmukh et al 2013). A significant number of contributions from research community indicates proven factors that the security challenges battle in distributed computing is continuous (CSGE, 2014; Kumar et al 2015; Mukherjee et al 2013; Schwarz et al 2005). This makes it a more crucial requirement for the service providers to tighten up security measures while giving the consumer some form of guarantee that they are to satisfy certain security parameters apart from the traditionally known focus on Quality of Service (QoS) (Zhou et al 2014). Example of a guarantee of services from the provider of web-based services is a Service Level Agreement (Undheim, Chilwan, & Heegaard, 2011, p. 2). This project is motivated by exploring and investigating SLA security concerns beyond Quality of Service (QoS). Findings drawn from the in-depth study forms the basis for deciding whether it is feasible to propose a solution to improve security concerns in SLA.
- Concept of security concerns in SLA
Casola et al (2015) addressed questions as to whether security can be provided in form of a service, or could a SLA be sufficing in meeting security requirements. These questions are no doubt a centre of controversy in web-based services. In support to that fact, Bianco et al 2008; Zhou et al 2014 pointed that despite security challenges faced in the SOA, majority of current SLA focus is more directed in Quality of Service. This is evident that it is a shared view that current SLAs are rather based on quality provision, not making it clear to consumers of underlying security concerns compromising the so called “Quality of Service”. Given such, security issues that may rise because of failing to implement a Service Level Agreement with more coverage of security concerns may be overwhelming. Security measures in a diversified environment may be quite challenging due to data complexity (CSGE, 2014; JIANG et al 2016; Kumar et al 2015; Mukherjee et al 2013; Schwarz et al 2005). Therefore, it should be in the best interest of web series providers to give maximum security assurance to their consumers in SLA. Such is paramount in establishing strong business relationships in web services (Belanger et al 2002). Numerous research indicates that the appalling rate of security issues in e-commerce makes it hard to win the trust of consumers (Belanger 2002; Cyra and Górski 2008; Motallebi et al 2012; Aris et al 2011). This opens argumentative ideologies such as whether a more secure SLA may prove a positive difference? It is anticipated that some of the questions are to be answered in this study. Inclusion of security concerns such as confidentiality and integrity to QoS is the basis on which this study aims at answering some of such questions.
- Problem and hypothesis analysis
This project puts the following hypothesis to test, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. What makes web services unique is that despite being made by different companies they are interoperable. Their interoperability enables them to discover and communicate among themselves (Li-jie Jin et al 2002). The wide deployment means a large pool of services with same functionalities are located and invoked (Zhou et al 2014). Zhou et al (2014) views systems with huge diverse resources as the most vulnerable to security challenges while, JIANG et al (2016) echoes the same idea. As web services deployment vastly expands to accommodate the increasing demand of the new trend, so does the security concerns (CSGE 2014; Mukherjee et al 2013). To establish more security and consumer satisfaction in web services, security concerns must be prioritised (Zhou et al 2014). It is in the interest of service providers attend to numerous security concerns that may affect consumers and cost them money. This is crucial in delivering secure services to consumers as a competitive weapon in business (Belanger et al 2002). There have been many efforts done to regulate services as a measure to promise users security (Kelly 2012; Tomlinson and Lewicki 2015; Undheim, Chilwan, & Heegaard, 2011, p. 2; Verma 2004). Increased deployment of web services to cope with consumer demands, results in interaction complexity between providers and consumers. Therefore, security hold the key to protection of interactions (Deshmukh et al 2013).
- Aims
Overall, this study is aimed at analysing existing SLA security concerns in web – based services to identify lacking security concerns.
- Objectives
Focus is directed in achievement of the aim through investigating security concerns in Service Level Agreement of web-based services. This is to establish the basis of which a solution can be proposed to extent SLA security concerns through inclusion of confidentiality and integrity in current parameters.
To explore and suffice the requirements of the hypothesis being put to test, existing literature is to be studied to investigate the following;
- Web-based services and their functionality aspects
- Exploring the role of Service Level Agreement in Web services
- Parties involved in a Service Level Agreement
- Identify security concerns apart from Quality of Service
- Investigate the importance of security concerns such as confidentiality and integrity, and identify the consequences that may befall the Service provider if security breach occurs because of lacking the two
- Based on the study from literature review, security holes resulting from lack of confidentiality and integrity will be addressed forming the basis of viability of the idea to extend security concerns in SLA to include confidentiality and integrity.
- Research Questions (RQs)
Based on the research aims in 1.5 and research objectives in 1.6, the following research questions have been formulated;
RQ1. What is the role of SLA in Web Services?
Formulation of this research question is based on identifying the importance of SLA in web services. Answers to RQ1 will give an understanding of security issues affecting web services and relevancy of SLA.
RQ1.1 What are relevant security threats affecting SLA?
RQ2. What SLA security parameters currently exist in Web services?
The key objective to this question is based on investigating current focus on security in SLA to identify lacking security parameters. This will assist in suggesting what can be done to include new parameters that can provide enhanced security in SLA.
RQ3. Who has the responsibility to ensure security concerns are investigated in SLA?
This question assists in identifying who is accountable for initiating and deploying SLA.
RQ4. Do Web services achieve an added value from SLA?
This question analyses effects of adding new security concerns to the consumers. Formulation of the question is useful as the web services providers interest lies on establishing and building strong relations with consumers. Therefore, it crucial to establish security as a token for enhanced SLA.
- Relevance and Significance
In consideration to web-based services such as cloud computing, email, storage, it is crucial to establish Service Level Agreements fit for purpose. This is crucial as part of contractual agreements as it establishes trust into the service provider by the consumer (Dukee 2010; Li-jie Jin et al 2002; Verma, 2004). A Service Level Agreement (SLA) is a consensus/agreement as part of a contract between two parties namely, service provider and the service consumer (user), (Kelly 2012; Tomlinson and Lewicki 2015; Undheim, Chilwan, & Heegaard, 2011, p. 2; Verma 2004). The SLA is made up of parameters offered to the consumer by the provider. The SLA underlines the expectation of the customer from the service providers, as well as addressing the obligations of both the parties partaking in the agreement. The service provider is under obligation to provide services being paid for by the consumer. Failure to which the service provider consequently suffers financial reparation’s (Li-jie Jin et al 2002). Additionally, and most importantly, SLA includes the terms regarding availability, performance and security of the service among other parameters from the provider’s end, inclusive of all that is to be adhered once the agreement takes place (Verma, 2004). From the provider’s side, this guarantees service provisions while the consumer signs in agreement to what is offered to them. The agreement between the two stakeholders is voluntary. However, the term “
agreement” is not as easy as the word sounds, for both stakeholders to reach to that stage, it may take a lot of controversial ideologies about parameter expectations (Kelly 2012; Tomlinson and Lewicki 2015). A yet another difficult situation, “
negotiation” will be faced in compromise to reach an agreement by both parties’ through surrendering a certain measure of their freedom. Negotiation becomes necessary where there are conflicting ideas (Tomlinson and Lewicki 2015). A comprehensive study is to be taken in anticipation to assist both stake holders understand each other’s view point to ease the agreement process (Hamilton 2015). To overcome security holes resulted on failing to implement security measures that will protect the current SLA from security vulnerabilities, this study proposes a solution. Therefore, relevancy and significance is formed efforts to seal security holes in SLAs, by proposing a more secure SLA.
- Overview of the project structure
Considering the overwhelming size of the project, this section act as a project pointer as it gives an overview of how work is being approached as follows;
Chapter 1: This is formed of an introduction to the project, hypothesis (main subject of the study), “Web Services are widely deployed and play an important role in today’s Internet paradigm”. Title of study, Motivation and background, security concerns in Service Level Agreement (SLA), problem and hypothesis analysis, aims and objectives are all in the first chapter. Research question are to be addressed with justification for significance of study and rationale.
Chapter 2: Second chapterexplores Service Level Agreements and related security concerns, including existing literature review. More focus on this chapter is centred on literature review for establishment of security concerns. To give an understanding of the subject, an overview of web services, and that of SLA. Overviews are to establish the relationship between web services and SLAs in detail. The outcome of studying existing SLAs will determine proposition of a solution that will extent SLA security concerns, with the aim to improve the current state and bridge security gaps for other overlooked security elements.
Chapter 3: Design and development work is undertaken in this chapter. This is where requirements specifications for proposing a solution that will extend security concerns in SLA will be addressed. A combination of results from questionnaire survey and literature review form the basis of proposing a solution. This is an action executed to reduce security holes resulted due to more focus on (QoS) in current SLAs.
Chapter 4: Critical Analysis of Proposed Methodology or Artefact will take place in this chapter. An overall analysis will be made to outline the origin of the proposal ideology, the proposed solution, advantages and disadvantages that are likely to result. Also, limitations of the project.
Chapter 5: Evaluation of the proposed solution will take place on this chapter discussing methods for evaluation including results from the discussion. Overall work done throughout the project will be discussed in summary to all previous chapters. Most importantly project conclusion and the direction of project future.
CHAPTER 2: LITERATURE REVIEW
Chapter overview
An in-depth study of existing work on existing SLA standards such as WS-Agreement and WSLA, investigating their content to identify the extend in covering security concerns, such as confidentiality and integrity. Results of the investigation anticipate identifying security holes or shortfalls such as lack of focus on confidentiality and integrity. To give a clear picture of the study elements, the chapter will start with an overview of web services and Service Level Agreements. More focus of the overview will be on security concerns as they are the basis of the work undertaken in the project. Results from the literature review will contribute to the establishment of an idea to be used in proposing a solution for incorporation of security concerns such as integrity and confidentiality.
2.1 Definition of Web Services
Web services are among the growing software architecture trends. They do not have a standard definitive term but various terms (Xiang, 2007). Software components build to operate platform-independently, are defined as web services (Li-jie Jin et al 2002; Zhou et al 2014). Web services have provided dynamic interoperability among in e-commerce (Wang et al, 2004). Once deployed, they are discoverable and invokable by other applications (Fensel and Bussler, 2002). Cloud is an example of Web -based services currently being viewed as the IT industry backbone (El-Awadi et al., 2015; Toms 2004). Figure 2.1.2. elaborates the typical architecture of a web services. However, the architecture is not limited to the attributes in 2.1.2. Composition varies with considering of principles and parameters included. Justification of diagram choice for illustration of web services architecture in this study is based on relevancy.
2.1.2 Web Services architecture
Figure 1. Web services architecture
(Balaji et al, 2013).
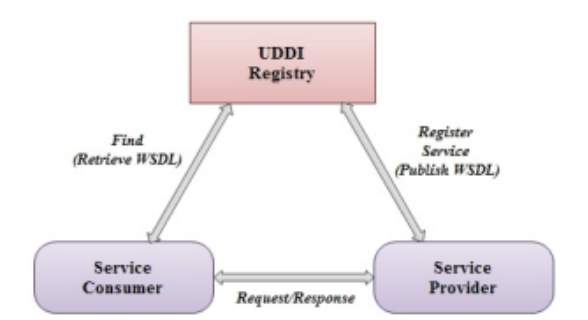 Web Services Architecture roles
Web Services Architecture roles
- Service provider: Respectively there are two perspectives in which the provider can be addressed, depending on the situation. These are the following; owner or a host platform. Form a business view point the provider is the service owner. Relating to architectural view point, the host platform is referred to as the service provider Kreger 2001; Q Yu et al 2006.
- Service requester: This is also viewed from business and architectural view point. From the business view, this is the consumer or business with expectations for functions from the provider. From architectural view point, it is an application which discovers and invoke services or initiate interactions with services Kreger 2001; Q Yu et al 2006.
- Service registry: This is service register used by providers in publishing their services. This is also known as the directory of registered services (Bansal et al, 2010). The registry plays a services or communication initiation role between the provider and the consumer (service requester) Kreger 2001; Q Yu et al 2006.
How a Web Service Architecture Operates
There are three contributory elements through which web services can be exploited as follows;
publish, find and bind (Kreger, 2001).
A publication describing the service, a quest for the service, followed by invocation of a service(s).
- Publish: Service descriptions are published by the service provider, describing the service.
- Find: A consumer makes a quest for a service. This could be either directly or through the service registry.
- Bind: Service invocation or initiation with the interaction runtime takes place.
2.2 Understanding Service Level Agreements (Answers to Research Questions)
Consumers have lately been faced with being indecisive on which services among the widely distributed and diversified web services due to competitive providers. As an intervention strategy to the situation, a mechanism to overcome that becomes necessary in form of a contract. This contract is used to initiate negotiations and is known as a Service Level agreement (SLA). SLA has a centralized role through assisting service providers in the process of defining services to be delivered to consumers (Bouras et al., 2005). Answering research questions below will define the role of SLA in web services, address security threats affecting SLA, outline existing SLA security parameters in web services, clarifying stake holder responsibilities and suggest the value of SLA to web services.
RQ1. What is the role of SLA in Web Services?
A service level agreement (SLA) refers to a contract between the service provider and its internal as well as external customers that details what services will be rendered by the provider and the level or standards of performance that will be met by the provider. A major of the SLA is establishing customer expectations in respect to the standard of performance and the quality of work to be rendered by the provider (Kelly 2012; Tomlinson and Lewicki 2015). SLA helps the parties define the availability and uptime of the services, that is, it helps set the percentage of time the services will be available. SLA key performance benchmarks are developed upon which the actual performance will be compared. This ensures quality work throughout the stipulated time. SLA also provides a notification schedule respect to failure or network issues. In addition, it will indicate the expected response time for the different type of issues that may arise. SLA provides a documentation of how a downtime will be addressed and how the customer will be compensated in case of a contract breach. Security promises are also outlined in SLA, although presently, most research materials seem to have a concentrated focus in the Quality of Service Aspects. Research by Bouguettaya, 2013 regards SLA as posessing or serviong as a composion of blueprint and guarantee for cloud services.
RQ1.1 What are relevant security threats affecting SLA?
There are numerous security threats affecting SLA as identified by the European Network and Information Security Agency (ENISA) (2009) make sure this is appearing in master ref list. SLAs are more than often affected by loss of governance. This happens especially at the drafting of the SLAs where most of them are poorly drafted and affected by customer not being specific during the drafting process (reference if possible). Research suggests that when SLAs are not soundly deployed will have adversities (Li-jie Jin et al 2002; IBP, 2013).
RQ2. What SLA security parameters currently exist in Web services?
Casola et al, (2015) expresses security as existing among factors representing major limitations in adopting cloud computing. They mentioned this is due to lack of transparency in how service providers grant security, but rather focusing on service aspects such as availability and performance. Where secure SLAs are implemented and deployed, proves security can be offered as a service. Zhou et al, (2014) echoes that security should be treated as a priority for achievement of established consumer satisfaction in web services. They also pointed that current SLA is overshadowed by Quality of Service. This is evident that security parameters are yet to be dominant in web services SLAs.
RQ3. Who has the responsibility to ensure security concerns are investigated in Service Level Agreements (SLA)?
Service level agreements are based on agreement between the provider, consumer and any third party (Kelly 2012; Tomlinson and Lewicki 2015). However, for that agreement to be reached, it somehow originates from the provider as it describes services which the provider is willing to commit to provide (Bouras et al., 2005). In this case, the provider initiates the SLA to guarantee services to the consumer. From consumers’ perspective, it is the description of expectations such as quality of services (Bianco et al 2008). To reach to a consensus, an SLA is drafted outlining provider and consumers’ obligations and responsibilities (Bouras et al., 2005). During the entire lifecycle of the SLA, more responsibilities require service providers to ensure they meet their security promises through investigation any security issues. (Li-jie Jin et al, (2002) mentioned that should the service provider fail to meet their obligations, this may have adverse effects such as financial loss. In consideration to findings, the answer to this question identifies the service provider as the party accountable for initiating and deploying, and reviewing SLA.
RQ4. Do Web services achieve an added value from SLA?
Using Service Level Agreements (SLAs) in web services is essential for provision of added value (Soomro, Aijaz, Ahmed 2016). This ensures consumer satisfaction due to successful deliverance of Quality of Service (QoS) as expected. Availability, reliability, performance and quality of services are all defined by the SLA. SLA definition also includes ensuring timely, safe and secure message or information delivery (Bianco eta l, 2008). A well implemented SLA satisfying crucial security elements such as confidentiality and integrity offers added value to web services (CISCO, 2005; Soomro, Aijaz, Ahmed 2016). By satisfying security requirements in SLA deployment, trust is built in consumers, thereby resulting in the web services being able to cease more business opportunities with consumers through recommendations (Zeginis and Plexousakis, 2010). Unlike placing entire responsibility on the service provider, SLAs establishment follows a two-way service accountability. This means consumers are also responsible for failure to abide by agreed SLA terms and conditions (CISCO, 2005). In the service lifecycle, SLAs play a critical role through influencing engineering and operational decisions. Popularity of cloud computing is partly due to SLA implementation (Müller et al. 2014). SLAs are used widely in service-oriented architectures and distributed systems. Through these agreements, entities can agree on what services will be offered and with clearly agreed terms for delivery. Service level agreements also include who will be responsible for completion, execution, privacy aspects, and potential failures. More importantly, SLAs are limited to the description of responsibilities and expectations. The best way to understand these agreements is to break them down into schemas, negotiation protocols, SLM management, and implementations (You et al. 2015). A service level agreement cannot guarantee the availability of the service described. Additionally, it cannot deliver a good service out of a poor one. However, it can mitigate the risk of subscribing to a bad service (You et al. 2015). An SLA suitable for purpose enforces service provision and limits (Casola et al, 2015). A service level agreement needs supporting tools and mechanisms applied during different phases of its lifecycle, which requires monitoring of service execution adherence to the shared terms and enforcement. The figure below shows the SLA lifecycle;
Figure 2: SLA Lifecycle
(IBM Version 8.5) requires relocating ref and add to list. If not to replace diagram
![Figure 5.8: Service Level Agreement Life-Cycle [57]](https://images.ukdissertations.com/13/0010698.003.jpg) 2.3 Linking SLA to Web Services and addressing security issues
2.3 Linking SLA to Web Services and addressing security issues
There is a wide coverage research on SLAs (Clark and Gilmore 2006; Miller 2012; Stanik et al 2014). However, it is a proven factor that majority existing SLAs are lacking confidentiality and integrity while focusing more on Quality of Service (Zhou et al 2014). The scenario in figure 2 below, shows how web services are exploited and gives an analysis of elements that consumers are likely to be enticed by, to an extent of prioritising Quality of Service. This indicates the focus on Quality of Services seem to have a stronghold in relationships between providers and consumers (Mani and Nagarajan 2002). Current research suggests that Service Level agreements on a Service Oriented architecture focus on Quality of Service (QoS) (Bianco et al 2008; Zhou et al 2014). Dukee (2010) suggested SLAs are a form of security to the consumer as compensation is provided in breach of the agreement. El-Awadi et al (2015) pointed out there is a lot of scepticism from numerous consumers relating cloud providers’. The scepticism is a result of the gap between their Quality of Service promises and what the SLA has on offer. As a result, focus on QoS with diverted attention from other security parameters, potentially resulting in economic adversities has been identified in this study as an unresolved issue that has existed for a long time (Li-jie Jin et al 2002).
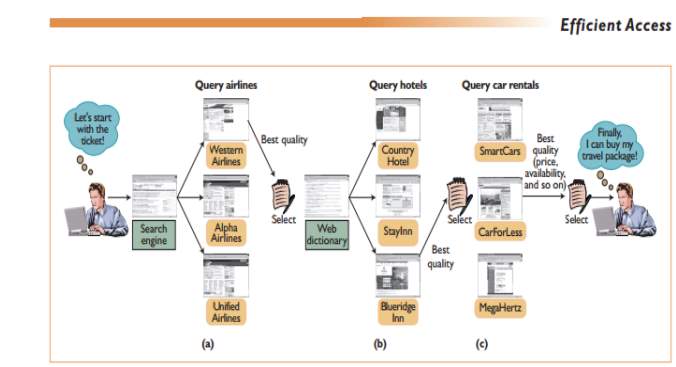
The pictorial diagram below, named figure 2 is a typical demonstration of web services interoperability in day to day business between the providers and consumers (Li-jie Jin et al 2002). In the picture, Ouzzanni and Bouguettaya (2004), gave a three-step scenario a consumer named Ravi takes in planning his journey. In step (a) Ravi makes a query for an air ticket with 3 air lines named Western Air Lines, Alpha Airlines and Unified Airlines. In step (b) Ravi makes a query for accommodations among Country Hotel, StayInn and Blueridge Inn, then (c) a car from a rental company between SmartCars, CarForLess, MegaHertz. All the required services for Ravi’s quest are accessible in a large pool (Frankova 2010). An in-depth analysis of the diagram above proves the fact that the consumer’s quest is more focused on elements such as “best quality” which is to do with transactional Quality of Service (QoS) in Web services (Bianco et al 2008). Based on QoS focus of web services, my assumption is that SLA focus in pursuit of the same idea may be to satisfy consumers passion for quality. The final decision made by Ravi indicates that Quality of services is at the top of consumers’ priorities followed by others such as cost and availability among others. It is therefore necessary for providers to put more effort in addressing security parameters such as confidentiality and integrity. This study anticipates that Extending security concerns to SLA to include confidentiality and integrity, may positively add value to SLA.
Figure 2. Interoperability in web services
(Ouzzani and Bouguettaya 2004)
 2.4
2.4 Existing Service Level Agreements
Investigating the extend in which security concerns such as confidentiality and integrity are covered in existing WS-Agreement and WSLA,
CHAPTER 3: PROPOSED SOLUTION
Chapter overview
Work in this chapter focuses on proposing a solution to extend security concerns to incorporate confidentiality and integrity. Questionnaire based survey results are to be included in this section and identified security holes from literature review will be addressed, followed by a suggested solution to improve security in SLA. A suggested solution will be used for as project proposal for improvement.
3.1 Questionnaire Survey
A questionnaire is a research tool used in obtaining information from a representative population selected to take part in a survey. Information obtained through questionnaires is motivated by various reasons such as identifying consumer trends, patterns, opinions and trends. Questionnaires with the objective to analyse results are normally made up of closed questions. The objective of this survey is to collect information relevant to web services consumers and their online behaviour, while abiding to Data Protection Act 1998 (Tipping, 2016). Data protection Act is in force in the interest to protect information relating to individuals. This makes it illegal for the individual conducting a survey to use data in any way apart from what it had been obtained for (Tipping, 2016). Displaying that data in one table makes it easier to count number of opted answers for each question. By so doing it makes it easier to plot charts/graphs for analysing the results. This also eases the process of converting data to information for presentation to individuals whom it may need to be shown to (Durbin, 2004) A questionnaire based survey has been used in this project for consumer involvement. Results drawn from the survey ascertains relevance of the survey to the study. An in-depth results analysis has been done on each question in this study. This has been done with consideration to make it easier for disseminating information as there are many questions.
3.1.1 Survey Data Results
Key:
P1 to
P20 = Participant 1 to participant 20
Q1 to Q13 = Survey Questions
Numbers for example 5,3,1,2 represent opted answers in the survey by each participant. The table had been designed in way that makes participant numbers to tally with their opted responses and question numbers.
Table 1 is made up of all the data results from the questionnaire survey. P 1 to P 20 represents number of participants to promote anonymity in the survey.
Instructions for using table 1 data
Formation of table 1 has been formulated as a time management strategy. This has been done by displaying all data from the survey in one table for use in analysing results.by so doing it makes it presentable rather than having to keep counting responses throughout the analysis. The following is a breakdown on how table 1 has been used in displaying all results;
Using a combination of P1 to P 20 and Q1 to Q13, numbers in between are opted responses to be matched with participant, question number. By so doing, small tables of data had been produced faster for all questions. 3 D pie charts displaying results in fractions (%) had been produced using data from results obtained from each question. For more clarification, reference can also be made through the key above.
Table 1. Questionnaire results
|
|
Project Questionnaire responses
|
|
Participants
|
|
Q1 |
Q2 |
Q3 |
Q4 |
Q5 |
Q6 |
Q7 |
Q8 |
Q9 |
Q10 |
Q11 |
Q12 |
Q13 |
| P1 |
5 |
3 |
2 |
1 |
1 |
2 |
1 |
5 |
2 |
5 |
1 |
4 |
1 |
| P2 |
4 |
1 |
2 |
1 |
2 |
4 |
1 |
1 |
2 |
3 |
1 |
4 |
2 |
| P3 |
5 |
3 |
3 |
3 |
2 |
4 |
1 |
2 |
3 |
1 |
1 |
3 |
2 |
| P4 |
5 |
2 |
3 |
1 |
3 |
1 |
1 |
3 |
3 |
4 |
1 |
4 |
2 |
| P5 |
5 |
1 |
2 |
1 |
1 |
4 |
2 |
2 |
3 |
1 |
1 |
3 |
2 |
| P6 |
4 |
1 |
3 |
3 |
1 |
2 |
2 |
5 |
2 |
2 |
1 |
3 |
2 |
| P7 |
4 |
3 |
3 |
1 |
4 |
3 |
2 |
2 |
3 |
5 |
1 |
1 |
1 |
| P8 |
4 |
1 |
4 |
1 |
4 |
3 |
3 |
3 |
2 |
4 |
1 |
4 |
3 |
| P9 |
5 |
1 |
4 |
1 |
5 |
3 |
1 |
3 |
3 |
3 |
1 |
4 |
2 |
| P10 |
3 |
1 |
4 |
3 |
1 |
4 |
1 |
2 |
3 |
4 |
1 |
4 |
4 |
| P11 |
5 |
3 |
5 |
1 |
1 |
4 |
1 |
2 |
3 |
4 |
1 |
4 |
4 |
| P12 |
5 |
2 |
4 |
3 |
1 |
2 |
1 |
2 |
1 |
3 |
1 |
3 |
2 |
| P13 |
5 |
1 |
4 |
3 |
1 |
2 |
1 |
3 |
3 |
4 |
2 |
3 |
4 |
| P14 |
5 |
1 |
3 |
1 |
3 |
1 |
2 |
2 |
3 |
2 |
3 |
4 |
2 |
| P15 |
4 |
2 |
4 |
3 |
1 |
4 |
3 |
3 |
3 |
3 |
2 |
4 |
3 |
| P16 |
5 |
1 |
2 |
1 |
2 |
1 |
1 |
2 |
1 |
4 |
2 |
2 |
3 |
| P17 |
4 |
2 |
4 |
3 |
1 |
4 |
3 |
3 |
3 |
3 |
2 |
4 |
3 |
| P18 |
5 |
2 |
4 |
3 |
1 |
2 |
2 |
1 |
3 |
1 |
3 |
3 |
2 |
| P19 |
4 |
1 |
5 |
1 |
2 |
3 |
1 |
3 |
2 |
3 |
1 |
4 |
2 |
| P20 |
5 |
4 |
3 |
1 |
4 |
1 |
1 |
2 |
2 |
4 |
2 |
2 |
3 |
3.1.2 Survey Data Display and analysis
Question 1: How frequently do you use cloud based applications for instance, (banking, business applications, social media, etc.)?
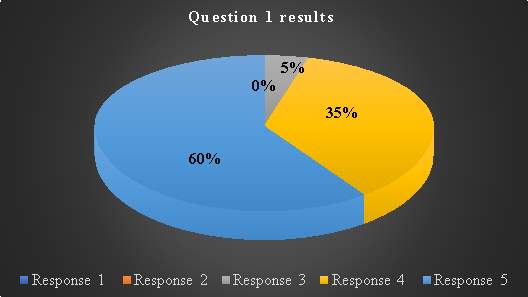
Question 1 formation is based on investigating level of consumer dependence in cloud based applications and many others which are part of the widely-deployed web services. Obtaining user online behaviour gives an insight to their likeliness of falling victims to security issues in web services. 0% in responses one less people using could-based services. Nowadays many people use internet banking which is cost effective in terms of travelling and time (Kumar et al., 2016). Suggestively, the population between 5% and 35% are beginning to exploit e-banking and business applications such as, video interview applications among others. Majority of consumer representative population at 60% indicates popularity of web-bases services and their increased demand. This results in complexity of web services security management. As a result, needs, continuous review and restructuring of SLA security elements to include more security concerns.
Table 2. Question 1 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
Response 5
|
| Much Less 1---------------2---------------3-----------4--------------5 Very Frequent |
| 0 |
0 |
1 |
7 |
12 |
Chart 1: Question 1 results
 Question 2: Do you store any personal data in the cloud?
Question 2: Do you store any personal data in the cloud?
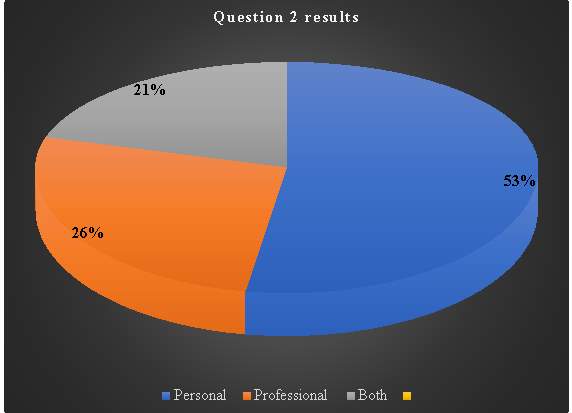
This question is aimed at generating statistics on cloud storage use. Although this is being tested on a significant number of consumer population, any data obtained will be generated into useful information as it is not practical to obtain information from a majority population. Responses given indicate 21% as the least number of people using cloud storage. This could be due to various things such as lack of knowledge on the type of technology, insecurities towards the cloud among others. 26% being the median number who may have intermediate knowledge or any other reasons. The highest population at 53% presumes the growth dependency in web-based services. This may also mean majority population of consumers find cloud storage the most reliable due to the ability to access stored data from anywhere (Sun et al., 2014).
Table 3. Question 2 data analysis
| Response 1 |
Response 2 |
Response 3
|
| Personal |
Professional |
Both |
| 10 |
5 |
4 |
Chart 2: Question 2 results
 Question 3: Do you store any personal or professional data in the cloud?
Question 3: Do you store any personal or professional data in the cloud?
This is just to have a view on whether consumers participating in the survey utilise any cloud storage services. For those who indicated to use cloud, more further requirements of the question were that they indicate the type of data they store. In this question, a Likert scale was used. The approach of setting scales in answering questions, allows participant to have a judgement within the scale (Moors et al., 2014).
Table 4. Question 3 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
Response 5
|
| Not at all ---------------2---------------3-----------4--------------5 Very Much |
| 0 |
4 |
6 |
8 |
2 |
Chart 3: Question 3 results
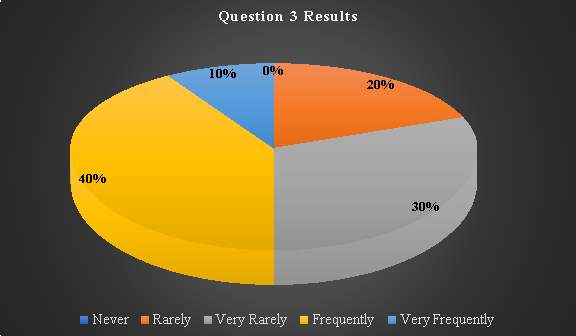 Question 4: Of the applications that you use, which are you most concerned about someone hacking into?
Question 4: Of the applications that you use, which are you most concerned about someone hacking into?
Motivation of the question lies on investigating the type of web-based applications that consumers feel insecure about despite need for exploitation. The different responses of 0%, 40 and 60% is a clear indication that despite the growing number of consumers exploiting web services, there are also growing security concerns. Complex security management in widely distributed computing environments is resulted by increased demand their use (Armoni, 2002)
Table 5. Question 4 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
| Banking |
Email |
Social Networking |
Cloud Storage
|
| 12 |
0 |
8 |
0
|
Chart 4: Question 4 results
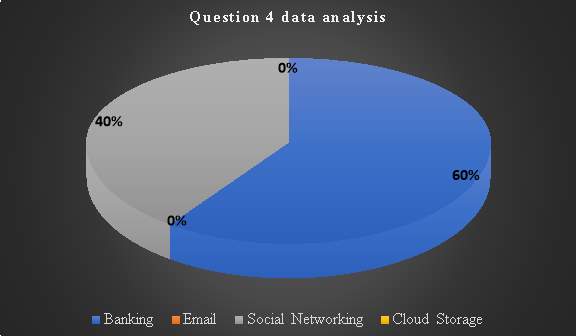 Question 5: Which Social networking website are you mostly concerned about for misuse of your data from hackers?
Question 5: Which Social networking website are you mostly concerned about for misuse of your data from hackers?
This is just to have a view of social networking security concerns from the representative consumers’ view point. By so doing it assists web services providers in working towards gaining consumer trust in those sites through improving SLA to adopt critical security concerns such as confidentiality and integrity. Despite Facebook being one of the most dominant social networks with survey results made up of majority population at 50%, is also the highest opted response indicating security concerns from users.
Table 6. Question 5 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4
|
| Facebook |
Snapchat |
Instagram |
WhatsApp |
| 10 |
4 |
3 |
3 |
Chart 5: Question 5 results
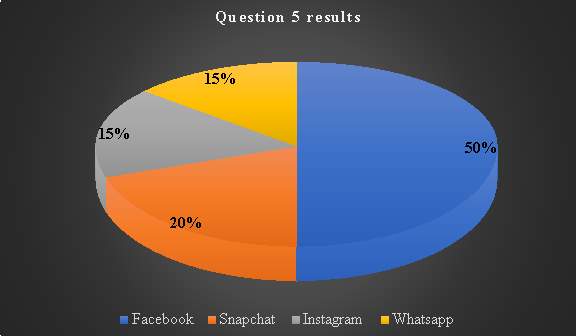 Question 6: Which Cloud storage are you mostly concerned about for misuse of your data from hackers?
Question 6: Which Cloud storage are you mostly concerned about for misuse of your data from hackers?
Formulation of this question is based on an insight to consumers’ insecurities named cloud storages. By so doing it may lead into speculating the reason behind their insecurity. This will be useful in proposing addition of those security parameters in the new SLA solution. By so doing it is anticipated that this will make the SLA negotiation less difficult.
Table 7. Question 6 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
Response 5
|
| Dropbox |
One Drive |
Google Drive |
iCloud |
Other |
| 4 |
5 |
4 |
6 |
0 |
Chart 5: Question 6 results
 Question 7: Which email providers are you mostly concerned about for misuse of your data from hackers?
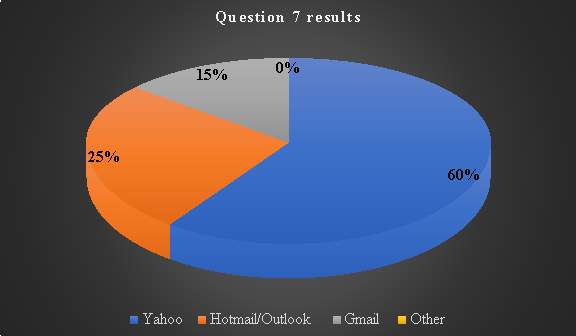
Question 7: Which email providers are you mostly concerned about for misuse of your data from hackers?
This is an investigation to find out email providers whose email services have a history of being hacked adversely affected consumers’. A further investigation will be on the security breaches faced by the email services to ascertain inclusion in SLA. Relating varying percentages representing consumer insecurities, it is a clear indication that if consumer scoring is to be used in email accounts, Yahoo at 60% will be highly likely to attract a lot of criticism. Another indication is that Hotmail/Outlook at 25% in still being viewed with a benefit of the doubt. It is therefore reasonable to say Gmail is the most trusted of the representative email based applications (Zara 2014).
Table 8. Question 7 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4
|
| Yahoo |
Hotmail/Outlook |
Gmail |
Other |
| 12 |
5 |
3 |
0 |
Chart 6: Question 7 results
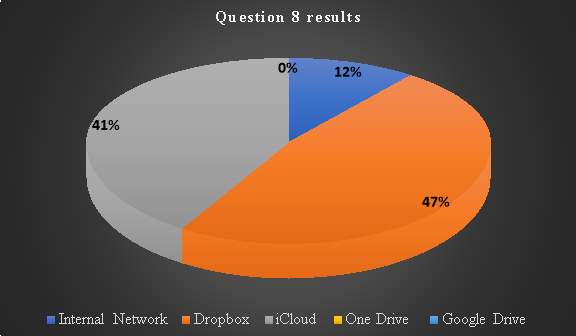
 Question 8: What system for file storage and sharing does your peer ask you to use?
Question 8: What system for file storage and sharing does your peer ask you to use?
This question is aimed at investigating consumers’ peer to peer networking preferences. Analysing peer-to peer networking is beneficial in network security is it gives a view of consumer trust levels in web services (Manoj et al., 2013). The level in which a web service may be preferred to others is mostly related to Quality of Service parameters such as reliability, availability and security concerns (Junqing et al., 2012).
Table 9. Question 8 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
Response 5
|
| Internal Network |
Dropbox |
iCloud |
One Drive |
Google Drive |
| 2 |
8 |
7 |
0 |
2 |
Chart 7: Question 8 results
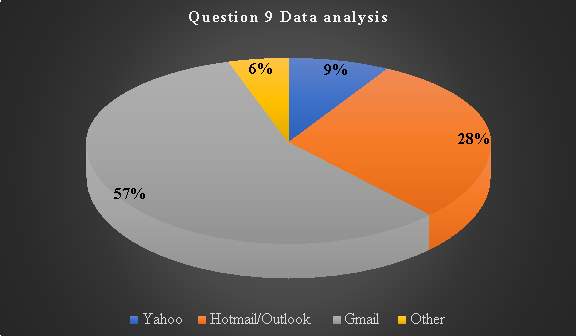
 Question 9: What email provider does your peer ask you to use?
Question 9: What email provider does your peer ask you to use?
This is just to investigate the most favourable email applications/ services among peers. By so doing it assists in making further investigation for the choice of service.
Table 10. Question 9 data analysis
| Response 1 |
Response 2
|
Response 3 |
Response 4 |
| Yahoo |
Hotmail/Outlook |
Gmail |
Other |
| 2 |
6 |
12 |
0 |
Chart 8: Question 9 results
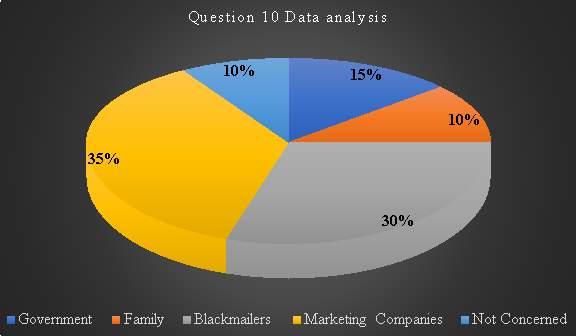
 Question 10: When it comes to your data privacy, who are you most concerned with?
Question 10: When it comes to your data privacy, who are you most concerned with?
This question is based on investigating consumer worries about data privacy. Data privacy is related to security elements such as confidentiality and integrity.
Table11. Question 10 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4 |
Response 5
|
| Government |
Family |
Blackmailers |
Marketing Companies |
Not Concerned |
| 3 |
2 |
6 |
7 |
2 |
Chart 9: Question 10 results
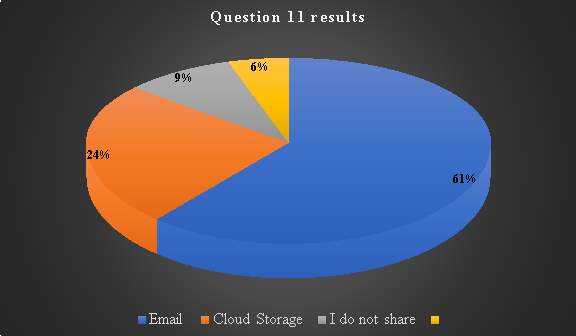
 Question 11: How do you most frequently share documents?
Question 11: How do you most frequently share documents?
Consulting participant frequency in sharing documents or files gives a view on their level of exploitation of file sharing applications in distributed computing environments. This opens discussions as to whether this is about Quality of Services or crucial security elements such as an SLA promising security concerns such as integrity and confidentiality
.
Table 12. Question 11 data analysis
| Response 1 |
Response 2 |
Response 3
|
| Email |
Cloud Storage |
I do not share |
| 13 |
5 |
2 |
Chart 10: Question 11 results
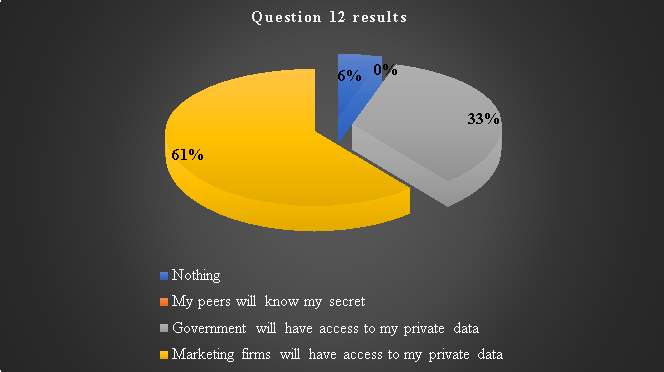
 Question 12: What are your main worries regarding data insecurity/exposure?
Question 12: What are your main worries regarding data insecurity/exposure?
This question indicates the level of data security concerns, worrying consumers about invasion of privacy and data integrity compromisation. While a minority representative population indicates that they do not have data insecurity worries, most seem to worry about access of their private information from the government. Worries relating the government being able to access web services consumer private information, could be perceived to lack of knowledge that the government operate legally on a need to know basis. To elaborate this, it is mostly in the public interest that certain individuals may find themselves in such a situation. This is for example, if a serious crime that puts the public at risk occurs, this may attract the government’s involvement (Zoonen, 2016). Unlike the others, marketing firms are associated with cold calling which is an example that some services sale consumer information to third party (Phelps et al., 2000). This in most cases is a result of consumer activities online.
Table 13. Question 12 data analysis
| Response 1 |
Response 2 |
Response 3 |
Response 4
|
| Nothing |
My peers will know my secret |
Government will have access to my private data |
Marketing firms will have access to my private data |
| 1 |
0 |
6 |
11 |
Chart 11: Question 12 results
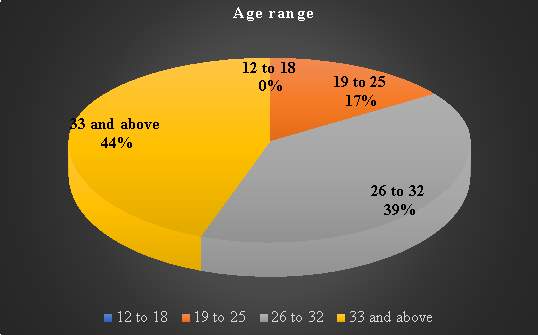
 Question 13: What is your age group?
Question 13: What is your age group?
A total 20 students between 19-33+ participated in the survey. All participants are within Liverpool John Moores School of Computing and Mathematical Sciences took part in a voluntary survey for this project. 0% participated between 12-18. There are two main reasons as follows, anyone under 18 and is obliviously under normal circumstances would need parental consent to take part (). Obtaining parental consent for participants to satisfy legal and ethical issues will take time considering project time scale. 17% was made up of those aged 19 to 25, 39% was made up of participants in age 26 to 32. 44% indicates mature students were among those who were in the labs at the time of the survey.
Table 14. Question 13 data analysis
| Response 1
|
Response 2 |
Response 3 |
Response 4
|
| 12-18 |
19-25 |
26-32 |
33 +
|
| 0 |
3 |
7 |
8 |
Chart 12: Question 13 results
 3.2 Analysing the questionnaire based survey
3.2 Analysing the questionnaire based survey
Questionnaires provide a relatively cheap, quick, and efficient way of obtaining information from diverse audiences. Compared to the long and tedious research methods such as face to face interviews, questionnaires are among the most cost effective. You don’t need hire surveyors to ask people questions. A questionnaire can be placed on a website or simply sent via email. This eliminates printing costs and the need for the researcher to be present when the questionnaire is being administered (Brace, 2008).
Questionnaires allow the researcher to reach unlimited number of respondents since they are not constrained by the need of field researchers who can only cover a specific geographic area. For example, a researcher may decide to send mass emails to respondents across any region of choice. This greater reach also gives the researcher a unique opportunity of predefining a representative sample. For example, the researcher can choose emails as per pre-set variables and thus avoid sending random surveys.
Due to the highly-structured nature of questionnaire, it makes data analysis easier. Not only this but conducting advanced statistical tests been found to be seamless as the researcher is able to control the kind of data to expect from the respondents. This has time efficiency benefits. Therefore, where results are needed within a short space of time, it eases the process (Mitchell, 2009).
Finally, due to their static nature, questionnaires that are well designed and tested can always be re-used across different audiences with just some minor tweaks. Given the fact that questionnaire design can be time consuming, this capability greatly saves on the time taken to design and execute the surveys
Limitations of Questionnaire based surveys
Just like other research methods, questionnaires despite their wide usage have their own limitations. A major limitation arises due to the lack of physical contact between the researcher and the respondents. Mostly questionnaires are administered through digital platforms; online surveys and mobile surveys. This introduces a physical distance between the researcher and the respondents
(Athanasiou, 2010).
One of the major disadvantages faced through questionnaires is that responses may be biased. This makes it hard to verify data authenticity in such cases (Athanasiou, 2010).
The process of producing and deploying questionnaires may be time consuming as it involves finding participants, appropriate environment and specified deadlines. In this case, the project is to be done within six months. This makes it hard as they are procedures to be followed such as legal and ethical issues. To figure out whether one can be part of the representative population, confirmation of their age is required, and this may mean approaching an alternative individual should age restrictions fail to be met. The survey in this study had been contacted on a voluntary basis, which leaves no obligations to any of the participants should they wish to opt out last minute.
Rationale of survey
Every dissertation is guided by a research question or hypothesis. After formulating the research question, the researcher chooses a data collection method suitable for gathering the required information. There are various ways in which data can be obtained in surveys. Data required for the survey somehow suggests the best approach to obtain it. Carrying out a survey is a crucial element in proposing projects involving consumers. This gives an insight in what is expected of the provider (Zhang, 2009).
Studies show that respondents are more honest and are willing to share rather sensitive information through surveys than face to face interview (Bowden et al., 2015). This gives surveys created around sensitive information an edge in terms of obtaining accurate and reliable information (Edward, 2009). A dissertation survey provides the data needed for analysis. A survey provides data that can be used to compare the dissertation findings with past research. Being able to compare the findings with past data is very important in establishing approaches in bridging gaps. Through the survey, the researcher can compare their research with past data. Apart from suggesting or producing a solution to bridge gap, a survey helps formulate recommendations for further research (Ilieska, 2013).
3.3 Analysis of problem
Quantifiable literature proves complexity on focus on Quality of service by existing work in Service Level Agreements (;; ; ; ; ; ;) as many refs as possible to justify quantifiability, at least 4-6 refs from lit review. This is a significant fact that focus on crucial security parameters in SLA, such as confidentiality and integrity is still immature in the research area. Meeting as many as possible security parameters in SLA will earn web services and SLA alike trust from consumers (Stankov et al, 2012). Meeting security requirements is the key to success in any business (reference). Zhou et al (2013) also addressed security issues as an important factor shadowing the SOA platform and development of applications associated with it. JIANG et al (2016) echoed web services dominance is also associated with multiple security issues adversely affecting
reliability, confidentiality and data non-repudiation. This assumes more focus is directed in satisfying consumers’ measurable quality expectations such as speed, reliability, Accuracy, capacity, Scalability and costs. By doing so, a result of serious consequences such as financial loss to the web service providers may occur. In justification to this ideology, the provider has a responsibility to ensure security failure which should be compensated for. For instance, work in the following studies, Kuan Hon et al., 2012.
Considering work by Zhou et al, 2013 and JIANG et al, this is evident that security parameters are an area still requiring to be fully addressed in the research community. If the research community put more focus in inclusion of security parameters such as confidentiality and integrity, this will ensure providers, consumers and any other third parties are fully informed on the gravity of security failures. As a strategic approach, this study will suggest a SLA QoS solution that will incorporate crucial security elements such confidentiality
3.4 Problem Requirements
This identifies requirements needed to make a proposal for a solution that will extend SLA to include security parameters such as confidentiality and integrity. This is done in anticipation for future requirements which may require modification. Therefore, features modifiability in the unmeasurable requirements section
3.4.1 Requirements definitions for SLA
SLA Measurable requirements (Qualities)
Theoretically, SLA quality specifications can be addressed and specified if both stake holders have an understanding on measuring and verification of the outcome (Dobson, 2005; Bianco et al, 2008). The following requirement specifications are based on measurable and unmeasurable qualities;
Accuracy: This is measurable by errors in service delivery. Periodically, errors can be collected to ascertain average occurrence.
Capacity: This is a measurement of data handling capacity. In web services, it measures reasonable number of requests that can be made over a stipulated time.
Cost: This refers to costs such as; (i) service requests costs per service, (ii) data size (ii) peak hours requests
Latency: This is defined by the time taken between a service request and execution.
Trial/ Provisioning time: This is the time between consumer registration and initial service exploitation.
Reliability: This concerns delivery mechanism and guarantee. This also includes that criteria in which message delivery takes place. For instance, by priority order.
Scalability: This concerns service elasticity. To elaborate this fact, it regards to the ability to maintain speed while coping with increasing demands from consumers with time. This is inclusive of other factors such as reliability and possibility to remove or add instances.
Reversibility: In web-based services such as cloud, retrieval and deletion of data by the provider and consumer can be done as agreed in the contract.
SLA unmeasurable requirements (Qualities)
Interoperability: This concerns communication facilitation between different entities.Given such, information is communicated via semantics operating as agreed (Brownsword, 2004).
Modifiability: This concerns the ability to adapt to relevant changes as required to accommodate factors such as change in requirements. Possible changes relevant to modifiability are such as;
- interface
- implementation.
Security: This is the ability of a system or service to reject unauthorised exploitation of resources, requests and privileges among others. Apart from committing to provisioning of quality aspects such as uptime and connectivity, providers need to prioritise security. For the security equation to balance, the provider need to address the importance of security over other quality related parameters to the consumers. Addressing security issues to consumers smoothens the process of initiation for security negotiation. When implementing security as a measure for resistance of unauthorised access or exploitation, this can be done through the following mechanisms (Bianco et al 2008);
- consumer/user authentication – This is an access control strategy to ensure that services exploitation is based on authorisation rather than random access. A complete protocol for authentication normally holds user/ consumer attributes such as the following, an email address, unique identifier and a personalised greeting to address the consumer when they log in, such as, “Good evening, Isaac”. Should this be the users first time to make a service request, they are automatically requested to go through registration procedures and create a password.
- consumer/ user authorisation – This is a state of being granted access to resources following being authenticated. For example, the consumer trying to gain access to a web based service, they make a quest after discovery process. When they quest for a service they may be granted access following successful authentication of their details.
- data encryption- In web based services, data encryption takes place on applications and Simple Object Access Protocol (SOAP). Data encryption in web services is done by use of numerous encryption algorithms. However, each algorithm poses own limitations. Combining cryptography algorithm can be done to overcome the limitations (Kadam and Khairnar, 2015).
Key parameters that can be used in defining security qualities are such as the ability of a system or web service to provide (Manoj and Chandrasekar, 2013; Siddique and Muhammad, 2014);
- Non-repudiation: This is a security control feature for making senders and recipients accountable for having send or received communicated messages non-denial.
- Confidentiality: This is achieved by use of cipher text. Text is encrypted and decrypted to originality on the other end
- Integrity: This is a measure for ensuring accuracy. Data accuracy is ensured by restriction of unauthorised modification when data is being stored or processed.
- Assurance: This is a promise made for provision of security to the consumers. For the consumers to have confidence in the provider (s), promises made shall be met.
- Auditing: In Service Level agreement security audits are carried out systematically. This is a way to ensure that their existence last as they are just contacts rather than legally bound agreements (Barbosa et, al 2006). This can be done in the following ways;
- Manual/technical assessment
- Vulnerability scans
- Application reviews to identify violations
3.5 Design and Development
3.5.1 Proposed solution: An Approach to Secure Service Level Agreements
Proposed Service Level Agreement Composition
The proposed SLA will be composed of the following;
- Negotiation: (Blackwell and Dixon, 2003; Rahman, 2000; The Art of Service, 2001)
Responsibilities for each entity (
provider and
consumer) should be negotiated. Negotiation should be done in consideration to requirements and constrains from each entity. This strategy anticipates optimised SLA provisions.
- Agreement: (Blackwell and Dixon, 2003; The Art of Service, 2001)
An agreement should be reached through negotiation. Establishment of an agreement from both entities in negotiated specifications/aspects, is crucial as it lays a foundation for successful deployment. During the process of negotiation and reaching an agreement, both stakeholders become more informed. Due to understanding each other’s needs, preferences, and priorities, among others, a strong relationship develops.
- Quantifying service levels: (Blackwell and Dixon, 2003; Rahman, 2001)
This is a performance assessment. Key performance indicators (KPIs) are among the most appropriate tools for testing the pilot project Velimirovic et al., (2011)
This project anticipates use of security management as equality effective for monitoring and determining performance. This may also involve exploring consumer preferences or requirements. By doing so costs and gains become justifiable.
- Clarification of responsibilities: (Blackwell and Dixon, 2003; The Art of Service, 2001)
For guaranteed QoS provision, responsibilities should be clarified between provider and consumer. All responsibilities assigned in the agreement process are featured in the proposed SLA.
- Security obligations: (Prasad Padhy et al, 2012)
For successful implementation of security parameters in the proposed solution, both parties should act responsibly abiding by the agreement made. The provider has the sole responsibility to ensure implementation and management of security parameters as agreed. On the other hand, the consumer should also abide by the terms of the agreement. Failure of the service provider to commit o their promise may result in financial loss. On the other hand, where the consumer is found failing to abide or responsible for security violation, there are consequences too. The Lifecyle below in
figure 4, indicates how the proposed solution may be implemented, while
figure 5 shows the security management;
Figure 4: Proposed solution Lifecycle
Phase 1: Negotiation Phase 
Provider and Consumers Agree on;
- Inclusion of confidentiality and integrity to QoS
Phase 2: Enforcement and Deployment phase 
- Activation of security parameters/mechanism
Phase 3: Management and Monitoring phase 
- Investigating security breaches
Phase 4: Remediation 
- Identification of security violations and application of counter measures/remedies
Phase 5: Review/Termination 
- Restructuring of SLA terms, In some cases, possible dissolution
Use of phases in the SLA lifecycle promotes effective management in web based services. This is crucial considering shared responsibilities between both stakeholders of the agreement. Additionally, using a lifecycle is among development fundamental aspects in the web services paradigm (Rojas et al, 2016).
Phase 1 - Negotiation Phase: In relation to the proposed solution. The following takes place between the provider and consumer parties in phase 1;
- Defining terms of agreement
- Requirements specification for security parameters for extension of QoS in SLA
- Negotiation
Phase 2 - Enforcement and Deployment: This is the stage at which the negotiated security parameters are enforced in SLA and delayed. The provider and consumer trade on the following conditions;
- Finance
- Acceptable services
Phase 3 - Management and Monitoring phase:
Required services execution and management takes place. This is done subject to obligation of defined security parameters. Management takes place in form of the following tasks;
- Real-time monitoring of the SLA
- Ensuring compliance
- Performance reports
- Reactive procedures
- Enforcement of polices
- Investigation and controlling of SLA security violations
Phase 4 – Remediation:This is a phase at which a remediation takes place between both stakeholders in respect of the following;
- Corrective procedures following identification of any area of dysfunction
Phase 5 - Review/Termination: The “
agreement” is thereby goes through dissolution procedures. Outcome of this phase is determined by the following reasons;
- Expiration of the agreement/contract
- Security or contractual violations
- Request from the consumer
SLA Security management
Security Management: Aparecida de Chaves et al. (2010).
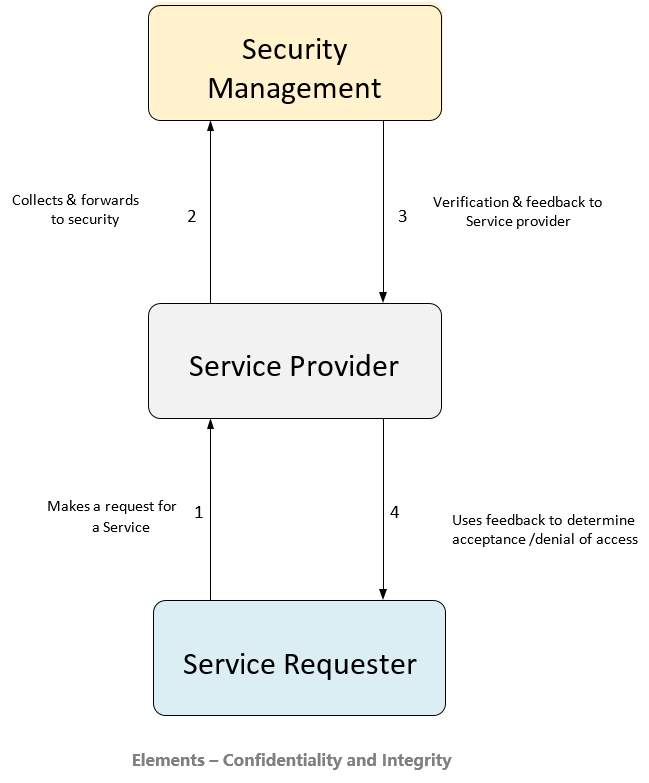
For effective functionality and sustainability and promotion of “fitness for purpose”, once successfully established, the proposed solution needs continuous/ongoing management. Ongoing management will be done in corporation of entire lifecycle parameters. This is crucial due to constant changing nature of web services deployment. Diagram Figure 5 below, had been developed for this study in Microsoft Visio(2017) However, due to nature of moving components it has been found reasonable to display a screenshot version..
Figure 5: SLA Security Management
 CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
Chapter overview
A critical analysis of the methodology will take place in this chapter. Results from the survey, study form existing work and the proposal are all scrutinized. This will be used to identify advantages and disadvantages that may be associated with the new solution.
4.1 Evaluation
CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
Chapter overview
A critical analysis of the methodology will take place in this chapter. Results from the survey, study form existing work and the proposal are all scrutinized. This will be used to identify advantages and disadvantages that may be associated with the new solution.
4.1 Evaluation
To identify significance of this project, work has been centered on an in-depth study on Service Level Agreements (SLA) security concerns. With consideration to wider deployment of web services and the need to elevate security principles, it has been found in this study that secure Service Level Agreements are crucial. Research findings revealed a concentrated focus on Quality of Service aspects features such as speed and availability while security has been overlooked. Relevancy and suitability of the proposition made in the study is based on a combination of survey results and literature review on web services and SLA respectively. Focus on this project has been centered on addressing the importance of security aspects to aid QoS. Significance of addressing security issues and proposing a solution for securing SLA, lies on an effort to bridge the security gaps resulted by lack of focus on security concerns in SLA (Cottrell, 2003).
4.1.2 Advantages
- The proposed solution is a strategic measure for inclusion key security parameters to extend SLA Quality of Service. Improvement of the SLA thorough inclusion confidentiality and integrity establishes robust SLA suitable for purpose.
- Considering the rate at which security threats are growing in distributed computing, there is a need for entering SLA agreement that promises security.
- A secure SLA gives more assurance to consumers and gains trust.
- Offering security as a service is a valuable competitive weapon, considering wide deployment nature of web services, it makes those that promise security more favorable as opposed to quality centered.
- An Approach to Secure Service Level Agreements sounds very promising and is anticipated to elevate security standards in web based services. This may attract positive feedback from consumers.
4.1.3 Proposed solution limitations
- Acceptance of something new may be quite challenging. This could be faced with conflicting ideologies some of regarding it limited in research. Consumers on the other hand may feel it sounds too good to be true, thereby resulting in skepticism/doubts.
- They may be costs associated in dissolving existing agreements, resulting in web services providers not considering change.
- The newly proposed solution needs constant reviews to keep up with advancing technology.
4.2 Challenges of An Approach to Secure Service Level Agreements
Considering current research mainly focus on Quality of Service, several challenges may threaten success of proposed solution. This for example;
Implementation of the newly proposed idea often proves difficult. This is a dysfunctional threat.
Due to increased data complexity in distributed computing, it may prove very difficult to introduce the proposed solution and expect guaranteed efficiency. Constant reviews are crucial, therefore makes management a huge challenge.
- Management of the proposed solution
Due to implementation and data complexity issues, management becomes a role that may need to be fully assigned to a security expert. This may come costs.
4.4 Project Limitations
Shortfall of security concerns in Service Level Agreement has been at the centre of this study. A significant number of sources has been consulted for literature review in the study. The result of which is complexity of information spanning from early 2000s to present. Given the stipulated guidelines in which the work had to be carried out among other obstacles, time management has been affected in many ways. Therefore, with regards to the survey carried out in the study, it has not been possible to revisit participants for feedback.
CHAPTER 5: EVALUATION, CONCLUSION AND FUTURE WORK
Conclusive summary
Research and all work carried out in this study aimed at determining other parameters outside Quality of Service that are crucial in establishing successful SLAs in web-based services. This chapter concludes the study taken on SLA. It gives an overview of all the project chapters (chapter 1, chapter 2, chapter 3 and chapter 4) including suggested future dimension of the project.
Chapter 3: PROPOSED MODEL
5.1 Conclusions
The following hypothesis has been put to test in this study, “Web Services are widely deployed and play an important role in today’s Internet paradigm”. Example of web services are such as holiday booking, flight booking systems and amazon web services in e-commerce among other mission critical services. The unique nature of web services deployment enables collection of numerous service providers in one pool making consumer quests for services easier. Service Level Agreements (SLA) are increasingly gaining popularity in web based services such as email, e-commerce, cloud and many other distributed computing environments. A comprehensive study on SLA has been done in this project to examine the extent at which existing work in SLA covers security parameters. Focus has been directed on investigating the extend in which security concerns such as confidentiality and integrity are covered in existing WS-Agreement and WSLA. Work in this report does not only examine Service Level Agreements but also proposed a solution that will extend QoS to include security parameters such as confidentiality and integrity. In addition, a dissemination of the SLA composition has been carried out and pros, cons and challenges of implementing a newly proposed have been considered through critical analysis of the methodology.
The overwhelming amount of literature consulted in this study is evident that majority SLA focus is concentrated on QoS quality aspects such as availability, reliability and speed among others but failing to attend to security related aspects. This project has been carried out in anticipation for enhanced security in SLA through adoption of lacking parameters. For ensuring “fitness for purpose” and improved effectiveness, a representative number of supposed consumers had been selected randomly to take part in a voluntary survey. Inclusion of consumers’ is important as they will have an opportunity to voice their security concerns. The results of which had been used in consideration for consumer requirements in the proposal.
Overall, Chapter 1 marked the introduction of the study, Chapter 2 gave an overview of web services to give the reader a clear understanding on them. In addition, chapter 2 includes establishment of the relationship between web services and Service Level agreements and includes literature review of existing work on SLA. Work on existing SLA is the core attribute of this project as the proposed solution is based on it. Design and development of the proposed solution took place in Chapter 3, while a critical analysis of the proposed solution had been done in chapter 4. Conclusively, Chapter 5 accounts for the hypothesis and all work carried out through the report and suggests future work.
5.2 future work
As this is a pilot project. Future work suggests testing the solution for use in a distributed computing environment. Another suggestion for future improvement is to make constant reviews to the solution. This will assist in identifying strengths and weaknesses as well as planning towards adoption of future requirements and disaster planning in case of possible SLA failures.
Reminder Comment: Now work in this study excluding Literature review is totals 11670
Appendices
Appendix 1: Analyzing security in Service Level Agreement questionnaire based Survey
Attention to applicant
“Web Services are widely deployed and play an important role in today’s Internet paradigm”. For satisfaction of user requirements and legal fulfillment, it is currently crucial for web- based services to have a Service Level Agreement (SLA) in place. Given such, as part of a project on analyzing (SLA) for user involvement, am conducting a survey to investigate user security awareness in services such as, email, storage and cloud all falling under web-based services. This survey is expected to be taken in an average of 5 minutes. Your contribution is much appreciated without critics. In consideration to Data Protection 1998 relating to user participant details, information given in this survey is anonymized and is used appropriately with relevancy to project.
Note: participation in this survey is voluntary and not subject to any obligations and contractual agreements. Therefore, please feel free to exclude yourself from the study at any time without notice.
- How frequently do you use cloud based applications (i.e. Banking, business applications, social media, etc.)?
Much Less Very Frequent
1--------------------2----------------3----------------4---------------5
- Do you store any personal or professional data in the cloud?
☐ Personal ☐ Professional ☐ Both
- Are you worried at all about the security of the cloud-based applications or data stored in the cloud?
Not at all Very Much
1--------------------2----------------3----------------4---------------5
- Of the applications that you use, which are you most concerned about someone hacking into?
☐ Banking ☐ Email ☐ Social Networking ☐ Cloud Storage
- Which Social networking website are you mostly concerned about for misuse of your data from hackers?
☐ Facebook ☐ Snapchat ☐ Instagram ☐ WhatsApp
- Which Cloud storage are you mostly concerned about for misuse of your data from hackers?
☐ Dropbox ☐ One Drive ☐ Google Drive ☐ iCloud ☐ Other
- Which email providers are you mostly concerned about for misuse of your data from hackers?
☐ Yahoo ☐ Hotmail/Outlook ☐ Gmail ☐ Other
- What system for file storage and sharing does your peer ask you to use?
☐ Internal network ☐ Dropbox ☐ Google Drive ☐ iCloud ☐ One Drive
- What email provider does your peer ask you to use?
☐ Yahoo ☐ Hotmail/Outlook ☐ Gmail ☐ Other
- When it comes to your data privacy, who are you most concerned with?
☐ Government ☐ Family ☐ Blackmailers ☐ Marketing companies ☐ Not concerned
- How do you most frequently share documents?
☐ Email ☐ Cloud Storage ☐ I don’t share
- What are your main worries regarding data insecurity/exposure?
☐ Nothing ☐ My peers will know my secret ☐ Govt. will have access to my private data ☐ Marketing firms will have access to my private data
- What is your age group?
☐ 12-18 ☐ 19-25 ☐ 26-32 ☐ 33 and above
14)
What do you consider as level of your IT/ internet security awareness?
☐ none ☐ beginner ☐ intermediate ☐ proficient
15) What is your gender?
Male ☐ female ☐ prefer not to say☐
Signature of participant Date:
Name of researcher:
Signature of researcher Date:
Appendix 2: Survey respondent Consent
Project Title: Analysing security in Service Level Agreement (SLA)
Researcher: Isaac Zennah
Participant:
University: Liverpool John Moores
School: Computing and mathematical Sciences
Average Survey time: 5 minutes
Key: ☐ tick box
- I have been given full information on the subject and have agreed to take part. ☐
- I understand that this survey is subject to voluntary conditions. Therefore, I have been informed that I can opt out any time without any obligations ☐
- Assurance had been given that under Data Protection Act 1998 any information given will be used with relevance to the study. I will be consulted should there be any need for third party distribution. ☐
- I agree to take part in the survey that the researcher is conducting for analysis as required for a project above. ☐
- I had been informed any future use of information from the survey related to the study remains confidential ☐
Researcher: ___________________ Date:
Signature: _____________________
Participant: ____________________ Date:
Signature: ____________________
Appendix 3: Records of monthly supervision meetings
November Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date: 4
th November 2016
| Main issues / Points of discussion / Progress made |
| Main issues – Completing ethics application form
Points of discussion – Question about creating project topic from the original idea, and to understand how survey data can be collected and used in a legally acceptable manner that meets LJMU standards.
Progress made – Submission of project specification was made within deadline. |
| Actions for the next month |
| To search a variety of academic resources for journals, research papers and textbooks that relate to my project and compile them base on their relevance. |
| Deliverables for next time |
| Draft literature review. |
| Other comments |
| I Plan to attend Academy Skill support workshops during the reading week. I believe the workshops covering critical analysis and thinking, researching, paraphrasing, and referencing are crucial to my project’s success. |
 December Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
December Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date:...............02/12/12
| Main issues / Points of discussion / Progress made |
| Main issues – Not being able to submit Literature review as planned due to family problem.
Point of discussion – Setting new date to complete Literature Review, also the issue of designing and developing project questionnaires
Progress made – No substantial progress has been made this month, reason being I was unable to meet deliverable set by my supervisor last month. |
| Actions for the next month |
- To complete Literature Review and project questionnaires
- Allocate more time to my project to recover lost progress
- Endeavour to meet all recommendations
|
| Deliverables for next time |
| Focus more on the project for the next month as time is running out. |
| Other comments |
|
Supervisor signature:

........................
Student signature: ..........................
January Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date: 20/01/2017
| Main issues / Points of discussion / Progress made |
- Questionnaires in finish stages, about to be sent out
- Previous recommendation was acted upon by finishing my Literature review over the Christmas holiday.
- Currently working on my proposed solution – what I intend to achieve in my project
|
| Actions for the next month |
- Will chase and collect questionnaires from participants
- Plan to complete methodology
|
| Deliverables for next time |
| Check the marking criteria and prepare your report in the expected format.
Analyse the problem and requirements before the solution so that your solution will address those issues you identified during analysis. |
| Other comments |
|
Supervisor signature:

........................
Student signature: ..........................
February Report
6000PROJ Final Year Project
Monthly Supervision Meeting Record
Student: ...................................Isaac Zennah Date: February 2017
| Main issues / Points of discussion / Progress made |
- To discuss issues concerning setbacks I have experienced
- I have completed chapter 1 and 2
|
| Actions for the next month |
- To work on analysis of problem and problem requirement
|
| Deliverables for next time |
|
| Other comments |
| I feel I am losing time - I wrote quite a bit but I had to rewrite most of it because I realised some ideas were not well developed. However, I have increased the time I spend on my project to make up for lost time. |
Supervisor signature: ........................
Student signature: ……………………………………….
March Report
6000PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date: March 2017
| Main issues / Points of discussion / Progress made |
- To approve questionnaire
- To discuss project structure
- On reflection of last supervisory meeting, I have Written reference of every project research – therefore I have come up with project structure which if approved I wish to follow in my project
- I have drafted the abstract to follow as the project progresses, namely: -
- Hypothesis
- Aims
- Methodology
- Findings
- Conclusion
|
| Actions for the next month |
| If questionnaire is approved I will distribute 25 – 27 in return for 18-20 to accommodate an expected withdrawal of participants. |
| Deliverables for next time |
|
| Other comments |
|
Supervisor signature:

........................
Student signature: ..........................
Appendix 4: Report Structure Documentation
| Report Structure Documentation |
- SUBJECT
Analysing security in Service Level Agreement (SLA) |
- SUBMISSION DATE
21 April 2017 |
- REPORT TYPE
Final Year Project (36%) of the undergraduate BSc (Hons) Cyber Security |
- AUTHOR
Isaac Zennah |
- UNIVERSITY NAME
Liverpool John Moores |
- ABSTRACT (376 words)
A total of 5 paragraphs |
SUBJECT KEY WORDS
Web-based services,
Service Level Agreement (SLA),
Quality of Service (QoS),
confidentiality, integrity |
NUMBER OF SOURCES CONSULTED IN THE STUDY |
 Web Services Architecture roles
Web Services Architecture roles
![Figure 5.8: Service Level Agreement Life-Cycle [57]](https://images.ukdissertations.com/13/0010698.003.jpg) 2.3 Linking SLA to Web Services and addressing security issues
There is a wide coverage research on SLAs (Clark and Gilmore 2006; Miller 2012; Stanik et al 2014). However, it is a proven factor that majority existing SLAs are lacking confidentiality and integrity while focusing more on Quality of Service (Zhou et al 2014). The scenario in figure 2 below, shows how web services are exploited and gives an analysis of elements that consumers are likely to be enticed by, to an extent of prioritising Quality of Service. This indicates the focus on Quality of Services seem to have a stronghold in relationships between providers and consumers (Mani and Nagarajan 2002). Current research suggests that Service Level agreements on a Service Oriented architecture focus on Quality of Service (QoS) (Bianco et al 2008; Zhou et al 2014). Dukee (2010) suggested SLAs are a form of security to the consumer as compensation is provided in breach of the agreement. El-Awadi et al (2015) pointed out there is a lot of scepticism from numerous consumers relating cloud providers’. The scepticism is a result of the gap between their Quality of Service promises and what the SLA has on offer. As a result, focus on QoS with diverted attention from other security parameters, potentially resulting in economic adversities has been identified in this study as an unresolved issue that has existed for a long time (Li-jie Jin et al 2002).
The pictorial diagram below, named figure 2 is a typical demonstration of web services interoperability in day to day business between the providers and consumers (Li-jie Jin et al 2002). In the picture, Ouzzanni and Bouguettaya (2004), gave a three-step scenario a consumer named Ravi takes in planning his journey. In step (a) Ravi makes a query for an air ticket with 3 air lines named Western Air Lines, Alpha Airlines and Unified Airlines. In step (b) Ravi makes a query for accommodations among Country Hotel, StayInn and Blueridge Inn, then (c) a car from a rental company between SmartCars, CarForLess, MegaHertz. All the required services for Ravi’s quest are accessible in a large pool (Frankova 2010). An in-depth analysis of the diagram above proves the fact that the consumer’s quest is more focused on elements such as “best quality” which is to do with transactional Quality of Service (QoS) in Web services (Bianco et al 2008). Based on QoS focus of web services, my assumption is that SLA focus in pursuit of the same idea may be to satisfy consumers passion for quality. The final decision made by Ravi indicates that Quality of services is at the top of consumers’ priorities followed by others such as cost and availability among others. It is therefore necessary for providers to put more effort in addressing security parameters such as confidentiality and integrity. This study anticipates that Extending security concerns to SLA to include confidentiality and integrity, may positively add value to SLA.
Figure 2. Interoperability in web services
(Ouzzani and Bouguettaya 2004)
2.3 Linking SLA to Web Services and addressing security issues
There is a wide coverage research on SLAs (Clark and Gilmore 2006; Miller 2012; Stanik et al 2014). However, it is a proven factor that majority existing SLAs are lacking confidentiality and integrity while focusing more on Quality of Service (Zhou et al 2014). The scenario in figure 2 below, shows how web services are exploited and gives an analysis of elements that consumers are likely to be enticed by, to an extent of prioritising Quality of Service. This indicates the focus on Quality of Services seem to have a stronghold in relationships between providers and consumers (Mani and Nagarajan 2002). Current research suggests that Service Level agreements on a Service Oriented architecture focus on Quality of Service (QoS) (Bianco et al 2008; Zhou et al 2014). Dukee (2010) suggested SLAs are a form of security to the consumer as compensation is provided in breach of the agreement. El-Awadi et al (2015) pointed out there is a lot of scepticism from numerous consumers relating cloud providers’. The scepticism is a result of the gap between their Quality of Service promises and what the SLA has on offer. As a result, focus on QoS with diverted attention from other security parameters, potentially resulting in economic adversities has been identified in this study as an unresolved issue that has existed for a long time (Li-jie Jin et al 2002).
The pictorial diagram below, named figure 2 is a typical demonstration of web services interoperability in day to day business between the providers and consumers (Li-jie Jin et al 2002). In the picture, Ouzzanni and Bouguettaya (2004), gave a three-step scenario a consumer named Ravi takes in planning his journey. In step (a) Ravi makes a query for an air ticket with 3 air lines named Western Air Lines, Alpha Airlines and Unified Airlines. In step (b) Ravi makes a query for accommodations among Country Hotel, StayInn and Blueridge Inn, then (c) a car from a rental company between SmartCars, CarForLess, MegaHertz. All the required services for Ravi’s quest are accessible in a large pool (Frankova 2010). An in-depth analysis of the diagram above proves the fact that the consumer’s quest is more focused on elements such as “best quality” which is to do with transactional Quality of Service (QoS) in Web services (Bianco et al 2008). Based on QoS focus of web services, my assumption is that SLA focus in pursuit of the same idea may be to satisfy consumers passion for quality. The final decision made by Ravi indicates that Quality of services is at the top of consumers’ priorities followed by others such as cost and availability among others. It is therefore necessary for providers to put more effort in addressing security parameters such as confidentiality and integrity. This study anticipates that Extending security concerns to SLA to include confidentiality and integrity, may positively add value to SLA.
Figure 2. Interoperability in web services
(Ouzzani and Bouguettaya 2004) 2.4 Existing Service Level Agreements
Investigating the extend in which security concerns such as confidentiality and integrity are covered in existing WS-Agreement and WSLA,
CHAPTER 3: PROPOSED SOLUTION
Chapter overview
Work in this chapter focuses on proposing a solution to extend security concerns to incorporate confidentiality and integrity. Questionnaire based survey results are to be included in this section and identified security holes from literature review will be addressed, followed by a suggested solution to improve security in SLA. A suggested solution will be used for as project proposal for improvement.
3.1 Questionnaire Survey
A questionnaire is a research tool used in obtaining information from a representative population selected to take part in a survey. Information obtained through questionnaires is motivated by various reasons such as identifying consumer trends, patterns, opinions and trends. Questionnaires with the objective to analyse results are normally made up of closed questions. The objective of this survey is to collect information relevant to web services consumers and their online behaviour, while abiding to Data Protection Act 1998 (Tipping, 2016). Data protection Act is in force in the interest to protect information relating to individuals. This makes it illegal for the individual conducting a survey to use data in any way apart from what it had been obtained for (Tipping, 2016). Displaying that data in one table makes it easier to count number of opted answers for each question. By so doing it makes it easier to plot charts/graphs for analysing the results. This also eases the process of converting data to information for presentation to individuals whom it may need to be shown to (Durbin, 2004) A questionnaire based survey has been used in this project for consumer involvement. Results drawn from the survey ascertains relevance of the survey to the study. An in-depth results analysis has been done on each question in this study. This has been done with consideration to make it easier for disseminating information as there are many questions.
3.1.1 Survey Data Results
Key:
P1 to P20 = Participant 1 to participant 20
Q1 to Q13 = Survey Questions
Numbers for example 5,3,1,2 represent opted answers in the survey by each participant. The table had been designed in way that makes participant numbers to tally with their opted responses and question numbers.
Table 1 is made up of all the data results from the questionnaire survey. P 1 to P 20 represents number of participants to promote anonymity in the survey.
Instructions for using table 1 data
Formation of table 1 has been formulated as a time management strategy. This has been done by displaying all data from the survey in one table for use in analysing results.by so doing it makes it presentable rather than having to keep counting responses throughout the analysis. The following is a breakdown on how table 1 has been used in displaying all results;
Using a combination of P1 to P 20 and Q1 to Q13, numbers in between are opted responses to be matched with participant, question number. By so doing, small tables of data had been produced faster for all questions. 3 D pie charts displaying results in fractions (%) had been produced using data from results obtained from each question. For more clarification, reference can also be made through the key above.
Table 1. Questionnaire results
2.4 Existing Service Level Agreements
Investigating the extend in which security concerns such as confidentiality and integrity are covered in existing WS-Agreement and WSLA,
CHAPTER 3: PROPOSED SOLUTION
Chapter overview
Work in this chapter focuses on proposing a solution to extend security concerns to incorporate confidentiality and integrity. Questionnaire based survey results are to be included in this section and identified security holes from literature review will be addressed, followed by a suggested solution to improve security in SLA. A suggested solution will be used for as project proposal for improvement.
3.1 Questionnaire Survey
A questionnaire is a research tool used in obtaining information from a representative population selected to take part in a survey. Information obtained through questionnaires is motivated by various reasons such as identifying consumer trends, patterns, opinions and trends. Questionnaires with the objective to analyse results are normally made up of closed questions. The objective of this survey is to collect information relevant to web services consumers and their online behaviour, while abiding to Data Protection Act 1998 (Tipping, 2016). Data protection Act is in force in the interest to protect information relating to individuals. This makes it illegal for the individual conducting a survey to use data in any way apart from what it had been obtained for (Tipping, 2016). Displaying that data in one table makes it easier to count number of opted answers for each question. By so doing it makes it easier to plot charts/graphs for analysing the results. This also eases the process of converting data to information for presentation to individuals whom it may need to be shown to (Durbin, 2004) A questionnaire based survey has been used in this project for consumer involvement. Results drawn from the survey ascertains relevance of the survey to the study. An in-depth results analysis has been done on each question in this study. This has been done with consideration to make it easier for disseminating information as there are many questions.
3.1.1 Survey Data Results
Key:
P1 to P20 = Participant 1 to participant 20
Q1 to Q13 = Survey Questions
Numbers for example 5,3,1,2 represent opted answers in the survey by each participant. The table had been designed in way that makes participant numbers to tally with their opted responses and question numbers.
Table 1 is made up of all the data results from the questionnaire survey. P 1 to P 20 represents number of participants to promote anonymity in the survey.
Instructions for using table 1 data
Formation of table 1 has been formulated as a time management strategy. This has been done by displaying all data from the survey in one table for use in analysing results.by so doing it makes it presentable rather than having to keep counting responses throughout the analysis. The following is a breakdown on how table 1 has been used in displaying all results;
Using a combination of P1 to P 20 and Q1 to Q13, numbers in between are opted responses to be matched with participant, question number. By so doing, small tables of data had been produced faster for all questions. 3 D pie charts displaying results in fractions (%) had been produced using data from results obtained from each question. For more clarification, reference can also be made through the key above.
Table 1. Questionnaire results
 Question 2: Do you store any personal data in the cloud?
This question is aimed at generating statistics on cloud storage use. Although this is being tested on a significant number of consumer population, any data obtained will be generated into useful information as it is not practical to obtain information from a majority population. Responses given indicate 21% as the least number of people using cloud storage. This could be due to various things such as lack of knowledge on the type of technology, insecurities towards the cloud among others. 26% being the median number who may have intermediate knowledge or any other reasons. The highest population at 53% presumes the growth dependency in web-based services. This may also mean majority population of consumers find cloud storage the most reliable due to the ability to access stored data from anywhere (Sun et al., 2014).
Table 3. Question 2 data analysis
Question 2: Do you store any personal data in the cloud?
This question is aimed at generating statistics on cloud storage use. Although this is being tested on a significant number of consumer population, any data obtained will be generated into useful information as it is not practical to obtain information from a majority population. Responses given indicate 21% as the least number of people using cloud storage. This could be due to various things such as lack of knowledge on the type of technology, insecurities towards the cloud among others. 26% being the median number who may have intermediate knowledge or any other reasons. The highest population at 53% presumes the growth dependency in web-based services. This may also mean majority population of consumers find cloud storage the most reliable due to the ability to access stored data from anywhere (Sun et al., 2014).
Table 3. Question 2 data analysis
 Question 3: Do you store any personal or professional data in the cloud?
This is just to have a view on whether consumers participating in the survey utilise any cloud storage services. For those who indicated to use cloud, more further requirements of the question were that they indicate the type of data they store. In this question, a Likert scale was used. The approach of setting scales in answering questions, allows participant to have a judgement within the scale (Moors et al., 2014).
Table 4. Question 3 data analysis
Question 3: Do you store any personal or professional data in the cloud?
This is just to have a view on whether consumers participating in the survey utilise any cloud storage services. For those who indicated to use cloud, more further requirements of the question were that they indicate the type of data they store. In this question, a Likert scale was used. The approach of setting scales in answering questions, allows participant to have a judgement within the scale (Moors et al., 2014).
Table 4. Question 3 data analysis
 Question 4: Of the applications that you use, which are you most concerned about someone hacking into?
Motivation of the question lies on investigating the type of web-based applications that consumers feel insecure about despite need for exploitation. The different responses of 0%, 40 and 60% is a clear indication that despite the growing number of consumers exploiting web services, there are also growing security concerns. Complex security management in widely distributed computing environments is resulted by increased demand their use (Armoni, 2002)
Table 5. Question 4 data analysis
Question 4: Of the applications that you use, which are you most concerned about someone hacking into?
Motivation of the question lies on investigating the type of web-based applications that consumers feel insecure about despite need for exploitation. The different responses of 0%, 40 and 60% is a clear indication that despite the growing number of consumers exploiting web services, there are also growing security concerns. Complex security management in widely distributed computing environments is resulted by increased demand their use (Armoni, 2002)
Table 5. Question 4 data analysis
 Question 5: Which Social networking website are you mostly concerned about for misuse of your data from hackers?
This is just to have a view of social networking security concerns from the representative consumers’ view point. By so doing it assists web services providers in working towards gaining consumer trust in those sites through improving SLA to adopt critical security concerns such as confidentiality and integrity. Despite Facebook being one of the most dominant social networks with survey results made up of majority population at 50%, is also the highest opted response indicating security concerns from users.
Table 6. Question 5 data analysis
Question 5: Which Social networking website are you mostly concerned about for misuse of your data from hackers?
This is just to have a view of social networking security concerns from the representative consumers’ view point. By so doing it assists web services providers in working towards gaining consumer trust in those sites through improving SLA to adopt critical security concerns such as confidentiality and integrity. Despite Facebook being one of the most dominant social networks with survey results made up of majority population at 50%, is also the highest opted response indicating security concerns from users.
Table 6. Question 5 data analysis
 Question 6: Which Cloud storage are you mostly concerned about for misuse of your data from hackers?
Formulation of this question is based on an insight to consumers’ insecurities named cloud storages. By so doing it may lead into speculating the reason behind their insecurity. This will be useful in proposing addition of those security parameters in the new SLA solution. By so doing it is anticipated that this will make the SLA negotiation less difficult.
Table 7. Question 6 data analysis
Question 6: Which Cloud storage are you mostly concerned about for misuse of your data from hackers?
Formulation of this question is based on an insight to consumers’ insecurities named cloud storages. By so doing it may lead into speculating the reason behind their insecurity. This will be useful in proposing addition of those security parameters in the new SLA solution. By so doing it is anticipated that this will make the SLA negotiation less difficult.
Table 7. Question 6 data analysis
 Question 7: Which email providers are you mostly concerned about for misuse of your data from hackers?
This is an investigation to find out email providers whose email services have a history of being hacked adversely affected consumers’. A further investigation will be on the security breaches faced by the email services to ascertain inclusion in SLA. Relating varying percentages representing consumer insecurities, it is a clear indication that if consumer scoring is to be used in email accounts, Yahoo at 60% will be highly likely to attract a lot of criticism. Another indication is that Hotmail/Outlook at 25% in still being viewed with a benefit of the doubt. It is therefore reasonable to say Gmail is the most trusted of the representative email based applications (Zara 2014).
Table 8. Question 7 data analysis
Question 7: Which email providers are you mostly concerned about for misuse of your data from hackers?
This is an investigation to find out email providers whose email services have a history of being hacked adversely affected consumers’. A further investigation will be on the security breaches faced by the email services to ascertain inclusion in SLA. Relating varying percentages representing consumer insecurities, it is a clear indication that if consumer scoring is to be used in email accounts, Yahoo at 60% will be highly likely to attract a lot of criticism. Another indication is that Hotmail/Outlook at 25% in still being viewed with a benefit of the doubt. It is therefore reasonable to say Gmail is the most trusted of the representative email based applications (Zara 2014).
Table 8. Question 7 data analysis
 Question 8: What system for file storage and sharing does your peer ask you to use?
This question is aimed at investigating consumers’ peer to peer networking preferences. Analysing peer-to peer networking is beneficial in network security is it gives a view of consumer trust levels in web services (Manoj et al., 2013). The level in which a web service may be preferred to others is mostly related to Quality of Service parameters such as reliability, availability and security concerns (Junqing et al., 2012).
Table 9. Question 8 data analysis
Question 8: What system for file storage and sharing does your peer ask you to use?
This question is aimed at investigating consumers’ peer to peer networking preferences. Analysing peer-to peer networking is beneficial in network security is it gives a view of consumer trust levels in web services (Manoj et al., 2013). The level in which a web service may be preferred to others is mostly related to Quality of Service parameters such as reliability, availability and security concerns (Junqing et al., 2012).
Table 9. Question 8 data analysis
 Question 9: What email provider does your peer ask you to use?
This is just to investigate the most favourable email applications/ services among peers. By so doing it assists in making further investigation for the choice of service.
Table 10. Question 9 data analysis
Question 9: What email provider does your peer ask you to use?
This is just to investigate the most favourable email applications/ services among peers. By so doing it assists in making further investigation for the choice of service.
Table 10. Question 9 data analysis
 Question 10: When it comes to your data privacy, who are you most concerned with?
This question is based on investigating consumer worries about data privacy. Data privacy is related to security elements such as confidentiality and integrity.
Table11. Question 10 data analysis
Question 10: When it comes to your data privacy, who are you most concerned with?
This question is based on investigating consumer worries about data privacy. Data privacy is related to security elements such as confidentiality and integrity.
Table11. Question 10 data analysis
 Question 11: How do you most frequently share documents?
Consulting participant frequency in sharing documents or files gives a view on their level of exploitation of file sharing applications in distributed computing environments. This opens discussions as to whether this is about Quality of Services or crucial security elements such as an SLA promising security concerns such as integrity and confidentiality.
Table 12. Question 11 data analysis
Question 11: How do you most frequently share documents?
Consulting participant frequency in sharing documents or files gives a view on their level of exploitation of file sharing applications in distributed computing environments. This opens discussions as to whether this is about Quality of Services or crucial security elements such as an SLA promising security concerns such as integrity and confidentiality.
Table 12. Question 11 data analysis
 Question 12: What are your main worries regarding data insecurity/exposure?
This question indicates the level of data security concerns, worrying consumers about invasion of privacy and data integrity compromisation. While a minority representative population indicates that they do not have data insecurity worries, most seem to worry about access of their private information from the government. Worries relating the government being able to access web services consumer private information, could be perceived to lack of knowledge that the government operate legally on a need to know basis. To elaborate this, it is mostly in the public interest that certain individuals may find themselves in such a situation. This is for example, if a serious crime that puts the public at risk occurs, this may attract the government’s involvement (Zoonen, 2016). Unlike the others, marketing firms are associated with cold calling which is an example that some services sale consumer information to third party (Phelps et al., 2000). This in most cases is a result of consumer activities online.
Table 13. Question 12 data analysis
Question 12: What are your main worries regarding data insecurity/exposure?
This question indicates the level of data security concerns, worrying consumers about invasion of privacy and data integrity compromisation. While a minority representative population indicates that they do not have data insecurity worries, most seem to worry about access of their private information from the government. Worries relating the government being able to access web services consumer private information, could be perceived to lack of knowledge that the government operate legally on a need to know basis. To elaborate this, it is mostly in the public interest that certain individuals may find themselves in such a situation. This is for example, if a serious crime that puts the public at risk occurs, this may attract the government’s involvement (Zoonen, 2016). Unlike the others, marketing firms are associated with cold calling which is an example that some services sale consumer information to third party (Phelps et al., 2000). This in most cases is a result of consumer activities online.
Table 13. Question 12 data analysis
 Question 13: What is your age group?
A total 20 students between 19-33+ participated in the survey. All participants are within Liverpool John Moores School of Computing and Mathematical Sciences took part in a voluntary survey for this project. 0% participated between 12-18. There are two main reasons as follows, anyone under 18 and is obliviously under normal circumstances would need parental consent to take part (). Obtaining parental consent for participants to satisfy legal and ethical issues will take time considering project time scale. 17% was made up of those aged 19 to 25, 39% was made up of participants in age 26 to 32. 44% indicates mature students were among those who were in the labs at the time of the survey.
Table 14. Question 13 data analysis
Question 13: What is your age group?
A total 20 students between 19-33+ participated in the survey. All participants are within Liverpool John Moores School of Computing and Mathematical Sciences took part in a voluntary survey for this project. 0% participated between 12-18. There are two main reasons as follows, anyone under 18 and is obliviously under normal circumstances would need parental consent to take part (). Obtaining parental consent for participants to satisfy legal and ethical issues will take time considering project time scale. 17% was made up of those aged 19 to 25, 39% was made up of participants in age 26 to 32. 44% indicates mature students were among those who were in the labs at the time of the survey.
Table 14. Question 13 data analysis
 3.2 Analysing the questionnaire based survey
Questionnaires provide a relatively cheap, quick, and efficient way of obtaining information from diverse audiences. Compared to the long and tedious research methods such as face to face interviews, questionnaires are among the most cost effective. You don’t need hire surveyors to ask people questions. A questionnaire can be placed on a website or simply sent via email. This eliminates printing costs and the need for the researcher to be present when the questionnaire is being administered (Brace, 2008).
Questionnaires allow the researcher to reach unlimited number of respondents since they are not constrained by the need of field researchers who can only cover a specific geographic area. For example, a researcher may decide to send mass emails to respondents across any region of choice. This greater reach also gives the researcher a unique opportunity of predefining a representative sample. For example, the researcher can choose emails as per pre-set variables and thus avoid sending random surveys.
Due to the highly-structured nature of questionnaire, it makes data analysis easier. Not only this but conducting advanced statistical tests been found to be seamless as the researcher is able to control the kind of data to expect from the respondents. This has time efficiency benefits. Therefore, where results are needed within a short space of time, it eases the process (Mitchell, 2009).
Finally, due to their static nature, questionnaires that are well designed and tested can always be re-used across different audiences with just some minor tweaks. Given the fact that questionnaire design can be time consuming, this capability greatly saves on the time taken to design and execute the surveys
Limitations of Questionnaire based surveys
Just like other research methods, questionnaires despite their wide usage have their own limitations. A major limitation arises due to the lack of physical contact between the researcher and the respondents. Mostly questionnaires are administered through digital platforms; online surveys and mobile surveys. This introduces a physical distance between the researcher and the respondents (Athanasiou, 2010).
One of the major disadvantages faced through questionnaires is that responses may be biased. This makes it hard to verify data authenticity in such cases (Athanasiou, 2010).
The process of producing and deploying questionnaires may be time consuming as it involves finding participants, appropriate environment and specified deadlines. In this case, the project is to be done within six months. This makes it hard as they are procedures to be followed such as legal and ethical issues. To figure out whether one can be part of the representative population, confirmation of their age is required, and this may mean approaching an alternative individual should age restrictions fail to be met. The survey in this study had been contacted on a voluntary basis, which leaves no obligations to any of the participants should they wish to opt out last minute.
Rationale of survey
Every dissertation is guided by a research question or hypothesis. After formulating the research question, the researcher chooses a data collection method suitable for gathering the required information. There are various ways in which data can be obtained in surveys. Data required for the survey somehow suggests the best approach to obtain it. Carrying out a survey is a crucial element in proposing projects involving consumers. This gives an insight in what is expected of the provider (Zhang, 2009).
Studies show that respondents are more honest and are willing to share rather sensitive information through surveys than face to face interview (Bowden et al., 2015). This gives surveys created around sensitive information an edge in terms of obtaining accurate and reliable information (Edward, 2009). A dissertation survey provides the data needed for analysis. A survey provides data that can be used to compare the dissertation findings with past research. Being able to compare the findings with past data is very important in establishing approaches in bridging gaps. Through the survey, the researcher can compare their research with past data. Apart from suggesting or producing a solution to bridge gap, a survey helps formulate recommendations for further research (Ilieska, 2013).
3.3 Analysis of problem
Quantifiable literature proves complexity on focus on Quality of service by existing work in Service Level Agreements (;; ; ; ; ; ;) as many refs as possible to justify quantifiability, at least 4-6 refs from lit review. This is a significant fact that focus on crucial security parameters in SLA, such as confidentiality and integrity is still immature in the research area. Meeting as many as possible security parameters in SLA will earn web services and SLA alike trust from consumers (Stankov et al, 2012). Meeting security requirements is the key to success in any business (reference). Zhou et al (2013) also addressed security issues as an important factor shadowing the SOA platform and development of applications associated with it. JIANG et al (2016) echoed web services dominance is also associated with multiple security issues adversely affecting reliability, confidentiality and data non-repudiation. This assumes more focus is directed in satisfying consumers’ measurable quality expectations such as speed, reliability, Accuracy, capacity, Scalability and costs. By doing so, a result of serious consequences such as financial loss to the web service providers may occur. In justification to this ideology, the provider has a responsibility to ensure security failure which should be compensated for. For instance, work in the following studies, Kuan Hon et al., 2012.
Considering work by Zhou et al, 2013 and JIANG et al, this is evident that security parameters are an area still requiring to be fully addressed in the research community. If the research community put more focus in inclusion of security parameters such as confidentiality and integrity, this will ensure providers, consumers and any other third parties are fully informed on the gravity of security failures. As a strategic approach, this study will suggest a SLA QoS solution that will incorporate crucial security elements such confidentiality
3.4 Problem Requirements
This identifies requirements needed to make a proposal for a solution that will extend SLA to include security parameters such as confidentiality and integrity. This is done in anticipation for future requirements which may require modification. Therefore, features modifiability in the unmeasurable requirements section
3.4.1 Requirements definitions for SLA
SLA Measurable requirements (Qualities)
Theoretically, SLA quality specifications can be addressed and specified if both stake holders have an understanding on measuring and verification of the outcome (Dobson, 2005; Bianco et al, 2008). The following requirement specifications are based on measurable and unmeasurable qualities;
Accuracy: This is measurable by errors in service delivery. Periodically, errors can be collected to ascertain average occurrence.
Capacity: This is a measurement of data handling capacity. In web services, it measures reasonable number of requests that can be made over a stipulated time.
Cost: This refers to costs such as; (i) service requests costs per service, (ii) data size (ii) peak hours requests
Latency: This is defined by the time taken between a service request and execution.
Trial/ Provisioning time: This is the time between consumer registration and initial service exploitation.
Reliability: This concerns delivery mechanism and guarantee. This also includes that criteria in which message delivery takes place. For instance, by priority order.
Scalability: This concerns service elasticity. To elaborate this fact, it regards to the ability to maintain speed while coping with increasing demands from consumers with time. This is inclusive of other factors such as reliability and possibility to remove or add instances.
Reversibility: In web-based services such as cloud, retrieval and deletion of data by the provider and consumer can be done as agreed in the contract.
SLA unmeasurable requirements (Qualities)
Interoperability: This concerns communication facilitation between different entities.Given such, information is communicated via semantics operating as agreed (Brownsword, 2004).
Modifiability: This concerns the ability to adapt to relevant changes as required to accommodate factors such as change in requirements. Possible changes relevant to modifiability are such as;
3.2 Analysing the questionnaire based survey
Questionnaires provide a relatively cheap, quick, and efficient way of obtaining information from diverse audiences. Compared to the long and tedious research methods such as face to face interviews, questionnaires are among the most cost effective. You don’t need hire surveyors to ask people questions. A questionnaire can be placed on a website or simply sent via email. This eliminates printing costs and the need for the researcher to be present when the questionnaire is being administered (Brace, 2008).
Questionnaires allow the researcher to reach unlimited number of respondents since they are not constrained by the need of field researchers who can only cover a specific geographic area. For example, a researcher may decide to send mass emails to respondents across any region of choice. This greater reach also gives the researcher a unique opportunity of predefining a representative sample. For example, the researcher can choose emails as per pre-set variables and thus avoid sending random surveys.
Due to the highly-structured nature of questionnaire, it makes data analysis easier. Not only this but conducting advanced statistical tests been found to be seamless as the researcher is able to control the kind of data to expect from the respondents. This has time efficiency benefits. Therefore, where results are needed within a short space of time, it eases the process (Mitchell, 2009).
Finally, due to their static nature, questionnaires that are well designed and tested can always be re-used across different audiences with just some minor tweaks. Given the fact that questionnaire design can be time consuming, this capability greatly saves on the time taken to design and execute the surveys
Limitations of Questionnaire based surveys
Just like other research methods, questionnaires despite their wide usage have their own limitations. A major limitation arises due to the lack of physical contact between the researcher and the respondents. Mostly questionnaires are administered through digital platforms; online surveys and mobile surveys. This introduces a physical distance between the researcher and the respondents (Athanasiou, 2010).
One of the major disadvantages faced through questionnaires is that responses may be biased. This makes it hard to verify data authenticity in such cases (Athanasiou, 2010).
The process of producing and deploying questionnaires may be time consuming as it involves finding participants, appropriate environment and specified deadlines. In this case, the project is to be done within six months. This makes it hard as they are procedures to be followed such as legal and ethical issues. To figure out whether one can be part of the representative population, confirmation of their age is required, and this may mean approaching an alternative individual should age restrictions fail to be met. The survey in this study had been contacted on a voluntary basis, which leaves no obligations to any of the participants should they wish to opt out last minute.
Rationale of survey
Every dissertation is guided by a research question or hypothesis. After formulating the research question, the researcher chooses a data collection method suitable for gathering the required information. There are various ways in which data can be obtained in surveys. Data required for the survey somehow suggests the best approach to obtain it. Carrying out a survey is a crucial element in proposing projects involving consumers. This gives an insight in what is expected of the provider (Zhang, 2009).
Studies show that respondents are more honest and are willing to share rather sensitive information through surveys than face to face interview (Bowden et al., 2015). This gives surveys created around sensitive information an edge in terms of obtaining accurate and reliable information (Edward, 2009). A dissertation survey provides the data needed for analysis. A survey provides data that can be used to compare the dissertation findings with past research. Being able to compare the findings with past data is very important in establishing approaches in bridging gaps. Through the survey, the researcher can compare their research with past data. Apart from suggesting or producing a solution to bridge gap, a survey helps formulate recommendations for further research (Ilieska, 2013).
3.3 Analysis of problem
Quantifiable literature proves complexity on focus on Quality of service by existing work in Service Level Agreements (;; ; ; ; ; ;) as many refs as possible to justify quantifiability, at least 4-6 refs from lit review. This is a significant fact that focus on crucial security parameters in SLA, such as confidentiality and integrity is still immature in the research area. Meeting as many as possible security parameters in SLA will earn web services and SLA alike trust from consumers (Stankov et al, 2012). Meeting security requirements is the key to success in any business (reference). Zhou et al (2013) also addressed security issues as an important factor shadowing the SOA platform and development of applications associated with it. JIANG et al (2016) echoed web services dominance is also associated with multiple security issues adversely affecting reliability, confidentiality and data non-repudiation. This assumes more focus is directed in satisfying consumers’ measurable quality expectations such as speed, reliability, Accuracy, capacity, Scalability and costs. By doing so, a result of serious consequences such as financial loss to the web service providers may occur. In justification to this ideology, the provider has a responsibility to ensure security failure which should be compensated for. For instance, work in the following studies, Kuan Hon et al., 2012.
Considering work by Zhou et al, 2013 and JIANG et al, this is evident that security parameters are an area still requiring to be fully addressed in the research community. If the research community put more focus in inclusion of security parameters such as confidentiality and integrity, this will ensure providers, consumers and any other third parties are fully informed on the gravity of security failures. As a strategic approach, this study will suggest a SLA QoS solution that will incorporate crucial security elements such confidentiality
3.4 Problem Requirements
This identifies requirements needed to make a proposal for a solution that will extend SLA to include security parameters such as confidentiality and integrity. This is done in anticipation for future requirements which may require modification. Therefore, features modifiability in the unmeasurable requirements section
3.4.1 Requirements definitions for SLA
SLA Measurable requirements (Qualities)
Theoretically, SLA quality specifications can be addressed and specified if both stake holders have an understanding on measuring and verification of the outcome (Dobson, 2005; Bianco et al, 2008). The following requirement specifications are based on measurable and unmeasurable qualities;
Accuracy: This is measurable by errors in service delivery. Periodically, errors can be collected to ascertain average occurrence.
Capacity: This is a measurement of data handling capacity. In web services, it measures reasonable number of requests that can be made over a stipulated time.
Cost: This refers to costs such as; (i) service requests costs per service, (ii) data size (ii) peak hours requests
Latency: This is defined by the time taken between a service request and execution.
Trial/ Provisioning time: This is the time between consumer registration and initial service exploitation.
Reliability: This concerns delivery mechanism and guarantee. This also includes that criteria in which message delivery takes place. For instance, by priority order.
Scalability: This concerns service elasticity. To elaborate this fact, it regards to the ability to maintain speed while coping with increasing demands from consumers with time. This is inclusive of other factors such as reliability and possibility to remove or add instances.
Reversibility: In web-based services such as cloud, retrieval and deletion of data by the provider and consumer can be done as agreed in the contract.
SLA unmeasurable requirements (Qualities)
Interoperability: This concerns communication facilitation between different entities.Given such, information is communicated via semantics operating as agreed (Brownsword, 2004).
Modifiability: This concerns the ability to adapt to relevant changes as required to accommodate factors such as change in requirements. Possible changes relevant to modifiability are such as;
 Provider and Consumers Agree on;
Provider and Consumers Agree on;




 CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
Chapter overview
A critical analysis of the methodology will take place in this chapter. Results from the survey, study form existing work and the proposal are all scrutinized. This will be used to identify advantages and disadvantages that may be associated with the new solution.
4.1 Evaluation
To identify significance of this project, work has been centered on an in-depth study on Service Level Agreements (SLA) security concerns. With consideration to wider deployment of web services and the need to elevate security principles, it has been found in this study that secure Service Level Agreements are crucial. Research findings revealed a concentrated focus on Quality of Service aspects features such as speed and availability while security has been overlooked. Relevancy and suitability of the proposition made in the study is based on a combination of survey results and literature review on web services and SLA respectively. Focus on this project has been centered on addressing the importance of security aspects to aid QoS. Significance of addressing security issues and proposing a solution for securing SLA, lies on an effort to bridge the security gaps resulted by lack of focus on security concerns in SLA (Cottrell, 2003).
4.1.2 Advantages
CHAPTER 4: CRITICAL ANALYSIS OF PROPOSED SOLUTION
Chapter overview
A critical analysis of the methodology will take place in this chapter. Results from the survey, study form existing work and the proposal are all scrutinized. This will be used to identify advantages and disadvantages that may be associated with the new solution.
4.1 Evaluation
To identify significance of this project, work has been centered on an in-depth study on Service Level Agreements (SLA) security concerns. With consideration to wider deployment of web services and the need to elevate security principles, it has been found in this study that secure Service Level Agreements are crucial. Research findings revealed a concentrated focus on Quality of Service aspects features such as speed and availability while security has been overlooked. Relevancy and suitability of the proposition made in the study is based on a combination of survey results and literature review on web services and SLA respectively. Focus on this project has been centered on addressing the importance of security aspects to aid QoS. Significance of addressing security issues and proposing a solution for securing SLA, lies on an effort to bridge the security gaps resulted by lack of focus on security concerns in SLA (Cottrell, 2003).
4.1.2 Advantages
 December Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date:...............02/12/12
December Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date:...............02/12/12
 ........................
Student signature: ..........................
January Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date: 20/01/2017
........................
Student signature: ..........................
January Report
6000PROJ / 6001PROJ Final Year Project
Monthly Supervision Meeting Record
Student: Isaac Zennah Date: 20/01/2017
 ........................
Student signature: ..........................
February Report
6000PROJ Final Year Project
Monthly Supervision Meeting Record
Student: ...................................Isaac Zennah Date: February 2017
........................
Student signature: ..........................
February Report
6000PROJ Final Year Project
Monthly Supervision Meeting Record
Student: ...................................Isaac Zennah Date: February 2017
 ........................
Student signature: ..........................
Appendix 4: Report Structure Documentation
........................
Student signature: ..........................
Appendix 4: Report Structure Documentation




