Investigating the Parameters of the Internet of Things
Info: 8136 words (33 pages) Dissertation
Published: 9th Dec 2019
Tagged: Information Technology
Chapter No. 01
Introduction To IoT
1.1. Prologue TO Internet:
The Internet, once in a while called essentially “the Net,” is an overall arrangement of PC systems – a system of systems in which clients at any one PC can, in the event that they have consent, get data from some other PC (and some of the time talk straightforwardly to clients at different PCs). It was brought about by the Advanced Research Projects Agency (ARPA) of the U.S. government in 1969 and was first known as the Arpanet. The first point was to make a system that would permit clients of an exploration PC at one college to “converse with” inquire about PCs at different colleges. A side advantage of Arpanet’s outline was that, since messages could be steered or rerouted in more than one bearing, the system could keep on functioning regardless of the possibility that parts of it were annihilated in case of a military assault or other fiasco.

Figure 1.1. Internet
Today, the Internet is an open, helpful and self-managing office available to countless individuals around the world. Physically, the Internet utilizes a bit of the aggregate assets of the right now existing open media transmission systems. Actually, what recognizes the Internet is its utilization of an arrangement of conventions called TCP/IP (for Transmission Control Protocol/Internet Protocol). Two late adjustments of Internet innovation, the intranet and the extranet, additionally make utilization of the TCP/IP convention.
So it was about the web that what is the web and how it functions. Presently we will present “IoT”.
1.1.1. Internet Of Things (IoT):
The Internet of things (IoT) is the between systems administration of physical gadgets, vehicles (likewise alluded to as “associated gadgets” and “brilliant gadgets”), structures, and different things—installed with hardware, programming, sensors, actuators and system network that empower these articles to gather and trade information. In 2013 the Global Standards Initiative on Internet of Things (IoT-GSI) characterized the IoT as “the foundation of the data society.” The IoT enables items to be detected or controlled remotely crosswise over existing system framework, making open doors for more straightforward coordination of the physical world into PC based frameworks, and bringing about enhanced productivity, exactness and financial advantage notwithstanding lessened human mediation. At the point when IoT is increased with sensors and actuators, the innovation turns into a case of the more broad class of digital physical frameworks, which additionally includes advances, for example, keen lattices, savvy homes, shrewd transportation and brilliant urban areas. Everything is extraordinarily identifiable through its installed registering framework however can interoperate inside the current Internet foundation. Specialists appraise that the IoT will comprise of right around 50 billion protests by 2020.
Presently at a similar end, we can characterize IoT as such moreover. The Internet of Things (IoT) is an arrangement of interrelated processing gadgets, mechanical and computerized machines, articles, creatures or individuals that are given interesting identifiers and the capacity to exchange information over a system without expecting human-to-human or human-to-PC cooperation.
The Internet of Things (IoT) world might be energizing, yet there are not kidding specialized difficulties that should be tended to, particularly by designers. In this handbook, figure out how to meet the security, investigation, and testing necessities for IoT applications.
A thing, in the Internet of Things, can be a man with a heart screen embed, a ranch creature with a biochip transponder, a vehicle that has worked in sensors to alarm the driver when tire weight is low – or whatever other common or man-made question that can be allocated an IP address and furnished with the capacity to exchange information over a system.
IoT has developed from the meeting of remote advancements, small scale electromechanical frameworks (MEMS), smaller scale administrations and the web. The union has torn down the storehouse dividers between operational advances (OT) and data innovation (IT), permitting unstructured machine-produced information to be investigated for bits of knowledge that will drive upgrades.
Kevin Ashton, prime supporter and official chief of the Auto-ID Center at MIT, first said the Internet of Things in an introduction he made to Procter and Bet in 1999. Here’s the manner by which Ashton clarifies the capability of the Internet of Things:
“Today PCs and, in this way, the web are completely reliant on individuals for data. Almost the greater part of the about 50 petabytes (a petabyte is 1,024 terabytes) of information accessible on the web were first caught and made by people by writing, squeezing a record catch, taking an advanced picture or filtering a standardized identification.
The issue is, individuals have restricted time, consideration and exactness all of which implies they are bad at catching information about things in this present reality. On the off chance that we had PCs that knew everything there was to think about things utilizing information they accumulated with no assistance from us we would have the capacity to track and number everything and enormously diminish waste, misfortune and cost. We would know when things required supplanting, repairing or reviewing and whether they were crisp or past their best and better.”
Figure 1.2. IoT Environment
1.1.2. Eventual fate of IoT:
Around 3.2 billion people are associated with the Internet, speaking with each other and sharing data. In any case, we’re not really alone in the internet. Machines are additionally doing likewise, imparting and offering data to each other and with us, over basically a similar unpredictable and associated worldwide work. Also, they as of now dwarf us.
An expected 4.9 billion sensors are associated with the Internet as of this written work, and that number is evaluated achieve 38 to 50 billion in only five short years. This is what’s comprehensively fueling the Internet of Things (IoT). Associated autos, associated coordination’s, associated clothing…connected everything.
The foundation of the Internet of things are sensors inserted wherever assembling each and every minute of information, tenaciously ordering our general surroundings, and sending that data up to cloud servers to control applications and investigation.
Dana Blouin, driving IoT mastermind and Chief Data Scientist at DRVR, gives an adept portrayal. “I by and large depict the Internet of Things as an increase of the present Internet, where rather than website pages there are gadgets. Furthermore, much the same as how we can visit and associate with pages we would now be able to visit and connect with gadgets like a climate station, your auto or your cooler.”
1.1.3. Problem Statement:
Web of Things (IoT) is a tremendous field having a considerable measure of day by day life applications that can facilitate the life, information and intriguing realities. Be that as it may, its limited condition, affectability, less similarity and power issues makes it hard to be for all intents and purposes actualized. Our venture is, “Investigation of parameters of IoT”. In this we need to investigate the parameters of IoT on which its fundamental idea or building lies yet it is truly hard to be measured and afterward to set them on prerequisite. So we are attempting to first break down and after that to actualize those parameters in an immaculate and finish IoT condition.
1.1.4. Points and Goals:
We have the accompanying points and goals that we need to accomplish while completing this venture:
- To comprehend the fundamentals of IoT
- To take in the earth in which IoT works
- To take in the applications and conventions of the IoT condition
- To take in the parameters of IoT
- Practically execution of the parameters of IoT
- Calculating the outcomes by editing those parameters.
1.2. IoT as the upcoming Industrialization:
The buildup machine affirms that the effect of the Internet of Things will change, well, everything. The market for associated autos alone is anticipated to reach $54 billion in the following two years. The IoT showcase for social insurance is evaluated to reach $117 billion by 2020 from applications like patient observing and healing center operations. What’s more, at a cross-industry scale, advertise pioneer GE Digital evaluations that the “Mechanical Internet,” the business-to-business IoT, so to speak, can possibly include – hold to your cap – $15 trillion (with a “T”) to the worldwide GDP by 2035. That likens to a gigantic worldwide effect on efficiency, occupations and personal satisfaction.
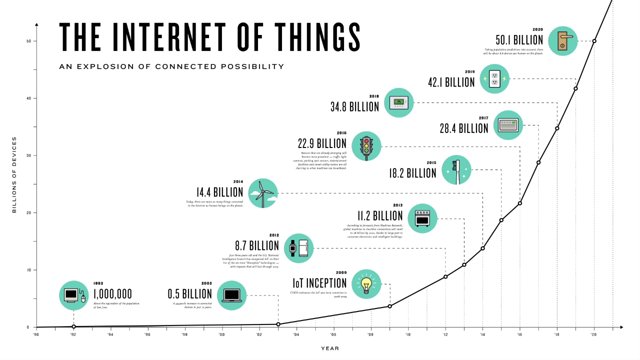
Figure 1.3. Future Growth of IoT
It is a 1893 World’s Fair minute for those arranging and building the Internet of Things, as what’s to come is forecasted and the conceivable outcomes appear to be inestimable. Zach Supalla, who basically rethought the light for the Internet period and runs his own particular IoT organization, says “Movement will show signs of improvement with insightful road lights. Sustenance will get less expensive (and better) in view of savvy agribusiness.”
The conceivable outcomes are inestimable.
1.3. Procedure:
So here is the procedure divide. We will complete it well ordered helpfully. The means that we will take to complete this undertakings, are composed in the accompanying:

Chapter No. 02
IoT Protocols & Parameters.
2.1. Protocol (Conventions):
In data innovation, a convention is the extraordinary arrangement of guidelines that end focuses in a media transmission association utilize when they convey. Conventions indicate associations between the conveying elements.
Conventions exist at a few levels in a media transmission association. For instance, there are conventions for the information trade at the equipment gadget level and conventions for information exchange at the application program level. In the standard model known as Open Frameworks Interconnection (OSI), there are at least one conventions at each layer in the media transmission trade that both closures of the trade must perceive and watch. Conventions are frequently portrayed in an industry or worldwide standard.
So in IoT we have diverse conventions for various layers. They are composed in the accompanying:
- Infrastructure (ex: 6LowPAN, IPv4/IPv6, RPL)
- Identification (ex: EPC, uCode, IPv6, URIs)
- Comms / Transport (ex: Wifi, Bluetooth, LPWAN)
- Discovery (ex: Physical Web, mDNS, DNS-SD)
- Data Conventions (ex: MQTT, CoAP, AMQP, Websocket, Node)
- Device Management (ex: TR-069, OMA-DM)
- Semantic (ex: JSON-LD, Web Thing Model)
- Multi-layer Systems (ex: Alljoyn, IoTivity, Weave, Homekit)
Yet, as per the request of our venture, which is Information Conventions, we will concentrate just the accompanying two conventions:
- CoAP
- MQTT
2.2. CoAP (Constrained Application Protocol):
The cooperation model of CoAP (Constrained Application Protocol) is like the customer/server model of HTTP. In any case, machine-to-machine connections regularly result in a CoAP usage acting in both customer and server parts. A CoAP ask for is comparable to that of HTTP (Hypertext Transfer Protocol) and is sent by a customer to ask for an activity (utilizing a Technique Code) on an asset (distinguished by a URI) on a server. The server at that point sends a reaction with a Reaction Code; this reaction may incorporate an asset portrayal.
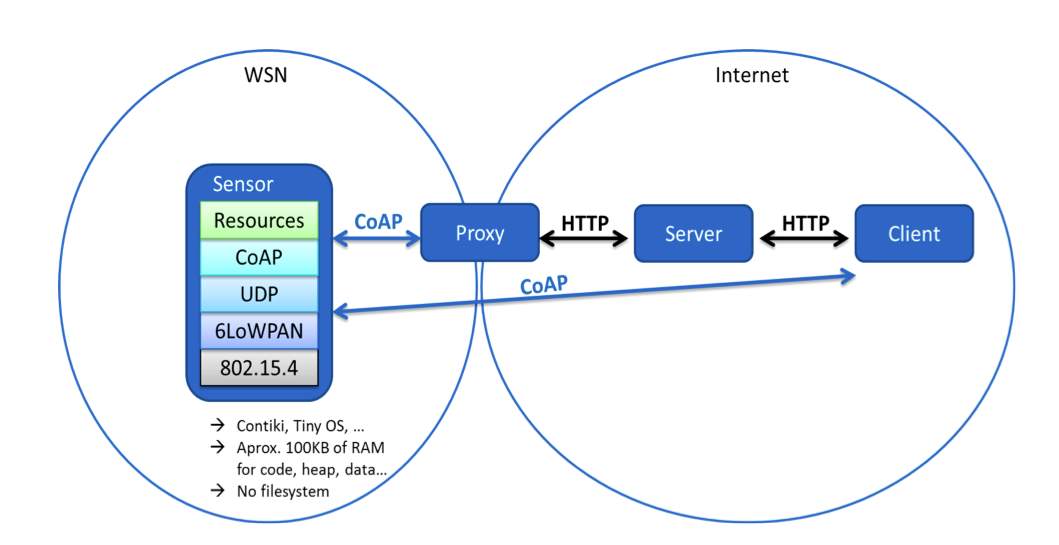
Figure 2.1. CoAP (Constrained Application Protocol)
Not at all like HTTP, CoAP manages these exchanges nonconcurrently over a datagramarranged transport, for example, UDP. This is done intelligently utilizing a layer of messages that backings discretionary dependability (with exponential back-off). CoAP characterizes four sorts of messages:
- Confirmable
- Non-confirmable
- Acknowledgement
- Reset
Strategy Codes and Reaction Codes incorporated into some of these messages make them convey solicitations or reactions. The essential trades of the four sorts of messages are to some degree orthogonal to the demand/reaction collaborations; solicitations can be conveyed in Confirmable and Non-confirmable messages, and reactions can be conveyed in these and in addition piggybacked in Affirmation messages.
One could consider CoAP intelligently as utilizing a two-layer approach, a CoAP informing layer used to manage UDP and the nonconcurrent idea of the connections, and the demand/reaction communications utilizing Strategy and Reaction Codes (see Figure 1). CoAP is however a solitary convention, with informing and demand/reaction as just elements of the CoAP header.
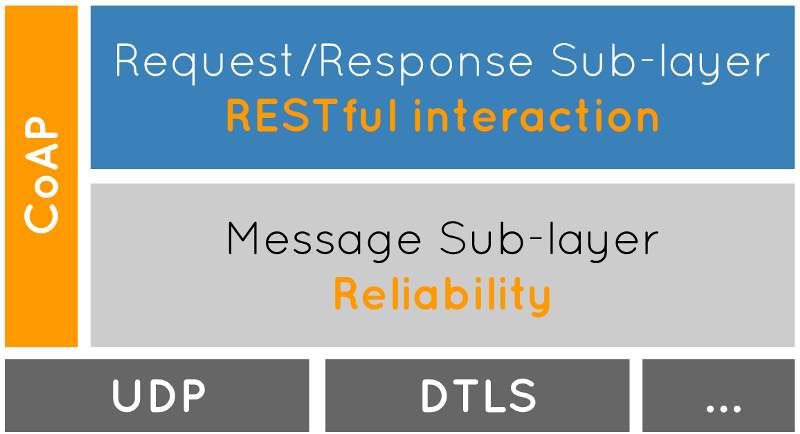
Figure 2.2.
Theoretical (Abstract) Layering of CoAP (Constrained Application Protocol)
2.2.1. Features (Elements) of CoAP:
CoAP has some vital elements and the qualities which are composed in the accompanying:
- Web convention satisfying M2M prerequisites in compelled conditions.
- UDP official with discretionary dependability supporting unicast and multicast demands.
- Asynchronous message trades.
- Low header overhead and parsing multifaceted nature.
- URI and Substance sort bolster.
- Simple intermediary and storing capacities.
- A stateless HTTP mapping, enabling intermediaries to be fabricated giving.
- Access to CoAP assets through HTTP consistently or for HTTP.
- Simple interfaces to be acknowledged then again finished CoAP.
- Security authoritative to Datagram Transport Layer Security (DTLS).
2.2.2. Request (Demand)/Response (Reaction) Model:
CoAP utilizes Request (Demand) / Response (Reaction)display for its correspondence model or informing model. CoAP ask for and reaction semantics are conveyed in CoAP messages, which incorporate either a Strategy Code or Reaction Code, separately. Discretionary (or default) demand and reaction data, for example, the URI and payload media sort are conveyed as CoAP choices. A Token is utilized to coordinate reactions to demands autonomously from the fundamental messages.
An ask for is conveyed in a Confirmable (CON) or Non-confirmable (NON) message, and, if quickly accessible, the reaction to a demand conveyed in a Confirmable message is conveyed in the subsequent Affirmation (ACK) message. This is known as a piggybacked reaction. Two cases for a fundamental GET ask for with piggybacked reaction are appeared in Figure 4, one effective, one bringing about a 4.04 (Not Discovered) reaction.
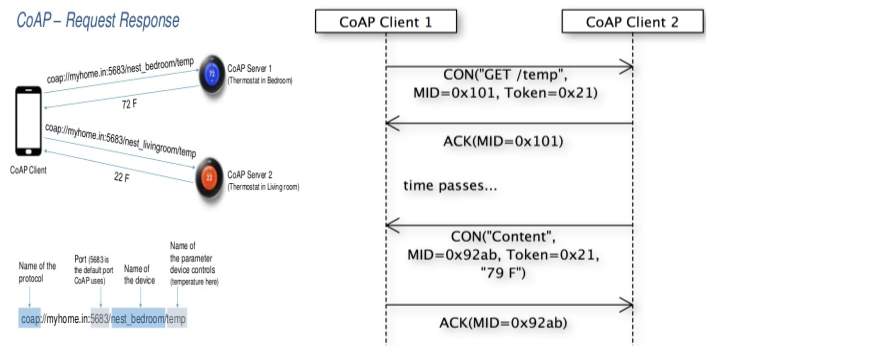
Figure 2.3.
Two GET Solicitations with Piggybacked Reactions
In the event that the server is not ready to react quickly to a demand conveyed in a Confirmable message, it just reacts with a Void Affirmation message so that the customer can quit retransmitting the demand. At the point when the reaction is prepared, the server sends it in another Confirmable message (which at that point thus should be recognized by the customer). This is known as a “different reaction”.
In the event that a demand is sent in a Non-confirmable message, at that point the reaction is sent utilizing another Non-confirmable message, despite the fact that the server may rather send a Confirmable message. This kind of trade is delineated in following figure.
2.3. MQTT:
MQTT remains for MQ Telemetry Transport. It is a Distribute (Publish)/Subscribe, to a great degree basic and lightweight informing convention, intended for compelled gadgets and low-data transmission, high-inactivity or inconsistent systems. The outline standards are to limit organize transmission capacity and gadget asset necessities while additionally endeavoring to guarantee dependability and some level of affirmation of conveyance. These standards additionally end up making the convention perfect of the developing machine-to-machine” (M2M) or “Web of Things” universe of associated gadgets, and for versatile applications where data transfer capacity and battery control are at a premium.
MQTT is a lightweight distribute/subscribe convention with dependable bi-directional message conveyance. Created in 1999 by Andy Stanford-Clark (IBM) and Arlen Nipper. The first issue was to send sensor information from oil pipelines via a satellite connection
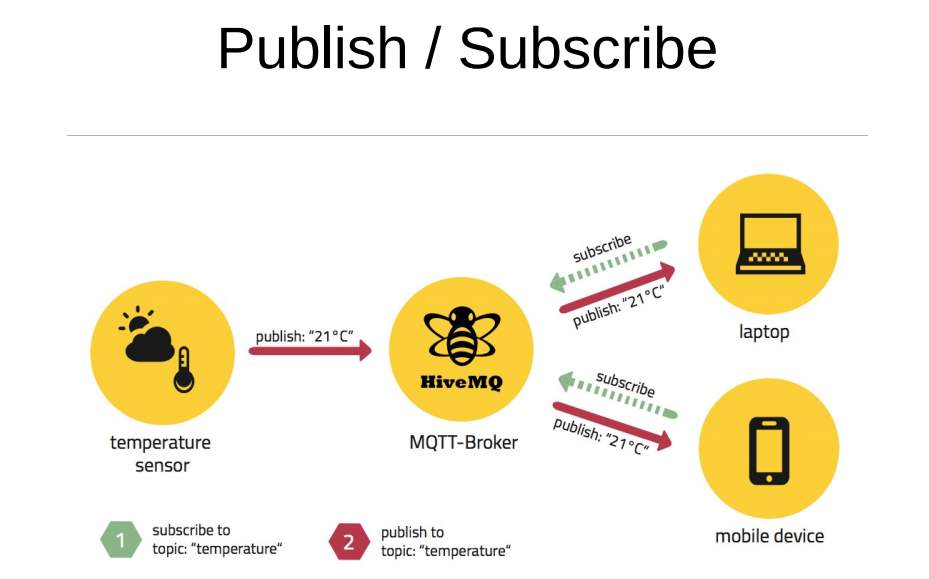
Figure 2.4.
A Distribute (Publish)/Subscribe Model
2.3.1. Key Parts (Aspects) of MQTT:
MQTT have some particular key perspectives for which it has been composed. They are composed in the accompanying:
- It has been intended to deal with high volumes of information in low transmission capacity systems.
- It has little code impression.
- It keeps running on top of TCP/IP. Both customer and specialist require a TCP/IP stack. A few varieties like MQTTSN keep running over non-TCP/IP systems.
- It abstains from surveying
- It is occasion situated
- Recovery, store and forward, and distribute/subscribe are a piece of the usage (no compelling reason to actualize in the application rationale)
2.3.2. Distribute (Publish)/Subscribe Model:
MQTT depends on this distribute/subscribe demonstrate. The model has the accompanying perspectives:
- It decouples the distributer from the endorser.
- Clients are constantly associated with a specialist.
- Both distributers and endorsers are “customers”.
- A customer communicates something specific (distributer).
- One or more customers get the message (endorsers).
- MQTT utilizes “points” to figure out which message is steered to which customer.
- A subject is a “various leveled organized string”.
2.3.3. Key Components:
There are primary components that are utilized as a part of the MQTT demonstrate. A concise presentation of everything about component is composed in the accompanying:
Customer (Client):
- Can be a microcontroller up to a server.
- Implementation is straight-forward. –
- Some numbers: C=30kb, Java=100kb. –
- MQTT customer libraries are accessible for an immense assortment of programming dialects, for instance Android, Arduino, C, C++, C#, Go, iOS, Java, JavaScript, .NET, and so forth.
(Representative)Broker:
- Core of any distribute/subscribe convention.
- Receives all messages from customers, channels them, and afterward sends messages to all customers intrigued by a specific point.
- Handles verification/approval of customers.
- Highly adaptable, simple to incorporate into backend frameworks, disappointment safe. Association, dependably started by a customer.
Associate Bundle (Connect packet):
Associate bundle incorporates the accompanying elements into it:
- Customer ID: Novel ID per agent.
- Clean Session: Flag (Banner) to show if the session must be diligent or not. A constant session (Clean Session = false) implies, that the intermediary will store all memberships for the customer and every missed message (with Nature of Administration (QoS) 1 or 2). On the off chance that the banner is set to genuine, the dealer won’t store anything for the customer and will cleanse all data from a past relentless session.
- Username/Secret key: Sent in plaintext. Application must encode it.
- Will Message: Its motivation is to tell different customers when a customer disengages awkwardly. The specialist sends this message for the benefit of the customer.
- Keep Alive: Period in secs the customer is resolved to send a PING to the agent, so each other know whether the flip side is alive and reachable.
MQTT Message Structure:
MQTT message structure consists of the accompanying banners (flags) and headers:
- Fixed Header: It is incorporated into each message.
- Variable Header: Incorporated into a few bundles. Its substance relies upon the bundle kind.
- Payload: Incorporated into a few parcels.
- The MQTT settled header has a length that can differ from 2 to 5 bytes.
- The initial two snack speaks to the message sort and bundle particular control banners.
- From the second byte begins the rest of the bundle length. This uses a “variable-length encoding” that can take upto 4 bytes.
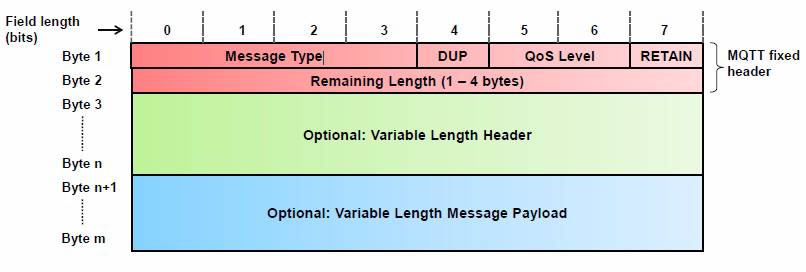
Figure 2.5.
MQTT Message Demonstrate
2.4. Parameters of IoT:
There are a few measures or parameters for anything that must be finished. In the event that we discuss IOT, there are a few parameters that are utilized as standard for IOT. The majority of the execution of the setup of IOT bases on these parameters. In the accompanying we will portray those specific parameters that premise this vital field:
- Ease of Use/Usability (Application Layer):
One of the basically vital parameter while utilizing Web of Things is its Ease of use. As the gadgets which are included in this differ a great deal fit as a fiddle and size, it is exceptionally hard to judge the conduct and activities at ongoing. It is an intense assignment to really perform ease of use testing on these applications, since these gadgets are relatively little in measure and thus can’t give any sort of assistance or documentation viz. apparatus tips, illustrations and so forth. As a term it appears to be straightforward, yet when it really comes to testing ease of use, there is absence of clearness and comprehension for these IOT gadgets.
- Testing in This Present Reality (Session Layer):
Web of Things and Ongoing go as an inseparable unit. Any of IOT application can turn out to be steady just if tried altogether with constant components since there is parcel of network by sensors, between the physical components and the applications. Conventional testing techniques may demonstrate useless and consequently it is critical to recover continuous situations for testing methodologies. Limiting your test set up to a testing lab isn’t the correct way. You need to move out to a genuine circumstance and that as well, with lesser hardware’s and offices as might be given in the real situation, so that the real conduct of the application may surface in prior stages.
- Security (Application Layer):
It is another element to be appropriately tried is the Security angle. The greater part of the Web of Things is powerless to security issues like secret word settings, getting to the UI without passwords or absence of information encryption. It is an intense employment, for the end clients and all the more in this way, for the analyzers, to bring up conceivable hacking components from where security can pass, with the extent of venture spreading out so wide and far. Prior, the IOT was a hazy area and henceforth security was never observed forthright however now with IOT getting more commonplace, it is dependably a superior stride to keep security highlights verified.
- Connectivity (Network Layer):
The venturing stone to achievement of any Web of Things application is most grounded and consistent network. Two things are fundamentally urgent while testing network: one is there ought to be a faultless availability between every one of the gadgets which can be tried by having the greater part of the testing gadgets cooperating. Be that as it may, as time says, availability may jettison you on occasion. At such circumstances, the application needs to guarantee information security and capacity so that at whatever point the association is reestablished, your information has returned to shape as it might have been. This can be mimicked by turning off the web association on gadgets, incidentally moving out of Wi-Fi zone or by moving to standalone mode.
- Parameters for Transport Layer:
Transmission of information is the most vital parameter or part of the IOT. Information transmission assumes imperative part in the viability, effectiveness, unwavering quality and the survival of any of the correspondence framework. What’s more, promote in it, the thing which is particularly vital is the entry and dispatch of the data in time in light of the fact that if there is even an almost no postponement in accepting or transmitting any of the data then the entire framework will demolished. There are other parameters that are in charge of the transmission of the data at the transmitter side and also at the collector side. These parameters are as per the following:
- ACK_TIMEOUT:
This term that is essentially used to inform the sender side either a sent message is gotten or not at the collector side. There is a particular day and age that is utilized for it. On the off chance that the message is gotten with in that era, at that point ACK will alright generally message will be resend. Normally its opportunity is above than 1 second.
- MAX_RETRANSMIT:
Parameter that involves the retransmission of the impeded message that has not gotten at the beneficiary side. It is likewise customizable as indicated by the request of the planned framework.
- ACK_RANDOM_FACTOR:
This parameter is in charge of the synchronization of the messages and their affirmations that must be sent either as the conclusion of Yes or No.
2.4.1. Parameters of Different Layers in Internet of Things (IoT):
As there are diverse layers required in IoT, so there are distinctive parameters comparing to each of the layer. They are composed in the accompanying:
- Parameters for Network(System) Layer:
System/Network layer assumes a vital part in the IOT. The parameter that is related with this layer is Center/Middle Box Traversal Rules. Center boxes are utilized to watch the information activity that is gone through the system layer. They are dependable to check and clear the questions about system movement. In any case, in IOT center boxes have nothing to do. The fundamental focuses about this are composed in the accompanying:
- Middle boxes keep up per stream state
- TCP utilizes center boxes
- NAT characterizes fractional way on inside and outside side
- UDP can’t utilize center box
- Per-stream state is annihilated when utilized by different applications
- Timeout for NAT should more noteworthy than 2 minutes
- 15s required for 1 for every stream state
Parameters for Data Link/Information Connection Layer:
There are two parameters that categories into the class of Information Connection Layer. The reason is that those two parameters include with the information transmission and the managing information.
- Bulk Exchange/Transfer.
- Low volume data.
Hence these are the parameters that should must be considered while sending the information through this layer in IOT. Quickly the focuses that incorporates these two parameters can be canvassed in the accompanying focuses:
Mass Exchange/Bulk Transfer:
The greater part of the circumstances in IOT, we need to manage the overwhelming information rates. So there are a few focuses that must be remembered while planning the framework.
- It SHOULD must utilize TFRC.
- It SHOULD screen the bundle misfortune rate.
- Packet misfortune is worthy if TCP stream over a similar system way under a similar system way under a similar system condition would accomplish a normal throughput, measured on a sensible timescale that is at the very least that of UDP stream.
- It is adequate in indicated ways however not in the open web condition, it will influence the speed of the web.
Low Volume Information/Data:
Here and there we need to manage the low information rates in IOT. Generally the frameworks are intended for higher information rates. So if high transmission capacities are assigned to a few channels and low information is going through those channels, at that point there will be a great deal of wastage of assets. So the accompanying focuses must be consider while managing this parameter.
- Transmit only 1 UDP as per round-trip time.
- An application ought to keep up a gauge of the RTT for any goal with which it imparts.
- TCP utilizes an underlying estimation of 3 seconds, which is additionally Prescribed as an underlying incentive for UDP applications.
- Initial time out ought to be least.
- SHOULD NOT send greater than 1 UDP in 3s on the grounds that the absence of return activity keeps the identification of bundle misfortune.
2.4.2. Transmission Parameters:
There are some particular parameters that should must be consider while the transmission of information. The things that must be transmitted, should must take after the accompanying parameters for the correct activity and proficient transmission of the information.
- MAX_TRANSMIT_SPAN:
It is the greatest time from the principal transmission of a Confirmable message to its last retransmission. For the default transmission parameters, the esteem is (2+4+8+16)*1.5 = 45 seconds, or all the more by and large its equation can be characterized as:
ACK_TIMEOUT * [(2 * MAX_RETRANSMIT) – 1] * ACK_RANDOM_FACTOR
- MAX_TRANSMIT_WAIT:
It is the most extreme time from the primary transmission of a Confirmable message to the time when the sender abandons getting an affirmation or reset. For the default transmission parameters, the esteem is (2+4+8+16+32)*1.5 = 93 or for the most part:
ACK_TIMEOUT * [(2 * (MAX_RETRANSMIT + 1) – 1] *ACK_RANDOM_FACTOR
- MAX_LATENCY:
It is the greatest time a datagram is relied upon to take from the begin of its transmission to the finishing of its gathering. This consistent is identified with the MSL (Maximum Segment Lifetime). It can be taken as 2 minutes or 100 seconds according to prerequisite.
- PROCESSING_DELAY:
It is the time a hub takes to pivot a Confirmable message into an affirmation. We accept the hub will endeavor to send an ACK before having the sender time out, so as a preservationist supposition we set it equivalent to ACK_TIMEOUT.
- MAX_RTT:
The most extreme round-trip time, or:
(2 * MAX_LATENCY) + PROCESSING_DELAY
From these qualities, we can determine the accompanying esteems applicable to the convention operation.
- EXCHANGE_LIFETIME:
It is the time from beginning to send a Confirmable message to the time when an affirmation is never again expected, i.e., message-layer data about the message trade can be cleansed. EXCHANGE_LIFETIME incorporates a MAX_TRANSMIT_SPAN, a MAX_LATENCY forward, PROCESSING_DELAY, and a MAX_LATENCY for the path back.
- NON_LIFETIME:
It is the time from sending a Non-confirmable message to the time its Message ID can be securely reused. On the off chance that numerous transmission of a NON message is not utilized, its esteem is MAX_LATENCY, or 100 Seconds. It is more secure to utilize the esteem: MAX_TRANSMIT_SPAN + MAX_LATENCY or 145 Seconds with the default transmission parameters.
2.5. Impact of Changing the Parameters:
The qualities for ACK_TIMEOUT, ACK_RANDOM_FACTOR, MAX_RETRANSMIT, NSTART, DEFAULT_LEISURE, & PROBING_RATE might be arranged to values particular to the application condition (counting progressively balanced esteems); be that as it may, the setup strategy is out of extent of this report. It is PRESCRIBED that an application situation utilize predictable esteems for these parameters; the particular impacts of working with conflicting esteems in an application domain are outside the extent of the present detail.
The transmission parameters have been accomplished a conduct within the sight of clog that is sheltered in the Web. In the event that a design yearnings to utilize distinctive esteems, the onus is on the setup to guarantee these blockage control properties are not abused.
Specifically, a lessening of ACK_TIMEOUT underneath 1 second would abuse the rules. CoAP was intended to empower usage that don’t keep up round-trip-time (RTT) estimations. In any case, where it is fancied to diminish the ACK_TIMEOUT altogether or increment NSTART, this must be done securely when keeping up such estimations. Arrangements MUST NOT diminish ACK_TIMEOUT or increment NSTART without utilizing systems that guarantee clog control security, either characterized in the design or in future benchmarks archives.
ACK_RANDOM_FACTOR MUST NOT be diminished beneath 1.0, and it ought to have an esteem that is adequately unique in relation to 1.0 to give some assurance from synchronization impacts.
MAX_RETRANSMIT can be unreservedly balanced, yet an esteem that is too little will diminish the likelihood that a Confirmable message is really gotten, while a bigger incentive than given here will demand promote modifications in the time esteems.
On the off chance that the decision of transmission parameters prompts an expansion of determined time esteems, the design instrument MUST guarantee the balanced esteem is additionally accessible to every one of the endpoints with which these balanced esteems are to be utilized to impart.
Chapter No. 03
Methodology
3.1. Methodology:
Methodology is the name of technique or a process that is applied or adopted to achieve a specific goal. In our project to accomplish our goals, we have applied the sequential methodology. The whole project is divided into sections or parts and at every step a different process is done to done with the project. All of the processes are done in sequence and are aligned to each other. So if we look at the flow chart which is followed to complete the project, then all of the steps can be shown in one single table and are as follows:

These were the basic steps that are taken to complete this project. Now in the following the justification of this methodology is given.
3.2. Software:
So here is the portion of software. We have used the VMware software in our project. It is a virtual machine. So now the question is that what the virtual machine is?
Virtual Machine:
In computing, a virtual machine (VM) is an emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination.
Figure. 3.1
In VMware we have used the UBUNTU operating system.
3.3. Implementation:
In the above passage we have discussed about the software that we have used for our project. Now it is the portion of the implementation that how we have implemented the things into our project using the software. The following steps can be included in the implementation portion.
- First of all the Linux environment was setup in the VMware
- After making the environment, the Go programming language was installed in the UBUNTU
- Then the command window was established for the coding of the server
- Server code was written in the command window
Figure 3.2
- After implementing this on the computer, the mobile application was used for the further progress of the project
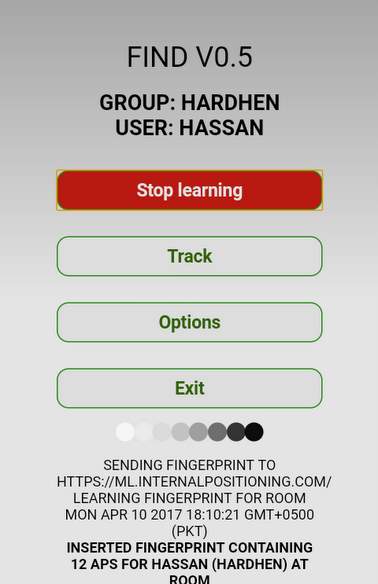
Figure 3.3
Chapter No. 04
FIND Server & Application
4.1. Find:
FIND is a system for inside route and revelation. It is utilized to find the distinctive keen gadgets in any of the IoT condition. It frames a server essentially and after that the majority of the information of the gadgets are sent to that server utilizing the Discover application. The interface can be viewed as takes after:
Figure 4.1. FIND (Discover) Web Service (Utility)
The site is termed as, “Internal Positioning System”. Presently on the off chance that we need to realize that what is the FIND and the concise presentation of this, we should come to realize that what is the interior situating. So with a specific end goal to realize that what the Inner Situating Framework is, let is us gone to the accompanying point.
4.1.1. Internal Positioning System (Inner Situating Framework):
Utilizing FIND, and just your cell phone or tablet, you will have the capacity to point your position in your home or office.
Not at all like GPS on your cell phone, this framework has geolocation of underneath 10 sq ft. Additionally not at all like GPS, the application uses previous operations so it has no noteworthy cost to your battery.
This framework is open-source and completely configurable additionally simple to utilize and easy to set up. It is suited to little scale home applications and also huge scale industrial and educational applications.

Figure 4.2. Internal Positioning Systems
4.1.2. Find Server And Application:
Find (Discover) server and Find application is utilized for the inner situating framework in this venture. Discover server is made on UBUNTU working framework and the Find application is downloaded from the Play store in android.
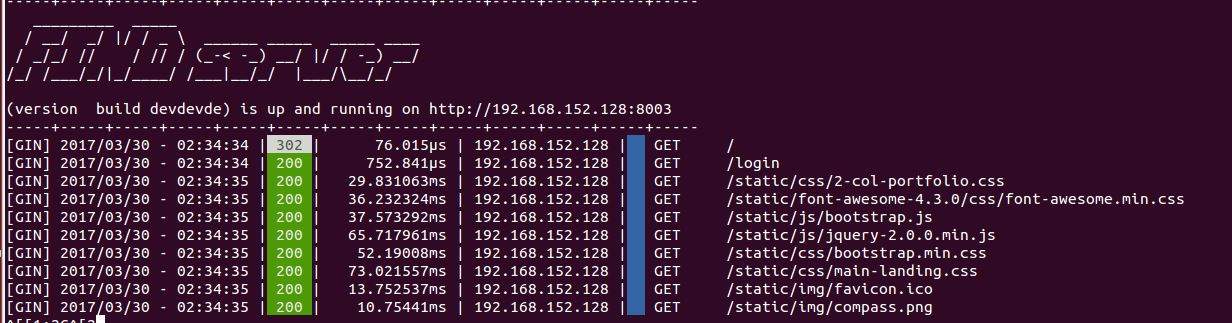
Figure 4.3. FIND Server
It is the photo of the Find server that has been made on the Linux working framework. Presently there is the Discover application that has been downloaded from the Play store. The working chart of the application is as in the accompanying:
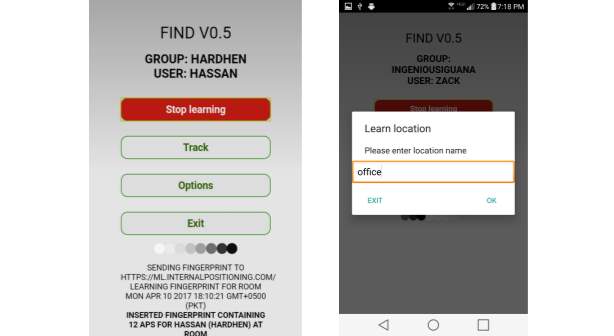
Figure 4.4. FIND Application
So here are the photos of the Discover application that is being utilized as a part of our venture.
4.2. Working And Functionality (Usefulness):
Presently it was about the server and the application that is being utilized as a part of the venture. Presently in the event that we gain additionally ground about the usefulness and the working of the server, at that point we need to give a brief and nitty gritty data about the working situation of the Discover server or this inner situating framework that how it is functioning and what are the things that are really required in this and how they are functioning and how they are associated with each other.
So as a matter of first importance gone to the pecking order that how this model is functioning. This all can be clarified from the accompanying picture:
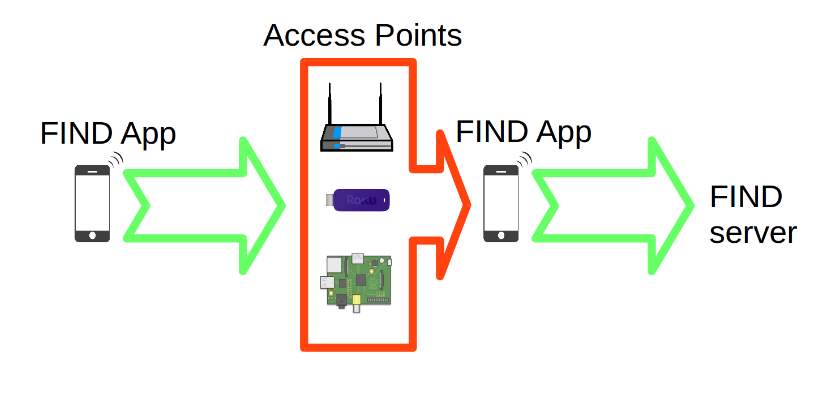
Figure 4.5. Setting Up FIND Server
So it is the photo of the setup that how the Discover server can be setup. The chain of importance can be portrayed in the accompanying stream sheet or in well-ordered process.
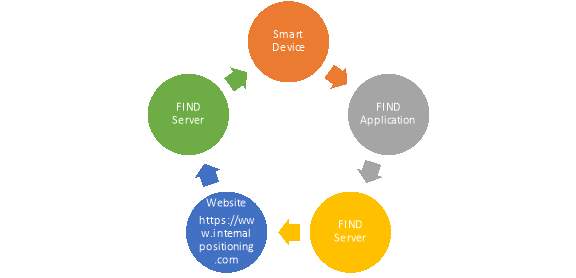
So the tracking of any of the brilliant gadget can be made through this procedure that utilized as a part of this the greater part of the procedure.
Presently there are diverse phrasings, terminologies and the fundamental procedures that are utilized as a part of this venture. Essentially they are the foundation of the venture that are being utilized to play out the greater part of the functionalities.
These the greater part of the capacities are incorporated into a particular sort of subject or the key term where they are performed. That is known as API (Application Program Interface). It is portrayed totally in the up and coming subject.
4.2.1. API (Application Program Interface):
Application Program Interface (API) is an arrangement of schedules, conventions, and instruments for building programming applications. A Programming interface indicates how programming segments ought to connect. Also, APIs are utilized when programming graphical UI (GUI) parts. A decent Application Programming Interface makes it less demanding to build up a program by giving all the building squares. A software engineer at that point assembles the pieces.
The above composed focuses are portrayed in the accompanying one by one:
1. POST /learn:
Present a unique mark (Finger Print) to be utilized for taking in the order of the area. The data for the unique mark (Finger Print) is assembled from the WIFI customer – either the application or the program.
2. POST /track:
Present a unique mark (Finger Print) to be utilized for ordering the area. The data for the unique mark (Finger Print) is assembled from the WIFI customer – either the Application or the program.
3. GET /compute:
Recalculates the priors for the database for the gathering.
4. GET /location:
Gets the areas for the predefined user(s) in the predetermined gathering.
5. GET /locations:
Get a guide of the presently known areas, the quantity of fingerprints and the present exactness.
6. DELETE /username:
Erases all the following fingerprints for determined client in the predefined gathering.
7. DELETE /areas:
Mass erase areas.
8. DELETE /database:
Erase database and all related information.
9. PUT /Mixin:
Permits abrogating of the Mixin parameter. Estimation of 0 utilizes just the RSSI Priors, while estimation of 1 utilizes just the Macintosh pervasiveness measurements.
10. PUT /database:
Relocate a database. This duplicates every one of the substance of one database to another. In the event that the gathering does not exist, it will be made. The gathering that is moved from is not erased.
11. PUT /MQTT:
Enables you to get to MQTT surges of your information. This is accessible on people in general server utilizing the outsider (3rd Party) mosquito server.
12. GET /status:
Returns status of the server and some data about the PC.
13. GET /GROUP/dashboard:
A dashboard site for the predetermined gathering. We can alternatively pass a parameter that will channel the predefined clients for the live real-time (continuous) tracking.
Chapter No. 05
Results
5.1. Results:
So here comes the result portion. Up till now we have done with our FIND server which was the main objective of our project. Here is the final result of the picture of the server which we have made during the completion of our project.
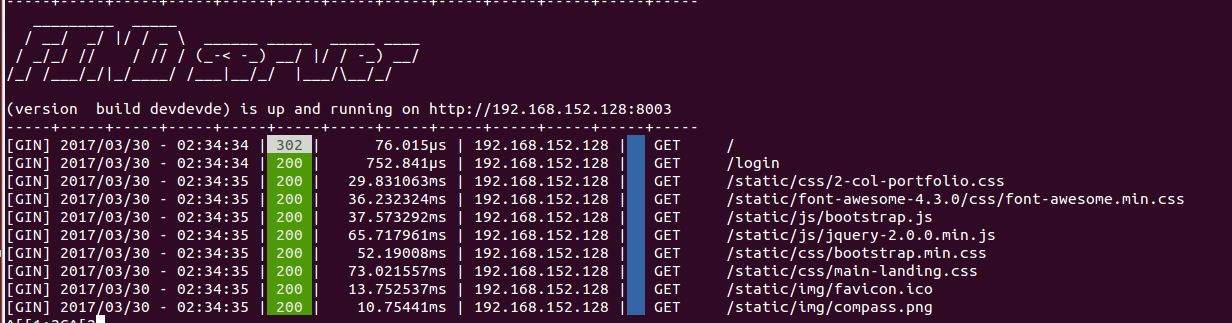
Figure 5.1
This is our server and we can see the different values on it. These values depicts the following characteristics or the functionalities of the server.
- The access time
- Different processes taken during the interaction
- Time consumed for each process
- Link status
- IP address for each of the connected device
These all of the steps are done in the server portion which is being run on the UBUNTU operating system. Now we have the other part of our result which is from the mobile application.
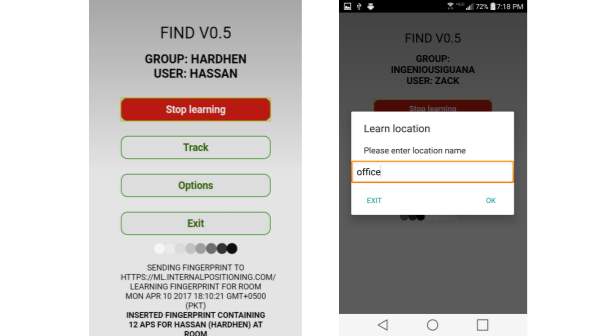
Figure 5.2
This is the interface of the mobile application that is named as “FIND” and is available at the android server. Now the functionality of this application is written in the following.
- First of all a group has been made on this application
- Here that group is named as office
- Then that specific place “Office” is learnt by the application
- “Tracking” option is used to track or locate the position of that specific device
- All of the data is sent to the FIND server
- The server shows the location of that device
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Technology"
Information Technology refers to the use or study of computers to receive, store, and send data. Information Technology is a term that is usually used in a business context, with members of the IT team providing effective solutions that contribute to the success of the business.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




