Three Step Authentication for ATM Machines
Info: 10004 words (40 pages) Dissertation
Published: 30th Nov 2021
Chapter 1: INTRODUCTION TO THE STUDY
1.1 Background to the Project
ATM known as Automated Teller Machine was invented by John Shepherd-Barron during the early 1960s. ATM is a cash dispensing machine at the requirement of cheque and pin number. Later on the machine was improvised to read magnetic strip cards (Verma, 2012). In Malaysia, ATM were introduced through MEPS in the year of 1996 (MEPS, 2014). ATM are undeniably important when it comes to money dispensing. Though there were some cases dealing with the vulnerabilities of ATM including hacking the software and breaking the ATM safe stealing money (FinanceTwitter, 2014). The ATM contains only two type of authentication that includes pin number and card validation. So a proper authentication and verification system was proposed by the developer to enhance validation and authentication to the current system. The developer’s proposed system contains fingerprint scanning, facial recognition, and user login as the authentication components
1.2 Problem Context
Nowadays in Malaysia the level of authentication given to ATM authentication remains same as with two factor authentication. This is very much insecure since the two factor authentication involves with pin number and the card. Someone with the capability of stealing the card and knowing the pin number makes the victim very vulnerable (Meggitt, 2016).
The problem is that this two factor authentication sometimes cannot validate all types of user. This in fact neglects certain users from using the ATM such as blind people and also the other problem is that if the card is stolen and the thief knows the pin number as well then there is more trouble(Popken, 2014). The other supporting problem is that when the user forgets the pin number then the user cannot use the ATM (Brooker, 2015).
These are the problem associated with two factor authentication. Sadly, no bank or financial institutes did manage to solve this issue that commonly occurs in our society. Most of the time these institutes does not want to implement new technology to the ATM because it might cost them to change or upgrade each and every ATM in this country (Lamagna, 2016).
1.3 Rationale
Therefore, to overcome this complexity or problem associated with two factor authentication can be handled through by implementing biometric validation using thumbprint verification and facial recognition (Spence, 2014). In this way the rightful owner of the account will be able to do money transaction regardless if even the owner is blind or the owner has forgotten their pin number. A lot of this minor issues that causes nuances to the users of the ATM can be avoided by implementing these sort of verifications that will ensure only the right owner of the account can use it with no issue (Muller, 2016).
1.4 Potential Benefits
1.4.1 Tangible Benefits
- When requesting new card and pin number after losing it and also when the user forgets the pin number, the system enables them to temporarily use the system until they obtain new card and password thus making the user not wasting time waiting for the new card.
- The amount lost to illegal ATM transactions from the bank is reduced and the bank is able to keep more money in their safe.
- Number of new customers will increase on saving their money in that particular bank, thus increasing profit and popularity for the bank.
1.4.2 Intangible Benefits
- Integration of the ATM is improved very much as the implementation of two biometric devices such as facial recognition and fingerprint scanning inside of ATM. As the validation of the system is increased the integrity if the system also very much increases.
- As the three factor authentication is implemented on the ATM, the result of the user search is very much precise when it can verify thumbprint, facial image and pin number. So the search concretes on determining the right and correct user while maintain credibility of the system.
- Reputation of the bank that implements this security implementation goes sky high as more and more people save their money on that particular bank. So in turn will increase the share of the bank in the market plus adding value to the bank.
- Customers will be satisfied on saving their money on the bank that has this security features being implemented in the ATM. Customers also will be relieved of the threats that might happen implicating loss in their savings. Thus customers recommend that particular bank to other customers as well.
1.5 Target Users
The targeted users are all types of users. This system is made to encompass all types of users so that anyone and everyone is able to use the ATM machine.
1.6 Scope and Objectives
1.6.1 Aims
The aim is to analyse, design, and implement a secure level of ATM machines by using three step authentication.
1.6.2 Objectives
- To investigate the problem associated with the current authentication used by ATM
- To propose and design a system to improve the authentication of the ATM by integrating both fingerprint and facial recognition
- To implement the proposed authentication system of the ATM
- To evaluate and test the proposed authentication system of the ATM
1.6.3 Deliverables
This three factor authentication benefits the user in these certain ways:
- Increases the data confidentiality of the ATM machine
- improve authentication system
- advance verification stages to access bank account through ATM machines
1.6.4 Nature of Challenges
The challenge that will be met upon creating this system mostly on reading and identifying fingerprint and facial recognition. Each user have their own fingerprint and face that is distinct from each and every one. So in order to read or scan, a proper algorithm has to be implemented. The scanned data has to be stored in the database. Thus, emerging another challenge on determining which database is suitable for storing such data. Also not to forget, what suitable or compatible programming language can be used to connect such devices and be able to integrate along with the database becomes a challenge as a whole. There is also an integration challenge where all the devices has to work with no errors of what.
1.7 Overview of this report and Project Plan
This report shows the development of the system that contains literature review, research methodology, primary research, system architecture, project plan, conclusion and reflection. In the first chapter contains background of the problem statement, deliverables, benefits, aims, and objectives of the system to be delivered.
Literature review which is the second chapter contains domain research that contains the knowledge on ATM and the issues pertaining to ATM. The knowledge is about ATM authentication methods, biometric authentication methods for facial and fingerprint, and architecture of the entire ATM system. In chapter three, two development methodology are compared and one of it selected to use for developing the system. RUP methodology is the chosen to be used to develop this system.
Chapter four is the primary research whereby data collection method is mentioned. Type of data, data gathering techniques and the analysis of the data is discussed. Continuing to next chapter five, the system architecture is discussed on database, interface, and design of the system. During development, what necessary components that needed to be in the system like programming language and IDE chosen to name a few.
In chapter six, project plan is discussed on releasing the project and also test plan to test the system checking the errors and bugs. Final chapter is on conclusion and reflection of the developer throughout the development of the system.
Chapter 2: LITERATURE REVIEW
2.1 Introduction
Automated Teller Machine (ATM) is important to both the customers and to the bank company. Since the importance of ATM is undeniable, protecting the integrity of ATM is also important. As more and more customers use ATM, the bank customers become the main victim to illicit activities by criminals. They tend to steal the debit or credit card and also the number and use those to steal money. By the time the customers realise about this the thief gets away with all the money. This sort of menacing trouble is within in our society and by having multiple level of authentication only such issue can be tackled with (Mahmood and Shaikh, 2013).
2.2 ATM Machines
To define ATM, it’s a cash machine or cash dispenser which is an electronic computerized telecommunications device that allows bank customers access their bank account. This machine accepts money from the customer though deposits and dispenses money to the customer as well. ATM also allows other banking options to be done. ATM operates when inserted credit or debit card into the machine. That particular card contains the customer’s account number and the pin number embedded in the card’s magnetic strip. ATM verifies by communicating with banks computers checking for the balance and sends notice about the transaction. This brilliant machine was invented by John Shepherd-Baron, an inventor from UK. The idea was to have a cash dispenser operating 24/7 (Curran and King, 2008).
There are issues pertaining with ATM including both internal and external. External meaning that human factors that threat the integrity of the system and the factors are from illegal activities. Credit card fraud, shoulder-surfing observation attack, credit card skimming, and recording with hidden camera when users enter pin number into ATM. Such attacks or threats have made banks register immense loss. Not only the bank but also money of the customer is being stolen. The most common attack is the shoulder-surfing attack and this attack is commenced just by observing the pin entry by the customer and knowing it. So after stealing the credit card taking money from that account is very easy (Khan, Hasan and Xu, 2015).
Such attack is increasing every year and sadly the customers are lot legally protected by the credit card companies and banks. There are also other scams like deploying fake terminals, credit card cloning, and wormhole attacks. Sometime user cannot rectify between the real ATM and a fake ones and uses it, losing the card information. Credit card skimming works when customers enters their card through the card slot in the ATM, the skimming device installed will get hold of the card information. Also if a user wishes to pay using card after having dinner at a restaurant there is a possibility that their card might be cloned through card cloning device (Tade and Adeniyi, 2016).
2.3 Similar System
The similar system of online banking or ATM machines is present and is the two factor authentication using mobile phones. This particular system contains two authentications which is done in a secure manner. What the authentications are is the One Time Password generation and an SMS based mechanism. ATM uses two factor authentication in which the user must possess an ATM card and must remember pin number in order to use ATM. One Time Password (OTP) is created without the even connecting the client to the server (Aloul, Zahidi and El-Hajj, 2009).
Mobile phone that the user has acts as a token and creates a one-time password using factors that it collected. Software will be installed in the phone to create the OTP. SMS based authentication works when the generated password doesn’t work or rejected. So the mobile phone can request one time password directly from the server without even generating from the phone. Server verifies the user after a message is sent from the phone through SMS (Aloul, Zahidi and El-Hajj, 2009).
In that message contains particular information about the user. After verifying, if the information is supplement, the server creates a random OTP number and send it to the user. User has limited to use the code before it expires. Such method requires both the client and server. The OTP algorithm are responsible for such random code generation. They are implemented to make users not be able to guess the next sequence. Sequence created must be random, unpredictable, and irreversible (Aloul, Zahidi and El-Hajj, 2009).
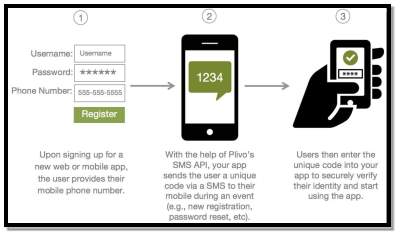
Figure 1 ATM Similar System (Plivo, 2017)
Image above shows the similar system that is found that functions similar to a contemporary ATM. Image above describes as when a user creates an account or does transaction, the user is notified with a unique code that the user enters into the application to verify their action. The same concept is adapted in online banking transaction as well.
2.4 ATM authentication Method
2.4.1 Biometric Methods
Issues that threatens the integrity of the system can be averted through implementing more security layers which are multi-level authentications that reduces such threats to the bank accounts of their customers. Customers will feel more comfortable when using the ATM more than ever. Biometrics is one option that can be included into one of multi-level authentication that can be included. What is biometrics? It is a method on scanning and analysing biological data of a human. For example fingerprint, iris, eye retina, voice pattern, DNA, facial pattern, and hand geometry (Rao and Nayak, 2014).
For this system two biometrics have been chosen fingerprint and facial pattern. The reason that these both are being used because most government and companies use this due to the fact it is easy to deploy, cost effective, and ease of use of verification (Rathod, Iyer and Meena S M, 2015). Fingerprint of each individual is unique is because each fingerprint has arches, whorls, loops, valleys, ridges, and furrows that is different from one than other. Facial patterns also works with the same concept albeit it uses facial features such as nose, eye distance, ear placement, and lips. The image of the face is captured and facial patterns are analysed to be stored which then can be used as a template (Singh and Nandi, 2012).
For verification the same facial image of the person is captured and again the facial patterns are analysed after that it is checked with the template and if it matches then the user is verified. The advantages of using biometrics are the person is present at that time of the authentication, the biometrics trait cannot be forged or lost, biometrics systems are hard to break, have good accuracy, and finally it is cost effective. Also a multimodal biometric system has its perks whereby it improves security elements and eliminates problems during recognition stage (Shaukat, Aziz and Akram, 2015).
2.4.2 Architecture
How does the ATM work or functions? Automated Teller Machine is a data terminal that has two input and four output devices. In order to communicate like any data terminal, ATM connects to the host processor. The host processor then connects to the internet service provider and which is the gateway to ATM network. After connecting to the network the ATM becomes available the card holder which is the user. Most host processors supports leased line that allows host processor directly connect through telephone line (Bowen, 2006).
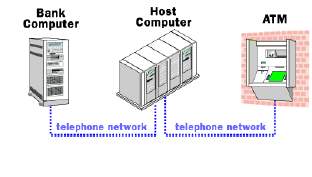
Leased line ATM are capable of handling thru-put therefore are placed at high volume locations. Such host processors are owned by bank institutions or owned by corporate service provider. Host processors that is owned by banks only supports bank owned ATM (Bowen, 2006).
2.5 Conclusion
To conclude this system, this system has three components those are user validation using username and password, fingerprint recognition, and facial recognition. The completed system comprises all these components and work together. This system works from user authentication by entering username and password, after that authenticating user for fingerprint, and finally authenticating user for facial recognition.
Chapter 3: DEVELOPMENT METHODOLOGY
3.1 Introduction
For the development of this project, three software developing methodologies have been considered. Those methodologies include Rational Unified Process Methodology (RUP), Prototyping and Waterfall. To develop any system a methodology is important as it provides guideline as well as provides solution for any error faced.
3.2 Rational Unified Process Methodology (RUP)
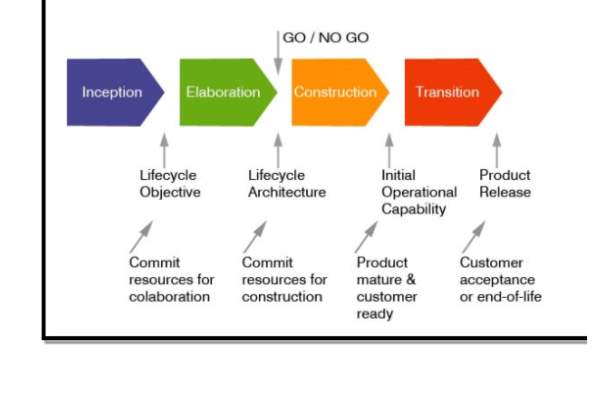
This methodology is a repetitive and adaptive system development tool that is now owned by IBM. RUP depends on timeline, important document model and unique team specialism. The project team utilise this methodology according to their need to create a robust software that meet project plan and the budget. RUP has six disciplines that needs to be followed. Those are business modelling, requirements gathering, analysis and design, implementation, testing and deployment. This methodology adopts an iterative method where it goes through several phases that is being used in many organisations. The phases are inception, elaboration, construction and transition (MyProjectManagementExpert, 2009).
At the first phase, the project plan is created and also use case or business case. In this phase everything is planned ranging from cost, risks, scope in order to develop a system with no bottlenecks. Without this phase it would be chaotic proceeding to the next step. Elaboration is the next step where the potential risks are resolved through solutions made by proper analysis. After planning out the solutions, plan of the entire project is structured. Prototypes are made to validate the risks that they have been taken care of. Developers choose which software to use and the budget for the development (MyProjectManagementExpert, 2009).
Next is the construction phase where codes are implemented into different parts of the system and this phase contains iteration that will increase if the size of the project is high. The system is tested till there is a fully working system completed with proper documentation that will be delivered to the customer. In the final phase transition, the product is delivered to the customer and they are trained to use the system. Updates and patches are released upon getting feedback from customers (MyProjectManagementExpert, 2009).
This methodology segments each development process into four phases that involves modelling, analysis and design, implementation, testing, and deployment (TatvaSoft, 2017). RUP is an object oriented and web based program or software development methodology. Such model also helps software engineers on guiding them, providing them with templates, and example for all aspects of software developing (TatvaSoft, 2017).
Advantages of using Rational Unified Process are is one which this methodology focuses on accurate and precise documentation. Moreover, customer or client requirements can be added throughout the methodology. When adding new requirements, it is based on the request management where it constantly updates or evolves the requirements (TatvaSoft, 2017).
Less integration is required throughout this project methodology since, the methodology itself contains integration process the entire time (TatvaSoft, 2017). RUP is an iterative model that allows developers to create a high level design of the application before beginning to build the actual product. After designing, a basic version of the application id built and then it is evolved into something better. Furthermore, RUP model makes developers design and develop application through step by step which eliminates flaws and defects in the system (Istqbexamcertification, 2012)
Disadvantages of RUP model is that each phase of the iteration is stagnant that contains no overlap. Each phase is rigid and it is on its own. Expensive system architecture or design problems might arise since not all the requirements are gathered in the foremost when designing and developing the application (Istqbexamcertification, 2012). Moreover, team members of the development team needs to be expert in their field so only then they can start to develop the application under this methodology. Designing and developing the system under this methodology might be confusing of its complexion and disorientation of processes (MyProjectManagementExpert, 2009).
Rational Unified Process (RUP) knows that conventional or traditional process shows only the single view of the process. On the contrary, RUP is explained according to these three perspective and they are dynamic, static, and practice perspective. Dynamic shows the phases of the model through time, static shows process activities that are active, and practice perspective advices on the good practices that can be used during the process. Conventionally RUP is described and explained by combining the static perspective and dynamic perspective (Sommerville, 2014).
3.2.1 Dynamic Perspective
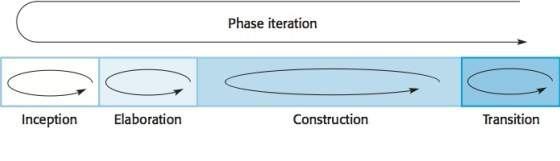
Rational Unified Process is a phase based model that contains four distinct phases in the software process. Compared to waterfall model, in which the phases contains process activities, RUP phases are closely related more to business than technical aspects. Iteration in RUP works in two ways. Each phase undergoes through its own iterative process with results developing incrementally. At the same time, all the process goes through an iterative process like the image below portrays (Sommerville, 2014).
3.2.2 Static Perspective
Static perspective of the RUP concentrates on the activities that take place during the creation process. Such are known as workflows in the RUP explanation. Six core process workflows and three core supporting workflows are found in the processes. RUP is created in parallel with the UML so workflow of the description is associated with UML models. The six core models are business modelling, requirements, analysis and design, implementation testing, and deployment (Sommerville, 2014).
Good thing about presenting in dynamic and static perspective shows that phases of the development phases are not in correlation with specific workflows. During the early stages of the process of RUP, mostly time and effort is focused on workflows like business modelling and requirements while through later in the process, it is testing deployment that is focused most (Sommerville, 2014).
3.3 Prototyping Methodology
In this methodology, before implementing coding or design a disposable prototype is built to really understand the customer’s requirements. The prototype is created based on the current requirements. Using this methodology, the customer gets to view of the system that is about to be created, in other words customers get to see the mock-up so that they able to understand the requirements better. This methodology is important if there is a huge and complex system is about to be created (Istqbexamcertification, 2012).
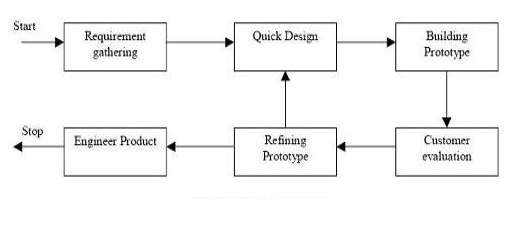
When showing the mock-up to the client most of the system functions are not programmed. At the end of the methodology a full working completed system is delivered to the system. Prototype methodology is very useful when there is a lot of customer interaction needed. Systems like online and web services need frequent customer interaction so prototype methodology is suitable for these types of systems. Constant feedback from customer is important since this methodology is suitable when creating a system with good computer interface systems (Istqbexamcertification, 2012).
3.4 Waterfall Methodology
This model was the first methodology that was to be introduced. This model is noted as a linear-sequential life cycle model. This methodology is very easy to use and understand. Waterfall methodology requires previous phase to be completed before starting the next phase and there is no iteration. Projects that are small and there is no certain requirements are suitable to use waterfall methodology. At the final phase the project is reviewed to check whether the project is a success or failure. Testing is done after the completion of the development. Each phase of this model does not overlap (Istqbexamcertification, 2016).
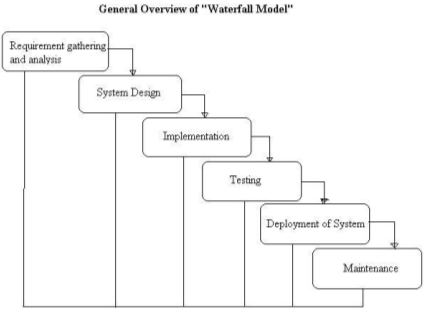
Figure 6 Waterfall Model (2016)
Waterfall methodology requires less customer interaction when developing the product. End product is then demonstrated and showed the functionalities of the system to the customer. Any failure after developing the product is a drawback and this adds cost on eliminating the error as well as updating the entire documentation. This methodology is suitable when the technology is understood to develop the product. The major setback of this methodology is that any error or oversight in any phase, the developers cannot rollback and have to deal the problem no matter what the cost (Istqbexamcertification, 2016).
3.5 Comparison between Methodologies
| Rational Unified Process | Waterfall Methodology | Prototyping Methodology | |
| Phases | Inception, Elaboration, Construction, Transition | Requirement gathering, System design, Implementation, Testing, Deployment of system, Maintenance | Requirement gathering, Quick design, Building prototype, Customer evaluation, Refining product, Engineer product |
| Iteration | Yes | No | Yes |
| Customer Involvement | Throughout the project | At the end of the project | Throughout the project |
| Type of project | Huge | Small | Small |
| Flexible phases | Yes | No | Yes |
| Documentation | Less | Heavy | Less |
Table 1 Comparison Table
The methodology chosen here to develop the system is Rational Unified Process because this project is huge and the potential risks are analysed beforehand to reduce error, cost and time wasted to find solutions. The integration process takes less time to complete as it is done throughout this methodology. When developing this system, the devices that are required for scanning should work with the system prompting no error, so the integration matters a lot in this project and RUP suits just fine. Iterations in RUP that can be utilised very well in when developing this system
3.6 Conclusion
To conclude, compared to all of the methodologies, Rational Unified Process stands out to be the most suitable methodology for this project. Using this methodology, completing the project would be fast as well as effective to complete the project. Any changes or new requirements added, can easily be adapted into the methodology since it is an iterative process.
Chapter 4 Development / Deployment
4.1 Programming Language Chosen
4.1.1 C# Programming Language
C# is an object oriented language that allows the developers to build many secure and robust programs that run on .Net Framework. C# can be used to program Windows Client Application. XML Web Services, and database applications. This language is also easy to learn and can be learned quick if the developer has the basic knowledge of C, C++, or Java (Microsoft, 2017)
4.2 IDE Chosen
4.2.1 Visual Studio 2013
Visual Studio 2013 is capable of programming C#, C++, F#, JavaScript, and HTML. The system that is about to be created is programmed with using C# and Visual Studio is best integrated development there is. The advantages of using Visual Studio 2013 is because the debugging of this IDE is fast and efficient. Also the SDK for the fingerprint device, it can be installed in Visual Studio and it allows such SDK being installed. Moreover, facial recognition SDK which is the EmguCV which will be installed also can be used in Visual Studio 2013 to create facial recognition programs by importing EmguCV libraries.
4.3 Libraries Chosen
4.3.1 One Touch SDK
The libraries used for fingerprint is One Touch SDK from Digital Persona itself which is the fingerprint device brand. This SDK contains library that can be installed and be used for C# coding. One Touch SDK provides library for getting the fingerprint from the scanner and be able to store in the database.
4.3.2 EmguCV
EmguCV is a multi-platform .Net wrapper for OpenCV image analysing and computing library. This SDK allows developers to use OpenCV libraries to be used in C#, VB, VC++, and Python. Moreover, this wrapper can be compiled in Visual Studio, Xamarin, and in Unity as well. This SDK is available for Windows, Linux, Android, and Mac OS X (EmguCV, 2017).
4.4 Database Management System Chosen
4.4.1 MySQL
The database chosen is MySQL for storing the data and retrieving the data for both facial and fingerprint. Data being stored by both authentications are in the form of image such as BLOB format. MySQL can be integrated with C# programming and allows storage of such data to be stored.
4.5 Operating System Chosen
4.5.1 Windows 8
This is a Microsoft operating system which was released in the year of 2012. Both the MySQL and Visual Studio 2013 along with the necessary SDKs are installed in Windows 8. This operating system will be the baseline for the completion of the system (WhatIs, 2014).
4.6 Web Server Chosen
None
4.7 Operating System Chosen
None
4.8 Conclusion
To conclude, all the specified specifications will be used to develop the system. The language that is chosen is C# which will be used to develop the system. System that is programmed will have to integrate with the fingerprint scanning and facial recognition. Using Visual Studio as the IDE will provide enough stability and scalability to use those scanning and recognition devices and work with the coded program.
Chapter 5 Primary Research
5.1 Introduction
For the primary research, the developer has decided to use questionnaire and interview as the data gathering method. Questionnaire and interview will help the developer on gathering the information and analysing it for the problem that is being faced by the users of the current existing system.
5.1.1 Questionnaire
Questionnaires are cost effective, quick and efficient in the way of collecting large amount of data from large number of respondents. This method is fast due to the fact that, the researcher does not need to be present when the questionnaire is being filled. Questionnaires are way too useful for large respondents when interview would be time consuming. When creating and designing questionnaire, the language used must be suitable and appropriate for the respondents so that they can understand (McLeod, 2014).
For investigating patterns and frequency questionnaires are very useful. User also will feel satisfied with the collection of data from questionnaire because it shows the respondents attitude and opinion clearly (Evalued, 2006). Questionnaires can be classified by being both quantitative and qualitative based on the questions that it has. Answers from closed ended questions are evaluated with quantitative method whereas answers from open ended questions are evaluated with qualitative method (Dudovskiy, 2016).
Some of the questionnaire advantages include high speed of data collection, low cost or no cost needed, and questionnaire contains high level of objective compared to other data collection techniques that are available (Dudovskiy, 2016). Moreover, other advantages of questionnaire include the data collected is simple to manage and analyze, respondents can take their own time to answer the questions, and questionnaires are fairly easy and quick for respondents to answer the questions (Evalued, 2006).
5.1.2 Interview
Interview is a private meeting between people asking the question and people who are answering the question. The person who answers the question being asked is known as interviewee while the person who asks the question is known as interviewer. Interview is conducted when the purpose is to get the viewpoint of others or to get to know each other. There are different sort of interview types such as personal interviews, evaluation interview, persuasive interview and many more (The Business Communication, 2014).
Interview allows the researcher to investigate issues in depth manner. It also allows an individual to express their opinion regarding any issues though it can be about sensitive information which people feel uncomfortable when discussing in a group. Interview adds human perception and understanding towards the data collected. The questions asked can be either open ended or closed ended. For this research the developer has chosen open ended and closed ended questions to conduct interview (Evalued, 2006).
Some of the advantages of interview methodology is that it is time saving, less expensive, selecting perfect candidate for the interview, and also interview allows to get a high response rate from the candidate chosen (The Business Communication, 2014).
5.2 Design
5.2.1 Questionnaire
The following collection of questions were created to collect the viewpoint from random sample of people that use the existing system. Purpose of collecting these viewpoints are to provide information and guide the developer on developing the system. A total of 10 questions will be required for the respondents to respond to and some of the questions might to relate to other.
| Question 1 | Do you feel your money transaction in the ATM is secured and protected? |
| Objective | This question is to confirm their confidence level towards the existing system. |
| Answer | Yes
No |
Table 2 Questionnaire Question 1
| Question 2 | Do you think that the current transaction process in the ATM can easily be compromised? |
| Objective | This question is to check the people on their awareness of current system vulnerabilities. |
| Answer | Yes
No |
Table 3 Questionnaire Question 2
| Question 3 | Are you aware of shoulder surfing or any other attacks that can be done on ATM to compromise secured data? |
| Objective | This question is asked to know the respondents knowledge on the attacks that can be performed towards ATM. |
| Answer | Yes
No |
Table 4 Questionnaire Question 3
| Question 4 | If the answer is yes based on question 3, do you think that the current system should be improved by adding more verification features? |
| Objective | The purpose of this question is to clarify that they need a better secure system |
| Answer | Yes
No |
Table 5 Questionnaire Question 4
| Question 5 | What kind of information do you think that the attacker would want by attacking the system? |
| Objective | The purpose of this question is to know whether the respondents have the knowledge on importance of their personal data. |
| Answer |
Table 6 Questionnaire Question 5
| Question 6 | When performing transaction in the ATM, do you know or aware of your information being stolen at that time? |
| Objective | The purpose of this question is to know whether the respondents are aware of their surroundings. |
| Answer | Yes
No |
Table 7 Questionnaire Question 6
| Question 7 | If the answer is yes based on question 4, are you willing to give more information of yourself to increase the level of verification in the ATM? |
| Objective | This question is to vindicate that respondents are willing to cooperate to make the system more secure. |
| Answer | Yes
No |
Table 8 Questionnaire Question 7
| Question 8 | Do you feel that by adding biometric verification would enhance the level of secure transaction in the ATM? |
| Objective | The purpose of this question is to know their preference on biometric verification. |
| Answer | Yes
No |
Table 9 Questionnaire Question 8
| Question 9 | If the answer is yes based on question 8, do you think that those biometric verification can be facial recognition and fingerprint verification? |
| Objective | The purpose of this question is confirm their preference on biometric verification. |
| Answer | Yes
No |
Table 10 Questionnaire Question 9
| Question 10 | If the answer is yes based on question 9, do think it is ok if the ATM takes longer time to do transaction because of those biometric verification even though the level of security is higher? |
| Objective | The purpose of this question is vindicate their preference on adding biometric verification in the ATM transaction process. |
| Answer | Yes
No |
Table 11 Questionnaire Question 10
5.2.2 Interview
These questions were prepared to ask the users of the existing system by the developer. The users of the system include students, lecturers and etc.
Name: Occupation:
Date: Time Start: Time End:
Location: Mode of Interview:
| Question 1 | Do you know think that the amount of data that you have given to the bank is enough to have a secured transaction in ATM? |
| Answer: | |
| Objective | To know that the respondents think they have provided sufficient data to have a secured transaction in ATM. |
Table 12 Interview Question 1
| Question 2 | Have you ever experienced or saw or heard any incidents occurring particularly compromising or stealing information when performing transaction in ATM? |
| Answer: | |
| Objective | To investigate whether the respondents have been in that situation before or know these incidents does occur during transaction. |
Table 13 Interview Question 2
| Question 3 | What would your opinion would be if biometric verification would be added to the ATM to increase the level of transaction security? |
| Answer: | |
| Objective | To investigate respondents’ preference on biometric verification. |
Table 14 Interview Question 3
| Question 4 | What sort of biometric verification can be added to increase the level of transaction security in ATM? |
| Answer: | |
| Objective | To investigate respondents’ knowledge on biometric verification. |
Table 15 Interview Question 4
| Question 5 | Are you willing to provide biometric information such as fingerprint and facial image to bank so that they can provide better and secure ATM transaction? |
| Answer: | |
| Objective | To investigate respondents’ willingness to cooperate with authorities to have a better secure transaction. |
Table 16 Interview Question 5
| Question 6 | If your answer is no to question 5, can you give reasons on not giving such information to bank authorities? |
| Answer: | |
| Objective | To investigate respondents’ reasons on not giving those fingerprint and facial images to bank authorities. |
Table 17 Interview Question 6
Chapter 6 Requirements Validation
Results of the questionnaire and interview will be analysed in this chapter to be able to have an overview of the feedback given by the public who use this system every day in their daily lives. Their feedback includes the security implementation to the current system privy towards fingerprint and facial authentication as well as security related threats towards the current system.
6.1 Analysis of Data
6.1.1 Analysis of Questionnaire Data Collected
The questions proposed in the earlier chapter was implemented in the Google Form and then were sent out 30 respondents. Upon receiving their feedbacks, such analysis was performed and shown below.
| Question 1 | Do you feel your money transaction in the ATM is secured and protected? |
| Result | 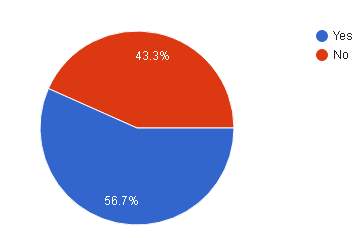 |
| Analysis | From the pie chart above it shows that majority of 56.7% which are 17 feel their transaction is protected while 13 or 43.3% think their transaction is not protected. |
Table 18 Analysis of Questionnaire Question 1
| Question 2 | Do you think that the current transaction process in the ATM can easily be compromised? |
| Result | 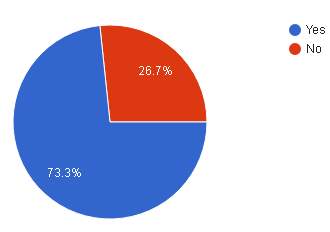 |
| Analysis | As for the result above, majority of 73.3% or 22 people think that the transaction can be compromised while 26.7% or 8 think the transaction cannot be easily compromised. |
Table 19 Analysis of Questionnaire Question 2
| Question 3 | Are you aware of shoulder surfing or any other attacks that can be done on ATM to compromise secured data? |
| Result | 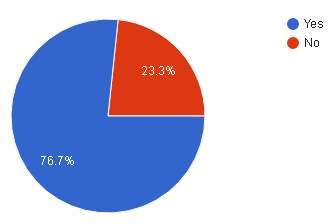 |
| Analysis | The pie chart above shows that majority of 76.7% or 23 know about such attacks and 23.3% or 7 of them are not aware of such attacks being made. |
Table 20 Analysis of Questionnaire Question 3
| Question 4 | If the answer is yes based on question 3, do you think that the current system should be improved by adding more verification features? |
| Result | 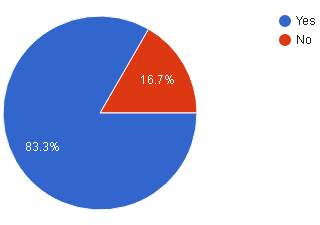 |
| Analysis | Majority of the respondents 83.3% or 25 from shown pie chart above, agree that the current system should be improved while 5 or 16.7% does not think ATM need more verification features. |
Table 21 Analysis of Questionnaire Question 4
| Question 5 | What kind of information do you think that the attacker would want by attacking the system? |
| Analysis | According to the responses from the 30 respondents 10 respondents believe that the attacker would want the user’s pin number or password of their account. Moreover, 13 of the respondents believe that the attacker would want the user’s information such as account details or personal information. Finally, 7 of the respondents believe that the attacker would want to know about the bank balance of the user. |
Table 22 Analysis of Questionnaire Question 5
| Question 6 | When performing transaction in the ATM, do you know or aware of your information being stolen at that time? |
| Result | 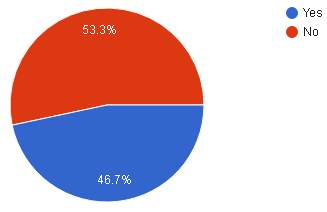 |
| Analysis | From the pie chart above, majority of the respondents 53.3% or 16 believe that they are not aware about their information being stolen and 46.7% or 14 think they are aware of it. |
Table 23 Analysis of Questionnaire Question 6
| Question 7 | If the answer is yes based on question 4, are you willing to give more information of yourself to increase the level of verification in the ATM? |
| Result | 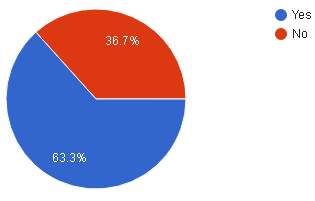 |
| Analysis | According to the pie chart above majority 63.3% or 19 are willing to give more information about themselves to increase the level of verification and 36.7% or 11 are not willing to give more information about themselves. |
Table 24 Analysis of Questionnaire Question 7
| Question 8 | Do you feel that by adding biometric verification would enhance the level of secure transaction in the ATM? | |
| Result | 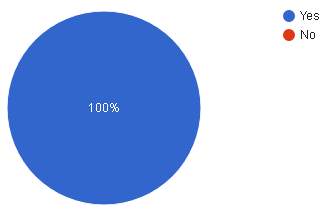 |
|
| Analysis | According to the pie chart above, 100% or 30 respondents feel that by adding biometric verification would increase level of secure transaction in the ATM. |
Table 25 Analysis of Questionnaire Question 8
| Question 9 | If the answer is yes based on question 8, do you think that those biometric verification can be facial recognition and fingerprint verification? |
| Result | 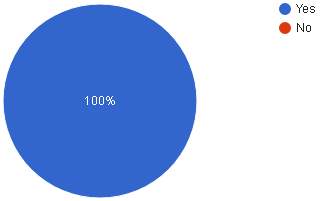 |
| Analysis | According to the pie chart above, 100% or 30 respondents feel that those biometric verification can be fingerprint verification and facial recognition. |
Table 26 Analysis of Questionnaire Question 9
| Question 10 | If the answer is yes based on question 9, is it ok if the ATM takes longer time to do transaction because of those biometric verification even though the level of security is higher? |
| Result | 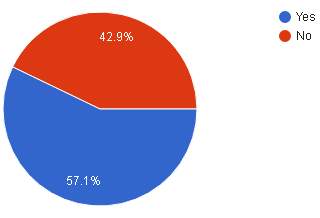 |
| Analysis | The pie chart above shows that majority 56.7% or 18 think it is ok if it takes longer time to do transaction with those biometric verification in the ATM and 42.9% or 12 think that is not ok. |
Table 27 Analysis of Questionnaire Question 10
6.1.2 Analysis of Interview Data Collected
The analysis of the interview conducted after interviewing the interviewees that use the system frequently are Mr Ryan, Mr Pavien, and Mr Tajuddin. The mode of interview conducted was face-to-face with all of the interviewees. The analysis of each interview is discussed below with the answers from the respondents.
Interview 1
Name: Ryan Neville Raja Occupation: Student
Date: 23/5/17 Time Start: 10.13AM Time End: 10.25AM
Location: Library Mode of Interview: Face-to-Face
| Question 1 | Do you know think that the amount of data that you have given to the bank is enough to have a secured transaction in ATM? |
| Answer: No, not enough |
Table 28 Analysis of Interview 1 Question 1
| Question 2 | Have you ever experienced or saw or heard any incidents occurring particularly compromising or stealing information when performing transaction in ATM? |
| Answer: Yes, Seen before happening |
Table 29 Analysis of Interview 1 Question 2
| Question 3 | What would your opinion would be if biometric verification would be added to the ATM to increase the level of transaction security? |
| Answer: More Secure, Better verification |
Table 30 Analysis of Interview 1 Question 3
| Question 4 | What sort of biometric verification can be added to increase the level of transaction security in ATM? |
| Answer: Fingerprint, Facial, Iris |
Table 31 Analysis of Interview 1 Question 4
| Question 5 | Are you willing to provide biometric information such as fingerprint and facial image to bank so that they can provide better and secure ATM transaction? |
| Answer: Yes, Willing to give more information |
Table 32 Analysis of Interview 1 Question 5
| Question 6 | If your answer is no to question 5, can you give reasons on not giving such information to bank authorities? |
| Answer: |
Table 33 Analysis of Interview 1 Question 6
Interview 2
Name: Pavien Raj A/L Rajan Occupation: Student
Date: 23/5/17 Time Start: 11.00AM Time End: 11.10AM
Location: Library Mode of Interview: Face-to-Face
| Question 1 | Do you know think that the amount of data that you have given to the bank is enough to have a secured transaction in ATM? |
| Answer: No, not enough data has been given |
Table 34 Analysis of Interview 2 Question 1
| Question 2 | Have you ever experienced or saw or heard any incidents occurring particularly compromising or stealing information when performing transaction in ATM? |
| Answer: Yes, Have heard in the news |
Table 35 Analysis of Interview 2 Question 2
| Question 3 | What would your opinion would be if biometric verification would be added to the ATM to increase the level of transaction security? |
| Answer: More secure |
Table 36 Analysis of Interview 2 Question 3
| Question 4 | What sort of biometric verification can be added to increase the level of transaction security in ATM? |
| Answer: Iris, Fingerprint, Facial |
Table 37 Analysis of Interview 2 Question 4
| Question 5 | Are you willing to provide biometric information such as fingerprint and facial image to bank so that they can provide better and secure ATM transaction? |
| Answer: Of course to make sure secure transaction occur |
Table 38 Analysis of Interview 2 Question 5
| Question 6 | If your answer is no to question 5, can you give reasons on not giving such information to bank authorities? |
| Answer: |
Table 39 Analysis of Interview 2 Question 6
Interview 3
Name: Tajuddin bin A.Rashid Occupation: Lecturer
Date: 30/5/17 Time Start: 10.15AM Time End: 10.30AM
Location: B05-03 Mode of Interview: Face-to-Face
| Question 1 | Do you know think that the amount of data that you have given to the bank is enough to have a secured transaction in ATM? |
| Answer: Yes, willing not to give more information |
Table 40 Analysis of Interview 3 Question 1
| Question 2 | Have you ever experienced or saw or heard any incidents occurring particularly compromising or stealing information when performing transaction in ATM? |
| Answer: Yes heard before |
Table 41 Analysis of Interview 3 Question 2
| Question 3 | What would your opinion would be if biometric verification would be added to the ATM to increase the level of transaction security? |
| Answer: Feel more secure, concern with functionality |
Table 42 Analysis of Interview 3 Question 3
| Question 4 | What sort of biometric verification can be added to increase the level of transaction security in ATM? |
| Answer: Fingerprint |
Table 43 Analysis of Interview 3 Question 4
| Question 5 | Are you willing to provide biometric information such as fingerprint and facial image to bank so that they can provide better and secure ATM transaction? |
| Answer: Yes willing to give such information |
Table 44 Analysis of Interview 3 Question 5
| Question 6 | If your answer is no to question 5, can you give reasons on not giving such information to bank authorities? |
| Answer: |
Table 45 Analysis of Interview 3 Question 6
For the analysis of the interview, in question1, Mr Ryan, Mr Pavien agreed that not enough data has been given and are willing to give more information while Mr Tajuddin is not willing to give enough data mentioning that, enough data has been given to the banks. This question has shown that users not all are willing to give more information to have a secured transaction even though some are willing to do so.
In question 2, the interviewees, all of them have heard or seen or experienced about the attacks done on ATM to compromise security. This clearly shows that attacks done on ATM to compromise security on transaction is not just a small issue and every user of ATM knows of such threat exist.
In question 3, Mr Ryan, Mr Pavien, and Mr Tajuddin all of them mentioned more secure and better verification if biometric verification would be added to the ATM to increase the level of the transaction done. This question clearly shows that the users of this system agreed, upon increasing verification methods by including biometric verification, the level of having a secured transaction is much higher and safer.
In question 4, Mr Ryan and Mr Pavien answered that they would want fingerprint, iris and facial biometric verification to be added to the ATM while Mr Tajuddin answered fingerprint itself should be enough to for biometric verification to be added into the ATM. Through analysing their answers, it can be concluded that most of the users of the ATM would prefer more than one biometric verification to be on the ATM but some prefer just to have one biometric verification.
In question 5, Mr Ryan, Mr Pavien, and Mr Tajuddin all answered that they are willing to give their biometric information to the banks so that they can provide a better secure ATM transaction. So this can be concluded that, users of the ATM are willing to give biometric information such as fingerprint, facial or iris to the bank. This shows that users prefer biometric verification to be in the ATM.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




