Review, Simulation and Comparison of WSN Routing Protocols
Info: 10913 words (44 pages) Dissertation
Published: 22nd Feb 2025
Tagged: Information Technology
REVIEW, SIMULATION AND COMPARISON OF WSN ROUTING PROTOCOLS
Abstract
A wireless sensor network (WSN) is a wireless network that consists of numerous sensor based devices which are deployed over a region and are used to gather data related to environmental features. The wide range of nodes communicate together using radio signals that can be transmitted directly between the sender and the destination nodes or making use of many nodes forming a route between them. There is no dedicated medium for the signal traversal and as various paths can exist to route the traffic, routing protocols are needed to provide a set of rules based on which the data transfer can happen. WSNs find much use in the areas where human intervention is limited and least access is needed over a duration. The applications where continuous monitoring of environmental data is needed make use of sensor networks. Because of the growing demand of the WSNs, routing protocols are being studied to address the various limitations and provide a standardized solution based on the major categories of network. In this thesis, a comprehensive overview of WSN is presented touching the existence, applications, challenges with the design. The concerns associated with its routing protocols and the solutions which could be applied have been studied. The testing of the protocols has been done by building network models in simulator and obtaining various parameter values. A comparative study has been demonstrated using simulation in MATLAB.
Click to expand Table of Contents
Table of Contents
Chapter 1: INTRODUCTION
1.1 Project Aim
1.2 Project Objective
1.3 Thesis Structure
Chapter 2: Background and Motivation
2.1 The Wireless Sensor Network (WSN)
2.2 Sensor node
2.3 WSN Issues
2.4 WSN Routing Protocol
2.4.1 Design issues of WSN Routing Protocols
2.4.2 WSN Routing Protocol Classification
2.5 Summary
Chapter 3: WSN Routing Protocols
3.1 LEACH protocol (Low Energy Adaptive Clustering Hierarchy)
3.1.1 Advantages and Disadvantages
3.2 PEGASIS protocol (Power-Efficient Gathering in Sensor Information Systems)
3.2.1 Advantages and Disadvantages
3.3 DEEC (Distributed Energy Efficient Clustering)
3.3.1 Advantages and Disadvantages
3.4 Summary:
Chapter 4: WSN Simulation
4.1 Why use simulation in WSNs
4.2 Simulation model
4.3 Types of Simulations Surrounding Wireless Sensor Networks
4.4 Challenges in Selecting the Simulator framework
4.5 Why MATLAB?
4.5.1 System Requirements for MATLAB R2017a
4.5.2 Key Features
4.6 Summary
Chapter 5: Comparative Metrics in WSN
5.1 Metrics that can be measured in simulation
5.2 Metrics used in our study
Chapter 6: Implementation Analysis
6.1 Implementation proposal
6.2 Simulation Results
Chapter 7: Conclusion
Bibliography
Appendix: Pre-requisite
List of Figures
Figure 1. Basic WSN structure……………………………………12
Figure 2. WSN routing mechanism…………………………………17
Figure 3. Phases in LEACH……………………………………..19
Figure 4. LEACH routing………………………………………19
Figure 5. LEACH scenarios……………………………………..21
Figure 6. PEGASIS routing……………………………………..24
Figure 7. Behavior of node energy consumption over time……………………26
Figure 8. Flowchart of DEEC routing………………………………..27
Figure 9. Dead nodes in LEACH protocol……………………………..39
Figure 10. LEACH node distribution………………………………..40
Figure 11. LEACH network model variables……………………………41
Figure 12. PEGASIS node distribution……………………………….42
Figure 13. PEGASIS network model variables…………………………..43
Figure 14 a. DEEC network model variables……………………………44
Figure 14 b. DEEC network model variables……………………………45
Figure 15. Protocol Comparison…………………………………..46
Glossary
| WSN | Wireless Sensor Network |
| IoT | Internet of Things |
| LEACH | Low Energy Adaptive Clustering Hierarchy |
| PEGASIS | Power-Efficient Gathering in Sensor Information Systems |
| DEEC | Distributed Energy Efficient Clustering |
| BS | Base Station |
| CH | Cluster Head |
| ADC | Analog to Digital Converter |
| QoS | Quality of Service |
| TDMA | Time Division Multiple Access |
| RE | Residual Energy |
| CSMA MAC | Carrier Sense Multiple Access, Medium Access Control |
| TCP/IP | Transmission Control Protocol, Internet Protocol |
| BER | Bit Error Rate |
Chapter 1: INTRODUCTION
1.1 Project Aim
A review, simulation and comparison of WSN Routing Protocols. Simulate the WSN routing protocols using a Simulator and compare them listing their good and weak points. Generate a selection table of routing protocols that show each protocols properties and function.
1.2 Project Objective
The latest improvement in the IoT, Internet of Things is the usage in the fields of health which is dependent on the environmental measurements and this makes the WSNs a hot topic for research. The network details are not yet clearly standardized which can be just used to set up a WSN. Thus, there is vast scope of its study and different scenarios needs to be well tested and verified which requires a testbed. WSNs comprise of many sensor nodes that are costly and again setting up a whole network with these nodes just for study involves much of cost and consumes lot of time. So, simulation in WSNs is important to evaluate any new ideas or changes made to the existing systems. The parameters can be finetuned in simulators to obtain results based on varying scenarios.
The project aims to review the WSN Routing Protocols: LEACH, PEGASIS, DEEC and simulate them using MATLAB. The tool will be used to demonstrate Routing Protocols in operation in a WSN with varying number of nodes.
1.3 Thesis Structure
Chapter two of this thesis will explore the background topics which include the discussion of Wireless Sensor Network (WSN), its requirements, various WSN routing protocol classification, and challenges of WSN routing.
Chapter three will discuss the protocols: LEACH, PEGASIS and DEEC in detail elaborating the working of these.
Chapter four outlines the need of Simulation in WSN and various challenges associated with it.
In Chapter five, the various metrics associated with routing protocols have been discussed, emphasizing the metrics under our comparison.
Finally, Chapter six will discuss the MATLAB implementation of the protocols and how their simulation results have been used to make the comparison.
Chapter 2: Background and Motivation
In this chapter, the background theory of Wireless Sensor Network (WSN) will be discussed. It is intended to give a general background of the basic concepts of its requirements, various WSN routing protocol classification, and the challenges of WSN routing.
2.1 The Wireless Sensor Network (WSN)
The improvement in the field of sensor devices has led to have possibility of numerous size ranged devices with capability to sense low power and perform programmable computing, these devices can measure various parameters in the environment and are suitable for wireless communication. The low cost also favors establishing a network of sensor devices which may contain various nodes to improve the reliability and accuracy of data and the area coverage [1].
Many sensor nodes are spread across the region to form a wireless sensor network. The data is sensed by individual nodes and is gathered at the sink node where the redundant data can be aggregated into one and compressed for further usage. This aggregated data needs to be forwarded to the base station [2].
The number of messages that are exchanged between the sensor nodes and the base station gets reduced. The performance of data gathering at the sink depends on the rate at which the data is sensed and then transmitted to the sink node. The ability of the sink node to carry out the process of data aggregation effects the efficiency of the routing protocol when the environmental interference is considered.
Wireless sensor network comprises of nodes which relate to every other node present in the network. Each sensor node in the network consists of three subsystems:
- The sensor subsystem that senses the environment,
- The processing subsystem that computes locally on the data sensed by nodes
- The communication subsystem that shares the gathered data with other nodes in network.
A sensor node collects the data based on their sensing capability and communicates with the neighboring nodes and the base station. A base station connects the sensor network with other networks.
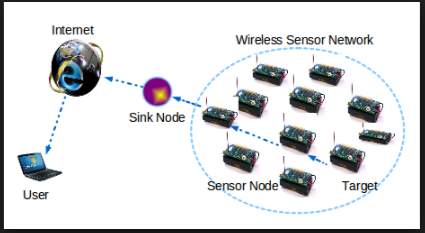
Figure 1. Basic WSN structure
2.2 Sensor node
To improve the lifetime of the wireless sensor network the protocols designed for data gathering must be energy aware [4]. The sensing unit of the Sensor node consists of the sensor and the analog-to-digital converter. The sensor collects the data based on sensing of analog signals which are then converted by ADC into digital signals and forwarded into the processing unit. The processing unit unites the nodes to aggregate together the data sensed over a region. The nodes are connected to the network by the transceiver unit. [4]
Requirements of a WSN can be listed as:
- use of many sensors
- attachment of stationary sensors
- reduced consumption of energy
- capability to organize the network
- signals can be processed together
- ability to make queries in the network
2.3 WSN Issues
The issues that may exist with WSN are the network deployment keeping it simple, connected, fully covered, scalable, tolerant to faults, secure and make efficient usage of energy.
The nodes need to access the common medium and there can always be contention due to the packet collision. The multiple hops in the transmission of data between the nodes and to the base station also leads to interference. The energy consumed by the nodes in wireless network and the quality of service is dependent on the time taken for transmission of data.
The energy spent in computation is less as compared to that spent for communication. To improve the energy consumption in the network and enhance the lifetime it becomes important to be able to communicate only the useful data to the sink node.
Network energy determines the time length for which the region can be monitored and this determines the life of the network. This energy can be utilized efficiently by grouping the sensors together into clusters with each cluster having a master node or cluster head and the rest being cluster members. It is the master node in the cluster that is responsible to perform data aggregation. Increasing the population of sensor nodes to monitor a region will improve the overall network energy but does increase the cost of deployment. The cost of battery replacement also adds up so its demanding to make use of sensors which have higher battery [4].
The growing interest in WSN and the emergence of new architectural technique is the reason for studying of routing protocols. Routing protocols for wired networks and ad-hoc networks are not applicable to wireless sensor networks. A WSN system incorporates a gateway that provides wireless connectivity back to the wired world and distributed nodes. [4]
2.4 WSN Routing Protocol
The routing protocol is a defined set of rules to route data from source to destination moving from node to node across different paths available. In Wireless Sensor Networks (WSNs), it is the way data is collected and routed from the network field (source) to the base station (destination). Improved reliability and low power consumption is needed for designing the routing protocols for sensor networks [4].
2.4.1 Design issues of WSN Routing Protocols
- Fault Tolerance
- Scalability
- Production Costs
- Operating Environment
- Power Consumption
- Data Delivery Models
- Data Aggregation/Fusion
- Quality of Service (QoS)
- Data Latency and Overhead
- Node Deployment
Fault Tolerance - It is the ability with which the functions of the sensor network can be sustained in case of any failure of the nodes. The failure may be due to the lack of power, any physical damage and interference in the environment.
Scalability - There should be variable number of sensor nodes allowed to be deployed in the area to support response to all events.
Production Costs - The cost of each sensor node needs to be kept low to maintain the total cost of the network as the individual node cost effects the overall cost.
Operating Environment - Sensor network deployment should be independent of the environmental constraints.
Power Consumption - The power needed for signal transmission in wireless network depends on the distance between the nodes.
Data Delivery Models - It depends on the application of sensor network which data model can be used for its delivery across the region. There can be periodic data transmission from the sending node, or the data may begin to traverse when such event occurs that triggers the need to transmit data.
Data Aggregation/Fusion - Aggregation of data from different sources can be made.
Quality of Service (QoS) - There exist certain quality parameters like the lifetime of sensor nodes and the network, how reliable the data transmission is, how efficient the energy consumption is, how aware the location gathering information is.
Node Deployment - The deployment of nodes depends on the application and effects the overall protocol performance [5].
2.4.2 WSN Routing Protocol Classification
The routing protocol for WSN can be classified based on how the data is forwarded between the nodes. The data-centric routing protocol allows the sink node to send request for data from the sensor nodes that are placed in its region. Attributes are used to specify the data being sent from the nodes towards the sink node. There is always redundancy in the data collected at the sink.
The location-aware routing protocol assumes that the nodes know their geographical location.
Location information can be used to improve the performance of routing and to provide new types of services.
The QoS based routing protocols considers quality based parameters like data delivery ratio, network latency and energy consumption. Good quality of service is based on high data delivery ratio, lower latency and low energy.
The proactive routing protocols look for paths prior to any demand for traffic routing. Even if there is no traffic flowing at certain times, Paths can be looked for and recorded.
The reactive routing protocols trigger the routing as and when data is ready to be sent and is accordingly forwarded to the nodes as per the path set based on query initiation.
The source-initiated protocols establish the routing path when a source node makes a request for it. The data availability is advertised by the source node and then the data delivery is initiated.
The destination initiated protocols setup the routing path once the destination is ready for reception of any data.
2.5 Summary
This section has discussed the use of WSN and its issues. It also touched how the various routing protocols are classified and the issues in their design.
Chapter 3: WSN Routing Protocols
The routing protocols selected for comparison have been elaborated in this chapter. The protocols are different based on the way they route the data gathered from an area with the help of sensor nodes to the cluster heads and forward it to the base station. The advantages and limitations of each have also been included.
The main mechanism of routing can be depicted as in the figure below.
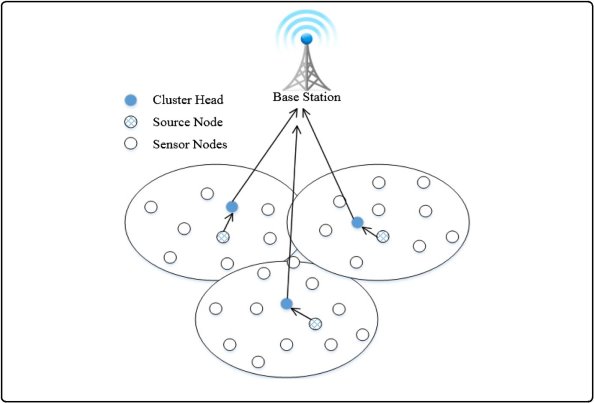
Figure 2. WSN routing mechanism
3.1 LEACH protocol (Low Energy Adaptive Clustering Hierarchy)
It is basically a cluster based protocol. The routing operation is divided into rounds, with each round having a new set of nodes selected for operating as cluster-heads (CH). For p number of rounds, the repetition of node nominated as cluster head is not possible. Each round provides every single node a 1/p probability of becoming a cluster head. As a round comes near to its end, every non-head node selects nearest cluster head to transmit through it. The cluster head compresses the data once aggregated which is then forwarded to the base station, this extends the longevity of major nodes. This protocol distributes the consumed energy uniformly amongst all nodes. The assumption that all nodes exist in the wireless transmission range of the main network base station makes its deployment different than the rest of protocols. Almost 5% of the nodes present in the network are the cluster heads. In case of larger sensor networks, use of Time Division Multiple Access (TDMA) adds to the delays. [6]
The routing protocol works in steps which are categorized under a setup phase and a steady phase. The first phase is responsible to create the cluster in the network. The nodes with higher energy tend becoming the cluster head amongst all other nodes. Formation of cluster head is based on TDMA which prevents any congestion in the data traffic. The process of cluster head selection is in steps: Every node keeps generating a number between 0 and 1 on a random basis which is compared against the threshold value P(n). The value being less than the threshold value, makes the node eligible to become the cluster head. Once the node has been selected as cluster head its value for P (n) becomes 0 and it cannot be again selected to become head of the cluster. The non-zero value of P(n) makes the node to be considered as a non-head node. The information about the head selection is sent to all other nodes. As the nodes get informed of the head node, they begin transmitting information to this cluster head. The head is the point of deciding what data should be selected to keep and forwarded further to the base station.
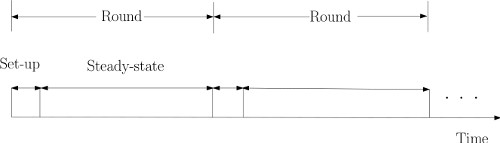
Figure 3. Phases in LEACH
The next step called the steady phase is where the cluster nodes sense and transmit the data collected to the head node. This cluster head gathers all the data sent by the nodes, performs aggregation followed by compression and sends it back to the sink node or the cluster head. When the nodes are not transmitting they can sleep. Cluster heads are rotated randomly. It transmits only new data to the sink. The LEACH protocol is distributed and needs no global knowledge. The data aggregation which occurs in the cluster head saves energy of the network.
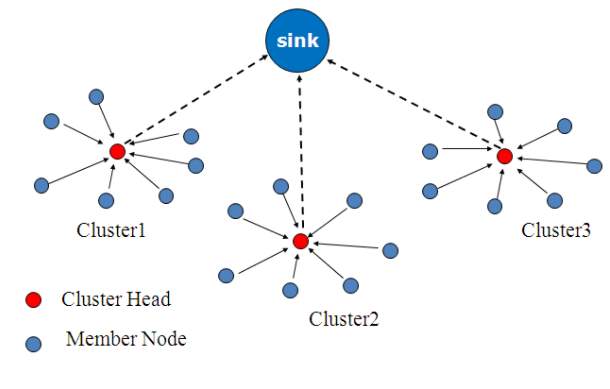
Figure 4. LEACH routing
As there is an increase in the transmission interval there is reduction in the number of transmissions. This increase in the transmit period is responsible for the delay in reception of any time critical data But, because of the increased period, critical real-time data may reach the user with elongated time. To reduce the delay in the reception of critical data, this interval needs to be reduced but it may lead to increase in the number of data transmissions and the amount of energy being consumed which reduces the network lifetime. Inside the cluster structure the cluster head determines and sends out a TDMA schedule which contains the sequence in which the nodes can transmit the data. A slot in time is allotted to every node in the cluster which can be used to send data to the cluster head. Once all the nodes in the cluster are done with their transmission, the TDMA allocation is again followed. LEACH finds its use in the applications where environmental attributes like temperature, pressure or moisture change patterns all to be measured within a region. The data is collected on a periodic basis and is evaluated centrally thus making it appropriate for usage where network needs to be monitored over a period. [6]
Properties of LEACH can be summarized as to include:
- Cluster based
- Cluster head selection based on sensor having highest energy
- Cluster membership adaptive
- Data aggregation at cluster head
- Cluster head communicate directly with sink or user
- Communication done with cluster head via TDMA
- Threshold value
As can be seen in the figure below, the second scenario is better because the cluster-heads are spaced out and the network is more properly sectioned.
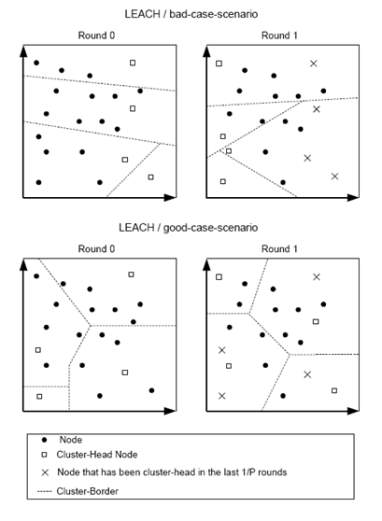
Figure 5. LEACH scenarios
3.1.1 Advantages and Disadvantages
The various advantages of LEACH protocol are:
- The data aggregation at the Cluster Head leads to reduction in the network traffic.
- Single hop based routing from nodes to cluster head results in saving energy.
- There is an improvement in the lifetime of the sensor network.
- Information about the node location is not required to create the cluster.
- No information from the base station is needed to control the network.
- No global knowledge of the network is needed, thus making LEACH a distributed protocol. [7]
Besides the advantages of LEACH, it also has some Demerits which are as follows:
- The number of cluster heads in the sensor network is not fixed in LEACH.
- The data collected by the cluster nodes may never be able to reach the base station in case of failure of Cluster head.
- The cluster size is variable and the distribution of nodes is also varied. As the node spread in the network varies in range, there is an increase in energy consumption and has great impact on the performance of the entire network. [7]
3.2 PEGASIS protocol (Power-Efficient Gathering in Sensor Information Systems)
This routing protocol is a near optimal chain-based protocol and extends the lifetime of network. In PEGASIS, every node makes a way to adjust the power of signal to be heard only by the close neighbor so that it can communicate with it. This close node is found by measuring the signal strength. Once the chain is formed, the protocol elects a leader based on residual energy and it is this node which collects all the data sensed from nodes and transmits it to the base station. This reduces the energy spent by every node on an average. There is no cluster formation in PEGASIS as happens in LEACH, it rather makes use of a single node in a chain to transmit to the Base station instead of multiple nodes. This approach reduces the overhead and lowers the bandwidth requirements from the Base Station. [8]
PEGASIS starts with the farthest node and following a greedy algorithm forms a chain structure while moving towards other sensor nodes. The basic idea here is that the nodes communicate with the neighbors and once data is gathered, it is combined at a single point and is then sent to the sink node. The selection of the network leader takes turns and this maintains energy distribution among all the nodes. As the distribution of energy is even, it improves the efficiency of the network and enhances the longevity of network. [8].
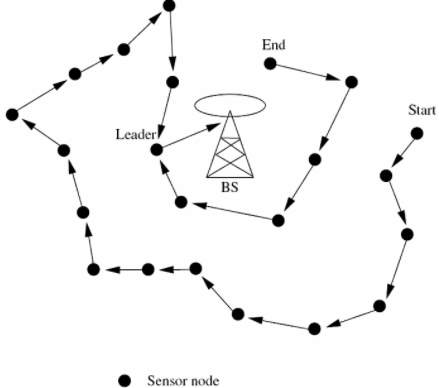
Figure 6. PEGASIS routing
The two steps on which the PEGASIS routing protocol is based are: Chain construction and Gathering data.
Chain construction is based on greedy algorithm and needs to be completed prior to the start of the round. The chain construction begins from the nodes that are far away from the base station as it is assumed that such nodes have more close neighbors and thus they can start communicating with each other over the chain.
Once the chain is formed, every node communicates with the nearby nodes, collects data and forwards to the next neighbors. Any node i which is in some random position j on the chain takes turn transmitting to the BS. In every round of communication, the node appointed as leader is placed randomly and thus it supports the network against any failures. [8]
The data fusion takes over all the nodes and not on the end nodes of the chain. The motive behind fusing data together is to combine the data into a fixed length packet and transmit it to the next node in the chain. In every node, energy dissipated to make communication with neighbors.
3.2.1 Advantages and Disadvantages
Advantages of PEGASIS over LEACH:
- The distance for transmission of data between the nodes is less in PEGASIS.
- The number of messages gathered at the head node is less when compared to LEACH.
- If the network range is kept same, the PEGASIS routing protocol shows double the improvement as compared to LEACH.
- The energy dissipated among all the sensor nodes is balanced due to the selection of each of the nodes a head.
Disadvantages of PEGASIS:
- The distance between the head node and the base station is a consideration at the time of head node selection.
- Energy level is not a concern while making selection of the head node.
- Single head node may become a bottleneck of the network causing delay.
3.3 DEEC (Distributed Energy Efficient Clustering)
This routing protocol follows a distributed scheme to define clusters in WSN which are heterogenous. To define the cluster heads, both the initial and residual energy levels are used. A probability is determined for each node depending on the ratio of residual energy of each node and the average energy of the network. Increased initial and residual energy makes the chances of becoming cluster-heads more than the nodes which have low energy. There are two types of heterogeneous networks i.e. two-level heterogeneous network and multi-level heterogeneous network model based on the different levels of energy of nodes.
DEEC protocol elects the Cluster head based on the residual energy of every node.
Figure 7. Behavior of node energy consumption over time
When compared to LEACH, the setup phase is different but steady phase remains the same. The node energies can be determined a priori, and thus the Cluster head selection process is based here on the use of residual energy of the node. The cluster head after selection advertises to all the network nodes about it being elected based on CSMA to avoid any traffic collision. In this protocol, the broadcasted packets contain additional information like the cluster head id, cluster head residual energy as parameters inside the packet. This information can be used again and again in the next rounds for electing the head.Once the selection of cluster head is made, it checks the residual energy again to see for how long it can remain as head and then move to the steady state phase. This involves sending all the gathered data to the base station. Once the round completes with the two phases, again the residual energy is broadcasted for next cluster head selection until the last node dies. This improves the battery lifetime, thus optimizing the network efficiency.
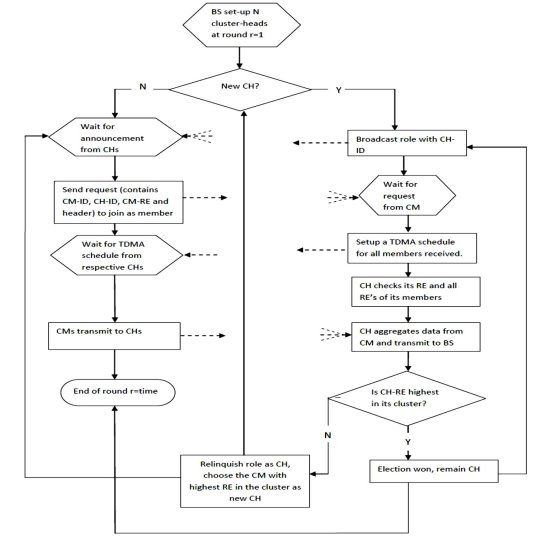
Figure 8. Flowchart of DEEC routing
3.3.1 Advantages and Disadvantages
Advantages of DEEC include:
- DEEC improves the performance of the multi-level Heterogeneous wireless network.
- The Cluster head is selected based on the residual energy and every round is independent of the others.
- DEEC assumes each node a chance of election if its RE is higher than its neighbors.
- DEEC guarantees that every CH has enough energy to play its role, until at least the end of the network life time.
Limitations of DEEC:
- The nodes whose residual energy is low always remain at low priority and may never become the head and may even die more rapidly than the others.
3.4 Summary
This section has discussed thoroughly the various implementation challenges to implement these routing protocols, while describing their working in detail.
Chapter 4: WSN Simulation
Simulation is the imitation of some real thing or a process. Network simulation has been used for study in various areas like academic research, industrial development, analyzing, designing, simulating and verifying the performance of different network protocols. Simulation supports debugging, reproduction, exploration of parameters without depending on the existing hardware or software. It provides a better view of the behavior and performance of the networks and its protocols [14].
4.1 Why use simulation in WSNs
To implement a topology in WSN and then apply testing over it for study is very costly. To evaluate various networking algorithms, routing protocols, networking schemes and any new ideas, simulation is the best option and it supports variable sized topology and structure. Simulators support various parameters that can be finetuned to test different.
The WSN simulators perform and produce results depending on how correct the simulation model is and how suitable that simulation tool is to implement the network model. The choice of the simulator is always a tradeoff between the requirements of precision in the results, the need of having detailed results and the improved performance and how scalable the network model can be.
The WSNs simulator must enable user to model the network topology to specify the nodes and the links between those nodes, model the application flow(traffic) between the nodes, Provides network performance metrics as output and results in Visualization and animation of packet flow.
4.2 Simulation model
The network simulation is modeled into following entities:
Nodes
Each node is a physical device monitoring a set of physical variables. Nodes communicate with each other via a common radio channel. Depending on the application and deployment scenario, a WSN can contain from a few to several thousands of nodes.
Environment
The main difference between classical and WSN models is the additional “environment” component. This component models the generation and propagation of events that are sensed by the nodes, and trigger sensor actions, i.e. communication among nodes in the network.
Radio channel
It characterizes the propagation of radio signals among the nodes in the network. Very detailed models use a “terrain” component, connected to the environment and radio channel components. The terrain component is taken into consideration to compute the propagation as part of the radio channel, and influences the physical magnitude. [15]
Sink nodes
These are special nodes that, if present, receive data from the net, and process it. They may interrogate sensors about an event of interest. The use of sinks depends on the application and the tests performed by the simulator.
Agents
A generator of events of interest for the nodes. The agent may cause a variation in a physical magnitude, which propagates through the environment and stimulates the sensor. This component is useful when its behavior can be implemented independently from the environment, e.g., a mobile vehicle. Otherwise, the environment itself can generate events. [16]
4.3 Types of Simulations Surrounding Wireless Sensor Networks
Wireless Sensor Network Simulators use Trace-Driven as well as Discrete Event Simulation.
Discrete Event Simulation
Discrete Event Simulation is easy to use over different aspects of sensor nodes in Wireless Sensor Network. The global variables help to provide the values for the various parameters and this allows the scheduler to make the predictions well in advance. Such simulation facilitates the dynamic memory management that facilities the manipulation in various entities and supports the normal simulation along with debugging capability [18].
Trace-Driven Simulation
Trace-Driven Simulation finds its use majorly in the time crucial roles and real-time applications. It determines every information in detail which provides an in-depth detail of the simulation model to the users. This may sometime increase the complexity of simulation.
4.4 Challenges in Selecting the Simulator framework
The Wireless sensor network comprises of many different sensor nodes. These nodes have resource constraints like reduced battery, less bandwidth and lower computing. Different simulator software has been designed with different application requirement and parameters needed. The results from Simulation are true for a region or environmental scenario that has been considered for the study. In WSN, the simulations are effected by the model chosen in terms of its correctness and suitability to the application [19].
Th language platform developed to perform determines the Performance and the varying requirements like memory, storage size and processing capacity effects the scalability [20].
The configuration of a WSN typical trial requires to answer (at least) questions like:
- How many nodes are there in the test?
- Where is each node placed?
- Do nodes move? all of them? how?
- Which energy model is used?
- How many physical environments are there? how they generate events?
- Which physical magnitudes should measure each node?
- Which statistics must be measured in the experiment?
- Which are the parameters of the radio model? [21]
The vast number of variables involved in the definition of a WSN experiment requires the use of specific input scripting languages, with high-level semantics. Additionally, it is likely that large quantities of output data will also be generated through many replicas of the experiments. Therefore, a suitable output scripting language, that helps to obtain the results from the experiments quickly and precisely is desirable.
The key properties of good Simulator are
- Availability
- Scalability
- Performance
- Support for rich-semantics & scripting languages
- GUI, debugging and tracing support.
4.5 Why MATLAB?
MATLAB is the easiest and most productive software that can be used to analyze the data, create network models and develop algorithms. In MATLAB, the debugging is faster than other languages and thus improves the time of development and ability to meet the project completion timeline.
It is based on matrix computation and this makes it easy to compute mathematical models based on numbers and symbols. Its supports equations and algebraic expressions and performs fast computations making the code run faster.
The MATLAB language supports traditional programming language features like controls the flow, handles error and object-oriented programming paradigms. It improves the results with enhanced visualization through support for 2D and 3D plotting functions.
MATLAB is suitable for analysis of layer 1 and to some extent of layer 2, of TCP/IP protocol and it considers the parameters like energy consumption and packet delivery to sink. Detailed model can be created by adding path-loss factor to the delivery channel. The metrics to be considered for the comparison in this project can be easily modeled using MATLAB, parameters can be simulated and changed quite freely with its scripting language.
4.5.1 System Requirements for MATLAB R2017a
Operating system – Windows 10
Processors – Any Intel or AMD x86-64 processor
Disk Space – 2 GB for MATLAB only,4–6 GB for a typical installation
RAM – 2 GB
Graphics – No specific graphics card is required.
4.5.2 Key Features
- It is a high-level language and suitable in scientific and engineering computing
- It provides a desktop environment that supports continuous experimentation, new design, and problem-solving features
- It has graphical support for visualization of data and tools to create customized plots
- It has add-on toolboxes which make it suitable for applications in the field of engineering and scientific
- It has tools to build applications to provide customized user interfaces
4.6 Summary
This chapter has covered the need of simulation in WSN. The classification of various simulators and the requirements for any simulation setup and the choice of MATLAB has been discussed with details on its features.
Chapter 5: Comparative Metrics in WSN
This chapter will include the metrics that can be measured using simulation of WSN protocols. These measurements are used for evaluating the protocol and then can be used in different applications.
5.1 Metrics that can be measured in simulation
Network Delay
Average time taken between a packet initially sent by the source to reach the destination. Measuring this delay considers the queuing and the propagation delay of the packets. [23]
Network Throughput
Number of packets per second received at the destination.
Success Rate
The total number of packets received at the destinations verses the total number of packets sent from the source.
Latency
The average message latency is defined as the average amount of time between the start of disseminating a data and its arrival at a node interested in receiving the data. Hence, the latency measures time performance for the individual message. [24]
Energy Consumption
Sum of used energy of all the nodes in the network for communication, including transmitting, receiving, and idling.
Network Lifetime
Time until message loss rate is above a given threshold.
Packet Generation Rate
It is the number of packets that the sensor node transmits in one-time period which is usually one second. [25]
5.2 Metrics used in our study
The metrics that have been considered for comparison are:
- Stability Period is the period (or round) up to which all nodes are alive. This period lies between rounds 1 to the round at which the first node dies.
- Instability period is the period between the first dead node and last dead node. This period should be kept as small as possible.
- Energy dissipation
- Different values of heterogeneity
Chapter 6: Implementation Analysis
6.1 Implementation proposal
To compare the routing protocols LEACH, PEGASIS and DEEC, simulation of their network models in MATLAB is proposed where the metrics can be evaluated and compared under the study.
Network model
To implement a protocol, first a network topology needs to be set up and then the protocol defines how the nodes will communicate amongst themselves and how the flow of data needs to be routed.
The steps can be listed as following:
- Define x and y Coordinates of the Sink, which gathers all the data from the nodes in the network.
- Declare the Number of Nodes in the field
- Select an Optimal Election Probability of a node to become cluster head
- Construct the Energy Model that includes parameters:
- Initial Energy
- Energy of transmission
- Energy of reception
- Energy dissipation in free space
- Energy dissipation in multipath
- Maximum number of rounds
- Creation of the random Sensor Network which includes:
- Random Election of Normal Nodes
- Random Election of Advanced Nodes
- CH selection per round
- Operation for epoch marks the process after the CH selection starts and involves:
- Number of dead nodes
- Number of dead Advanced Nodes
- Number of dead Normal Nodes
- bit transmission between Base Station and Cluster Heads
- check for condition when the first node dies
- Calculate Energy dissipated in terms of ETA: Transmitted power, EDA: data aggregation, Energy dissipated by associated Cluster Head and Energy dissipated while receiving information from node.
6.2 Simulation Results
The graphs obtained from MATLAB have been listed below to show the simulation results:
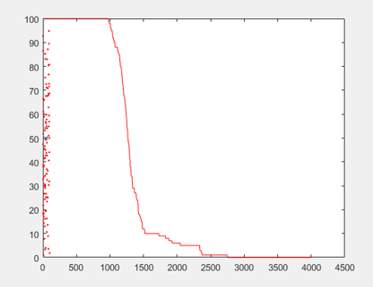
X axis = number of rounds
Y axis = network performance(lifetime)
rmax=4000
Figure 9. Dead nodes in LEACH protocol.
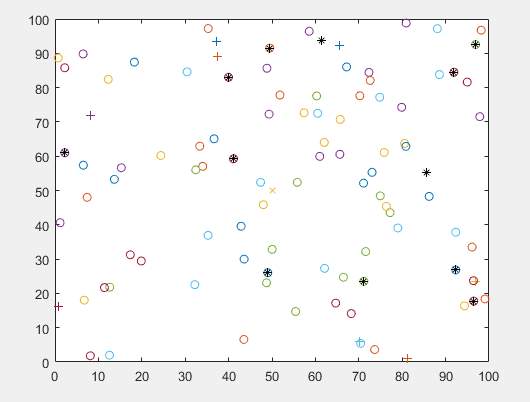
X axis= 100 meters
Y axis= 100 meters
Network dimensions
Figure 10. LEACH node distribution
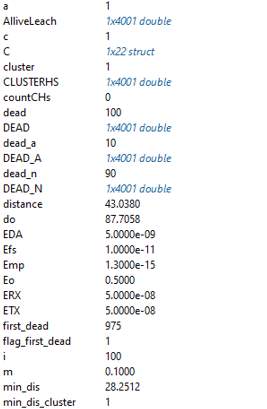
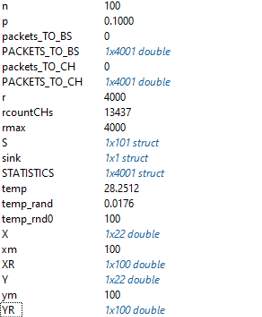
Figure 11. LEACH network model variables
X axis= 100 meters
Y axis= 100 meters
Network Dimensions
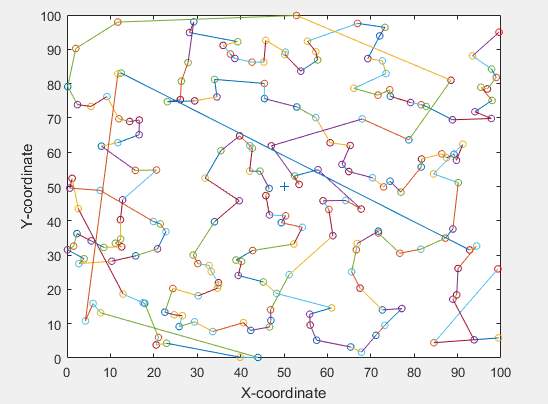
Figure 12. PEGASIS node distribution
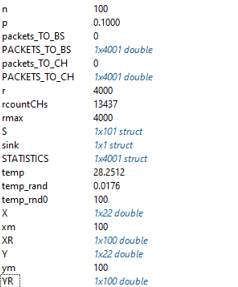
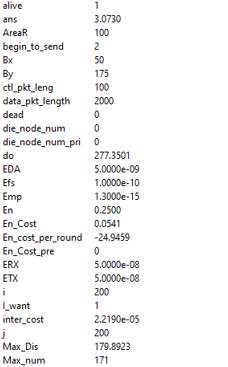
Figure 13. PEGASIS network model variables
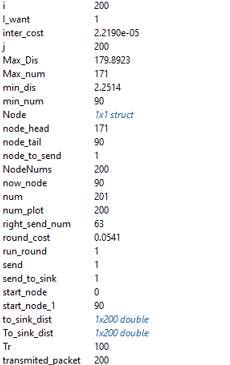
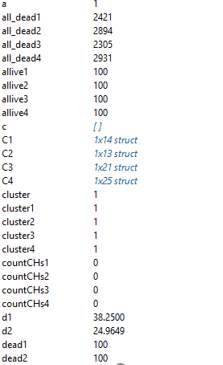
Figure 14 a. DEEC network model variables
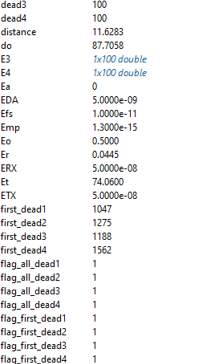
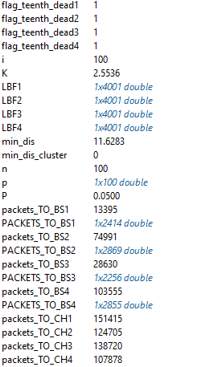
Figure 14 b. DEEC network model variables
| Routing Protocol | Routing Technique | Power Consumption | Application Type |
| LEACH | Hierarchical routing | High | Health monitoring |
| PEGASIS | Hierarchical routing | Maximum | Health monitoring |
| DEEC | Flat routing | Limited | Environment monitoring |
Figure 15. Protocol Comparison
The results show that in flat network topology, all nodes collaborate with each other to perform sensing task. The base-station positioning problem gets more challenging in case of multi hop routing since each sensor node not only transmits its own data but also forwards data from its neighbors when requested. The problem becomes simpler when sensors directly transmit to the base station. However, given the limited transmission range for the sensor nodes, this assumption cannot be applied to WSNs that cover large areas. The factor of scalability is considered important while designing a sensor network and single gateway architecture (flat network architecture) is not scalable when the number of sensors increases and is spread over a large area since usually sensor nodes cannot communicate to a very large distance. As the node density increases, there is more chance that gateway is overloaded. This overloading can cause inefficient communication and large latency. To cope with these problems cluster-based or hierarchical routing is utilized in wireless sensor networks to perform energy efficient routing.
The obtained results have shown that LEACH has some advantages over DEEC, for example, the data aggregation used in LEACH reduces the energy of the nodes that is otherwise used while making transmission of data packets and presence of any redundant data increases this energy with increase in the number of rounds. LEACH protocol proves to have higher data latency and enhanced node failure tolerance because of the TDMA routine followed by it. Network lifetime and throughput in case of LEACH are more than the DEEC and the percentage of losses is comparatively lower.
Results obtained with Simulation show that the performance of PEGASIS improves with an increasing size of network over LEACH. It eliminates the overhead involved in the formation of clusters as happens in LEACH. It reduces the length that the data transmitted from non-head nodes should travel, lowers the number of transmissions among the multiple nodes in same round by using single transmission with the base station.
Chapter 7: Conclusion
The ease of use and availability of smart and small sized sensor devices is making the wireless sensor network popular. There exist certain limitations on the usage and capacity of these devices which need to be considered while designing wireless network applications. Main concerns while developing routing protocols in WSN can be the energy usage which needs to be kept minimal, the number of such sensor devices to be used to enhance the size of the network. To support a wide range of sensor network, sensor nodes with different levels of energy can be employed. The routing protocols that support such variable energy fall under Hierarchical routing protocols [26]. Such nodes can coordinate using exchange of messages between them. The nodes near to the region being sensed form a cluster and collect the various parameters and send the sensed data to their cluster head which is responsible to aggregate the different values and reduce any redundancy among the collected data. It is this cluster head which forwards the same to the base station. The base station is connected to the various networks which use the sensed data in further measurements as needed by the applications. Based on the size of the network, the cluster formation has different effect. Cluster oriented approach proves to be beneficial in large and populated networks as compared to small spread networks [27].
The project on WSN and its routing protocols the understanding of network, the requirements, challenges and the limitations were gained. As the network comprises of numerous nodes spread globally, routing of data needs protocols specific for WSN. The requirements and the challenges here are different from those in wired network due to the difference in the medium of transmissions. The different routing protocols have different ways of processing and routing the data from the source to destination nodes. [30]
The energy level and other parameters make the sensor nodes different from each other. The routing protocol which supports similar nodes in the network fall under homogenous routing category and the ones which work over different types of sensor nodes are categorized as heterogenous routing protocols. The route from the transmitting node to the ultimate sink node may see multiple nodes in between [31]. The nodes that have different energy levels can be clustered together and each cluster then has own data aggregation and further forwarding to the next network [35].
After reading the various classifications of routing protocols, the three protocols LEACH, PEGASIS both belonging to hierarchical group and DEEC which is a flat routing protocol were taken for comparison. For same, these protocols needed to be set up to work over many nodes and this was to be simulated using a suitable platform which supports wireless implementations. Simulator is used for the study as setting a test bed for actual topology setup for sensor nodes and then studying the actual routing amongst the nodes will demand a high cost and effort which is not realistic for this project. There are many simulators that are available that support WSN functionality and they have different scripting languages that are used to implement topologies in them [36]. To select one of all the simulators available literature survey was carried out and based on the requirement of project and the time needed for implementation, the choice of MATLAB was made.
MATLAB was easy to use as a tool to set up the topology and implement the protocol. Different scripts were written for each protocol and the parameters were set to vary the network scenarios. The results were obtained with different measurements for metrics plotted as graphs and as network model variables. These have been used to frame the advantages and limitations of the protocols in similar scenario of node distribution [45].
There is a vast scope to research in the WSN and the routing protocols. As part of fulfillment of the goal of this project, where a comparison of three protocols has been made based on few metrics, there lies lot more to be explored. After getting the opportunity to read through a good amount of literature based on the studies and work already performed, the security edge to the routing protocols is an area in trend. [47]
To summarize my experience while working over this project ,I can sum up that Wireless sensor routing protocols is a research oriented topic which can be worked over for a longer duration to explore many of its layers but working on this time bound and realm aimed project has definitely provided much awareness of the actual working of sensor nodes, data collection and flow to the application network .This has led to keen interest in exploring the related fields in near future as part of self-awareness or getting a chance to work on actual related scenario based projects.
Bibliography
[1] A.Akkaya and M.Younis, “A Survey on Routing Protocols for Wireless Sensor Networks”, Science Direct, September 2003.
[2] GACS and L.Buttyan, “A Taxonomy of Routing Protocols for Wireless Sensor Networks”, Laboratory of Cryptography and System Security (CRYSYS), January 2007.
[3] Gopi Saminathan Arumugam, Thirumurugan Ponnuchamy, “EE-LEACH:development of energy-efficient LEACH Protocol for data gathering in WSN,” EURASIP, no. 76, 2015.
[4] Reshma I. Tandel, “Leach Protocol in Wireless Sensor Network : A Survey,” IJCSIT, vol.7, p. 4, 2016.
[5] Parth M Dave, Purvang D Dalal, “Simulation & Performance Evaluation of Routing Protocols in Wireless Sensor Network,” International Journal of Advanced Research in Computer and Communication Engineering, vol. 2, no. 3, 2013.
[6] Hemali M.Bhalodiya, Sunera Kargathara, Mohit Meghani, “A Survey on Secure Hierarchical LEACH Protocol over Wireless Sensor Network,” International Journal of Enginering Research and Development, vol. 10, no. 12, pp. 36-41, 2014.
[7] Jigisha Parmar, Ashishgoud Pirishothm, “Study of Wireless Sensor Networks Using Leach,Teen and Apteen Routing Protocols,” IJSR, pp. 1221-1224, 2013.
[8] S. Lindsey, and C. Raghavendra, “PEGASIS:Power- efficient gathering in sensor information systems,” IEEE Aerospace Conference Proceedings,2002, pp.1125-1130.
[9] Dheeraj,Ritu Verma, “Review Paper on Hierarchal Energy Efficient Protocols in wireless Sensor Netwroks,” IJARCSSE, vol. 4, no. 6, 2014.
[10] L.Almazaydeh, E. Abdelfattah,M.Al-Bzoor, Al-Rahayfeh, “Performance Evaluation of Routing Protocols in Wireless Sensor Networks”, International journal of computer science & information Technology, 2(2), 66-75, 2010.
[11] M.Chhimwal, “Comparison between Different Wireless Sensor Simulation Tool”, IOSR Journal of Electronics and Communication Engineering, 5(2), 54-60,2013.
[12] A.Mishra,S. Phulre, V.Richhariya, “Routing Protocols for Wireless Sensor Networks: A Survey”, International Journal of Computer Applications, 118(1), 12-15,2015.
[13] M. Abo-Zahhad, O.Amin,M. Farrag, A. Ali, “A Survey on Protocols, Platforms and Simulation Tools for Wireless Sensor Networks”, IJEIC, 5(6), 17-34,2014.
[14] D.Bhattacharyya,T. Kim,S. Pal, “A Comparative Study of Wireless Sensor Networks and Their Routing Protocols”, Sensors, 10(12), 10506-10523,2010.
[15] T.Sharma, H. Singh, A. Sharma, “A Comparative Review on Routing Protocols in Wireless Sensor Networks”, International Journal of Computer Applications, 123(14), 28-33,2015.
[16] Laiali Almazaydeh, Eman Abdelfattah, Manal Al- Bzoor, and Amer Al- Rahayfeh, “Performance Evaluation of Routing Protocols in Wireless Sensor Networks,” International Journal of Computer Science and Information Technology, Volume 2, Number 2, April 2010.
[17] Bhakti Parmar, Jayesh Munjani, “Analysis and Improvement of Routing Protocol LEACH using TEEN,APTEEN and Adaptive Threshold in WSN,” International Journal of Computer Applications, vol. 95, no. 22, 2014.
[18] K .Akkaya and M. Younis, “A Survey on Routing Protocols for Wireless Sensor Networks,” Elsevier Ad Hoc Network Journal, Vol. 3, pp. 325-349, 2005.
[19] Sohrabi K, Daniel Minoli and Taieb Znati. Wireless Sensor Networks: Technology,Protocols and Applications. Wiley and sons Publication. 2007.
[20] M. Younis, M. Youssef and K. Arisha, “Energy-Aware Routing in Cluster-Based Sensor Networks,” in the Proceedings of the 10th IEEE/ACM(MASCOTS2002), Fort Worth, TX, October 2002.
[21] Fengjun shang, Yang Lei,An energy based clustering routing algorithm for WSNs, scientific research,2012.
[22] Wenjing Guo; Wei Zhang; Gang Lu. Education Technology and Computer Science (ETCS), 2010.
[23] Alekha Kumar Mishra, Rukshan Ur Rahman, Rahul Bharadwaj, Rohit Sharma, “An enhancement of PEGASIS protocol with improved network lifetime for Wireless Sensor Networks”, Power Communication and Information Technology Conference (PCITC) 2015 IEEE, pp. 142-147, 2015.
[24] Alekha Kumar Mishra, Manoj Kumar Samantara, “A Dynamic Energy-Efficient Chain Formation Scheme for PEGASIS in Wireless Sensor Networks”, Computational Intelligence and Networks (CINE) 2016 2nd International Conference on, pp. 41-46, 2016, ISSN 2375-5822.
[25] Sachin Sarode, Apeksha Sakhare, “Review on LEACH: A protocol for energy efficient Wireless Sensor Network”, Electronics and Communication Systems (ICECS) 2015 2nd International Conference on, pp. 1021-1026, 2015.
[26] A. P. Chandrakasan, H. Balakrishnan, W. B. Heinzelman, “An application-specific protocol architecture for wireless microsensor networks”, IEEE Trans. Wireless Commun., vol. 1, no. 4, October 2002.
[27] S. Lindsey, C. Raghavendra, “PEGASIS: Power-Efficient Gathering in Sensor Information Systems”, IEEE Aerospace Conf., March 2002.
[28] S. Sahu, N. Kumar, V. Jain, “Survey on Recent Clustering Algorithms in Wireless Sensor Network”, International Journal of Scientific and Research Publications, vol. 3, 2013.
[29] Y. Chen, Y. Lin, N. Wang, “An intersection-based coverage algorithm for PEGASIS architect in wireless sensor networks”, Proceedings of the 2012 International Conference on Machine Learning and Cybernetics Xian, 15–17 July, 2012.
[30] F. Sen, Q. Bing, L. Tang, “An Improved Energy-Efficient PEGASIS-Based Protocol in Wireless Sensor Networks”, Eighth International Conference on Fuzzy Systems and Knowledge Discovery, 2011.
[31] Jingjing Yan, Mengchu Zhou, Zhijun Ding, “Recent Advances in Energy-Efficient Routing Protocols for Wireless Sensor Networks: A Review”, Access IEEE, vol. 4, pp. 5673-5686, 2016, ISSN 2169-3536.
[32] M. Taufiq Nuruzzaman, Huei-Wen Ferng, “A low energy consumption routing protocol for mobile sensor networks with a path-constrained mobile sink”, Communications (ICC) 2016 IEEE International Conference on, pp. 1-6, 2016, ISSN 1938-1883.
[33] A. Muthu Krishnan, P. Ganesh Kumar, “An Effective Clustering Approach with Data Aggregation Using Multiple Mobile Sinks for Heterogeneous WSN”, Wireless Personal Communications, 2015, ISSN 0929-6212.
[34] Jin Wang, Bin Li, Feng Xia, Chang-Seob Kim, Jeong-Uk Kim, “An Energy Efficient Distance-Aware Routing Algorithm with Multiple Mobile Sinks for Wireless Sensor Networks”, Sensors, vol. 14, pp. 15163, 2014, ISSN 1424-8220.
[35] K. Hong, S. Sengupta, R. Chandramouli, “Cross-Layer MAC Enabling Virtual Link for Multi-Hop Routing in Wireless Ad Hoc Networks”, Communications (ICC) 2010 IEEE International Conference on, pp. 1-5, 2010, ISSN 1938-1883.
[36] Aurelio La Corte, Alessandro Di Stefano, Marialisa Scata, Marco Leotta, “A Energy- Preserving Model for Wireless Sensors Networks Based on Heuristic Self-Organized Routing”, Systems Man and Cybernetics (SMC) 2013 IEEE International Conference on, pp. 3198-3202, 2013.
[37] Harith Yahya, Yaarob Al-Nidawi, Andrew H. Kemp, “A dynamic cluster head election protocol for mobile wireless sensor networks”, Wireless Communication Systems (ISWCS) 2015 International Symposium on, pp. 356-360, 2015, ISSN 2154-0225.
[38] Hector Kaschel, Johanna Ortega, “Energy efficiency in routing protocols applied to WSN”, Automatica (ICA-ACCA) IEEE International Conference on, pp. 1-8, 2016.
[39] F. Farazandeh, R. Abrishambaf, S. Uysal, T. Gomes, J. Cabral, “A Hybrid Energy- Efficient routing protocol for Wireless Sensor Networks”, Industrial Informatics (INDIN) 2013 11th IEEE International Conference on, pp. 18-23, 2013.
[40] Aurelio La Corte, Alessandro Di Stefano, Marialisa Scata, Marco Leotta, “A Energy- Preserving Model for Wireless Sensors Networks Based on Heuristic Self-Organized Routing”, Systems Man and Cybernetics (SMC) 2013 IEEE International Conference on, pp. 3198-3202, 2013.
[41] Yogita Bahuguna, Jyoti Rawat, “An Efficient Routing Protocol in Heterogeneous Wireless Sensor Network Considering Obstacle”, Advances in Computing and Communication Engineering (ICACCE) 2015 Second International Conference on, pp. 249-252, 2015.
[42] Noura Al-Hoqani, Shuang-Hua Yang, Daniel P. Fiadzeawu, Ross J. Mcquillan, “In- Network On-Demand Query-Based Sensing System for Wireless Sensor Networks”, Wireless Communications and Networking Conference (WCNC) 2017 IEEE, pp. 1-6, ISSN 1558-2612,2017.
[43] Abu Raihan M. Kamal, Md. Abdul Hamid, “Supervisory routing control for dynamic load balancing in low data rate wireless sensor networks”, Wireless Networks, vol. 23, pp. 1085, ISSN 1022-0038,2017.
[44] I. F. Akyildiz et al., “Wireless sensor networks: a survey”, Computer Networks, Vol. 38, pp. 393-422 March 2002.
[45] Y. Yu, R. Govindan, and D. Estrin, “Geographical and energy aware routing: A recursive data dissemination protocol for wireless sensor networks”, Technical Report UCLA/CSD-TR-01-0023, UCLA Computer Science Department, May 2001.
[46] S. Lindsey and C.S. Raghavendra, “PEGASIS: Power-efficient Gathering in Sensor Information System”, Proceedings IEEE Aerospace Conference, vol. 3, Big Sky, MT, pp. 1125-1130,2002.
[47] I. F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci, “Wireless sensor networks: a survey”, Computer Networks (Elsevier) Journal, Vol. 38, no. 4, Mar. 2002, pp. 393-422.
[48] Subramanian Ganesh, Ramachandran Amutha, “Efficient and secure routing protocol for wireless sensor networks through SNR based dynamic clustering mechanisms”, Communications and Networks Journal of, vol. 15, pp. 422-429, 2013, ISSN 1229-2370.
[49] N. Javaid, T.N. Qureshi, A.H. Khan, A. Iqbal, E. Akhtar, M. Ishfaq, “EDDEEC: Enhanced Developed Distributed Energy-efficient Clustering for Heterogeneous Wireless Sensor Networks”, Procedia Computer Science, vol. 19, pp. 914, 2013, ISSN 18770509.
[50] Shan Zhong, Guihua Wang, Xiaohui Leng, Xiaona Wang, Lian Xue, Yue Gu, “A Low Energy Consumption Clustering Routing Protocol Based on K-Means”, Journal of Software Engineering and Applications, vol. 05, pp. 1013, 2012, ISSN 1945-3116.
[51] Samayveer Singh, Satish Chand, Bijendra Kumar, “Energy Efficient Clustering Protocol Using Fuzzy Logic for Heterogeneous WSNs”, Wireless Personal Communications, 2015, ISSN 0929-6212.
[52] Mourad Hadjila, Hervé Guyennet, Mohammed Feham, “A Chain-Based Routing Protocol to Maximize the Lifetime of Wireless Sensor Networks”, Wireless Sensor Network, vol. 05, pp. 116, 2013, ISSN 1945-3078.
Appendix: Pre-requisites
- MATLAB– The software can be Downloaded and Installed using your Math Works account:
- https://www.mathworks.com/mwaccount
- https://uk.mathworks.com/products/matlab.html
- For development of scripts, MATLAB classes need to be known and their usage need to be understood for efficient coding.
- To implement the protocols into scripts, their working knowledge needs to be well versed with.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Technology"
Information Technology refers to the use or study of computers to receive, store, and send data. Information Technology is a term that is usually used in a business context, with members of the IT team providing effective solutions that contribute to the success of the business.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




