Efficiency of Developing an Automated Bluetooth Employee Payroll Application
Info: 23459 words (94 pages) Dissertation
Published: 11th Dec 2019
Investigating The Efficiency Of Developing An Automated Bluetooth Employee Payroll Application
Abstract
The importance and prevalence of Bluetooth technology combined with the increasing trends in the development of RF communication protocol advancements is the basic premise and stimulus of this discourse. This discourse will focus on and analyze the overall impact of an automated Bluetooth payroll system if implemented within an organisation to monitor employee clock-in and clock-out schedules. This is a crucial consideration when Bluetooth dependent systems are installed as although they bring many benefits, they also bring certain drawbacks, as well as introduce security concerns and vulnerabilities to the organisation and system architecture. The discourse explores how an automated Bluetooth payroll system would be implemented within an organisation to automate the process of calculating, processing and reporting on employee salaries based on the total time spent clocked in into the system each day the come to work. It also highlights some functional and non-functional requirements of such as system and proceeds to provide an implementation showing the scope and critical features that the system would require to function properly within an organisational setting.
Table of Contents
2.0 Chapter 2: Literature Review
2.3 Advantages of Automated Attendance Tracking
2.4 Security Challenges and Protocols that are Associated with Automated Payroll Systems
2.4.1 Secure Network Protocols
2.5 Security Intrusion detection and prevention protocols for automated payroll systems
2.5 1 Reducing Knowledge Transfer risks in automated payroll systems by using Bluetooth
2.6 Similar Products and Systems
2.6.1 Payroll Automation via Time Sheets
2.6.4 Advantages of the proposed Bluetooth based mobile application over GPS
2.7 Bluetooth Connectivity and Network Performance
2.7.1 Network Performance Indicators
2.7.2 Selection of measurements
3.0 Chapter 3: Research and Methodology
3.1.1 What are project methodologies?
3.2 Quantitative and Qualitative Research
4.0 Chapter 4: Ethical, Legal and Social Considerations
4.0.1 Information rights and obligations
4.0.2 Property rights and obligations
4.0.3 Accountability and control.
5.1 Non-Functional Requirements
7.0 Chapter 7: Prototype and Technology Review
7.1 Web application GUI Implementation
7.1.2 Authentication Level: Login Failure
7.1.3 Successful Login: Redirected To Main Dashboard Page
7.1.4 Different Views of Employees
7.1.6 Manual Clock IN Employees
7.1.7 Add New Device via Mac Address
7.2 Android App GUI Implementation
7.2.1 Employee Registration /Create Account
7.2.3 Employee Not Clocked IN/ Session Inactive
7.2.4 Employee Clocked IN/ Session Active
7.2.5 Employee Logs/ Clock INs
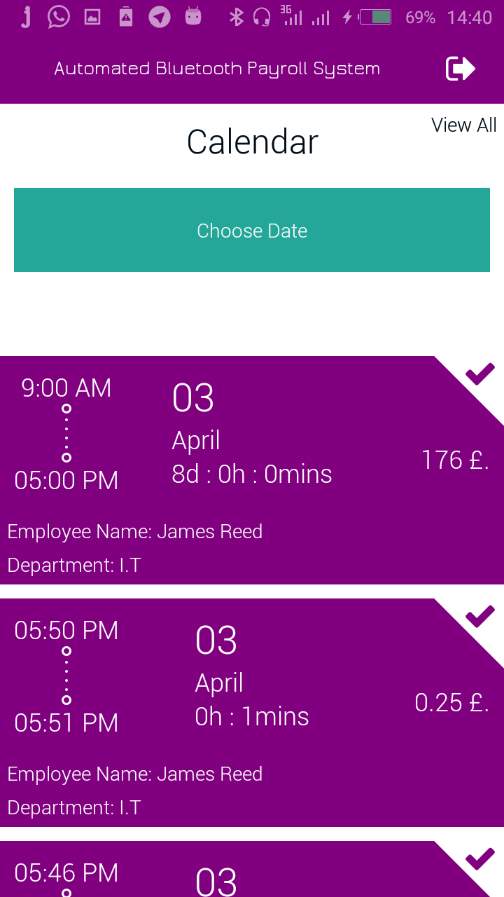
7.2.5 Admin Employee Schedule/ Clock IN Logs
7.4 System Breakdown, Code and File Linkages
7.4.2 Database Functions/ Queries
7.5 Android Mobile Application (App)
7.5.2 Mobile Service and ServiceHandler
7.5.4 Key Libraries and imported classes
7.5.6 Bluetooth Search and Broadcast
8.2.1 Black Box Test Case 1- Admin Login
8.3.1 Keyboard Interactivity Test
8.3.2 High Contrast Color Test
9.0 Chapter 9: Project Evaluation and Reflection
11.1 Appendix A — Bluetooth Communication
11.2 Appendix B- Project Methodologies?
1. Chapter 1: Introduction
1.1 Background
The importance and prevalence of Bluetooth technology combined with the increasing trends in the development of RF communication protocol advancements are the basic premise and stimulus of this discourse. This discourse will focus on and analyse the overall impact of an automated Bluetooth payroll system if implemented within an organisation to monitor employee clock-in and clock-out schedules. This is a crucial consideration when Bluetooth dependent systems are installed as although they bring many benefits, they also bring certain drawbacks, as well as introduce security concerns and vulnerabilities to the organisation and system architecture. For example, the fact that Bluetooth devices can operate at with peer-to-peer communication, this may introduce some security risks i.e. a ‘man-in-the-middle’ attack or even packet sniffing. Subsequently, if the present organisation’s hardware is inadequate, services running that are reliant on the Bluetooth installation (e.g. web services, server resources) may suffer or possibly cease as a result. Of course, to any businesses, this would be unacceptable, though a real possibility if the impact of the automated Bluetooth payroll system is not analysed thoroughly before implementation.
To accomplish this, the discourse will be structured in a number of different stages. The first of which will be in-depth research into the primary aspects of Bluetooth and RF communication technology, as well as discussing available project design methodologies to enable successful completion of the project. This research will provide a large body of knowledge that will be drawn on when the discourse progresses to the implementation stage and should provide a solid and reliable foundation to design and build the implementation system and application.
Following this, the discourse will move on to its testing and implementation phase where an automated Bluetooth payroll system will be developed and, using a number of justified indicators, the use of the system will be assessed. During this period, a test plan will be created, implemented, and the resulting data will be documented and analysed. To supplement testing, the quality and usability of the system will be tested using other fundamental indicators to ensure the system functions as expected and meets the requirements specified.
The next subsection will discuss the different stages and project aims in greater detail.
1.2 Aims and Objectives
To tackle the issues raised in the Background, this subsection will outline a number of initial aims and objectives for the discourse. These objectives are designed to ensure that the individual tasks within the discourse will be sufficient to produce an accurate and educated response to the core issues raised. The key aim of the project is to design, develop and implement a mobile application and web-based backend for an automated Bluetooth payroll system. The key deliverables for the project will be an Android-based mobile App and a Web Dashboard that shall work together in real-time to automate employee clocking and payroll calculation based on the time spent at work.
1.2.1 Key features:
- Android Application
-Employee and Admin Login
-Employee Registration
-Employee reset password with email notification
-Clock-In via Bluetooth
-Clock-Out via Bluetooth
-Viewing of Clocking Logs
-Offline and Online Sync of Logs
-Viewing of employees and logs based on calendar date
- Web Backend
-Admin Login
-Admin Registration
-Employee Registration
-Deleting Employees
-Changing Employee Salaries
-Making Payments to Employees
-Manual Clocking
-Adding Clocking Devices based on Bluetooth MAC Address
-Deleting Clocking Devices
-Viewing Employee Logs and due salaries
1.2.2 Objectives
The first main objective is to research, compare and analyse a broad variety of Project Design Methods that are applicable for building such a platform. These methods are important to the overall success of the project as they will provide its basic structure, and assist in pulling together all the different elements into a cohesive and successful project.
The second objective will be to investigate the strengths and weaknesses of Bluetooth and RF communication technologies. This will involve analysing and comparing both of their architectures, technologies and components, and subsequently, assess the need for using Bluetooth as the implementation channel for an automated payroll system. Further, in-depth research will be completed on strictly RF communication protocol based processes that Bluetooth is known to implement, for example, bonding and paring.
To complement this research, a summary of computer networking in general will also be discussed, including topologies, components, protocols and vulnerabilities. This should help to enhance overall awareness of how networks operate, their problems, and ultimately understand how Bluetooth can be integrated within the organisational structure.
The next primary objective is to design a testing plan that will be used when the automated payroll Bluetooth system is implemented. This is a very important objective as it will outline how the system will be tested and is essential to providing an accurate response to the overall project aim. Some of the primary performance indicators (in addition to others decided upon at this stage) that will be used are whether the features specified above are functional.
Based on the previous objective, the next will be to implement the automated Bluetooth payroll system and carry out extensive and varied testing. Providing the testing plan created is suitable, the test should be able to accurately demonstrate to what extent the mobile application can help enhance automation of payroll services within the organisation with regards to employee clock-ins and clock-outs. This will provide the basis for answering the key research question as specified below.
The final main objective will be to interpret and evaluate all of the test data and, attempt to bring together the knowledge gained from both the primary and secondary areas of research. As a result of this, the answer to how Bluetooth technology and RF communication protocols can be used within an organisation to automate payroll services should become apparent.
1.3Deliverables and Outcomes
In addition to outlining the main objectives, this discourse looks to accomplish, a number of deliverables or outcomes which will also be established from the offset. The majority of these deliverables are based on the objectives and what they will actually produce; however, there will also be additional deliverables that relate to the management of the project.
The first deliverable will be a comprehensive research dissertation, encompassing project design methodologies and in-depth research on existing RF communication technology. This will particularly focus on Bluetooth, though touching on the traditional also, resulting in a thorough exploration of Bluetooth systems.
The testing phase of the project will involve a number of key deliverables, including a robust, justified and documented testing plan to enable the most accurate results possible. Documenting the resulting test data after implementation (in addition to producing graphs) will form another key deliverable. Subsequently, this data will be evaluated, and a conclusive report will be produced with the viability of implementing an automated Bluetooth payroll system as its focal point.
A final evaluation pertaining to the overall success of the project will be produced after the testing and analysis phase has completed. This evaluation will contain a critical examination of the project as a whole, and attempt to determine how successful the project was. This will include limitations of the project, ways in which it could have been improved, and what steps would be taken if the project were to be repeated.
1.4 Research Question
This discourse is going to explore attendance tracking systems, and the main research will focus on automated attendance tracking systems for payroll. The key research question is to investigate whether a mobile based application can help increase the efficiency of a clocking system through the use of Bluetooth technology rather than the already done before GPS versions. Thus meaning, there will be intense care to detail on every aspect of positives & negatives compared to GPS and other communication methods.
2.0 Chapter 2: Literature Review
2.1 Introduction
The brisk development of new technology has essentially changed the nature of work and increased the complexity systems within many industries. The world becomes more and more complicated, and these complex systems require a tight combination between technical and human subsystems (Goetsch & Davis, 2013). In this sense, the failure of either subsystem can often cause a failure of the entire system. Moreover, cataclysmic breakdowns of these systems create serious threats, not only for those within the organisation but also surrounding public. Concurrently, timing schedules needed for time-based payroll modules within the workplaces have also become more intricate and in some cases more urgent.
In this view, most timing schedules are said to be the very heart of organisations which rely on a time-based payroll system. Organisations of this kind often rely on an attendance tracking and both Goetsch and Davis (2013) agree that the cornerstone of processing time-based payrolls is efficiency and accuracy in timekeeping. In the face of new mandates, it is believed that attendance tracking can play a vital role in helping organisations respond to the many challenges that normal payroll systems may face. According to Soewito et all. (2015, p.208), attendance tracking also has an important role in reducing labour costs within the organisation if there is efficient time keeping. The execution of effective timekeeping in the organisation surroundings had been recognised as essential. Generally, this will protect the employers and the employees from payment conflicts that often arise in scenarios where the there is a laxity in how timekeeping is handled, especially when employee payrolls are calculated based on the clock in and clock out times.
2.3 Advantages of Automated Attendance Tracking
First and foremost is cost visibility. Automated time tracking helps make costs visible and trackable by providing some metric of measure. This is very important for an organisation since they can be able to view how labour costs stack up against the organisation’s expenditure and how the costs can be reduced to increase revenue. The second importance suggested by Moniz and Jong (2014) is billing automation. Referencing secondary research conducted by Rapp and Bachrach (2013), Moniz and Jong (2014) found that organisations could lower costs by using time tracking and attendance tracking measures to automate invoicing and billing. The organisation can integrate systems that automate billing and invoicing of employees based on auto generated timesheets, and this can help reduce labour costs by directly streamlining the payroll process for the organisation’s employees. Finally, Moniz and Jong (2014) suggest business intelligence as the third advantage that automated time tracking can offer an organisation. By knowing and keeping track of employee clock-in and clock-out times as they work on various tasks or projects, the information derived can be used to predict resource usage and even help dictate budgeting for future similar projects (Krishnan & Narayanswamy, 2015).
Figure 1 Shows an Automated Timesheet Report Process Flow
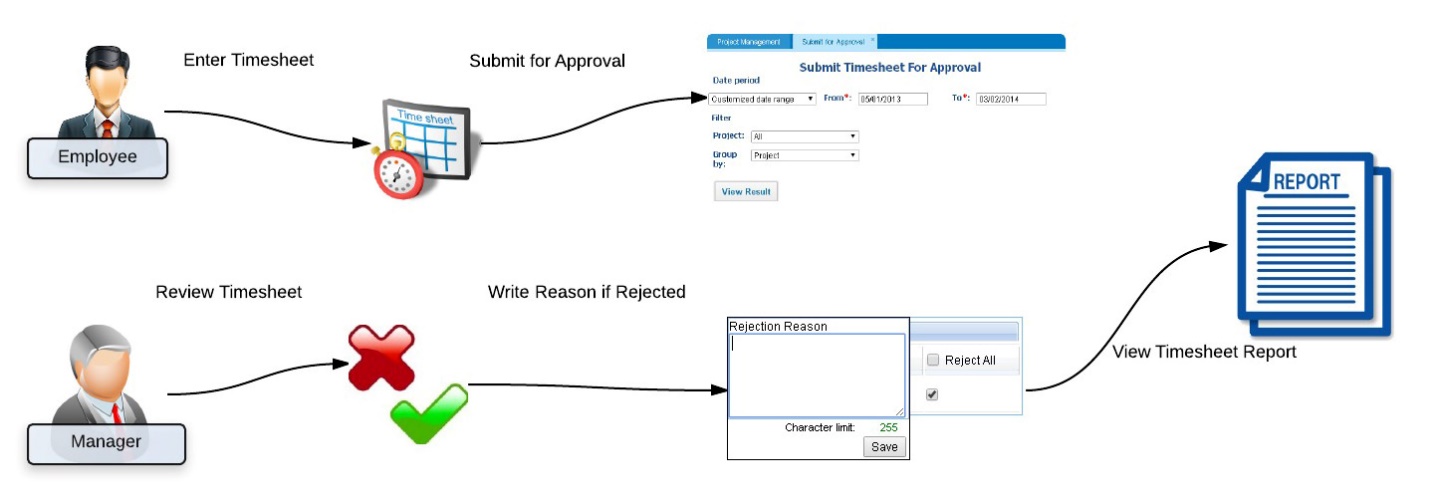
Source: https://www.kpi.com
2.3.1 Automated Job Costing
According to Duparc et all. (2013), an automated system for tracking employee time attendance can be very helpful in creating a workforce that is unified and an environment that is more likely to accommodate dynamic schedules, different employees working different shifts and can also help enhance overtime cost tracking. Being able to definitively cost employee working hours can help supervisors have access to real-time department expenditure costs based on hours worked and provide insights into employee performance. Molnár et all. (2014) Also, agree that proper automated job costing techniques can help create a culture of self-dependency within an organisation and foster employee job satisfaction especially when designing an adaptive workflow management system. They agree that automated job costing not only provides a set of techniques for calculating employee wages, routines and overall performance but it must be capable of interceding between ‘best practise’, norms of conduct and good order and at the same time create an organisational environment that relies on effective time management. Trkman (2010) further considers that it is an individual and group values, attitudes, competencies and patterns of behaviour that verified the commitment to, and the manner and proficiency of, an organisation’s time management culture. Trkman (2010) also stressed that an organisation with effective job costing techniques is categorised by a positive time management culture that is established on mutual trust, by shared perceptions of the importance of time management and by confidence in the efficiency of job costing techniques.
2.4 Security Challenges and Protocols that are Associated with Automated Payroll Systems
In Computer Security, Rozenberger (2005) seeks to bring out security aspects of networks and protocols that may arise from companies integrating automated payroll services. In the introduction, he recognises the dire need to embrace security measures for such systems since today’s world is primarily founded on the internet and networking on a local and global scale. The relevance of computer security when working with automated payroll systems can, therefore, not be underestimated. He continues to note that hacking has become the 21st-century internet and networking vice. Hacking that results from access through illegal and non-verified outsourcing services is responsible for crimes such as sabotage, industrial espionage, among other forms of white collar crimes and can cripple and organisation, if it’s payroll systems, are comprised. There is also an alarming spread of viruses, trojan horses, worms, and other malicious programs that threaten the security and integrity of data and information held and shared across networks within an automated payroll system. Therefore, need to embrace security measure in protocols and networks is inevitable.
2.4.1 Secure Network Protocols
Secure Networking Protocols Portal is a tutorial presented by Koren (2011), a Dean at RAD University. In the tutorial, she seeks to conceptualise some of the protocols that support communication over the internet since the communication is always under threat from intrusion, sabotage and other threats that affect computers networked by the Internet once automated payroll services are outsourced from non-verified vendors.
Koren (2011) gives a deeper insight of protocols that ensure “privacy, authentication, data integrity, and non-repudiation” by information systems that deal with the sensitive nature of payroll automation. In a bid, to embrace and enforce the four aspects of data as noted by Koren (2011), the essence of cryptography is brought out. Koren notes that although some form of security of authentication mechanisms have no emphasis, cryptography is a fundamental necessity as far as security and integrity are concerned when building automated payroll systems that often deal with an organisation’s finances (Koren, 2011).
Figure 2 Shows the Secure Network Layer Protocol Tunnel
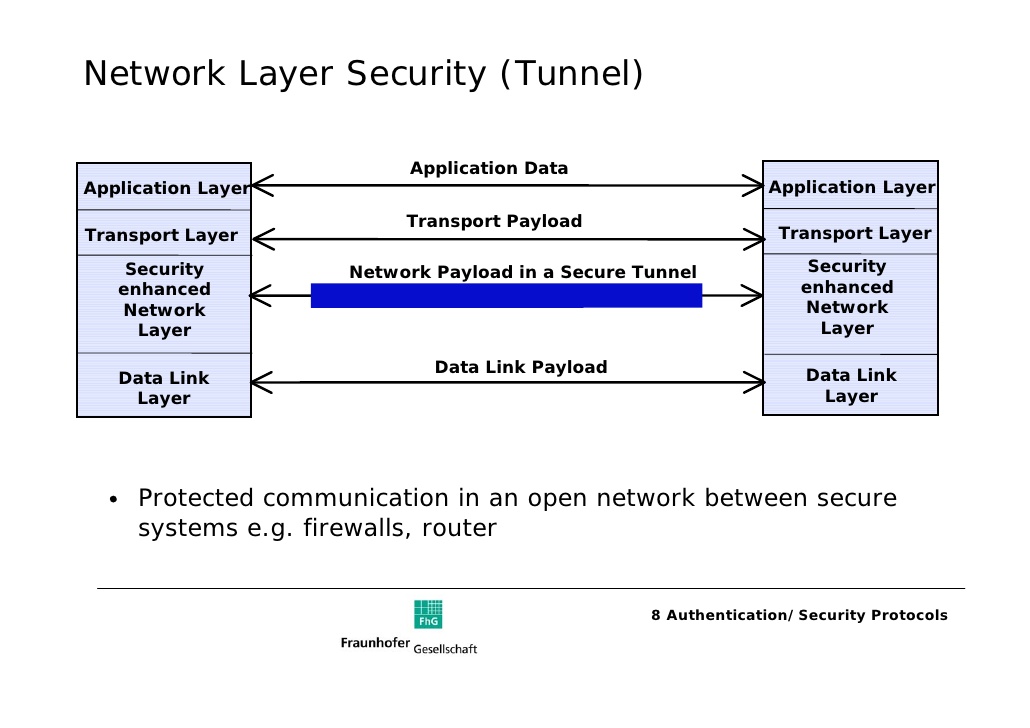
Source: Authentication Protocols- NLS
2.4.2 Cryptography
Cryptography, in simple terms, involves a mechanism of securing data while it is in transit over a network. The data is encrypted by the sender, converting it into gibberish to anyone who attempts to tap it i.e. through some form of a man-in-the-middle attack. Upon reception by the receiver, he/she uses a key that decrypts the information. Decryption converts the information to its original state. This technique ensures that data and information on transit are secure and maintains its integrity, especially when working with automated systems such as payroll and critical organisational financial services. Koren (2011) goes further to expound on the distribution of private and public keys alongside other security protocols that are geared towards data security and integrity in payroll systems. On a business context, such protocols and techniques are pivotal to boosting organisations’ confidence in the Internet and networks that the automated payroll system relies on. Overall, this enables business organisations to maximise the automated payroll system’s resources fully with minimal risks especially in cases where some financial services are integrated to the payroll system (Koren, 2011).
2.5 Security Intrusion Detection & Prevention Protocols For Automated Payroll Systems
Intrusion detection and prevention protocols (IDPs) combine both detection and prevention capabilities which are vital for automated payroll systems. As the name suggests, their primary role is identification and prevention of unauthorised access to the networks they monitor (Scarfone & Mell, 2007, p. 2-1). The network structure of the organisation requires the implementation of the inline sensor technique. Inline sensors run on the simple logic that all network traffic must pass through them for screening. They are similar to network firewalls in terms of data flow (Scarfone & Mell, 2007, p. 4-4).
2.5 1 Reducing Knowledge Transfer risks in automated payroll systems by using Bluetooth
One of the key strengths of the Bluetooth is its ability to reduce deployment and operation costs while offering comprehensive network security, which is vital in most automated payroll services (Mohamed et all. 2008). Bluetooth is capable of handling packets and requests of different devices hence its suitability in automating some processes within an organisation. Furthermore, Bluetooth is now part and parcel of most smartphones in the market as it comes pre-configured within the device from most manufacturers and also provides an accommodative user experience and addresses this need by integrating a simplified user interface for connectivity and paring purposes.
Figure 3: Shows the Bluetooth Security Manager Layer Architecture
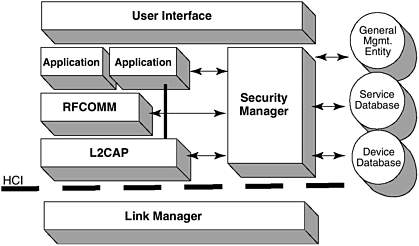
Source: http://flylib.com
2.6 Similar Products and Systems
One of the similar products to the proposed system is the traditional time sheets often used in most organisations to calculate employee payrolls. The difference with regards to usability is with automated timesheets the clock in data is often captured manually using a terminal and fed into the system. The drawback of this is it often leads to long queues if the number of employees or individuals coming into the workplace at a particular time is high which the case is often since most employees often arrive at the workplace at the same time.
Figure 8: shows an example of an Automated Time Sheet to Payroll Process

Source: http://www.tsci.us/images/TimeGuardian
2.6.1 Payroll Automation via Time Sheets
Heide (2009), described timesheets as documents that offer and an indication as to the number of hours that employees have worked and are often integral in the daily operations of both the accounts and human resources departments within an organisation. They are critical in helping calculate pay checks and were traditionally displayed in a tabular format but have since evolved into digital spreadsheets which offer a wider array of options (Aghaeepour et al, 2013, p.228-238). They can be traced to the 19th century when employers often used time cards to help calculate payrolls and assist in management accounting. Employees had timecards and whenever they arrived at the workplaces, special time clocks would be used to stamp their time card to indicate arrival at the workplace and log their check-in time. Likewise, in the evening, the time clock would stamp their timecards indicating their time of departure from the workplace. Heide (2013) further stipulates that time sheets should play a more definitive role within the organisation other than just logging arrival and departure times. His suggestion was the incorporation of timesheets into project tracking, management and even cost estimation.
Both Moniz and Jong (2014) assert that use of automated timesheets can help gauge employee performance and when integrated within a project context can act as an effective tool for measuring throughput in a bid to determine which tasks are problematic versus which are easily achievable. Although initially associated with factory workers, time sheets slowly found a place in blue collar jobs and after some time even found constant usage within corporate organisations. Moniz and Jong (2014) assert that today, automated time and attendance tracking can help an organisation with cost optimisation in certain key areas.
Linking this to the research question, the spread and increased access to smartphone technology, has made automation of attendance tracking more efficient with the integration of mobile applications into the attendance tracking eco-system. The biggest advantage this has provided is the flexibility and convenience it provides since there is no need for special hardware or implementation of expensive physical infrastructure.
In comparison to traditional timesheets, use of smartphones for conventional attendance tracking is being adopted in a number of institutions. There are more advantages offered by the use of smartphones in comparison to traditional attendance tracking, and another key advantage is cost reduction. Traditional time card based attendance tracking is quite costly in comparison to the use of smartphones. There is a need to purchase a number of physical time cards and devices for tracking employee attendance when working with traditional timesheets. Furthermore, it is also very costly to capture, transcribe, manage and evaluate the employee information from the timesheets in a fast and structured manner to enable efficient payroll processing. The use of smartphones has helped reduce this cost significantly since the biggest investment is only on the software implementation cost which is a one-off cost if the system is developed by the organisation or institution. Most of the employees have smartphones hence the hardware implications for implementing and automated payroll system would be minimal since all they would need to use is their normal smartphone device to interact with the system.
To further help answer the research question, modern day smartphones have a wide variety of features, and one of them is biometric support. Some smartphones allow for retinal scans or fingerprint reading, and this can be of great value if integrated into an attendance tracking systems. One of the disadvantages of traditional clocking system is that employees can easily clock each other in or out if there isn’t stringent supervision. With the help of biometric smartphone features for verification coupled by Bluetooth for automated clocking, it is possible to integrate and utilise these two key features within the system and hence significantly reduces the problem of false clock-ins and clock-outs through employee impersonation. This helps ensure that there is the integrity of data since smartphone biometrics are a reliable means of verification. Furthermore, there won’t be a need to invest heavily on expensive biometric scanning solutions since a smartphone with fingerprint reading capabilities can easily be used with the Android application to automate verification before clocking. This helps reduce set-up costs quite significantly.
2.6.2 Bluetooth Low Energy
The advent of Bluetooth Low Energy (BLE) is another important selling point as to why a smartphone and more so Bluetooth based automated attendance and payroll system is most effective. BLE is a form of Bluetooth standard protocols often used with beacons which are devices that run on coin-cell battery and can broadcast and respond to Bluetooth signals at very low frequencies hence can retain energy for a long time; in some cases two to even three years. This makes a huge difference in comparison to traditional GPS which relied on satellites to achieve somewhat similar results but at the costly expense of both data and power.
Most smartphones in production today come with the support of BLE and Google have been in the forefront of ensuring most Android devices come with BLE support. A key advantage that BLE provides is that with the help of triangulation algorithms, smartphones with BLE support can provide some level of accuracy in regards to indoor positioning which is one of the biggest drawbacks for GPS based systems or applications. An automated payroll system that relies on Bluetooth and more so Bluetooth Low Energy is, therefore, a very efficient solution since a high level of accuracy can be achieved by the system at minimal energy consumption.
2.6.3 Competitive Systems
There are quite a number of competitive systems that focus of attendance tracking for employees. Some popular ones are ClockShark, Bloomr and TimeCard. These provide functionality for mobile time tracking, and employees and supervisors can interact with the systems via an Android or IOS Mobile application. TimeCard, for example, have the TSheets app both for Apple and Android users that allows employees to clock-in or out, submit timesheets and PTOs, change tasks assigned to them all via GPS co-ordinates. With ClockShark and Bloomr, supervisors can clock-in our clock-out their employees in real-time by attaching GPS co-ordinates to their timesheets. When the supervisor has clocked in a specific crew, GPS tracking is turned on, and once they are clocked out by the supervisor, their GPS tracking is turned off. These systems and apps are directly reliant on GPS for verification of location before any clocking is done and this although reliable in some cases has proven to have some challenges in certain scenarios. One main scenario is that GPS is reliant on satellite communication and hence is often disrupted by poor weather conditions or in areas where there are network connectivity issues, the mobile apps and system do not function as expected.
Another issue with the application that is GPS reliant is the fact that GPS does not work very well indoors. This means that if an organisation requires employees to clock-in or out when they are within the premises, then this proves to be a challenge to use ClockShark, Bloomr or TimeCard (Tsheets). There is hence a need for a more efficient solution, and the proposed approach is to use Bluetooth-based technology as a substitute to GPS for attendance tracking. Bluetooth provides a number of advantages over using GPS for attendance tracking as highlighted below.
2.6.4 Advantages of the proposed Bluetooth-based mobile application over GPS
2.6.4.1 Offline & Online Support
Bluetooth technology does not require internet connectivity to operate since the signal and data is transmitted via radio frequencies unlike GPS tracking with requires a constant and stable internet connection. This means that the proposed mobile application can allow for offline syncing of data when just connected to Bluetooth for clocking and once connectivity is resolved can upload the data to the server without losing any location verification integrity. Through the use of Bluetooth, the mobile application to be built will give the employees or supervisors the flexibility of working even in areas with limited or no connectivity since the data can be cached once confirmation is made via Bluetooth that the employee is at the specific venue.
2.6.4.2 Indoor Usage
Another major advantage the Bluetooth-based mobile application has over the other three mentioned GPS based application is indoor usage. Bluetooth, unlike satellite, can comfortably be used indoors as long as the proximity radius of operation is maintained. This is highly adventitious in situations whereby there are different points of entry or exit within the organisation through which the employees can clock-in or out.
Even within the organisations building, the Bluetooth-based mobile application and system can work without disruption or interference of the signal as is the case with the other three GPS based mobile apps.
2.6.4.3 Battery Consumption
Another advantage that a Bluetooth-based mobile application and system would have over the GPS-based approach is in regards to battery consumption, especially with the current support for Bluetooth Low Energy Devices (BLE). GPS tracking drains battery powered for most smartphones at a very fast rate due to the constant signal connection and location updates sent to and from the satellite via the devices antennae. This makes costly with regards to battery consumption and most employees may shy away from such a solution and opt for a more optimum Bluetooth Low Energy solution that drains less power from their devices.
2.6.4.4 Remote Configuration
This is another advantage that a Bluetooth-based system would have over the three GPS based applications and similar systems. Bluetooth devices are identifiable by a unique address referred to as a MAC address which each device broadcasts. It is hence possible to add, configure and delete devices in your system remotely and at your convenience based on their MAC addresses. This makes convenient and possible to add a number of clocking devices, change or delete them as the organisation grows and the number of employees increases. This can be done remotely and hence help increase the efficiency and capacity of employee attendance tracking which would otherwise not be quite as easy if it was being done on a GPS based system.
2.7 Bluetooth Connectivity andNetwork Performance
The focus of this investigation is to investigate whether a mobile based application can help increase the efficiency of a clocking system through the use of Bluetooth technology. Therefore, in order to be able to accurately measure this, there may be a need to network performance once the system has been implemented and is supporting a number of Bluetooth connected devices. Thus, this section will outline a number of ways in which network performance can be measured once the Bluetooth based automated payroll system is rolled out.
2.7.1Network Performance Indicators
The issue of network performance is certainly not a clear-cut issue and the vast variety of methods and indicators available attests this view. Also, network performance can be looked at from the perspective of the end-user or network administrator; in many cases the two parties’ views on network performance will differ greatly. The end-users (employee’s) opinion, while it should not be dismissed out-of-hand, is generally not a good way to measure or gain an understanding of network performance. This is primarily because the end-user’s opinion lies in their perception of network speed, while the network administrators would lie in real and tangible figures.
Thus, it is from the latter’s viewpoint that this investigation should most likely proceed on.
As such, some of the primary indicators that can be used to determine network performance once a number of Bluetooth devices from various employees are connected are:
- Bandwidth
- Throughput
- Load/Network Utilisation
- Response Time
- Round Trip Time
- One-Way/Two-Way Delay
- Packet Loss
- Jitter
- Packet duplication/retransmission
- Packet re-ordering
These are individual measures that reflect the current performance of the network. However, they are somewhat limited by the fact that, when used alone, the “true” performance of the network may not necessarily become clear. As such, using a combination of indicators or creating a network baseline, are generally more popular and useful methods of accurately measuring performance.
2.7.2Selection of measurements
As a result of the previous section and, the objectives stated at the beginning of the investigation, the following indicators can be used during testing once the web backend and Android application are implemented:
- Throughput
- Round Trip Time
- Latency (delay)
- Packet loss
- Jitter
To expand on these choices further, throughput or bandwidth consumption can be taken in two instances. The first is the maximum throughput produced in a given time frame; the second is the average throughput in a given time frame. These two measurements can be implemented during the first phase of testing employee clock-in and clock-out. Maximum throughput is an important measurement to take especially when considering bandwidth provision. This is because the bandwidth of a link used to transport traffic within the network needs to be able to accommodate all of the bandwidth used by the employee’s devices connections to ensure no clocking data is lost or corrupted as it is transmitted to the server/backend. Average throughput is equally important as this essentially records the expected bandwidth (crucial for baselining purposes) and, the sustained amount of traffic that needs to be provided for.
These indicators should provide enough evidence to accurately identify the impact implementing a Bluetooth-based automated payroll system would have on the network. Statistics on throughput is relatively easy to acquire, and indicate the general condition of the network. Delay and packet loss are well-established gauges of the performance of real-time applications, and as this project involves traffic as clocking data is transported to the server, they are both vital. Further, though jitter was not initially named as a key indicator, it can be used as a vital statistic for real-time traffic. Round Trip Time (RTT) can also be used as it provides a good indication of the basic performance of the link. It is also easy to accurately measure via the use of the ping utility, which is built-in to Windows operating systems.
The indicators not chosen for this investigation were deemed not suitable, for example, packet re-ordering statistics would be problematic to acquire and may result in inaccurate or unrepresentative results especially since the system and mobile application supports both online and offline caching of data hence might give inconclusive statistics if there are network connectivity issues.
2.8 Conclusion
In conclusion, there is a need for automated payroll systems within organisations and a Bluetooth-based approach for automating timesheets and attendance tracking is a good implementation approach and can help enhance operational efficiency. Bayaki et all. (2008, pp 157-168), further supports this by asserting some of the advantages that Bluetooth has such as the ability to combine with other systems essential in sustaining a fully functional and efficient network in an organisation where some devices need to communicate. Bluetooth connectivity also incorporates intrusion prevention protocols (IPPs) that facilitate secure connections within the system, while enforcing stringent security measures (Bayaki et all, 2008 pp 157-168). This not only allows the free flow of data within the network, but also makes this particular IPP more suitable and cost-effective than typical ones and enhances security in networks and systems such as automated payrolls which are very sensitive.
3.0 Chapter 3: Research and Methodology
As per the objectives and deliverables outlined in the Project Proposal, this major section of secondary research will focus exploring and examining the diverse number of aspects associated with Bluetooth Communication Protocols for implementation with the Automated Payroll System.
3.1Project Methodologies
3.1.1What are project methodologies?
The definition of a Project Management Methodology is a highly debated matter, with many academics and professionals disagreeing on exactly what it is. For example, the Association for Project Management (APM, 2010) defines Project Management as “the process by which projects are defined, planned, monitored, controlled and delivered such that the agreed benefits are realised” (APM, 2010). Whereas Charvat (2003, p3), a project management consultant, defines it as “a set of guidelines or principles that can be tailored and applied to a specific situation.” So, while the APM focuses on the processes in managing projects, Charvat (2003) does not mention this, and instead focuses on principles. Despite this, in general, methodologies follow a similar structure of splitting projects up into clearly defined stages. Also, many methodologies contain common stages, for example, planning, implementation, testing and delivery.
3.1.2Methodologies
To ensure that this project is completed as successfully as possible, it will employ a combined methodology of Waterfall and Prince 2 model which are described briefly below.
3.1.2.1Waterfall
The Waterfall model is one of the earliest models and accordingly, embodies a traditional approach to project management used predominantly in software development. It uses a logical, sequential method in order to complete the project, and splits the project into a number of distinct phases. The model follows a stepwise approach where each phase is completed in-turn, and so the next phase will only be progressed to once the previous phase has finished. It is through this stage-by-stage style that the method gained the name “Waterfall”.
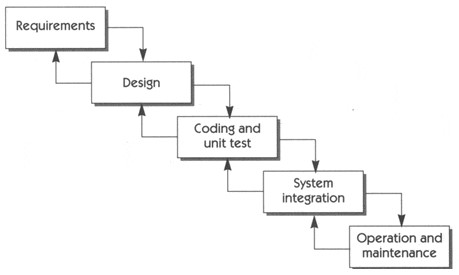
Fig 4: Waterfall model of software development (Leffingwell & Widrig, 1999, p134)
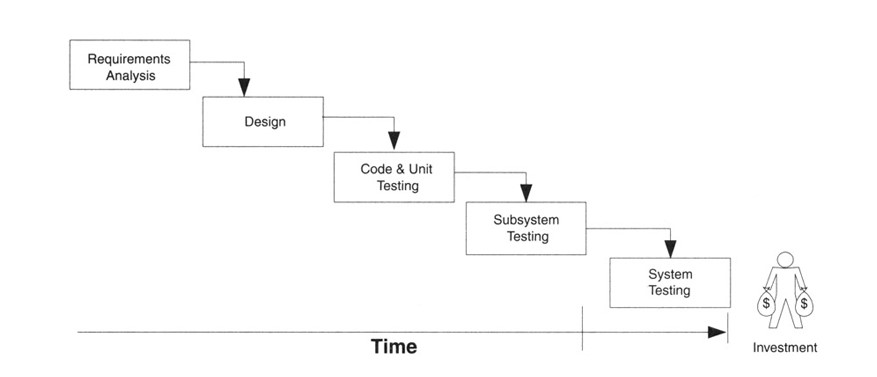
Fig 5: Waterfall development methodology (Charvat, 2003, p124)
Fig 1.2, which clearly shows that after the design stage the risk of project failure increases.
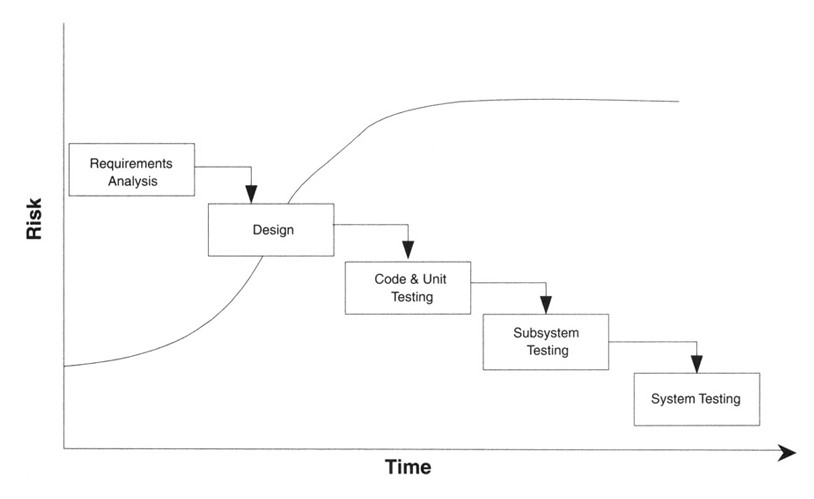
Fig 6: Waterfall development methodology (Charvat, 2003, p124)
3.1.2.2Prince2
Prince2, or Projects IN Controlled Environments, is a project management framework that aims to assist in the management, organisation and control of projects. Prince2 was originally intended for IT projects and is the official UK Government standard for IT project management (OGC, 2009b). However, due to its success and the fact that it is non-propriety, it has been adopted for use in many non-IT projects and is prevalent in both the public and private sector.
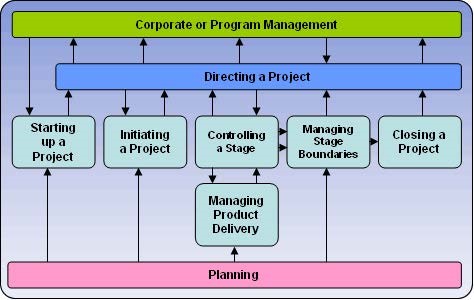
Fig 7: PRINCE2 Process Model (Prince2, 2010)
3.2Quantitative and Qualitative Research
Qualitative and Quantitative research are two of the main types of scientific research methods to be used in the project. The two methods focus on different areas and scope, with qualitative focusing on evidence of a subjective nature, while quantitative deals with the objective (Stake, 2010, p11). Further, qualitative research attempts to determine the reason or meaning behind an event by utilising people’s behaviour and opinions. Quantitative is essentially the classic Scientific model where all data and evidence is kept as unbiased as possible (Mack et al, 2005)
4.0 Chapter 4: Ethical, Legal and Social Considerations
Establishing and maintaining a high level of ethics is an important consideration when undertaking a discourse of this type. This is to ensure that the discourse maintains its integrity and remains credible. Hence, the following considerations will be made when carrying out this project:
- Read, understand and adhere to the British Computer Society (BCS) Code of Conduct (BCS, 2006) and Code of Good Practice (BCS, 2004)
- Comply with all sections of the Data Protection Act (Legislation.gov.uk, 1998) and The Privacy and Electronic Communications Regulations (Legislation.gov.uk, 2003)
- If any individuals external to the project participate at any stage during the project, their full consent will be obtained prior and their right to confidentiality will be made clear
- All external materials (quotes, text, diagrams) will be explicitly referenced using the Harvard Method
- Follow the universities research ethics approval process, and comply with its code of conduct for research guidelines.
- Any data obtained during the Implementation phase will not be tampered with or manipulated in any way and will comply with all legal considerations
Design, development and implementation of the proposed system shell be guided by the five moral Dimension of the information age as shown in the Figure below.
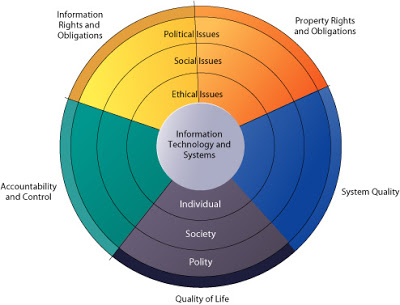
Fig. The Relationship between Ethical, Social, and Political Issues in an Information Society
4.0.1 Information rights and obligations
The proposed project and system will respect and uphold the rights of all actors involved and there is an obligation to protect both data and information of all actors who will interact with the system internally or externally. The system shall be structured in a manner such that the privacy of all actors is maintained at all times and it shall not be used to spy or gather direct or indirect intelligence with regards to the actions, habits, profiles or surveillance of the actors. The system shall also aim to provide data security and protection from any unauthorised access or manipulation.
4.0.2 Property rights and obligations
All the intellectual property of the system shall remain intact and this includes all materials, designs, resources and source code used in the development of the system and shall remain in the sole ownership of the developer. None of these materials shall be distributed or copied and shall be respected as pertains to copyright, patent law or trade secrets.
4.0.3 Accountability and control.
The system shall have mechanisms in place to ensure accountability and controls such as access roles and session based logins. Actors shall operate within their defined set of rights and permissions as specified with regards to the kind of operations they are permitted to perform and the kind of privileges they have within the system. The system shall also ensure that proper accountability is enforced and due process is followed when determining liability in case of any issue or concern. The system shall also be built with proper channels for ensuring there is minimal damage to the organisation and its actors in case of any system failure or breakdown. This shall also be resolved as quickly as possible to ensure all aspects of the system are always in control and managed in a responsible manner.
4.0.4 System quality.
The system shall be built to operate and function at optimum efficiency and with the highest standards of quality. This includes fixing and minimization of any system errors and bugs and proper testing shall be conducted to ensure the system operates at an acceptable standard of quality. The system shall also operate under certain rules and protocols to ensure high standards of quality both from hardware and software so as to deliver optimal performance.
4.0.5 Quality of Life
The system shall operate within the specified confines of boundaries, access and equity. The system shall operate with fairness to all actors and shall function without bias. The system shall also be used within its boundaries and shall have regulatory oversight to ensure it operates and functions within the specified scope. It shall not be used for computer abuse and other acts that may qualify as computer abuse such as SPAM or cyber-bullying. Furthermore, the system shall operate with minimal health risks and shall be designed to be as user-friendly as possible to avoid health impact issues such as Repetitive Stress Injury (RSI) or cause eye strain conditions such as Computer Vision Syndrome. Thus, ensuring there is no detriment to the quality of life of any of the actors interacting either internally or externally with the system.
5.0 Chapter 5: Requirements
The system to be developed is an automated Bluetooth payroll system that works on both Web and Mobile (Android Platform). Below is given criteria on how the system works.
5.1 Non-Functional Requirements
5.1.1 Performance/Time:
The system requires automatic clock-in of employees via Bluetooth and hence is very responsive.
Response time: This system offers much quicker response time than typical traditional applications since Bluetooth protocols are faster to broadcast and connect to.
5.1.2 Usability:
Usability is a crucial point in the system. As most users don’t have experience with a system like this, users will use the system in a way like a traditional punch-card systems used when clocking into work and clocking out in the evening. By use of a mobile phone application designed using Material Design Principles; the system makes its usability in terms of user experience and design much friendly.
5.1.3 Security
The system makes use of Roles to enhance security such that some User can only perform some operations under authorised permission. Some user groups can be configured so that they can never have certain permission. For example, the admin user group can be set to have permissions to register, edit salary and even delete employees from the system.
5.1.4 Modularity
The system has also been architectured in a modular manner applying the MVVM
(Model-View-View-Model) pattern of architecture. For instance, the connection files are separated and accessed via object-oriented class object i.e. DB_Connect.php (Connection Class) and DB_Functions_Insert.php (Function Class). Then the views class, i.e., app_employees.php (Contains the HTML Code that shows the retrieved employees as a list as retrieved from the database.)
5.2 Functional Requirements
Some functional requirements for the Automated Bluetooth Payroll System. Functional requirements are necessary for the implementation and proper functioning of a system while non-functional requirements are more non-specific for the operation of the system (Shoewu &Lawson, 2011).
5.2.1 Software Requirements
5.2.1.1 Android Operating System
An Android Operating System with a minimum OS Level 2.3 and above is needed. This is to enable installation and running of the Mobile Application Apk that the employees and admin can use to clock in and view logs.
5.2.1.2 PHP Server
A server running PHP 5.0 + is needed to effectively run the Web Application. The system utilises server-side processing and hence the server should be able to handle a number of multiple requests. The server can be configured using the DB_Config.php file by specifying its Host Name, Username, Password and Database to access.
5.2.1.3 MYSQL Database
The system backend is built on a MYSQL Database and utilises the MYSQLI Connection model. The connectivity has been split to a MVVM approach and hence is handled by the DB_Connect.php file which creates a connection object passed as a parameter to all MYSQLI queries.
5.2.2 Hardware Requirements
5.2.2.1 Android Device
An Android mobile device is required for installation and running of the mobile application. The device can run an Android operating system from as low as 2.3 but for optimal performance a 4.0 and above device is recommended.
5.2.2.2 Computer/P.C
The web application is accessible via the web and hence a computer is needed. The system is accessible via the web on any computer device hence has no constraint to either Windows or Linux system. It works across all P.C Operating Systems.
5.2.2.3 Modem/Router/ Internet Gateway Device
The system via web application is accessible via the internet hence a modem, router or gateway access device is needed. Since the server is hosted online, the system will have to be accessed via the internet and both the Android Device and Web Application communicate via an internet connection.
5.2.2.3 Language Requirements
These are the main languages used and some supporting/complimentary frameworks
5.2.2.3.1 Front End
- HTML – Web Application
- CSS –Web Application
- JQUERY – Web Application
- AJAX – Web Application
- Java – Android Application
5.2.2.3.1 Back End
- MYSQL- Database
- PHP – Server Processing Web Application
- PHP was chosen as the preferred server-side processing method instead of C# since it is very reliable with regards to performance and would also integrate well with the API for communication between the Web application and Android Application in real-time.
- PHP also offers a number of reliable server side processing functions and integrates with the MYSQL Backend Database by offering a number of connection methods that help streamline communication within the API Endpoints and Database when requests and queries are made.
6.0 Chapter 6: Design
6.1.0 Design Approach
The Automated Bluetooth Payroll System built uses a Model-View-View-Model approach on a standard Factory pattern and is structured using the 3 tier architecture. This means that the database tier is separate from the business component which is separate from the front end GUI. This enables for business operations abstraction.
This choice of design also enables the code framework to be less cluttered and structure less. Data Access Classes and API Facades are used to provide an interface for interaction between the three tiers.
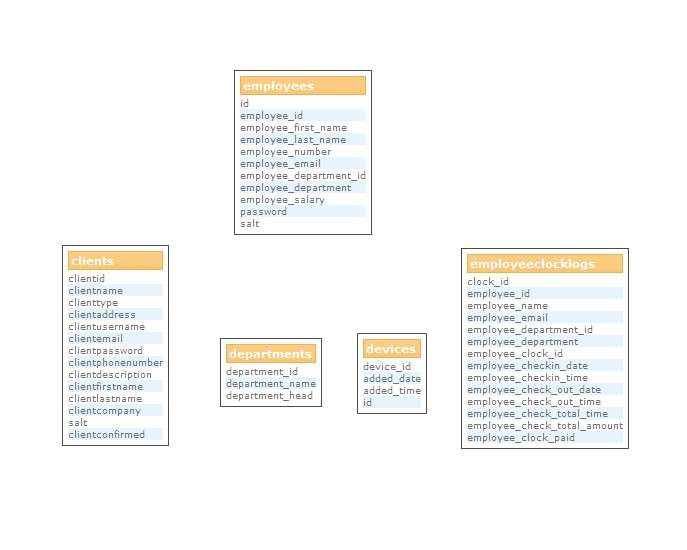
6.1.1 Database Design
The database design is directly mapped from the class diagram. The path attribute for employees, devices, clock logs and other tables is dependent on the class fields, because the fields for the database can be filled by the relations between variables and parameters passed through the admin GUI. An android based mobile application is provided to give information on various employees’ logs and clock in’s available.
Conceptual
I came up with the database design based on content I thought would be relevant in matching a payroll system.
Database Diagram Below:
Tables
Clients
Departments
Devices
EmployeeClockLogs
Employess
6.1.2 Diagrams
Below are some key diagrams which represent the system and how it works in terms of the underlying structure and relationships between classes and various user roles within the Automated Bluetooth Payroll System.
6.1.2.1 Class Diagram
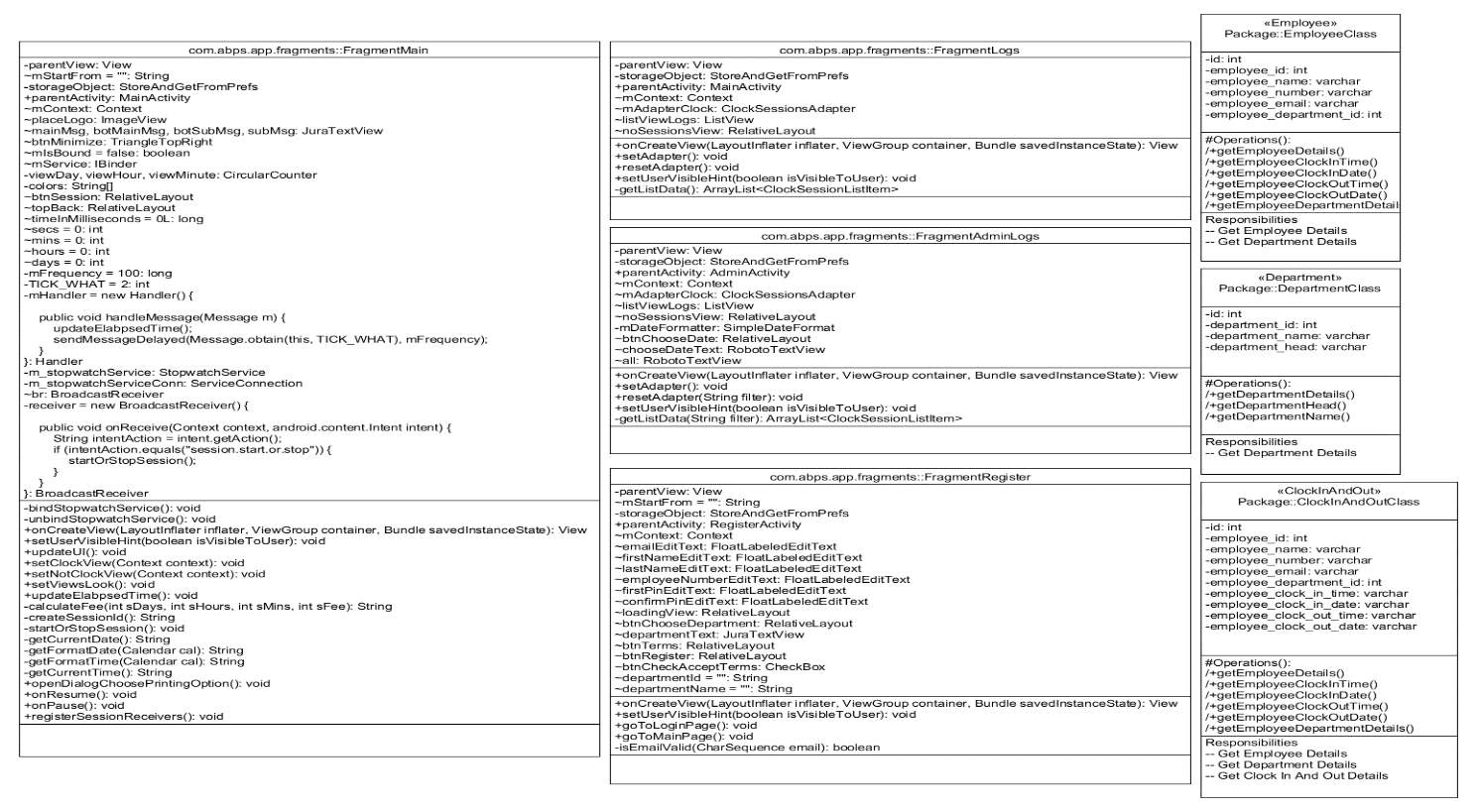
6.1.2.2 Use Case Diagram
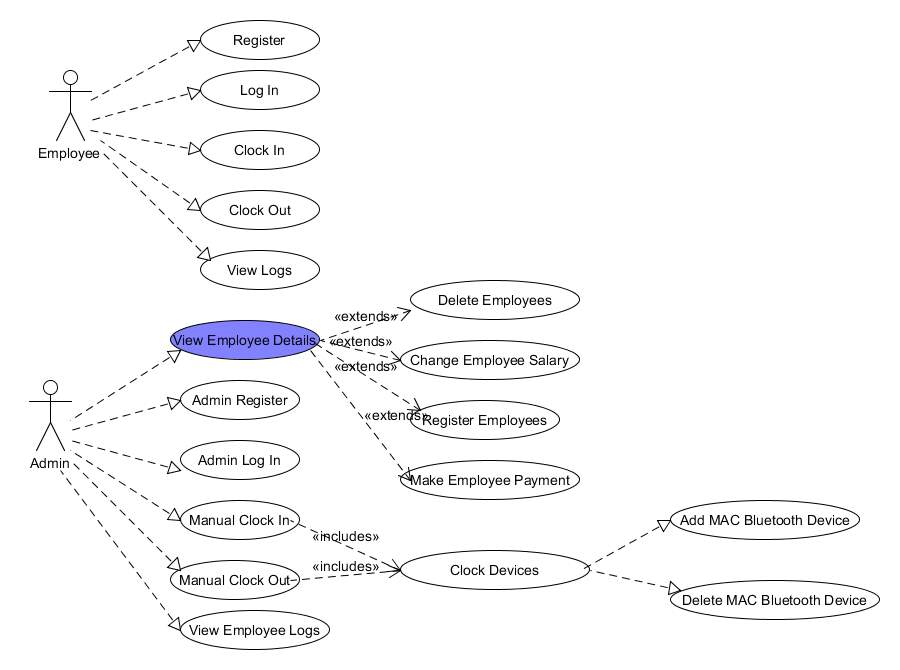
6.1.2.3 Database Diagram
6.1.2.4 Flow Chart Employee
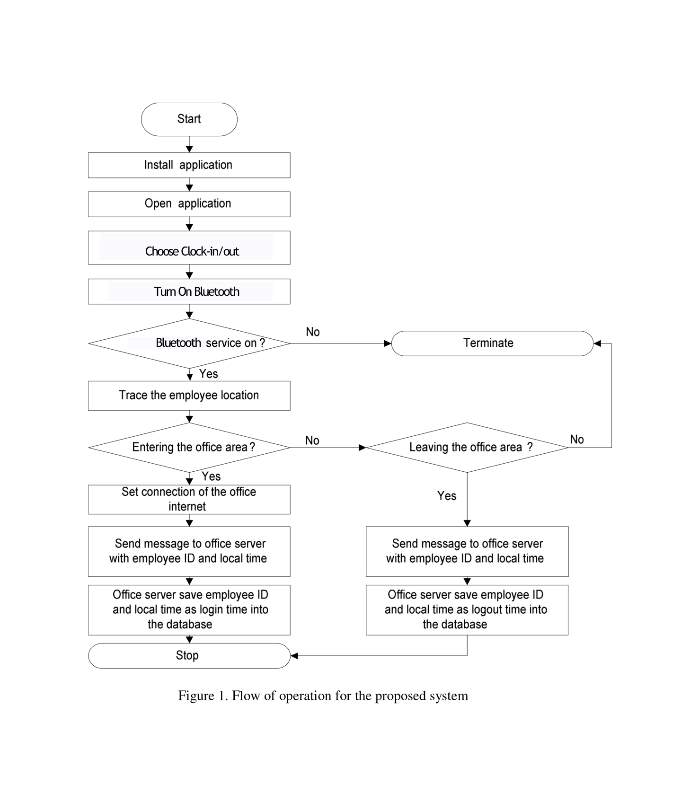
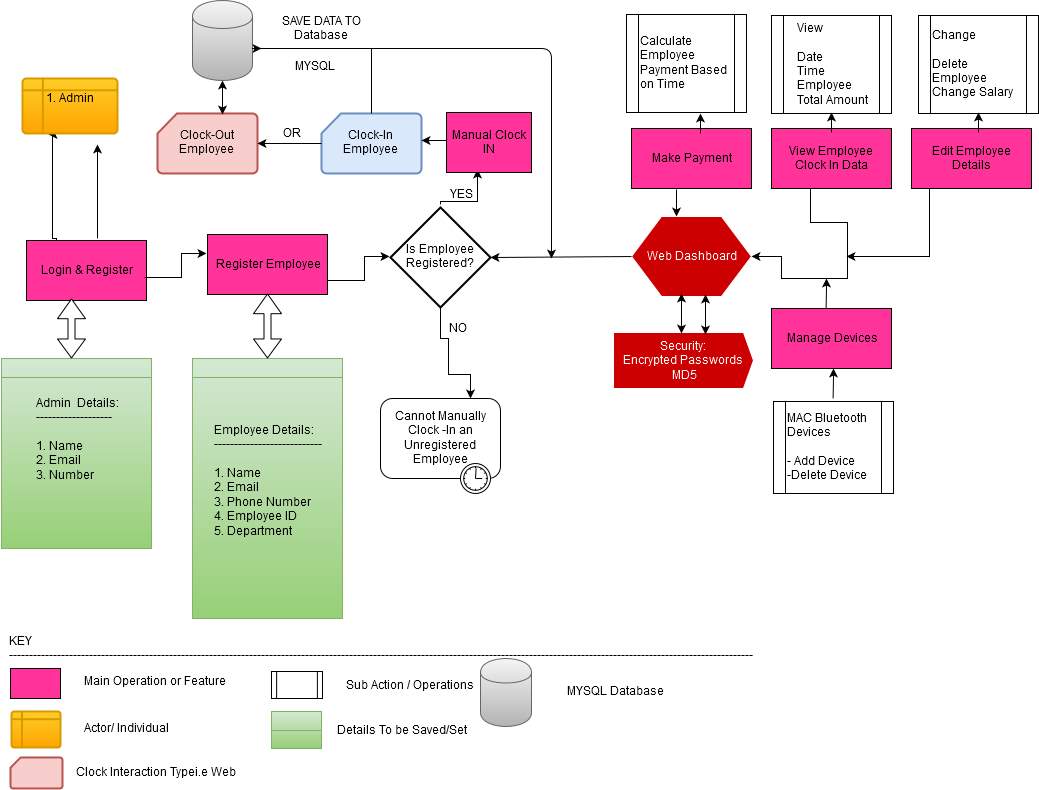
6.1.2.5 Flow Chart Admin
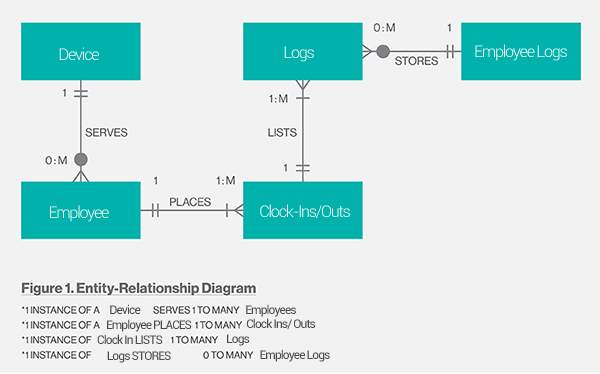
6.1.2.6 Entity Relationship Diagram
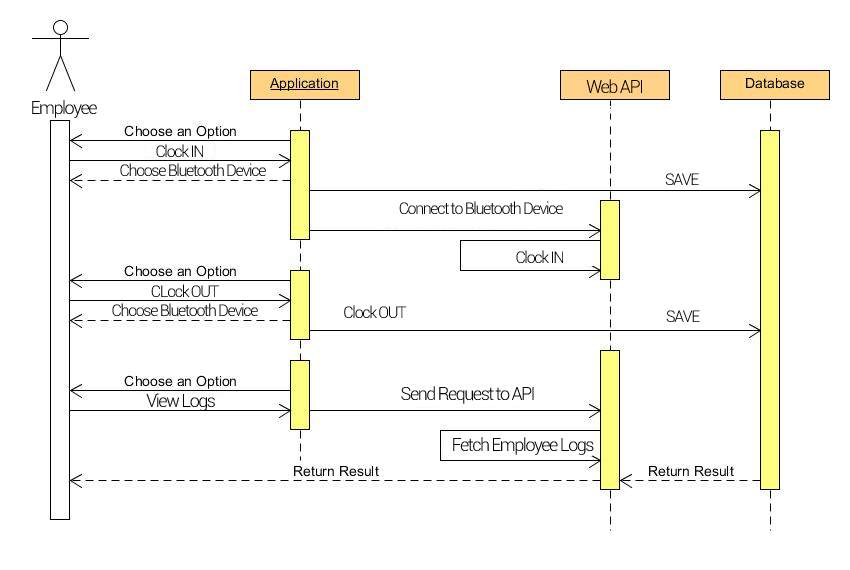
6.1.2.7 Sequence Diagram Main
6.1.2.8 Sequence Diagram register
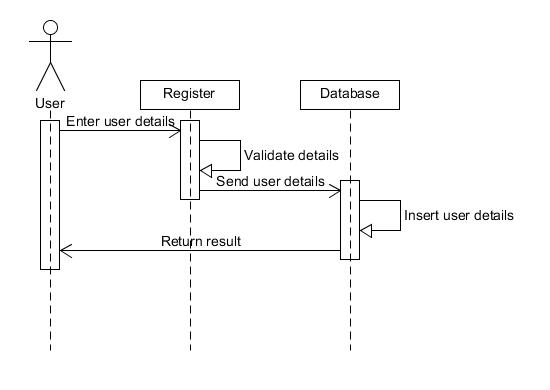
6.1.2.9 Sequence Diagram Login
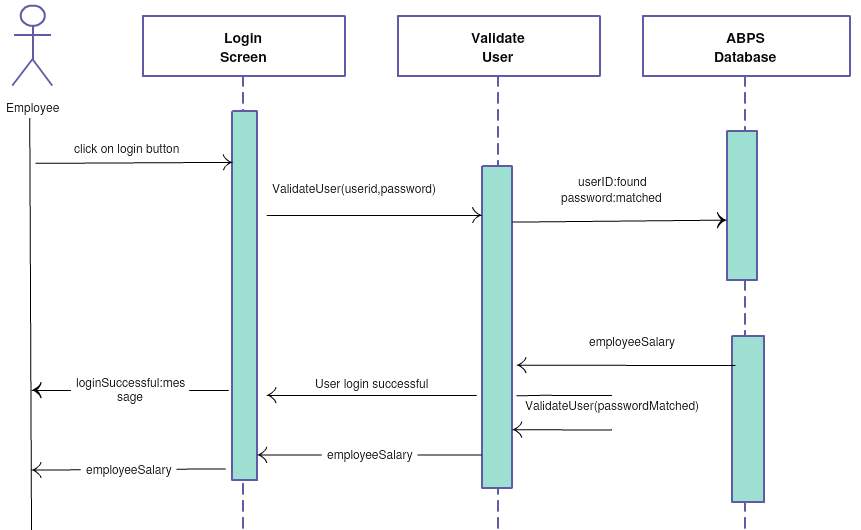
7.0 Chapter 7: Prototype and Technology Review
7.1 Web application GUI Implementation
The graphical user interface has been made as simple and user friendly as possible.
The GUI provides an authentication mechanism which helps in identifying the privileges of the person accessing the system at that specific instance.
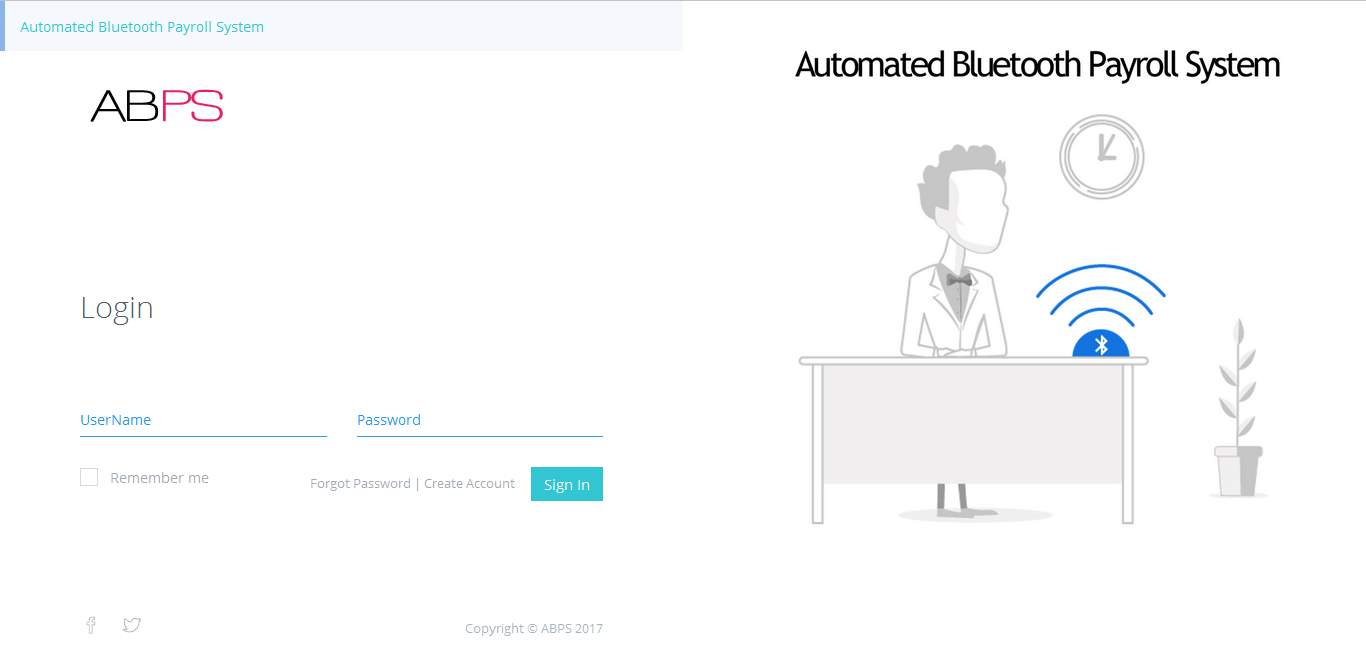
7.1.1 First Login Launch
All functionality is disabled until the user logs in with correct details.
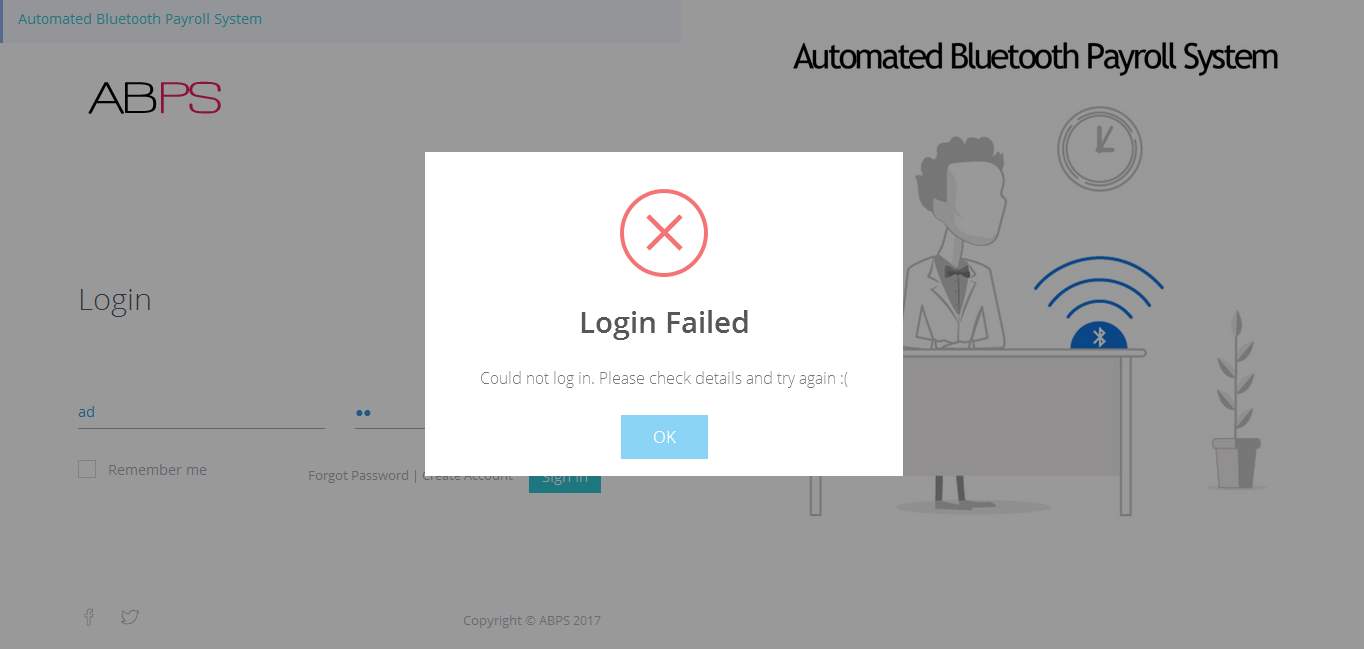
7.1.2 Authentication Level: Login Failure
7.1.3 Successful Login: Redirected To Main Dashboard Page
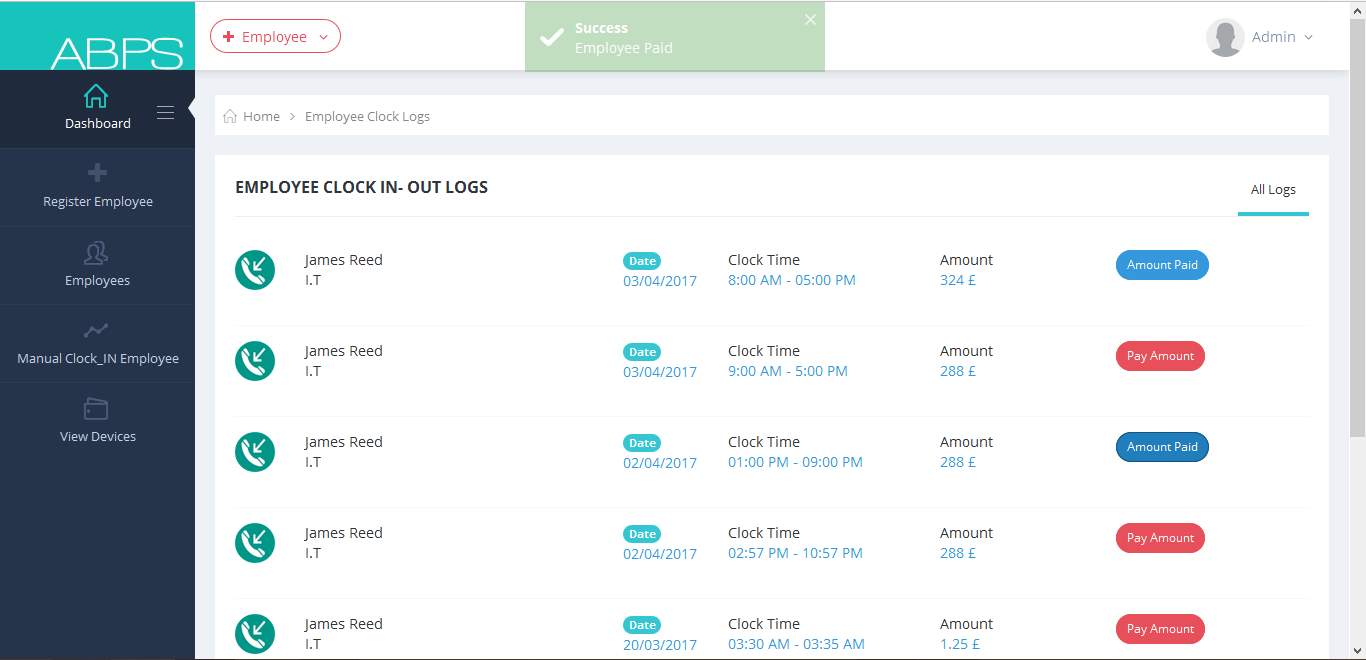
7.1.4 Different Views of Employees
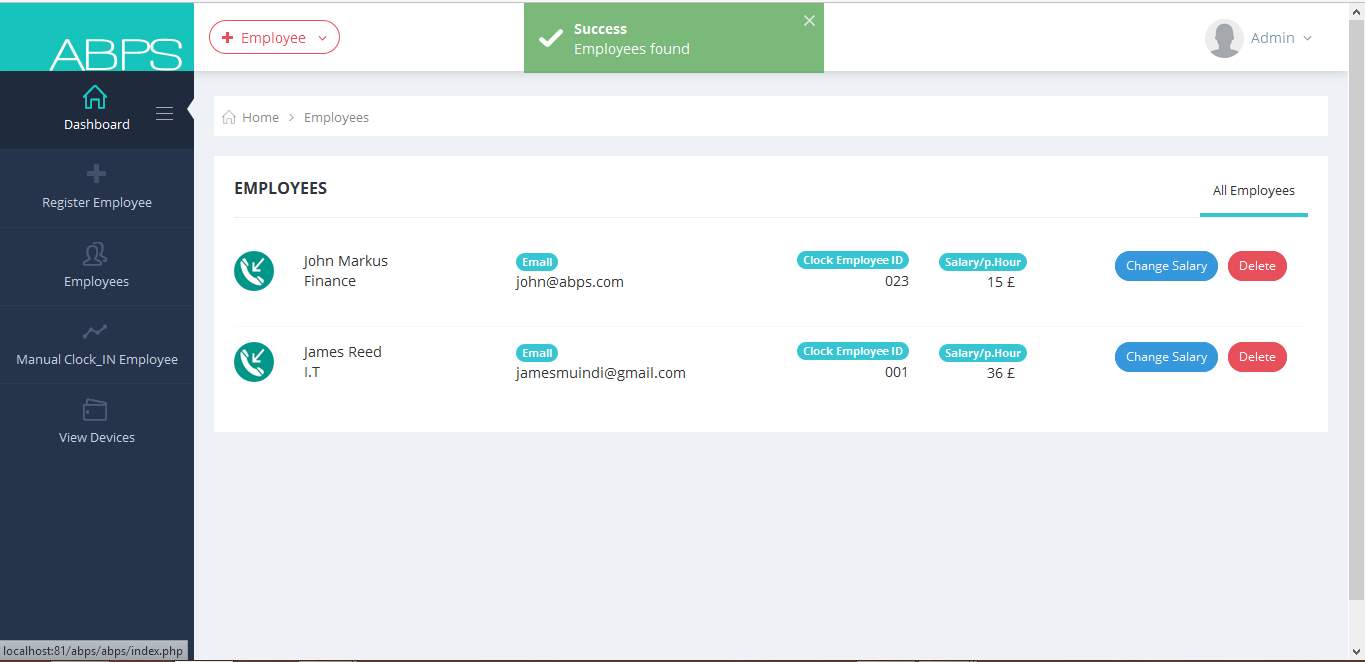
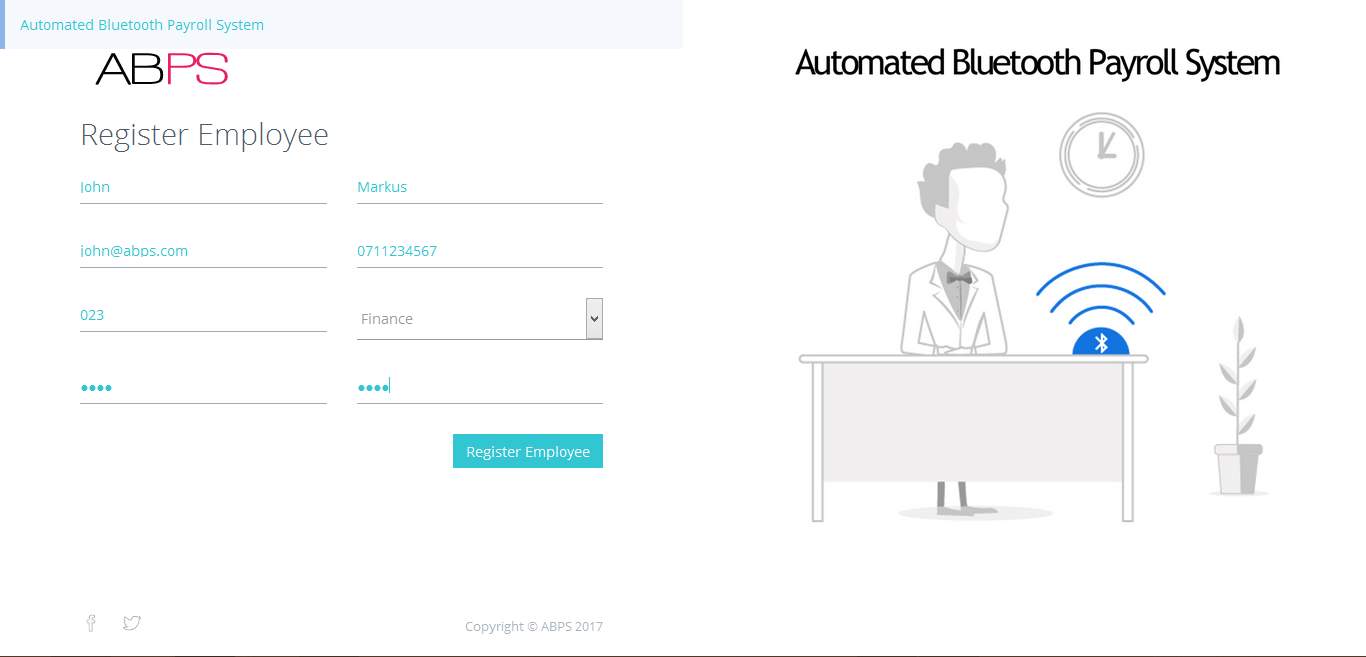
7.1.5 Register New Employee
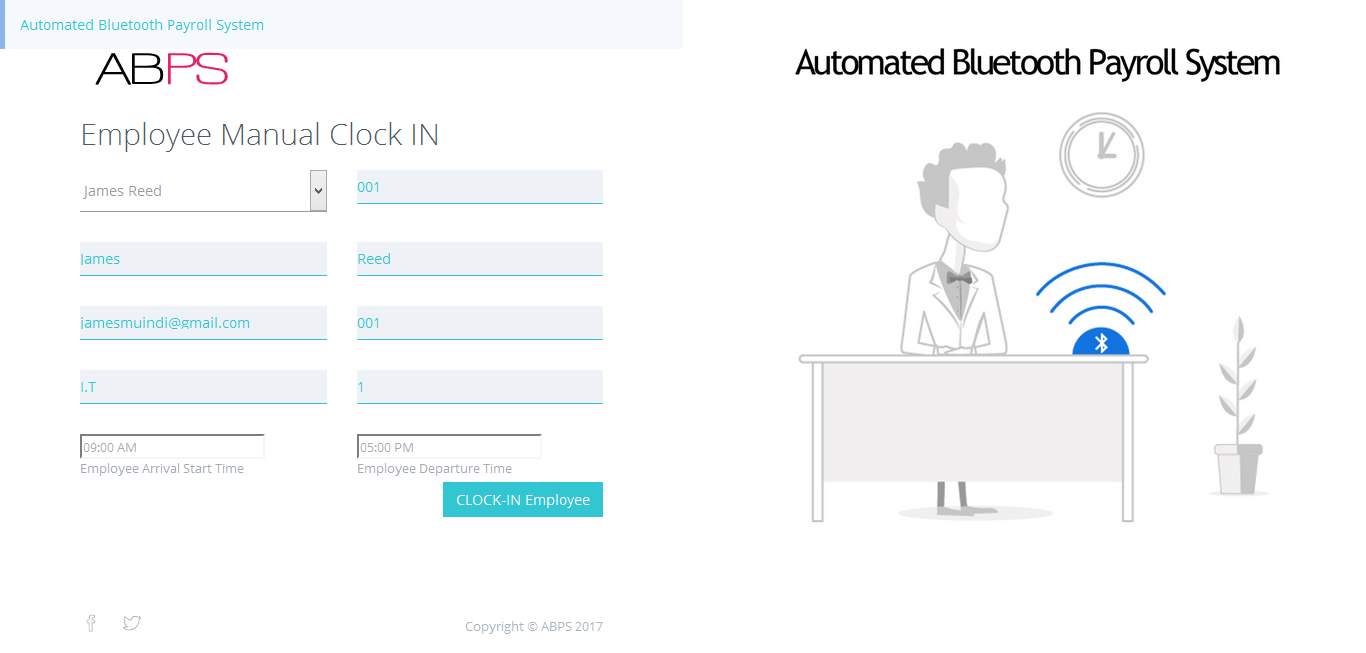
7.1.6 Manual Clock IN Employees
7.1.7 Add New Device via Mac Address
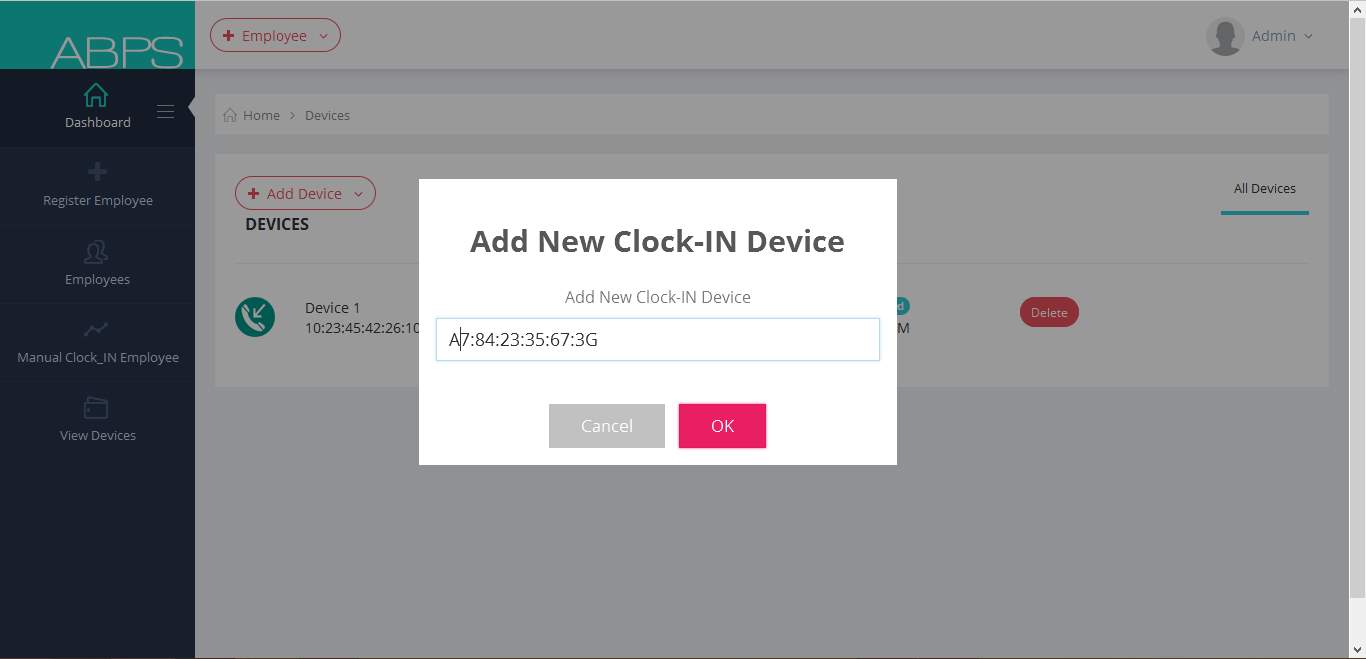
7.2 Android App GUI Implementation
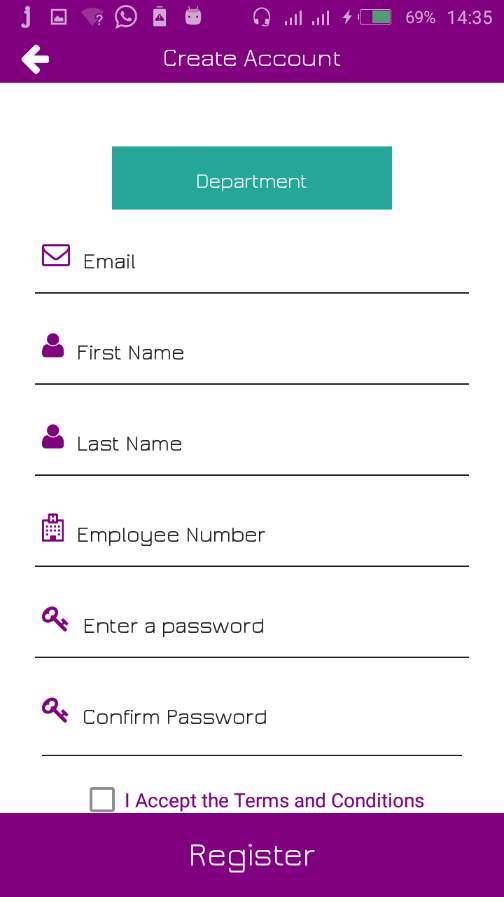
7.2.1 Employee Registration /Create Account
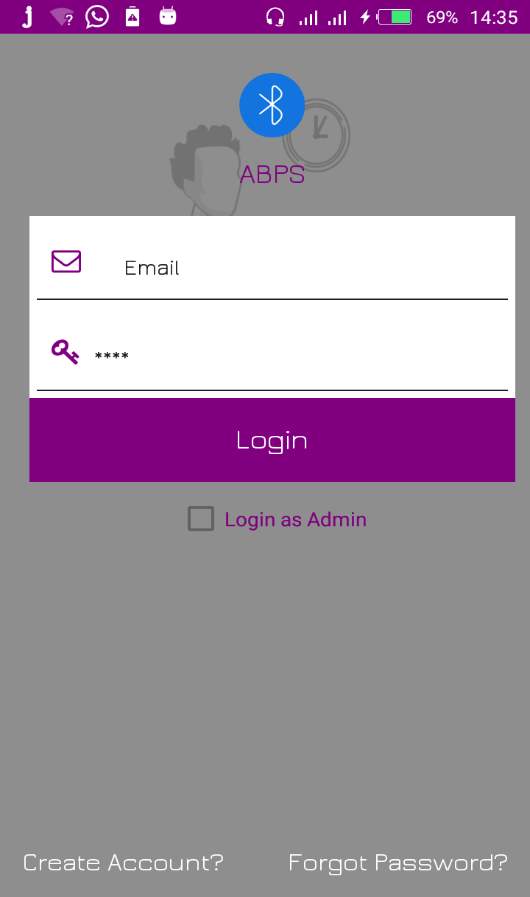
7.2.2 Login
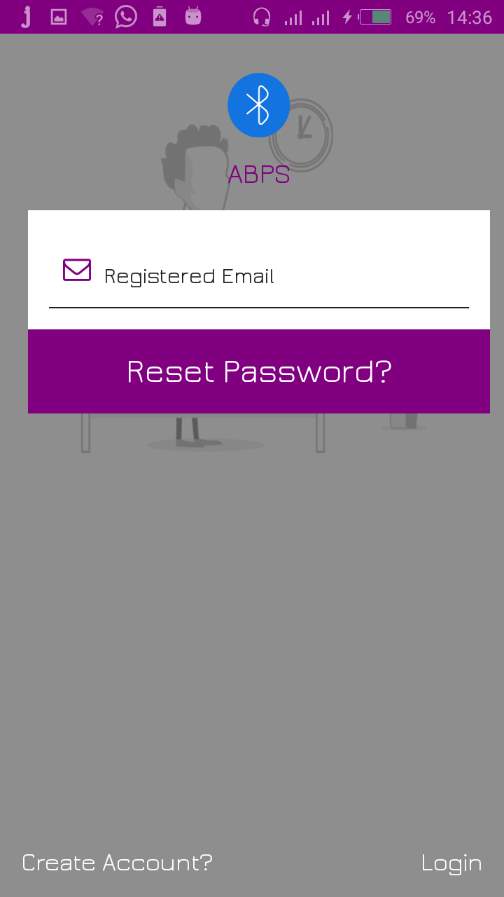
7.2.3 Forgot Password
7.2.3 Employee Not Clocked IN/ Session Inactive
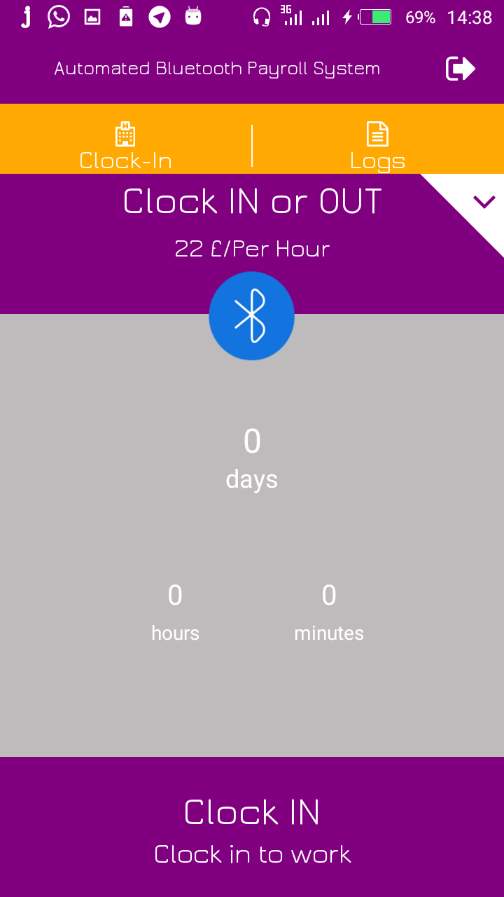
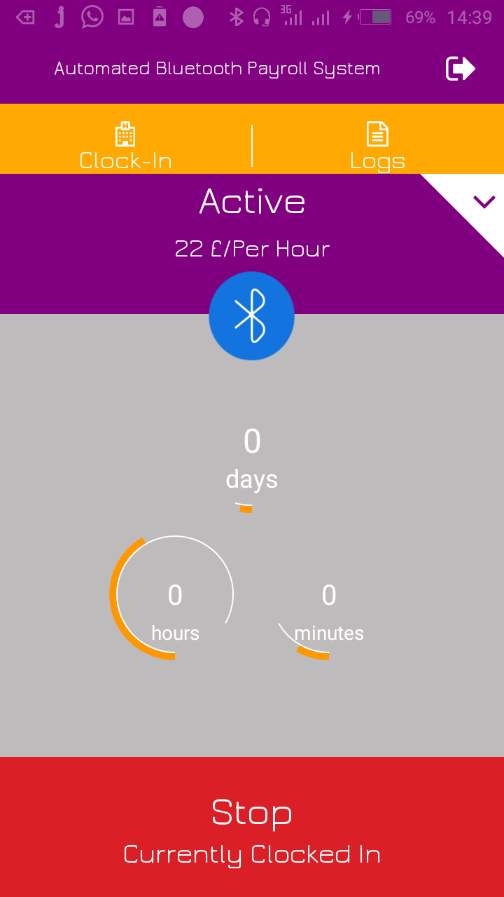
7.2.4 Employee Clocked IN/ Session Active
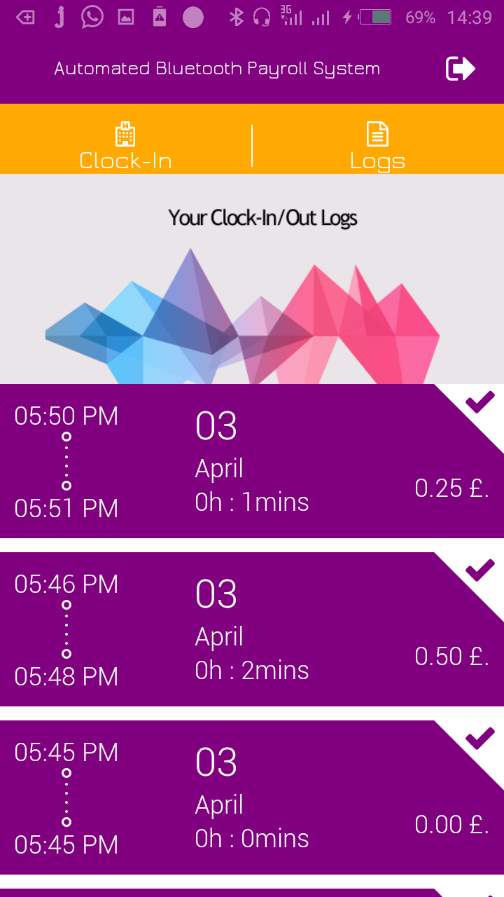
7.2.5 Employee Logs/ Clock INs
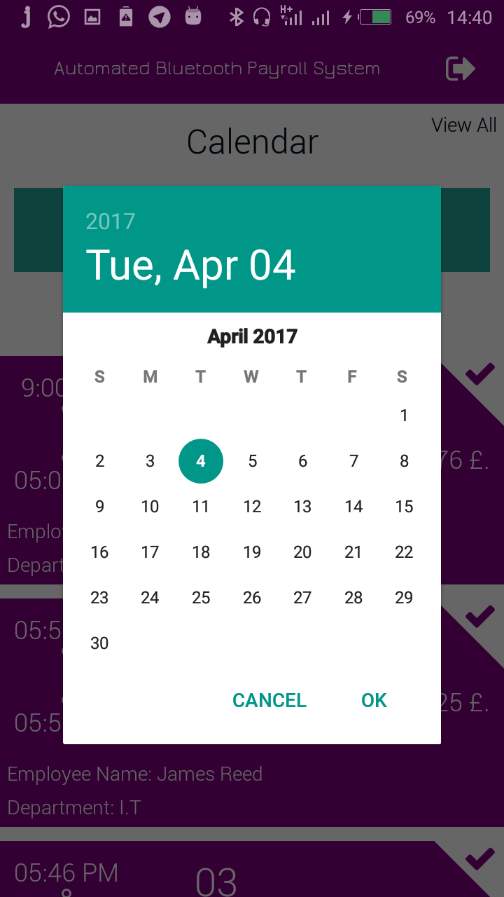
7.2.5 Admin Employee Schedule/ Clock IN Logs
7.3 Technologies Used
7.3.1 Language Requirements
These are the main languages used and some supporting/complimentary frameworks
7.3.1.1 Front End
- HTML – Web Application
- CSS –Web Application
- Javascript & JQUERY – Web Application
- AJAX – Web Application
- Java – Android Application
7.3.1.2 Back End
- MYSQL- Database
- PHP – Server Processing Web Application
- PHP was chosen as the preferred server-side processing method instead of C# since it is very reliable with regards to performance and would also integrate well with the API for communication between the Web application and Android Application in real-time.
- PHP also offers a number of reliable server side processing functions and integrates with the MYSQL Backend Database by offering a number of connection methods that help streamline communication within the API Endpoint s and Database when requests and queries are made.
7.4 System Breakdown, Code and File Linkages
7.4 Web Application
7.4.1 Database Connection
For the database connection there are 2 key files under the “..abpsabpsabps_apiinclude” directory
- Config.php
This file contains the constants needed for the database connection i.e DB_HOST, DB_USER, DB_PASSWORD, DB_DATABASE
- DB_Connect.php
This is file has the class that creates the MYSQLI connection object and picks the config constants as parameters.
This connection object is needed in every query to the database and is created using the connect method as shown below:
// Connecting to database
public function connect() {
require_once ‘include/config.php’;
// connecting to mysqli
$con = mysqli_connect(DB_HOST, DB_USER, DB_PASSWORD,DB_DATABASE);
if (!$con) {
die(“Connection error: ” . mysqli_connect_error());
}
// return database handler
return $con;
}
7.4.2 Database Functions/ Queries
These are the main functions that communicate with the MYSQL database backend with the help of the connection object stated above. They include some functions such as getEmployees, getDevices, storeUser among others.
There are 2 main files
- DB_Functions_fetch.php
This file includes the class that has all the functions for FETCHING data from the database i.e getEmployees or getDevices
The construct for the class creates and stores the connection object mentioned earlier above as a global variable
// connecting to database
function __construct() {
require_once ‘include/DB_Connect.php’;
// connecting to database
$this->db = new DB_Connect();
$GLOBALS[‘con’]= $this->db->connect();
}
Then we can now query the database running various SQL Statement Queries to retrieve data from the database. I.e. getting all the employees. When running the SQL Query using mysqli_query we pass the global connection object as a parameter and the SQL Query statement.
public function getClockInEmployees()
{
$theQuery= “SELECT * FROM employees ORDER BY id DESC”;
$result = mysqli_query($GLOBALS[‘con’], $theQuery) or die(mysqli_error());
if ($result)
{
// get user details
return $result;
}
else
{
return false;
}
}
-DB_Functions_Insert.php
This file includes the class that has all the functions for INSERTING, UPDATING or DELETING data from the database i.e storeUser or deleteDevice.
The construct for the class creates and stores the connection object mentioned earlier above as a global variable
// connecting to database
function __construct() {
require_once ‘include/DB_Connect.php’;
// connecting to database
$this->db = new DB_Connect();
$GLOBALS[‘con’]= $this->db->connect();
}
Then we can now query the database running various SQL Statement Queries to insert data into the database. I.e. Inserting or Creating a new Device. When running the SQL Query using mysqli_query we pass the global connection object as a parameter and the SQL Query statement.
public function addDevice($device_id, $added_date, $added_time)
{
$theQuery= “INSERT INTO devices (device_id, added_date, added_time) VALUES(‘$device_id’, ‘$added_date’, ‘$added_time’)”;
$result = mysqli_query($GLOBALS[‘con’], $theQuery) or die(mysqli_error());
if ($result)
{
// get user details
return true;
}
else
{
return false;
}
}
7.4.3 API Endpoints
For the API Endpoints there are 2 main api files found in the “abpsabpsabps_api” directory.
These two files are the core of the system since they act as endpoints for both the Web Application and Android Mobile App.
Similar to the Functions Classes they are divided into two:
- abps_fetch_data.php
This file includes the methods that have all the functions for FETCHING data from the database through calling the functions specified in the DB_Functions_fetch.php file i.e getEmployees or getDevices
- abps_insert_data.php
This file includes the methods that have all the functions for INSERTING, DELETING or UPDATING data from the database through calling the functions specified in the DB_Functions_Insert.php file i.e. addNewDevice or storeUser
Each API call has a tag property set which specifies the kind of method or function to call. i.e.
$tag = $_POST[‘tag’];
Each method or API call echoes back a JSON (JavaScript Object Notation) Response that is encoded.
For example when an API call or request to get devices would be handled as below:
7.4.3.1 API Endpoint Example
http://mypayrolladmin/abps/abps/abps_api/abps_fetch_data.php?
7.4.3.2 Parameters
tag = get_clock_in_devices
7.4.3.3 API Execution
//First We create an Object of the DB_Functions.php Class
$bd = new DB_Functions();
//Then we can make a function call to the class as below
$db->getClockInDevices();
//This fetches the data and returns a MYSQL Fetch Array which we can loop through using a WHILE loop to append the data retrieve to a response that we shall echo back as a reponse as shown below
$numberOfDevices= mysqli_num_rows($clockDevicesResult);
$devices = array();
while($loopDevices = mysqli_fetch_array($clockDevicesResult))
{
$data = array();
$data[‘device_id’] =$loopDevices[‘device_id’];
$data[‘added_date’] =$loopDevices[‘added_date’];
$data[‘added_time’] =$loopDevices[‘added_time’];
array_push($devices, $data);
}
if($numberOfDevices > 0)
{
$response[“result_code”] = 1;
$response[“message”] = “Devices found”;
$response[“data”] = $devices;
echo json_encode($response, JSON_PRETTY_PRINT);
}
else
{
$response[“result_code”] = 0;
$response[“message”] = “No Devices found”;
echo json_encode($response, JSON_PRETTY_PRINT);
7.4.3.4 API Response
All the API Responses are structured in a JSON Schema with 3 key attributes
Integer: result_code -> an integer value to help in carrying out some operation
String : message -> a message highlighting the result of the API call
Array : data -> an Array that returns the data fetched or retrieved from the database
The response for the API call above for fetching the devices appears as:
{
“result_code“: 1,
“message“: “Devices found”,
“data“: [
{
“device_id”: “A7:84:23:35:67:3G”, “added_date”: “04/04/2017”, “added_time”: “02:33 PM” },
{ “device_id”: “10:23:45:42:26:10”, “added_date”: “03/04/2017”, “added_time”: “04:41 PM” }
] }
7.4.3.4 Ajax Request Example from the app_devices.php view
Data will be sent to the API endpoint via a POST request to retrieve the list of devices and append them to the HTML devices list with the tag specified as “tag=get_clock_in_devices”;
<Script>
function getDevices()
{
var dataString = “tag=get_clock_in_devices”;
console.log(dataString);
$.ajax({
type: “POST”,
url: “abps_api/abps_fetch_data.php”,
data: dataString,
cache: false,
success: function(response)
{
var dispResponse=””;
var resObject= JSON.parse(response);
var result_code = resObject.result_code;
var message = resObject.message;
var data = resObject.data;
if(result_code === 1)
{
dispResponse = ‘Devices found’;
for(i=0;i<data.length;i++)
{
var device = data[i];
7.4.4 Other Key Files and Pages
- app_login.php
Page for logging in as an administrator
- app_devices.php
Page for listing all devices and also adding a new device that the employee can use to Clock IN via Bluetooth. This is identified by the MAC Address.
- app_employees.php
Page for listing all of the employees that have been registered on the system.
- app_logout.php
Page for logging out and terminating/ unsetting the current active session of the logged in administrator.
- app_manual_clock_in.php
Page for then administrator to manually Clock IN an employee in case they cannot clock in via the mobile Android app or are having issues with their devices connectivity.
- app_register_employee.php
Page for admin to register an employee to the system
7.5 Android Mobile Application (App)
7.5.1 Activities
- Admin Activity
Main Activity when you log in as an administrator. It allows you to view all the employees clock in logs and you can filter employee logs via calendar to see which day employees work, how much time they worked and total amount owed/earned.
- LoginActivity
Activity for loggin in as an Admin or Normaol employee. One can also reset their password and email with instruction is sent to them based on the email they registered with.
- MainActivity
The main activity that holds the 2 key fragments for employees Clocking IN and also viewing their logs
- RegisterActivity
Activity for employees registering to the system
- StopWatch Service
This is a background service that is able to keep track of how long an employee is clocked in trhoug the use of a stopwatch counter based on Days, Hours and minutes that their session is active
7.5.2 Mobile Service and ServiceHandler
7.5.2.1 GetData
Main file that handles all the data request to the API endpoints. An example of a data request is
// SERVER_USER_GET_REQUESTS_URL is the API Endpoint URL
public void getDevicesSilent()
{
String serverUrl = SERVER_USER_GET_REQUESTS_URL;
String theLoadingMsg=””;
String theOp=”get_devices”;
List<String> params = new ArrayList<String>();
HashMap<String, String> uParams = new HashMap<String, String>();
uParams.put(“tag”, “get_clock_in_devices”);
//Run the request as a background service
(new LongOperation(serverUrl,params,uParams, theLoadingMsg, theOp, ServiceHandler.POST,true)).execute();
}
7.5.2.2 ServiceHandler
Main class that handles sending of all the requests to the endpoint and retrieving the rresponse.
Requests are sent via POST to the endpoint with the params written via a Buffered Writer.
OutputStream os = conn.getOutputStream();
BufferedWriter writer = new BufferedWriter(
new OutputStreamWriter(os, “UTF-8”));
writer.write(getPostDataString(postDataParams));
7.5.2.3 ServiceHandlerObject
This is an object that retirves the response from the Serfvice Handler and relays it to the calling method to perform some operation on the GetData file such as performUserGetDevices(ServiceObject object)
The response retrieved from the object is a JSON object and hence the GSON Library is used to parse it and map it to a corresponding object. i.e Gson gson = new Gson();
String result= theObject.getResult();
DevicesObject devicesResponse = gson.fromJson(result.toString(), DevicesObject.class);
int resultCode= devicesResponse.getResult_code();
String resultMessage= devicesResponse.getMessage();
if(resultCode == RESULT_CODE_OK)
{
//Store Values
ArrayList<DeviceData> devices = (ArrayList<DeviceData>) devicesResponse.getData();
storageObject.saveDeviceDataToPrefs(devices);
Log.d(“Get Devices Found”,”Found some “+devices.size()+” devices”);
}
else
{
Log.d(“Get Devices Failed”,”Get Devices Failed”);
}
}
7.5.3 Shared Preferences
– StoreAndGetFromPrefs
This is a file used for saving data to the android device local storage through its shared Preferences.
I.e when a user logs in we save some of their details to the device local storage using an object of this class.
StoreAndGetFromPrefs storageObject = new StoreAndGetFromPrefs(context);
storageObject.saveUserNameToPrefs(“James”);
storageObject.saveUserEmployeeIdToPrefs(“001”);
storageObject.saveUserDepartmentToPrefs(“Finance”);
7.5.4 Key Libraries and imported classes
– GSON > Library to map the JSON response to a corresponding POJO object.
– JacksonFasterXML > com.fasterxml.jackson.annotations Libray to map the JSON notations string to an object with its corresponsidng Getters and Setters.
-HttpMime Library to enable carry our POST and GET http requests to our API endpoint.
-Common this is the main Application class file which avails some application wide functions such as getting the Typeface for textviews.
7.5.5 Fragments
7.5.5.1 Main Fragment
package com.abps.app.fragments;
import java.text.SimpleDateFormat;
import java.util.Calendar;
import java.util.Date;
import java.util.Random;
import java.util.concurrent.TimeUnit;
import android.content.BroadcastReceiver;
import android.content.ComponentName;
import android.content.Context;
import android.content.Intent;
import android.content.IntentFilter;
import android.content.ServiceConnection;
import android.graphics.Color;
import android.os.Build;
import android.os.Bundle;
import android.os.Handler;
import android.os.IBinder;
import android.os.Message;
import android.support.v4.app.Fragment;
import android.text.format.DateFormat;
import android.view.LayoutInflater;
import android.view.View;
import android.view.View.OnClickListener;
import android.view.ViewGroup;
import android.widget.ImageView;
import android.widget.RelativeLayout;
import android.widget.Toast;
import com.abps.app.GeneralCommands;
import com.abps.app.MainActivity;
import com.abps.app.StopwatchService;
import com.abps.app.constanst.IWhereMyLocationConstants;
import com.abps.app.font.JuraTextView;
import com.abps.app.mobileservices.GetData;
import com.abps.app.objects.ClockSessionObject;
import com.abps.app.prefs.StoreAndGetFromPrefs;
import com.abps.app.view.CircularCounter;
import com.abps.app.view.TriangleTopRight;
import com.abps.app.R;
import com.orhanobut.dialogplus.DialogPlus;
import com.orhanobut.dialogplus.DialogPlus.Gravity;
import com.orhanobut.dialogplus.OnDismissListener;
import com.orhanobut.dialogplus.ViewHolder;
public class FragmentMain extends Fragment implements IWhereMyLocationConstants {
private View parentView;
String mStartFrom=””;
private static StoreAndGetFromPrefs storageObject;
public static MainActivity parentActivity;
static Context mContext;
//Local Views
ImageView placeLogo;
static JuraTextView mainMsg,botMainMsg,botSubMsg,subMsg;
static TriangleTopRight btnMinimize;
boolean mIsBound=false;
IBinder mService;
//Counter
private CircularCounter viewDay,viewHour,viewMinute;
//Other Views
private String[] colors;
static RelativeLayout btnSession;
static RelativeLayout topBack;
//Timer
long timeInMilliseconds = 0L;
int secs = 0;
int mins = 0;
int hours = 0;
int days = 0;
// Timer to update the elabpsedTime display
private final long mFrequency = 100; // milliseconds
private final int TICK_WHAT = 2;
private Handler mHandler = new Handler() {
public void handleMessage(Message m) {
updateElabpsedTime();
sendMessageDelayed(Message.obtain(this, TICK_WHAT), mFrequency);
}
};
// Connection to the backgorund StopwatchService
private StopwatchService m_stopwatchService;
private ServiceConnection m_stopwatchServiceConn;
BroadcastReceiver br;
private void bindStopwatchService() {
parentActivity.bindService(new Intent(parentActivity, StopwatchService.class),
m_stopwatchServiceConn, Context.BIND_AUTO_CREATE);
mIsBound= true;
}
private void unbindStopwatchService() {
if ( m_stopwatchService != null ) {
if(mIsBound)
{
parentActivity.unbindService(m_stopwatchServiceConn);
mIsBound= false;
}
}
}
@Override
public View onCreateView(LayoutInflater inflater, ViewGroup container, Bundle savedInstanceState) {
parentView = inflater.inflate(R.layout.fragment_clocked, container, false);
parentActivity = (MainActivity)getActivity();
mContext= parentActivity.getApplicationContext();
storageObject = new StoreAndGetFromPrefs(mContext);
parentActivity.startService(new Intent(parentActivity, StopwatchService.class));
m_stopwatchServiceConn = new ServiceConnection() {
@Override
public void onServiceConnected(ComponentName name, IBinder service) {
m_stopwatchService = ((StopwatchService.LocalBinder)service).getService();
if(m_stopwatchService.isStopwatchRunning())
{
updateElabpsedTime();
setClockView(mContext);
}
}
@Override
public void onServiceDisconnected(ComponentName name) {
m_stopwatchService = null;
}
};
bindStopwatchService();
colors = getResources().getStringArray(R.array.colors);
placeLogo= (ImageView) parentView.findViewById(R.id.placeLogo);
btnMinimize= (TriangleTopRight) parentView.findViewById(R.id.btnMinimize);
btnSession= (RelativeLayout) parentView.findViewById(R.id.botView);
topBack= (RelativeLayout) parentView.findViewById(R.id.topView);
mainMsg= (JuraTextView) parentView.findViewById(R.id.mainMsg);
botMainMsg= (JuraTextView) parentView.findViewById(R.id.btnMainMsg);
botSubMsg= (JuraTextView) parentView.findViewById(R.id.btnSubMsg);
subMsg= (JuraTextView) parentView.findViewById(R.id.subMsg);
subMsg.setText(mContext.getResources().getString(R.string.rate, storageObject.retrieveUserSalaryFromPrefs()));
btnMinimize.setOnClickListener(new OnClickListener() {
@Override
public void onClick(View v) {
// TODO Auto-generated method stub
parentActivity.moveTaskToBack(true);
parentActivity.overridePendingTransition(R.anim.nothing, R.anim.hide_to_bottom);
storageObject.setMinimized(true);
}
});
viewDay = (CircularCounter) parentView.findViewById(R.id.viewDay);
viewHour = (CircularCounter) parentView.findViewById(R.id.viewHour);
viewMinute = (CircularCounter) parentView.findViewById(R.id.viewMinute);
setViewsLook();
btnSession.setOnClickListener(new OnClickListener() {
@Override
public void onClick(View v) {
// TODO Auto-generated method stub
openDialogChoosePrintingOption();
//startOrStopSession();
}
});
mHandler.sendMessageDelayed(Message.obtain(mHandler, TICK_WHAT), mFrequency);
registerSessionReceivers();
return parentView;
}
@Override
public void setUserVisibleHint(boolean isVisibleToUser) {
super.setUserVisibleHint(isVisibleToUser);
// Make sure that we are currently visible
if (this.isVisible()) {
// If we are becoming invisible, then…
if (isVisibleToUser) {
// TODO stop audio playback
if(storageObject.isClock())
{
setClockView(mContext);
}
else
{
setNotClockView(mContext);
}
}
}
}
public void updateUI()
{
days = hours / 24;
viewDay.setValues(days, secs*2, secs*3);
viewHour.setValues(hours, secs*2, secs*4);
viewMinute.setValues(mins, secs*1, secs*2);
}
public static void setClockView(Context context)
{
topBack.setBackgroundColor(context.getResources().getColor(R.color.theme_color));
btnSession.setBackgroundColor(context.getResources().getColor(R.color.theme_red));
mainMsg.setText(context.getResources().getString(R.string.sessionactive));
botMainMsg.setText(context.getResources().getString(R.string.sessionstop));
botSubMsg.setText(context.getResources().getString(R.string.sessionclocked));
}
public static void setNotClockView(Context context)
{
topBack.setBackgroundColor(context.getResources().getColor(R.color.theme_color));
btnSession.setBackgroundColor(context.getResources().getColor(R.color.theme_color));
mainMsg.setText(context.getResources().getString(R.string.clockinorout));
botMainMsg.setText(context.getResources().getString(R.string.clockin));
botSubMsg.setText(context.getResources().getString(R.string.clockinmsg));
}
public void setViewsLook()
{
//Set Days
viewDay.setFirstWidth(getResources().getDimension(R.dimen.first))
.setFirstColor(Color.TRANSPARENT)
.setSecondWidth(getResources().getDimension(R.dimen.second))
.setSecondColor(Color.parseColor(colors[0]))
.setThirdWidth(getResources().getDimension(R.dimen.third))
.setThirdColor(Color.WHITE)
.setBackgroundColor(Color.TRANSPARENT);
//Set Hours
viewHour.setFirstWidth(getResources().getDimension(R.dimen.first))
.setFirstColor(Color.TRANSPARENT)
.setSecondWidth(getResources().getDimension(R.dimen.second))
.setSecondColor(Color.parseColor(colors[0]))
.setThirdWidth(getResources().getDimension(R.dimen.third))
.setThirdColor(Color.WHITE)
.setBackgroundColor(Color.TRANSPARENT);
//Set Minutes
viewMinute.setFirstWidth(getResources().getDimension(R.dimen.first))
.setFirstColor(Color.TRANSPARENT)
.setSecondWidth(getResources().getDimension(R.dimen.second))
.setSecondColor(Color.parseColor(colors[0]))
.setThirdWidth(getResources().getDimension(R.dimen.third))
.setThirdColor(Color.WHITE)
.setBackgroundColor(Color.TRANSPARENT);
}
public void updateElabpsedTime() {
if ( m_stopwatchService != null )
{
m_stopwatchService.getFormattedElabpsedTime();
hours = m_stopwatchService.getHours();
mins = m_stopwatchService.getMins();
secs = m_stopwatchService.getSecs();
updateUI();
}
}
private String calculateFee(int sDays, int sHours, int sMins, int sFee)
{
int fee=0;
String totalFee=””;
if(sDays<1)
{
if(sHours<1)
{
float mFee= (float) (sMins * 0.25);
float tFee= sHours + mFee;
totalFee= String.format(“%.2f”, tFee);
}
else
{
//some algorithm
fee= (sHours*sFee);
float mFee= (float) (sMins * 0.25);
float tFee= fee + mFee;
totalFee= String.format(“%.2f”, tFee);
}
}
return totalFee;
}
private String createSessionId() {
// TODO Auto-generated method stub
char[] chars1 = “ABCDEF012GHIJKL345MNOPQR678STUVWXYZ9″.toCharArray();
StringBuilder sb1 = new StringBuilder();
Random random1 = new Random();
for (int i = 0; i < 12; i++)
{
char c1 = chars1[random1.nextInt(chars1.length)];
sb1.append(c1);
}
String sId=””;
sId= sb1.toString();
return sId;
}
private void startOrStopSession() {
// TODO Auto-generated method stub
if(!m_stopwatchService.isStopwatchRunning())
{
m_stopwatchService.start();
storageObject.setLastClockSession(0,0,0,0,”ABC”,0);
storageObject.setClock(true);
setClockView(mContext);
}
else
{
m_stopwatchService.pause();
//Get Day Hours and Seconds
int sdFee= Integer.parseInt(storageObject.retrieveUserSalaryFromPrefs());
String sessionTotalAmount = calculateFee(days,hours,mins,sdFee);
ClockSessionObject session = new ClockSessionObject();
Calendar cal = Calendar.getInstance();
// remove next line if you’re always using the current time.
cal.add(Calendar.DAY_OF_MONTH, -days);
cal.add(Calendar.HOUR, -hours);
cal.add(Calendar.MINUTE, -mins);
String sessionStartTime = getFormatTime(cal);
//Date currentDate = new Date(System.currentTimeMillis() – TimeUnit.HOURS.toMillis(1));
String sessionId=createSessionId();
String sessionStartDate = getCurrentDate();
String sessionEndTime = getCurrentTime();
session.setSessionId(sessionId);
session.setSessionClockDate(sessionStartDate);
session.setSessionClockDays(“”+days);
session.setSessionClockEndTime(sessionEndTime);
session.setSessionClockFee(sessionTotalAmount);
session.setSessionClockHours(“”+hours);
session.setSessionClockMins(“”+mins);
session.setSessionClockLogged(“false”);
session.setSessionClockRefNumber(storageObject.retrieveUserEmployeeNumberFromPrefs());
session.setSessionClockStartTime(sessionStartTime);
session.setSessionUserEmail(storageObject.retrieveUserEmailFromPrefs());
session.setSessionUserNumber(storageObject.retrieveUserEmployeeNumberFromPrefs());
storageObject.addClockSessionObjectInPreferences(session);
//Update TO DB
String userEmployeeId= storageObject.retrieveUserEmployeeNumberFromPrefs();
String userName =storageObject.retrieveUserNameFromPrefs();
String userEmail=storageObject.retrieveUserEmailFromPrefs();
String userDepartmentId=storageObject.retrieveUserDepartmentIdFromPrefs();
String userDepartment=storageObject.retrieveUserDepartmentFromPrefs();
String sessionEndDate= sessionStartDate;
String sessionTotalTime= days+”:”+hours+”:”+mins;
GetData ob1 = new GetData();
ob1.initializeSilent(parentActivity);
ob1.userClockIn(userEmployeeId, userName, userEmail, userDepartmentId, userDepartment, sessionId, sessionStartDate, sessionStartTime, sessionEndDate, sessionEndTime, sessionTotalTime, sessionTotalAmount);
m_stopwatchService.reset();
unbindStopwatchService();
setNotClockView(mContext);
storageObject.setClock(false);
storageObject.setPaidForLastSession(false);
}
}
private String getCurrentDate() {
SimpleDateFormat df = new SimpleDateFormat(“dd/MM/yyyy”);
String date = df.format(Calendar.getInstance().getTime());
return date;
}
private String getFormatDate(Calendar cal) {
SimpleDateFormat df = new SimpleDateFormat(“dd/MM/yyyy”);
String date = df.format(cal.getTime());
return date;
}
private String getFormatTime(Calendar cal) {
String delegateTime = “hh:mm aa”;
String time = (String) DateFormat.format(delegateTime, cal.getTime());
return time;
}
private String getCurrentTime() {
String delegateTime = “hh:mm aa”;
String time = (String) DateFormat.format(delegateTime,Calendar.getInstance().getTime());
return time;
}
public void openDialogChoosePrintingOption()
{
View contentView = parentActivity.getLayoutInflater().inflate(R.layout.dialog_content_choose_clockin_option, null);
final DialogPlus dialogPlus = new DialogPlus.Builder(parentActivity)
.setContentHolder(new ViewHolder(contentView))
.setGravity(Gravity.CENTER)
.setBackgroundColorResourceId(R.color.transparent)
.setCancelable(true)
.setOnDismissListener(new OnDismissListener() {
@Override
public void onDismiss(DialogPlus dialog) {
// TODO Auto-generated method stub
parentActivity.hideKeyboard();
}
})
.create();
//Content View
View content = dialogPlus.getHolderView();
final RelativeLayout btnUseDefault = (RelativeLayout) content.findViewById(R.id.btnUseDefault);
final RelativeLayout btnSearchForDevice = (RelativeLayout) content.findViewById(R.id.btnSearchForDevice);
btnUseDefault.setOnClickListener(new OnClickListener() {
@Override
public void onClick(View v) {
// TODO Auto-generated method stub
if(storageObject.retrieveDeviceObjectsFromPrefs().size() > 0)
{
dialogPlus.setDismiss();
GeneralCommands ob1 = new GeneralCommands(parentActivity);
ob1.openDialogChooseDefaultDevice();
}
else
{
Toast.makeText(mContext, mContext.getResources().getString(R.string.nodefault), Toast.LENGTH_SHORT).show();
}
}
});
btnSearchForDevice.setOnClickListener(new OnClickListener() {
@Override
public void onClick(View v) {
// TODO Auto-generated method stub
//dialogPlus.setDismiss();
GeneralCommands ob1 = new GeneralCommands(parentActivity);
if (Build.VERSION.SDK_INT >= 23)
{
//Do Nothing
if(ob1.isBluetoothOn())
{
if(!parentActivity.isLocGood)
{
parentActivity.displayLocationSettingsRequest();
dialogPlus.setDismiss();
}
else
{
ob1.openDialogSearchForDevice();
dialogPlus.setDismiss();
}
}
else
{
Toast.makeText(mContext, mContext.getResources().getString(R.string.turnonbluetooth), Toast.LENGTH_LONG).show();
dialogPlus.dismiss();
}
}
else
{
if(ob1.isBluetoothOn())
{
ob1.openDialogSearchForDevice();
dialogPlus.setDismiss();
}
else
{
ob1.turnOnBluetooth();
Toast.makeText(mContext, mContext.getResources().getString(R.string.turningonbluetooth), Toast.LENGTH_LONG).show();
dialogPlus.setDismiss();
}
}
}
});
content.setOnClickListener(new OnClickListener() {
@Override
public void onClick(View v) {
// TODO Auto-generated method stub
parentActivity.hideKeyboard();
dialogPlus.dismiss();
}
});
dialogPlus.show();
}
//Receiver Stuff
@Override
public void onResume() {
registerSessionReceivers();
super.onResume();
}
/***
* Unregister for broadcasts
*/
@Override
public void onPause() {
mContext.unregisterReceiver(receiver);
super.onPause();
}
public void registerSessionReceivers()
{
IntentFilter filter = new IntentFilter();
filter.addAction(“session.start.or.stop”);
mContext.registerReceiver(receiver, filter);
}
private BroadcastReceiver receiver = new BroadcastReceiver() {
public void onReceive(Context context, android.content.Intent intent) {
String intentAction = intent.getAction();
if (intentAction.equals(“session.start.or.stop”))
{
//Do something
startOrStopSession();
}
}
};
}
7.5.6 Bluetooth Search and Broadcast
The Bluetooth search, scan and broadcast is handled within the GeneralCommands file using the initBroadcast(listViewDevices) method.
This method creates an intent and sends it as a broadcast when some Bluetooth devices are found after the Bluetooth discovery is complete.
Once devices arte found the list view of devices is populated with the device name and MAC Address which is matched against the devices the Administrator has added on the web application as the ones allowable to clock in or out the employee.
private void initBroadcast(final ListView listViewDevices) {
broadcastReceiver = new BroadcastReceiver() {
@Override
public void onReceive(Context context, Intent intent) {
// TODO Auto-generated method stub
String action = intent.getAction();
BluetoothDevice device = intent
.getParcelableExtra(BluetoothDevice.EXTRA_DEVICE);
mDeviceAdapter= new ClockInDeviceAdapter(mContext, listDataDevices);
listViewDevices.setAdapter(mDeviceAdapter);
if (BluetoothDevice.ACTION_FOUND.equals(action))
{
if (device == null)
return;
final String address = device.getAddress();
String name = device.getName();
if (name == null)
name = “BT”;
else if (name.equals(address))
name = “BT”;
ClockInDeviceListItem item=new ClockInDeviceListItem();
item.setDeviceName(name);
item.setDeviceAddress(address);
listDataDevices.add(item);
mDeviceAdapter.notifyDataSetChanged();
finishLoading();
}
else if (BluetoothAdapter.ACTION_DISCOVERY_STARTED
.equals(action)) {
//Loading
String info = mContext.getResources().getString(R.string.searchingdevices);
startLoading(info);
} else if (BluetoothAdapter.ACTION_DISCOVERY_FINISHED
.equals(action)) {
//Hide View
if(listDataDevices.size()>0)
{
finishLoading();
}
else
{
String info = mContext.getResources().getString(R.string.nodevicefound);
problemLoading(info);
}
}
}
};
intentFilter = new IntentFilter();
intentFilter.addAction(BluetoothDevice.ACTION_FOUND);
intentFilter.addAction(BluetoothAdapter.ACTION_DISCOVERY_STARTED);
intentFilter.addAction(BluetoothAdapter.ACTION_DISCOVERY_FINISHED);
mContext.registerReceiver(broadcastReceiver, intentFilter);
}
8.0 Testing
This section provides a testing report for the Automate Bluetooth Payroll System. The test is composed of Unit testing and Accessibility testing. The unit tests are for both black box testing and white box testing. The accessibility testing contains the keyboard interactivity test and high contrast colors test with Nielsen’s Heuristics considered.
8.1 White Box Testing
This entails evaluating the internal structure and code of the system. This test mainly explores the lines of code that are executed and entails a review of code that is internal to the system.
For white box testing, the main class to be explored is FragmentMain.java and specifically the evaluation of the CalculateFee method for calculating employee’s salary.
private String calculateFee(int sDays, int sHours, int sMins, int sFee)
{
int fee=0;
String totalFee=””;
if(sDays<1)
{
if(sHours<1)
{
float mFee= (float) (sMins * 0.25);
float tFee= sHours + mFee;
totalFee= String.format(“%.2f”, tFee);
}
else
{
//some algorithm
fee= (sHours*sFee);
float mFee= (float) (sMins * 0.25);
float tFee= fee + mFee;
totalFee= String.format(“%.2f”, tFee);
}
}
else
{
fee= (sHours*sFee) + (24*sDays * sFee);
float mFee= (float) (sMins * 0.25);
float tFee= fee + mFee;
totalFee= String.format(“%.2f”, tFee);
}
return totalFee;
}
8.1.1 Statement Coverage
This is evaluation of the lines of code to determine that each line of code is executed exactly once.
In the unit test for the method of calculating employee fees if for instance:
Example testCase_01
sDays =0
sHours = 5
sMins= 30
sFee= 15
Then the method call for
calculateFee(int sDays, int sHours, int sMins, int sFee)
becomes
calculateFee(0, 5,30, 15);
In this case all the lines of code within the first if condition are executed since the number of days is less than 1. The number of hours are more than 1 so the second if condition is skipped and the statements within the else condition are executed.
The new value for fees is calculated as fee= (sHours*sFee); which is fee= (5*15); resulting in anew value for fee as 75.
Then the value for mFee is calculated using float mFee= (float) (sMins * 0.25);
Which translates to float mFee= (float) (30 * 0.25); which result in mFee= 7.5
Then the new total is calculated as fee + mfee which is 75+ 7.5= 82.5
This is then returned as the total salary.
8.1.2 Branch Coverage
This type of teste explores the IF statement condition and its true or false branches/nodes. It entails validating the true branch and also validating the false branch.
In example of a testCase_02
Example testCase_02
sDays =2
sHours = 6
sMins= 35
sFee= 15
Then the method call for
calculateFee(int sDays, int sHours, int sMins, int sFee)
becomes
calculateFee(2, 6,35, 15);
In this test case the second branch is explored for the first else condition since the number of days are more than 1.
In this case the new value for fee is calculated as fee= (sHours*sFee) + (sDays * sFee); which translates to fee= (6*15) + (24*2 *15);
The value is multiplied by 24 since a day usually has 24 hours and the standard fee is calculated hourly.
The new value for fee becomes 810
Value for mFee is float mFee= (float) (sMins * 0.25); mFee= 35*0.25 = 8.75
Total fee returned will now be 818.75
8.1.3 Path Coverage
This tests all the path and ensures all conditions are traversed at least once.
In example of a testCase_03
Example testCase_03
sDays =0
sHours = 0
sMins= 42
sFee= 15
Then the method call for
calculateFee(int sDays, int sHours, int sMins, int sFee)
Becomes
calculateFee(0, 0,42, 15);
In this test case the first path is explored for the first if condition since the number of days are less than 1.
Since the number of hours is also less than 1, the first path of the next if statement is explored.
Value for mFee float mFee= (float) (sMins * 0.25);
mFee= 42*0.25 = 10.5
Total fee returned will now be 10.5
8.2 Black Box Testing
This is a system evaluation technique which explores the specification of a functional or non-functional requirement without reference to the internal structure of the component.
8.2.1 Black Box Test Case 1- Admin Login
Variables:
Username – String
Password – String
8.2.1.1 testCase_01- Failure
Username: admin, Password: admin23
Authentication Level: Login Failure
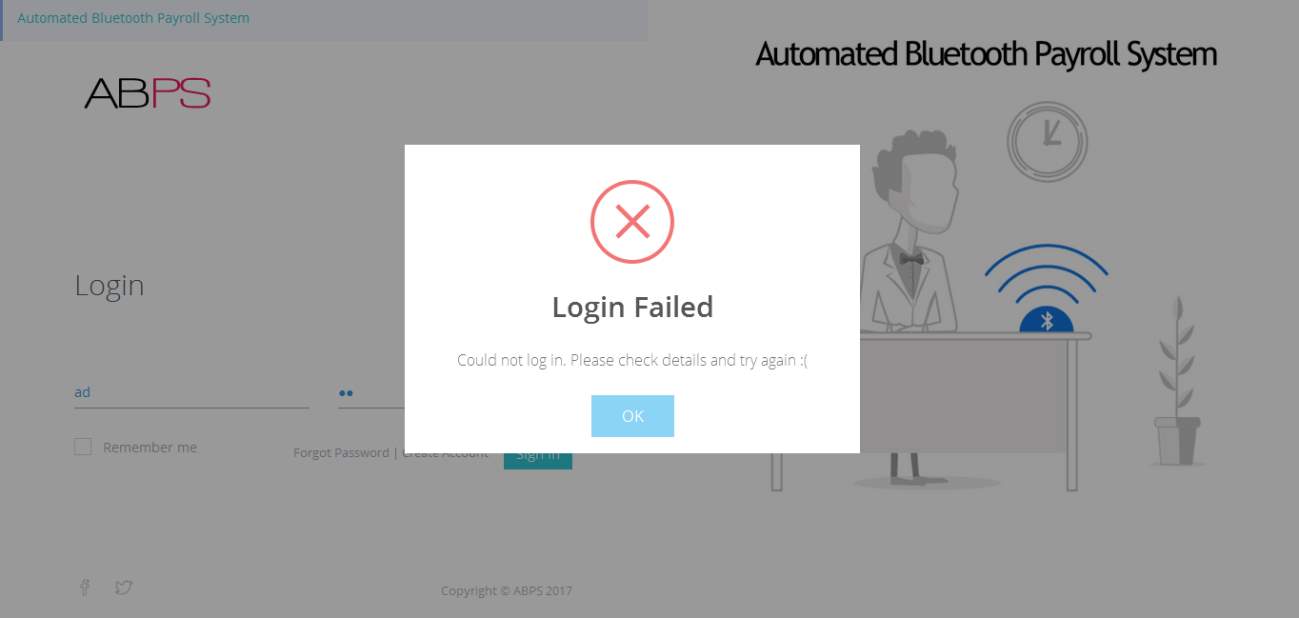
8.2.1.2 testCase_02- Success
Username: admin, Password: admin
Successful Login: Redirected To Main Dashboard Page
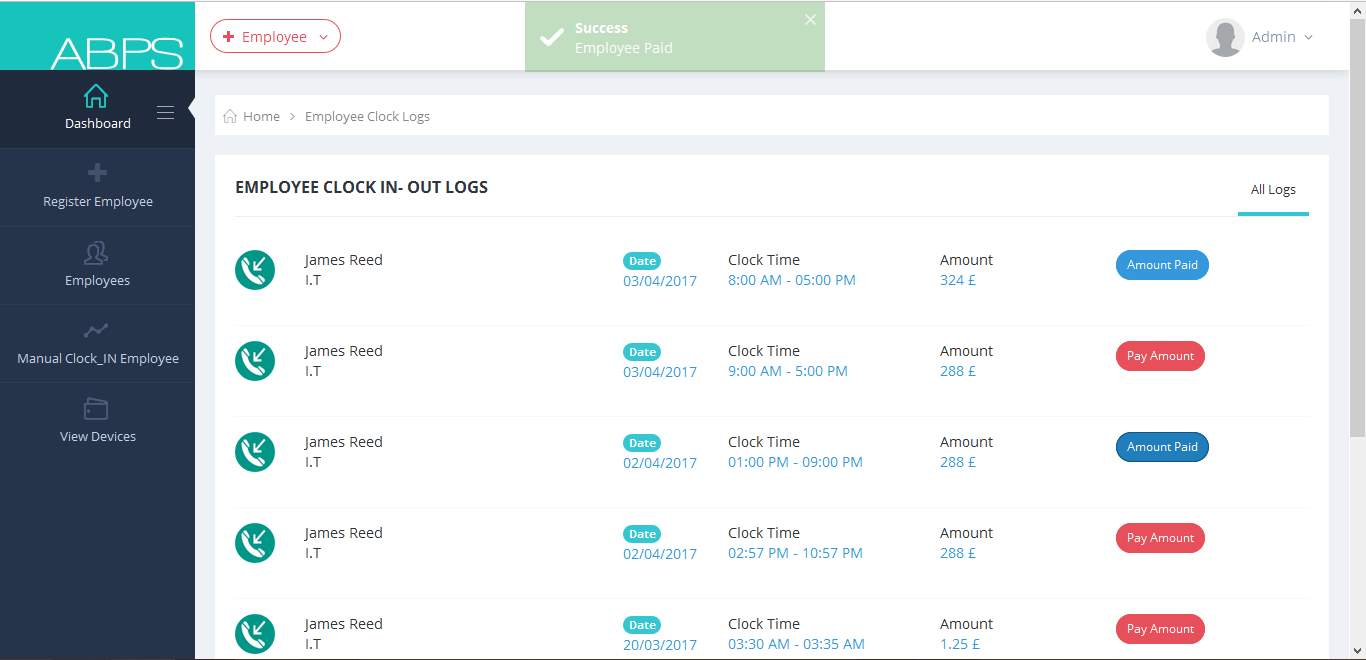
8.2.1.3 testCase_03 : Android Mobile App Retrieve Employee Logs for Specific Date
Parameters: logs_date
Example :logdate=4-04-2017 (4th April, 2017)
Admin Employee Schedule/ Clock IN Logs Result
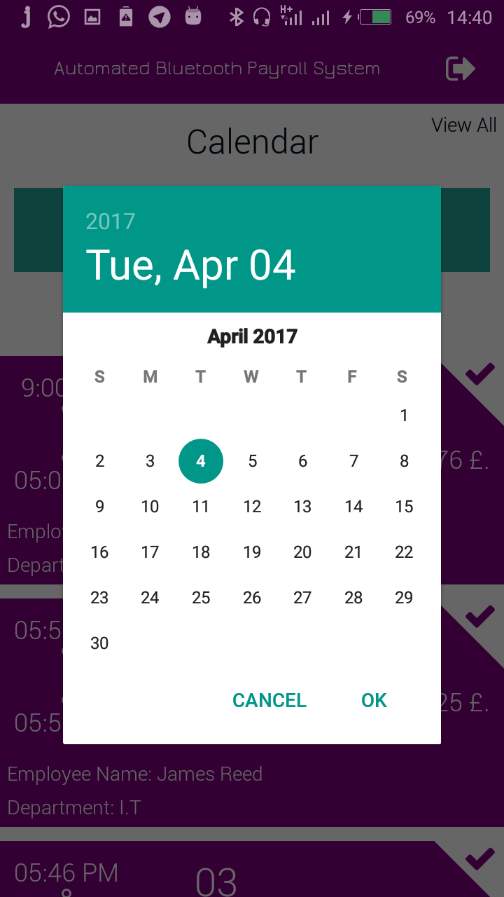
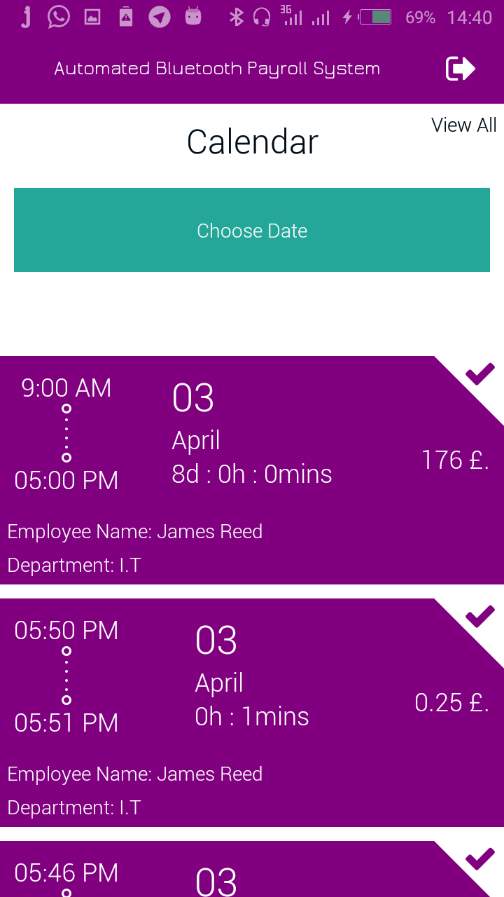
8.3 Accessibility Test
This is a test to ensure that features or some components of the system can be used by people with disabilities.
8.3.1 Keyboard Interactivity Test
When the mouse is unplugged from the laptop when using the web application, it is possible to interact and navigate the system by use of the keyboard only. One can easily use the TAB key to move to the next edit text when manually trying to clock in an employee
Manual Clock IN Employees
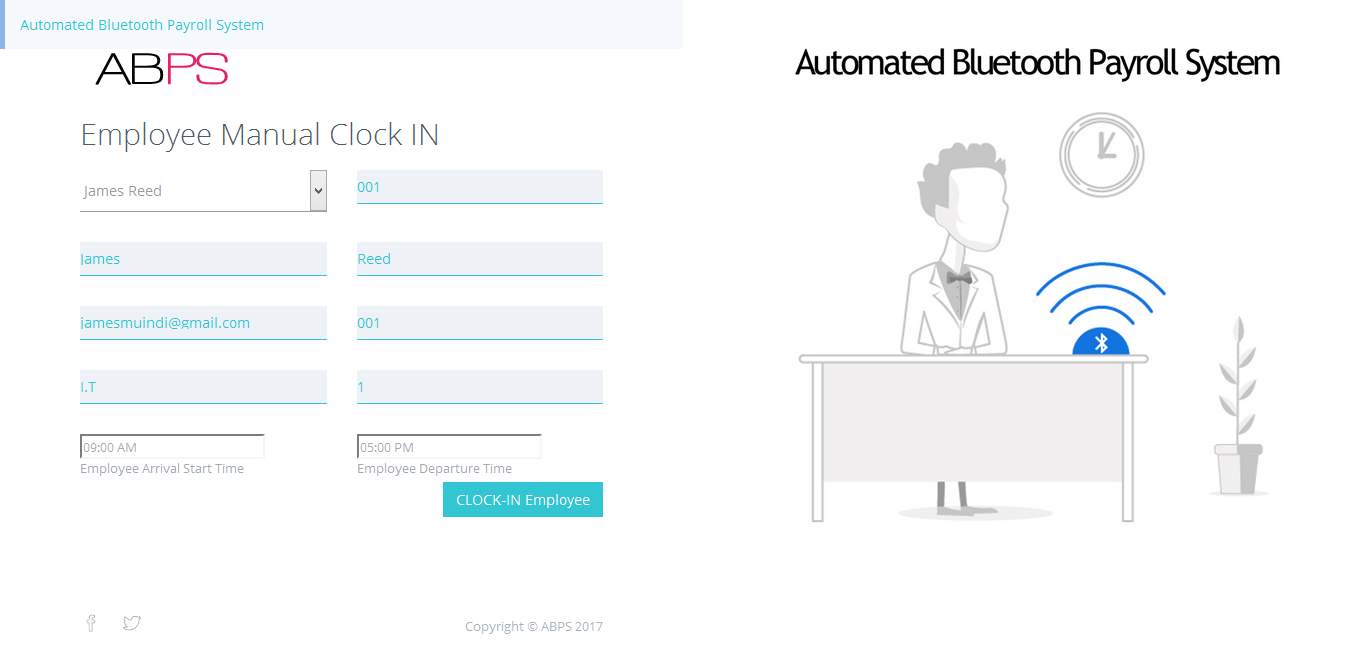
Results:
- It is possible to interact with all controls on the web application/dashboard without the mouse and only use of the keyboard
- Items are focused when use of the TAB key is on their position
- Visual order matches the interaction order.
People with disability who cannot use a mouse to interact with the web can use the keyboards and also persons with impaired vision who often cannot see the mouse pointer can interact with the system using the keyboard comfortably.
8.3.2 High Contrast Color Test
Users with low vision or those with light sensitivity are able to comfortably interact with the system even in high contrast mode.
Result
The system uses Purple as a Primary color and maintains color consistency throughout the application. All foreground and background colors are kept consistent hence making it easier for persons who use the application with high contrast to interact with the system comfortably.
Employee Not Clocked IN/ Session Inactive: Colors Purple & Yellow
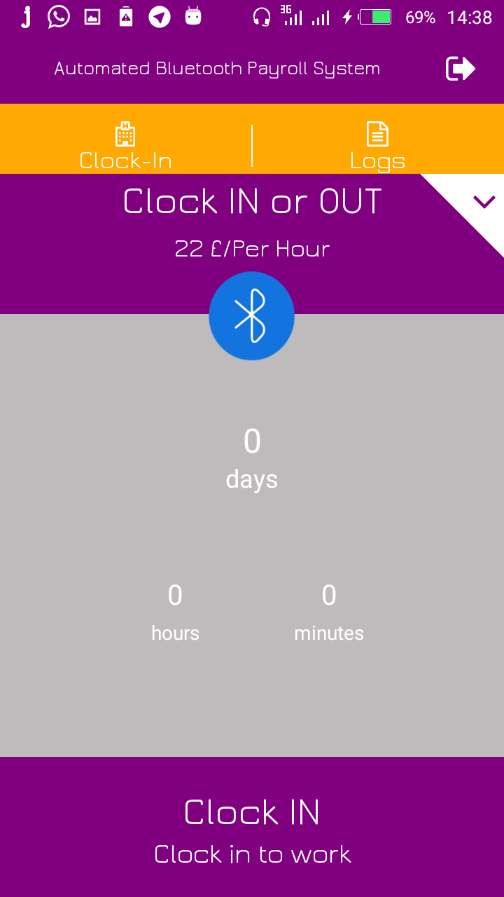
8.4 Summary Testing
| #TEST | Purpose of Test | Test Values (data) | Expected Results | Actual Results | Corrective Action |
| 1 | Calculate Fee | calculateFee(int sDays, int sHours, int sMins, int sFee)
becomes calculateFee(0, 0,42, 15); |
10.5 | 10.5 | Noe Taken |
| 2 | To check the mobile application accepts correct admin | LoginAdmin(admin,admin) | Accepts and logs in Admin and proceeds to Employee Logs Page | Accepts and logs in Admin and proceeds to Employee Logs Page | None Taken |
| 3 | To check the mobile application denies wrong admin | LoginAdmin(Admin,ad) | Denies Admin Login with response “Entre correct username or password” | Denies Admin Login with response “Entre correct username or password” | None Taken |
| 4 | To check the mobile application accepts correct employee | LoginEmployee(user,user) | Accepts and logs in Employee and proceeds to Employee Main Clock/In or Out Page | Accepts and logs in Employee and proceeds to Employee Main Clock/In or Out Page | None Taken |
| 5 | To check the mobile application denies wrong employee | LoginEmployee(user,us) | Denies Employee Login with response “Enter correct username or password” | Denies Employee Login with response “Enter correct username or password” | None Taken |
9.0 Chapter 9: Project Evaluation and Reflection
This final section of the project will address to what extent the investigation as a whole can be deemed a success. In order to do this, both positive and negative aspects of the investigation will be considered, along with what has been learnt from the investigatory process. Improvements and future developments to the project will follow this analysis, focusing on ways in which the project could have been improved, as well as possible extensions and expansions to the project in future research.
9.1Project Success
The success of the investigation in its entirety will be largely based on whether the objectives and deliverables stated in the Proposal have been accomplished, given the initial constraints of the project. How effectively the problems highlighted in the Analysis and Design phase were addressed (in the Implementation phase) will also be examined. Lastly, the overall management of the project, including time management and organisational skills, will be evaluated.
For the most part, the objectives initially set out in the proposal have been achieved. One of the objectives was to design an appropriate testing prototype and plan that would be carried out in the Implementation phase. The actual prototype is found in Chapter 8. I am comfortable in deeming this testing prototype a fulfillment of the objective as it took into account much of the knowledge gained in the secondary research, as well as being logical and methodical in nature. I also believe that all aspects of each test on the prototype were covered explicitly, for example, variables, topology, method, allowing the testing process to be carried out relatively productively. Problems did arise however; these will be covered in more detail in the next section. This example objective exemplifies why I believe the objectives to have been accomplished.
In terms of the deliverables stated in the Proposal, I also judge these to have been completed successfully as each deliverable can be clearly identified within the project report. Further, the attainment of the objectives and deliverables means that in these terms, the project can be considered successful; this also provides credence to the plausibility of the investigation as a whole.
With respect to how effectively the testing results and analysis satisfied the questions highlighted in the Analysis and Design stage (see Chapter 6), I believe that in many ways the tests carried out did accurately address the questions. For example, the issue regarding the provision of automatic clock-in and clock-out via Bluetooth was dealt with by creating a number of connecting devices uniquely identified by their MAC address on the portal and making these available for auto-clocking via the Android Mobile application . The results of building these features were able to determine an approximate level of resources and requirements required when taking into account a number of crucial implementation parameters, such as availability of connectivity devices and both functional and non-functional requirements that may be required to fully implement the Automated Bluetooth Payroll System in a real-world operational business environment. So in this regard, the question was effectively answered.
As highlighted, project management is a crucial factor in the success of any project. In this case, I believe that the project methodology created in Chapter 3 was an appropriate method to follow given the size and nature of the investigation. This method was followed for the most part with only a small number of instances where deviation occurred. The structure of the method also allowed the project to be organized efficiently; before each stage was initiated, the requirements of the stage were considered. This allowed for greater productivity and a more efficient use of time. Also the ability to alter the initial project requirements (i.e. objectives/deliverables) allowed for the necessary flexibility when the project progressed, as elements had to be altered slightly. For example, it was originally intended to test HTTP requests-per-second; however as a result of subsequent research and the Analysis and Design stage, this indicator was deemed unsuitable for testing. In summary, I believe that the project was well managed and that the time and resources available were utilized efficiently and optimally. All major targets and deadlines were met and at no point did project progress fall significantly behind. In some instances though, work rate did decrease as result of other projects and commitments.
Finally, I believe that the investigation as a whole was a detailed and thorough response to the overall aim of the investigation, and that through the secondary research, design, testing and analysis, the extent to which Bluetooth technology can be used to automate payroll systems was comprehensively tackled.
9.2Project Problems
The first of many issues that were encountered during this project was to decide what project to do and why choose that type of area. Originally a GPS employee tracking system was on my mind. I told my supervisor this and although I had high hopes I got much needed feedback. The feedback I received changed my mind immediately as it made sense to use nearer field communication such as Bluetooth. With GPS it was able to be at a completely different location but still apparently be at the place required. This was due to the poor accuracy of GPS compared to Bluetooth. It was difficult for me to implement the Android app as I did not have much experience developing Apps. A lot of help from my supervisor & online assistance such as YouTube, Online forums and websites made everything possible for my project as when I had coding problems I could ask my supervisor or research online, more often than not I would get an answer. Even though that on the whole I feel the project was executed well, inevitably a number of issues were encountered along the way. One of the main problems occurred during implementation, for example being able to implement multithreading of the Bluetooth connections to make it possible to clock-in from multiple devices proved to be a challenge. The issue was countered by constructing a single thread for allowing connectivity to one device after Bluetooth discovery. This then made it possible for accurate, consistent connection to one device for clocking in and clocking out.
No other critical issues were encountered in the other sections of the investigation, though one of the more challenging aspects of the secondary research phase was filtering through all the materials gathered. A considerable amount of resources were acquired for research, including white papers, technical documentation, conference papers, books and websites, and processing each one and extracting the most useful and pertinent information was a somewhat difficult task.
9.3Learning Outcomes
As this project was essentially the largest project I have undertaken there was a learning curve to a degree in terms of project management. Subsequently, possibly the most noteworthy skills learnt during the investigation are that of time management and organisation. Time was a crucial aspect of the project to manage as a mismanagement of this could have led to failing to meet deadlines or falling behind schedule. For the most part I believe the correct work rate was maintained, moreover I believe that as the project progressed into the different stages I gradually improved my time management skills. So, the most efficient part of the project was the Implementation phase as I had learnt from previous phases the most efficient way to utilize the time available, as well as balance other work/module commitments.
Other areas in which I feel have improved as a result of the investigation are my testing and analytical skills. Prior to this investigation I had not undertaken a project of this type before and so initially, my testing and analytical skills required might have been lacking somewhat. After completing all the testing and analysis though I believe that these skills have been significantly developed. This also gives me greater confidence that in situations where I need to carry out primary research and analysis again, my competency level is enhanced as a direct consequence of this project.
This project was also the first time I had used a project management method to guide me from start to finish. All previous projects have not utilized any official structured methodology. I consider this introduction to project management methods to be an important one as from secondary research, I have discovered that they are widely used in Industry; therefore it seems likely that at some point I will be using them in employment. Thus, relatively early experience in using such methods can only be beneficial.
Lastly, I believe that I have significantly increased my knowledge with respect to the topics relevant to this investigation, i.e. Bluetooth technology. Many of these technologies, such as Bluetooth protocols, were directly related to my degree which in turn is beneficial both in terms of my continuing education and employability. On the other hand a number of topics would be considered outside the scope of my degree, such as threading; I believe increased knowledge in these areas just as beneficial as widening my overall technical knowledge will again put me in greater stead academically and in industry.
9.4Improvements
In terms of how I feel the project could be improved upon if attempted again, I would firstly attempt to create a more realistic corporate network environment. In this investigation, it was created through the use of a single clocking device instance where different device types were distinguished by their MAC address. While this method fulfilled the criteria set out in Analysis and Design in a sense, it was limited in that all the data and connections on the network was simulated by only two clients the app and a single clocking device, where in actuality it would be sourced from 10s or perhaps 100s of employee devices. Of course a simulation on these scales would probably still be infeasible given the time and resources allocated in this investigation, however to increase the accuracy of simulation I could use three employee devices each for clocking in (giving a total of 9 clients). Thus, the workload of the devices in the system would increase slightly with more sources and destinations for traffic.
Another way in which I would like to improve the simulation would be to create multi-threading and sockets for allowing clock-in and clock-out via multiple devices. This would make it possible to make listeners for connectivity and connection lost instances so as to keep track of when the employee is within the organisation compound or if they have left.
In relation to improving aspects of project management, I feel that the review process after each stage could have been documented better. The project methodology stated that this review process would occur, and it did, but was not actually documented. This was mainly down to time constraints and prioritizing other areas of the project. However I feel that the investigation would have benefitted from this documentation and so if I were to undertake this project again, I would make sure time was allocated for this process.
9.5Future Work
Even though I believe that I appropriately addressed the initial premise of the investigation, there is enough scope in the premise for additional work to be carried out. This is primarily down to the term “Bluetooth protocol performance”, for which there is no definite definition or all-inclusive test. As such, more Bluetooth protocol performance metrics could be examined and analyzed. Also Bluetooth socket analysis is another aspect that secondary research demonstrated may have some indication as to some performance metrics of the automated payroll system. For example, many differing socket topologies and setups exist. This, in addition to the fact that many types of Bluetooth adapters exist, means that even when similar system settings are used, the resulting throughput produced might differ significantly.
Subsequently, these factors present a number of areas for future expansion. One of which is the use of a multitude of Bluetooth connection devices from different manufacturers. Implementing a testing plan using perhaps 3 or 4 of these, using the same settings, should produce a wider variety of results. This is largely down to the fact that each vendor may tweak the precise protocol settings slightly. This type of investigation is useful when planning the implementation of a system as a single manufacturer may want to be used throughout the system.
Finally, another area in which I believe the project would benefit from expansion is a greater use of security policies, and test and analyses how they affect Automated Bluetooth Payroll System. The main security option implemented in this investigation was the use of MD5 encryption on the backend, which logically secures passwords and data at the database level. However security can also be enforced at the Android App level via certain means such as encryption, certificate pinning and transmission of data via SSL to avoid Man-in-the Middle attacks.
Aghaeepour, N., Finak, G., Hoos, H., Mosmann, T.R., Brinkman, R., Gottardo, R., Scheuermann, R.H., FlowCAP Consortium and DREAM Consortium, 2013. Critical assessment of automated flow cytometry data analysis techniques. Nature methods, 10(3), pp.228-238.
APM. (2010). [Online]. APM Definitions. Available from: http://www.apm.org.uk/Definitions.asp. [Accessed: 27th February 2017].
Bayaki, E., Lampe, L. and Schober, R., 2008. Performance evaluation of bluetooth systems with LDI, modified LDI, and NSD receivers. IEEE Transactions on Vehicular Technology, 57(1), pp.157-168.
British Computer Society. (2004). Code of Good Practice Version 1. [Online]. Available from: http://www.bcs.org/server.php?show=conMediaFile.395. [Accessed: 23 October 2010].
British Computer Society. (2006). Code of Conduct for BCS Members. [Online]. Available from: http://www.bcs.org/server.php?show=conMediaFile.393. [Accessed: 23 October 2010].
Charvat, J. (2003). Project Management Methodologies-Selecting, Implementing, and Supporting Methodologies and Processes for Projects. Hoboken, New Jersey, USA: John Wiley & Sons, Inc.
Duparc, J., Moser, T., Sieber, P., Thorleifsson, H., Timalapur, A.K., Guenther, F. and Bold, A., Sap Ag, 2013. Managing consistent interfaces for employee time event and human capital management view of payroll process business objects across heterogeneous systems. U.S. Patent 8,515,794.
Goetsch, D.L. and Davis, S.B., 2014. Quality management for organizational excellence. Upper Saddle River, NJ: pearson.
Heide, L., 2009. Punched-card systems and the early information explosion, 1880–1945. JHU Press.
JISCinfoNet. (2003). [Online]. An Introduction to PRINCE2. Available from: http://www.jiscinfonet.ac.uk/infokits/project-management/prince2.pdf. [Accessed: 25 October 2010].
Koren, D. (2011). [Online]. Secure Networking Protocols Portal. RAD University. Available from: http://www2.rad.com/networks/applications/secure/main.htm [Accessed: 27th February 2017].
Krishnan, P., Huska, R. and Narayanswamy, R., Replicon, Inc., 2015. Systems and methods for capturing employee time for time and attendance management. U.S. Patent 9,111,402.
Leffingwell, D. & Widrig, D. (1999). Managing Software Requirements: A Unified Approach. New Jersey, USA: Addison Wesley Longman, Inc.
Mack, N, et al. (2005). Qualitative Research Methods: A Data Collector’s Field Guide. USA: Family Health International.
Mohamed, M.A., Abu El-Azm, A.E.S., El-Fishawy, N.A., El-Tokhy, M.A. and Abd El-Samie, F.E.S., 2008. Optimization of Bluetooth frame format for efficient performance. Progress In Electromagnetics Research M, 1, pp.101-110.
Molnár, B., Zsigmond, M., Suhajda, Z. and Fekete, I., 2014. Amnis-Design and Implementation of an Adaptive Workflow Management System.
Moniz, A. and de Jong, F., 2014, April. Sentiment analysis and the impact of employee satisfaction on firm earnings. In European Conference on Information Retrieval (pp. 519-527). Springer International Publishing.
OGC. (2009b). Prince 2 Background. [Online]. Available from: http://www.ogc.gov.uk/methods_prince_2__background.asp. [Accessed: 17 February 2017].
OGC. (2009c). Prince 2 Overview. [Online]. Available from: http://www.ogc.gov.uk/methods_prince_2.asp. [Accessed: 02 February 2017].
Prince2.com. (2011). [Online]. PRINCE2 Processes — The PRINCE2 Process Model. Available from: http://www.prince2.com/prince2-process-model.asp. [Accessed: 27 February 2017].
Rapp, A.A., Bachrach, D.G. and Rapp, T.L., 2013. The influence of time management skill on the curvilinear relationship between organizational citizenship behavior and task performance. Journal of Applied Psychology, 98(4), p.668.
Riordan, R M. (2005). Designing Effective Database Systems. USA: Addison-Wesley Professional.
Rozenberger, A. (2005). [Online]. Computer Security. Available from: http://www2.rad.com/networks/2005/computersecurity/main.htm [Accessed: 27th February 2017].
Scarfone, K. and Mell, P., 2007. Guide to intrusion detection and prevention systems (idps). NIST special publication, 800(2007), p.94.
Shoewu, O. O. M. Olaniyi, and Lawson (2011), “Embedded Computer-Based Lecture Attendance
Management System”, Journal of Computing and ICT (Journal of IEEE Computer Section), 4(3):27 – 36
Soewito, B., Gaol, F.L., Simanjuntak, E. and Gunawan, F.E., 2015, August. Attendance system on Android smartphone. In Control, Electronics, Renewable Energy and Communications (ICCEREC), 2015 International Conference on (pp. 208-211). IEEE.
Stake, R E. (2010). Qualitative Research: Studying How Things Work. Guilford Press.
Trkman, P., 2010. The critical success factors of business process management. International journal of information management, 30(2), pp.125-134.
10.1 Table of Figures
- Figure 1: Shows an Automated Timesheet Report Process Flow
- Figure 2: Shows the Secure Network Layer Protocol Tunnel
- Figure 3: Shows the Bluetooth Security Manager Layer Architecture
- Fig 4: Waterfall model of software development (Leffingwell & Widrig, 1999, p134)
Fig 5: Waterfall development methodology (Charvat, 2003, p124) - Fig 6: Waterfall development methodology (Charvat, 2003, p124)
- Fig 7: PRINCE2 Process Model (Prince2, 2010)
- Figure 8: Shows an example of an Automated Time Sheet to Payroll Process
11.0Appendices
11.1Appendix A — Bluetooth Communication
Bluetooth can be defined as a wireless communication standard that enables devices to exchange data over short distances. Most Bluetooth devices work within a range of 10m -100m and often transmit radio waves within these range to facilitate communication between devices. Bluetooth communication is often used to provide high quality streams under efficient power consumption by use of BR/EDR (Basic Rate/Enhanced Data Rate) which ensure high quality transmission of data over a stream.
10.1.2 RF Protocol
RF protocol can be defined as Radio Frequency Protocols and these are a set of defined rules that provide a standard as to how radio wave frequencies transmit and receive data. Bluetooth communication relies heavily of RF protocols in pairing and transmission of data between connected devices.
11.2 Appendix B- Project Methodologies
The Association for Project Management (APM) defines Project Management as “the process by which projects are defined, planned, monitored, controlled and delivered such that the agreed benefits are realized” (APM, 2010).
Charvat (2003, p3), a project management consultant, defines it as “a set of guidelines or principles that can be tailored and applied to a specific situation.”
Project management methodologies are all designed to address the many problems associated with managing and running projects. General, methodologies follow a similar structure of splitting projects up into clearly defined stages. Also, many methodologies contain common stages, for example, planning, implementation, testing and delivery.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Technology"
Technology can be described as the use of scientific and advanced knowledge to meet the requirements of humans. Technology is continuously developing, and is used in almost all aspects of life.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




