A Project Report on E-Decor
Info: 11060 words (44 pages) Dissertation
Published: 16th Dec 2019
Tagged: Design
ABSTRACT
E-Decor is the android application. There are many apps of online booking for movies, purchases goods or fashion but there is no app for Events and Wedding Decorators, Caterers, Photographer etc. So, we have decided to build an app that display all the event and wedding service provider available at user’s location so they can see all the information about them directly through app. Using this application, customer can aware idea of recent themes and decoration regarding their function
Table of Contents
| TITLE | |||
| CERTIFICATE PAGE | I | ||
| DECLARATION OF ORIGINALITY | II | ||
| ACKNOWLEDGEMENT | III | ||
| ABSTRACT | X | ||
| TABLE OF CONTENT | IV | ||
| List Of Figures | VII | ||
| List Of Table | IX | ||
| CHAPTER-1 | |||
| Introduction | |||
| 1.1 | Project Summary | 1 | |
| 1.2 | Aim and Objective of Project | 1 | |
| 1.3 | Problem Specification and scope | 1 | |
| 1.4 | Technology and Literature Review | 3 | |
| 1.5 | Materials/ Tools are Required | 3 | |
| CHAPTER-2 | |||
| Project Management | |||
| 2.1 | Project Planning and Scheduling | 4 | |
| 2.1.1 | Project Development Approach and Justification | 4 | |
| 2.1.2 | Project Plan | 4 | |
| 2.1.2.1 | Milestones | ||
| 2.1.2.2 | Deliverables | ||
| 2.1.2.3 | Roles | ||
| 2.1.2.4 | Responsibilities | ||
| 2.1.2.5 | Resources | ||
| 2.2 | Risk Management | 7 | |
| 2.2.1 | Risk Identification | 7 | |
| 2.2.2 | Risk Analysis | 7 | |
| 2.2.3 | Risk Planning | 8 | |
| CHAPTER-3 | |||
| System Requirement | |||
| 3.1 | User Characteristics | 11 | |
| 3.2 | Hardware And Software Requirements | 11 | |
| 3.3 | Constraints | 12 | |
| CHAPTER-4 | |||
| System Analysis | |||
| 4.1 | Study Of Current System | 14 | |
| 4.2 | Problem And Weakness Of Current System | 14 | |
| 4.3 | Requirement of new system | 14 | |
| 4.3.1 | Functional Requirements | 14 | |
| 4.3.2 | Non-functional Requirements | 14 | |
| 4.4 | Feasibility study | 15 | |
| 4.4.1 | Technical Feasibility | 15 | |
| 4.4.2 | Economic Feasibility | 15 | |
| 4.4.3 | Operational Feasibility | 16 | |
| CHAPTER-5 | |||
| System Design | |||
| 5.1 | Function of System | 17 | |
| 5.5.1 | Use Cases | 17 | |
| 5.5.2 | Data Flow Diagram | 18 | |
| 5.5.2.1 | Context Level | 18 | |
| 5.5.2.2 | First Level | 19 | |
| 5.5.3 | Class Diagram | 25 | |
| 5.5.4 | Activity Diagram | 26 | |
| 5.2 | Data modelling | 29 | |
| 5.2.1 | ER Diagram | 29 | |
| 5.3 | Data dictionary | 30 | |
| CHAPTER-6 | |||
| Implementation Details and Planning | |||
| 6.1 | Implementation Environment | 39 | |
| 6.1.1 | Implementation planning | 39 | |
| 6.1.2 | Administration module implementation | 39 | |
| 6.1.3 | User components implementation | 39 | |
| 6.2 | Security Features | 40 | |
| 6.3 | Coding Standards | 40 | |
| 6.4 | Input and Output Design / screen shots of designing pages | 41 | |
| CHAPTER-7 | |||
| Testing | |||
| 7.1 | Testing Plan | 58 | |
| 7.2 | Testing Strategy | 60 | |
| 7.3 | Testing Methods | 61 | |
| 7.3.1 | Statistical Testing | ||
| 7.3.2 | Defect Testing | ||
| CHAPTER-8 | |||
| Limitation and Future Enhancement | |||
| 8.1 | Limitation | 63 | |
| 8.2 | Future work | 63 | |
| 8.3 | Conclusion | 63 | |
| REFERENCES | |||
LIST OF FIGURES
Figure No Figure Description Page
Figure 1.1 Android Architecture 4
Figure 1.2 Agile Development Model 11
Figure 2.2 Time Line 15
Figure 5.1 Use case 24
Figure 5.2 DFD-Context Level 25
Figure 5.3 DFD-First Level: User 26
Figure 5.4 DFD: First Level: Admin 27
Figure 5.5 Class Diagram 28
Figure 5.6 Activity Diagram 29
Figure 5.7 Register and login 30
Figure 5.7 Home page 30
Figure 5.7 Decoration and catering 30
Figure 5.7 Detail and photos 30
Figure 5.7 Get direction 30
Figure 5.7 Feedback 30
LIST OF TABLES
Table No Table Description Page
Table 1.1 JSON 6
Table 1.2 XML 7
Table 2.1 Project Plan 12
Table 2.2 Milestone 13
Table 2.3 Risk Type – Possible Risk 17
Table 2.4 Risk Planning 18
Table 3.1 Hardware requirements 19
Table 3.2 Software requirements 20
Table 5.1 User Registration 31
Table 5.1 Seller Registration 31
Table 5.1 Seller Details 31
Table 5.1 Seller Gallery 31
CHAPTER 1: INTRODUCTION
- Project Summary
E-Decor is android-based application. There are many apps of online booking for movies, purchases goods or fashion but there is no app for booking events and wedding decorators online. So, we have decided to build an app that display all the event and wedding service provider available at user’s location so they can see all the information about them directly through app.
- Goals and Objectives
The objective of the project is to achieve the goals listed below which will help user interact with the system and make maximum benefit out of it.
- Easy Management of seller (service provider) profile.
- Client can see all decorators, caterers, photographer etc. service providers
- Easy to search as per user’s requirement
- Easy Up gradation of profile
- Get direction to the service provider
- Easy to filter by location, city and area
- Better management
- Easily understandable software for end user and also for developer
- Customer Satisfaction
- To provide huge maintenance of records
- Scope:
- User can see all the service provider at his/her location.
- User can see all services of service provider like catering services, decorators, photographer, etc.
- Seller (Service provider) Upgrade his/her profile.
- Search is easy.
Administrator:
- Can login as Administrator.
- Can add the new Services provider (Seller).
- Can manage App users and Vendors data.
- Can manage complain and feedback.
Customer:
- Can register.
- Can login.
- Can see all vendors near at user location.
- Can see all the information of vendors like contact info., services, gallery etc.
- User can communicate with service provider for more information.
- Can reviews the service providers(Vendors).
Advantages:
- User can see all the available service provider near at his/her location or can also search it.
- User can see all the details of service provider like services, contact info, photo gallery etc.
- User can get direction to the particular service provider and also make a call to them.
1.4 Technologies and Literature Review of Past Work/System
The technologies use to develop “M2CI-Module to Code Interpreter” are as follow:
- Android
- Core Java
- JSON
- XML
- Android Studio & SDK
- PHP
- Android
Android is an Open Source and Linux-based OS for mobile devices such as smartphones and tablets. Android was developed by the Open Handset Alliance, manage by Google, and other companies.
Android Architecture:
Android operating system is a stack of software components which is divided into five sections and four main layers as shown below in the diagram.
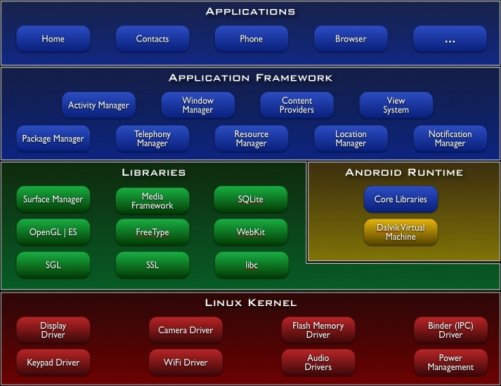
Figure 2.1: Android Architecture
Linux Kernel:
The bottom layer is Linux Kernel which is base of Android. This provides basic system functionality like process management, memory management, device driver management like Camera, Keypad, Display, Audio, Wi-Fi, etc. Also, the kernel handles all the things that Linux is really good at such as networking and a vast array of device drivers, which take the pain out of interfacing to peripheral hardware.
Libraries:
On top of Linux kernel there is a set of libraries used in Android, including open-source Web browser engine WebKit, SQLite database which is a useful repository for storage and sharing of application data, libraries to play and record audio and video.
Android Runtime:
Dalvik Virtual Machine is the key component of this third section of the architecture. Dalvik Virtual Machine is a kind of Java Virtual Machine specially designed and optimized for Android.
The Dalvik Virtual Machine uses some great Linux features like memory management and multi-threading, which is built-in in the Java programming language. The Dalvik Virtual Machine enables every Android application to run in its own process, with its own instance of the Dalvik virtual machine.
Application Framework:
The Application Framework layer provides many higher-level services like Activity Manager, Content Provider, Broadcast Provider, etc. to applications in the form of Java classes.
Applications:
All the Android application be at the top layer. We will write our application to be installed on this layer only. Examples of such applications are Phone, Contacts, Messages, Browser, Games etc.
2) Core Java
Java is used as default programming language to build Android application. Java is a high-level object-oriented programming language developed by Sun Microsystems.
Java source code files (.java extension) are compiled into a format called bytecode (.class extension), which can then be executed by a Java interpreter. Compiled Java code can run on most computers because Java interpreters and runtime environments, known as Java Virtual Machines (VMs), exist for most operating systems like Linux, Mac OS and Windows. Bytecode can also be converted directly into machine language instructions by a just-in-time compiler (JIT).
3) JSON
JSON or JavaScript Object Notation is a lightweight text-based open standard designed for human-readable data interchange. Conventions used by JSON are known to programmers, which include C, C++, Java, Python, Perl, etc.
- JSON: JavaScript Object Notation.
- JSON is a syntax for storing and exchanging data.
- JSON is text, written with JavaScript object notation JSON is easy to read and write than XML.
- JSON is language independent.
- JSON supports array, object, string, number and values.
| Table 1.1 JSON | |||||||||
| Filename extension | .json | ||||||||
| Internet media type | application/json | ||||||||
| Developed by | Douglas Crockford | ||||||||
| Type of format | JavaScript Programming language | ||||||||
4) XML
Extensible Markup Language (XML) is a markup language that defines a protocol for encoding documents in such a format that is both human-readable and machine- readable. The format of XML is purely a textual data format.XML design mainly focuses on document style.
The goals in designing the XML is to provide simplicity, efficiency, and provide stability over the Internet
.
| Table 1.2 XML | |
| Filename extension | .xml |
| Internet media type | application/xml, text/xml |
| Developed by | World Wide Web Consortium |
| Type of format | Markup language |
5) Android Studio & SDK
Android Studio is the official integrated development environment (IDE) for Android platform development. It was announced by Google and it is freely available under the Apache License 2.0.
Based on JetBrain’s IntelliJ IDEA software, Android Studio is designed specifically for Android application development. It is available for download on Windows 7 or higher, Mac OS X and Linux (64-bit OS), and replaced Eclipse Android Development Tools (ADT) which was used earlier by Google for building Android application.
The Android SDK is a software development kit provided by Google for Windows, Mac OS X, and Linux computers. Android SDK comes with predefined java classes and interfaces. The Android SDK is mainly designed to help developers create, test, and debug their Android apps. Android SDK also provides documentation, example code, virtual Android machines for running apps, framework code, support for development environments, debugging tools, and more.
6) PHP
PHP (hypertext pre-processor) is widely used open source general scripting language that is especially suited for web development and that can be embedded with HTML.
PHP code may be embedded into HTML code, or it can be used in combination with various web template systems, web content management systems and web frameworks. PHP code is usually processed by a PHP interpreter implemented as a module in the web server or as a Common Gateway Interface (CGI) executable..
What Can PHP Do?
- PHP can generate dynamic page content
- PHP can create, open, read, write, delete, and close files on the server
- PHP can collect form data
- PHP can send and receive cookies
- PHP can add, delete, modify data in your database
- PHP can be used to control user-access
- PHP can encrypt data
CHAPTER 2: PROJECT MANAGEMENT
2.1 Project planning and scheduling
Effective management of a software project depends on thoroughly planning the process of project. A well planned strategy leads to the best and optimal use of the resources available and ensures completion of project on time.
Project plan sets out the resources available to the project, the work breakdown and a schedule for carrying out work. The project needs a lot of research and thus scheduling was a difficult task as there was a need for carrying out a lot of study about various techniques and testing them at various stages, thus maintaining the schedule was also difficult.
2.1.1 Project Development Approach (Process Paradigm) and Justification
We have chosen the Agile Development Model for this system development. In any other development model initially developers have to identify requirements fully. If requirement changes then they have to change their methods of development, or if some requirements have to be removed then, after each iteration they can do modification in requirements.
While in Agile model customer can change their requirements any time. While coding is going on, parallel testing is simultaneously going on. Henceforth, the modification in code is easy and the team can work faster.
In software application development, agile software development (ASD) is a methodology for the creative process that anticipates the need for flexibility and applies a level of pragmatism into the delivery of the finished product. Agile software development focuses on keeping code simple, testing often, and delivering functional bits of the application as soon as they’re ready.
The goal of ASD is to build upon small client-approved parts as the project progresses, as opposed to delivering one large application at the end of the project.
Spiral Model
The spiral model is a risk-driven process model generator for software projects. Based on the unique risk patterns of a given project, the spiral model guides a team to adopt elements of one or more process models, such as incremental, waterfall, or evolutionary prototyping.
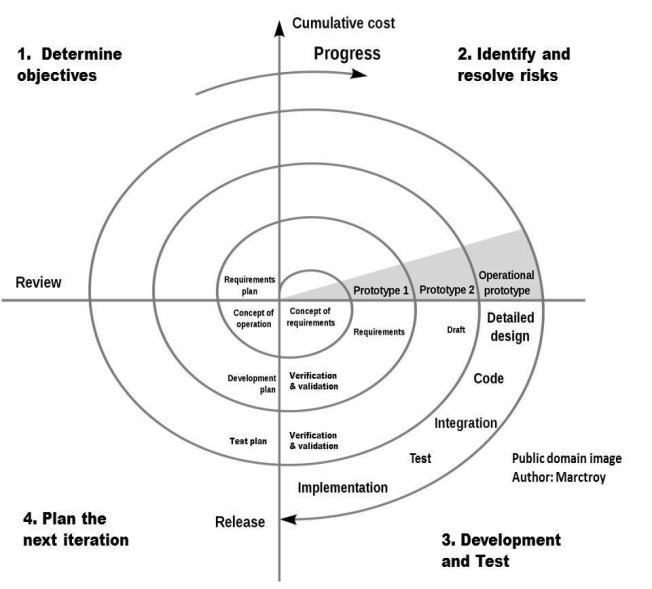
Figure 3.1: Agile Development Model
2.1.2 Project Plan
Table 2.1 Project Plan
| Task Description | Time Taken | Year |
| Domain Understanding | July | 2016 |
| Requirement gathering and analysis | August | 2016 |
| Define Objectives | September | 2016 |
| System Design | October | 2016 |
| Partial documentation | November, December | 2016 |
| Implementation | January, February, March | 2017 |
| Testing | April | 2017 |
| Final Documentation | May | 2017 |
2.1.2.1 Milestones
Management needs information. As project is tangible, this information can only be provided as documents that describe the state of the project being developed without this information it is impossible to judge progress at different phases and therefore schedules cannot be determined or updated. Milestone is an end point of the project process activity.
Table 2.2 Milestone
| Project process activity | Milestone |
| Project Plan | Project schedule |
| Requirement collection | User requirements, System requirements |
| Design
Data Design User Interface Design |
System Design Documents |
| Implementation
Code for giving security Code for reports |
Access Rights
Report Generation |
| Testing | Setting validation and error messages |
- Deliverables
At each milestone there should be formal output such as report that can be represented
to the management.
- Milestones are the completion of the outputs for each activity.
- Deliverables are the requirements definition and the requirements specification.
- Milestone represents the end of the distinct, logical stage in the project.
- Milestone may be internal project results that are used by the project manager to check progress.
- Deliverables are usually Milestones but reverse need not be true.
- We have divided the software process into activities for the following milestone that should be achieved.
2.1.2.3 Roles
This phase defines the role and responsibilities of each and every member involved in developing the system. To develop this system there was only one group with three members working on the whole application. Our team structure is of mixed control team organization as it consists of both democratic and chief programmer organizations.
The democratic arrangement at the senior engineer’s level is used to decompose the problem into small parts.
- Responsibilities
Each member was responsible for each and every part of developing the system.
Each of the group members has sufficient knowledge in several programming languages. Each member has to work to the whole with complete unity to end up each activity in time. The task is divided so that each member should complete it and carry forward to the next member with their tasks smoothly.
2.1.2.5 Resources
Android Studio is the default integrated development environment, it contains base work space and extensible plugin system for the customer in the environment written in Java and XML.
Android SDK software development kit is required to develop Android based application. It contains built in classes, methods and interfaces.
JDK 1.6+ java development toolkit is generic and used to develop java based application. It allows language construct like classes and methods.

Figure 2.2: Time Line
2.2 Risk Management
Risk management is an extremely important task in all projects and so it is in this project as well. Software is a difficult undertaking. So lots of things can go wrong. It is for this reason that being prepared understanding the risks and taking proactive measure to avoid or manage them is a key element of good Software Project Management.
Recognizing what can go wrong is the first step called Risk identification. Next each risk is analysed to determine that it will occur and the damage that it will do if it does occur. Once this information is established, risks are ranked, by probability and impact. Finally, a plan is developed to manage those risks with high probability.
2.2.1 Risk Identification
Risk is an inevitable concept of software projects and it mainly concerns future happenings. We want to produce a well working system therefore we have to consider all the possible defects and unexpected conditions. First of all, we have to define possible risks and develop a management style for each of them. After a deep investigation we identified the following possible risks of our project.
- The tasks that are planned in the schedule may overflow
- Some team members may not focus on the project deeply.
- A team member may leave the group.
- The team members may not be suitable for group work.
- The motivation of team members may not be sufficient.
- The number of people in the project may not be enough for the project.
2.2.2 Risk Analysis
For the risk management we select the most catastrophic risks of this list and we developed special several strategies in order to handle or block these unexpected situations. According to our risk table the most effective risks are as show below:
Table 2.3 Risk Type – Possible Risk
| Risk | Probabilities | Effects |
| Application components which should be reused contain defects limit their functionality | Moderate | Serious |
| Change of requirements which require proposal of major design rework | High
Moderate |
Serious
Serious |
| Scheduling slippage:
The time required for the development of app. is underestimated, so schedule slippage will occur |
High | Serious |
| The size of application is underestimated | High | Tolerable |
| Power Failure | High | Tolerable |
| Inexperienced team member | Medium | Tolerable |
2.2.3 Risk Planning
- A risk plan is a list of all risks that threaten the project, along with a plan to mitigate some or all of those risks. Some people say that uncertainty is the enemy of planning. If there were no uncertainty, then every project plan would be accurate and every project would go off without a hitch. Unfortunately, real life intervenes, usually at the most inconvenient times. The risk plan is an insurance policy against uncertainty.
- Into higher the mitigation response is the action plan to eliminate, reduce, or minimize the probability of a risk event occurring and or the impact of the project risk event should it occur. The output from the activity is a Risk Mitigation Plan that contains a set of actions directed at minimizing the potential occurrence or impacts of risks on a project and a Risk Contingency Plan to be activated. For low impact, low probability risks, a mitigation plan may not be prepared, rather these risk items will be monitored to ensure that they do not transpire or evolve risks.
| Table 2.4 Risk Planning |
| Risk | Plan |
| Requirement
Changes |
Derive traceability information to access requirements,
Change impact and maximize information hiding. |
| Schedule risk | To reduce this risk, we are going to complete our project according to our schedule. |
| Performance | Investigate Database which can effectively process. |
CHAPTER 3: SYSTEM REQUIREMENT
System requirements study involves a clear and thorough understanding of the product to be developed with the view of removing all ambiguities from customer perception.
3.1 User Characteristics
Customers or Users can use our application for searching different service provider as
per their requirement and can also see their contact information, reviews, and conclude whether it fulfill User’s requirement or not.
Admin can manage application and database and also account of all the processes done in the system.
3.2 Hardware and Software Requirements
Table 3.1 Hardware requirements
| Requirements | Description |
| Processors | Intel 3rd gen I3 or higher |
| RAM | 4GB or higher |
| Monitor | 800×600 or larger |
| Hard disk | 40 GB or Above |
Table 3.2 Software requirements:
| Requirements | Description |
| Platform | Windows 7+ / Linux / Mac OS 10+ |
| Software Development Kit | Android SDK & JDK |
| Tool | Android Studio |
| Device | Android KitKat or higher |
- Constraint
- Hardware constraints:
We have used Android Studio to build the application and for that Minimum 2gb MB RAM is required with 800MB of Hard Disk Space with minimum 1 GHz processor. This is one-time hardware requirement
- Reliability
This application must be reliable means it should not be crashed during the execution. We have cared properly no to crash the software. We have used unlimited bandwidth to give high performance in the heavy traffic on the application site.
- Availability
We have considered all the basic requirements of the users before developing the site. So we have provided most of the features to be useful in the application, like submit requirements, updation in requirements, analysis of requirements.
- Security
Security is also a prime requirement of any application. For the security purpose we have used Login authentication before using any feature of the application. We have also encrypted the password of the user in the database to make more secure database.
- Maintainability
The application is online when we want to maintain anything we have to put site offline. The maintainability of site will be little bit hard but we have designed the application in a way that it will be easy to maintain the application.
- Portability
We have used JAVA, PHP as a back end language and XML as front end. For business login, JAVA compiler compiles any of the syntaxes written in JAVA language.
CHAPTER 4: SYSTEM ANALYSIS
4.1 Study of Current Systems
To update any content or any part of app it requires to change the content manually and publish the app to Play Store globally.
4.2 Problems and Weakness of Current System
Right now in the current scenario users can’t see all the detail of service provider going there (at store). Many of them have their personal website but there isn’t any platform that gives all the information at one place.
4.3Requirements of new System
As users can see all the detail of service provide available at his/her location. In addition, they can also able to see photo gallery (new themes in case of decoration) within the application.
4.3.1 Functional Requirement
- Users can create an account.
- After that, users can login into it.
- Users can find all the service provider (stores) available at his/her location.
- Users can filer it by city/area.
- Service provider can update his/her profile.
- User can get direction to Service provider.
- User also can make a call just in one tap.
4.3.2 Non-Functional Requirements
- Should work efficiently even on slow internet connections.
- Dynamic contents like success story are expected.
- Secure Database.
- Communication between users and service provider.
- Provides customer support and feedback or reviews facility.
- Customer satisfaction.
4.4 Feasibility Study
A feasibility study is a preliminary study undertaken to determine and document a project’s viability. The results of this study are used to make a decision whether to proceed with the project, or table it. If it indeed leads to a project being approved, it will – before the real work of the proposed Project starts – be used to ascertain the likelihood of the project’s success. It is an analysis of possible alternative solutions to a problem and a recommendation on the best alternative.
Four types of project feasibility have been considered:
- Technical Feasibility
- Economic Feasibility
- Operational Feasibility
4.4.1. Technical Feasibility:
The following factors suffice for considering the given project as Technically Feasible.
- The system developed in Android technology which is well known and today we can easily get the technical help of Android technology from the internet.
- The system developed in Android technology is specified by the client.
- We have used this technology and similar types of tools that can be useful to develop this system.
- The project is required to be implemented using Android Studio & SDK which are readily available for the development environment.
4.4.2. Economic Feasibility:
Economic feasibility is very important in development of the software for any company. Because it gives an idea, whether the project going to be developed can be completed at a cost affordable both by the client and developer. The availability of the required hardware and software used to develop our project makes it economically very feasible. Also the company is having all the other required resources needed for the project hence the project is feasible with respect to economy.
4.4.3 Operational Feasibility:
Proposed System is beneficial only if they are turned into Information Systems that will meet the organization’s operating requirements. This test of feasibility asks if the system will work when it is developed and deployed. Are there any major barriers to implementation? The following factors suffice for considering the given project as operational Feasible.
As the System is going to be developed at the place where it is going to be implemented, the track of the operations related to the software is constantly monitored by them and sufficient support is available.
CHAPTER 5: SYSTEM DESIGN
5.1 Function of System
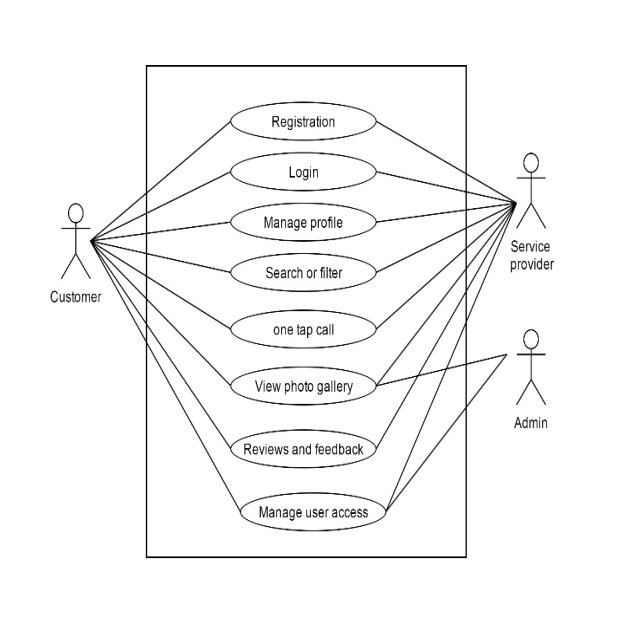
5.1.1 Use Case
Figure 5.1: Use Case diagram
5.1.2 Data Flow Diagrams
5.1.2.1 Context Level
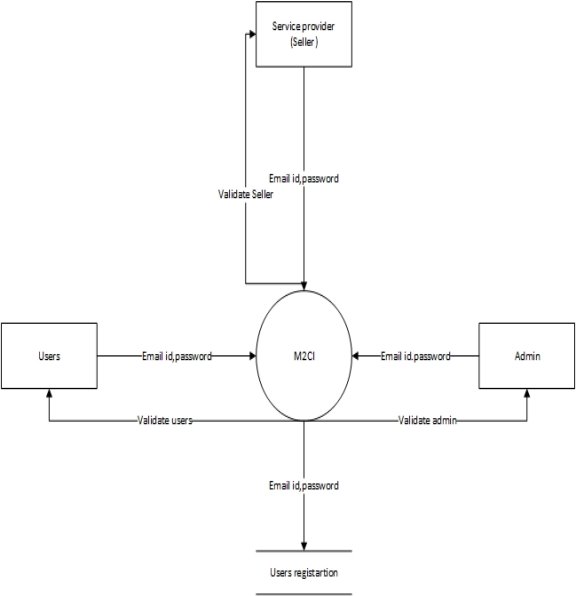
Figure 5.2: DFD-Context Level
5.1.2.2 First Level: User
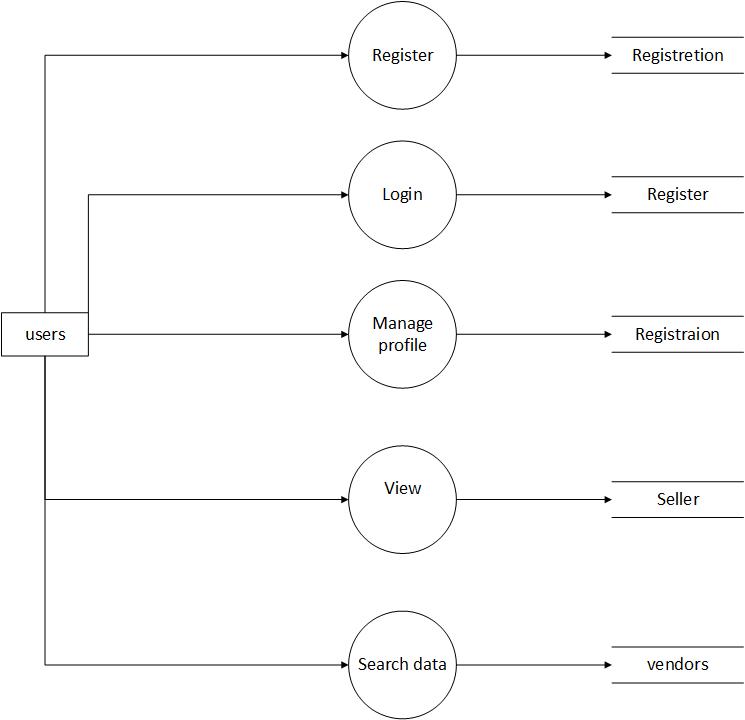
Figure 5.3: DFD-First Level: User
5.1.2.3 First Level: Admin
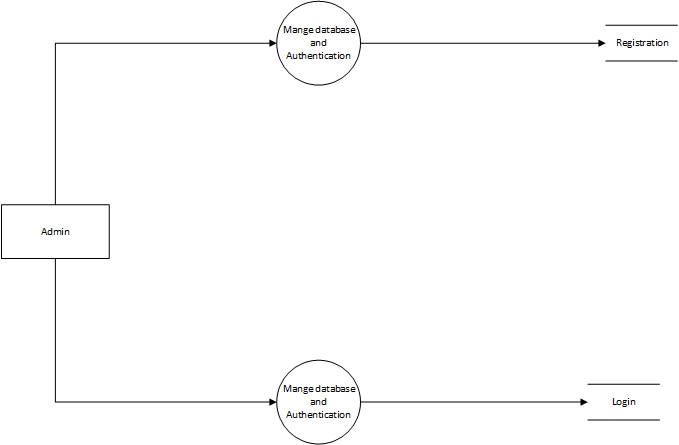
Figure 5.4: DFD-First Level: Admin
5.1.3 Class Diagram:
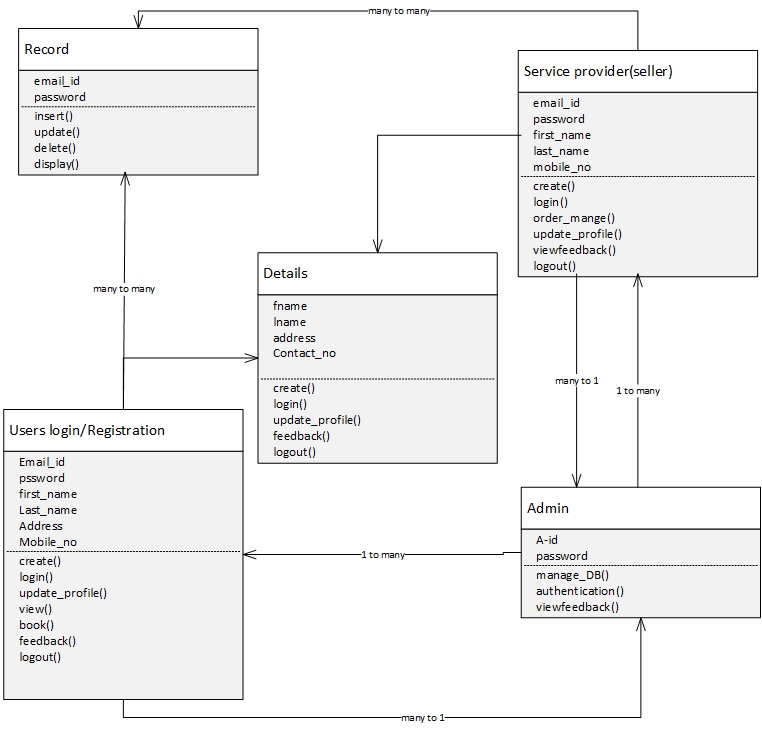
Figure 5.5: Class diagram
5.1.3 Activity Diagram
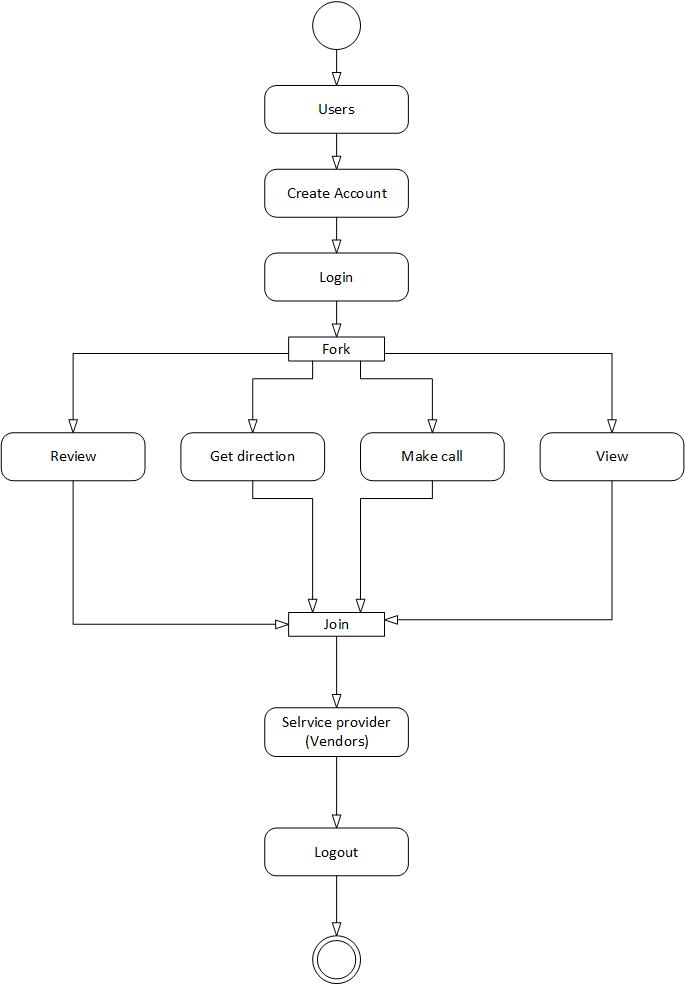
Figure 5.6: Activity diagram
5.2 Data Modelling
5.2.1 ER Diagram
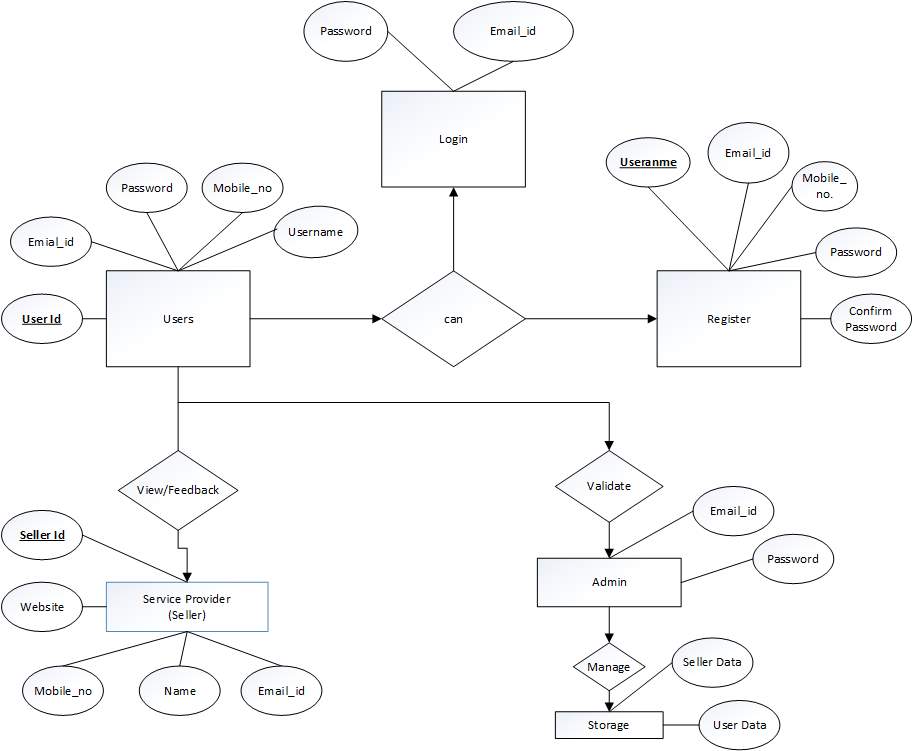
Figure 5.7: ER Diagram
5.3 Database Design
5.3.1 User Registration
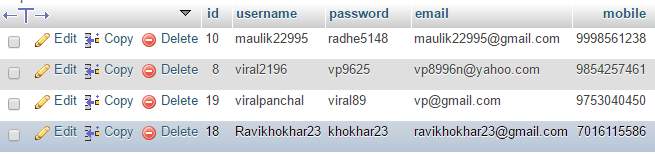
Table 5.1 User Registration
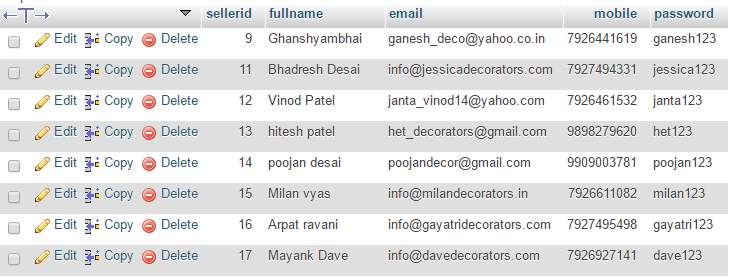
5.3.2 Seller Registration
Table 5.2 Seller Registration
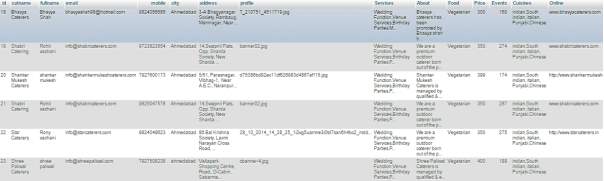
5.3.2 Seller Details
Table 5.3 Seller Details
5.3.2 Seller Gallery
Table 5.4 Seller gallery
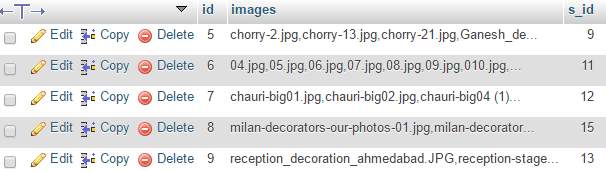
CHAPTER 6: IMPLEMENTATION, PLANNING AND DETAIL
6.1 Implementation Environment
The project is multi-user as it is launched on the internet; all users can access it simultaneously. The project is a result of group consequences. The team structure depends on the management style of the organization, the number of people in the team, their skill levels and the problem difficulty.
6.1.1 Implementation Planning
Implementation phase requires precise planning and monitoring mechanism in order to ensure schedule and completeness. We developed the application in various sub phases in Implementation Phase.
6.1.2 Administration Module Implementation
This subsystem involves administration specific services like voice through search, weather report, latest news, set the alarm, Wikipedia results, feedback, etc.
6.1.3 User Components Implementation
In these phase we have developed user interface components like weather report card view, latest news card view and mic button for searching through voice and also provide feedback page for posting complaint or requesting any new feature.
6.2 Security Features
Security means protecting the data from accidental or intercepting events. The data and programs must be protected from the threats, theft, disk corruption and any other destruction.
In our application user gives feedback through his/her email id and password of Gmail account so the administration or other person can’t get the password of user they only get the email-id of the user’s and in our application we are not providing any login or registration feature so there is no chance to get users information by other person’s.
6.3 Coding Standards
Coding standards keep the code consistent and easy for the entire team to read and re-factor. When the team focuses move from “me” to “we”, coding standards becomes a natural outcome. Code must be formatted to agree coding standards. A coding standard should serve two primary purposes. It should preclude those practices that are likely to cause bugs and prescribe those that avoid them. Habit of using coding standards is a sign of good programmer.
Naming Convention
Use of full word descriptors that accurately describe the variable, functions, id and class names. Keeping underscore between two words in file names. and naming the class files as e.g.: Homepage, MyLocation, Decoration_main etc.
Function Naming
Function and methods naming are applied as per their function. Ex: onResponse(), accessLocation(), getItem().
Variable Naming
The name or Id of any input variable starts with a lower case letter and if there comes another word, it should have the first letter as capital. The name will have a value attached “name” with it and the Id will have along an “id” with it. Ex: userName, emailId, password.
Indentation
If else structure, For Next, While and, Do while constructs have been properly intended.
General Code Clean
- Remove unused and disposable code.
- Remove unused variables.
6.4 Input and Output Designs / Screen shots of Designing Pages
USER REGISTERATION & LOGIN
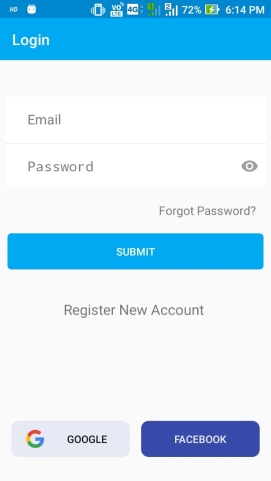
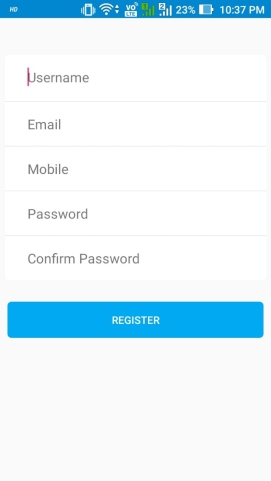
Figure 6.1: Register And login
NAVIGATION DRAWER & SEARCH
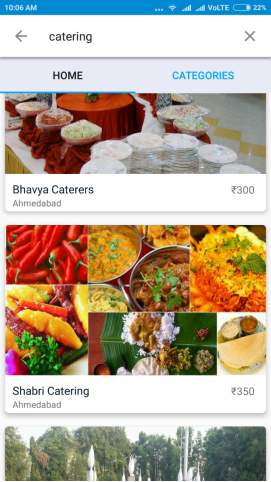
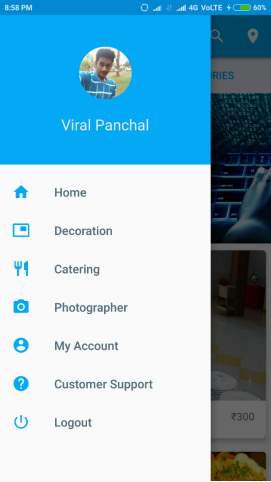
Figure 6.2: Navigation Drawer and Search
HOMEPAGE
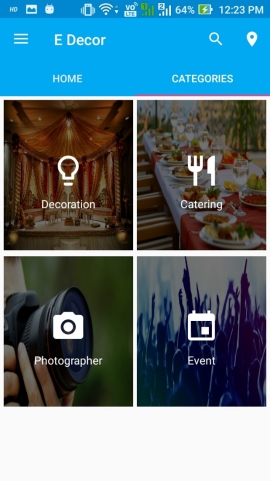
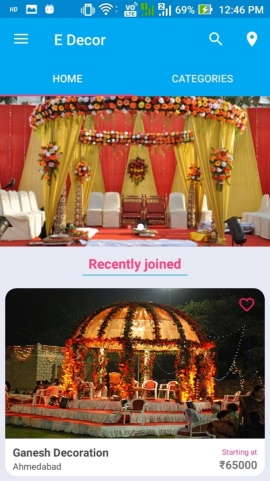
Figure 6.3: Homepage

DECORATION AND CATERING
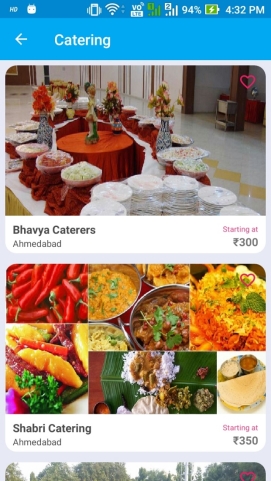
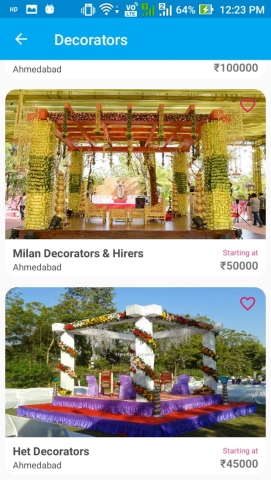
Figure 6.4: Decoration and Catering
DETAILS AND PHOTOS

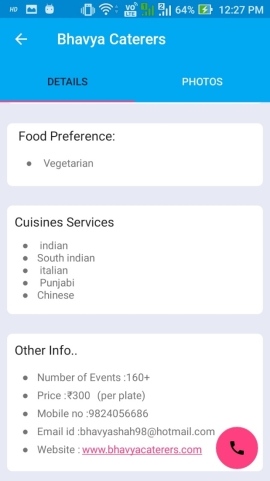
Figure 6.5: Details and Photos
GET DIRECTION & FEEDBACK
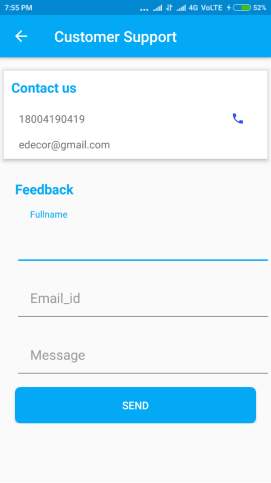
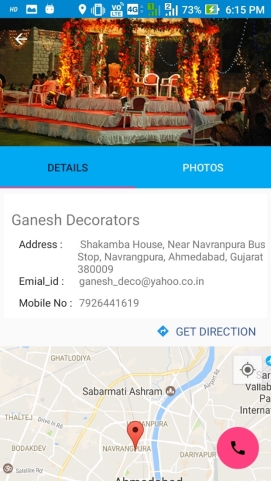
Figure 6.6: Get direction & Feedback
CHAPTER 7: TESTING
Testing is a process of executing a program with the intent of finding an error. If testing is conducted successfully, it will uncover the error in the software.
Secondly, testing demonstrates that software functions appear to be working according to specification and that performance requirements appear to have been met. In additional, data collected as testing is conducted provides a good indication of software reliability and some indication of software quality as whole.
But there is one thing that testing cannot do: Testing cannot show the absence of defects, it can only show that software errors are present.
There are several objectives which are as follows:
Testing Principle
Following are the testing principle which are used:
- All tests should be traceble to customer requirement.
- Tests should be planned long before testing begins.
- Testing should be in small and progress toward testing in the large.
- Exhaustive testing is not possible.
- To be most effective, testing should be conduct by independent third party.
7.1 Testing Plan
The aim of the testing process is to identify all defects existing in software product. However for most practical systems, even after satisfactorily carrying out the testing phase, it is not possible to guarantee that the software is error free. This is because of the fact that the input data domain of most software products is very large. It is not practical to test the software exhaustively with respect to each value that the input data may assume. Even with this practical limitation of the testing process, the importance of testing should not be underestimated. It must be remembered that testing does expose many defects existing in a Software product. Thus testing provides a practical way of reducing defects in a system and increasing the users confidence in a developed system.
Functional Testing
The testing technique that is going to be used in the project is black box testing. In black box testing the expected inputs to the system are applied and only the outputs are checked.
The working or the other parameters of the functionality are not reviewed or tested on the black box testing technique. There is a specific set of inputs for each and every module which is applied and for each set of inputs the result or the output is verified and if found as per the system working this testing is termed or result is declared as pass.
If the set of inputs that are provided to each module are not giving the outputs as per the expected results from the module then the result of that testing is to be declare failed.
In the black-box testing approach, test cases are designed using only the functional specification of the software, i.e. without any knowledge of the internal structure of the software. For this reason, black-box testing is known as functional testing.
Equivalence Class Partitioning
In this approach, the domain of input values to a program is partitioned into a set of equivalence classes. This partitioning is done such that the behavior of the program is similar for every input data belonging to the same equivalence class. The main idea behind defining the equivalence classes is that testing the code with any one value belonging to an equivalence class is as good as testing the software with any other value belonging to that equivalence class. Equivalence classes for software can be designed by examining the input data and output data.
Boundary Value Analysis
A type of programming error frequently occurs at the boundaries of different equivalence classes of inputs. The reason behind such errors might purely be due to psychological factors. Programmers often fail to see the special processing required by the input values that lie at the boundary of the different equivalence classes. For example, programmers may improperly use < instead of <=, or conversely <= for <. Boundary value analysis leads to selection of test cases at the boundaries of the different equivalence classes.
Structural Testing
In the white-box testing approach, designing test cases requires thorough knowledge about the internal structure of software, and therefore the white-box testing is called structural testing.
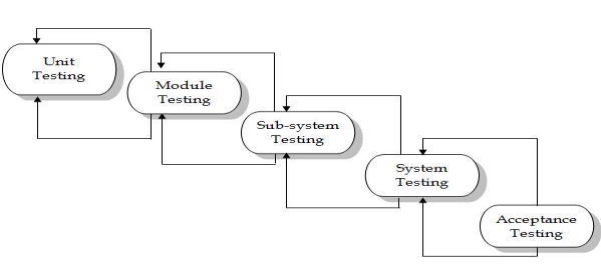
Figure 7.1: Testing Process
7.2 Testing Strategy
The black box testing is going to be used for the project. The entire module is going to be checked for the specific inputs and the output is going to be checked. We are going to test the modules individually and thereafter if found to be working as per the expectations they are going to be integrated with other successfully tested modules and then on integrated.
At last all the modules are integrated and thereafter it is checked on a broader basis and all the requirements which are specified are checked for each integrated system modules. If all the functionalities are successfully satisfied than the entire integrated system is found to be working perfectly alright.
The integration is going to be in a bottom up manner where in each individual modules are going to be checked for the first time initially. Later on as and when other modules are developed and are in a working condition than they are integrated and the entire system is going to be generated.
7.3 Testing Methods
Involve execution and implementation of the software with test data and examining the outputs of the software and its operational behavior to check that it is performing as required.
7.3.1 Statistical Testing
Used to test the program’s performance and reliability and to check how it works under operational conditions. Tests are designed to reflect the actual user inputs and their frequency. The stages involved in the static analysis are follows.
- Control Flow Analysis
- Unreachable code
- Unconditional branches into loops
- Data Use Analysis
- Variable used before initialization
- Variables declared but never used
- Variables assigned twice but never used between assignment
- Possible array bound violations
- Declared variables
- Interface Analysis
- Parameter type mismatches
- Parameter number mismatches
- Non-usage of the results of functions
- Uncalled functions and procedures
- Storage Management Faults
- Unassigned pointers
- Pointer arithmetic
7.3.2 Defect Testing
Intended to find inconsistencies between a program and its specification. These inconsistencies are usually due to program faults or defects.
We have tested our functions of component to check the specification of our components. We selected input set to test the components like in query process we gave the different kinds of inputs to examine their output.
We test software with sequences that have only a single value. We used different sequences of different sizes in different tests. Derived tests so that the first, middle and last elements of the sequence and accessed to reveal the problems at partition boundaries.
| Sr. No. | Type of Testing | Responsibility | Remarks |
| 1 | Unit Testing | Independent code
(working in any circumstances) |
Checking whether the code is flexible for further changes to be made. It affect any other module to any extent or not. Perform alpha testing to reduce bugs. N-Unit tool used. |
| 2 | Integration | Testing done to check Interdependencies of units. No gaps in data flow | To ensure that running the current test affects the previous code to achieve each test case. All fixes are achieved. |
| 3 | System | System as a whole working on any environment. | |
| 4 | Acceptance | System should operate in the expected manner. End user maps his initial requirements with the system. | To ensure no gaps. To achieve the overall functionality. |
CHAPTER 8: LIMITATION AND FUTURE ENHANCEMENT
8.1 Limitation
As our application is completely on server side so, user must have to require a strong and reliable internet connection And the other limitation is that, Right now decorators,catereing provider, and photographers are included as vendors in our application and it also provide services for some specific area or city.
8.2 Future work
We want to add more categories like invitation card printing service provide,DJ service provider etc.We also want to add booking facility in our application and also want to include more area and city to cover a more vedor in our app.
8.3 Conclusion
Our application provides reliable and easy approach between vendors and customers.
Customers or Users can use our application for searching different service provider as per their requirement and can also see their information, reviews and conclude whether it fulfill User’s requirement or not.
References
3. https://www.urbanclap.com/ahmedabad-wedding-caterers
4. http://www.justdial.com/Ahmedabad/Wedding-Decorators/ct-104719
5. http://stackoverflow.com/questions/tagged/android
6. https://developer.android.com/design/
7. https://www.simplifiedcoding.net/android-login-and-registration-with-php- mysql/
8. http://www.androidhive.info/2016/01/android-working-with-recycler-view/
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Design"
Design is utilised in a broad range of industries and could include any number of different subjects from architecture and interior design, to products, packaging, logos, vehicles or anything in between.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




