Development of New Steganography Algorithm
Info: 7964 words (32 pages) Dissertation
Published: 9th Dec 2019
Tagged: Cyber SecuritySecurity
4.1 Introduction
This chapter provided the system activity for the image steganography, this includes the hiding/embedding of the secret message the unveiling of the message as well as the systematic step by step approach toward ensuring the implementation of these steps. The chapter start by explaining the new system thereby providing a hint on its content.
4.2 The Proposed Methodology
The proposed system uses a strong approach to embedded secret message into one of three channels of the RGB colours of an image. bitxoring, transposition, bits shuffling, secret key, and cryptography to develop a new algorithm for steganography system. The new algorithm will provide the below important in enhancing the security of data.
- Before the mapping of the secret message the image carrier from the cover image by transposition this will mislead the file attacker.
- Encryption of the secret key and data are encrypted using strong and repetitive algorithm to provide strong security that cannot be easy attacked or breached.
- The Secret data will be hide by mapping it with the frequency of the blue colour in the carrier image using modification method for gray colour.
- Improve file security in the internet by effective encryption and embedding of secret message which can only be unveil by an authorized third party.
Different encryption method will be used to ensure efficient hiding of a secret message on a selected cover image, these modules include the File Mapping and Encryption methods to hide a secret message and ensure its security. The general diagram explaining the new methodology is displayed on figure 4.1 below.
4.3 Encryption Algorithm
Encryption algorithm is the step-by-step approach adopted to hide message in an innocent image, this algorithm is the procedural methodology developed to provide security against malicious attacked of a File over the internet. The encryption algorithm are used to hide in this algorithm, it is this algorithm that provide the first step on the ensuring security of a file over the internet as well as serve as the first stage on the image steganography adopted for this research work. The algorithm start with the accepting an input of image hide message on it and give an output of encrypted Stego-image with a secret data and key bits. Below are outline of the encryption algorithm.
Input: Original Coloured Image and a Document
Output: a Stego_Image Consisting a secret message
Step 1: Select to be hided and a required encryption key.
Step 2: Translate the selected key into a single dimensional array (1D array)
Step 3: Use a Logic of 1 to apply bitxor process on the single array bit of the secret key with a logical 1.
Step 4: Rearrange the encrypted nits from the bitxor while interchanging the even and odd bits from step 2.
Logically:
If the secret key nits=1
Perform bitxor process with logical 1.
Else
Do not implement bitxor process.
End if
Step 5: Repeat step 4 until all secret data bits are encrypted.
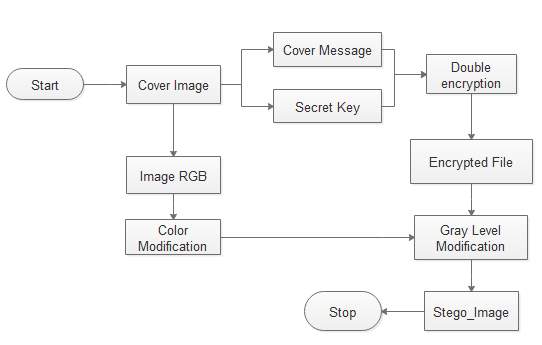
Fig 4.1 steps of text hiding and unveiling on image
4.4 Mapping Module
The mapping procedure was adopted to effectively place the secret message into the carrier/cove image pixel for final encryption. The cover image channels are transformed after which the 1 to 1 mapping is done to place the secret data into the in the cover image to maintain the bit and pixel of the original cover image to obtain a stego image output.
Input: Cover Image, Secret Message
Output: Stego_Image
Step 1: select Carrier Image
Step 2: Transform the Cover image in Step 1.
Step 3: Select Secret File
Step 4: Perform 1-1 mapping to hide the message in step 3 into Image in Step 2
Step 5: Stego Image.
4.5 Hiding Algorithm
Input: Coloured Image as cover, secret data and key,
Output: Stego_image
Step One: Select the colour cover image and divide it into red, green, and blue channels
Step Two: Apply image transpose on all the three channels of the input image
Step Three: Encrypt the secret key and secret data according to the encryption module 3.1
Step Four: Convert the pixel values if the blue channel by adding 1 if the first bit of the cover image is one (1). If the pixel value is even, add one to the pixel.
Step Five: Map the secret data of step 4 based on secret key bits (SKB) such that
- If the secret key bits is even the system will add one (1) to the pixel value.
- If the pixel value of the secret key bit value is 0 or odd, subtract 1 from the pixel value.
- If the secret bit pixel value is 1 or even, the system will add 1 to the pixel value.
Step Six: Repeat step 5 until all secret bits are mapped with the gray-levels of carrier image
Step Seven: Take the transpose of all three planes and combine them to make the stego image
4.6 Extraction Algorithm
Figure 4.2 describes the flow diagram for retrieving text from image. The user needs to input the key file and generated stego image. The same key file should be used at the time of hiding and extracting. After the input is provided, the data is validated and checked for exceptions, and if any exceptions are found, the process begins again. If no exceptions are found, then an alteration is done to extract the secret message from the image file. This extracted secret message will then be displayed on the screen or else be saved in a file.
Input: Stego Image, Secret Key
Output: Secret data
Step One: Select Stego_image
- Divide the Stego_Image colour RGB (Red, Green, and Blue) into different channels
Step Two: Transpose all the three colour channels of the Stego_image
Step Three: Extract LSB of the blue channel.
Color pixel = bmp.GetPixel(j, i);
for (int n = 0; n < 3; n++)
{
switch (colorUnitIndex % 3)
{
case 0:
{
charValue = charValue * 2 + pixel.R % 2;
} break;
case 1:
{
charValue = charValue * 2 + pixel.G % 2;
} break;
case 2:
{
charValue = charValue * 2 + pixel.B % 2;
} break;
}
colorUnitIndex++;
if (colorUnitIndex % 8 == 0)
{
charValue = reverseBits(charValue);
if (charValue == 0)
{
Step Four: Repeat the extract in step three till all the secret bits are successfully extracted
Step Six: Decrypt the bits by Reverse encryption method in steps 3-1 to develop the original text.
Step Seven: Secret Message.
4.8 Evaluation of Image Quality
This aspect deals with the study of the original image and the developed stego_image to determine whether if there will be a detectable change or physical modification of the original image hence verify the effectiveness of the algorithms and the steps taken toward the steganography development. The quality of each (that is the Original Image and the steganography output file) where analysed extensively using the common measures used to compare the degree of quality.
The new steganographic algorithm has a high embedding capability and a low visual distortion. The encryption methods are quietly durable against malicious attacks, including noise addition, smoothing, quantization and normal mesh editing. In addition to robustness, the new algorithm offer acceptable embedding capacity without incurring noticeable visual distortion after embedding.
The efficiency of the new encryption and steganography is evaluated in terms of embedding capacity, embedding distortion and robustness. The embedding distortion between the original mesh and its corresponding was analyse by root mean square error (RMSE), Peak Signal ratio , Signal Noise Ratio and The robustness is verified using the Normalise Close Correlation method according to the correlation coefficient between the original message string and the extracted one.
4.8.1 Mean-Square Error (MSE)
This provides the similarities between images, it gives distortion level between original and Stego_image. It is viewed as measure of image signal quality (Wang & Bovik 2009). Mean Square Error is used widely for accessing image quality because; it is simple to determine, it is excellent metric for image optimization and its parameter are easy to calculate.
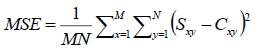 4.1
4.1
The mean-squared error (MSE) between two images is calculated using the equation above:
Where: M and Nare number of rows and columns of the cover images, respectively. Y and X are the Stego image signal and the signal of the original image.
Mean-squared error depend strongly on the image intensity scaling. A mean-squared error of 100.0 for an 8-bit image (with pixel values in the range 0-255) is good while MSE of 100.0 for a 10- bit image (pixel values in 0-1023) is scarcely measureable (Allawi 2015).
4.8.2 Peak Signal-To-Noise Ratio
Peak-Signal-to-Noise ratio give explanation of the of image quality by providing the ratio of image signal and the distortion power of the image in a logarithmic ration. It is also viewed as the relative explanation of image perception by human in term of quality. The higher the PNSR the higher the image quality (Wolf & Pinson 2009). Peak Signal-to-Noise Ratio (PSNR) gives image quality by scaling the Mean Square Error according to the image range.
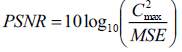 4.2
4.2
PSNR is values are presented in decibels (dB). PSNR is a good measure for comparing restoration results for the same image, but between-image comparisons of PSNR are of less meanings.
4.8.3 Signal to Noise Ratio (SNR)
This give the ratio of the signal to noise power, it is an index that gives the level of the changes and effect on the images based on a certain effect (Steganography), it gives the quantity/transformation level of the Image (Sundar 2015). The signal to noise ratio is expressed in the equation 4.3 below.
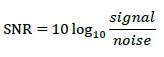 4.3
4.3
4.8.4 Normalize Cross-correlation
This compares the two image based on the relationship thy have in common, it is used to measure how far the two image deviate or relate to one another (Muhammad et al. 2015). The NCC is expressed as in equation 4.4 below.
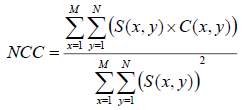 4.4
4.4
CHAPTER FIVE
System implementation deals with the new system development, installation, Testing and made ready for use. Details of the system and key point of the requirement specification are highlighted and put in work. System implementation is an essential step in software and project development its success determines the accomplishment of the new system. At this instance, after all is said and done the system is duly ready to be implemented. System design is concerned mainly with the coordination of activities, job procedures and equipment utilization in order to achieve organizational objectives. It addresses data input and output data, processing and interface.
This stage involves the design and final implementation of the system, a system was designed that will allow user to encrypt a message in an image which can also be decrypted.
5.2 Implementation
A user is required to upload an image file, then the level of secrecy is selected. The message to be transferred is typed in into the message box, after this, the user inputs his/her password for encryption and embedding secret message into the image. Finally, the user clicks the button “Write Message to Image”. After the appropriate measure have been taken, the user would be required to download a new image which carries the secret message, which is the “Crypto-Stego image” The algorithm used for the LSB technique makes it very difficult for the human eye to detect changes in the images sent and received over the internet.
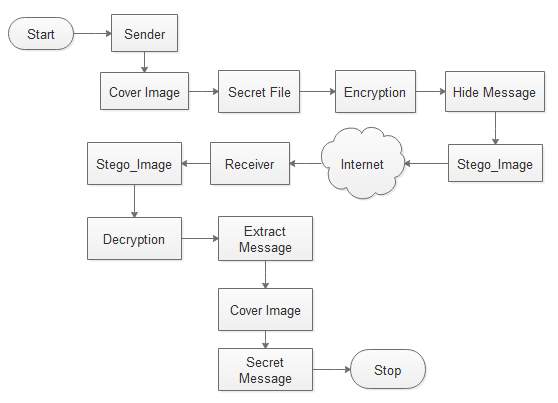
Fig 5.1: Implementation steps
The choice of programming language to use for this programme is visual basic. The structure of the Basic programming language is very simple, particularly as to the executable code. Visual Basic has many new and improved features such as inheritance, interfaces, and overloading that make it a powerful object-oriented programming language. It is particularly easy to develop graphical user interfaces and to connect them to handler functions provided by the application. Visual Basic fully integrates the .NET Framework and the common language runtime, which together provide language interoperability, garbage collection, enhanced security, and improved versioning support. C++ has been used for the design of the system and rendering functions for the steganography execution.
5.3 Hardware Requirement
For this system to run effectively there must be a provision of the following hardware:
- A minimum hard disk space of 20 Gigabytes (GB)
- RAM size of 1GB
- A VGA colour monitor
- Mouse
- Keyboard
5.4 Software Requirement
- Windows operating system such as Windows 2008. Windows 7.
- Visual basic 6.0 software.
5.5 Architecture of the New Method
Architecture defines the broad structure of the system to be developed it consider the computers and networks that are used to construct the overall system. According to Lunn (2003) architecture involves the software tools that are used to construct the system, such as compilers, modelling tools, databases, and packages. Figure 3.9 describes the architecture of the system implementation. The modules of the steganography tool are also included in the architecture. The user can be either the sender or the receiver. The cover file in the above architecture can be image, audio, and video. The in-depth flow of this architecture is described in the design approach.
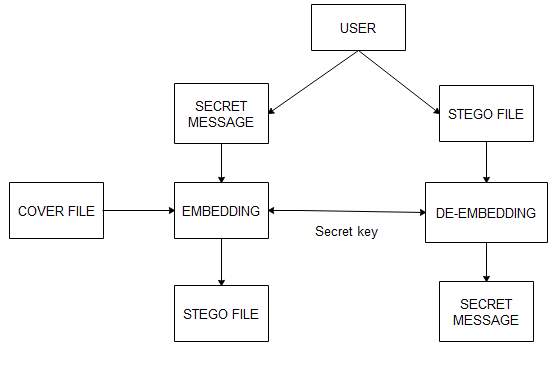
Figure 5.2 Architecture of Proposed Steganography
5.6 Module Description
This gives the actual pictorial presentation of the designed system. The modules are represented in a step by step process starting from the system launch up to file decryption or unhidden of the message.
Start the application
Figure 4.3 Application Launched
Figure 5.3 shows the Welcome page. It is the first interface that appears on the screen when the application is being loaded. This page displays the name of the application and some other information about the software. The page consist of all the several option that the application can perform, this includes the Extraction of hidden massage option, the Hide option for hiding message in an image, the upload (for both image and the message to hide) button as well as the save button which will allow user to save the encrypted image after the text is hidden in it.
Sender Section
Most of the activities in the sender section is encryption and setting password key for the steganography. The sender functions start from the figure 5.4 below.
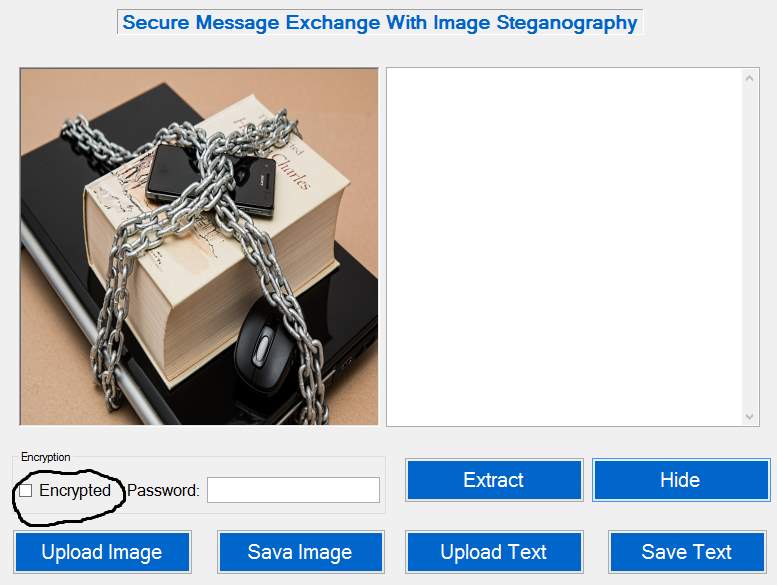
Figure 5.4: Select Encrypt password
5.6.2 Encryption
The steps below describes the process of hiding text in Image (Encryption Phase) of Image Steganography After lunching the application, it can be used to hide text in image or extract hidden text from image with the authentication password. If the user does not click on encrypt like shown below. The password will be stored as plaintext.
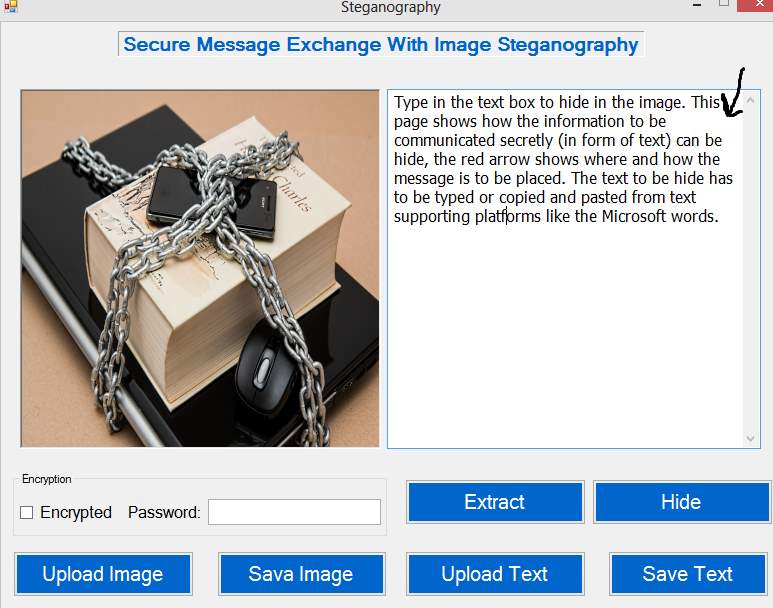
Figure 5.5: Type in Text box
Type in the text box to hide in the image. This page shows how the information to be communicated secretly (in form of text) can be hide, the red arrow shows where and how the message is to be placed. The text to be hide has to be typed or copied and pasted from text supporting platforms like the Microsoft words. After the text is typed the user can then go ahead to upload the image in which the text is to be hided.
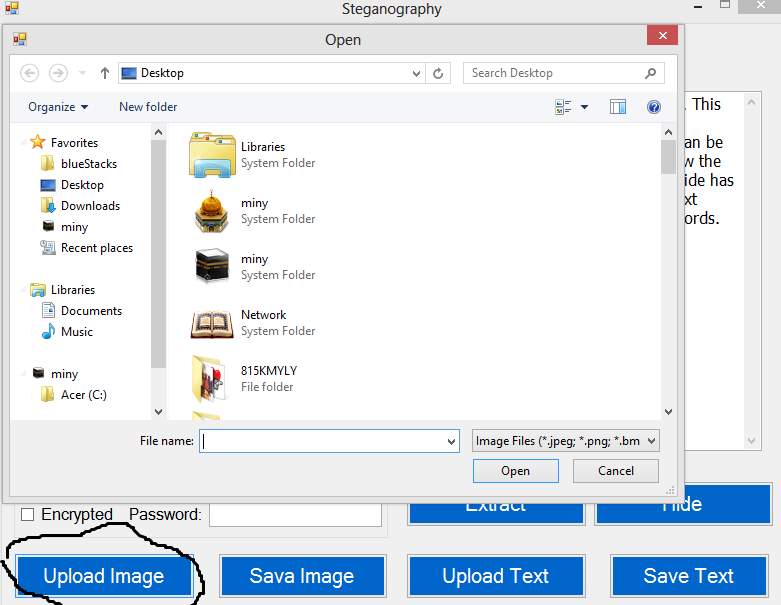
Figure 5.6: Locate Image to Upload
Upload an Image you will like to use, once the user clicked on the upload button the above page will be displayed which will allow selection from various storage in the user’s device, if you don’t want to use the default Image. Only bmp. Png and Jpeg files are allowed. After the upload the page below is displayed which shows the selected image and the successfully message.
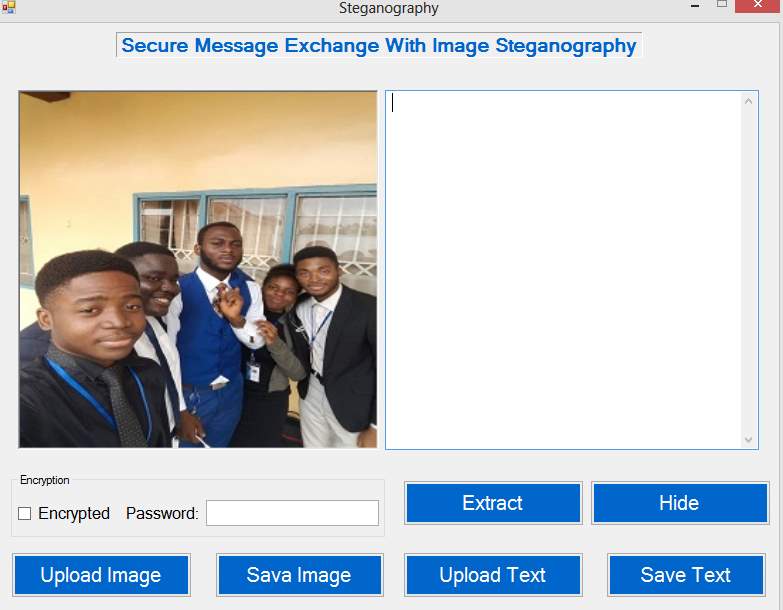
Figure 5.7: Image Successfully Uploaded
Upload Text: Instead of typing in the textbox, you can upload a text file (.txt only). The page below shows how an already typed and saved image can be uploaded into the system for hidden, this simplify the need of type in the text before hiding, with this function the user can be able to upload a .txt document.

Figure 5.8 Upload Text file
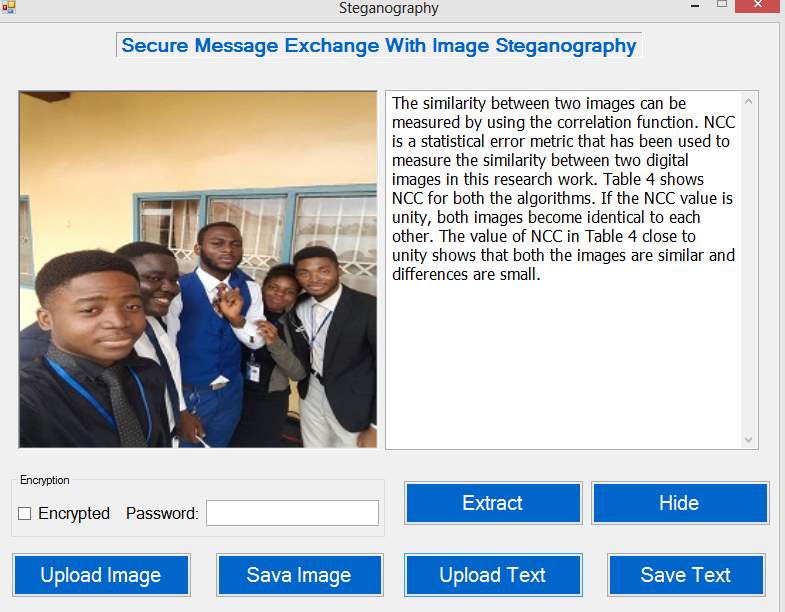
Figure 5.9 Text file Successfully Uploaded
After the saved .txt file has been uploaded successfully the system displayed the page above which will shows to the user the actual content of the document uploaded.

Figure 5.10 Password Length Error
5.6.3 Password selection
Password Length: We set the password length to minimum of 10, so it will show an error as shown below if password size is lower than expected. The encryption process will only be successful with correct selection of encryption password of maximum 10 characters length.
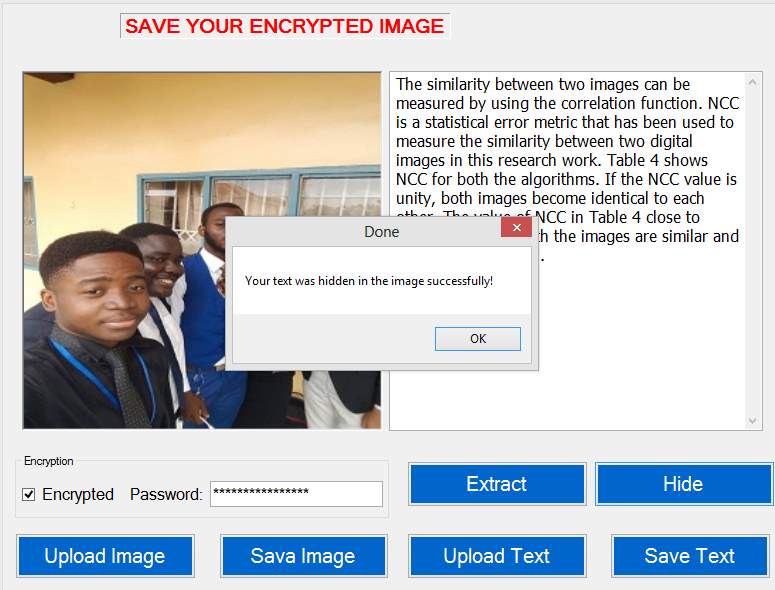
Figure 5.11 Successful Hiding
Successful Encryption: Set a password and click on Hide to encrypt your data in the file. After encryption safe your new image to your system and send to the receiver. The figure below shows the page that the system displayed to allow user save the encrypted image.
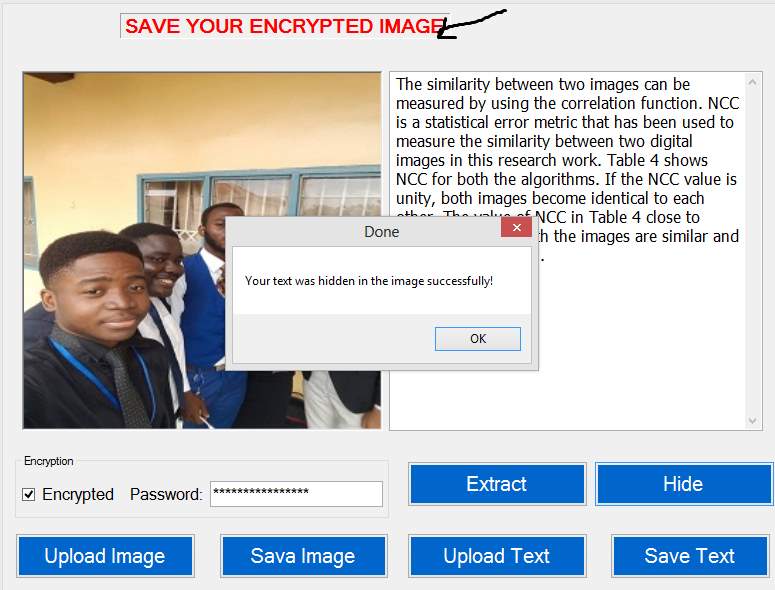
Figure 5.12 Prompt to save Image
5.6.4 Decryption
This section describes the process of extracting encrypted text from a file.
Step 1: Upload the Image
Step 2: Enter Password
The system made use of two approach in flagging wrong password. The first approach is yields rubbish text (YRT) if the password is wrong, we made use of that if the user fails to click on encrypted when is required or click when is not required. The second approach just by simply telling the user that the password is wrong. For successful encryption the decryption (that is the unhidden) password has to be the same with the Encryption password which will only be known by the user who by his own will select it during the encryption process as indicated above.
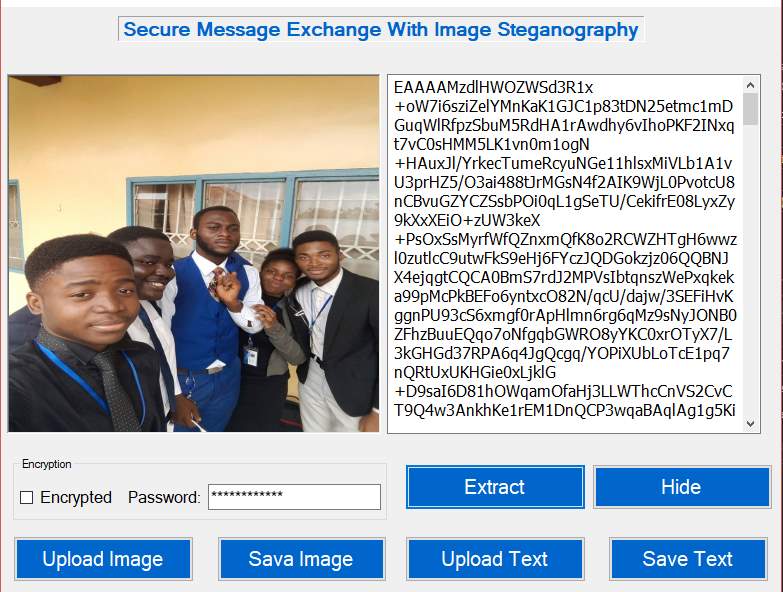
Figure 5.13 Rubbish Text Generation
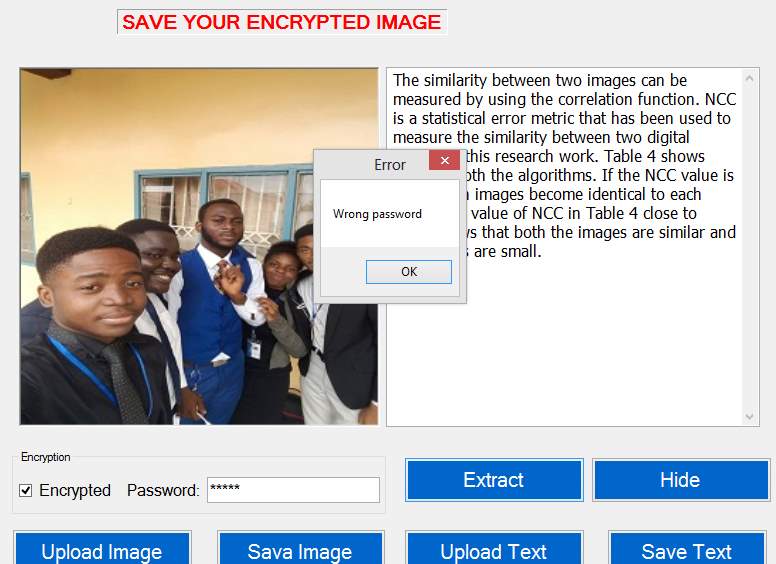
Figure 5.14 Wrong Password alert
Successful Decryption; The decrypted text can be saved on your system
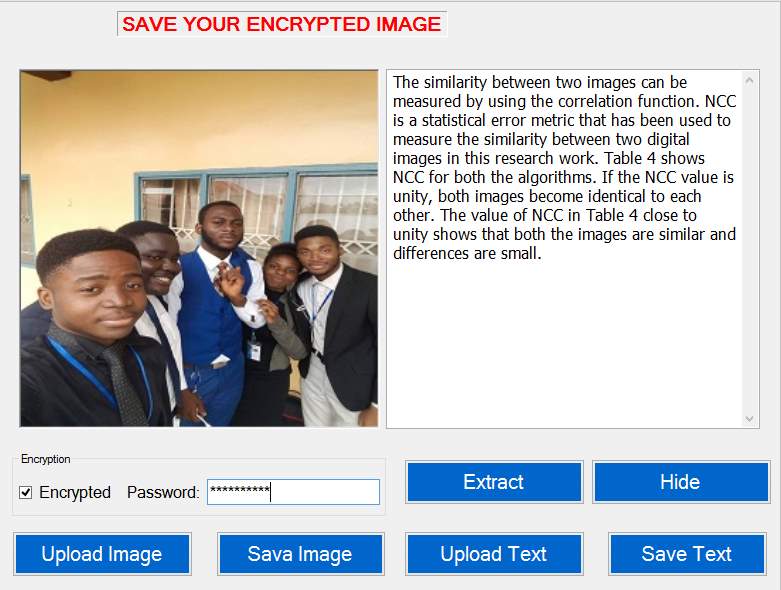
Figure 5.15 Successful Decryption.
5.7 Security Analysis
The system was design in such a way that the security is guaranteed in different ways as listed below to ensure that only the user with the password can access the confidential information:
- Password: User must set a password to protect the hiding data, so even when you are aware of the steganography you still can’t decrypt except you have the password, the encrypt password is ten variable length.
- Encrypted: User can encrypt their password to protect from strong attackers
- In distinguishability: You cannot differentiate between original Image and the image containing the data.
Figure 5.16 Original Image

Figure 5.17 Image with embedded text

Secured from Computer Experts: Even if the adversary is an expert that can open the encrypted image with text reading software such as the notepad, he/she won’t still be able to decrypt the image.
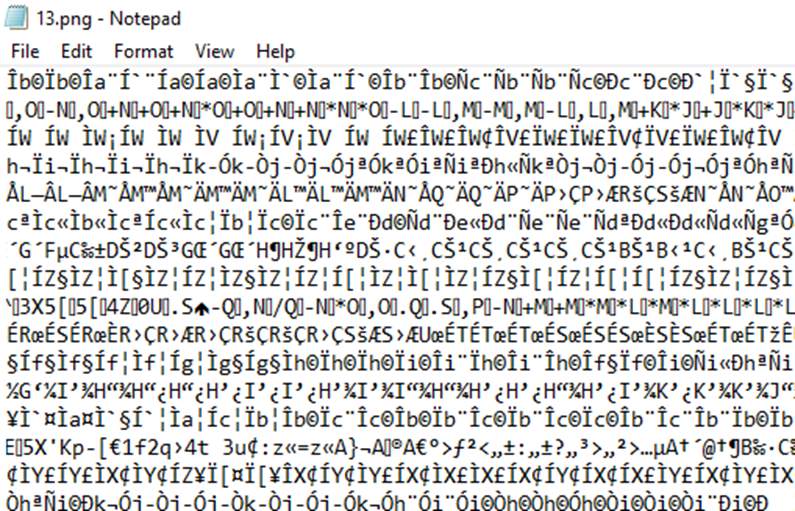
Figure 5.18 Note pad view of Encrypted Image
5.8 Results Discussion and Analysis
The experimental result deals with the final output of the system, while the analysis deals with thorough evaluation of the result to access the performance of the new developed system. The result gathered from the new method was compared with the results recorded by Muhamud et al. (2015). The system was evaluated using different methods which includes the analysis after a hiding text document of size 4kb (438 bytes) into six different images of varying quality but same dimension of (252×252). After the embedding the quality of the stego image was analysed using PNS, SNR, SME and RMSE method. Though there is no detectable physical difference between the two files this quality is supported by the report of Feng et al. (2014).
The results of the Image quality analysis were presented on table 5.1, the parameters analysed include the Peak-Signal-Noise ratio, Mean Square error (MSE), Root Mean Square Error (RMSE) and the Normalize-Cross-Correlations., the result were compared with the result recorded by Muhammad et al. (2015).
The average PNSR values recorded for the stego images is 51.1467 dB which is above the PSNR value of 40 decibel (dB) considered for a high quality steganography, since the PSNR value is above 30dB this represents that the steganography gives a higher quality of stego images and hence there will be no noticeable deformation in stego images which can be easily detectable. The PSNR values also is greater than 40.5017 recorded by Karim’ et al. (2011) and 35.3686 recorded by Akhter (2015) for sound in image steganography, this shows the effectiveness of the algorithm to produce high quality of stego images.
Similarly, the MSE values of the proposed algorithm are small as compared to the Karim et al. (2011) method. Furthermore, the RMSE scores of proposed method are smaller than the Karim et al. (2011) method. This means that the proposed algorithm provides promising results in terms of PSNR, confirming its better performance.
The smooth straight line graph of the PNSR values for the six image as shown in figure 5.1 shows no variation if compared with the result of Karim et al. (2011), which shows a large significant variation of the graph plotted, but it is relatively close to the report of Muhammad et al. (2015) sowing a graph close to a straight line. This lack of variation of the PNSR values shows that the new algorithm performs well for all types of images better than those in Karim et al. (2011) and Akhter (2015).
Table 5.1: Image Quality of the Stego_Images
| S/N | Images | PNSR (dB) | MSE | RMSE | |||
| New Method | Muhammad et al. (2015) | New Method | Muhammad et al. (2015) | New Method | Muhammad et al. (2015) | ||
| 1 | School | 51.0723 | 58.0648 | 0.4961 | 0.4487 | 0.7043 | 0.6698 |
| 2 | Indiana | 50.8740 | 58.0362 | 0.5193 | 0.4490 | 0.7206 | 0.6700 |
| 3 | Heart | 51.5415 | 58.0352 | 0.4453 | 0.4490 | 0.6673 | 0.6700 |
| 4 | Face | 51.1207 | 58. 3242 | 0.4810 | 0.4392 | 0.6935 | 0.6627 |
| 5 | Car | 50.9472 | 59.3242 | 0.5106 | 0.4319 | 0.7146 | 0.6627 |
| 6 | Box | 51.3246 | 60.3252 | 0.4681 | 0.4462 | 0.6841 | 0.6571 |
| Average | 51.1467 | 58.6580 | |||||
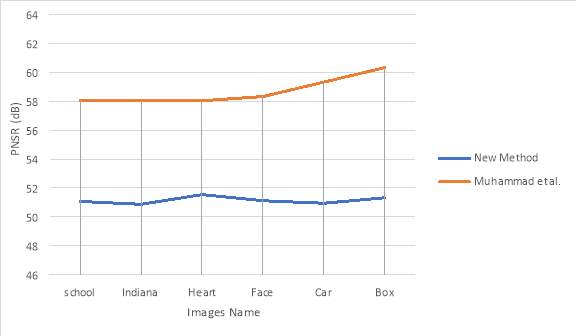
Figure 5.19: Images Quality
The correlation was used to measure the similarity between the two images (the cover and the stego-image), Near Cross Correlation was used to determine the correlation between the two images. The result shows average values of 0.9965, NCC is a statistical error metric used to measure the similarity between two digital images (Muhamud et al. 2015) If the NCC value is unity (1.0) this indicate that both images are identical. Thus the images are similar and the differences between them are small. The high near cross correlation recorded in this research shows that the proposed algorithm provide better results in terms of NCC also and verifies its effectiveness.
Table 5:2 Near Cross-Correlation of the Image (NCC)
| S/N | Images | NCC Value | |
| New Techniques | Muhammad et al. (2015) | ||
| 1 | School | 0.9909 | 0.9999 |
| 2 | Indiana | 0.9991 | 0.9999 |
| 3 | Heart | 0.9899 | 0.9993 |
| 4 | Face | 0.9999 | 0.9999 |
| 5 | Car | 0.9979 | 0.9995 |
| 6 | Box | 0.9995 | 0.9999 |
| Average | 0.9965 | 0.9997 | |
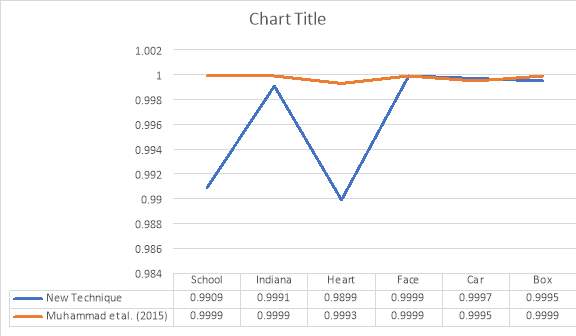
Figure 5.20: NCC Values of the Images
CHAPTER SIX
6.0 CONCLUSSION AND RECOMMENDATIONS
6.1 Summary
The various users of this system were presented with their different role played on images steganography, Algorithms and techniques comprising of the step by step process for the sending and receiving, hiding and unveiling of a text in an image as a secret message was presented, these techniques are developed as modifications to the existing algorithms for message hiding in an image using the Least Significant bit. The techniques and the algorithms provide the basic solution to unauthorized access who always find it fun and joyful event to access messages/information that are not meant for them where represented, the techniques start from the selection to the encryption and embedding of the secret message to the transfer and the unveiling of the secret message using the Least Significant Bit technique.
The process relies on two users the sender and the receiver who will be guided and supplied by the steganography software developed, the sender select cover file and the secret message and the key while the receiver will obtained the secret message using the secret key shared.
This thesis analysed several existing steganographic methods using different techniques of steganography to find out their strength and weaknesses theoretically in order to come up with more robust and effective technique of image hiding, secret message transfer and unveiling of secret message. The thesis come with a new algorithm after several analysis and researches in-depth in image hiding, the proposed algorithms uses Least Significant Bit to hide a secret message saved in text format and embedding capacity without degrading the quality of image. The algorithms are used to develop a new system for image hiding, and the system was tested and analysed experimentally, the results of the system testing are evaluated using some common statistics sets and was found to be very effective in both hiding and unveiling the secret message thus verified the effectiveness of the algorithms. Comparisons with the existing methods show that embedding capacity, visual quality and security of stego images are improved significantly.
Effective implementation of this software will take care of the basic requirements of the secret message communication because it is capable of providing easy and effective method for reliable and secret communication between two parties guided by a related to activities, With these, the objectives of the system design was achieved
Developing algorithm and testing the algorithm by developing a new system system application is not an easy task. It all started from the requirement gathering and passes through so many other stages before completion. Based on the benefits of this system and tremendous value it will add in secure communication between two entities, the below recommendation are to be considered;
It is recommended that the new system should be used with the necessary specifications of the system requirements and provision for an uninterrupted power supply should be made available throughout the hours of operation to the system been crashed.
There should also be basic computer knowledge for the users of the software.
It is recommended that the software scope should be included in the future work to include video as well as audio steganography.
In order to allow for future expansion, the system has been designed in such a way that will allow possible modification as it may deem necessary, whenever the idea arises.
REFERENCES
“Reference guide: Graphics Technical Options and Decisions”, http://www.devx.com/projectcool/Article/19997
Ahsan, K. & Kundur, D., (2002) “Practical Data hiding in TCP/IP”, Proceedings of the Workshop on Multimedia Security at ACM Multimedia, 2002
Akbas E. Ali (2010). “A New Text Steganography Method By Using Non-Printing Unicode Characters” (PDF). Eng. & Tech. Journal. 28.
Anderson, R.J. & Petitcolas, F.A.P., (1998) “On the limits of steganography”, IEEE Journal of selected Areas in Communications, May 1998
Ankit Gambhir and Sibaram Khara (2016), “Integrating RSA Cryptography & Audio Steganography”, IEEE ICCCA.
Anupa, Mondal, Shiladatiya Pujari, (2015): A Novel Approach of Image Based Steganography Using Pseudorandom Sequence Generator Function and DCT Coefficient’’ IJCNIS, Vol 17:3. pp 42-49. DOI: 10.5815/ijnics.2015.03.06.
Artz, D., (2001): “Digital Steganography: Hiding Data within Data”, IEEE Internet Computing Journal, June 2001
B. Ptzmann, Information hiding terminology. In Anderson [5], pp. 347-350, ISBN 3-540-61996-8, results of an informal plenary meeting and additional proposals.
BBC News, 2007. Hiding messages in plain sight. [Online] Available at: HYPERLINK http://news.bbc.co.uk/go/pr/fr/-/1/hi/technology/6361891.stm http://news.bbc.co.uk/go/pr/fr/- /1/hi/technology/6361891.stm . and Biology Society. Hong Kong, China, 1998. 29 Oct-1 Nov. pp.703-706.
Bender, W. et al., 2000. Applications for data hiding. IBM Systems Journal, 39(3&4), pp.547-68.
Bender, W., Gruhl, D., Morimoto, N. & Lu, A.(1996), “Techniques for data hiding”, IBM Systems Journal, Vol 35, 1996
Bin Li, Junhui He, Jiwu Huang, Yun Qing Shi. (2011) A Survey on Image Steganography and Steganalysis. Journal of Information Hiding and Multimedia Signal Processing, Vol. 2, pp. 142-172, April 2011.
Cachin, C., An Information-Theoratic Model for Steganography, in Proceedings of the Second International Workshop on Information Hiding, vol. 1525 of Lecture Notes in Computer Science, pp. 306-31, Springer, 1998.
Chandramouli, R., Kharrazi, M. & Memon, N., (2003): “Image steganography and steganalysis: Concepts and Practice”, Proceedings of the 2nd International Workshop on Digital Watermarking, October 2003
Chang, C.C., Hu, Y.S. & Lu, T.C., (2006): A watermarking-based image ownership and tampering authentication scheme. Pattern Recognition Letters, 27(5), pp.439-46.
Chincholkar A.A. and Urkude D.A (2012). Design and Implementation of Image Steganography. Journal of Signal and Image Processing, Volume 3, Issue 3, pp. 111-113, 2012.
Currie, D.L. & Irvine, C.E., (1996): “Surmounting the effects of lossy compression on Steganography”, 19th National Information Systems Security Conference, 1996
Dunbar, B., (2002): “Steganographic techniques and their use in an Open-Systems environment”, SANS Institute, January 2002
E.T. Allawi (2015): Secure communication based on encryption and LSB Steganography Voice. A thesis submitted to the department of computer science, Universy of Middle East in partial fulfilment of the requirements for the award of Masters in Computer Science.
F.A.P. Information hiding techniques for steganography and digital watermarking. Norwood: Artech House, INC.
Fang Y, Zeng K, Wang Z, Lin W, Fang Z, Lin C-W. (2014): Objective Quality Assessment for Image Retargeting Based on Structural Similarity. IEEE J Emerg Sel Topics Circuit Syst; 4(1):95-105.
Fatema Akhter (2013): A Novel Approach for Image Steganography in Spatial Domain. Global Journal of Computer Science and Technology Graphics & Vision. Volume 13: Online ISSN: 0975-4172 & Print ISSN: 0975-4350
Fridrich, Jessica; M. Goljan; D. Soukal (2004). “Searching for the Stego Key” (PDF). Proc. SPIE,Electronic Imaging, Security, Steganography, and Watermarking of Multimedia Contents VI.5306: 70–82. Retrieved 23 January 2014.
Frith, D., (2007). Steganography approaches, options, and implications. Network Security, 8, pp.4-7.
Frontline Defenders, 2003. Cryptology and Circumvention. Online Available at: HYPERLINK http://www.frontlinedefenders.org/manual/en/esecman/chapter3_4.html http://www.frontlinedefenders.org/manual/en/esecman/chapter3_4.html
G. Julius Caesar (2011), Cryptography. Security Engineering: A Guide to Building Dependable Distributed Systems (pp.1-42). New York, NY.
Handel, T. & Sandford, M., (1996): “Hiding data in the OSI network model”, Proceedings of the 1st International Workshop on Information Hiding, June 1996
Jain, A.K. & Uludag, U., 2002. Hiding fingerprint minutiae in images. In Proceedings of Workshop on Automatic Identification Advanced Technologies. New York, USA, 2002. 7- 8 June. Pp.97-102.
Jamil, T., (1999): “Steganography: The art of hiding information is plain sight”, IEEE Potentials, 18:01, 1999
Jessica Fridrich, Miroslav Goljan, and Rui Du,”Reliable (2010): Detection of LSB Steganography in Color and Grayscale Images”
Johnson, N.F. & Jajodia, S., (1998). Exploring steganography: Seeing the unseen. IEEE Computer, 31(2), pp.26-34.
Johnson, N.F. & Jajodia, S., (1998): “Exploring Steganography: Seeing the Unseen”, Computer Journal, February 1998
Johnson, N.F. & Jajodia, S., (1998): “Steganalysis of Images Created Using Current Steganography Software”, Proceedings of the 2nd Information Hiding Workshop, April 1998
K.S. Seethalakshmi, Usha. B, Sangeetha. K. N, (2016) “Security Enhancement in Image Steganography Using Neural Networks and Visual Cryptography”, IEEE Int. Conf. Computation System and Information Technology for Sustainable Solutions (CSITSS).
Kamaldeep Joshi, Rajkumar Yadav (2015), “A New LSB-S Image Steganography Method Blend with Cryptography for Secret Communication”, IEEE ICIIP.
Karim M. (2011): A New Approach for LSB Based Image Steganography Using Secret Key. In: 14th International Conference on Computer and Information Technology (ICCIT 2011). Dhaka, Bangladesh. p. 286-291.
Khan Farhan Rafat and Muhammad Sher, (2013): An Eccentric Scheme for Oblivious Communication. International Journal of Computer Science Issues (IJCSI). Volume 10, Issue 4, No. 2, July 2013, Pp. 89-96. www.ijcsi.org Impact Factor 0.242
Khan Muhammad, Jamil Ahmad, Muhammad Sajjad, Muhammad Zubair (2015): Secure Image Steganography Using Cryptography and Image Transposition. Manuscript received on 18th February 2015, reviewed and accepted on 22nd June 2015 as per publication policies of the NED University Journal of Research.
Kieser R., Reynison P., Mulligan T. J., (2005): Defination of Signal-to-Noise ratio and its critical role insplit-beam measurement. ICES Journal of Marine Science. Journal du Consel 62(1): 123-130.
Krenn, R., “Steganography and Steganalysis”, http://www.krenn.nl/univ/cry/steg/article.pdf
Krista Bennett, “Linguistic Steganography: Survey, Analysis, And Robustness Concerns For Hiding Information In Text”, Cerias Tech Report 2004-13, Center for Education and Research in Information Assurance and Security, Purdue University, West Lafayette, IN 47907-2086
Lee, Y.K. & Chen, L.H., (2000) “High capacity image steganographic model”, Visual Image Signal Processing, 147:03, June 2000.
Liu, P., Zhu, Z., Wang, H. & Yan, T., (2007): A novel image steganography using chaotic map and visual model. In International Conference on Intelligent Systems and Knowledge Engineering (ISKE 2007). Chengdu, China, 2007. Atlantis Press.
Lunn, Ken. (2003). Software Development with UML, New York: Palgrave Macmillan.
Marvel, L.M., Boncelet Jr., C.G. & Retter, C.,(1999) “Spread Spectrum Steganography”, IEEE Transactions on image processing, 8:08.
Marvel, L.M., Boncelet Jr., C.G. & Retter, C.,(1999): “Spread Spectrum Steganography”, IEEE Transactions on image processing, 8:08, 1999
Miaou, S., Hsu, C., Tsai, Y. & Chao, H., 2000. A secure data hiding technique with heterogeneous data-combining capability for electronic patient records. In Proceedings of the IEEE 22nd Annual EMBS International Conference. Chicago, USA, 2000. 23-28 July. Pp.280-283.
Moerland, T., (2009) “Steganography and Steganalysis”, Leiden Institute of Advanced Computing Science, www.liacs.nl/home/ tmoerl/privtech.pdf.
Moresh Mukhedkar, Prajkta Powar and Peter Gaikwad (2015), “Secure non-real-time image encryption algorithm development using cryptography & Steganography”, IEEE INDICON.
Nehru, Gunjan, and Puja Dhar. “A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach.” International Journal of Computer Science Issues (IJCSI) 9.1 (2012).
Nikhil Patel, Shweta Meena (2016), “LSB Based Image Steganography Using Dynamic Key Cryptography”, International Conference on Emerging Trends in Communication Technologies (ETCT).
Nirinjan, U.C. & Anand, D., 1998. Watermarking medical images with patient information. In
Osuolale, A. Festus (2017): Secure Data Transfer Over the Internet using Cryptosteganography, Internaational Journal of Scientifica & Engineering Reserach. Volume 8, ISSN 2229-5518
Owens, M., (2002): “A discussion of covert channels and steganography”, SANS Institute, 2002
Pahati, OJ (2001-11-29). “Confounding Carnivore: How to Protect Your Online Privacy”. AlterNet.Archived from the original on 2007-07-16. Retrieved 2008-09-02.
Petitcolas, F.A.P., 2000. Introduction to information hiding. In Katzenbeisser, S. & Petitcolas,
Petitcolas, FAP; Anderson RJ; Kuhn MG (1999). “Information Hiding: A survey” (pdf). Proceedings of the IEEE (special issue). 87 (7): 1062–78. doi:10.1109/5.771065. Retrieved 2008-09-02.
Polygraphiae (cf. p. 71f)” (in German). Digitale Sammlungen. Retrieved 2015-05-27.
Pooja Yadavi, Nishchol Mishra, Sanjeev Sharma, “A Secure Video Steganography with Encryption Based on LSB Technique.” 2013 IEEE International Conference on Computational Intelligence and Computing Research. IEEE, 2013.
Proceedings of the 20th Annual International Conference of the IEEE Engineering in Medicine
Provos, N. & Honeyman, P., (2003) “Hide and Seek: An introduction to steganography”, IEEE Security and Privacy Journal, 2003.
R.Poornima1 and R.J.Iswarya2 (2014): An overview of digital image Steganography, International Journal of Computer Science & Engineering Survey (IJCSES) Vol.4, pg 23-31 DOI: 10.5121/ijcses.
Rad R.M., Attar A., Atani R.E (2013): A comprehensive Layer nased encryption method for visual dat. International Journal of Signal Processing, Image Processing and Pattern Reccognition. 6(1): 37-48.
Rainer Böhme (2010). Advanced Statistical Steganalysis information security and cryptography. New York, NY: Springer. DOI: 10.1007/978-3-642-14313-7.
Ria Das, Indrajit Das (2016), “Secure Data Transfer in IoT environment: adopting both Cryptography and Steganography techniques”, IEEE Int. Conf. on Research in Computational Intelligence and Communication Networks (ICRCICN).
Rini Indrayani, Hanung Adi Nugroho, Risanuri Hidayat, Irfan Pratama (2016), “Increasing the Security of MP3 Steganography Using AES Encryption and MD5 Hash Function”, International Conference on Science and Technology-Computer (ICST), IEEE.
Sadaf Bukhari, Muhammad Shoaib Arif, M.R. Anjum, and Samia Dilbar, (2016) “Enhancing security of images by Steganography and Cryptography techniques”, IEEE Int. Conf. Innovative Computing Technology (INTECH).
Silman, J., (2001): “Steganography and Steganalysis: An Overview”, SANS Institute, 2001
Simmons, G., (1983): “The prisoners problem and the subliminal channel”, CRYPTO, 1983
Stefan Katzenbeisser and Fabien A.P. Petitcolas (2000): Introduction to information hiding. In Information Hiding: Techniques for Steganography and Digital Watermarking, Artech House. 1-14, Boston.
T. Morkel, J.H.P. Eloff, M.S. Olivier (2007): An Overview of Image Steganography. Information and Computer Security Architecture (ICSA) Research Group. Department of Computer Science. University of Pretoria, 0002, Pretoria, South Africa
T. Y. Liu and W. H. Tsai,(2007) “A New Steganographic Method for Data Hiding in Microsoft Word Documents by a Change Tracking Technique,” in IEEE Transactions on Information Forensics and Security,vol. 2, no. 1, pp. 24-30, March 2007. doi: 10.1109/TIFS.2006.890310
The Oxford English dictionary: being a corrected re-issue, Clarendon Press, Oxford, 1933.
University of Pretoria, 0002, Pretoria, South AfricaNeil F. Johnson, Sushil Jajodia (1998):”Exploring Steganography: Seeing the Unseen”, IEEE 0018-9162/98.
Venkatraman, S., Abraham, A. & Paprzycki, M., (2004): “Significance of Steganography on Data Security”, Proceedings of the International Conference on Information Technology: Coding and Computing,
Vipul Shanna and Madhusudan (2015): Two New Approaches for Image Steganography using Cryptography. IEEE Int. Conf. Image Information Processing.
Wang Z., Bovik A. C., (2009): Meaan Square Error. Love it or leave it?. A new look at signial fidelity measures. Signal Processing Magazine. IEEE 26(1); 98-117.
Wang, H & Wang, S, (2004): “Cyber warfare: Steganography vs. Steganalysis”, Communications of the ACM, 47:10, October 2004
Westfeld and A. Pfitzmann (1999). Attacks on steganographic systems, in Proc. 3rd Int. Workshop on Information Hiding, vol. 1768, pp.61–76, 1999.
Zarrelli, Natalie,
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Security"
Security relates to the protection and safety provided to people, objects or organisations. Security can take many forms, though some of the most common forms of security are security guards, security measures, and security software.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




