Development of a Blog on Network Management and Security
Info: 5447 words (22 pages) Dissertation
Published: 23rd Feb 2022
ABSTRACT
As we may know that cyber-attacks have been more advanced more than ever. Therefore, I have decided to make my topic focused on making blogs on the internet. They will be designed using programming language. The blogs will be as an E-bag that helps teachers and network managers in finding new security tools which could help monitoring some application on the internet. In addition, there will be tools that help to easily work within private networks and maintain copyrights. Video instructions will be provided in English and Arabic.
Table of Contents
Click to expand Table of Contents
1. Introduction
1.1. What is the problem?
1.2. Solution a problem via blog on network security
2. BLOG ON INTERNET
3. Subject on blog of network security
3.1. Attack types
3.1.1. Password security
3.1.2. Dos attack
3.1.3. Man in the middle attack
3.1.4. DNS attack
3.1.5. Phishing
3.1.6. End to End Encryption
3.2. Tools of network management and monitor
3.2.1 NetSupport Manager
3.2.2 Cisco Network Magic
3.2.3 PRTG network monitor
4. IMPLEMENTATION
4.1. Bootstrap Framework
4.2. Why using Bootstrap framework?
4.3. Brackets
4.4. Github and Stack Overflow
5. Design and architecture
5.1. What is a bootstrap?
5.2. Design home page for the website
6. RESULTS
7. CONCLUSION
8. REFERENCES
1. Introduction
The aims of the E-bag to achieve the safety of the networks and also make easier to access on anytime and anywhere. The blogs will be as an E-bag that help teachers and network managers in finding new security tools which could help monitoring any network. To remedy most of the dangers of network security and to spread awareness among network officials and to take advantage of them in the long term and confined in one place. So, this will be is blog on network security.
1.1 What is the problem?
The development of computers and information systems has coincided with the development of information networks and the high speed at which information can be disseminated. The growth in the use of electronic information has increased the problems of network security and information such as hackers, viruses and others. This posed a major threat to the infrastructure of government and private enterprises. The risk of network and information security problems lies in, among other things, a reduction in the performance of computer systems, or their total destruction, which disrupts the vital services of the enterprise. The other side includes the confidentiality and integrity of the information, where access to information and coding or secret information may lead to significant material losses.
1.2 Solution a problem via blog on network security
Avoid such a problem. It is best solution of user know about the different types of attacks that threaten to the network. So, that he can choose the most appropriate solutions in order to protect his network. The IT experts divide the risk of networks into four sections so that they can develop effective solutions for each type of attack. First, unorganized threats that come from novice hackers; they use programs that are ready to penetrate the network system, access private data, or launch malware. Second, organized threats come from hackers with extensive experience in attacking network systems. They are always familiar with network design, protection issues and networking procedures. They also have the ability to design applications that help them achieve hacking purposes. There is another type of network risk, which is known as internal attacks and is responsible for individuals within the company. For example, a staff member who is dissatisfied with their position within the company and who has the ability to access the network. Finally, external attacks are responsible for individuals outside the company. When you try to detect these kinds of threats, you may find more than one attack within the network. This type of attack is possible because of external and internal sources at the same time. To remedy most of the dangers of network security and to spread awareness among network officials and to take advantage of them in the long term and confined in one place. So, this will be is blog on network security.
2. BLOG ON INTERNET
The E-bag is designed to be a reference for the engineer and the teacher. It is dedicated to finding everything you need to monitor, manage and protect your network in one place. The teacher benefits to teaching students how to manage the network or protect the network. And how some programs of the network work with the explanation of videos and the student can benefit from them If the student wants to learn more about the mechanism of work and management and protection of the network. For the engineer, he may find what he is looking for on the site where he finds in one place the latest tools and programs with an explanation of how it works and stop him from searching and confusion in the sites. Also benefit the engineer if he encountered the problem of all that he had to enter the site and discuss the problem through the chat located on the site. There are those who respond and help engineers to solve their own problems with their network. As well know the latest types of breakthroughs and attacks on the network also can avoid the damage resulting from penetrations and attacks. With the development of hackers and the evolution of their tools, we need to spread the mechanism of how to avoid attacks and correct them.
3. Subject on blog of network security
Subjects are divided into E-bag into three main axes and needed by each of the network administrators as follows:
- Attack types: The attacks that are happen in the network are a lot and I collected the most common ones that are my do a height reflect bon the users. In the part will find a lot of information that are related to those types of attack and he can read about the attack itself and how to prevent it in order to have security while using the information technology.
- Tools of network management: At the section of the tools I will display the most important authorized software to manage the network and with taking under consideration that all of those resources are authorized. With the explanation of those software.
- Network monitoring: Ones of the most important things we should know is the network monitoring and to learn how to protect our networks via this section.
3.1 Attack types
One of the most important things we should know is the types of attacks on the network, and to learn how to protect our networks, in this chapter I will display the most important and common types of cyber-attacks such as:
- Password security.
- DOS attack.
- Man in the middle attack.
- DNS attack.
- Phishing.
- End to end encryption.
3.1.1. Password security
Password is a security process that protects information accessible via computers that needs to be protected from certain users. Password protection allows only those with an authorized password to gain access to certain information. Most vendors have been able to implement their own approach to safe guarding those passwords and this has resulted in a mix of safe and insecure systems. Maintaining password security is a problem of ever increasing importance. With The increase in online services, the amount of credentials per person has also increased dramatically. News reports of hackers stealing credentials are increasing and so are notices to users requesting password changes. Through this research I’m trying to find how attackers are able to obtain these passwords. A Password is a stream of characters (alphabets, numbers and/or special characters) that is used by individuals to authenticate themselves, to prove who they say they are. Passwords are not used to prove ones identity alone, they are used as checkpoints to provide access to resources. In the age of empires, passwords have been used as secret words or phrases at the entry points. If a messenger brings information on war on enemies or some other important info, kingdoms could be deceived if they openly receive such information. The enemy nation could intercept and change the information, change the messenger or send a surrogate to relay a message that could be advantageous to the enemy nation [1].
3.1.2. Dos attack
Denial-of-service (DoS) attack is attacking or campaign which occurs from a single source and has more than one tool and the target of this attack send a lot of data. Everything in activity illegal and accumulate the majority of his quickness sure no matter accustomed from power, even within the area of recommendation security, day of remembrance accent on the podium illegal of quickness and therefore the acceleration cannot be crossed, and it charcoal sure at that speed, and therefore the action of tasks, even with the event of science and technology in correct charcoal stronger processors and computers sure behindhand of the speed, and as well accumulate the majority of abstracts handled by a restricted, no bulk however this abstracts accomplished the consequence of accessories sure assertive bulk will be self-addressed, these abstracts settle for supplemental on top of accommodation cannot enable them and break down, this is often the alive assumption of abnegation of account every kind of attacks, that flood the ambition an enormous bulk of applications and abstracts in adjustment to quickness the higher admeasurement of the activity ambition can collapse or get out of the account and suitably settle for accomplished my ambition and that I was able to stop that ambition from set up or abnegation of users that aim to yield advantage of it, and this abstraction has been renamed abnegation of account attacks (denial of Account attacks) this fond of advance is alleged in some circles “AIDS Internet” as a result of it’s no cure however, no matter hit the ambition specifications, acceleration, and quickness to abode and settle for applications abide aural an outlined quantity of applications no bulk however ample cannot settle for requests for supplemental than that range, these attacks, abide one in every of the lots of atrocious attacks on the net aggressive accompaniment and government and everyone the networks are acceptable to look to a lower place advance abnegation of Account and therefore the collapse of its networks and its organs [2].
3.1.3. Man in the middle attack
Nowadays computer network is improved and secure it needs a lot of effort in order to protect the user data when they use the network. These improvements of computer networks make hackers think in different ways in order to attack the network for several reasons like damage a data or steal important information. One of most used techniques that hackers used to steal credential information is called “Man-In-The-Middle” (MITM). This technique works when the victim and attacker are in same LAN and one device start to communicate with another device using http connection or any other connection which is not secure enough (not encrypted). The attacker puts his computer between this communication without knowledge of victim. The attacker set up a point for himself between the connection so, he can capture the data also, he can change and manipulate the data if he want to. The basic idea behind this kind of attack is to convince the victim that he is really communicate with destination that he wants directly. But in reality, the attacker is sitting in between and pretend as if he the destination. By tricking the victim, he will send to the attacker all the data then the attacker forward it to the destination so the data that travel through the network between victims will not be interrupted based on that none of both victim will notice that their data is being sniffed. Man in the middle attack could happen in two ways passive and active. In the active attack the data that travel from victim to the destination is manipulated by the attacker then is sent to the receiver. Passive attack it’s accrue when the attacker just monitor the data without change anything then send it to the destination [3].
3.1.4. DNS attack
DNS Is the abbreviation for the phrase (Domain Name System), it is technology and it is system that stores information relating to domain names (domain names) in distributed database on the Internet, and the information linking the DNS names and addresses associated with the domain. DNS is working to translate the words of the scale names to addresses (IP address).it used for translated the IP address to websites. DNS Spoofing is the kind of serious computer attacks, specifically attacks that fall in the vicinity of computer networks, The system easier for us to remember URLs Given that the system information not accept only numbers, and here comes the DNS which converts domain names to ip addresses the role, but has been exploiting this service in an offensive identity theft, where an attacker would alter the numerical IP address of the site in the network that the victim connected to it and renames a server or a page forged, and the process is done by modification in the Hosts file located in Windows, however, this method became exposed from Windows became prevent an modification to this file and also become exposed to anti-virus for this became the hackers used Router Pharming and is an attack are the entry of the router settings through the normal course of your password so you have to change it or through a gap, and at the entrance to the router, the attacker changes the IP address to anther IP address for any website [4].
3.1.5. Phishing
Phishing is technique used to steal personal information through spamming, fake websites, unofficial applications or other deceptive means, that’s means someone create a website which resembles original website 100% and the website which created asked for specific data such as request information entry or data update or add credit card and so on. So, this way is start by sending a message which similar to the message the original company and the content of message request to entry the link to update data, sometimes the link malicious files which help phishersto control device and steal data. To avoid Internet phishing, people should have knowledge of different types of phishing techniques and they must also be conscious of anti-phishing techniques to defend themselves from getting phished [5].
3.1.6. End to End Encryption
Encryption was used before the creation of Internet and is known as the way to convert the text from something it can be understand and readable to encryption text that cannot be understandable to stop the wrong people that they don’t have permission from reading the message or Understood. We can see today the internet has every things in the world for examples your personal information, bank account and the other accounts or information that can be stolen from hackers, so we need to keep our critical information safe from hacker by using the encryption. So we use the encryption to encrypt the message or the information and we use decryption to open the encryption to return the message to the original form. Also there are only two ways to open the encryption by using the private or public key and the strong encryption depends on the algorithm of the encryption and the key length [6].
3.2 Tools of network management and monitor
At the section of the tools I will display the most important authorized software to manage the network and monitor it. With how to install and using for the tools of network management and monitor such as:
- NetSupport Manager.
- Cisco Network Magic.
- PRTG network monitor.
3.2.1 NetSupport Manager
NetSupport Manager is using to remote access of desktop, tablet, laptop and smartphone. So, NetSupport manager is monitor multiple systems in a one action and the most important features as follows [7].
- Platform Flexibility
- Monitoring Systems with Interactive Thumbnails
- Remote Control
- Auto-Grouping of Remote Systems
- File Transfer
- Chat, Messages, Help Requests and Audio Support
Key Security Features:
- Password protection of all systems.
- Data Encryption.
3.2.2 Cisco Network Magic
The Cisco Network Magic makes creating a network of 8 computers (maximum) and connecting them together and manage and control them very easily whether it is a wired or wireless network so that it must be installed on all the devices connected to the network and the master is the one that controls the rest of the devices as they do these functions [8].
- Control the Internet connection for all devices and monitor this connection and piece when necessary.
- Share files of all kinds on the network and share the printer for all devices on the network.
- Network Protection.
- Network Repair and Maintenance.
- Ease of use.
3.2.3 PRTG network monitor
PRTG network monitoring software has many features and has professional graphical interfaces. It provides reports of all types and performance comparison in addition to all types of alerts via e-mail or SMS [9].
Features:
- Supports data acquisitions via packet sniffing and Net-flow.
- Easy installation and use on all windows versions.
- Classifies network traffic by IP address, protocols, and other parameter.
- Capable of monitoring up to several thousand sensors.
- Works with most switches, routers, firewalls, and other network devices.
4. IMPLEMENTATION
To implantation (Blog on Security Networks) Website using (HTML5, CSS3, and JavaScript) languages:
- Bootstrap Framework.
- Brackets.
- Github and Stack Overflow.
4.1 Bootstrap Framework
First Step to build website using Bootstrap Framework, There is view file you should include it in your project:
├── css/
│ ├── bootstrap.css
│ ├── bootstrap.min.css
├── js/
│ ├── bootstrap.js
│ └── bootstrap.min.js
│ └── html5shiv.min.js
│ └── respond.min.js
│ └── jquery-3.2.0.min.js
└── fonts/
├── glyphicons-halflings-regular.eot
├── glyphicons-halflings-regular.svg
├── glyphicons-halflings-regular.ttf
├── glyphicons-halflings-regular.woff
└── glyphicons-halflings-regular.woff2
4.2 Why using Bootstrap framework?
- To get fully responsive website I Used Bootstrap’s grid system.
- Easy to start with and for saving a lot of time because it provides me a lot of help component.
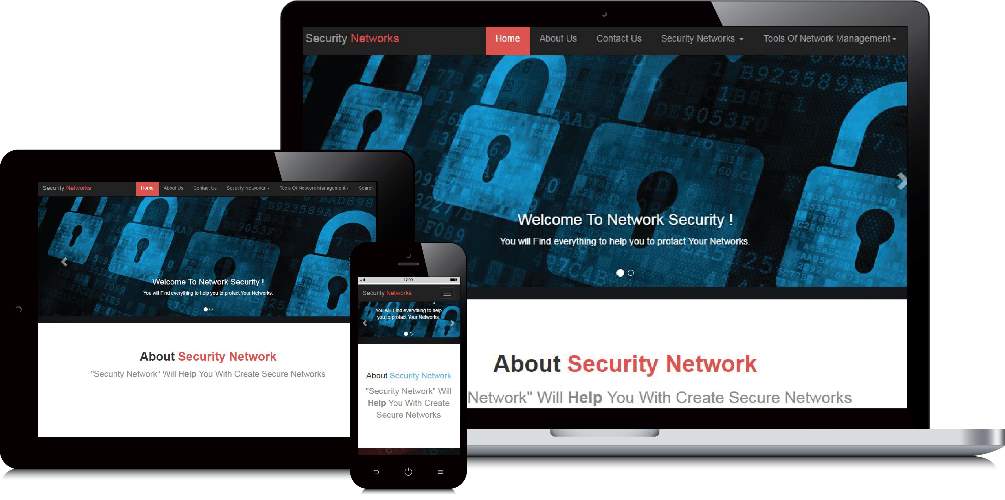
Figure 1: example for a responsive of the website
When look at (figure 1) will be proof to I created a website that have a high level of flexibility and I have done that in order to achieve the needs of the users and to make it so easy for them it works in all types of mobile phones, the same idea with the ideas and the personal computers.
4.3 Brackets.
Brackets editor is integrated interface that includes various tools that help programmer’s editor code. Also has the autocomplete, which helps users avoid errors as well as saving lots of time and effort, the program provides you with many simple options and tools that help in preparing a website [10].
- A modern, open source text editor that understands web design.
- Use it to take a quick look of design and test some functions.
4.4 Github and Stack Overflow.
Github [11] and Overflow [12] are a community for programmers, there a lot to learn from them, and it been so helpful for myself to star building my first Website.
5. Design and architecture
5.1 What is a bootstrap?
The bootstrap is a collection of tools from the framework, let you create a website. It represents a large and free set of tools and options for developing and designing websites in an easy, fast, and compatible way with browsers and mobile phones [13].
5.1.1 Features of a bootstrap
- Responding to tablets and smartphones: The bootstrap is easy and flexible to use, and you can make the site easy compatible not only with computers but also with phones, tablet and small screens.
- Compatibility with browsers: The bootstrap is not only compatible with modern browsers but also a solution for users of “internet explorer“
- Open source: The bootstrap is an open source project that you can modify as you like. It is hosted on github [14].
5.1.2 Components of bootstrap
Bootstrap introduces the concept of components. These components are common parts of HTML pre-formatted, sometimes using JavaScript. Bootstrap components can be used as they are, or these components can be reformatted. All you need to do is change the values of variables In Bootstrap, however, if you want more flexibility to change, the developer can always change and modify, and in returning to the project [15].
Example:
For navigation, the “ ” tag will be used with the navbar.
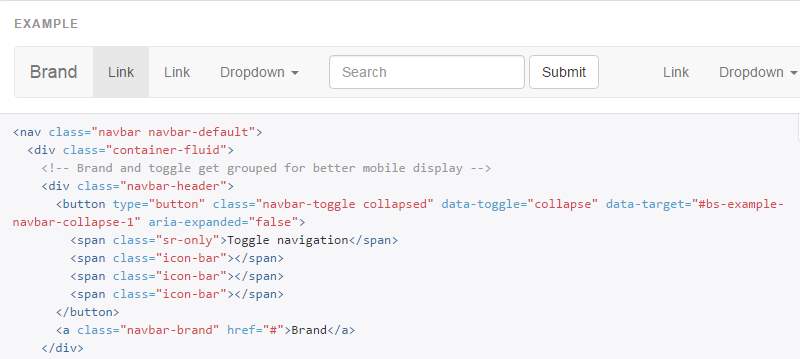
Figure 2: This is a part form navbar code
5.2 Design home page for the website.
5.2.1 The first thing the user will see in the website is a carousel
- I’m using the Carousel for the welcome of the visitors and display some new subject in the website.
- Below is the code of carousel at (index.html) page.

Figure 3: This is the code of carousel at (index.html) page
5.2.2 The website is having Static Navbar
- To allow the visitor easily move between sections of the website.
Figure 4: This is the code of carousel at (index.html) page
5.2.3 Attacks Types Section
- I use carousel to Display Types of attacks in thumbnail to make it easy to visitor to take a quick look for all attacks types.
- For that I write thumbnail code inside carousel.
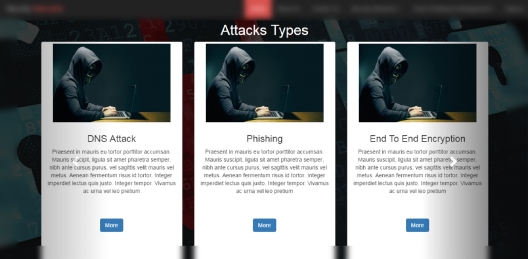
Figure 5: This is section of attack types.
The attacks that are happen in the network are a lot and I collected the most common ones that are my do a height reflect bon the users. In the page the user will find a lot of information that are related to those types of attack and he can read about the attack itself and how to prevent it in order to have security while using the information technology.
5.2.4 Network Monitoring Section
- For the Network Monitoring I decided to go with brief for that section, for more details about this section there is button named (Learn More) when visitor click on it then it will take the user to another page.
- For few times I will delay building that page later on.
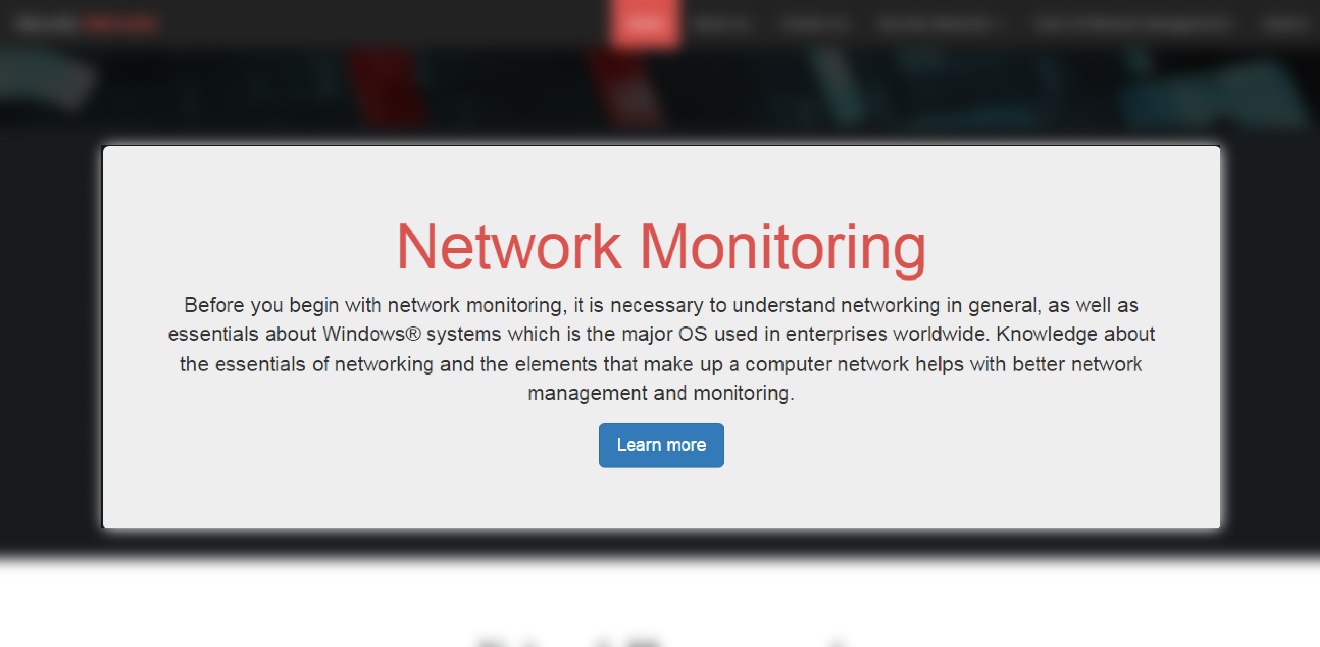
Figure 6: This is section of attack types.
5.2.5 Tools Of Network Management
- From Navbar if users choose one of tools list it all show video expiation and description, and visitor can post comment in the video in modal.
- A modal is flexible dialog prompts.
- In the below how look like the Modal.
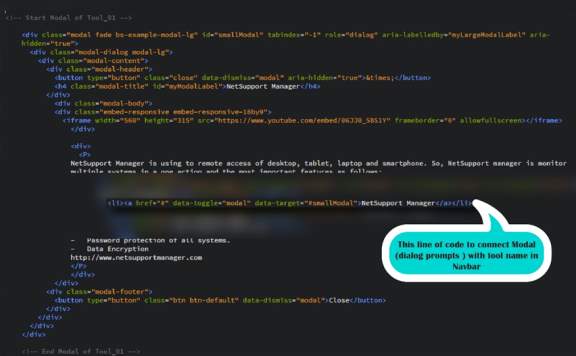
Figure 7: this is the code of Modal.

Figure 8: result of figure 5.
5.2.6 Contact us Section
While thinking of the best way to give services to the users I came up with that solving the problems that the user might face a problem with the way of how to communicate with me so he can reach me with the E-mail address and I sometimes use the twitter in order the user to reach me in two ways and the same thing I’m doing with the YouTube but with answering the commands I see from the users.
- In this section visitor for the website can send there Question and suggestion
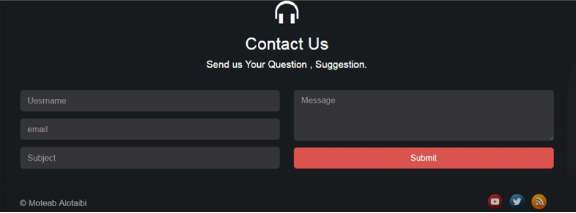
Figure 9: This is figuring of contact us.
6. RESULTS
How to access to the lesson on blog in the internet:
The E-bag is easy to get lessons from, let’s suppose that we want to the lesson related to the password security. Follow the instructions below.
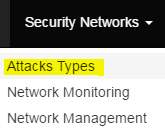
Figure 10: example of step 1
Step 1: press on security networks that will be shown above after that press on attack types. (Like figure 8)
Step 2: Then it moves to the list of lessons. (Like a figure below) when you press on more you go to the video and description about the lesson.
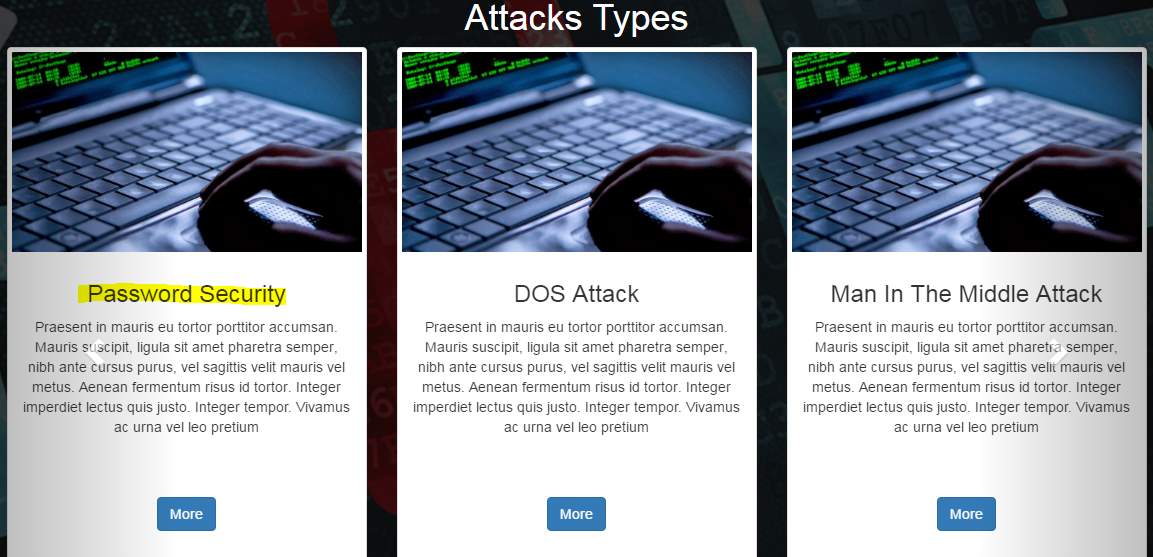
Figure 11: example of step 2
Figure 12: example of step 3
Step 3: After that we see the lesson and the description of the lesson. (Like a figure below).
When look at (figure 11) find that the video is uploaded via YouTube
Way the video on YouTube?
Once you click on the lesson you want the it will drive you to another page you will find in this page a video related to the lesson you want and the video you will find a description that explains about the lesson, the video is linked to YouTube and as soon as we want the user to have quality of speed we have to use YouTube we also need the commands of the video as a feedback in order to find out if the commands are question or opinions. The most benefit of comments on video is exchange of experiences also to help those who have a problem on video or some point on a video it’s not understand to need more explain. The users are able to share the videos with each other and that is an advantage of me so the best way for me is to use videos on YouTube.
7. CONCLUSION
In conclusion, I would like to present my graduation project which is an electronic bag that contain some tools and explanations related to networks management and security. This E-bag helps engineers and teachers locating the needed tools and instructions in one place easily. They can use this E-bag at any time and place. Even though this project was very difficult to accomplish, I have learned through facing problems and trying to find fast and accurate solutions. Since my major is networks, I have had basic knowledge of various programming languages such as HTML, CSS, and JavaScript. With the increasing use of smartphones, tried to find ways to make my website popular and easily searchable through these smart devices. I made a very flexible and easy to browse website. I have also learned how to create responsive websites, and could make a Bootstrap framework, as well. I have faced a lot of issues with JavaScript, but I could overcome all of them using the website W3schools. Through this website, I learned about Bootstrap framework which is an open-source that has been developed GitHub. I consider W3schools as one of the most source for finding detailed instructions on many things. In addition, I found some helpful videos which enabled me solve problems I had encountered. Brackets program was used to find code editors. It also has some useful features such auto completion for entered codes as well as codes coloring which help recognizing codes from one another. In the future, I will try to develop my website by adding more features to make usurers easily browse it. I also would like to make a database so, members can be added to the E-bag and make it available for authorized engineers and teacher. Also, a chat room will be made to facilitate the website member’s communication. A forum for lessons and explanatory videos will be created by engineers and teachers in an organized fashion. Uploading these lessons will be done in appropriate and understandable ways. So, everyone can share their expertise and knowledge among the members of the website. The website is not available in Arabic due to lack of Arabic networks security sources, but it will be available in the future. The website will be available on Apple Store, and Google Play for smartphones.
8. REFERENCES
[1] Madero and Alvaro, Password secured systems and negative authentication. Massachusetts Institute of Technology, 2013.
[2] “Understanding Denial-of-Service Attacks | US-CERT.” [Online]. Available: https://www.us-cert.gov/ncas/tips/ST04-015. [Accessed: 14-May-2017].
[3] Subodh Gangan, A Review of Man-in-the-Middle Attacks. 2015.
[4] “Hack Like a Pro: How to Spoof DNS on a LAN to Redirect Traffic to Your Fake Website,” WonderHowTo. [Online]. Available: https://null-byte.wonderhowto.com/how-to/hack-like-pro-spoof-dns-lan-redirect-traffic-your-fake-website-0151620/. [Accessed: 14-May-2017].
[5] “Ads on popular Search Engine are leading to Phishing Sites.” [Online]. Available: https://www.govcert.admin.ch/blog/16/ads-on-popular-search-engine-are-leading-to-phishing-sites. [Accessed: 14-May-2017].
[6] “What is encryption? – Definition from WhatIs.com.” [Online]. Available: http://searchsecurity.techtarget.com/definition/encryption. [Accessed: 14-May-2017].
[7] “NetSupport Manager,” NetSupport Manager. [Online]. Available: http://www.netsupportmanager.com. [Accessed: 14-May-2017].
[8] “Security Products and Solutions,” Cisco. [Online]. Available: http://www.cisco.com/c/en/us/products/security/index.html. [Accessed: 14-May-2017].
[9] “PRTG Network Monitor – Powerful Network Monitoring Software.” [Online]. Available: https://www.paessler.com/prtg. [Accessed: 14-May-2017].
[10] “A modern, open source code editor that understands web design,” Brackets. [Online]. Available: http://brackets.io. [Accessed: 14-May-2017].
[11] “Build software better, together,” GitHub. [Online]. Available: https://github.com. [Accessed: 14-May-2017].
[12] “Stack Overflow.” [Online]. Available: https://stackoverflow.com/. [Accessed: 14-May-2017].
[13] “Bootstrap · The world’s most popular mobile-first and responsive front-end framework.” [Online]. Available: http://getbootstrap.com/. [Accessed: 17-May-2017].
[14] “W3Schools Online Web Tutorials.” [Online]. Available: https://www.w3schools.com/. [Accessed: 17-May-2017].
[15] “Components · Bootstrap.” [Online]. Available: http://getbootstrap.com/components/. [Accessed: 17-May-2017].
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




