Applications of Cryptography for Computer Authentication
Info: 7130 words (29 pages) Dissertation
Published: 10th Dec 2019
Tagged: Computer Science
Comments:
Table of Contents
Aim and Objectives…………………………………………………………………………………………………………….3
Task 1 Two important modern methods of Cryptography………………………………………………………..4
Task 2 Cryptographic techniques in Computing……………………………………………………………………..9
Task 3 Authentication of users in Windows server…………………………………………………………………12
Task 4 Kerberos Protocol and where it may be found……………………………………………………………..14
REFERENCES (APA format)
Aim
The aim of this assessment is to discuss cryptography and its uses along with computer authentication. Kerberos system and how it works. Microsoft Windows authentication processes.
Objectives:
- To explain the essence of Cryptography in computing
- To discuss the different ways that cryptography is used to secure electronic transactions on the web
- To deliberate the Windows authentication
- To outline the Kerberos protocol and its uses
- To make a written assessment with a minimum of 3000 words.
Task 1. Describe two important modern methods of cryptography, their theory of operation, their strength and a comparison of their weakness. Specify the situations in the IT industry in which each method is, or has been, used.
Cryptography is defined as hiding the message to make it secret using scrambled codes. It allows the date to be changed into a code that is not legal for not permitted person and it needs to be converted back to its original message for it to become readable [1]. Encryption and decryption are the process of cryptography. Encryption is when the readable text is converted into coded text while the decryption is where the coded text is converted into readable text [2]. There are numerous types of cryptography but the symmetric and asymmetric key cryptography is the most used technique.
[1] https://www.techopedia.com/definition/1770/cryptography
[2] https://msdn.microsoft.com/en-us/library/windows/desktop/aa381939(v=vs.85).aspx
a. Symmetric-key Cryptography
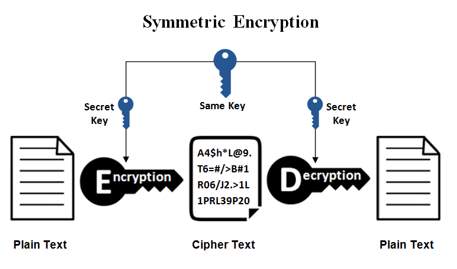
Figure 1.1[5]
i. Theory of operation
Symmetric-key Cryptography is also known as the private key cryptography [3]. It is the oldest and well-known technique of cryptography. This method is simple which only requires each computer that has a code that will be encrypted by an encryption software into packets of data before it is sent across the network to another and the same code it will use to decrypt the message for the receiving computers [4]. As we could see in this Figure 1.1, the process of encrypting and decrypting messages begins from the original sender. First, the sender’s message for example, “Tesla is the Best” is the original message will be encrypted by an encryption software and it is protected by a secret key and it will become cipher text which will convert all characters into a text of scrambled characters that is difficult to understand. Then the cipher text will be transmitted in a secure manner. As the ciphered text will be decrypted by a decryption software using the same key from the encryption’s secret key, the ciphered text will return to its original text. For the encryption and decryption software, there are blowfish, AES, DES and RC4-6 but the widely common symmetric algorithm is the AES [5].
[3] http://searchsecurity.techtarget.com/definition/private-key
[4] http://computer.howstuffworks.com/encryption2.htm
[5] https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are-differences
ii. Strengths
One of the main reason why symmetric key cryptography is used because of its complex security features [6]. The main reason of its complex security is that it could deduce the key via brute-force attack which means it made it difficult to make a guess the encrypted password. When it faces by an attacker, the symmetric key algorithms will be more difficult to crack. Another reason is the speed of symmetric key. Since they have the same key for the encryption and decryption, the process will be easier and faster [7]. An additional strength factor of symmetric key cryptography is the availability. [8] Since it is widely used, a lot of programs are using symmetric type of cryptography and it is accessible for commercial use as well.
[6] http://www.csc.villanova.edu/~mdamian/Past/csc3990fa08/csrs2007/01-pp1-7-MattBlumenthal.pdf
[7] https://itstillworks.com/advantages-disadvantages-symmetric-key-encryption-2609.html
[8] http://securitycerts.org/review/symmetric-key-strengths-weaknesses.htm
iii. Weaknesses
The main disadvantage of symmetric key algorithm was its acknowledgment of key [8.]. For it to be decoded by the receiver, their keys must be the same of the sender. The key of the sender and receiver used must be kept secure. If anyone found the key and knows the algorithm sequence of the structure of the message, all messages using the hacked key would be readable [9.]. Another disadvantage of symmetric key is its vulnerability. Once the hacker gets into the communication of either sender and receiver, all messages can be compromised [8.].
[9.] http://www4.ncsu.edu/~kksivara/sfwr4c03/lectures/lecture9.pdf
iv. Uses in IT field
There are two types of symmetric ciphers mainly: Stream ciphers and block ciphers [10.]. Stream ciphers includes RC4, Helix, A5/1-2, ISAAC and FISH while the block ciphers are RC5, AES, blowfish and DES. The most commonly used symmetric cipher is the AES. In the field of IT, AES is widely used in doing file transfers like FTPS and HTTPS. They are using AES for faster file transfer. As you could see in the Figure 1.2, the first step is sending the key (public) from the server. Second, the client will encrypt the data using the key (public) before transferring it into the server. Last, the main file will be encrypted using the key (session) and will be decrypted by the server using the same key.
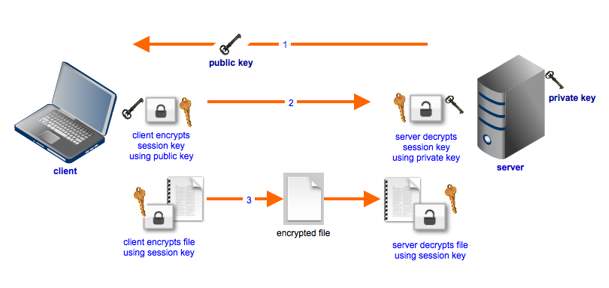
Figure 1.2 AES [11.]
[10.] https://www.quora.com/What-are-some-examples-of-symmetric-and-asymmetric-encryption
[11.] http://www.jscape.com/blog/aes-encryption
b. Asymmetric-key Cryptography
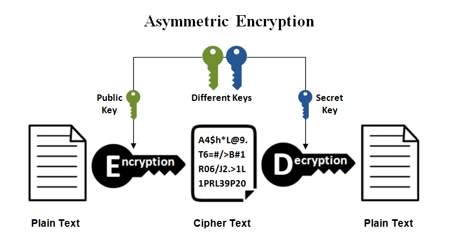
Figure [5.]
i. Theory of operation
The Asymmetrical cryptography is also known as the public key cryptography [5.]. This method is completely different from symmetric since symmetric is using the same key to encrypt and decrypt the message while asymmetric cryptography is using different key to decrypt the message. There will be two types of keys in asymmetric, public key and secret key. The process starts with the sender’s message will be encrypted using the public key. The encrypted message will be delivered to the receiver then the receiver will use the secret key to decrypt the message. The message will be secured because of its uniqueness even when the hacker intercepts the message with the public key, they cannot decrypt it with their own decryption since it is only the private key who can decrypt it. There will be no risk for the communication since it is invulnerable and difficult in interception.
ii. Strength
The main strength of asymmetric key encryption was its increased security. It is highly secured and the secret keys will not be needed to be transmitted to the receiver or anyone who is receiving the message [12.]. Further, there is no need for the keys to be exchanged from one to another. Another strength is the use of digital signature. The digital signature is required to validate a secured connection over the internet. The encryption strength of asymmetric key encryption is huge and vast that makes asymmetric algorithm difficult to hack [13.].
[12.] http://www.uobabylon.edu.iq/eprints/paper_1_2264_649.pdf
[13.] http://searchsecurity.techtarget.com/definition/asymmetric-cryptography
iii. Weakness
One of the main weakness of asymmetric key encryption is the speed of encryption. It is slower than symmetric method as both sender and receiver uses different types of keys for it to be secured enough from the hackers to crack the public and secret key. Another weakness of asymmetric key is the length of key. The asymmetric uses long keys in order to secure the data. Key management and validation are also makes the asymmetric encryption weak. Almost all the business implements the Public Key Infrastructure also known as PKI. PKI manages the keys for the companies handled by the Certificate Authorities also known as the CAs. These will lead to a costly negotiation for the companies. Key validation on the other hand will ensure the key before decrypting the message that will provide delay since there are a lot of public-key [14.].
[14.] https://www.techwalla.com/articles/the-disadvantages-of-asymmetric-encryption
iv. Uses in IT field
In the field of technologies, Riverst-Shanmis-Adleman commonly known as RSA is the most commonly used method of asymmetric algorithm. Numerous protocols namely SSH, SSL/TLS and OpenPGP depend on RSA algorithm [15.]. SSH is the easiest and simplest protocol for RSA. SSH is also called as the Secure Shell. SSH is used for network communication from one computer to another computer. SSH work when the client initiates the connectivity to the server and after that the server will send its public key. Then the channel will be opened for each communicating device. And last, the user will login to the host server [16.]. CISCO communication will get in network using SSH for telnet to login to the user then to its routers or switches.
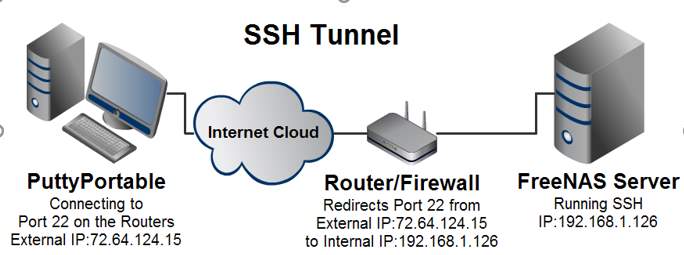
Figure 1.3 SSH [17.]
[15.] http://searchsecurity.techtarget.com/definition/RSA
[16.] https://www.ssh.com/ssh/protocol/
[17.] http://wiki.joelchristian.com/images/4/4b/SSH_Tunnel.png
Conclusion:
In conclusion, both symmetric and asymmetric algorithm are the most commonly used methods of cryptography of today as both have their own uses in our daily electronic world. The main differences between the symmetric and asymmetric key cryptography is the use of public key and private key [18.]. Symmetric has the faster encryption process than the asymmetric but the asymmetric is more secure since it uses different keys [19.]. In the field of Information Communication Technology, both are integrating in different ways in creating a more secured environment for the future of telecommunication and data transfer.
[18.] https://www.ukessays.com/essays/computer-science/the-role-of-cryptography-in-network-security-computer-science-essay.php
[19.] https://brilliant.org/wiki/symmetric-ciphers/
Task 2. Survey the application of cryptographic techniques in computing. Include the ways that cryptography is used to secure electronic transactions on the web, and in a VPN.
a. SSH
SSH or the Secure Shell is a security protocol and is used in administering servers that are located far from the client. SSH uses different encryption algorithms that uses secure connection in transferring information to both communicating devices. SSH protocol begins with client-based computer to authenticate connection to the server-based computer and will encrypt the connection between them. The first stage of the session is about agreement between client and server to establish a secured encryption transfer. The second stage is for the user to be authenticated first and secondly to be determined by the server [20.].
There are different uses we can do with SSH. One of which is SSH tunneling. It is like permitting the remote SSH server to become a proxy server, that makes the network traffic flows from the local system to the designated SSH server by sending through a secure connection. SCP file transfer is another way of using SSH. It allows secured file transfer from client to client, client to server or server to server services. The use of SSH for terminal sessions can be used to access a secured remote session either thru local or international [21.].
[20.] https://www.digitalocean.com/community/tutorials/understanding-the-ssh-encryption-and-connection-process
[21.] https://www.howtogeek.com/114812/5-cool-things-you-can-do-with-an-ssh-server/
b. CHAP
CHAP, also known as Challenge-Handshake Authentication Protocol, offers a protection against a hacker using an exponential altering identifier and value. This will minimize the number of attackers in securing communications. This method is secured of its capabilities of locating the desired secret key in a large board of secret keys. CHAP is irreversible to be encrypted since it uses unique key that is difficult to be decrypted to an unknown attacker [22.].
CISCO routers and switches, widely uses CHAP authentication method. For example, there are 2 routers connected in a network. The first Router has its own username and the second router has also has its own username while password for both routers will be the same for intercommunication for both devices. There are 2 ways of CHAP authentication namely, 1-way and 2-way authentication. 1-way is a unidirectional which mean one to one method of transferring information while the 2-way is unidirectional which can be propagate information to and from the opposite routers simultaneously [23.].
[22.] http://www.networksorcery.com/enp/protocol/chap.htm
[23.] https://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/25647-understanding-ppp-chap.html
c. HTTPS
Hyper Text Transfer Protocol Secure, also known as HTTPS is similar to HTTP but it is more secured. HTTP is the protocol that uses transferred information between the browser that carries the data and to our connected websites. With the HTTPS, all connections between the browser and website will be secured. HTTPS uses the SSL or the Secure Socket Layer or the TLS or the Transport Layer Security which are asymmetric cryptograph [24.].
HTTPS is commonly used in online banking and shopping as it encrypts all the information of all the data being sent and received by the browser. Most of the attackers would create a fake website that would make the real clients believe that it is the right online banking site. HTTPS will eliminate this kind of hacking by using different ports in the connection that will be more secured when accessing delicate websites [25.].
[24.] https://www.instantssl.com/ssl-certificate-products/https.html
[25.] https://blog.hartleybrody.com/https-certificates/
d. VPN
Virtual Private Network, wide known as VPN, is a type of network that are using public connection, commonly the internet, to connect distant users to the company’s network. VPN is a secured private network that encrypts data from one computer to another and cannot be intercepted. The information being transferred travels between two different locations uses an encrypted tunnel. The process begins with the source’s firewall that requires the user to establish a secured connection. The data will then be encrypted before it passes the tunnel. On the last stage, the destination computer will decrypt the data back to its original format [26.].
VPNs are commonly used nowadays to hide browsing activity when connected to a public Wi-Fi. Potential hackers are using public Wi-Fi to access someone else’s computer, on the other hand VPN could access blocked websites like the internet censorship in China where they block their citizens to access Facebook and similar websites. Also, it could facilitate anyone to access private network while travelling for personal or business use [27.].
[26.] http://www.webopedia.com/TERM/V/VPN.html
[27.] https://www.howtogeek.com/133680/htg-explains-what-is-a-vpn/
e. Kerberos
Kerberos is another type of authentication protocol that uses a permission or permit to authenticate data. The main process of Kerberos is to avoid the storage of information locally which are the passwords of the user or storing it in the cloud. This uses a trusted third party and is built using symmetric-key cryptography. The permit is the proof of your own identity that is kept secret on local computer/machine so that the user can access the service on its own [28.].
Kerberos are commonly used in operating systems like Linux, Windows, among others. The login page is one basic example of Kerberos. All usernames and passwords are sent to the database of the server then the server will response back by sending the key back to the client. After the client passes the login page, it will now gain an access in the storage. This is a secured type of login since there are special keys involved when entering an operating system [29.].
[28.] http://www.roguelynn.com/words/explain-like-im-5-kerberos/
[29.] https://access.redhat.com/documentation/enUS/Red_Hat_Enterprise_Linux/6/html/Managing_Smart_Cards/Using_Kerberos.html
Task 3. Include a brief survey of the means used to authenticate users in a windows server environment, and the changes made in this technology from Windows NT to date. Focus on login authentication, and distinguish carefully between Integrated Windows Authentication and other techniques.
In a world of computer security, one requires a proof that we are unique enough in accessing protected information. In the method of authentication, any data must become valid or genuine [30.]. In this manner, many operating systems including Windows, are continuingly developing secured ways of authentication for users. Windows authentication also known as the Windows NT (New Technology), is a form of secured authentication for windows clients that uses username and password prior to sending the authentication across networks. The process begins within the windows authentication, then the browser of the client will transfer a secured hashed password into a cryptographic exchange between the user and the web server. Windows Authentication uses 2- types of authentication protocols namely, Kerberos and NTLM. Nowadays, Kerberos is the default windows authentication, once it is installed and enabled. The element of Windows Authentication comprises a ’useKernelMode’ that configures which kernel mode type of authentication to be used. In an intranet environment, windows authentication is used because of the following reasons: Webservers and client computers are using similar domain, Admin could verify every browser that its clients use the latest Internet Explorer version, HTTP proxy are no required as it is not supported by NTLM, and lastly, Kerberos requires an active connection to the Active Directory for offline purposes [31.]. A lot of protocols are combining different authentication packages like credential and negotiate security support provider that will enable the authentication for computers, users and large web services [32.].
In the early stage of Microsoft, Windows operating systems uses NTLM or the NT Lan Manager. However, in Windows 2000, Kerberos is the default authentication for the Windows operating systems. There are numerous reasons why Kerberos was chosen compared to NTLM. The first reason is that it is fast in authentication. Kerberos authentication is using a permit type of verification which surpasses the pass-through authentication for quicker process. The second reason is the mutual authentication. This means that the client authenticates the service, and vice versa. NTLM does not supports mutual authentication that makes the client-server relationship harder to communicate. The third reason is the flexibility of the Kerberos system. RFC or the Request for Comments 4120 is an open standard that provides single sign-on known as the SSO between other operating system and Windows. The fourth reason is the authentication delegation provision. Authentication delegation in modern networking is having 2 or more servers communicating with each other and could delegate each other. For example, Computer A can give authorization to Computer B to access an application to server C acting as a remote user. The last reason is that smart card logon is more secured authentication compared to NTLM because it has two factor authorizations [33.].
We know how to login using our username and password in Windows lock screen, however we know little about its process. Interactive logon is the first process in authenticating and authorizing a user in Windows operating systems. This will determine whether the user has permission to access he system. The user needs to log on to a computer via domain or local account using their own username and password. The username and password will verify the user’s credentials and identities. One good example is the security chip for the cars that will be read by external device which is the smart card reader [34.]. After the username and password has entered and verified, the user has access to the system. We could see from the figure 3.1 below being the Windows Official logon screen.
Figure 3.1 Windows Login Screen
Microsoft keeps on developing an improved authentication log in. They came up with the integrated Windows authentication. Using the integrated windows authentication, it provides users to access administration sites rather than allowing the credentials to send across the network. In this way, the browser that operates in the administrative interface, will start a cryptographic exchange between the web using Kerberos authentication and the user to verify the confirmation. This will give the system the integrated security but hinders the Internet Information Systems or IIS to access the systems using remote server administration [35.].
[30.] http://searchsecurity.techtarget.com/definition/authentication
[32.] https://technet.microsoft.com/en-us/library/hh831472(v=ws.11).aspx
[33.] http://windowsitpro.com/security/comparing-windows-kerberos-and-ntlm-authentication-protocols
[34.] https://technet.microsoft.com/en-us/library/cc780332(v=ws.10).aspx
[35.] https://technet.microsoft.com/en-us/library/cc732841(v=ws.11).aspx
Task 4. Include a description of the Kerberos protocol, and say where it might be found. Carefully list the implications that using Kerberos on a LAN has for the operation of the LAN.
Kerberos is one of the famous and widely used authentication protocol in networks. It uses advanced cryptography a secured authentication for user and server applications. Kerberos was created by Massachusetts Institute of Technology to make network security complexed. Kerberos eliminated network attackers in the internet by sniffing passwords from the network. Kerberos is a secured because of its client-server relationships that they must prove their identities before accessing each other to assure the data integrity and strict privacy in their surroundings [36.].
Kerberos works with 3 different groups. The first group is the client or the user, who want to access a certain computer or server. The second group is the resource or file server that accesses the files. The third group is the Key Distribution Center or the KDC, which is the active directory domain controller. In Kerberos authentication, the file server does not have direct connection to Key distribution center, so the client will have to be bridged between the KDC and the file server. It starts when the client logs its username and password to the computer as an authenticator together with the date and time of access for it to be secured by an attacker. The client has its own key to determine which certificate to be authenticated, so that the keys will not travel across the network. Then, the certificate of the client will be go through the KDC to verify the certificate. The KDC will now decrypt the secured certificate using their variety of keys and the KDC will grant a ticket, which is the TGT (Ticket Granting Ticket) being the domain controller. Then, in this time the ticket from the KDC will be included in the memory of the client. After that, when the client has been verified and it is now ready to access some files in the file server. Before the client can access the file server, it will again communicate to the KDC to gain a ticket but this process is faster, since the first connection between the client and KDC has been verified. In this manner the ticket from the client will be able to access the file server. All the tickets from the KDC and the file server will be in the client’s Kerberos tray, in order not to get another ticket every time the client accesses the file server. Every time the clients access the file server, it will just send the ticket and the file server will just verify the ticket for authentication. This connection of the three devices are secured because of the ticketing system of each devices that verifies the authentication process [37.].
With regards to the uses of Kerberos on Windows Operating systems, Windows Active Directory primarily uses Kerberos protocol. Every time you log on to the Active Directory and accessing network resources in file server, it uses Kerberos based protocol [38.]. Active directory allows the client and servers to be centralized. For example, we have multiple users in the office, each computer has its own account. Active directory could select some computers to access the server while limiting the other users using the domain group. Active directory also uses Group Policy. Group Policy is a group of objects that links the OUs/Organizational Unit for clients to use. This will make the network more secured and faster in access, since it is centralized and has connection policy in each computer [39.].
The implication of Kerberos on a LAN usually starts with three different devices that includes the workstations, routers as the Key Distribution Center (KDC) and servers confined with Kerberos system. At the start, the workstation will communicate with the router using LAN connection. The router will authenticity the identity of the workstation whether it is authorized or not. If the connection has been established, the server with Kerberos system will make its connection with its router. At the last stage, the workstation and the server will have a secured connection via LAN [40.]. With implication of Kerberos, we can conclude that its infrastructure and arrangement is complex.
[36.] https://web.mit.edu/kerberos/
[37.] https://www.youtube.com/watch?v=kp5d8Yv3-0c
[38.] http://windowsitpro.com/security/kerberos-active-directory
[40.] https://doc.opensuse.org/documentation/leap/security/html/book.security/cha.security.kerberos.html
REFERENCES:
[1] https://www.techopedia.com/definition/1770/cryptography
What is Cryptography? – Definition from Techopedia. (n.d.). Retrieved October 08, 2017, from https://www.techopedia.com/definition/1770/cryptography
[2] https://msdn.microsoft.com/en-us/library/windows/desktop/aa381939(v=vs.85).aspx
Data Encryption and Decryption. (n.d.). Retrieved October 08, 2017, from https://msdn.microsoft.com/en-us/library/windows/desktop/aa381939(v=vs.85).aspx
[3] http://searchsecurity.techtarget.com/definition/private-key
What is private key (secret key)? – Definition from WhatIs.com. (n.d.). Retrieved October 08, 2017, from http://searchsecurity.techtarget.com/definition/private-key
[4] http://computer.howstuffworks.com/encryption2.htm
Data Encryption and Decryption. (n.d.). Retrieved October 08, 2017, from https://msdn.microsoft.com/en-us/library/windows/desktop/aa381939(v=vs.85).aspx
[5] https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are-differences
Symmetric vs. Asymmetric Encryption – What are differences? (n.d.). Retrieved October 08, 2017, from https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are-differences
[6] http://www.csc.villanova.edu/~mdamian/Past/csc3990fa08/csrs2007/01-pp1-7-MattBlumenthal.pdf
Blumenthal, M. (2005). 1 Encryption: Strengths and Weaknesses of Public-key Cryptography [PDF]. Department of Computing Sciences Villanova University.
[7] https://itstillworks.com/advantages-disadvantages-symmetric-key-encryption-2609.html
Advantages & Disadvantages of Symmetric Key Encryption. (n.d.). Retrieved October 08, 2017, from https://itstillworks.com/advantages-disadvantages-symmetric-key-encryption-2609.html
[8] http://securitycerts.org/review/symmetric-key-strengths-weaknesses.htm
SecurITyCerts dot Org. (n.d.). Retrieved October 08, 2017, from http://securitycerts.org/review/symmetric-key-strengths-weaknesses.htm
[9.] http://www4.ncsu.edu/~kksivara/sfwr4c03/lectures/lecture9.pdf
Krishnan, K. (2004). Symmetric Key cryptosystem [PDF]. Ncsu.
[10.] https://www.quora.com/What-are-some-examples-of-symmetric-and-asymmetric-encryption
Rose, D. (2014, November 14). Symmetric and asymmetric encryption [Editorial]. What are some examples of symmetric and asymmetric encryption? Retrieved October 7, 2017, from https://www.quora.com/What-are-some-examples-of-symmetric-and-asymmetric-encryption
[11.] http://www.jscape.com/blog/aes-encryption
Villanueva, J. C. (n.d.). What AES Encryption Is And How It’s Used To Secure File Transfers. Retrieved October 08, 2017, from http://www.jscape.com/blog/aes-encryption
[12.] http://www.uobabylon.edu.iq/eprints/paper_1_2264_649.pdf
Advantages and Disadvantages of Asymmetric and Symmetric Cryptosystems [PDF]. (2008). UOBABYLON.
[13.] http://searchsecurity.techtarget.com/definition/asymmetric-cryptography
What is asymmetric cryptography (public key cryptography)? – Definition from WhatIs.com. (n.d.). Retrieved October 08, 2017, from http://searchsecurity.techtarget.com/definition/asymmetric-cryptography
[14.] https://www.techwalla.com/articles/the-disadvantages-of-asymmetric-encryption
https://www.techwalla.com/articles/the-disadvantages-of-asymmetric-encryption
[15.] http://searchsecurity.techtarget.com/definition/RSA
What is RSA algorithm (Rivest-Shamir-Adleman)? – Definition from WhatIs.com. (n.d.). Retrieved October 08, 2017, from http://searchsecurity.techtarget.com/definition/RSA
[16.] https://www.ssh.com/ssh/protocol/
SSH history with Tatu Ylonen. (n.d.). Retrieved October 08, 2017, from https://www.ssh.com/ssh/protocol/
[17.] http://wiki.joelchristian.com/images/4/4b/SSH_Tunnel.png
Christian, J. (2014). SSH tunnel. Retrieved from http://wiki.joelchristian.com/images/4/4b/SSH_Tunnel.png
The Role Of Cryptography In Network Security Computer Science Essay. (n.d.). Retrieved October 08, 2017, from https://www.ukessays.com/essays/computer-science/the-role-of-cryptography-in-network-security-computer-science-essay.php
[19.] https://brilliant.org/wiki/symmetric-ciphers/
Symmetric Ciphers. (n.d.). Retrieved October 08, 2017, from https://brilliant.org/wiki/symmetric-ciphers/
D. (2017, July 18). Contents. Retrieved October 08, 2017, from https://www.digitalocean.com/community/tutorials/understanding-the-ssh-encryption-and-connection-process
[21.] https://www.howtogeek.com/114812/5-cool-things-you-can-do-with-an-ssh-server/
Hoffman, C. (2017, July 14). 5 Cool Things You Can Do With an SSH Server. Retrieved October 08, 2017, from https://www.howtogeek.com/114812/5-cool-things-you-can-do-with-an-ssh-server/
[22.] http://www.networksorcery.com/enp/protocol/chap.htm
(n.d.). Retrieved October 08, 2017, from http://www.networksorcery.com/enp/protocol/chap.htm
Understanding and Configuring PPP CHAP Authentication. (2017, May 12). Retrieved October 08, 2017, from https://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/25647-understanding-ppp-chap.html
[24.] https://www.instantssl.com/ssl-certificate-products/https.html
Differnce between HTTP and HTTPS. (2017, May 15). Retrieved October 08, 2017, from https://www.instantssl.com/ssl-certificate-products/https.html
[25.] https://blog.hartleybrody.com/https-certificates/
Brody, H. (2013, July 24). Hartley Brody. Retrieved October 08, 2017, from https://blog.hartleybrody.com/https-certificates/
[26.] http://www.webopedia.com/TERM/V/VPN.html
Beal, V. (n.d.). VPN – virtual private network. Retrieved October 08, 2017, from http://www.webopedia.com/TERM/V/VPN.html
[27.] https://www.howtogeek.com/133680/htg-explains-what-is-a-vpn/
Hoffman, C. (2017, October 04). What Is a VPN, and Why Would I Need One? Retrieved October 08, 2017, from https://www.howtogeek.com/133680/htg-explains-what-is-a-vpn/
[28.] http://www.roguelynn.com/words/explain-like-im-5-kerberos/
Root, L. (n.d.). Explain like I’m 5: Kerberos. Retrieved October 08, 2017, from http://www.roguelynn.com/words/explain-like-im-5-kerberos/
[29.] https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Managing_Smart_Cards/Using_Kerberos.html
Chapter 3. Using Kerberos. (n.d.). Retrieved October 07, 2017, from https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/Managing_Smart_Cards/Using_Kerberos.html
[30.] http://searchsecurity.techtarget.com/definition/authentication
What is authentication? – Definition from WhatIs.com. (n.d.). Retrieved October 08, 2017, from http://searchsecurity.techtarget.com/definition/authentication
R. (n.d.). Windows Authentication. Retrieved October 08, 2017, from https://docs.microsoft.com/en-us/iis/configuration/system.webserver/security/authentication/windowsauthentication/
[32.] https://technet.microsoft.com/en-us/library/hh831472(v=ws.11).aspx
Windows Authentication Overview. (n.d.). Retrieved October 08, 2017, from https://technet.microsoft.com/en-us/library/hh831472(v=ws.11).aspx
[33.] http://windowsitpro.com/security/comparing-windows-kerberos-and-ntlm-authentication-protocols
Mar 25, 2007 Jan De Clercq. (n.d.). Comparing Windows Kerberos and NTLM Authentication Protocols. Retrieved October 08, 2017, from http://windowsitpro.com/security/comparing-windows-kerberos-and-ntlm-authentication-protocols
[34.] https://technet.microsoft.com/en-us/library/cc780332(v=ws.10).aspx
How Interactive Logon Works. (n.d.). Retrieved October 08, 2017, from https://technet.microsoft.com/en-us/library/cc780332(v=ws.10).aspx
[35.] https://technet.microsoft.com/en-us/library/cc732841(v=ws.11).aspx
Using integrated Windows authentication. (n.d.). Retrieved October 08, 2017, from https://technet.microsoft.com/en-us/library/cc732841(v=ws.11).aspx
[36.] https://web.mit.edu/kerberos/
(n.d.). Retrieved October 08, 2017, from https://web.mit.edu/kerberos/
[37.] https://www.youtube.com/watch?v=kp5d8Yv3-0c
C. (2012, October 11). Retrieved October 08, 2017, from https://www.youtube.com/watch?v=kp5d8Yv3-0c
[38.] http://windowsitpro.com/security/kerberos-active-directory
Sep 20, 2010 Brian Desmond. (n.d.). Kerberos in Active Directory. Retrieved October 08, 2017, from http://windowsitpro.com/security/kerberos-active-directory
What is Active Directory Domain Services and how does it work? (n.d.). Retrieved October 08, 2017, from https://serverfault.com/questions/402580/what-is-active-directory-domain-services-and-how-does-it-work
[40.] https://doc.opensuse.org/documentation/leap/security/html/book.security/cha.security.kerberos.html
(n.d.). Retrieved October 08, 2017, from https://doc.opensuse.org/documentation/leap/security/html/book.security/cha.security.kerberos.html
[41.] Ciampa, M. D. (2015). CompTIA security guide to network security fundamentals. Boston: Cengage Learning.
* check turnitin
https://www.scanmyessay.com/app/login
bryanldavid
Class ID: 9407781
Password: panukalat3
7529690
Ganapna
https://plagiarismcheckerx.com/buy
- APA
- plagiarism
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Computer Science"
Computer science is the study of computer systems, computing technologies, data, data structures and algorithms. Computer science provides essential skills and knowledge for a wide range of computing and computer-related professions.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




