Business Continuity Planning: Cyber Security Management
Info: 8246 words (33 pages) Dissertation
Published: 2nd Sep 2021
Tagged: Cyber SecurityBusiness Strategy
ABSTRACT
In today’s ever advancing world of technology, cyber attacks on organizations critical assets can cause serious losses and damages. Nowadays it is common to hear about businesses closing down after major attacks because they were unable to stand back on their feet after such cyber incidents or disasters. Unexpected or unplanned downtime and loss of important data can originate from a number of sources including power failures, natural disasters, human errors, malicious acts, etc. Business continuity entails the planning and preparation for such unexpected adverse situations in order to avoid the disruption of the activities of an organisation and maintain availability of its services. In the past, people thought of business continuity as simply being about getting computers, information and network back online. A good example in the financial sector is Banks who in the past outsourced their technology to service bureaus so as not to worry about disaster recovery or business continuity process. Today, business continuity not only includes protection of data but also the facilities and the people and even ensuring that the service bureaus have a rigorous business continuity plan in place. At the end of the day, organisations don’t want to lose their clients or go out of business so they must ensure that everything is well planned for the unexpected.
In every organization, the business continuity planning team must work closely with the information security team to produce an efficient recovery plan. Together, they must ensure that all or the same physical and information security mechanisms deployed at the primary site or main facility (e.g. Firewalls, antivirus, data encryption, etc) are implemented at an alternate location. In practice, it does not make sense to protect every single asset; therefore companies should be able to prioritize their business units. Once the different business units have been prioritized, a business impact analysis (BIA) should be developed. Every employee in an organization must be part of the business continuity plan but most especially the executives and the board of directors. Business continuity does not generate revenue but rather it is an expense, hence the need for the directors and executives to be actively involved in the entire process. In addition to a steering committee to help prioritize the business activities, companies can equally have a crisis management team who will be in charge of making recommendations on decision making during an incident or a disaster. Another important consideration should be a definition of governance which is the set of programs, policies and the responsibilities of each individual within the organization during the business continuity process.
Keywords: Business continuity planning phases, Business continuity plan sub-plans, Business impact analysis, Disaster recovery, Alternate sites, NIST 800-34, ISO27031, ISO22301
Table of Contents
II. BUSINESS CONTINUITY PLANNING METHODOLOGY
II.1 BUSINESS CONTINUITY STRATEGY
II.2 BCP ROLES AND RESPONSIBILITIES
II.3 BUSINESS CONTINUITY PLAN SUB-PLANS
II.4 BUSINESS CONTINUITY PLAN PHASES
II.4 BUSINESS CONTINUITY PLAN STRUCTURE
II.4.1 THE ISO 22301 STANDARD: 2012
II.4.2 CONTENTS OF A BUSINESS CONTINUITY PLAN
II.4.3 BUSINESS CONTINUITY PLAN MANAGEMENT
II.4.4 BUSINESS CONTINUITY BEST PRACTICES
III. CASE STUDY: BUSINESS CONTINUITY PLAN FOR A SMALL ORGANIZATION
III.1 PLANNING THE ORGANIZATIONAL STRATEGY
III.2 BUSINESS IMPACT ANALYSIS
III.4 DEVELOPMENT AND IMPLEMENTATION
I. INTRODUCTION
Business continuity is about identifying parts of business services and activities that an organisation will not want to lose when a disaster occurs such as information assets, employees and business premises. The need for a business continuity plan which will elaborate on how to maintain these assets in the event of an incident is crucial. Most organizations without effective plans for recovery or continuity in place go out of business after a disaster. Any incident, large or small, whether it is natural, accidental or deliberate, can cause major disruption to services but if the necessary plans are made before hand, the organization will be able to stand back on their feet within the shortest possible time.
An effective business continuity plan should be able to answer the following questions:
- Where is the business most vulnerable and what would be worst incident for the business?
- What are the most likely and greatest risks to the business and what effect will it have on the business?
- What can be done to minimise the risk of it happening or damage caused?
- What strategy should be implemented to ensure service continuity after a disaster?
The next sections of this document will focus on describing business continuity planning strategies and processes and also elaborate on how to develop, write and execute an effective business continuity plan.
II. BUSINESS CONTINUITY PLANNING METHODOLOGY
This research is based on secondary data reassembled from previous research, online journals, text books, BCP consultant websites, annual reports of institutes like NIST and ISO who are developing the standards and frameworks for business continuity.
II.1 BUSINESS CONTINUITY STRATEGY
Organizations should know whether they need to be fully or partially operational to survive after a major incident/disaster. A major incident or disaster can cause:
- Loss of critical records
- Loss of key people
- Computer system failure
- Computer virus/hacking
- Theft/fraud
- Failure of key equipment
- Brand damage
- Loss of key customers
- Loss of primary workspace
- Market shifts
- Product recalls
- Police activity
Consequences of these scenarios [1] include loss of stock / production capability / workspace, inability to service customers, bankruptcy, redundancies etc. The quicker operations recover, the better the chance of survival of the organization. Depending on the nature of services provided, some organizations might decide to shutdown their business activities till after the resolution of the incident while others can afford to run the business through the incident. The BCP should provide all the information required to ensure proper management of the immediate incident, recovery and continuity of the critical activities identified in the risk assessment process. Separate incident response plan, business recovery and continuity plans could be implemented for a large organization. For a small organization a single plan which incorporates all three plans may be sufficient.
Key strategies involved in the business continuity planning process include:
- Identifying critical activities to be recovered and timescales for their recovery
- Ensuring plans are easily accessible and copies are kept on and off site.
- Careful statement of purpose and scope of plan
- Proper documentation of roles of individuals
- Putting in place arrangements (including contact details and addresses) so that the relevant teams are mobilized as fast as possible when an incident occurs
- Building up strategies for communicating with staff, stakeholders and customers
Assuming the incident/disaster causes a loss of primary workspace either short term or long term, how then does the business keep functioning until the new office is ready?
- Old/current premises
The old premises might require minimal planning and arrangements for activities to continue.
- New premises
The organisation might procure alternate premises within a time constraint
- Shared workspace
- Work from home capability
After the BCP has been developed, it will be vital to update and test the plan with all the staff so that each employee is fully aware of their role and responsibilities. BCP testing can be carried out by:
- Walkthrough: this involves gathering the BCP team, going through the plan and checking for problems challenges
- Table top: this involves the BCP team using the plan to respond to a given incident/disaster scenario
- Simulation: this testing method uses a scenario to validate the plan while involving others.
II.2 BCP ROLES AND RESPONSIBILITIES
According to ISO 22301, business continuity plan [2] is defined as “documented procedures that guide organizations to respond, recover, resume, and restore to a pre-defined level of operation following disruption.” (clause 3.5).1It involves the identification, acquisition, documentation and testing of procedures and resources to guarantee the continuity of the activities of an organisation in the event of an incident or disaster. In other words it is involved with risk mitigation and business recovery planning. Such a plan must include authorities to invoke, instructions and communications strategy to assure continuity of operations. Inside an organization, BCP roles and the responsibility fall onto different categories of people, from the senior management to the BCP steering team.
Senior Executive Management
- Responsible for approval of plans, setting up the business continuity policy, prioritizing critical business functions, providing funding, resources and personnel, review results of tests and maintenance carried out on plans.
Senior Functional Management
- Responsible for the development and documentation of maintenance and testing strategies, identification and prioritization of critical systems, monitoring the progress of the plan, ensuring BCP tests are done and creation of teams for the execution of the plan.
BCP Team
- This a team appointed by management. They conduct the BIA and work with critical department representatives. They are also responsible for dealing with the immediacy of the disaster, getting alternate facilities for the restoration of critical services and the return of operations to original facility. Each team member should understand the objectives of the plan and be familiar with the department they are responsible for.
II.3 BUSINESS CONTINUITY PLAN SUB-PLANS
The BCP serve to protect, recover and sustain the organization [3].
PROTECT sub plan
This sub plan consists of the crisis communications and the incident management plans. On one hand, the crisis communications plan focuses on addressing notifications/communications with personnel and the public. On the other hand, the incident management plan provides procedures for minimizing loss of life and property in response to a physical threat; it does not focus on the business or IT process but rather on the personnel and property particular to an affected facility.
RECOVER sub plan
The recover sub plan consists of:
- Business Recovery Plan (BRP): steps for the recovery of business operations immediately after a disaster;
- Continuity of Support Plan/IT Contingency Plan: provides procedures and capabilities for the recovery of major applications and IT system disruptions;
- Incident Response Plan: provides procedures and capabilities for the recovery of business activities from incidents. It focuses on information security responses to incidents affecting networks;
- Disaster Recovery Plan (DRP): The purpose of this plan is to provide procedures necessary to return an organization’s essential and strategic functions to normal operating conditions.
SUSTAIN sub plan
This also called the continuity of Operations Plan (COOP). It provides procedures to facilitate recovery at an alternate site. There are different kinds of alternate sites [4]:
- Hot site: This is a fully operational and equipped backup site that has all hardware, software, workstations, servers, network equipments, etc necessary to have the organization’s activities running within minutes. The hot site can be directly connected to the production network and it generally keeps real time copies of data in the production network. The cost of setting up and maintaining such a site is quite high as regular maintenance of equipments is required, therefore should be considered for organizations or activities requiring minimum downtime.
- Cold Site: This is an empty site/space with necessary electrical installations, heating and air-conditioning systems that are capable of handling the operational load of the organization. It does not have any network equipment and facilities, hence might take time to set up for full operation.
- Warm Site: This site is not completely equipped like a hot site; it has no installed software applications but contains a portion of the necessary equipment and resources to restore business activities. They are not directly connected to the production network and may take several hours or days from when a disaster happens for it to be set up.
- Timeshare: This site is co-leased with a business partner or sister organization hence reduced costs. Inconveniencies may include difficulty in negotiation and a possibility that two or more participants might require the site at the same time.
- Service Bureau: They provide working space to organizations for a fee.
- Mutual Agreement: Two organizations can come together and sign a contract wherein each party agrees to assist each other during a disaster.
II.4 BUSINESS CONTINUITY PLAN PHASES
A strong business continuity plan needs to address responsibility, authority, priorities and testing. NIST’s “special publication 800-34, Rev. 1: Contingency planning guide for federal information systems” and ISO 27031 among others provide guidelines for planning of incidents and disasters that require a BCP .There are several phases in the BCP:
- Project Initiation: This phase involves obtaining senior management support, securing funding and resource allocation, determining the scope of the plan, naming BCP coordinators and team members;
- Business Impact Analysis (BIA): The BIA is initiated by the BCP committee and identifies and prioritizes all business activities based on their criticality. A BIA analyses the quantitative (loss of revenue, capital, etc) and qualitative (loss of reputation, market share, service quality, etc) damages an organization can sustain in the event of an incident. The objectives of the BIA include identification of all business assets, analyses of the impact the organization can handle, defining outage times for critical and non critical activities and lastly, establishing preventive controls. Recovery for activities or processes with the highest potential operational and financial impacts should be given higher priorities. The results from the BIA can then be used to build up recovery plans.
When conducting a BIA, the following metrics need to be defined:
- Service level objectives
- Recovery point objective (RPO is tolerance for loss of data)
- Maximum tolerable downtime (MTD)
- Mean time between failures (MTBF)
- Mean time to repair
- Minimum operating requirements
The management should establish recovery priorities for business processes that identify succession plans, MOAs/MOUs (Memorandums of Agreement/Understanding), Technologies, Facilities, communication systems, etc.
- Recovery Strategy: based on themetrics covered in the BIA
- Plan Design and Development: This phase is where the actual plan is written. It addresses responsibility and authority of staff, priorities and testing processes;
- Implementation: Both hard and soft copies of plans should be stored in multiple locations. The plan could be distributed according to the roles of staff, for instance accounting plan, IT plan, human resources plan, payroll plan, etc;
- Testing
- Maintenance
II.4 BUSINESS CONTINUITY PLAN STRUCTURE
II.4.1 THE ISO 22301 STANDARD: 2012
ISO 22301 aims at assisting organizations [5] to be prepared and more confident to handle outages or interruptions in their services and continue their operations. It presents a scheme to help organisations protect against, respond to, and recover from incidents. ISO 22301 also aims at assisting organizations in the design of a business continuity management system that responds to its needs. Several countries including the United Kingdom have started replacing their existing national standards with the ISO 22301.
According to Dr. Stefan Tangen, Secretary of the ISO technical committee that developed the new standard, enforcing the ISO 22301 standard not only enables organizations to prove to customers, lawmakers, regulators, etc that they are observing good practices in their business continuity planning but It may also be used within an organization to measure itself against good practice, and by auditors wishing to report to management.
II.4.2 CONTENTS OF A BUSINESS CONTINUITY PLAN
A Business Continuity plan is developed to ensure that business operations return to normal as fast as possible in the event of a major disruption. A major incident can bring business to a standstill hence the need of a business continuity plan. A plan should identify all the essentials for keeping the business running and include processes to assure minimum down time and effectively manage a crisis. The business continuity plan should contain information required for an organization to keep functioning after an incident or a disaster. The size and complexity of such a plan varies from one organization to the other. Below is a sample business continuity checklist [6]:
Table 1: Sample Business Continuity Plan Checklist
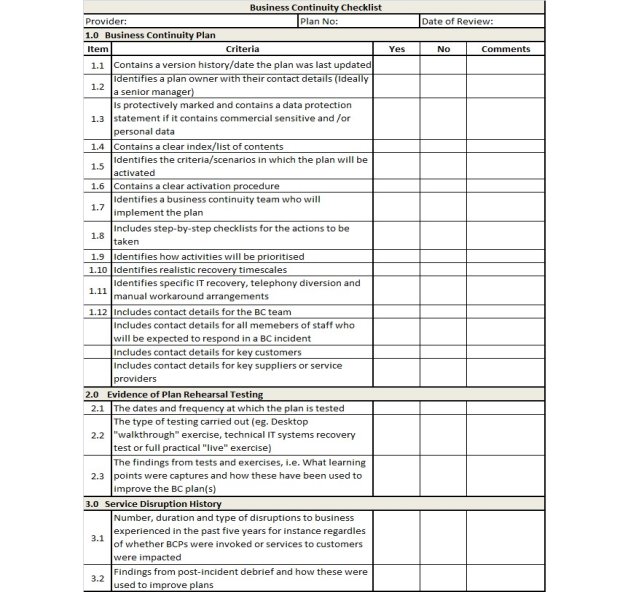
As a summary, a BCP should include the following sections:
II.4.2.1 Introduction – distribution list, summary and glossary
The introduction section of a BCP carries information about the users and version (date of last update), location of the plan, its objectives, a summary and definition of terms found in the plan [7].
- The distribution list details where duplicates of the plan could be found in case the original copy is not available at the time of the incident, users of the plan and any other documents.
- The summary gives a global overview and objectives of the BCP and also the expectations from the employees in the course of executing the BCP.
- The glossary explains the key vocabulary in the BCP.
II.4.2.2 Policy statement and reference documents
This includes references to the Business Continuity Policy, BIA, BCS, etc.
II.4.2.3 Roles and responsibilities
This section outlines the tasks assigned to each individual involved in the BC process. For instance staffs in charge of purchases, communication, evacuation, etc. It should clearly state the team members who will be called to manage the incident, monitor the maintenance of critical activities and follow up post incident recovery progress. This section should include a step-by-step checklist for the actions to be taken and priority levels should be assigned to each action.
II.4.2.4 Key contacts and communication
This contains the phone numbers and addresses of those involved in the activation and realization of the BCP (internal staff, subcontractors and service providers, emergency services, etc). The various means of communication and timings during the incident and those in charge of propagating information to the right people or places should be clearly mentioned.
II.4.2.5 Business impact analysis and risk management plan
The BIA contains the resources [8] needed to support each critical business activity, the impact of ceasing to perform these activities, how long the business could cope without these activities. The risk management plan identifies the key activities, the risks associated with these activities and their mitigation techniques. It outlines the potential risks for the business, analyses the likelihood of occurrence of these risks, prioritizes the risks, estimates the impact of the risk and identifies mitigation strategies.
II.4.2.6 Response plans
- Incident response plan: The IRP should illustrate the initial steps to be taken in order to minimize the loss or damage caused by the incident. It contains information on how to react immediately before, during and after an incident. The IRP may include the plan activation, incident response team, and the communications team.
- Disaster recovery plan: The DRP focuses on recovering the information and communication technology infrastructure after an incident within a realistic time frame so as to minimize losses. The recovery plans for activities should provide a step-by-step description of actions and responsibilities for recovering data, software and hardware and infrastructure.
IRP and DRP are and generally included as an annex to the BCP. Each response plan should list all the business activities, with precise RTO for each, when the plans should be activated or deactivated, the method of activation, details of which staff are authorised to activate the plan, etc.
II.4.2.7 Physical sites and Transportation
This section indicates the primary and alternative sites, where the assembly points are, routes and the means of transportation to alternative sites.
II.4.2.8 Required resources
This is a list of staff, service providers, facilities, infrastructure, information, equipment, etc. required for the recovery procedure and who is responsible to provisioning of each.
II.4.2.9 Testing, evaluation and maintenance
This section includes details about how you will test the BCP so as to ensure the accuracy and effectiveness of the plan. It includes schedules for performing regular tests and updates. Changes in hardware/software, laws, and environment warrant regular review and maintenance of the plan. The dates and frequency at which the plan is tested, findings from previous tests and exercises, etc could also be included. Tests could be performed through exercises, drills or auditing.
- A checklist test involves the distribution of copies of plan to the different departments of the organisation and obtaining review from functional managers
- A structured walk-through or table top test consists of bringing together representatives from each department go through the plan
- A simulation test goes through an actual disaster scenario
- A parallel test moves portions of systems to alternate site for processing
- A full-interruption test shuts down the original site and moves processes to an offsite facility
II.4.2.10 Restoration and resumption of activities from temporary measures
This section focuses on how to restore the business back to its original state or site after resolution of the incident.
II.4.3 BUSINESS CONTINUITY PLAN MANAGEMENT
The business continuity plan is a document that needs to be regularly tested and updated with improvements. This will help in the evaluation of its reliability and robustness in response to an incident. Updates to be BCP are made whenever there are changes in the activities or location of the business. The following strategies could be implemented for testing the BCP:
- Trainings and drill exercises : Adequate trainings should be provided to staff involved in the execution of the BCP
- Meetings: Meetings should be held to remind staff of their duties and responsibilities in the event of a disaster especially when modifications are made to the BCP
- Scenario testing: It is a good practice to simulate incidents or disasters as this will give a better idea of the effectiveness of the plan and also enable staff to be more familiar with BCP procedures in the event of a real incident. Nevertheless, scenario testing should be conducted during off peak hours to avoid creating a real disaster.
- Prevention – This incorporates the identification of risks and the likelihood or effects of its occurrence
- Preparedness – This is the process of identification and prioritization of critical business activities
- Response – Immediate actions taken to minimize the effects of an incident
- Recovery – Actions taken to recover from an incident so as to reduce RT and service disruptions
II.4.4 BUSINESS CONTINUITY BEST PRACTICES
Thinking ahead enables organizations to prepare for the worst and put some arrangements in place to speed up their response to an incident. They might even be able to avert the disaster in the first place by identifying the need for some additional resilience. Business Continuity is all about considering what action would achieve minimum disruption to an organization in a given scenario, and then making sure that those actions are possible. To do that, we consider people, infrastructure and plans. The following considerations should be made for a BCP:
- Important data should be regularly backed up in a secured environment (eg. In the cloud or offline). Backups should be tested from time to time to ensure their integrity
- Perform periodic penetration tests, security audit and vulnerability assessments
III. CASE STUDY: BUSINESS CONTINUITY PLAN FOR A SMALL ORGANIZATION
This case study will illustrate in details the steps involved in the creation of a BCP for an imaginary company “Horizon Health”. The company Horizon Health focuses on securing in databases electronic health information of individuals and ensuring data is confidential, unaltered and available to the right individual. The company is located in central London and has 50 staffs. Ninety percent of the employees live within London while the rest live within the UK. The company has five departments. Its customers include patients, government agencies, educational establishments, medical practitioners and insurance companies. This guide can be useful to small companies who need to implement or improve their BCPs. [10]
The business continuity planning process will go through five stages:
- Planning the Organizational Strategy
- Business Impact Analysis
- Controls
- Development and Implementation
- Testing and Maintenance
III.1 PLANNING THE ORGANIZATIONAL STRATEGY
It is at this stage that the BCP project is initialized, meetings with senior management are held, BCP team members are designated and project scheduling is done.
- Project Initialization: The newly appointed Information Security Manager (ISM) has been given an outdated emergency plan with a list of individuals to contact in case of an emergency. Though the company has its IT data backed up at an alternate site the ISM decides to develop a proper BCP that will be more effective in the event of a disaster.
- Preparation for Meeting with Senior Management: The ISM requires some information from the Project Manager which will enable him to back up his arguments for the need of a BCP before the Senior Management. Both the Project Manager and the Senior Manager from each department will be responsible for identifying key personnel that will contribute to the plan.
- Kickoff Meeting: The ISM will have to inform and convince the senior management about the lack and the need for a formal business plan. He needs to let them know that the BCP will need to be regularly tested and maintained. The senior management realizes the need for a BCP and gives it full support to the ISM to continue with the BCP project.
- Project Team Creation: With the help of the project manager (PM), the ISM presents the personnel from each department (IT, human resources, etc) who will take part in the BCP process.
- Project Schedule: The PM intends that the project lasts for three months beginning on the 29/03/2018. BCP team members from core departments could spend between 60 to 90% of their weekly work time on the project while members from other departments could spend between 10 to 30% of their time contributing to the project. The figure below schedules the BCP project with all the departments:
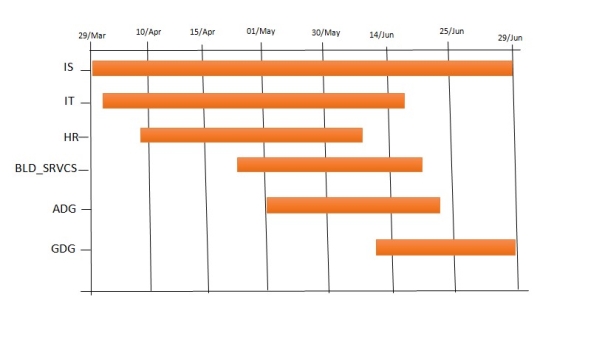
Figure 3: Gantt chart for BCP creation schedule
III.2 BUSINESS IMPACT ANALYSIS
The next task involves the BIA. This will be done in the form of a questionnaire and the following information will be gathered:
- Identification of business activities/operations
- Financial and operational impacts to the organization that could result from failure of each activity
- Resources required for recovery of activity
- Support for timely recovery of critical operations
- Etc
The BIA serves as a guide for the construction of the BCP and is tailored depending on the organization’s activities. The following were obtained from Horizon Health staff, customers and stakeholders:
- What are the business drivers and expectations for the security assessment?
Horizon Health Response: Good business practices and health laws are drivers for the assessment. We want to be prepared for the unexpected and gain our customers trust in our services.
- What are the activities of the company?
Horizon Health Response: We provide an electronic platform for the collection and storage of confidential health information of individuals and care facilities.
- What are the critical operations of the company and what technologies support them?
Horizon Health Response: Secure transfer of patient information on their request and processing of payments. For this we use the Internet, VPN and data encryption technologies.
- What are the regulatory bodies that govern your business activities?
Horizon Health Response: HIPPA- it governs activities related to the access of private health information.
- Have you had any security incidents in the past?
Horizon Health Response: Yes, in the past one our database servers were hacked. This caused some of our patient’s health data were leaked to the public. We had several court cases and settlements to deal with.
- What are your security concerns?
Horizon Health Response: Similar incidents like the one mentioned above could recur.
Not only are we going to incur financial losses but also the reputation of the company will be ruined. We are concerned about the confidentiality and integrity of patient data.
- How is the organization structured?
Horizon Health Response: We have fifty employees divided into six departments; the executives, the London data group, the global data group, the information technology IT and Information security departments.
- What are the roles of the IT and IS staffs?
Horizon Health Response: They are responsible for network operations and configurations server /equipment maintenance and backup of data. The IS personnel also perform internal audits.
- What networking hardware/software equipment do you possess and what security measures are put in place?
Horizon Health Response: We have 2 servers in our main office building, 55 desktops installed with Avast antivirus, 2 printers, one photocopier and one scanner. All software installed in equipments within our network is regularly updated and patches are sometimes installed.
- Describe your remote environment?
Horizon Health Response: We have 5 employees who access our servers and databases from out of the office via Cisco Secure VPN.
- What security policies are being implemented?
Horizon Health Response: We have disaster recovery, Access control, Usage, Facility security and information access policies. These policies are accessible to all employees and any updates to the policies are communicated. Updates are performed by the executives and the internal audit teams. New employees also go through an induction program where they are briefed about the security policies of the organization.
- Describe the security architecture of your company
Horizon Health Response: We have firewalls, Intrusion detection systems, but no cloud-based data center. Thanks to the firewall and IDS systems we monitor and review logs in the network.
- How does the business process work?
Horizon Health Response: Our critical activities involve secure and confidential retrieval and distribution of patient data to patients, hospitals and insurance companies. The IT team is responsible for managing the database. In the event of a disaster, our backup processes will need to be activated and depending on the circumstances we might have to take legal actions against security breaches. Acceptable downtime is one hour.
- What happens when an employee’s contract is terminated?
Horizon Health Response: The employee’s company email account is deactivated and all company equipment e.g. phone, PC, etc is retrieved. His access to the company’s premises and data center is also restricted.
- How is the backup and recovery process performed?
Horizon Health Response: Real time mirroring of patient data into a remote server is done such that in the event of a disaster, the administrators can readily regain access to information.
- How do you handle an incident?
Horizon Health Response: Once an incident is detected, we follow a documented set of procedures to alert the security department and manage the incident.
- What physical security policies are in place?
Horizon Health Response: We have surveillance cameras within and around the company’s premises. Employees are not allowed to copy information out from the company’s devices.
The tables below illustrate the results from the business impact and risk assessment data for Horizon Health:
Table 2: Business Impact for Horizon Health
| Assets | Loss of Integrity | Loss of Confidentiality | Loss of Availability | |
| 1 | Patient Information | High | High | Medium |
| 2 | Internal Documents | Medium | Medium | Low |
| 3 | HR Records | High | High | Medium |
| 4 | Advertising Literature | Low | Medium | Low |
Table 3: Risk Assessment for Horizon Health
| Threats/Event Examples | Severity of Loss | Duration of Impact | Probability of an Incident | |
| 1 | Hardcopy/Electronic fraud or extortion | low | Extended | Rare |
| 2 | IT personnel do not have complete understanding of HIPPA regulations | High | Isolated | Rare |
| 3 | Backups unreliable and other mission critical systems | High | Isolated | Likely |
| 4 | Hacker or Dos attacks | High/medium | Isolated | Rare |
| 5 | Malware and spam, possession of unlicensed software | Medium | Extended | Likely |
| 6 | Technology obsolescence databases | Medium | Extended | Rare |
| 7 | Disruptive or destructive malware (Trojan horse, worm or virus) | High/medium | Isolated | Common |
| 8 | Civil lawsuit, retaliation or vengeance brought by employee for discrimination or harassment | High | Isolated | Rare |
III.3 CONTROL MECHANISMS
The selection and implementation of the appropriate countermeasures to ensure the confidentiality, integrity and availability of information systems is very essential. In the case of Horizon Health, the following controls could be implemented:
– Employees should be schooled on lawsuits that can follow if patient information is leaked or compromised
– Hardcopies of patient information to be disposed should be done in a careful and discrete manner. Eg. Shredding.H
– Cloud based backup services should be implemented
– The company should consider outsourcing to server service providers
– Operating systems and software should be regularly patched.
III.4 DEVELOPMENT AND IMPLEMENTATION
The BCP team leader (the information security manager) will be responsible for the activation upon receiving information from the emergency management team EMT about a major incident or disaster. He is responsible for contacting all other BCP team members in the event of a disaster that requires execution of the business continuity plan. Considering the size of Horizon Health, the EMT will be part of the BCP team.
Depending on the severity of the incident, the BCP team leader will decide if activities need to be moved to an alternate site. For this, there exists a hot-site located 20 miles outside London. While core departments’ employees can work directly on this site, all other employees will be required to work from home via VPN. There is a backup server at this hot site, so company operations should be able to run smoothly from there.
III.5 TESTING AND MAINTENANCE
Quarterly tests and exercises will be performed by the IT and IS departments to test for effectiveness of the plan. Any future changes to the Horizon Health personnel, vendors, mission statement or functions shall be reflected in the plan.
IV. CONCLUSION
A BCP is designed to avoid or mitigate risks and the impact of an incident/disaster. There is no standard plan for business continuity; every organization needs to develop a suitable BCP based on a number of factors ranging from its size, budget, technology, and activities. Senior level organizational support for BCP is quite essential as without their approval, the BCP cannot be successfully created and implemented. Other elements to consider include funding, time constraints and staffs as all three elements contribute to the success of the BCP project.
A well-structured BCP will give the organizations clients and stakeholders more confidence in the business practices. When business is impacted by an incident/disaster, it usually costs money and time to get things back to normal, and although Insurance cover helps, claims might take a long time. When everyone is impacted, you have a little more time but eventually customers will have to go to other competitors. Disaster Recovery Plans focus primarily on IT whereas BCPs envelope the entire business process recovery. Typically, BCP/DRPs contain 5 steps, which include a variety of sub-sets from emergency response to crisis management, with a scope that extends from a technology perspective to a people perspective.
V. RECOMMENDATIONS
A properly written and comprehensive plan can save an organization in times of, while a poorly written plan will only cause the company extra losses and costs. Regular data restoration tests, back-up of data, antivirus/antimalware updates on workstations and servers should be performed Organizations should involve business continuity professionals and managed services providers in their cyber security business continuity plan.
VI. REFERENCES
[1] Peter Carr, Editor, “ Business Continuity for Facilities Managers”, pp 4-8. Fast Track Solutions Ltd
[2] Dejan Kosutic. 2018. Business continuity plan: How to structure it according to ISO 22301. [ONLINE] Available at: https://advisera.com/27001academy/knowledgebase/business-continuity-plan-how-to-structure-it-according-to-iso-22301/. [Accessed 27 February 2018].
[3] Kelly Handerhan. 2012. Business Continuity & Disaster Recovery Planning. [ONLINE] Available at: https://www.cybrary.it/skill-certification-course/business-continuity-disaster-recovery-planning-certification-training-course. [Accessed 15 March 2018].
[4] Michael E. Whitman, Herbert J. Mattord. 2013. “Management of Information Security”, 4th ed, pp 138-147.
[5] Liz Gasiorowski-Denis. 2012. ISO publishes new standard for business continuity management. [ONLINE] Available at: https://www.iso.org/news/2012/06/Ref1587.html. [Accessed 6 March 2018].
[6] Chris Owens/Annette Mercer. 2014.
The Business Continuity Plan. [ONLINE] Available at: http://psnc.org.uk/halton-st-helens-and-knowsley-lpc/wp content/uploads/sites/45/2013/12/BCP-LPC-18-6-14.pptx. [Accessed 19 March 2018].
[7] Queensland Government. 2017. What’s in a business continuity plan?. [ONLINE] Available at: https://www.business.qld.gov.au/running-business/protecting-business/risk-management/continuity-planning/plan. [Accessed 22 March 2018].
[8] M. H. Goh, Editor, “Implementing Your Business Continuity Plan”, (2nd ed., p. 104). GMH Pte Ltd,
Singapore, (2010)
[9] Queensland Government. 2009. Business Continuity Planning. [ONLINE] Available at: http://www.mackay.qld.gov.au/__data/assets/pdf_file/0018/151434/Business_Continuity_Planning_Guide.pdf. [Accessed 31 March 2018].
[10] Veo Taylor. 2009. CASE STUDY: Small Organization Business Continuity Plan Creation. [ONLINE] Available at: http://cs.lewisu.edu/mathcs/msis/projects/msis595_VeoTaylor.pdf. [Retrieved 05 April 2018].
https://en.wikipedia.org/wiki/Business_continuity#BC/BCM_plan_(BCP)
VII. APPENDIX
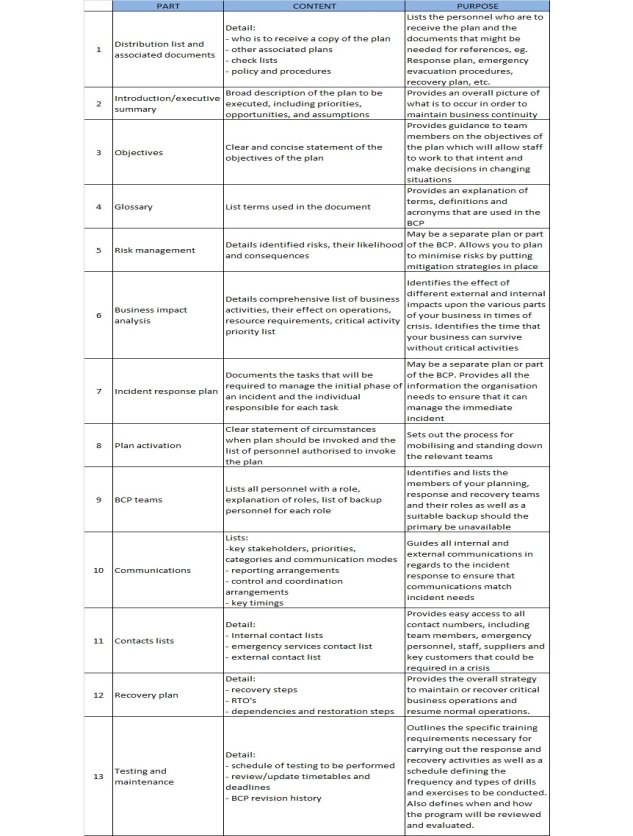
Figure 5: Sample BCP Template
VIII. ACCRONYMS
| BCP | Business Continuity Planning |
| BIA | Business Impact Analysis |
| COOP | Continuity Of Operations Plan |
| DRP | Disaster Recovery Plan |
| EMT | Emergency Management Team |
| HIPAA | Health Insurance Portability and Accountability Act |
| IS | Information Security |
| ISO | International Organization for Standardization |
| IT | Information Technology |
| MOA | Memorandum of Agreement |
| MOU | Memorandum of Understanding |
| NIST | National Institute of Standards and Technology |
| VPN | Virtual Private Network |
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Business Strategy"
Business strategy is a set of guidelines that sets out how a business should operate and how decisions should be made with regards to achieving its goals. A business strategy should help to guide management and employees in their decision making.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




