Security Procedures for a Small Computer Network
Info: 39211 words (157 pages) Dissertation
Published: 1st Oct 2021
Tagged: Cyber Security
Table of Contents
2.1. Implementing the planned solution
Prototype built in Packet Tracer
c. Hardening the Wireless Router
The prototype build on VMware for server configurations
a. Setup the Prototype computers
b. Deploying Basic Settings by Using Group Policy
d. Setup Windows Server Backup
2.2. A Security Report for Mr Williamson
A.1. – Network Device Security
A.2. – Network Administration Principles
A.3. – Network Design Elements and Components
A.4. – Common Protocols and Services
A.5. – Troubleshooting Wireless Security
Section B – Compliance and Operational Security
B.2. – Integrating Systems and Data with Third Parties
B.3. – Risk Mitigation Strategies
B.4. – Basic Forensic Procedures
B.5. – Incident Response Procedures
B.6. – Security-Related Awareness and Training
B.7. – Physical Security and Environmental Controls
B.8. – Risk Management Best Practices
Section C – Threats and Vulnerabilities
C.3. – Social Engineering Attacks
C.5. – Application Attack Types
C.6. – Mitigation and Deterrent Techniques
C.7. – Discovering Security Threats and Vulnerabilities
Section D – Application, Data, and Host Security
Section E – Access Control and Identity Management
2. Development Stage
Introduction
In this stage of the project will be provided evidence of implementing the planned solution to the task and tracking the implementation. This will involve the implementation of the plan created in first stage (Planning Stage), reviewing or adjusting the plan if is necessary.
The purpose of the project is to design security procedures for a small computer network, supporting at least 10 users divided into three groups with significantly different requirements and two different geographical locations.
A prototype will be created to be presented, using appropriate techniques such as software, logbooks, work diaries, reports, etc. As a software, will be used, as follow:
- Packet Tracer – to design the network and to configure CISCO elements
- VMware – where to install the Windows Server 2008 R2 and to be able to show the Microsoft Server configuration, using Active Directory to manage: Group Polices, Organizational Units, Users, Groups, etc.
- Microsoft Project 2010 – to create a Gantt Chart. (the Gantt Chart was created on Planning Stage and now, in this stage must follow the task or to adjust it, in accordance with the reality)
The prototype design and configuration will be explained on details, justifying the solutions chosen, using: logbooks, screen shoots, etc.
Apart from this, will be produced a fully detailed report, where to be explained why is necessary to apply the solution chosen. This report will cover the following areas:
- Network security
- Compliance and operational security
- Threats and vulnerabilities
- Application, data and host security
- Access control and identity management
After that, the next step on the project will be focused on testing the implemented solution. Will be tested almost everything, starting with the connectivity between PCs (ping) and finishing with the security settings. Because the prototype environment in is limited, the report cannot provide tests for all the components of the network, e.g. VPN.
At the last, but not the least, the Gantt chart will be adjusted in accordance with the changes occurred in Development Stage.
2.1. Implementing the planned solution
The solution and all the recommendations given on Planning Sage will be tested and applied on the current stage of the project, by building a Prototype. If will be demonstrate that the security solution chosen can work in Prototype, then it will be applied for Magic Memories network. The prototype will be created under laboratory conditions and will not be able to meet all the conditions of a real network, but will make every effort to be as accurate as possible.
To create a Prototype very similar with the real-life environment, should use some specific hardware and software solutions. As a hardware solution, will be used an PC and a Laptop; and as software solution will be used: Packet Tracer from Cisco, VMware – virtual machine, Microsoft Server 2008 R2 and Windows 7.
In fact, the prototype will consist of two parts:
- The first part will be built in Packet Tracer and will represent the entire network, with all the functionalities and security functions presented in detail.
- The second part will focus on setting functionality and implementing security in the client server. For this operation, the following software will be used: VMware, Windows Server 2008 R2, Windows 7 Professional. Everything will be set up into a laptop.
Prototype built in Packet Tracer
Design a new network | Functionality of the new network | Router Hardening | Switch Hardening | Secure Wireless Component | Printers Hardening
Cisco offer a powerful network simulation program named Packet Tracer. Using this program, can create a very accurate Prototype, which will meet most of the requirements to demonstrate that the chosen solution from Planning Stage has applicability for a real network.
Unfortunately, not all network components can be represented with this program. (e.g. VPN). Also, some aspects of network functionality are predefined and cannot be changed. Limits are also in the process of implementing some security settings, but these issues will be explained at an appropriate time during this report.
During the creation and presentation of this prototype, aspects of security, functionality, and network components that cannot be represented by Packet Tracer, will be explained in detail in order to be deployed in Magic Memories’ real network.
Building a prototype offers a series of advantages:
- It enables to test and refine the functionality of the network.
- It makes it possible to test the performance of the security applied.
- It’ll help to describe the final product more effectively.
- It will help the client – Mr. Williamson – to understand the importance of network security.
The first step in the process of creating an operational prototype that comply with all the security requirements required by the client is to redesign the entire network. This is necessary because the way it is configured the actual network creates premises for a high vulnerability. The concept of designing an ad-hoc network is not recommended for reasons of security and functionality. The current network uses a private IP address: 192.168.1.0/24
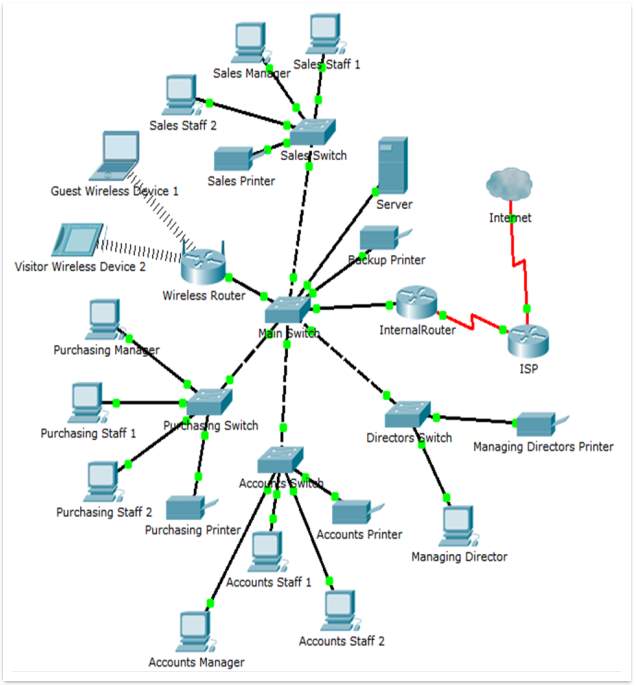
Figure 1 – The actual network
The solution chosen for the new network design is shown in the figure below.
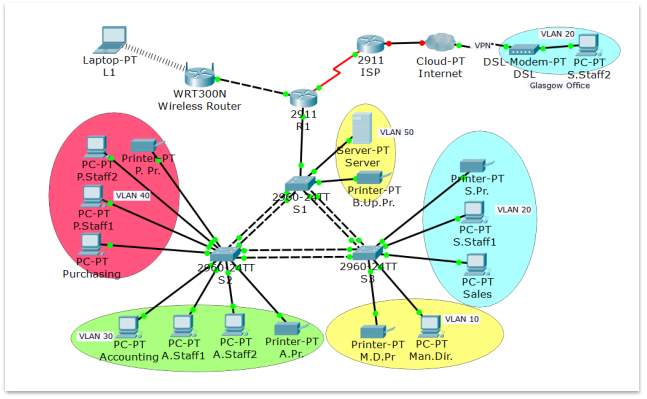
Figure 2 – The Prototype
As can be seen in the above-mentioned figure, in the new network design, for security reasons and better functionality, the original network has been divided into several parts, thus creating several subnets. The method used to divide the network was VLSM. Some of these subnets are VLANs and other are non-VLANs. In fact, each department has an assigned VLAN containing all devices belonging to that department.
The non-VLANs segments are: the wireless component of the network and the links between the Internal Router with the Wireless Router and ISP.
The initial IP address 192.168.1.0/24 will be divided into subnets using VLMS.
In the following table, named Table 1, it’s represented all subnets created.
Table 1 – The subnets
| Name of network | Subnet Mask | Network | 1ST Host | Last Host | Broadcast |
| VLAN 10
Man. Director |
255.255.255.240 | 192.168.1.0 | 192.168.1.1 | 192.168.1.14 | 192.168.1.15 |
| VLAN 20
Sales |
255.255.255.240 | 192.168.1.16 | 192.168.1.17 | 192.168.1.30 | 192.168.1.31 |
| VLAN 30
Accounting |
255.255.255.240 | 192.168.1.32 | 192.168.1.33 | 192.168.1.46 | 192.168.1.47 |
| VLAN 40
Purchasing |
255.255.255.240 | 192.168.1.48 | 192.168.1.49 | 192.168.1.62 | 192.168.1.63 |
| VLAN 50
Utilities |
255.255.255.240 | 192.168.1.64 | 192.168.1.65 | 192.168.1.78 | 192.168.1.79 |
| VLAN 60
Management |
255.255.255.240 | 192.168.1.80 | 192.168.1.81 | 192.168.1.94 | 192.168.1.95 |
| Wireless | 255.255.255.240 | 192.168.1.96 | 192.168.1.97 | 192.168.1.110 | 192.168.1.111 |
| Router – Wireless | 255.255.255.252 | 192.168.1.112 | 192.168.1.113 | 192.168.1.114 | 192.168.1.115 |
| Router – ISP | 255.255.255.252 | 192.168.1.116 | 192.168.1.117 | 192.168.1.118 | 192.168.1.119 |
Therefore, all wired devices – such as PCs, printers and server – will be grouped by one side of the Internal Router. This solution was chosen to separate the core part of the network from the wireless network components.
This solution was chosen to separate the main part of the network to the wireless component. The wireless components of a network are the most vulnerable parts of any computer network, that’s why it’s necessary to anticipate the potential security risk and to take additional precautionary measures related to this.
In this case the “Ethernet Network” and the “Wireless Network” will be separated by the Internal Router, where security measures will be implemented, such as: firewall/ACLs, passwords, routing restriction, port security, etc. All these security measures will act as a barrier between these two parts of the network.
At the same time, by applying a traffic filtering strategy, limiting in this way the range of possible external attacks, the Internal Router will act as a border between the company’s network and the Internet.
The “Ethernet Network” will be divided into several VLANs, based on departments. An extra VLAN will be configured for managerial functions, allowing for remote access in switches.
The reason why a VLAN strategy was used is because in this way the departments can be kept separate from each other and users from a department will not be able to access the computers in other departments. Communication between departments will only be possible through the Internal Router, where each VLAN will have a sub-interface configured. This method is called Inter-VLAN Routing. Because communication between VLANs is done only through the Internal Router, should be configurated security measures to restrict traffic between departments by implementing ACLs with different rules to meet the company’s needs. Using the VLAN strategy to divide the network creates a few benefits, such as: decrease the size of broadcast domains, segment traffic, no waste of IP addresses, etc.
Special attention should be paid to Glasgow’s office because it is geographically separate from the rest of the company, but must be in the same network as the rest of the users, being part of the Sales Department. For this reason, this office must be part of the same VLAN as its colleagues in Edinburgh, to be able to benefit from the same facilities and to gain same level of access to the server. At the same time, the Glasgow’s office must be accessible and should be able to be checked by the manager in the same way as the office in Edinburgh is checked. To make all these features to be possible, the connection between these two offices of the company will be achieved by using of VPN technology. The same technology will also be used for remote managers’ access to the network. Unfortunately, this connection cannot be configured and presented in Packet Tracer because this program does not have this feature. The benefits and security measures that VPN technology involves, will be explained in detail in the Security Report addressed to Mr. Williamson, presented later in this project.
All devices in the “Ethernet Network” will have a static IP address assigned. The main reason why this strategy was chosen instead of DHCP is the size of the network, which does not require a dynamic allocation of IP addresses, being easy to manually allocate them. Another reason why static IP addresses have been preferred is that this ensures a better network security. DHCP technology is very useful for large networks, as it reduces the time spent on setting IP addresses for each device. But at the same time, this technology can leave open access gates within the network. Using DHCP involve a less control of who gain access to the network resources. Even with a switch port security, a good hacker can gain access to the network by placing a bridge between an authorized device and its network port (a laptop with 2 NICs). However, much more about DHCP and static IP addresses into the Security Report.
The “Ethernet network” will be divided into six VLANs, each of these has allocated 14 available IP addresses. For the current needs of the company, a number of 3 to 5 IP addresses will be used in each VLAN. The rest of IPs, up to 14, will be available for scalability. The name of every VLAN and the IP addresses allocated are in detail explained in Table no 1.
The “Wireless Network” will be a separate, non-VLAN subnet with the IP address 192.168.1.96/28. Because this part of the network is strictly dedicated to mobile devices that belong to employees and visitors, it is necessary to use DHCP. For the beginning, the “Wireless Network” have 14 available IP addresses. One of these will be used for the default gateway, and the remaining 13 will be dynamically assigned to the users. The IP address of this subnet is 192.168.1.96/28. Special security measures will be configured in the Wireless Router to limit as much as possible the vulnerability of the wireless component. Later in this rapport, will be explained on details all these security settings.
The “Ethernet Network” area with all the VLANs and the “Wireless Network” will be the main parts of the Magic Memories network. The links between the Internal Router and the Wireless Router and the Internal Router and ISP will be part of two other subnets as follows: the first link will have the IP address 192.168.1.112/30 and the second one 192.168.1.116/30. A Loopback address will be configured in the Internal router; as follows: 192.168.1.121/30. Also, in the ISP router, a Loopback address will be configured to simulate Internet access; as follows: 209.100.100.100.
The devices used to configure the Prototype for the new network of Magic Memories are such follow:
- 2 Routers (the second is ISP)
- 1 Wireless Router
- 3 Switches
- 10 PCs
- 5 Printers
- 1 Server
- 1 Wireless device (Laptop)
Table 2 – IP Addressing table
| Device | Interface | IP Address | Subnet Mask | Def. Gate. |
Internal Router |
Serial 0/0/0 (DCE) | 192.168.1.117 | 255.255.255.252 | N/A |
| GigabitEthernet 0/1 | 192.168.1.113 | 255.255.255.252 | N/A | |
| GigabitEthernet 0/0 | N/A | N/A | N/A | |
| GigabitEthernet 0/0.10 | 192.168.1.14 | 255.255.255.240 | N/A | |
| GigabitEthernet 0/0.20 | 192.168.1.30 | 255.255.255.240 | N/A | |
| GigabitEthernet 0/0.30 | 192.168.1.46 | 255.255.255.240 | N/A | |
| GigabitEthernet 0/0.40 | 192.168.162 | 255.255.255.240 | N/A | |
| GigabitEthernet 0/0.50 | 192.168.1.78 | 255.255.255.240 | N/A | |
| GigabitEthernet 0/0.60 | 192.168.1.94 | 255.255.255.240 | N/A | |
| Loopback1 | 192.168.1.121 | 255.255.255.252 | N/A | |
| VLAN 10 | ||||
| PC Man. Director | NIC | 192.168.1.1 | 255.255.255.240 | 192.168.1.14 |
| Printer Man. Dir. | NIC | 192.168.1.2 | 255.255.255.240 | 192.168.1.14 |
| VLAN 20 | ||||
| PC Sales Man. | NIC | 192.168.1.17 | 255.255.255.240 | 192.168.1.30 |
| PC Sales Staff 1 | NIC | 192.168.1.18 | 255.255.255.240 | 192.168.1.30 |
| PC Sales Staff 2 Glasgow | NIC | 192.168.1.19 | 255.255.255.240 | 192.168.1.30 |
| Printer Sales | NIC | 192.168.1.20 | 255.255.255.240 | 192.168.1.30 |
| VLAN 30 | ||||
| PC Account. Man. | NIC | 192.168.1.33 | 255.255.255.240 | 192.168.1.46 |
| PC Account. Staff 1 | NIC | 192.168.1.34 | 255.255.255.240 | 192.168.1.46 |
| PC Account. Staff 2 | NIC | 192.168.1.35 | 255.255.255.240 | 192.168.1.46 |
| Printer Accounting | NIC | 192.168.1.36 | 255.255.255.240 | 192.168.1.46 |
| VLAN 40 | ||||
| PC Purchasing Man. | NIC | 192.168.1.49 | 255.255.255.240 | 192.168.1.62 |
| PC Purch. Staff 1 | NIC | 192.168.1.50 | 255.255.255.240 | 192.168.1.62 |
| PC Purch. Staff 2 | NIC | 192.168.1.51 | 255.255.255.240 | 192.168.1.62 |
| Printer Purchasing | NIC | 192.168.1.52 | 255.255.255.240 | 192.168.1.62 |
| VLAN 50 | ||||
| Server | NIC | 192.168.1.65 | 255.255.255.240 | 192.168.1.78 |
| Back up Printer | NIC | 192.168.1.66 | 255.255.255.240 | 192.168.1.78 |
| VLAN 60 | ||||
| S1 Management | 192.168.1.81 | 255.255.255.240 | 192.168.1.94 | |
| S2 Management | 192.168.1.82 | 255.255.255.240 | 192.168.1.94 | |
| S3 Management | 192.168.1.83 | 255.255.255.240 | 192.168.1.94 | |
| Non-VLAN | ||||
| Wireless Router | Internet interface | 192.168.1.114 | 255.255.255.252 | N/A |
| LAN Interface | 192.168.1.97 | 255.255.255.240 | N/A | |
| ISP | Serial 0/0/0 | 192.168.1.118 | 255.255.255.252 | N/A |
As have already said, the traffic between VLANs can’t be forwarded without a Layer 3 device, in this case a Router. For this purpose, the Inter-VLAN routing solution will be used and all traffic between VLANs will go through the Internal Router. The Inter-VLAN concept uses several methods to be applied, but in this case, the Router-On-A-Stick (ROAS) method will be used.
Table 3 – VLANs on Ethernet Network
| VLAN 10 | VLAN 20 | VLAN 30 | VLAN 40 | VLAN 50 | |
| Department | Man. Dir. | Sales | Accounting | Purchasing | Utilities |
| Manager | 192.168.1.1 | 192.168.1.17 | 192168.1.33 | 192.168.1.49 | – |
| Staff 1 | – | 192.168.1.18 | 192.168.1.34 | 192.1681.50 | – |
| Staff 2 | – | 192.168.1.19 | 192.168.1.35 | 192.168.1.51 | – |
| Printer | 192.168.1.2 | 192.168.1.20 | 192.168.1.36 | 192.168.1.52 | – |
| Server | – | – | – | – | 192.168.1.65 |
| Back-up Print. | – | – | – | – | 192.168.1.66 |
| Default GW | 192.168.1.14 | 192.168.1.30 | 192.168.1.46 | 192.168.1.62 | 192.168.1.78 |
On server, can be set up a DNS (Domain Name System). To do that, should follow these steps:
First, should assign an IP address for DNS Server, on server and on PCs as well.
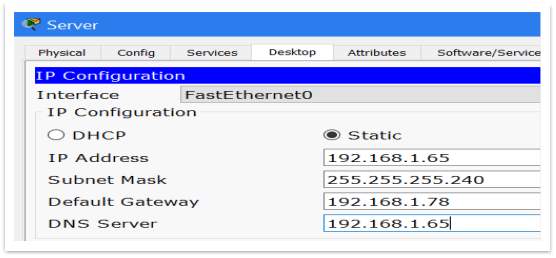
Figure 3 – Add DNS server IP on Server
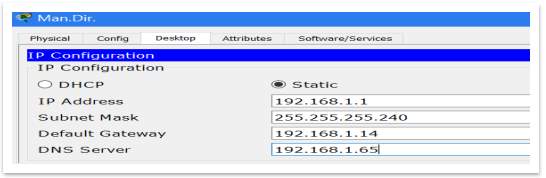
Figure 4 – Add DNS server IP on PC
After that should link this IP address with a chosen name, as www.magicmemories.com. To do that may turn on the DNS Service features, type the domain name and the IP address, then press add button.
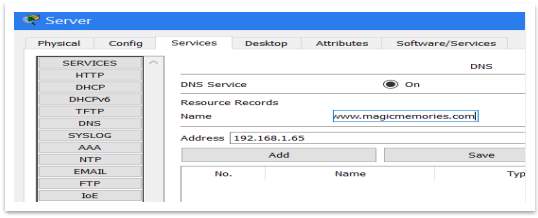
Figure 5 – Link the IP with the DNS name
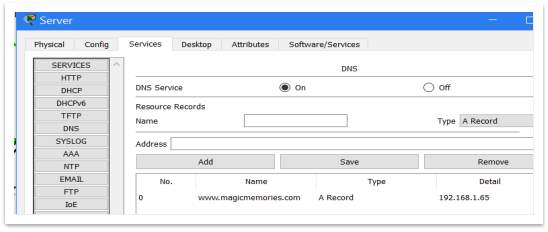
Figure 6 – Add the DNS to database
Last step is to test the DNS. From a PC, on Web Browser facility should type the chosen name.
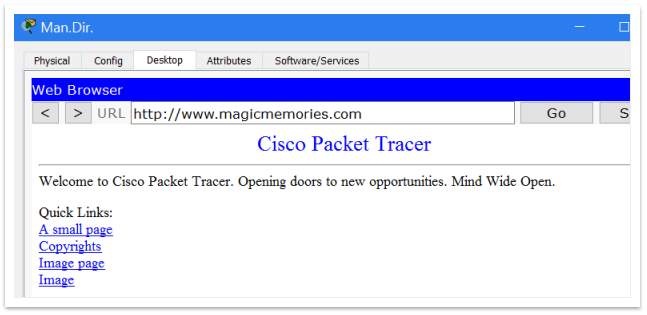
Figure 7 – Test the DNS
Once the new network has been built and its functionality has been tested, it can be traced to the next phase in configuring the Prototype, that is the implementation of security measures.
As a first step, security solutions must be found and applied to make devices difficult/harder to be attacked and compromised by criminals. This process is called Hardening. The devices that need to be hardened, are as following: Routers (including here the Wireless Router), Switches and PCs (including the server). The Hardening process, has several common parts, applicable to both routers and switches, but most of the configuration are specific to each type of device.
a. Router Hardening
As a first step, it should start with the closure of unused ports. To do this, should use the following commands
- Configure terminal
- Interface “name of interface”
- Shutdown
- Exit
- Do copy run start
Figure 8 – Router interfaces after was closed
Banner motd. This is not exactly a security feature but it is considered a “good practice”, because it gives the opportunity to display a warning text (banner) when somebody tries to connect to the router or switch through telnet or console connection.
Figure 9 – The warning text
As a next step in a router’s hardening process, should be limiting access to the device using passwords.
PT does not allow us to set passwords in PCs but allows us to set passwords in routers and switches. The passwords set in these types of devices are for secure access to IOS or for secure access to different IOS modes, such as follows:
- Enable password “password”, limits access to the privileged EXEC mode.
- Enable secret “password”, limits access to the privileged EXEC mode and the password can be encrypted with this command: “service password-encryption”
- Console password, limits device access using the console connection
- VTY password, limits device access over Telnet
The passwords chosen for the Prototype, are:
- Secret password = pass-one
- Console Password = pass-two
- VTY password = pass-two
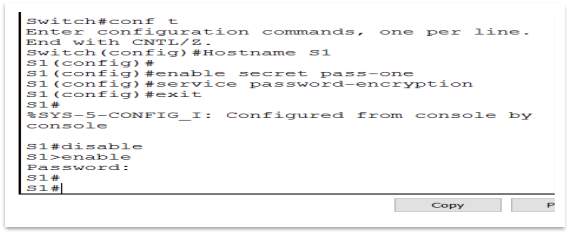
Figure 10 – Enable the password and encryption
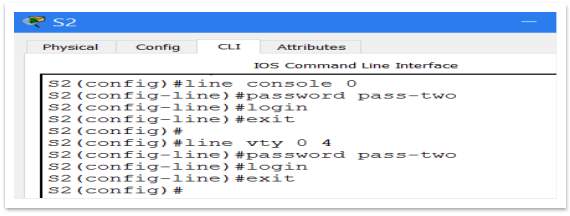
Figure 11 – Console and VTY passwords
VTY (telnet) password using “login” when set-up the passwords, allow us to login with the password required for authentication (pass-two). To be more secure, can use the command “login local” which require creation of a global user account, with a username and password, used for gain access to the router.
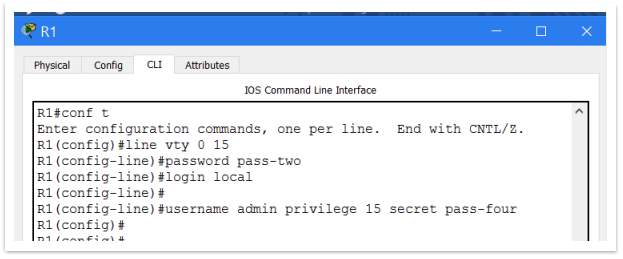
Figure 12 – Login local commands
- Username – ‘admin’,
- password – ‘pass-four’
- privilege – ‘15’ means administrative level rights.
Another useful command is “logging synchronous” which stops the Cisco IOS sending messages to the user as he is working.
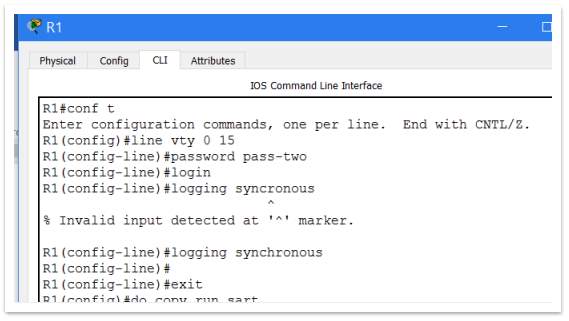
Figure 13 – Logging synchronous
Using SSH
An important step in the process of creating and delivering a secure network is also securing remote access to a device by using SSH instead of Telnet. The only way to secure Telnet is to use for it a Username and Password. Because the Telnet can’t be encrypted, the security issue remains open. Instead, using SSH for remote access, it is more secure, because can be encrypted. To be able to use SSH, this is the configuration used on router:
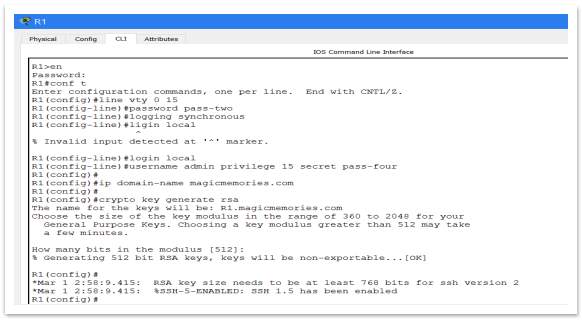
Figure 14 – Setup SSH (1)
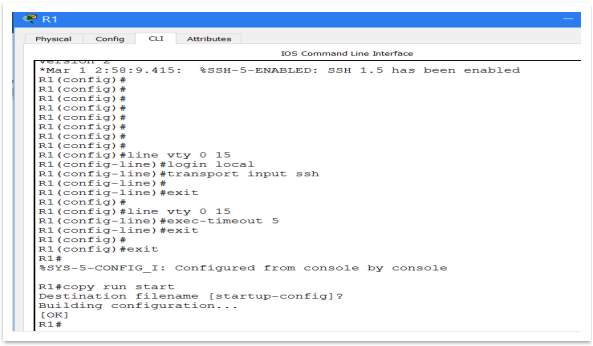
Figure 15 – Setup SSH (2)
A domain name (DNS) it was necessary to be created to run SSH encryption from. For prototype the chosen domain name is: magicmemories.com. After that the encryption can be created. In the prototype, it was used 521-bit encryption key. As can be see it on Figure 10, using the command ‘transport input ssh’, select to use SSH instead of Telnet. As well can establish the time after the router will drop the SSH link. The command ‘exec-timeout 5’ give instruction to router to don’t keep the SSH link if this is idle more than 5 minutes.
To be able to use remote access, should create an IP address on router to telnet via that. For that purpose, will be used a loopback address from Internal Router, named Loopback1 Anyway, the loopback address is very useful, not only for telnet or SSH. The IP address used for loopback interface is: 192.168.1.121/30
“Loopback interfaces are always up, whereas physical interfaces can change state, and the interface can potentially not be accessible. It is recommended to add a loopback interface to each device as a management interface and that it be used exclusively for the management plane. This allows the administrator to apply policies throughout the network for the management plane. Once the loopback interface is configured on a device, it can be used by management plane protocols, such as SSH, SNMP, and syslog, in order to send and receive traffic.” http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html#anc14
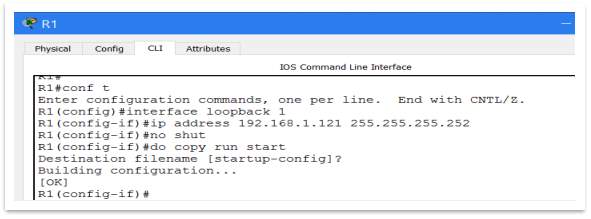
Figure 16 – Loopback address
Another step on the process of hardening the router is the Login Security. Once a user account it is created this user can access the router. That why it is necessary to secure the process of logging in.
In this sense, should configure some security criteria regarding the password.
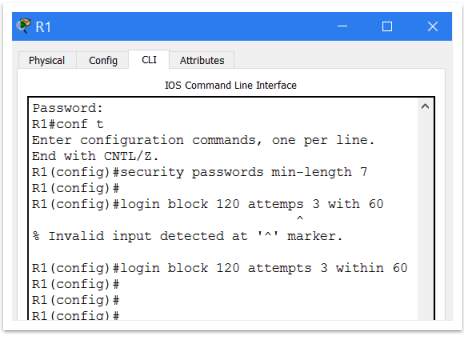
Figure 17 – Login security
That’s means:
- minimum password length should be 7 words
- if the login credentials are entered incorrectly 3 times within a span of 60 seconds, the Router will block all connections for 120 seconds.
Access Control List (ACL) is a way of filtering traffic. In the Prototype, it will be configurated an ACL on router, to make this device to act as a firewall.
This will be created for interface s/0/0/0 which connect the Magic Memories Network to the Internet and will be configurated to allow HTTP web traffic but will block the ping packets.
Because on the lab conditions can’t be recreated the Internet, a new device (server) will connected to the ISP router and in this way, can be simulated a web traffic. The new server will act as a webserver. The new device will not be a part of Magic Memories network. It will be used just to exemplify the settings of ACL on lab conditions. The IP address of the new device is: 10.0.0.2/8
On the Figure 18 showed below, the Webserver is linked with the ISP Router.
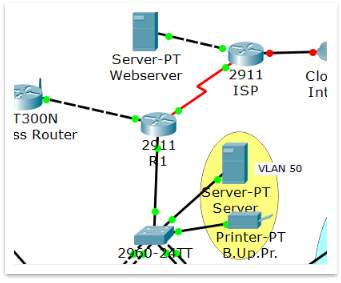
Figure 18 – New device added for ACL reason
Below, on Figure 20, it is the commands used to configure ACL, which will deny pinging in both directions but will allow web traffic. All the host devices are included in this ACL.
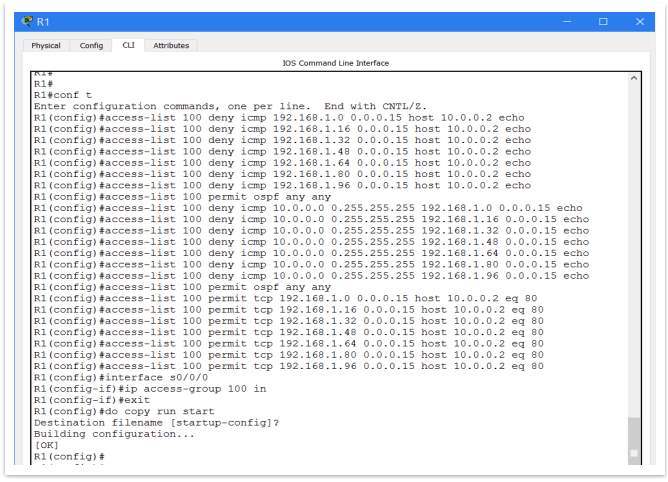
Figure 19 – ACL configuration
This is just a short example of ACL. In fact, many ACLs should be implemented to secure the network. Example of ACLs which should be set up to provide a well secured network: an ACL to restrict the remote access to the devices; an ACL to limit the ports used for SSH/Telnet, an ACL to limit the devices able to do SSH/Telnet, etc.
As a last step in the process of Hardening the Internal Router should be considered to disable some inactive services and protocols. Keeping them active can generate vulnerabilities in the network security system.
Disable unused services. These typically include: TCP and UDP minor services, File Transfer Protocol (FTP), Bootstrap Protocol (BOOTP), Cisco Discovery Protocol (CDP), Trivial File Transfer Protocol (TFTP), Configuration autoloading, Packet assembler/disassembler (PAD), Decnet Maintenance Operation Protocol (DEC MOP).
Disable management protocols. E.g. Simple Network Management Protocol (SNMP), Hypertext Transfer Protocol (HTTP) or Hypertext Transfer Protocol Secure (HTTPS).
Unfortunately, Packet Tracer does not have the function to close these services and protocols, so it is not possible to apply this in Prototype.
An alternative to manually hardening the router is using Cisco’s Security and Device Manager (SDM). This utility has ability to harden the router automatically and is available in the Graphical User Interface (GUI). Not available in Packet Tracer.
b. Switch Hardening
Switches are an important part of the network, so they should be hardened with the same carefulness and attention, just as the routers have been hardened. Part of the processes are similar as was for router, that’s why will not be explained on details. These are as follows:
Setup passwords:
- Enable password “password”, limits access to the privileged EXEC mode.
- Enable secret “password”, limits access to the privileged EXEC mode and the password can be encrypted with this command: “service password-encryption”
- Console password, limits device access using the console connection
- VTY password, limits device access over Telnet
The password chosen for the prototype, are as follows:
- Secret password = pass-one
- Console Password = pass-two
- VTY password = pass-two
Login security:Should be setup password criteria as: minimum length, number of time allowed to enter incorrectly the password and the duration of span, and finally the length of time for the switch will block all connections.
VTY (telnet): more configuration for remote access via telnet. Using “login local” can setup a Username, Password and Privilege Level. This command it is used to create a global user account. Another useful command is “logging synchronous” which stops the Cisco IOS sending messages to the user as he is working.
Banner motd: It is not a security settings, but can give a warning to everybody who try to connect to device.
Closing unused interfaces. For security reasons, it is recommended that all non-used interfaces to be closed. In this way, the area where the switch can be attacked is minimalised. The interfaces are closed manually and the process is quite simple. The commands used are:
- Conf t
- Int “name of interface” (for more interfaces, it is useful to use: “int range …” command)
- Shout down
- Do copy run start
- Exit
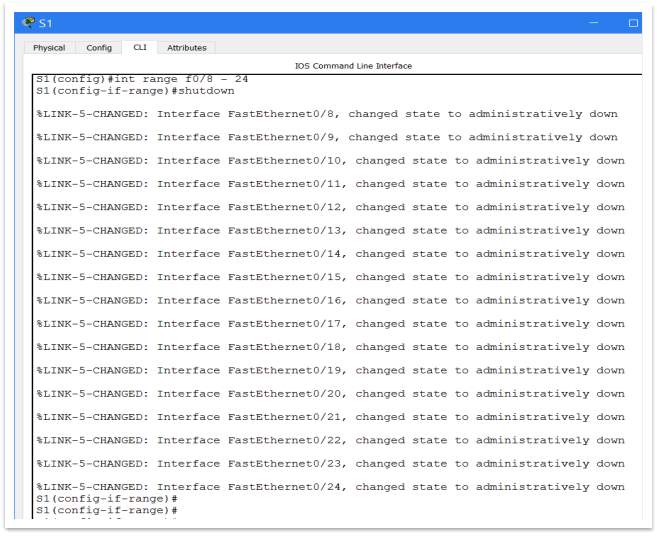
Figure 20 – S1 interfaces are administratively closed
SSH instead of telnet for remote access
To set up a SSH remote access on switch will follow the same process as it was presented above for router. The domain name is the same: magicmemories.com. Because the switch is a Layer 2 device, cannot be setup a loopback address. That’s why will be used instead VLAN 60, setup as a Management VLAN.
After that the encryption can be created. In the prototype, it was used 521-bit encryption key. As can be see it on Figure 16, using the command ‘transport input ssh’, select to use SSH instead of Telnet. As well can establish the time after the router will drop the SSH link. The command ‘exec-timeout 5’ give instruction to router to don’t keep the SSH link if this is idle more than 5 minutes.
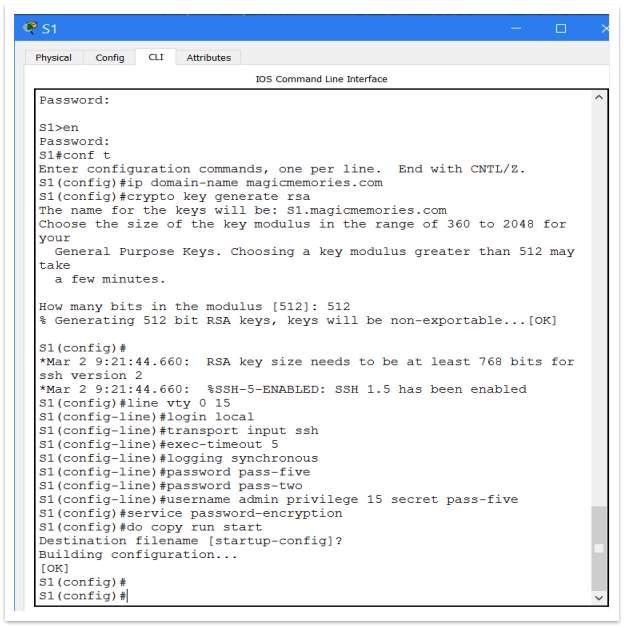
Figure 21 – Setup SSH on switch
The processes outlined above are common to those used to harden the router. In the next phase of this project, will be presented specific hardening processes, specifics only for switches. These are such follow:
Switch-port port security
Port security is probably the most important process in the attempt to make a switch harder accessible for hackers. A set of rules is configured for each port, depending on its parameters, specifications and usage. The process is done manually and can be applied only on active access ports. Not applicable for trunk ports.
The rules that can be setup, are such following:
- Secure MAC address, where can be setup a sticky MAC address or a specific MAC address. For prototype the chosen option is to assign a specific MAC address for every port.
- Maximum security address, represent the number of MAC addresses that can connects that port. For prototype the chosen option is 1.
- Security violation mode, setup what’s happened if an unauthorised access to the port is detected. Cisco IOS give us three options: protect, restrict and shutdown. For prototype the chosen option is “Restrict”.
The line of command used to setup the switch port security are as follows:
Switch(config-if)# switchport mode access
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security maximum “1”
Switch(config-if)# switchport port-security violation restrict
Switch(config-if)# switchport port-security mac-address “000D.BD4C.E78D”
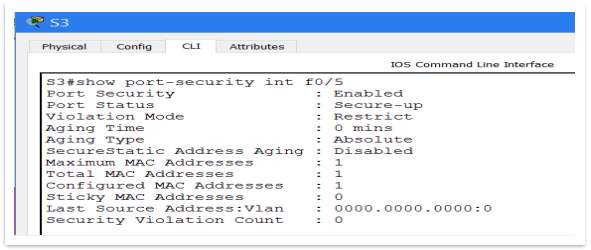
Figure 22 – Port Security Interface
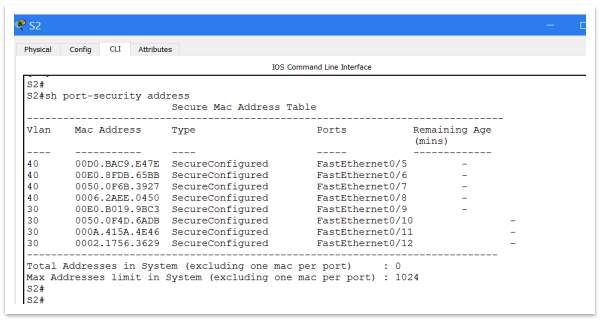
Figure 23 – Secure Mac Address Table
Spanning Tree Protocol (STP). It is important that this protocol to be implement because prevents loops to be formed. A loop can be dangerous and costly for any network, because can cause significant network disruptions. A loop can occur from a several reasons, such as follow: the entire network fail because of a hardware failure, a network attack or a configuration issue. To setup STP, should select one switch to be a Root Bridge. In this case the Root Bridge is Switch 1.
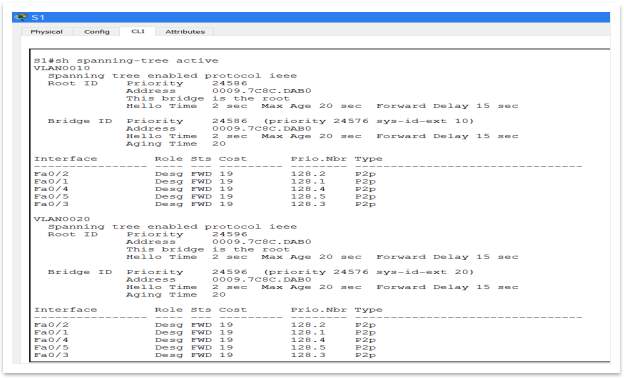
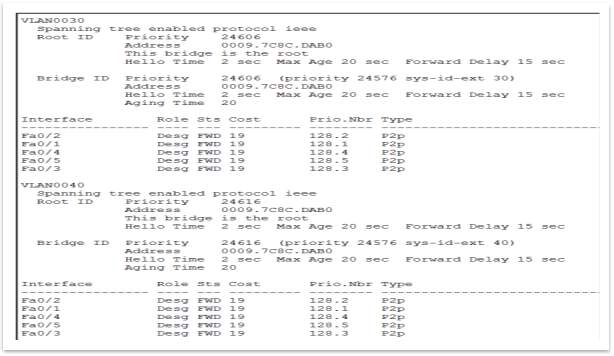
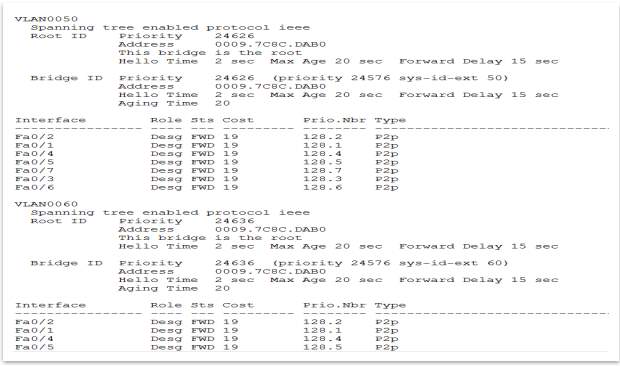
Figure 24 – S1 setup as a Root Bridge (3 pictures avove)
c. Hardening the Wireless Router
In the process of securing the network, a special attention should be paid to the Wireless Router, as it is one its most vulnerable parts.
To make this possible, we need to access the Wireless Router’s GUI, and there, in Basic Wireless Settings based under the Wireless Tab, to configure SSID features, by giving a Network Name and disabling the SSID Broadcast. In fact, the SSID is different than the Network Name assigned to a wireless router. Unfortunately, the Packet Tracer environment won’t allow to assign for SSID a name of 32-character string, that ensure the network name is different from other nearby networks. On laboratory condition, offered by the Packet Tracer, it is possible only to name the network. In this case, the network name is “Magic Memories”.
On same time, should disable the SSID Broadcast, to secure the wireless network. This will hide the network name or SSID from other users which search for wireless networks in the area.
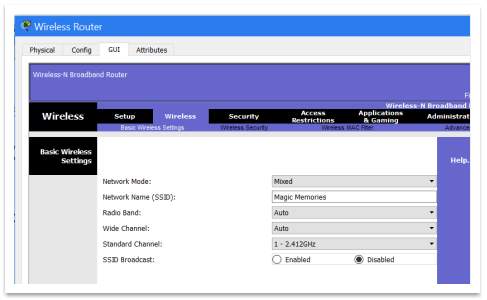
Figure 25 – Network Name and SSID Broadcast
After that, on Wireless Security screen, should chose a Security Mode suitable for our wireless network. In fact, the security mode chosen should be WPA2 Enterprise, but on lab condition WAP2 Personal it is more suitable because can be setup.
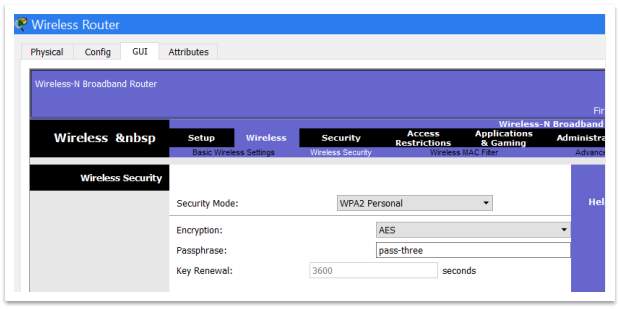
Figure 26 – Wireless Security
“WPA2 Personal is the main Wi-Fi security method and this is what most home and small business users use. It uses a single password. Most Wi-Fi networks use this method.
WPA2 Enterprise is also called 802.1x and is the enterprise method. This method shouldn’t be used by home users as it requires a RADIUS authentication server and needs a username and password. It supports multiple accounts for each user.” Security Concepts Note of Course, Edinburgh College
The encryption chosen for WPA2 Personal is AES (Advanced Encryption Standard) and the password is “pass-three”. The AES encryption was chosen instead of TKIP (Temporal Key Integrity Protocol) which is quite similar with the very-insecure WEP encryption. That’s why TKIP is no longer considered secure, and shouldn’t be using it.
To test these settings, try to connect the laptop to the wireless router. It will not be possible until the security steps will not be passed.
Figure 27 – Creating a profile
Figure 28 – Introduce the network name
Figure 29- Select security
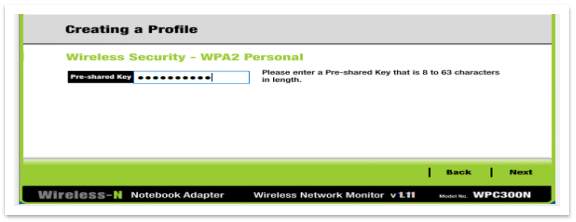
Figure 30 – Enter the password
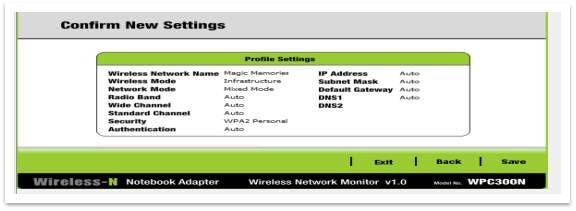
Figure 31 – Confirm settings
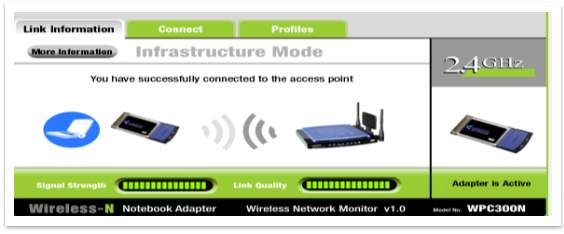
Figure 32 – Connection successful
The Wireless Router firewall. The Wireless Router in Packet Tracer comes with default firewall features and does not let users to configure it. Therefore, certain configurations cannot be demonstrated under laboratory conditions.
Figure 33 – Wireless Router Firewall
Other measure o security which should be applies is MAC filtering. This is a very powerful security tool and once is setup, allow access to the router only to that machines which have the MAC address registered on router. This can be worked on closed environment, where all the mobile devices belong to the company or are well known. But into an open environment, where the wireless access is permitted for guest and visitors, this tool is almost inefficient and cannot be used.
d. Hardening the printers
Usually the printers are ignored by the networks administrators and fail to secure them, but once a device has an IP address and internet connection can be accessed by a hacker. A series the actions can be taken in the process of hardening the printers, but in our Prototype, built in Packet Tracer, will be exemplify just one of them. This will be about limiting the access to the printer. To do that should remove the default gateway from printer configuration. If the printer doesn’t have a default gateway, then cannot gain access to the router. Without router access, cannot communicate with others VLANs. In this case the printing is only available on a VLAN which belong.
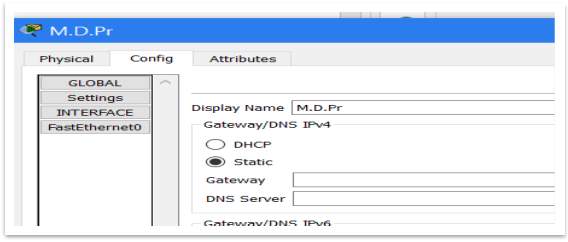
Figure 34 – No Default Gateway
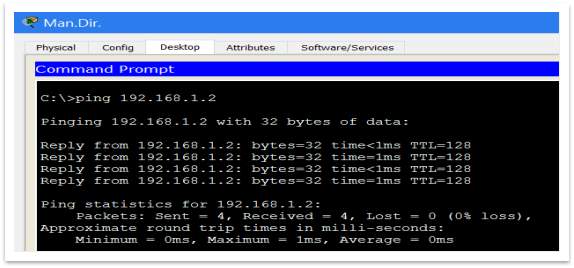
Figure 35 – Ping from same VLAN
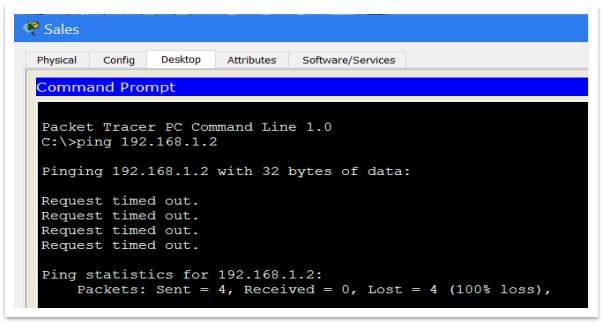
Figure 36 – Ping different VLAN
The backup printer will remain with the Default Gateway configurated to gain emergency access from any VLANs.
The prototype build on VMware for server configurations
This is a distinct part of the Prototype, so that it can be developed under laboratory conditions requires at least three computers, physical or virtual. For this case, three virtual machines installed in VMWare will be used. They will be part of the same private network with this IP address 192.168.1.0/24.
To meet the needs and requirements imposed and to create a functional and secure Prototype, the computers used must fulfil the following features:
- A computer must run Windows Server 2008 R2, Enterprise Edition, configured to provide the following functions:
- The primary domain controller for the SebastianMagicMemories.com Active Directory domain.
- A Domain Name System (DNS) server that can resolve names for the SebastianMagicMemories.com DNS zone.
- Two computers should run Windows 7, Professional Edition, configured as follows:
- A domain member in the SebastianMagicMemories.com domain
- A Telnet client
- One computer dedicated to Mr Williamson and the other to Mr Heron (Sales Manager)
To be able to configure the machines, should run as Administrator. For the Prototype, “sebastian” is the administrator. To be able to create the network VMWare should have these settings:
- On Virtual Machine Settings, should find Network Adapter then click on it
- By default, the VMWare network adapter is on NAT. This should be changed on Bridged with Replicate Physical Network Connection State.
a. Setup the Prototype computers
Set up the domain controller and create the domain
For Server, must install Windows Server 2008 R2 by using the following settings:
- Set the local Administrator (Sebastian) account password to F0rthv1ew
- Configure the network to use the following settings:
- IP address: 192.168.1.1
- Subnet mask: 255.255.255.0
- Default gateway: none
- DNS server address: 192.168.1.1
- Name the computer server-SebMM. Restart the computer.
- Install Active Directory by using the following settings:
- Create a new domain in a new forest, and name the domain SebastianMagicMemories.com.
- Set the Forest Functional Level to the highest level supported in the version of Windows Server 2008 R2
- Include DNS as part of the installation.
- Use the password F0rthv1ew for all user accounts.
- After installing Active Directory should restart the computer.
- Create a new user account in SebastianMagicMemories.com named Admin1, with a password of F0rthv1ew.
- Add Admin1 to the group Domain Admins.
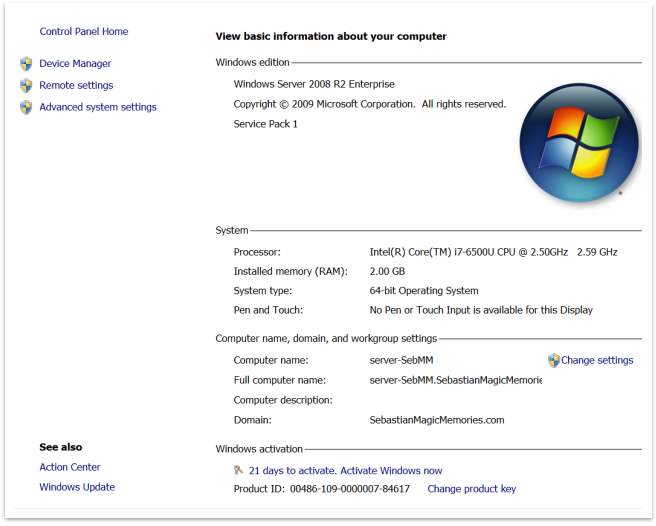
Figure 37 – Domain name and server name
For Client Machines, must install Windows 7 Professional, by using the following settings:
- When prompted to name the local administrator during setup, name it sebastian, and then set its password to F0rthv1ew.
- Name one computer CLIENT1 and second CLIENT2
- Identify the network location type as Work.
- Configure the network to use the following settings:
- IP address: 192.168.1.2 (for the first PC) and 192.168.1.3 (for the second PC)
- Subnet mask: 255.255.255.0
- Default Gateway: none
- DNS server address: 192.168.1.1
- Using the Turn Windows features on and off option in the Program and Features control panel program, install the Telnet Client onto the computer.
- Join the computer to the SebastianMagicMemories.com domain, and then restart the computer.
Figure 38 – Computer name and domain name for PC1
After these settings are done, must:
Enable Network Mapping on Domain and Public Networks
To do that must do another small setting in all three machines, as follow:
- On Run search area, type gpedit.msc, then open it.
- Go to Computer Configuration – Administrative Templates – Network – Link-Layer Topology Discovery.
- Double-click the Turn on Mapper I/O (LLTDIO) Driver policy, select Enabled and then select Allow Operation While in Domain. Then click Next Setting.
- Double-click the Turn on Responder (RSPNDR) Driver policy, select Enabled and then select Allow Operation While in Domain. Then click Next Setting.
- Click OK.
Figure 39 – Server Mapping
Figure 40 – Client Mapping
Now the network it is functional and all the machines from it are visible.
Examine the default security settings on server and clients
In this stage, will be checked the Windows Firewall in every machine. I got this result everywhere:
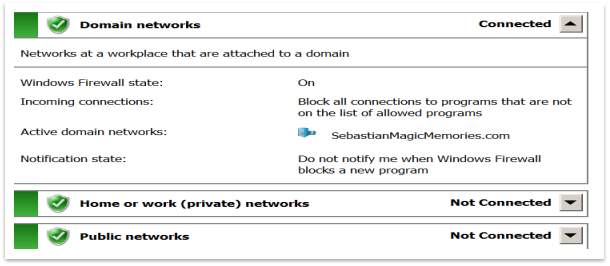
Figure 41 – Default Windows Firewall
This picture tells the firewall is on, what it is good for security. Of course, a lot of settings can be made by creating rules and policies to be applied to restrict traffic; to allow specific software to run on a specific machine; to give access or not for some certain users; to block, restrict or allow access to the machine, etc. But for the moment, will not go any further with the firewall settings.
b. Deploying basic settings by using Group Policy
In this section, it will be created Organizational Units (OU) containing the user accounts of the company’s employees. To develop the Prototype, the entire organizational structure of Magic Memories will be built into the Server. The two virtual PCs will be set and allocated to the Managing Director account (Mr. Williamson) and to the Sales Manager account (Mr. Heron).
Also, GPOs with specific rules and configurations will be created that will apply differently to user groups, depending on the specifics and requirements of each group.
Using Group Policy Management Editor can be configurated a GPO for basic firewall settings. Steps for deploying basic settings by using GPO.
Step 1: Creating OUs and placing Computer Accounts in them
- On Server, click Start, click Administrative Tools, and then click Active Directory Users and Computers.
- In the navigation pane, right-click SebastianMagicMemories.com, click New, and then click Organizational Unit.
- In the Name box, type Managing Director, and then click OK.
- Right-click SebastianMagicMemories.com again, and then click New, and then click Organizational Unit.
- In the Name box, type Sales Manager, and then click OK.
- In the navigation pane, click Computers.
- In the results panel, right-click CLIENT1, and then click Move.
- In the Move dialog box, click Managing Director, and then click OK.
- In the results panel, right-click CLIENT2, and then click Move.
- In the Move dialog box, click Sales Manager, and then click OK.
Figure 42 – Assign a computer to an OU
In this way, the OU was created as follow: Purchasing Manager, Accounting Manager, Sales Department, Purchasing Department, Accounting Department. Because it is working under laboratory conditions, it is not possible to assign a computer for each OU created.
Step 2: Add Users to the OU
Once OUs have been created, Users should be added to them. To complete this task, the following steps should be done, as in this example: Right-click on “Sales Manager” OU and select New > User. Then should add details as required: i.e. first name, last name, full name, user logon name. After that should set-up the password for the user (F0rthv1ew). Some password options must be set. For now, we will choose “Password never expires”. Anyway, these options may be changed later one.
Figure 43 – Users password chooses
Step 3: Create Groups
Once the OU and Users were created, should create Groups. To do that shall follow these steps, as in following example: Right click on the Sales Department OU and select New > Group. Call the group Sales Team. After that set up the group Scope and Type. For the Prototype the choise is global security group. Then, should select the group members. As in example, the members of Sales Team Group are: M Heron (Department Manager), L McKechnie and R Simpson (Staff) and R Williamson (Managing Director). For Sales Manager Group, the members are: M Heron (Department Manager) and R Williamson (Managing Director) and for Managing Director Group, just R Williamson is a member of it.
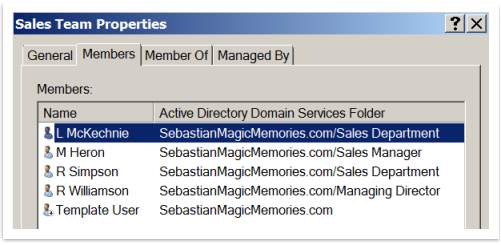
Figure 44 – Members of Sales Team Group
Step 4: Create Directories for each member the staff
Prior all OU, Users and Groups was created, as a next stage of the server setup process, it is to create a space where Magic Memories employees can save and secure their files. To do that, should create a new directory, named Home, following this path: Computer>Local Disk C>Home. After this directory is created, some sharing rules are applied, as shown below:
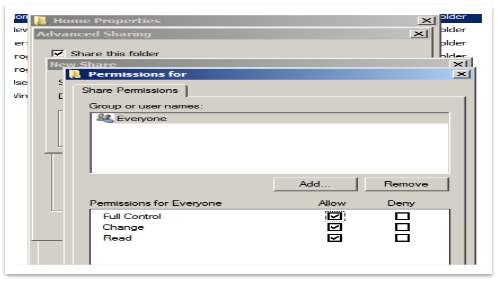
Figure 45 – Share rules for Home Directory
Once the Home folder is created and set with sharing rules, inside it, other directories must be created for each user. These directories are very useful because are a secure place where to store data and the access is generally permitted only to the user. Other users may have granted administrator privileges and gained authority to access any protected location on the filesystem including other users home directories.
Next will be showed how to create these directories and the link between user’s PC and Server’s User Home Directory. The way is as follow: go to ADU and C > Sales Manager OU. Then wright-click on M Heron user and choose Properties. Then go to the ‘Profile’ tab and configure the following:
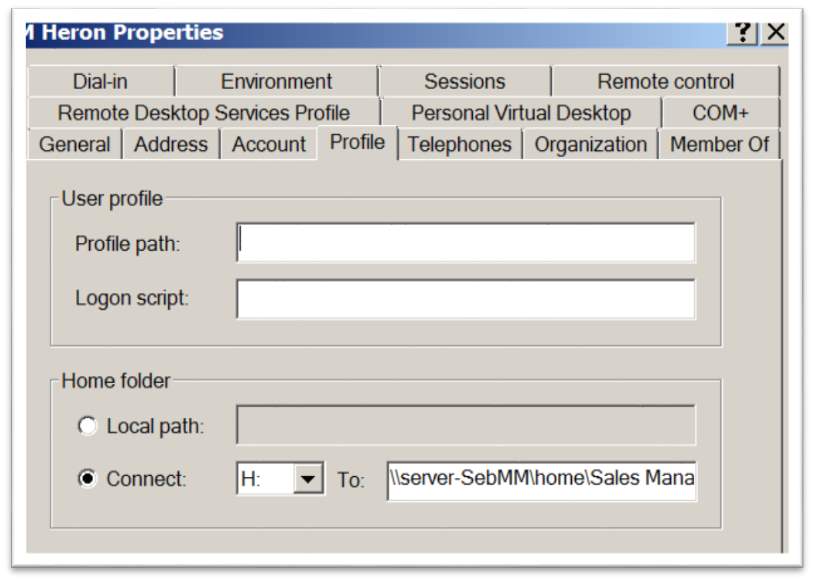
Figure 46 – Link User Home Directory
Connecting ‘H:’ to \server-SebMMHomeSales Manager, means that M Heron (Sales Manager) home directory is accessible through the “H” (an icon will appear in in his PC under “Computer”). That mean the disk “H:” is mapped to the Server “server-SebMM” and the shared directory “Home”. “Sales Manager” is the name of the folder created on Home and where the files of Mr Heron will be saved.
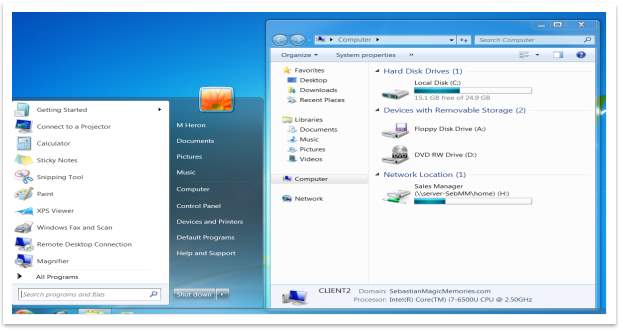
Figure 47 – Mapping
On server, the Home directory will be like that:
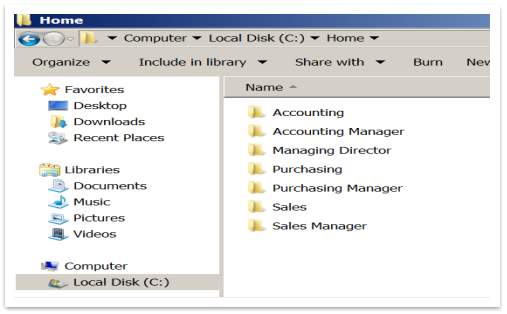
Figure 48 – Saving folders
Step 5: Sharing rules
In every department’s folder was created subfolders for each member of staff which belong to that department and for each of them was configurated rules regarding sharing and security.
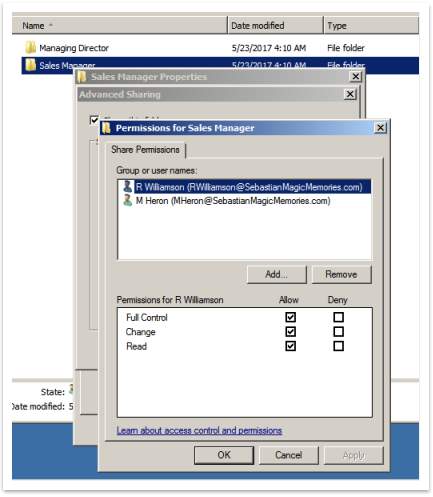
Figure 49 – Share permission example
Table 4 – Sharing permission
| Type of staff | Sharing Permission | Sharing not permitted |
| Staff 1 of department | Managing Director
Manager of department Staff 1 of department |
Staff 2 of department
All members of staff from other departments |
| Manager of department | Managing Director
Manager of department |
Staff 1 and 2 of the department
All members of staff from other departments |
| Managing Director | Managing Director | Everybody else |
Step 6: NTFS Permissions
Prior the sharing rules was created, as a next step should configure the NTFS permissions, using this path, as example: Right click on Sales Folder > Properties > Security > Edit. By clicking Add button give us the option to add Groups or Users at the Permission Access List to the folder. Should set the appropriate permissions for every name on the list. (e.g. full control or modify or read, etc.). To establish different level of security to another group, must create and add that group to the ACL below, with the different permissions configured.
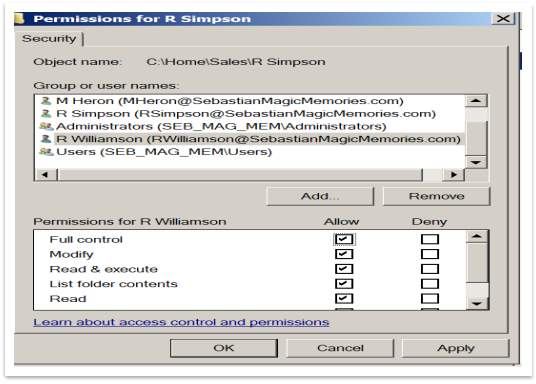
Figure 50 – NTFS ACL
Now must go on PCs where will be setup a new user for each machine. R Williamson will be the user of PC Client 1 and M Heron will be the user for PC Client 2. To do this should follow these:
- Control Panel then User Account and again User Accounts
- Manage User Account, then click Add
- Type in User name MHeron and domain SebastianMagicMemories.com, then Browse. Type the name MHeron and click Check Names.
- Choose level of access: standard, administrator or Other and press finish. A new user it was added to the computer.
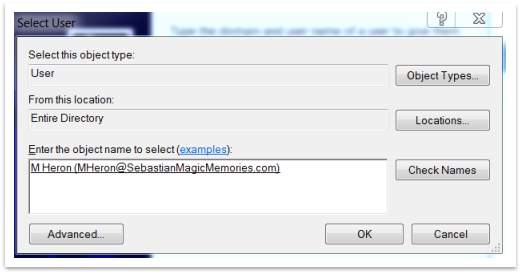
Figure 51 – Create a new user for PCs
In this way, the link will be created between PCs Users and their places on Servers.
c. Group Policy Management Console (GPMC)
The Group Policy Management Console (GPMC) is a very powerful tool that allow the administrator to gain access to all the GPOs, OUs, Users, Domains, etc. Basically, all the security settings can be done using GPMC. Of course, for our Prototype will be impossible to setup and apply all the security features, because are far too many and not all of them have applicability to our case. I’ll try to setup just few of them, the common security measures, specifically for Magic Memories needs.
Create a password and account lockout policy for a domain
Go to Start > Administrative Tools > Group Policy Management, then expand Forest > Domains > “SebastianMagicMemories.com”. Right-click Default Domain Policy and select Edit. On New Screen, under Computer Configuration, expand Policies > Windows Settings > Security Settings > Account Policies > Password Policy. The will get this screen:
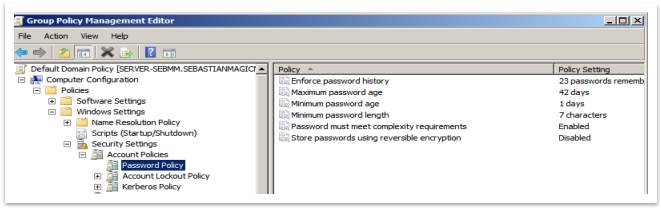
Figure 52 – Password Policies for a Domain
To modify any of these settings should double click on rule and change the value to meet the needs.
Create a password and account lockout policy for an OU (with a stronger security configuration).
To set a separate GPO for a specific OU, should follow these steps, as in the next example: Right-click on Managing Director OU and select “Create a GPO in this domain, and Link it here …”. Then name the GPO – “MD OU GPO” and OK. Next right-click on it and choose Edit. Start to configure the password, following this path: Computer Configuration, expand Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
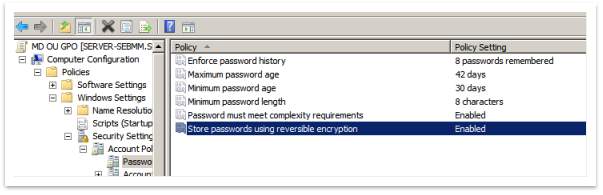
Figure 53 – OU password
Creating the GPOs to Store Settings
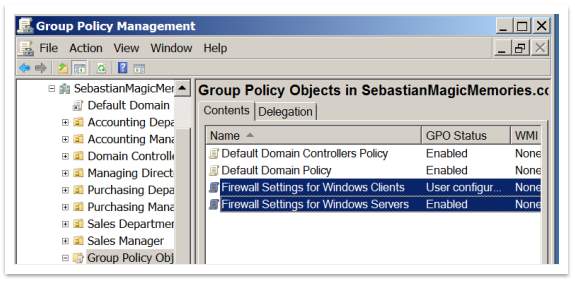
Figure 54 – GPO for Firewall |
Adding the GPO Setting to Enable the Firewall on Member Client Computers
- On Server, in Group Policy Management, click Group Policy Objects, right-click Firewall Settings for Windows Clients, and then click Edit.
- In Group Policy Management Editor, right-click the top node Firewall Settings for Windows Clients [SERVER-SEBMM.SEBASTIANMAGICMEMORIES.com] Policy, and then click Properties.
- Select the Disable User Configuration settings check box.
- In the Confirm Disable dialog box, click Yes, and then click OK.
- Under Computer Configuration, expand Policies, expand Windows Settings, expand Security Settings, and then expand Windows Firewall with Advanced Security.
- Click the node Windows Firewall with Advanced Security – LDAP://cn={11EB3F8D-AFA2-4E4B-89C6-3DAB8F7D360E},cn=policies,cn= system, DC = SebastianMagicMemories, DC = com, where the long number is a unique number assigned to OUR domain.
- In the results pane, under Overview, notice that for each network location profile Windows Firewall state is not configured, and then click Windows Firewall Properties.
- On the Domain Profile tab, click the drop-down list next to Firewall state, and then click On (recommended).
- In the results pane that Domain Profile now shows Windows Firewall is on.
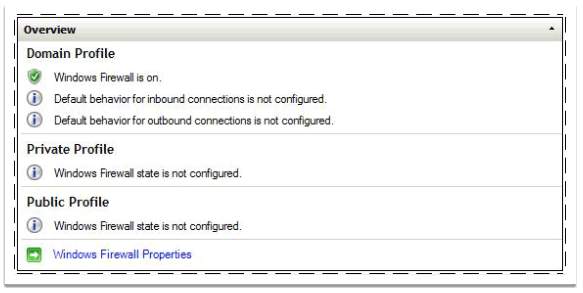
Figure 55 – Windows Firewall
Deploying the Initial GPO with Test Firewall Settings
In this step, must link the GPO to an OU to apply it to the domain-joined client computer.
Deploy the firewall settings:
- On Server, in Group Policy Management, in the navigation pane, right-click Sales Manager, and then click Link an Existing GPO.
- In the Group Policy objects list, click Firewall Settings for Windows Clients, and then click OK.
In this way assign firewall settings to all the Windows Clients from server. A next procedure what should be followed, is to assure that the Client Computers receive and applies the new GPO settings.
- On Sales Manager PC, open an administrator command prompt
- Then type gpupdate /force. After press enter.
- To be sure that the GPO was correctly applied, run gpresults /r /scope computer. In the new screen, must look after Applied Group Policy Objects, where is confirmed the entries for Firewall Settings for Windows Clients and Default Domain Policy.
- Open the Windows Firewall with Advanced Security snap-in
- Right-click the top node Windows Firewall with Advanced Security on Local Computer, and then click Properties.
- The Firewall State setting is “On (recommended)” and is disabled. This is the proof that it is now controlled by Group Policy and cannot be changed locally, even by an administrator.
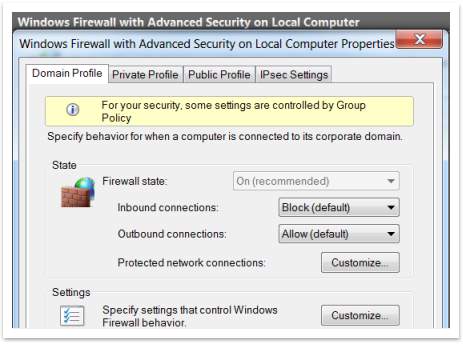
Figure 56 – Firewall is controlled by GPO from server
Adding the Setting that Prevents Local Administrators from Applying Conflicting Rules
In this step, it will be configurated a setting to prevent firewall rules created by network administrator to conflicting with the GPO-deployed rules.
- On Server, in Group Policy Management, click Group Policy Objects, right-click Firewall Settings for Windows Clients, and then click Edit.
- In Group Policy Management Editor, expand Computer Configuration, expand Policies, expand Windows Settings, expand Security Settings, and then expand Windows Firewall with Advanced Security.
- Right-click Windows Firewall with Advanced Security and then click Properties.
- On the Domain Profile tab, in the Settings section, click Customize.
- Change the Display a notification setting to No. This prevents Windows from displaying a notification to the user whenever a program is blocked.
- In the Rule merging section, change the Apply local firewall rules list to No.
- In the Rule merging section, change the Apply local connection security rules list to No.
- Click OK two times to return to Group Policy Management Editor.
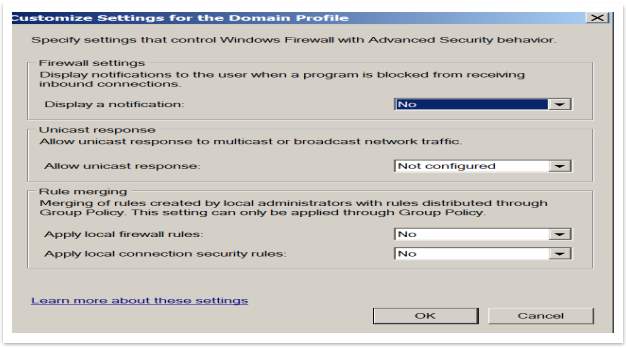
Figure 57 – Firewall settings
Configuring the Rest of Your Client Computer Firewall Settings
A local administrator can modify settings which are not under the GPO. That’s why is necessary to configure settings in GPO, that a local administrator to don’t be able to modify them.
- On Server, in the Group Policy Management Editor, right-click Windows Firewall with Advanced Security and then click Properties.
- On the Domain Profile tab, in the State section, set Inbound connections to Block (default), and set Outbound connections to Allow (default).
- Click OK to save your settings and return to the Group Policy Management Editor.
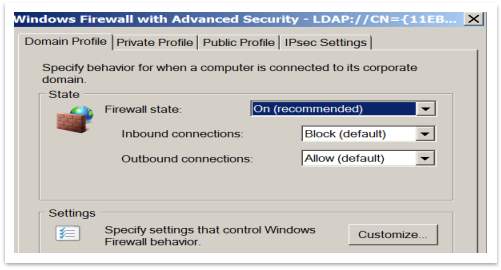
Figure 58 – Firewall settings to block external changes
Test the new restriction:
- On Sales Manager PC, in Administrator mode run: Command Prompt, type gpupdate /force, and then press ENTER. Wait until the command finishes.
- In the navigation pane of the Windows Firewall with Advanced Security snap-in, right-click the top Windows Firewall with Advanced Security node, and then click Properties.
- On the Domain Profile tab, notice that the restrictions now prevent a local user, even an administrator, from modifying the settings.
- In the Settings section, click Customize, and then notice that the settings that you configured in Group Policy cannot be locally changed.
- Click Cancel two times to return to the Windows Firewall with Advanced Security snap-in.
- Close the Windows Firewall with Advanced Security snap-in.
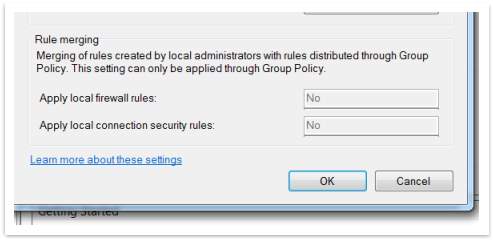
Figure 59 – Test that a local administrator cannot do changes on Firewall
Configure Automatic Updates by Using Group Policy
Open GPO Management and under Forest >SebastianMagicMemories.com > Default Domain Policy, right-click on last of them and select Edit. After that, following the path Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update > Configure Automatic Updates. Click on the last one and select Enable and choose what will happening when an update should be downloaded and installed.
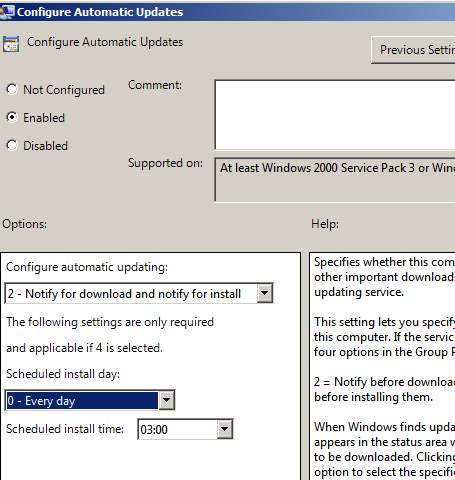
Figure 60 – Automatic Updates
d. Network Policy and Access Services (NPAS)
NPAS provide technologies that allow to deploy Virtual Private Networking (VPN). As well, with this technology can define and enforce policies used foe Network Access Authentication and Authorization by using NPS (Network Policy Server), HCAP (Host Credential Authorization Protocol), Routing and Remote Access Service, etc. For Prototype, will setup a VPN. To do that should add NPAS as a role, using for this task Server Manager. Once installation is finish, open “Routing and Remote Access” from Administrative Tools, to create a VPN. Next, right click on the Server icon and select the top option and Next on follow screen. Select Remote access (Dial-up or VPN) and after select VPN. The follow message showed bellow come:
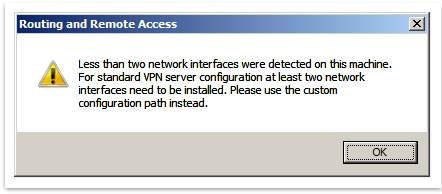
Figure 61 – An error message
To solve that error, should configure the virtual machine (VMware) by adding an extra network interface. After that, should continue by Selecting VPN. On the next three screens is nothing to modify, so the RRAS Setup Wizard should install the VPN.
Figure 62 – VPN on server
e. Hardening a Server
To reduce the attack surface on server and lower potential to potential for compromise, it is a good practice Security Hardening the Server, by applying some specifics checks or using some specialized software to analyze potential vulnerabilities. Several of them will be used on Prototype for exemplification.
Configure a security policy. To configure a security policy should use Security Configuration Wizard (SCW) from server.
Microsoft Baseline Security Analyzer (MBSA)
System and Application Updates. All ready in our Prototype it is applied a GPO regarding Automated Updates. Alternatively, can use Windows Server Update Services (WSUS) role. This should be added by going to Server Manager > Add roles. In the new screen select Server Roles and Windows Server Update Services. Click next and Install.
Remote Management Redux
Disable or delete unnecessary accounts, ports and services. Three local users are installed by default: Administrator, Guest and Help-Assistant. Should disable them following this path: Control Panel > Administrative Tools >
Uninstall Unnecessary Applications
Configure the windows 2008 Firewall
Configure Auditing
Disable unnecessary shares
Configure Encryption on 2008 server
Anti Virus amp; NAP
Least Privilege
f. Setup Windows Server Backup
Since backups are a copy of most valuable files and data of the company, the necessity of using a Backup Server it is almost vital. Backup security is not a project it is a process that requires constant monitoring and improvement. Without backup and recovery data facilities, a company can suffer negative consequences as losing: money, clients and trust.
That’s why in our prototype will install and run a backup server.
g. Setup Printer Server
h. IPSec configuration
i. Setup Antivirus on Server
2.2. A Security Report for Mr Williamson
Introduction
Nowadays, when business rely on the Internet more than ever and the technologies are more advanced and sophisticated, the business networks can face severe threats from bugs viruses and hackers at any time. That’s why it being so important to protect the computer network. Doesn’t matter how big or small is the business, once the company is working online, network security is one of the most important factor should be considered. Even like that, the network is not fully immune to an attack, but to minimalize the risk should be implemented a high-quality Network Security system.
Magic Memories company, as a part of the group of Small and Medium Enterprises (SMEs), face a high security risk. Many owners of SMEs, included here Mr Williamson, believe that the large companies and corporations are more expose to security threats than that of small companies. In fact, things are different. For example, according to Internet Security Alliance organization, destructive “Mydoom” worm affected one in three SMEs, but only one of six large companies. False sense of security affects a significant number of SMEs considered that they are not at risk and therefore unprotected their computers and networks against security threats such as the software spyware, viruses, worms, hacker attacks and theft customer information. In addition, having already “juggling” frequently with more problems, entrepreneurs placed the computer security in lower positions of the lists of priorities (if such list exists). Consequently, the small companies such a Magic Memories have not taken even basic security measures.
The reasons why the SMEs (as Magic Memories) are more expose to the security risks
As never before, the higher exposure of computers, networks and SME’s data to the security risks is due to several factors.
- Breaches in security systems of enterprise networks are more difficult to be made. In recent years, the big companies have increased significantly the security of their networks, due to the growing number of threats from the Internet and the need to comply with new regulations such as Basel II. Consequently, criminals are increasingly turning their attention strongly to more vulnerable targets – SMEs.
- Unprotected systems are easier to be identified by hackers. Nowadays, on the market exist many software tools, used by hackers, that constantly searching on the Internet seeking for computer network unprotected. Once discovered, unprotected computers can be accessed and controlled by hackers who can use it to launch attacks on other computers or networks.
- Security threats are becoming more sophisticated and damaging. The authors of spy software create malware which are difficult to eliminate, suffering “mutations” continue and spread on the Internet in minutes. At the same time, the hackers have now the resources to combine the threats and putting them on multiple forms, which are able to attack the networks on several different ways. If Magic Memories do not adopt a proper security solutions and up to dates, can be easily affected by security threats.
- Frequently, security threats are arising “from the inside”. Too often, security breaches come from systems within companies and most often, are unintended. For example, an employee can download unknowingly, spy software when playing certain online games or when accessing certain Web sites. The company network is vulnerable from inside, caused unintentionally by employees, due to lack of information and internal security.
- The lack of financial and technical resources allocated to network security by the SMEs such as Magic Memories, can affect seriously the future of the business. The impact of attacks on information security is higher. For example, if a DoS attack type (block service) will be launched against Magic Memories website which provide online shopping, it is unlikely that the lost revenue to be recovered. In addition, the effects of such an attack can seriously affect relations with customers and reputation.
What are the solutions?
The solution to protect the network against any security threats are multiple, complex and varied.
The first step is to include the issue of securing access to the Internet as a fundamental element in terms of priorities of the company. But it is not enough to declare that the network security it is a top priority. There must be a written and detailed plan dedicated to security, including policies and procedures, and, in case of companies with more employees, a plan containing the technical requirements. If security procedures are not in writing, it will be easy to employees to challenge them or to ignore them.
Also, there are several issues that Magic Memories should not lose sight of:
- Usually a small company are using a minimum of requirement to accomplish IT security, by protecting itself through a firewall, an antivirus and an antispyware programs. The network security solutions dedicated to Magic Memories, combines all three elements mentioned above and in addition, provides protection against identity theft, spam, phishing, etc.
- Magic Memories should assess procedures and security solutions implemented and establish if they meet the current business requirements. It is very usual that the managers of the business to don’t know or to don’t understand all the elements included in the security solutions implemented. For example, the routers from the company’s LAN have incorporated technologies like firewalls, which block intruders from accessing computers on the network. In any case, it is important to check the features and functionality of security features implemented.
- Mr. Williamson believe that even considering the aspects of cyber security is a difficult task. Therefore, one option is the use of external expertise. Hiring a consultant to carry out a security audit of the systems and networks can clarify the list of requirements strictly necessary. Also, security solutions can be established and network equipment vendors and technology providers. Another option is the use of external services. A provider of managed services, such as the leading provider of telecommunications services, can design, implement and maintain a security solution for network, for a relatively small monthly fee.
- Another key is regularly updated security solutions adopted by Magic Memories. Every day appear on new Internet security threats. If the systems are not updated quickly and regularly, they become ineffective against the attacks. Most antivirus can be automatically updated.
The network security is a functional basis for the commercial success of the Magic Memories, but the security measures should not be excessive, because it is possible to make the computers unusable. Magic memories need to strike the right balance between security and usability.
The company secure network release benefits that go beyond the context of protection against threats. By its nature, a secure network is a robust network and a robust network is a great base for implementation of new technologies, which can contribute significantly to increasing productivity and reducing operating costs. When a company is secure informatic, it becomes stronger, more flexible and certainly more competitive.
Accordingly, with the principle and theories presented above, the main reasons to protect the network are:
- Protect client data – As a business it’s a legal duty to keep all client’s data safe and secure. The rising of information theft make imperious necessary to provide a high-quality network security, to prevent and reduce the risk of falling victim to data theft.
- Protect employee’s data – By law, the personal data of the employees should be kept safe, secure and up to date by the employer.
- Protect computers from harmful spyware – A well secured network can be very efficient in protecting the company’s devices from physical harm, helping to safeguard the machines against virus or spyware attacks.
- Keep shared data secure – A secured network should keep shared information and data safe. Different configuration and level of security can be putted in place for specific computers that may have greater access to information and data than others.
- Traffic – A high level of traffic can affect the systems stability and as an immediate effect the network become vulnerable to attacks. A high-quality Network Security can reduce the risk of attacks.
- Increased network performance – by investing in facilities which increase the security of the network, the benefits of the business will be majors and helps to reduce the business costs for a long-term perspective. All of this will boost the profit.
If network security is compromised, the consequences could have major implications that can affect the entire business. Loss of privacy, theft and information loss are very dangerous for any business, that why it is necessary to be treated with a special attention and to consider any cost of security as an investment on the future health and prosperity of the business.
“Serious financial damage has been caused by security breaches, but because there is no standard model for estimating the cost of an incident, the only data available is that which is made public by the organizations involved.
‘Several computer security consulting firms produce estimates of total worldwide losses attributable to virus and worm attacks and to hostile digital acts in general. The 2003 loss estimates by these firms range from $13 billion (worms and viruses only) to $226 billion (for all forms of covert attacks). The reliability of these estimates is often challenged; the underlying methodology is basically anecdotal.’
However, reasonable estimates of the financial cost of security breaches can actually help organizations make rational investment decisions. According to the classic Gordon-Loeb Model analyzing the optimal investment level in information security, one can conclude that the amount a firm spends to protect information should generally be only a small fraction of the expected loss (i.e., the expected value of the loss resulting from a cyber/information security breach).” http://en.wikipedia.org/wiki/Computer _security
The process of implementing security into a computer network should take in consideration three important aspects: privacy (confidentiality), integrity and availability.
- Privacy (Confidentiality) is the capability of a network to provide access to information only to authorized persons.
- Integrity ensures that the information/data has not been altered by unauthorized persons.
- Availability may be defined as the time the computer network and resources within it are operational.
For each of these aspects of computer network security, attacks exist. That’s why in order secure a computer network must implement each of these aspects.
To be able to deliver a high-quality Network Security system, should be covered these areas on the network:
- Network security
- Compliance and operational security
- Threats and vulnerabilities
- Application, data and host security
- Access control and identity management
Section A: Network Security
According with SANS Institute “Network Security is the process of taking physical and software preventative measures to protect the underlying networking infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure, thereby creating a secure platform for computers, users and programs to perform their permitted critical functions within a secure environment.” https://www.sans.org/network-security/
To create a better picture about the Network Security concept it was appropriate to divide this area into smaller parts for a better and deep analysis and explanation.
A.1. – Network Device Security
Switches and Routers | Firewalls | VPN and VPN Concentrators | Network Intrusion Detection and Prevention | Protocol Analyzer | Unified Threat Management
Switches and routers are the core building blocks of any network. They are manufactured by many companies, but Magic Memories Company used Cisco devices.
The switches are OSI Layer 2 computer networking devices and are deal with MAC addresses. They connect other devices together on a computer network. The switches used on this project have 24 ports. Each switch port can be connected to one end of a network cable (CAT5e). For Magic Memories, will not be used wireless switches. Switches are limited to creating local networks.
Routers are OSI Layer 3 devices and can deal with IP addresses. They have the capability to connect networks. The routers serve as the traffic controller of the network. They can make decisions about the best paths for traffic to follow as it travels to its destination. The routers perform some security functions. ACL can be implemented on routers and act as a firewall.
The routers and switches play an important role in connecting systems together to create enterprise networks.
Firewall devices are the security guards of the networks. Are very useful devices because have capability to analyse all attempts to connect to systems on the network, and determining whether those requests should be allowed or denied, in accordance to the company’s security policy. The Magic Memories network don’t require implementing a firewall device. Instead, will be used a software solution for firewall.
VPN (Virtual Private Networks) have two important network security features: allow a secure interconnection of remote networks and allow a securely connect from remote locations back to the organization’s network. Both are useful for Magic Memories. First one permitted connection between Glasgow and Edinburgh Offices and the second one permitted the remote access for managers to the company network. VPNs work by using encryption to create a virtual tunnel between two systems over the internet.
Usually, when the numbers of VPNs are high it’s recommended to be use a device named VPN Concentrator. For Magic Memories network is not necessary.
Network Intrusion Detection and Prevention systems are very important part of the defensive system of networks against cybernetic criminals or any other security threats. With Intrusion Detection System, the network traffic will be monetarised and a permanent search will be performed looking for sign of potential malicious activity. If a suspect situation will be identified, an alert message will be send to the user.
Intrusion Prevention system, is similar with Intrusion Detection System, but have capability to take immediate action against any threat.
These two systems use two different techniques to detect suspicious traffic: Signature Detection and Anomaly Detection.
Protocol analysers are an important tool which allow network administrators to peer into the actual packets traveling on a network, and inspect them in deep detail. This is very useful when trying to troubleshoot network issues or investigate security incidents. The most common and free Protocol Analyser is Wireshark.
Unified threat management (UTM) solutions try to solve the financial issues faced by the small and mid-size companies, by providing many different security functions on a single device. UTMs are, very useful solutions for organizations that would not otherwise be able to afford sophisticated security devices.
A.2. – Network Administration Principles
Firewall Rule Management | Router configuration (Hardening) | Switch configuration (Hardening) | VLAN Management | Port Security | Maintaining Network availability | Flood guard | Spanning Tree Protocol | Network monitoring | SNMP | Storage networks
Firewall rule management it is a very important principle on the network security. The function of a firewall it is very simple: should block any unauthorised traffic from outside source to inside the protected network. To do that, the firewall should consult a list of rules maintained by administrator. If the attempted connection matches with a rule from list, then the access is granted. If not, the access is denied. The traffic pass firewall via ports and every type of traffic have allocated a specific port. E.g. web traffic has allocated port 80, SMTP e-mail traffic port 25, etc. The firewall can be setup to block some certain ports and leave open other.
Router configuration security (or Hardening). Router playan important role on network security, but for best performance need additionally configurations. For example, the function of filtering traffic is not their best strength, that’s why an administrator should implement an extra set of rules to make the router stronger and more difficult to be touched by the potentials attackers. The process to make the router impenetrable is named hardening. This process cover different areas and levels of security, as follow:
Using the passwords to lock down the router. These passwords must be applied at login mode to prevent the access and at privileged mode to prevent changes in configuration. These passwords should be encrypted as well.
Login mode passwords should be applied on Console, AUX, and VTY (telnet/SSH) interfaces. These passwords will control the remote access to the router (VTY) and will looked the console and auxiliary ports.
Setup a username and password. Allow us to setup some credentials for the users with access to the router.
Shutdown the unused interfaces. It is not reason to keep open the interfaces what are not in use. In this way, will be able to minimalize the area of manoeuvre for any potential attacker.
Disable any unused functions
Setup an ACL. Whit Access Control Lists (ACL) the routers are usually protected from attacks. ACLs acting as a firewall and allow traffic to pass router. Due their complexity, very often can be misconfigured or ineffective. That’s why should be kept as simple as possible to avoid any further inconvenience.
Protect the router with a firewall. Instead using ACL, a helpful solution is to use Cisco SMD Firewall Wizard. This software it is built to secure small offices “by using predefined rules to allow private-network users to access the Internet, and protect the private network from the most common outside attacks. The Firewall Wizard is capable of the following:
- Applying default access rules to inside and outside interfaces
- Applying default inspection rules to outside interface
- Enabling IP Unicast Reverse Path Forwarding (RPF) on the outside interface” (http://www.cisco.com/c/dam/en/us/td/docs/routers/access/cisco_ router_and_security_device_manager/application/notes/FPLCY-an.pdf)
Encrypt the sensitive traffic.
Set the correct time and date. This measure is necessary to ensure that the logs are correct and to be sure that the information included are accurate and is not altered by a lack of precision.
Enable proper logging. That means the router activities should be proper registered for statistical purposes, backup and recovery. To be able to do that, need to configure a buffered log on the router. But for security reasons it is better to be configurated a syslog server, where to be send all router logs.
Back up router configurations to a central source. Accidents or even criminal attacks are happening all time. That’s why backup is a very important part of process of hardening. The frequency of backups can be on daily basis or even weekly basis. In this sense, can be used a professional software, recommended by Cisco, named “Kiwi CatTools”.
Physically secure the routers. Can be considerate the first step on process of secure the network. Doesn’t matter how well secured is the router configuration if physically everybody can have access to device. That’s why it is imperious necessary to kept this kind of devices onto a locked room with a good system of ventilation.
Diagram, audit, and document the network
Switch Configuration security (Hardening) represent another important part into a process of secure the network. The switches represent targets for hackers, because anybody who gain access into a switch, gain access to the network. The process to make switches difficult to attack is named hardening.
Physical Security. One of the most difficult security task regarding switch security is maintaining physical security of the device, because these devices can be spread on different location of the company offices. The recommendation is to be keep all the switches together into a secure location.
Using the passwords to lock down the switch. These passwords must be applied at login mode to prevent the access and at privileged mode to prevent changes in configuration. These passwords should be encrypted.
Login mode passwords should be applied on Console, AUX, and VTY (telnet/SSH) interfaces. These passwords will control the remote access to the switch (VTY) and will looked the console and auxiliary ports.
Setup a username and password. Allow us to setup some credentials for the users with access to the switch.
Shutdown the unused interfaces. It is not reason to keep open the interfaces what are not in use. In this way, will be able to minimalize the area of manoeuvre for any potential attacker.
Apply switch-port security to the used ports, as: establish a Mac address which can be connected to a specific port; Violation Mode where to establish what is happening if an unknow device try to connect the network via a specific secure port; etc.
VLAN Management To create a well secured network for Magic Memories, should be implemented some common practice of security on VLANs. These are as follow: VLAN pruning, VLAN Trunk Negotiation and Port Security.
Port Security technique is limiting the MAC addresses that may be used on a specific port. Port security works on two different modes: static and dynamic. The firs mode is more secure but it is slower to be configured. The dynamic or sticky mode, is faster but can develop security issues, because of lack of control.
Maintaining network availability. Sometime, the legitimate users of the network are denied access to the network resources. This is happening when a specific type of attack has happened, named Denial of Service, which rely upon flooding devices with traffic until they are overwhelmed. Example of DoS attacks are: SYN Flood and MAC Flooding. To fight against those types of attacks, network devices often offer flood guard protection. These are designed to watch for these attacks and to limit their effects.
Another solution to fight with is to use Spanning Tree Protocol, which allow multiple physical connections between devices but restrict logical connections to remove the final links that would allow a loop between devices (switches)
Network monitoring it is an important aspect on process of secure the network. All the devices from network and the firewall produce logs which contains very useful information regarding security. At this logs, are registered useful information such as: details about the attempted connection; source and destination ports and IP Addresses; a timestamp indicating when the connection took place; and the identity of the firewall rule that either authorized or denied the connection. In this way, when start an investigation, can use the information from logs, to analyse security incidents, troubleshooting network issues or monitoring for suspicious activity.
Simply network management protocols (SNMP) provides network administrators with the means to centrally configure and monitor network devices. It is not useful on small networks as Magic Memories.
Storage Networks. For storage purposes, can be used a special type of networks name Storage Networks. Exist two types of this type of networks: NAS (Network Attached Storage) and SAN (Storage Area Networks)
A.3. – Network Design Elements and Components
DMZ | Addressing the network | Sub-netting the Network | VLANs and network segmentation | Network Access Control | Remote Access | Defence in Depth | Network Address Translation | Virtualization | Cloud Computing
DMZ – “In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization’s external-facing services to an untrusted network, usually a larger network such as the Internet.” https://en.wikipedia.org/wiki/DMZ_(computing). Because of the size and purpose of Magic Memories network, it is not necessary to use DMZ.
Addressing the network is the process to assign an IP address to the network. Exist two forms of addressing: public addresses, which are assigned by a central network authority, and may be used to reach systems located across the internet, and private addresses, which are available for anyone’s use, but may only be used on local networks, and will not work across the internet. For Magic Memories, will be use a private address: 192.168.1.0/24. Afterwards this IP address will be divided into small parts accordingly with the company needs, using two different methods: Subnetting and VLAN
Sub-netting the Network. The main reasons to divide a network in smaller parts, named subnets, is for manageability purposes. This process creates a series of advantages, even into a small network as Magic Memories company have. Another reason to use Subnetting is for Troubleshooting and Security matters. Basically, using this method, each subnetwork is connected to the router and all the traffic between subnetworks pass through that router. In this way, all the subnets are isolated and any eventually issue can be identified and fixed into a subnet, without disturbing the activity of hole company. On same way, it’s easy to secure subnets, because can apply different security rules on each of them, depend of the specific of the subnet. Also, if the security fail the effects can be isolated inside the subnet. This method is dealing with OSI Layer 3 and it is a physical way to divide a network.
VLANs (Virtual LANs) are an important network security control. It is a OSI Layer 2 method of dividing the network. It is a logical to divide a network. Use the switch technologies. With this method, can put together on same network users from different physical locations. It is secure because isolate the networks very well and users from a VLAN cannot communicate with another VLANs. All this is happening on Layer 2 and not involve firewalls or routers. To make this possible to work, should be enabled VLAN trunking to allow switches from different location to communicate and to configure each switch-port to connect an appropriate VLAN.
Network access control (NAC) is a technology used by the network administrators to restrict access to the authorised users to the resource that are not appropriate with their roles and attributions. NAC have an important role in network security because have the capability to intercept traffic from any devices connected (wired or wireless) to the network and verify them if have granted access to the network resources. The protocol used by NAC is called 802.1x and should be connected to an authentication server via a RADIUS connection. However, if a device fail to pass NAC, will be placed in a special quarantine VLAN, where it has limited internet access and no access to internal resources.
Remote Network Access. This aspect of network security it is referred to a technology used by Microsoft to gain remote access to a network, other than VPN. This technology is named Remote Desktops and provide administrators with graphical access to the desktop of the remote system. To grant this access, Microsoft provide Remote Desktop Protocol (RDP), which use full encryption for the entire connection. Must be configurated a Username and Password. Remote Desktop is a way to connect to servers located elsewhere.
Defence in depth is one of the core principles of information security, with a large applicability on network security. It is a layered approach of security and the principle which lead this security measure is to create a multiple, overlapping security controls to achieve the same control objective. As an example: how to secure against eavesdropping attacks? Using encryption through virtual private networks; encryption at the application layer; segmentation with VLANs. Another security objective can be Access Control. To create a defence in depth, should apply: Network access control (NAC), Role-appropriate VLANs, MAC Filtering and Port security. To protect perimeter is a very important aspect of network security and to protected in depth should implement: Routers with ACL, Strong Firewall roles and Intrusion Prevention System. In all cases if a security element fail remains other to protect the network.
A.4. – Common Protocols and Services
TCP/IP Protocols and the OSI Model | IP addresses | Domain Name Service (DNS) | Network Ports | ICMP
TCP/IP Protocols and the OSI Model. To make possible to create a functional computer network, it is in place a series of protocols. The basic one is called TCP/IP. In fact, are two protocols worked together to make up the modern networks. IP (Internet Protocol) is responsible to route information across networks, providing an addressing scheme and delivering packets from source to destination. TCP (Transmission Data Protocol) is responsible with Internet traffic. Another major transport layer protocol is UDP (User Data Protocol) and is used for voice and video application, where guaranteed delivery is not essential. All this protocols using a model named OSI (Open System Interconnection). OSI are composed by seven layers: Physical, Data Link, Network (IP seat), Transport (TCP and UDP seat), Session, Presentation and Application. A good understanding of OSI model is essential to deliver a well-secure network.
IP addresses. To be able to deliver traffic on the right place, need an addressing scheme. Because these addresses are used by Internet Protocol they are named IP Addresses. Today are in use two types of IP addresses: IPv4 and IPv6. The IPv4 it’s the most used, but because the numbers of users are grow very much in running out of addresses. IPv4 will be replaced by IPv6, which are considerable bigger address scheme. Magic Memories Company are using an IPv4 address in range of 192.168.1.0/24
Domain Name Service (DNS). This is a system created for people for a easy recognisable name instead on IP addresses. To be functional, this system use DNS Servers, where the domain names are translated into IP addresses. DNS is a Hierarchical System.
Network Ports. A system run many different services and application. The location on the system associated with an application is named Network Port. If the IP address conduct the traffic to a specific machine, the network port connects that traffic to a specific application from that device. E.g. Port 21 – FTP (File Transfer Protocol); Port 22 – SSH (Secure Shell); Port 53 – DNS (Domain Name System), Port 25 – SMTP (emails), Port 110 – POP, Port 80 – Web Server, Port 443 – Secure Webserver, etc.
ICMP. The Internet Control Message Protocol (ICMP) performs a variety of important administrative functions. The most used function is Ping Command. It is a troubleshooting method because establish if two devices communicate each other. The Traceroute is another function of ICMP, which identifies network paths. Other functions of ICMP are as follow: Destination unreachable, Redirects, Time exceeded, Addresses mask requests and replies. The ICMP plays a solid role in a network maintenance, being responsible with health and troubleshooting network connectivity issues.
Section B – Compliance and Operational Security
The second area of the rapport, will be referred at these aspects of the process of securing the computer network:
- designing security controls appropriate to Magic Memories business environment;
- mitigating the risks associated with third party relationships;
- responding to security incidents;
- building a security awareness training program;
- creating business continuity and disaster recovery plans;
- designing secure physical facilities.
B.1. – Risk Related Concepts
Security Controls | False Positives and False Negatives | Security policy frameworks | Security Policies | Risk Assessment | Quantitative Risk Assessments | Risk management
Security Control are mechanisms and procedures that companies put on place to manage security risks. To protect one objective can use multiple controls, named Défense in Depth. Controls can be categorised such as follow: after their purpose (preventive, detective and corrective); after the mechanism used to work; after the technology used; after the responsible business function, which implement them. All these controls can be grouped into three categories: Technical control, means the usage of technologies to achieve security objectives. Components of network infrastructure that’s performs security functions (e.g. firewalls, intrusion prevention systems and data loss prevention, software as anti-virus, encryption, etc.) are part of the technical controls. Management controls, are dealing with the mechanics of the risk management processes. As an example, is to made a regular risk assessment to identify vulnerabilities, threats, etc. Operational controls, are that processes putted on place to manage technology into a secure way. Example of these processes are: log monitoring, performing back-up checks, users access review, security trainings, etc.
False Positives and False Negatives concepts can explain the reasons why the controls fail. False positive errors, appears when a security issues is reported when is not present. Can be dangerous because reduce the administrator confidence in the system what report the alert, or even worst can influence the administrator trust on alert signals and ignore them. False negative errors, happen when a control don’t trigger a dangerous event and it should. This can give to the administrator a false sense of security.
Security policy frameworks. In line with good communication regarding security expectation and responsibilities of off staff, a clearly written guidanceshould in place.A set of rules and regulation must be implemented, easy accessible and understandable for everyone accessing it. That’s where the security policy framework comes in place and consist from four different types of documents: Security Policies, are the foundation for an organization’s information security program. Should be written for a long period and represent the company security expectation. Compliance with policies is mandatory. Usually the security policies are approved by the high management level. Security Standards, are in place to approve technical and operational details. They have mandatory status; can be approved by the department’s management. Security Guidelines, it’s the documents where the professionals give advice to the rest of company’s staff. Because they have advice status, compliance with it isn’t mandatory. Security Procedures, are step-by-step instruction. Follow the procedures, any employer should be able to perform a specific security task. Compliance with the procedures can be mandatory or optional, depends of the type of procedure.
Security Policy. Every organisation approaches security policies on different ways, depending of their activities, size, needs, etc. The policies may be simple or complex; long or short; but every policy should include several common elements. First one is regarding the security information included on policy. These should be as follow: Designation of individual responsible for security; Description of security roles and responsibilities; Authority for creation of security standards; Authority for incident response; Process for policy exceptions and violation.
The second mandatory element of any policy is a Published Privacy Policy. The Security policy should be published and everybody can have access to read it. The language used for written policy must be very clear and explicit. This is an essential requirement, so that everybody can understand it. On the same time, the policy must have included the legislation text, to protect the company.
The third policy should exist is an Acceptance Use Policy. Describes how individual may use information systems, prohibits illegal activities and describe what personal use is permitted. Should also explain how the company implements key principle of information security. Example of these principle are: Least privilege (assign users only the minimum set of permission necessary for their jobs); Separation of duties (prevents users from simultaneously holding two conflicting permissions); Mandatory vacation (force privileged users to take one or two weeks of consecutive vacation annually. In that way, fraud may show up when the user is unable to act to cover it up); Job Rotation (have similar purpose as mandatory vacation).
Risk Assessment. Risks are everywhere that’s why it is critical for security to understand and prioritise the risks. Risk assessment identify and prioritises the risks. Are three different processes to be considered in risk assessment: Threats (is an external force who jeopardise the security), Risks (occur when a vulnerability can be exploited by a threat.) and Vulnerability (is a security weaknesses). Prioritize risks by likelihood and impact. Likelihood is the probability that a risk will occur. Impact is amount of expected damage. A Risk Assessment can be done following two techniques: Qualitative risk Assessment (uses subjective ratings to evaluate risk likelihood and impact) and Quantitative Risk Assessment (uses objective numeric ratings to evaluate risk likelihood and impact).
Quantitative Risk Assessments is the process of using numeric data to assist a risk decision. To analyse the risk, the analyser should give a value to the risk variables. The first of these variable is the Asset Value (AV). Techniques foe AV: Original Cost, Depreciated Cost, Replacement Cost. The second variable should be considered is the Exposure Factor (EF). this is the value of expected percentage of damage to an asset. The third variable is Single-Loss expectancy (SLE)and is expected loos if a risk occurs one time. The formula to calculate the risk is AV*EF=SLE
Risk Management, is the process of systematically analysing potential responses to each risk and implementing strategies to control those risks appropriately. Risk Management Strategies: Risk Avoidance, Risk Transference, Risk Mitigation, Risk Acceptance, Risk Deterrence.
Risk Avoidance, changes the organisation’s business practices
Risk Transference, shifts the impact of a risk to another organisation
Risk Mitigation, reduces the likelihood or impact of the risk
Risk Acceptance, accepts the risk without taking further action
Risk Deterrence, takes actions that dissuade a threat from exploiting a vulnerability
B.2. – Integrating Systems and Data with Third Parties
Managing vendor relationships | Vendor agreements | Vendor information management | Social network security
Managing vendor relationships. Vendors have an important role in every company, because they provide the hardware and software used. The relations with vendors should by very carefully manage, protected like that the confidentiality, integrity and availability of the company. The security administrators should ensure that vendors security policies are at least as stringent as the company are. The life cycle of vendors’ relationship is as follow: Vendor selection, onboarding, monitoring, offboarding.
Vendor agreements. The first step on the process to evaluate a new vendor is to require a Service-level Requirements (SLR), This will document specific requirements that a customer has about any aspect of a vendor’s service performance. The SLR should be documented in a Service-Level Agreement (SLA). Other Agreements Types: Memorandum of understanding (MOU); Business partnership agreement (BPA); Interconnection security agreement (ISA). Security and compliance are key issues during the negotiation of agreements with vendors. Security and Compliance Terms: Document security and compliance requirements; Facilitate customer monitoring of compliance; ensure the right of audit and assessment.
Vendor information management. The services offered by the vendors are increase in volume and importance. That’s why the agreements between parts should contain clear data ownership language. Data ownership provision: customer retains uninhibited data ownership; vendor’s right to use information is limited to activities performed on behalf of the customer; vendor’s right to use information is limited to activities performed with the customer’s knowledge; vendor must delete information at the end of the contract.
Social network security. Today, the social networks are part of everybody’s day by day routine. The companies start to use social networks to advertise jobs, to recruit new staff or to promote the business. That’s why is important to secure the social network accounts. One of the most common attack against social network accounts is hijack. To prevent account Hijacking should use multifactor authentication.
B.3. – Risk Mitigation Strategies
Change Management | Audits and assessments | Data Loss Prevention (DLP)
Change Management. Changes are happening constant, especially on IT environment. Changes are usually good and means progress. But all the changes should be controlled. Change Management ensure that an organisation follow a standard process for requesting, reviewing, approving and implementing changes to information systems. Request for change (RFC) is the standard tool for change management. RFC deal with: description of the change, expected impact, risk assessment, rollback plan, identity of those involved, proposed schedule and affected configuration items. Changes must be approved before implementation. Baselines is an important aspect of change management, providing a configuration snapshot. Versioningis another important part on change management, because can assign numbers to each version of software.
Audits and assessments. Given the opportunity to the company to evaluate the security controls implemented. They are similar and proceed these actions: evaluate security controls; report on their effectiveness; recommend improvements. The main difference between them is that assessment is usually requested internally while audits are often imposed by external requirements. Audits follow a formal standard and use planned tests. Audits may be performed by two different types of entities: Internal Auditors (work for the company but report independently, usually performing audits at the request of organisation leadership) and External Auditors (are independent firms that normally perform audits at the request of a board of directors or regulators). Audits should have clearly defined scopes.
Data Loss Prevention (DLP). Provide technology solutions that search systems and monitor networks for sensitive information that is unsecured and provide the ability to remove the information, block the transmission or encrypt the stored data. DLP solutions work in two different environments: Host-Based DLP (uses software agents installed on a single system) and Network-Based DLP (Scans networks transmissions for sensitive information). DLP systems have two different ways to action: Pattern Matching (recognises known patterns of sensitive information, such as SSNs) and Watermarking (identifies sensitive information using electronic tags)
B.4. – Basic Forensic Procedures
Computer forensic | System and file forensics | Network forensics | Chain of custody
Computer forensic or Digital Forensic it a field where the security professionals are asked to evaluate electronic evidence. Digital forensic use investigative techniques that collect, preserve, analyse and interpret digital evidence. One of the most important principle is: investigations must never alter evidence. Volatility is an important issue when dealing with digital evidence and must take into consideration these principles: the relative permanence of a piece of evidence; evidence that may not last long is more volatile than more permanent sources of evidence. Order of Volatility: Network traffic; Memory contents; System and process data; Files; Logs. Time offsets help correlate records from different sources. Always should consider to alternate evidence sources, such as: video recordings or witness statements.
System and file forensics. When working with systems and files should never work with the evidence. Images take the place of original physical media. Hashes protect evidence. They provide a unique file signature. Use hashes to demonstrate that a file hasn’t been altered. Other forensic sources: Screenshots, Memory contents, process table, operating system configuration.
Network forensics. Network communications may be intercepted. To monitor suspicious traffic should be use a protocol analyser. One of the best is Wireshark and have capability to monitories the network, capturing full packet data. To stock full data, Wireshark need a lot of space. NetFlow can solve this issue offering almost same facilities as Wireshark. Routers and firewalls capture NetFlow data.
Chain of custody. Plays an important role because ensure the authenticity of evidence. Chain of custody provides a paper trail for evidence. Evidence should be labelled and stored in a sealed evidence container. Evidence log event: Initial collection, Transfer, Storage, Opening and resealing the container. Evidence log entry details: investigator name, date and time, purpose and nature of action.
B.5. – Incident Response Procedures
Building an incident response program | Incident identification | Escalation and notification | Incident mitigation | Recovery and reconstruction | Lessons learned and reporting
Building an incident response program. A security issues can occur anytime, doesn’t matter how well the security was implemented. That’s why is necessary to be on place a security incident response program. An IR Program should include these components: Policy and plan documentation; Procedures for incident handling; Guidelines for communicating externally; Structure and staffing model for the team; Description of relationship with other groups.
Incident response policy: Provide foundational authority for the program; Defines incidents that fall under the policy; include an incident prioritisation scheme.
Incident response procedures contain the details of the IR plan, such as: Notification, Escalation, Reporting, System isolation, Forensic analysis, Evidence handling.
Communications guidelines provide clear guidance on when and how to involve groups, such as: Seniors executives, Legal counsel, public relations, Regulatory agencies, Law enforcement.
Building an IR Team: should have representative from all the departments as follow: Management, Information security, Subject matter experts, Legal counsel, Public affair, Human resources, Physical security.
Incident identification. Monitoring is crucial to effective incident identification. Incident Data Sources: IDS and IPS, Firewalls, Authentication systems, Integrity monitors, Vulnerability scanners, System event logs, NetFlow records, Anti-malware packages. Security Incident and Event management (SIEM) represent a security solution that collects information from diverse sources, analyses it for signs of security incidents and retains it for later use. The first reports of an incident may come from external sources. First responder must act quickly to isolate affected systems.
Escalation and Notification. The Objective of Escalation and Notification Process: Evaluate incident severity based upon impact; Escalate response to an appropriate level; Notify management and other stakeholders. Triaging Incidents: Low impact, Moderate Impact and High Impact. Low Impact Incidents: have minimal potential to affect security; are normally handled by first respondent; Don’t require after-hours response. Moderate Impact Incidents: Have significant potential to affect security; Trigger incident response team activation; Require prompt notification to management. High Impact Incidents: May cause critical damage to information or systems; Justify an immediate, full response; Require immediate notification to senior management; Demand full mobilisation of incident response team. Essential is that first responder must have the ability to quickly activate a full incident response team.
Incident mitigation. The goal is to control damage and loss to the organisation through containment. Containment Strategy Evaluation criteria: Damage potential; Evidence preservation; Service availability; Resource requirements; Expected effectiveness; Solution timeframe. The company should use that criteria to select a containment strategy to balance business needs and security objectives. Mitigation Ends should offer stability and business activities should be functioning without danger.
Recovery and reconstruction. The goal of this phase is to remove effects of the incident and return to normal operations. Technical Recovery Effort: Rebuild compromised systems; Remove malware; Disable breached accounts; Restore corrupted or deleted data. Generally, reconstruction corrects vulnerabilities. Remediation Efforts include: Applying security patches; Updating firewall rules; Implementing intrusion prevention; Strengthening access controls. The responder should use a phased approach to recovery and reconstruction.
Lessons learned and Reporting. Lessons learned process provide incident responders with an opportunity to reflect on the incident response efforts and offer feedback hat will improve the organisation’s response to future incidents. For that should use a trained facilitator. Another essential aspect should be considered in time. As time passes, details quickly become fuzzy and memories are lost. Lessons Learned Questions: How well did staff and management perform? or Where documented procures followed? or Where those procedures adequate? or Did any actions inhibit the recovery effort? To answer to these questions should create a report that includes lessons learned and recommendations.
B.6. – Security-Related Awareness and Training
Security education | Information classification | Compliance training | User habits | User-based threats | Measuring security education
Security education. Security is strongly connected with the user’s behaviour. That’s why the security trainings are essentials. The process of educate people involve two aspects: Security training (provide users with the knowledge they need to protect the organisation’s security) and Security Awareness (keep the lessons learned during security training to top of mind for employees). Security training methods: Instruction in on-site classes; Integration with orientations; Education through online providers; Participation in vendor-provider classroom training. The company should customise training based upon user roles. The Training Frequency is essential and should be provided such as: Initial training for new employees; Update training foe employees with new roles; Refresh training on an annual basis; Awareness efforts throughout the year.
Information classification. Data Classification Policies assign information into categories, known as classifications, that determine storage, handling and access requirements. Classifications are assigned based upon sensitivity of information and criticality of information. Classification guides other security decisions. Labelling Requirements identify sensitive information. Finally, should securely dispose of information when no longer needed.
Compliance training. Compliance programs ensure that an organisation’s information security controls are consistent with the law, regulation and standards that govern the organisation’s activities. A security training should include compliance obligations. Compliance Obligations: Law, Regulation and Standards.
User habits. Security training programs should include topics regardless user’s habits. Some of these topics are such follow: Password security education programs; Clean desk policies and other data handling practices; physical security training should include discussions of the danger of tailgating; BOYD policies; cover appropriate use of social media and peer-to-peer networks.
User-based threats. Security training programs should include topics regardless User-based threats. Example of user-based threats are: Phishing uses messages to obtain information and convince user to perform risky action; Social engineering isn’t limited to email. It can occur over the phone or in person as well. Users should be aware that new threats arise every day.
Measuring security education. It is important for every company to measure security awareness of their staff. To do that, should simulate an attack and observe the staff reaction. Other way is to take a survey named Security Awareness Survey and ask questions like: How well does the organisation prepare you to deal with security threats? or Do you know your information security responsibilities? or Do you know where to report a security incident? These surveys help to measure how awareness changes over time.
B.7. – Physical Security and Environmental Controls
Environmental controls | Environmental protection | Physical security control types | Physical perimeter security
Environmental controls. One of the major risk in every network is the unappropriated use of electronic devices. The electronic equipment generates heat that’s why it is necessary to provide cooling system. The humidity is another factor should be considered. A high humidity leads to condensation that may damage electronic equipment. A low humidity leads to static electricity that may damage electronic equipment. Heating, Ventilation and Air Conditioning (HVAC) keep temperature under control.
Environmental protection. More dangerous situation can occur and put in danger the network devices, such a fire, flooding and electromagnetic interference. Fire is a grave threat in network environment. On the environment of electronic devices, to fight with fire using water in not recommended. The company should have in place Fire Extinguishers. To prevent and protect against flooding, should not place the equipment near the water pipes or a water sources. Electromagnetic interference (EMI) is generated by all electronic equipment. EMI interferes with normal operation of other equipment and enables eavesdropping attacks. EMI issues should be closely monitored.
Physical security control types. A category of physical security control is Intended Effect Categories and include: Deterrent Controls (are intended to prevent an intruder from trying to access a secure area), Preventive Controls (are intended to block an intruder from accessing a secure area) and Detective Controls (are intended to alert security personnel to a potential or actual security violation). Another physical security control is Mechanism of Action Categories and include: Technical Controls (use technology to deter, prevent or detect security violation) and Administrative Controls (rely upon business processes to enhance physical security). Other set of controls used for physical security are Compensating Controls, which fill known gaps in security.
Physical perimeter security. For a good physical security practice, should secure the perimeter where the devices are. First concept is: Locks restrict physical access. The looks can be: doors, lockers, key. The key can be: a classical key, an electronic, biometric, cipher, etc. Another way to secure perimeters are: video surveillance, a separate room, fences, etc.
B.8. – Risk Management Best Practices
Business continuity planning | Business continuity controls | High availability and fault tolerance | Disaster recovery | Backups | Testing Backups/DR plans
Business continuity planning represent a set of controls designed to keep business running in the face of adversity, whether natural or man-made. The objectives of business continuity plan are: confidentiality, integrity and availability. Defining BCP Scope: Business activities, systems used, controls used. BCP use a risk assessment name BIA (Business Impact Assessment) which identifies and prioritises risks.
Business continuity controls. The security administrator should ensure the network functionality and availability. The most important tool use to achieve that is redundancy, that protects against the failure of a single component. Single Point of Failure Analysis identifies and remove SPOFs (Single Point of Failure). SPOF analysis can continue until the cost of addressing risk outweighs the benefit. IT Contingency Planning is another aspect should be considered. Example of IT Contingency: Sudden bankruptcy of a key vendor; Insufficient storage or compute capacity; Failure of utility service. Perform a succession planning for staff is an important control.
High availability and fault tolerance. It is two technical concepts that improve the availability to the systems: High Availability (HA – uses multiple systems to protect against service failure) and Fault Tolerance (FT – makes a single system resilient against technical failures). Load Balancing is a different concept that spread demand across systems providing a scalable computing environment. Common point of failure: Power supply and Storage media. Power Supplies: Contain moving parts; have high-failure rates; can be redundant; May use different power sources. Storage Media. To achieve the protection against failure of a single device, it is used a technology named RAID (Redundant Arrays of Inexpensive Disks), which come in many forms. Two of them are more often used: RAID 1 (disk mirroring, stores the same data on two different disks) and RAID 5 (disk striping with parity, uses three or more disks to store data and parity information). RAID is a fault tolerance technique, not a backup strategy.
Disaster recovery. Sometime the security controls fail. That’s why is necessary to implement a Disaster Recovery strategy. Disaster recovery capabilities are designed to restore a business to normal operations as quickly as possible. Disaster recovery is a subset of business continuity. The Initial Response evaluate the damage caused by the disaster; recover whatever capabilities may be immediately restored; include a variety of activities depending upon the nature of the disaster. During the Disaster Recovery, employee responsibilities will be changed dramatically. Disaster Communications include initial activation of the disaster recovery team; regular status updates; tactical communications. After the danger passes, the team shifts to assessment mode. It is two tools which help companies to plan Disaster Recovery: Recovery Time Objective (RTO – maximum amount of time that it should take to recover a service after disaster) and Recovery Point Objective (RPO – Maximum period of time from which data may be lost in the wake of disaster). After developing a plan, responders restore services in an orderly fashion.
Backups. Are the most important part of any Disaster Recovery plan because modern businesses depend upon data. Backups provide a data “safety net”. Backup Media: tape backups, disk-to-disk backups, cloud backups. Are three primary backup types: Full Backups (include a complete copy of all data); Differential Backups (Include all data modified since the last full backup); Incremental Backups (include all data modified since the last full or incremental backup). Any organisation needs plan for Media Rotation Strategies which allow reuse of backup media. Most restoration requests are for recent backups. The most common backup rotation strategy is named “Grandfather-Father-Son Rotation (GFS)”.
Testing Backups/DR plans. Disaster Recovery (DR) Testing Goals: validate that the plan functions correctly and identify necessary plan updates. DR Test Types: Read-through (ask each team member to review their role in the disaster recovery process and provide feedback), Walk-through (gather the team together for a formal review of the disaster recovery plan), Simulation (use a practice scenario to test the disaster recovery plan), Parallel test (activate the disaster recovery facility but do not switch operations there), Full interruption test (switch primary operations to alternate facility and can be very disruptive to business). DR testing strategies often combine multiple types of tests.
B.9. – Security Goals
Confidentiality Controls | Integrity Controls | Availability Controls | Safety Controls
Confidentiality Controls. Access controls restricts users from accessing sensitive information without permission. Access controls protect confidentiality e.g. NTFS permission. Encryption protects information at rest or in transit, offering confidentiality. Steganography helps with confidentiality because hide information within images or other files.
Integrity Controls ensure that information is not altered without authorization. Sources of Integrity Failures: Intentional alteration, User error, Software or hardware error, Acts of nature. One of the most important control use to protect integrity is Hashing. Hash function create message digests from large files. These are unique ID for that file. Changes in hash values indicate changes in the underlying file. Based on hashes many integrity controls were developed. One of them is Digital Signature, which enforce Non-Repudiation (security goal that ensure the author of a piece of content cannot later claim that he or she did not create the message and that it is a forgery).
Availability Controls ensure that information and systems remain available to authorized users when needed. Availability Failure Causes: Malicious attackers, Component failures, Application Failures, Utility Failures. Are many Availability controls on place, such as follow: Redundant Components (protects a system against failure of a single part); High Availability (protects services against the failure of a single server); Fault Tolerance (protect services against disruption from a small failure). Operating System and Application patching also enhances availability.
Safety Controls protect the safety of individuals in the organization. Life safety must always be the first priority of any security program. Usually the physical controls are applied as safety controls. E.g. fences, lighting, video surveillance, lookers, doors, key, etc. The evacuation is a safety control, because should follow a predefined plan to escape and should follow a safe escape routes. Emergency drills remind employees of evacuation procedures including assembly points.
Section C – Threats and Vulnerabilities
C.1. – Malware Types
Malware Overview | Viruses and Worms | Trojans Horses | Adware, Spyware and Ransomware | Backdoors | Logic Bombs | Rootkits | Polymorphic Malware | Armored Virus | Botnets
Malware Overview. Malware means malicious software. To be able to protect a system against malware should understand how they are acting. Any type of malware has two components: a propagation mechanism (the way that a malware object spreads) and a payload (the malicious action that the malware performs). Any malware carry a type of payload.
Viruses and Worms. Viruses are a type of malware that are spreading from system to system by human actions. The most common form to protect against viruses is user education. Worms are a type of malware that are spreading without any help. Exploit systems vulnerabilities. That’s why the best way to protect against worms in to keep the systems updated.
Trojans horses are a type of malware. They disguise himself as beneficial programs; also, act as advertised when they are run, but in fact deliver their malicious payload behind the scenes. Application control provide a good defence in front of this threat.
Adware, Spyware and Ransomware are three different types of malware payloads. Adware is a way to display advertisements, generated revenues for malware author. Adware mechanisms: changing the default search engine; displaying pop-up advertisements; replacing legitimate ads with other ads. Spyware it’s another type of payload which gathers information without user consent. Spyware techniques: Logging keystrokes; monitoring web browsing; searching hard drives and cloud storage. Ransomware it is a type of payloads malware. It is acting by blocking access of the legitimate user to the system until a ransom is paid. This is possible by encrypted files with a secret key and then selling the key to a ransom.
Backdoors occurs when a software developer insert a piece of code into a program to gain future access, without using user credentials. Backdoors mechanisms: sometime they’re hardcoded accounts; sometime they’re default passwords, forgotten by users to be changed; sometimes the can be unknow access channels to gain access to the system.
Logic Bombs is a malware setup to execute a malicious action when certain conditions are met, such as: a date and time, file content, API call result.
Advanced malware are more sophisticated types of malware, as: Rootkits, Polymorphic Malware and Armored Viruses.
Rootkits. The root account is a special super-user account that provides unrestricted access to system resources, usually an administrator account. Rootkits escalate user privileges to the super-user account. Rootkits deliver a variety of payloads: backdoors, botnet agents, adware, spyware. Rootkits can run as: User Mode Rootkits (run with normal user privileges, being easy to write and difficult to detect); or as a Kernel Mode Rootkits (Run with system privileges, being difficult to write and easy to detect)
Polymorphic Viruses are dangerous malware because can fight with signature detection techniques provided by anti-malware software vendors, by changed themselves constantly. Another technique used by polymorphic viruses is to encrypt themselves using a different key on each infected system.
Armored Viruses can prevent reverse engineering by using these techniques: writing the virus in obfuscated assembly language; blocking the use of system debuggers; preventing the use of sandboxing.
Botnets are a collection of zombie computers used for malicious purposes. They are a network of infected machines that target a healthy computer. Once this machine is infected it is added to the botnet. The hackers use botnets as follow: renting out computing power; delivering spam; engaging in DDoS attacks; mining Bitcoin; wagging brute force attacks.
C.2. – Attack Types
Denial of Service Attacks | Eavesdropping Attacks | Man-in-the-Middle Attacks | Replay Attacks | Spoofing | Spam | Phishing | Vishing | Christmas Tree Attack | DNS and ARP poisoning | URL Hijacking (Typosquatting) | Password Attacks | Watering Hole Attack | Privilege Escalation |
Denial of Service Attacks disrupt the normal use of a computer resources. DoS attacks make a resource unavailable for legitimate use, send a huge number of requests to a server, is difficult to distinguish from legitimate requests. Limitations of a Dos Attack: require a massive amount of bandwidth and is easy to block based on IP address. That’s why was invented Distributed Denial of Service (DDoS) which is a denial of service attack that leverages a botnet to overwhelm a target. A special type of DDoS attack is a Smurf Attack which developed the capability to amplify the attack.
Eavesdropping Attacks rely on a compromised communications path as: network device tapping; DNS poisoning; ARP poisoning. These attacks are dangerous because can decrypt encrypted communications. The most common types of eavesdropping attacks are: Man-in the-Middle Attacks and Replay Attacks.
Man-in the-Middle Attacks “is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other” https://en.wikipedia.org/wiki/Man-in-the-middle_attack
Replay Attacks “is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed” https://en.wikipedia.org/wiki/ Replay _attack
Network Attacks are those attacks that are dealing with packets, and include: Christmas Tree Attack, DNS and ARP poisoning, and Typosquatting.
Christmas Tree Attack use Christmas Tree Packet which is a packet with every single option set for whatever protocol is in use. Some systems can’t handle with all options being set.
DNS and ARP poisoning. DNS poisoning disrupt the normal way to work of a DNS by providing false results. The ARP (Address Resolution Protocol), performs a function like DNS, but deeper down in the network stack. ARP Poisoning only works on a local network and it is a spoofing technique.
URL Hijacking (Typosquatting). This attack is based on users typing mistakes. Attackers registered hundreds of typos variation on official sites and a mistake is made the users is directed to a false website.
Password attacks. Because password secure access to the resources, the attacks against passwords are very frequent. Usually the attackers try to gain access to the of the passwords Hash. To protect the passwords the very first measure is to move the hash into a new location. Hash Function is a mathematical function that converts a variable-length input into a fixed-length output and must meet some criteria: It must produce a completely different output for each input; it must be computationally difficult to retrieve the input from the output; it must be computationally difficult to find two different inputs that generate the same output. It is four type of password attacks: Brute Force Attacks (try all possibilities); Dictionary Attacks (Try words from dictionary, e.g. English first); Hybrid Attacks (add variation to try, e.g. replacing letter I with number 1); Rainbow Table Attacks (use pre-computers hashes).
Watering Hole Attack are recent developed by hackers. Basically, it is use something who is likely to attract many users, as a website, because websites spread malware effectively.
Preventing insider threats. Statistically the most dangerous attacks are from inside the networks and are made it by trusted users. Best practice to control insider threat are: perform background checks to uncover past legal issues; give users only the permissions that they need; require multiple users to carry out sensitive operations; implement mandatory vacations for critical staff.
Privilege Escalation Attacks are a form of insider attack. Transform a normal user credentials in a powerful super-user credentials, gaining access to every level of information.
C.3. – Social Engineering Attacks
Social Engineering | Impersonation Attacks | Physical social engineering | Shoulder Surfing | Dumpster Diving | Tailgating |
Social Engineering. Most of the threats come from the human parts of social engineering, using psychological tricks to manipulate the victims. Are six main reason for successfully social engineering: Authority (people defer to authority), Intimidation (scaring people), Consensus (the herd mentality), Scarcity (“getting the last one” principle), Urgency (Time is running out) and Familiarity (people say yes to persons they like). To prevent social engineering the best practice is educated people.
Impersonation Attacks. Spams can be used to perform a social engineering attack. Phishing is a sub-category of spam. The main function of Phishing is staling credentials. Spear phishing attack is very targeted attack and have a high rate of success. Whaling is targeted attack on executives. Pharming attacks use a fake website for stealing credentials. Vishing is a voice phishing. Spim or spam via IM attacks are instant messaging to send spam or phishing. Spoofing faking identity for sent a fake message.
Physical Social Engineering Attacks are often use by attackers. Will be analysed three types of physical attacks: Shoulder surfing, dumpster diving, and tailgating
Shoulder surfing, is very simple attack and imply only to looks over the victim’s shoulders
Dumpster diving, represent the action when an attacker searching on trash looking for sensitive information may be on the binned documents.
Tailgating attacks are based on human curtesy to keep open a door when somebody is behind you. In this way the attacker can gain access to building, offices, etc.
C.4. – Wireless Attack Types
Wireless eavesdropping | WPA and WPS attacks | Propagation Attacks | Preventing rogues and evil twins | Bluetooth and NFC attacks
Wireless eavesdropping. Wireless networks are very unsecure. Wireless networking is governed by the IEEE 802.11 standard. Every WI-FI network uses plaintext service Set Identifiers (SSIDs) to be named. The WI-FI uses “beaconing” to advertise to other devices. Wireless Encryption protects confidentiality of communication, prevents eavesdropping, allows use of insecure transmission methods.
WI-FI Encryption Option: no encryption – not recommended because leave the network vulnerable; WEP (Wired Equivalent Privacy) – uses a static key and is very weak; WPA (Wi-Fi Protected Access) uses the TKIP (Temporal Key Integrity Protocol); WPA2 (Wi-Fi Protected Access v 2) uses AES (Advanced Encryption Standards) via CCMP
WPA and WPS attacks. The WPA have these attributes: fixes the problems inherent in WEP; use RC4 with 128-bit key, but adds TKIP, which changes its key constantly, with a new key for each packet. But even like that, WPA is not very secure because known attacks allow injection of packets and some limited decryption. These attacks work against the principles of TKIP. It’s more secure to use instead WPA2. Another security issue is using WPS (Wi-Fi Protected Setup) technology when connect a new device to a wireless network. This connection can be made by pressing a button on same time on both devices or to use a WPS 8-digits PIN. The attackers can discover that PIN relatively easy, and once is discovered they can have gain access to the network resources. Usually this technology is not used for business environments, but if exist should be disabled.
Propagation Attacks. Wireless networks are very expose to the attack because their open nature. Based on radio wave propagation, the attacks can be such as follow: Jamming and Interference attacks are possible because denial of service attacks are easy on wireless; the radio spectrum is open, but in a limited amount and the loudest signal always win, so it doesn’t take much to interfere with another signal.
Preventing rogues and evil twins When an unauthorised wireless access point it is connected to an enterprise network, in created a rouge access points. The risk is huge because they can bypass all the authentication mechanisms as WPA2. The most efficient way to fight to rouge access point is to use these technologies: the enterprise-grade wireless has built-in intrusion detection capabilities; unknown radios on the network can be identified; handheld tools can also help pinpoint them. The attacks Evil twins are very similar with phishing and farming attacks. The way to operate is quite simple, a criminal set up a fake access point with SSID of a real network and wait for users to be connected. Then can have access to their data. He company should have on place a system of detection of rouge access point and evil twins
Bluetooth and NFC attacks Very dangerous for company network can be the attacks against the mobile devices and in that way to gain access to the network resources. These types of attacks can be possible via NFC (Near Field Communication). The most common NFC is Bluetooth technology. Bluejacking occur then an attacker sends Bluetooth spam to a user’s device. Bluesnarfing means an attacker exploit firmware flaw in older Bluetooth devices. NFC Security: turn off discoverable mode; apply firmware updates; watch for suspicious activity.
C.5. – Application Attack Types
Cross-site Scripting | Cookies and attachments | Hijacking | Malicious Add-ons
Cross-site Scripting is commonly abbreviated XSS and occur when an attacker trick a user’s browser into downloading a script from one site and executing it on another site. If user is logged into the second site, the command may succeed.
Cookies and attachments Cookies are data stored by websites in user browsers, for recognise the user and remember information. The risks of cookies are: cookies can be used across different websites; cookies can track user activity; once the user log into a site, everything is de-anonymized.
Hijacking is “a form of active wiretapping in which the attacker seizes control of a previously established communication association” https://en.wikipedia.org/wiki/ Hijacking
Malicious Add-ons. The add-ons are also known as extensions. They add new functionality to browsers and other software. Are written by third-party developers. Security risks with Add-ons: might not know who wrote the code; Trojans may perform malicious secondary actions; permissions may be overly broad.
C.6. – Mitigation and Deterrent Techniques
Monitoring System Logs | Operating System Hardening | Physical Port Security | Security Posture | Reporting | Detection vs. Prevention
Monitoring System Logs. One of the most important action what a security administrator can take is Log Monitoring. The logs contain critical information that’s allow the administrators to determine breaches and penetrations on the system. To monitor the logs, should use a tool named Event Viewer. The firewall log can be view on Windows Firewall with Advanced Security, then click on Windows Firewall Properties.
Operating System Hardening means all the activities and actions taken by a system administrator in attempt to reduce the vulnerability of a server to attackers. Generally, the servers are easy targets for attacker because are designed to accept a multitude of connections from knows and unknows sources. Are three techniques in process of hardening the servers:
Disabling unused services. Hundreds of services are running on a typical system. Each one is a potential attack point. Can reduce the “attack surface” by disabling unnecessary services;
Protecting management interfaces Many application have management interfaces. For Windows is RDP (Remote Desktop Protocol). Access can be locked down using firewall rules.
Disabling unused accounts. It’s a good practice to keep the system and application account to a minimum. To do that should conduct regular account reviews. Before delete an account should disable first that account.
Physical port security restrict access by device. On this purpose, can use MAC Filtering, to configure a list of authorised MACs. Filtering is a high-maintenance activity. Can be configurated on wireless devices or switches. Using “Sticky” MAC Address method can reduce the effort to assign manually the MAC addresses to the ports. 802.1x Authentication is another method to secure a port. Use Username, Passwords and Certificates. Can be used on wired and wireless networks. Another good practice used for secure the network is: disable unused ports at the switch; Disable unused network interfaces on systems and network devices; use rouge machines detection features;
Security posture.Security controls are efficient just with a proper and precise using. To do that should setup a Baseline Security Configuration. In this way, should be sure that a consistent control across all the network’s systems is implemented. When the network’s systems are build, a good practice is to follow the industry’s experts advises.
Because security tools generate a huge quantity of data, a company should adopt a Continuous Security Monitoring Approach, which should include: firewalls, intrusion detection and prevention systems, data loss prevention systems, anti-malware technology, and vulnerability scanners.
Security Controls Categories. In the attempt to secure a network, a secure administrator use a set of controls to help fight against attacks. These controls are grouped as follow: Preventive, Detective and Corrective. Preventive Controls works before an incident. (e.g. firewalls, intrusion prevention systems, access control system, antivirus software, data loss prevention and physical security). Detective Controls identify an incident (e.g. intrusion detection systems, log monitoring, video monitoring, burglar alarms). Corrective Controls restore the systems to normal activities (e.g. disaster recovery, redundant servers, fault tolerant networks)
C.7. – Discovering Security Threats and Vulnerabilities
Security assessment tools | Scanning for vulnerabilities | assessing threats | Threat assessment techniques | Penetration Testing | Advance vulnerability scanning
Security assessment tools. A variety set of tools can be used to fight against informational attacks. These tools come in two forms: Passive tools (observe activities) and Active tools (interact with the machines). Example of security tools: Honeypots (attractive decoy machines); Honeynets (decoy networks), Protocol Analysers (peek into network traffic e.g. Wireshark).
Scanning for vulnerabilities.Scanners are used to discover vulnerabilities. As a security administrator, it is better to perform the scan regularly, to discover weakness before the hackers do. Are three types of scanners: Port Scanners, Vulnerability Scanners and Application Scanners. Port scanners scanning ports is looking for unlocked “doors” of the systems. Scanners probe systems for open networks ports. One of the most popular scanners in Nmap. Vulnerabilities scanners test open ports for active vulnerabilities. They also provide important information for remediation and a roadmap for exploitation. One popular scanner is Nessus. Application scanners identify potential danger in applications.
Assessing threats. Involve three different concepts strongly interconnected: Threats, Vulnerability and Risk. Threats it is an external force who jeopardise the security. Vulnerability is a security weaknesses. Risk occur when a vulnerability can be exploited by a threat.
Threat assessment techniques. To conduct a good assessment review should follow these procedures: Baseline reporting, an attack surface review, code reviews, and architecture reviews. Baseline Reporting provide an initial review of a system’s security status. Compares the current configuration to the expected baseline configuration. Can be automated with tools. Attack surface review enumerates the “attack surface”, all possible paths of attack. Make heavy use of port, vulnerability and application scanners. Adopt the mindset of an attacker. Code review performs assessments of software security. Include peer code review for an extra set of eyes to detect security issues. Should be a mandatory part of promotion and release process for new code. Architecture Review dissects how everything fits together. Analyse the interaction of various systems.
Penetration Testing. Tester attack systems and networks. They verify that exist and exploit known vulnerabilities. They also test security controls by attempting to bypass/defeat them. Are three type of penetration tests: White Box (attackers have full knowledge of the network environment). Black Box (attackers have no knowledge of the network environment) and Grey Box (attackers have some knowledge of the network environment).
Advance vulnerability scanning. Are two types of vulnerabilities scanners: Non-Intrusive (a “safe” mode that won’t disrupt system operation) and Intrusive (a “dangerous” mode that might disrupt system operation). When a vulnerabilities scanner run might occur two types of errors: False Positive (when a scanner reports a vulnerability that doesn’t exist) and False Negative (when a scanner fails to report a vulnerability)
Section D – Application, Data, and Host Security
D.1. – Application Security
Application Security | SQL injection prevention | Cross-site scripting (XSS) prevention | Cross-site request forgery (CSRF or XSRF) | Error and exception handling | Fuzz Testing | No SQL database
Nowadays, the implication of software application in all aspect of day by day life, including here the business activities, it is bigger and bigger. That’s why securing the application should be a must for any individual or company. This process can be very challenging and include some important aspects, such as follow:
- SQL injection prevention
- Cross-site scripting (XSS) prevention
- Cross-site request forgery (CSRF or XSRF)
- Error and exception handling
- Fuzz Testing
- No SQL database
From Magic Memories perspective, all these aspects of security are very important and critical, because the company will develop a commercial website. For a better security reason, the chosen way for hosting the company’s website was a Cloud solution. Prior this, all the security aspect regarding the web activity will be secured by the administrators of the Cloud Webserver.
On the same way, the design of the website will be realised by a professional web designer. All the security aspects regarding the website, such as HTML code, SQL, etc., will be on his duty to be accomplished.
D.2. – Mobile Security
Mobile device security | Mobile device management (MDM) | Mobile device tracking | Mobile application security | Bring your own device (BYOD)
Regarding Mobile security aspects, this rapport will be focused on BYOD (Bring your own device) because the company’s network have a wireless component and use this principle, because the company are not provided any wireless devices, as laptops or tablets.
Bring your own device (BYOD) Nowadays, this practice to use their own devices at work it’s very often used. To be secured, a series of policies should be implemented by company. When try to implement BOYD policies, some issues can occur, such as:
Who may bring devices at workplace?
What devices may they bring?
How will the security of those devices be managed?
But, the core issue related with BOYD is regarding the ownership, because in BOYD environment the device is own by the user but the data can be own both by company and user. The BOYD policies should be very careful written to stay legal. It is very easy to attempt to the user’s privacy. That’s why when the company decide to adopt a BOYD policy should develop a clear guide for onboard and off board devices. BOYD Onboarding should ensure the devices meets the security requirements and are safety configured. With BOYD Offboarding rule, a user should remove all corporate information from the personally devices. Finally, when developing a BOYD policies, the company should be aware about technical implication on their network architecture and infrastructure. The company should be prepared to support a lot of devices with a variety of hardware, software, applications, etc. BOYD technical issues are: Mobile device management, patching and antivirus management, use of camera, forensic procedures.
Mobile device management (MDM). If a network administrator try to configure security on every single mobile device is a big challenge. That’s why the Mobile Device Management (MDM) technology was invented. MDM Features: Perform device configuration management; Prevent users from modifying security settings; Control data stored on devices; manage application installed on devices. Application can be on Black-Lists on White-List, in function of their security reasons. When an application is on Black-List, the administrator can prohibit the installation of that application on mobile devices. On other hand, if an application is on White-List, the administrator can allow installation of approved application on mobile device.
D.3. – Host Security
Operating System security | Malware prevention | Application management | Host-based network security controls | Hardware security | Virtualisation Security
Operating System Security. The configuration of Operating System should meet the company’s security control requirements. OS security is critical. Compromised systems are gateway to compromised network. OS Security Issues: Security settings, patch management and trusted operated systems.
Security settings. Are many security settings in any OS, that’s why is necessary to establish a security baseline for the company, to meet their security requirements. One of the most important requirement is to don’t give to the user’s administrative rights. To do that will be used security GPOs and User Configuration to restrict access.
Patch management. Appling patches to OS is critical, ensuring the system is vulnerable to security exploits discovered by attackers. On Windows, the Windows update is the way to apply the security patches. Recommended to be Automated Updates.
Trusted Operating System. Have not applicability on civil sector included here the Magic Memories network. It is used only on super secure networks as military or government organisations.
Malware prevention. Malware comes from Malicious Software. Are many types of Malwares, but these was explained at a previous area of this report (Threats and Vulnerability). To prevent the Malware should use an antimalware software. These types of software use same detections mechanisms: Signature detection (Watches for known patterns of virus activity); Behaviour detection (Watches for deviations from normal patterns of activity).
Application management. It is very important for network security to manage which applications can run or cannot run into a OS part of the network. For this purpose, should be created two lists: Black-List and White-List. When an application is on Black-List, the administrator can prohibit the installation of that application on mobile devices. On other hand, if an application is on White-List, the administrator can allow installation of approved application on mobile device. On Windows OS, can setup this using a GPO Management and under AppLocker can create rules to block a certain application. Application also require Patching. Different software vendors provide different patches mechanisms, but basically for all types of software should connect the vendor resources and perform an update.
Host-based network security controls. The most important Host-based network security control is the firewall, because the Firewall Control Network Access, following the Default Deny Principle, blocking anything not explicitly allowed. Firewalls come in two forms: Network Firewalls (hardware devices that regulate connections two networks) and Host Firewall (software components of operating systems that limit connections to a server). The Host Firewall is a very powerful tool which protect an OS. Come imbedded on OS. Can be set up to protect against traffic from same domain; same network but different domain; and against any public sources. As well can be configurated Inbound Rules and Outbound Rules. Apart of firewalls, IDS (intrusion detection systems) and IPS (intrusion prevention systems) are two useful tools which help to secure a network. IDS alert administrators to suspicious network activities and IPS take proactive measures to block suspicious network activities. These two tools can be Network Based or Host Based, but are not imbedded on OS.
Hardware security. The data, which in the most valuable good of every company, is located and stored in devices. To secure the devices, specially the mobile one should be a priority. Encryption protects sensitive data on devices from thefts. Stolen devices are financial loos for a company, that’s why is necessary to physical protect them, using cable locks, lookers with keys or cipher, cabinets for laptops, security tags, etc.
Virtualisation Security. Virtual machines are nothing more than files. Can use Virtualisation as a security tool such as follow: Sandboxing untrusted software, Testing security controls. Virtualisation make the Elasticity easy, that’s mean expanding and contracting virtualised resources to meet changing usage demands on either a server or service basis. Virtualisation platforms must be patched just like operating systems and applications.
D.4. – Data security
Understanding data security | Data security policies | File permissions | Data Encryption | could storage security
Understanding data security. Data is one of the most valuable asset for a company. That’s why a special attention on process of secure a network should be given to the confidentiality, integrity and availability of information assets. When start to create a strategy to secure data, should keep in mind that data is on two different states: Data on Rest and Data on Motion. Data on rest is stored for a later use on a hard drive, USB stick, Magnetic tape, Cloud service or any other data storage environment. This type of data is very vulnerable to theft. Data on Motion is that kind of data which is moving, being sent over the network between two systems. Data Security Controls: clear policies and procedures covering data use and security; encryption to protect sensitive information; and access controls on stored data.
Data security policies. Having strong data security policies should be a must for any network administrator.Data security policies and procedures plays a few strong roles in the process of cybernetic security. Data security policy criteria: foundational authority for data security efforts; clear expectation for data security responsibilities; guidance for requesting access to information; process for granting policy exceptions. Another important process in data security is how the data are classified. A special policy it written for that, named Data Classification Policy. For business, the classification can be: highly sensitive, sensitive, internal, public. Data Storage Policies define where the data is stored in function of importance. Data Storage Policies regulate: appropriate storage locations; access control requirements; and encryption requirements. Data Transmission Policies protect data on motion. This is the most vulnerable point for data. Date Transmission Policies should cover: appropriate data transmissions; encryption requirements; acceptable transmission mechanisms.
Data Lifecycle Policies describe end-of-life for data. This stage of data, should be covered by two policies: Data Retention Policies and Data Disposal Policies. On Data Retention Policies, should specify the minimum and/or maximum periods that a company will retain different data elements. Data Disposal Policies describe proper techniques for destroying data that is no longer needed by the company.
File Permissions. File system access control can filter the access to data. Nowadays, the files systems are configurated with a way to restrict access to the files and directories. The NTFS file system it is a good example in this sense and have five basic set of permissions: Full Control (grants complete authority over a resource); Read Permission (allow the user to read the file); Read & Execute (also allow the user to execute an application); Write Permission (allow the user to create files and modify their contents); Modify Permission (includes both Read & Execute and Write permissions and include the ability to delete).
Data Encryption. This controls is very often used to protect sensitive information. The encryption protects data using algorithms and secret key. Most encryption uses software to encrypt data, e.g. AES Crypt. The encryption can be used to protect the entire hard drive by using Full Disk Encryption. Another useful encryption is Database Encryption because protects the content of database from attacks.
Section E – Access Control and Identity Management
E.1. – Identification
Identification, Authentication and Authorization | Username and access cards | Biometrics
Identification, Authentication and Authorisation are the three steps of Access Control Process. On first step, Identification, the security guard identify a process or an action who want to interact with the network. On second step, Authentication, that process should prove his identity. Finally, Authorisation step, gain the access inside the network if the process pass the perilously two steps.
Usernames and access cards. Identification mechanisms are that processes through a user can identify himself. The most common identifications mechanisms are: Usernames and Access cards. Usernames are easily identifying the individual; often consist of a first initial and last name; should not be considered secret. The Access cards are often serving as proof of employment and may perform both identification and authentication. The access cards can be magnetic stripe cards or smart cards.
Biometrics other form of identification are that processes able to recognise a person upon one on more physical characteristics. Very often serve both scope: Identification and Authentication. A good Biometric System may provide: easy enrolment; low false acceptance rates; low false rejection rates; low intrusiveness. Example of biometrics: fingerprint scanner, eye scan, voiceprint matching, facial recognition, etc.
E.2. – Authentication
Authentication factors | Multifactor authentication | Something you have | Password authentication protocol (PAP) | The Challenge Handshake Authentication Protocol (CHAP) | RADIUS and TACACS | Kerberos | LDAP and Secure LDAP
Authentication factors. Once a user identify himself to a system, must prove that claim of identity. This is the step of Authentication and is made up of five factors: Something you know (password, passphrases, etc.); something you are (biometrics authentication); something you have (require physical possession of a device as smartphone or authentication key fob); somewhere you are (requiring user presence in a specific location) and something you do (requires to perform some action).
Multifactor Authentication Because the authentication can be tricked, the solution is to combine the authentication techniques to make more difficult to be hacked.
Password Authentication Protocol (PAP) it is the earliest protocol to implement the remote access password security. It is very simple and efficient but have a big issue because is not using any encryption.
The Challenge Handshake Authentication Protocol (CHAP) it’s a secure alternative to PAP and an acceptable technology for use in a modern secure application.
RADIUS and TACACS are two protocols used for access control to the network. RADIUS (Remote Access Dial-In User Service) are used to allow diverse applications to rely upon the same authentication source. Need a RADIUS server. RADIUS disadvantages: uses unreliable UDP (User Datagram Protocol); does not encrypt the entire authentication sequence. TACACS (Terminal Access Controller Access Control System) is a better alternative to RADIUS. The current TACACS standard is developed by Cisco and is named TACACS+. Basically, have same function as RADIUS, but with two improvements: Use Transmission Control Protocol (TCP) instead of UDP. And encrypt full authentication session.
Kerberos, it’s an access control system and is very used to implement authentication protocols. It’s a ticked-based authentication system that allows users to authenticate to a centralized service and then use tickets from that authentication process to gain access to distributed systems.
LDAP (Lightweight Directory Access Protocol) is an important access control protocol. Active Directory use LDAP in combination with Kerberos.
E.3. – Authorisation
Understanding authorisation | Mandatory access Controls | Discretionary access controls | Access Control Lists | Advanced Authorisation Concepts
Understanding authorisation. The authorisation is the last step in the access control process. Exist two principle of authorisation who lead to a strong security: Least Privilege and Separation of Duties. Least Privilege is important for two reasons: can minimalize the damage of an internal attack and limits the ability of an external attack to gain privilege access. Separation of duties principle should involve minimum two people in sensitive business functions. Every company when dealing with Least Privilege and Separation of Duties should watch out for Privilege Creep, which occur when a member of staff is internally moved to another position with new privilege, but the old privilege are not cancellated and that person still can access them.
Mandatory Access Controls (MAC) is an access control system where the operating system enforces security policies that users may not modify.
Discretionary Access Controls (DAC) are a type of access control system where permissions may be set by the owners of files, computers and other resources. This is the most used access control because offer flexibility to the companies.
Access Control Lists. Under the DAC can be created a series the rules regarding resources permissions, named Access Control List (ACL). An ACL is a table contained user name and the permission granted; e.g. the NTFS file system implements ACL which granted a specific level of access for a particular user. Similar thing is applied for share permission.
Advanced Authorisation Concepts. Authorisation in an access control system can develop a few issues as follow: implicit deny principle, role-based authorisation and time of day restriction. Implicit Deny Principle acting in this way: Any action which is not explicitly allowed must be denied. The firewalls are the best example of Implicit Deny Principle. The Role-Based Access Control simplify the managing access because permissions are grouped together into functional roles and users are assigned to those roles. It is very useful when a new user arrives and must assign him with permission. Time of Day restrictions limit the use of resources during certain hours.
E.4. – Account Management
Account and privilege management | Account policies | Password policy | Managing Roles | Account monitoring | Suspending and terminating access
Account and privilege management. Performing the account management task is one of the most important duty for a network and informational security. These tasks are as follow: least of privilege, separation of duties, job rotation scheme and mandatory vacation. All these tasks where explained above, but as a conclusion they help to manage in a secure way accounts and privilege levels.
Account policies across the domain, the security administrator can apply security requirements and other settings, taking advantage of account policies. Active Directory provide a set of Group Policies functionalities that’s allow this type of configurations. Group Policies Objects (GPOs) can be created by administrator, with the intention of setting up configuration which can be applied to the entire domain or to a smaller group of users or computers, named Organisational Units (OU).
Password policy. Passwords are the most common authentication elements, that’s why is very important to keep them secure. A series of policies can be securely configurated by using GPO. One of the most important password requirement is to be difficult to guess. To achieve that, should implement a series of elements as: Password Length (a minimum 8 characters); Password Complexity (include uppercase and lowercase letters, digits and symbols). Another aspect is to prevent long-term illegitimate use by: Password expiration (e.g. every 90 days); Password history and reuse (Keep track of previous passwords and prevent reuse an old password). A strong password policy protects against brute force attacks, by: lockout the account (after a several incorrect password guesses) and disable the account (blocking the use of old accounts). Finally, should be provided a password recovery mechanism, which allow users to reset passwords on a self-service basis.
Managing Roles. Roles give to the security administrator possibility to manage easily the security permissions. Roles can be created by the administrator and using Security Groups can manage them and their permissions. The major benefit of roles: simplify account management; the administrator may assign permissions to new users by adding a role to the user; easily remove permissions from departing users by removing the roles. Another good thing of using roles is: Roles eliminate the danger of using bad account practices – the use on share or generic accounts.
Account monitoring. The users accounts should be careful monetarised, to prevent any possible issues. Account Security issues: inaccurate permissions (prevent legitimate work and grant extra access – privilege creep); illegitimate account use (unauthorised use of permitted access). Regarding first issue, a user access review is necessary. At this review, should: pull listing of user permissions, review permissions with managers, make any necessary adjustments and focus on users who recently changed roles. However, a Continuous Account Monitoring it’s imperious necessary to alert the administrator if strange activity is happening and flag any unusual activity, such as: unusual login location, strange login times, deviation from normal behaviour and high-volume activity.
Suspending and terminating access. A good practice is to remove users accounts when is no longer required. A prompt termination of unused accounts is critical for security, because: prevent users from accessing resources without permission and is especially critical when a user leave the company under bad circumstances. To remove these accounts, exist two methods: automatic and semi-automatic. A normal Workflow disable accounts automatically on a scheduled basis for planed departures. Emergency Workflow is a semi-automatic way to disable an account and occur when a user is fired, an immediately action is taken to suspend access to the account. Failure to terminate accurately an account, can create these situations: may inform a user in advance of pending termination or may allow a user access to resources after termination.
2.2. Testing
In this chapter, a series of tests will be made to verify if the prototype build for Magic Memories company it’s functional and enough secured to be applied to the real network.
All tests are included into a table. If a fault was founded it’s included into a separate table and finally a table with re-tested attempts it is be provided as well.
Table 5 – Test Table no. 1
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 1 | Ping a PC with his IP address | It’s expected to be possible to ping the own IP address | It is working | Y | N/A |
| 2 | Ping the Loopback Address 127.0.0.1 | It’s expected to be possible to ping the loopback address | It is working | Y | N/A |
| 3 | Check connectivity inside the same VLAN, by pinging Sales Manager PC with Staff 1 PC | It’s expected to be possible to ping machines inside same VLAN | It is working | Y | N/A |
| 4 | Check connection between VLANs, by pinging Sales Manager PC with Server | It’s expected to not be possible to ping between VLANs | The ping is not working | Y | N/A |
| 5 | Test ROAS, by pinging a PC to the default gateway interface | Should work fine, as long a sub-interface it is set up as default gateway for every VLANs | It is possible | Y | N/A |
| 6 | Check connection between VLANs, after was setup ROAS | It’s expected to be possible to ping between VLANs | It is working | Y | N/A |
| 7 | Check connection between a PC and Internet, by pinging ISP router | It’s expected to work fine | It is not working | N | 1 |
| 8 | Check connection between a PC and Wireless Router | It’s expected to work fine | It is not working | N | 2 |
| 9 | Test the DHSP on Wireless part of network | The mobile device should get automatically an IP address from the range of IPs allocated | It’s working perfectly | Y | N/A |
| 10 | Check connection between Laptop and one of the VLANs | Should work fine | It’s working perfectly | Y | N/A |
| 11 | Check connection between Laptop and Internet | The Laptop should be able to ping the ISP router | It’s working perfectly | Y | N/A |
| 12 | Test if the unused ports of the switches are closed | If I try to connect a PC to an unused port of the switch should not be possible | The connection at that port it is not possible | Y | N/A |
Table 6 – Test Table no. 2
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 13 | Test if the used ports of the switches are secured, allowed only one MAC Address to be connected | By connected at one of the used ports a different device, I expect that port to not be functional | The connection at this port is not working | Y | N/A |
| 14 | Test if the unused ports of the Internal Router are closed | If I try to connect a device to an unused port of the Internal Router should not be possible | The connection at that port it is not possible | Y | N/A |
| 15 | Test if the unused services on router are closed | The unused services as HTTP or TCP and UDP small services, existed in router by default should be closed | Doesn’t worked | N | 3 |
| 16 | Test the establish password for access to the privilege mode (SWITCH) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
| 17 | Test the establish password for access to the privilege mode (ROUTER) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
| 18 | Test if the passwords are encrypted (Switch) | With “show running-config” command it is possible to see that the passwords are not visible on plain text. That’s mean they are encrypted. | I can see the passwords are encrypted, because are not visible on plain text. | Y | N/A |
| 19 | Test if the passwords are encrypted (Router) | With “show running-config” command it is possible to see that the passwords are not visible on plain text. That’s mean they are encrypted. | I can see the passwords are encrypted, because are not visible on plain text. | Y | N/A |
| 20 | Test the establish password for access to Console (Switch) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
| 21 | Test the establish password for access to Console (Router) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
Table 7 – Test Table no. 3
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 22 | Test the establish VTY password for Telnet access (Switch) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
| 23 | Test the establish VTY password for Telnet access (Router) | When a wrong password is typed in the access is denied.
The access is permitted only with a correct password. |
Access denied with a wrong password
Access granted with the correct password |
Y | N/A |
| 24 | Test the Telnet (Switch) | From a PC, can remotely access the switch via Telnet, using Management VLAN (60) | It’s working | Y | N/A |
| 25 | Test “banner motd.” (Switch) | With “show running-config” command, can see the banner message is set up. | The message can be showed at the beginning, before gain access to privilege mode and as well on “show” command | Y | N/A |
| 26 | Test “banner motd.” (Router) | With “show running-config” command, can see the banner message is set up. | The message can be showed at the beginning, before gain access to privilege mode and as well on “show” command | Y | N/A |
| 27 | Test “login security” (Switch) | The expected results of this test are: to block the connection if the password was incorrect introduced for more than 3 time and to be able to re-introduce again the password after an establish length of time | Everything it is worked as I expected | Y | N/A |
| 28 | Test “login security” (Switch) | The expected results of this test are: to block the connection if the password was incorrect introduced for more than 3 time and to be able to re-introduce again the password after an establish length of time | Everything it is worked as I expected | Y | N/A |
| 29 | Test SSH connection (Switch) | The expected result of this test is to be allowed to access the switch Management VLAN via a PC, by introducing a password | It is worked | Y | N/A |
| 30 | Test the security on SSH connection (Switch) | Expected as after an establish time the switch to drop off the SSH link | It’s working perfectly | Y | N/A |
Table 8 – Test Table 4
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 31 | Test spanning tree with “show spanning-tree” command | Message expected “This bridge is the root” The Switch 1 became the bridge route for the network | The test works perfectly | Y | N/A |
| 32 | Test the Telnet (Rourer) | From a PC, can remotely access the Router via Telnet, using Loopback1 IP address 192.168.1.121 | It’s working | Y | N/A |
| 33 | Test SSH connection (Router) | The expected result of this test is to be allowed to access the router Loopback Address via a PC, by introducing a password | It is worked | Y | N/A |
| 34 | Test the security on SSH connection (Router) | Expected as after an establish time the switch to drop off the SSH link | It’s working perfectly | Y | N/A |
| 35 | Test OSPF routing protocol | The traffic on Internal Router it’s directed accordingly | The laptop can communicate with any PCs and have connection to the Internet as well. | Y | N/A |
| 36 | Test DHCP on wireless network, before implement any security | Expected as any mobile device to get an IP address from the range allocated for this part on network | It is worked | Y | N/A |
| 37 | Test the connectivity between the laptop and wireless router after implement on router security as: SSID name, WPA2 Personal, password | The laptop cannot be connected to the network. | Missing connectivity | Y | N/A |
| 38 | Test the connectivity between laptop and wireless router after was assigned to the new network co-ordinates. | The connectivity is established again, after introduce the new network name, security protocol and password. | It’s working perfectly | Y | N/A |
| 39 | Setup an ACL on internal router to act as a firewall between pings but able to allow the web traffic | Expected to not be possible to ping in and out from network but the web traffic to be allowed | It’s not working. Every traffic it is blocked | N | 4 |
| 40 | Test the printer accessibility | It’s expected that a printer from a specific VLAN to allow access to print only to the PCs part of that VLAN. All other PC are denied to access the printer. | It is functional | Y | N/A |
Table 9 – Tests Table no 5
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 41 | Test the username and the login password (Client PC) | The access to the PC will be allowed only with a specific username and password. If one of these are not correctly introduced the PC access will be denied. | It’s working | Y | N/A |
| 42 | Test the username and the login password (Server) | The access to the Server will be allowed only with a specific username and password. If one of these are not correctly introduced the PC access will be denied. | It’s working | Y | N/A |
| 43 | Test Windows Update on CLIENT PC | Expected as Windows Update service to be On and Automatic | It’s working | Y | N/A |
| 44 | Test Windows Update on Server | Expected as Windows Update service to be On and Automatic | It’s working | Y | N/A |
| 45 | Test the antivirus updates (Client PC) | The antivirus should have the update function activated and to be executed automatically | It’s setup on proper way | Y | N/A |
| 46 | Test the antivirus scan schedule (Client PC) | The antivirus should have the have the automatically scan schedule activated | It’s setup on proper way | Y | N/A |
| 47 | Test Managing Director sharing permission over the network | The Managing Director, from his PC, should have access to all private files stored on server belongs to other members of staff, but nobody else should have access to his files stored on server. | It’s working properly | Y | N/A |
| 48 | Test Sales Manager sharing permission over the network | The Sales Manager, should have access from his PC to all private files stored on server belongs to members of staff of his department, but nobody else should have access to his files stored on server, excepted Managing Director | It’s working properly | Y | N/A |
| 49 | Test Sales Staff 1 sharing permission over the network | The Sales Staff 1, shouldn’t have access from his PC to any private files stored on server belongs to other members of staff. Only he, Sales Manager and Managing Director should have access to his files stored on server. | It’s working properly | Y | N/A |
| 50 | Test Managing Director NTFS permission over the network | The Managing Director should have access to all private files and folders stored on server belongs to other members of staff, but nobody else should have access to his files stored on server. | It’s working properly | Y | N/A |
| 51 | Test Sales Manager NTFS permission over the network | The Sales Manager, should have access to all private files and folders stored on server belongs to members of staff of his department, but nobody else should have access to his files stored on server, excepted Managing Director | It’s working properly | Y | N/A |
Table 10 – Tests table no 6
| No. | Test carried on | Expected result | Actual result | Pass Y/N | Fault |
| 52 | Test Sales Staff 1 NTFS permission over the network | The Sales Staff 1, shouldn’t have access to any private files or folders stored on server belongs to other members of staff. Only he, Sales Manager and Managing Director should have access to his files stored on server. | It’s working properly | Y | N/A |
| 53 | Test the Firewall on server | ||||
| 54 | Test the Firewall on PC | ||||
| 55 | Test Port Vulnerability on server using ShieldsUp software | ||||
| 56 | Test port vulnerability on PC ShieldsUp software |
Table 11 – Faults Table
| No. | What is the Fault | How was it resolved | Fault fixed | Re-test No. |
| 1 | The PCs from VLANs cannot ping the ISP router | Setup OSPF routing protocol on Internal Router | Y | 1 |
| 2 | ||||
| 3 | Can’t shut down the unused services on router | The packet tracer doesn’t have installed this function | Y | n/a |
| 4 | After ACL was implemented, the traffic was blocked | Reconfigure OSPF routing Protocol | Y | 3 |
Table 12 – Re-tests / Fixed Fault Tests
| No. | Test carried on | Expected result | Actual result | Pass Y/N | ||
| 1 | Check connection between a PC and Internet, by pinging ISP router | I expect to be possible to ping the ISP router | It is working | Y | ||
| 2 | ||||||
| 3 | Test OSPF routing protocol, after implementing ACL | The traffic to be establish again | It is working | Y | ||
2.3. Managing the project
In the last chapter of Development Stage of Graded Unit, I will describe and give relevant information about the effectiveness of the Planning Stage and changes occurred during the development of the project.
As an Industrial Strike, has been in place at Edinburgh College, all the times and tasks from the original planning were affected, as follow:
- Submission date for Development stage where moved with one week forward.
- The meetings with the Client (Mr Williamson) on hold, until further notice
- Thus, the task “Adjust the prototype in accordance with client observations” hasn’t been processed
- Due a technical error I was unable to proceed in accordance with the project plan the task “Design a prototype according with the solution “. (VMware software crashed on the middle the project and I had to start from the beginning the Prototype)
I manage to implement the original plan as the small changes didn’t affect drastically the effectiveness of the entire project. Using the knowledge gained throughout the years of studies at Edinburgh College; applying principles and theories of integrated Units of studies I manage to approach the project in a holistic manner.
To support and evidence the contingency plan a Microsoft Project file will be uploaded alongside with the project.
Bibliography
Professor Messer (2016). Professor Messer’s CompTIA SY0-401 Security+ Training Course. Available at: http://www.professormesser.com/security-plus/sy0-401/sy0-401-course-index/. (Accessed: 21.03.2017)
Wikipedia (2017). DMZ (computing). Available at: https://en.wikipedia.org/wiki/DMZ_ (computing) (Accessed: 21.03.2017)
SANS (2017). Network Security Resources. Available at: https://www.sans.org/network-security/ (Accessed: 21.03.2017)
Use IT Computers (2017). 5 Reasons why network security is critical for business users. Available at: http://www.use-it.co.uk/use-it-news/5-reasons-network-security-incredibly-important-business-users/ (Accessed: 22.03.2017)
Wikipedia (2017). Computer security. Available at: http://en.wikipedia.org/wiki/Computer _security (Accessed: 24.03.2017)
Wikipedia (2017). Attack (computing). Available at: https://en.wikipedia.org/wiki/Attack_ (computing) (Accessed: 24.03.2017)
Microsoft Technet (2017). Overview of malware inspection. Available at: https://technet.microsoft.com/en-us/library/dd182018.aspx (Accessed: 25.03.2017)
Cisco (2017). What Is the Difference: Viruses, Worms, Trojans, and Bots? Available at: http://www.cisco.com/c/en/us/about/security-center/virus-differences.html (Accessed: 24.03.2017)
PC Tools (2016) What is Adware and Spyware? Available at: http://www.pctools.com/ security-news/what-is-adware-and-spyware/ (Accessed: 24.03.2017)
Vangie, B. (2017). The Difference Between Adware & Spyware. Available at: http://www.webopedia.com/DidYouKnow/Internet/spyware.asp (Accessed: 25.03.2017)
PC Tools (2016) What is a Rootkit Virus? Available at: http://www.pctools.com/security-news/what-is-a-rootkit-virus/ (Accessed: 26.03.2017)
Wikipedia (2017). Logic bomb. Available at: https://en.wikipedia.org/wiki/Logic_bomb (Accessed: 26.03.2017)
Kaspersky (2017). What is a Botnet? Available at https://usa.kaspersky.com/resource-center/threats/botnet-attacks (Accessed: 26.03.2017)
Wikipedia (2017). Ransomware. Available at: https://en.wikipedia.org/wiki/Ransomware (Accessed: 26.03.2017)
Rouse, M. (no date). Polymorphic malware. Available at: http://searchsecurity.techtarget. com/definition/polymorphic-malware (Accessed: 26.03.2017)
Beal, V. (2017). Armored Virus. Available at: http://www.webopedia.com/TERM/A/Armored _Virus.html (Accessed: 27.03.2017)
Wikipedia (2017). Man-in-the-middle attack. Available at: https://en.wikipedia.org/wiki/Man-in-the-middle_attack (Accessed: 27.03.2017)
Wikipedia (2017). Denial-of-service attack. Available at: https://en.wikipedia.org/wiki/Denial-of-service_attack (Accessed: 27.03.2017)
Wikipedia (2017). Replay attack. Available at: https://en.wikipedia.org/wiki/Replay_attack (Accessed: 27.03.2017)
Techopedia (2017). Spoofing. Available at: https://www.techopedia.com/definition/5398/ spoofing (Accessed: 27.03.2017)
Beal, V. (2017). Spam. Available at: http://www.webopedia.com/TERM/S/spam.html (Accessed: 27.03.2017)
Cisco (2017). Entrepreneur security. Available at: http://www.cisco.com/c/dam/ global/ro_ro/assets/pdfs/imm/04_Entreprenuer_security.pdf (Accessed: 27.03.2017)
https://techterms.com/definition/ssid
http://www.linksys.com/us/support-article?articleNum=136623
https://www.howtogeek.com/204697/wi-fi-security-should-you-use-wpa2-aes-wpa2-tkip-or-both/
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html#anc14
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Compliance and Operational Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Part-2-Compliance-Operational-Security/433938-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Network Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Part-1-Network-Security/433937-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Threats and Vulnerabilities. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Threats-Vulnerabilities/415404-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Application Data and Host Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Application-Data-Host-Security/433940-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Access Control and Identity Management. Available at: https://www.lynda.com/IT-Infrastructure-tutorials/CompTIA-Security-SY0-401-Cert-Prep-Access-Control-Identity-Management/415405-2.html (Accessed: 15.05.2017)
References
Professor Messer (2016). Professor Messer’s CompTIA SY0-401 Security+ Training Course. Available at: http://www.professormesser.com/security-plus/sy0-401/sy0-401-course-index/. (Accessed: 21.03.2017)
Wikipedia (2017). DMZ (computing). Available at: https://en.wikipedia.org/wiki/DMZ_ (computing) (Accessed: 21.03.2017)
SANS (2017). Network Security Resources. Available at: https://www.sans.org/network-security/ (Accessed: 21.03.2017)
Use IT Computers (2017). 5 Reasons why network security is critical for business users. Available at: http://www.use-it.co.uk/use-it-news/5-reasons-network-security-incredibly-important-business-users/ (Accessed: 22.03.2017)
Wikipedia (2017). Computer security. Available at: http://en.wikipedia.org/wiki/Computer_ security (Accessed: 24.03.2017)
Wikipedia (2017). Attack (computing). Available at: https://en.wikipedia.org/wiki/Attack_ (computing) (Accessed: 24.03.2017)
Microsoft Technet (2017). Overview of malware inspection. Available at: https://technet.microsoft.com/en-us/library/dd182018.aspx (Accessed: 25.03.2017)
Cisco (2017). What Is the Difference: Viruses, Worms, Trojans, and Bots? Available at: http://www.cisco.com/c/en/us/about/security-center/virus-differences.html (Accessed: 24.03.2017)
PC Tools (2016) What is Adware and Spyware? Available at: http://www.pctools.com/security-news/what-is-adware-and-spyware/ (Accessed: 24.03.2017)
Vangie, B. (2017). The Difference Between Adware & Spyware. Available at: http://www.webopedia.com/DidYouKnow/Internet/spyware.asp (Accessed: 25.03.2017)
PC Tools (2016) What is a Rootkit Virus? Available at: http://www.pctools.com/security-news/what-is-a-rootkit-virus/ (Accessed: 26.03.2017)
Wikipedia (2017). Logic bomb. Available at: https://en.wikipedia.org/wiki/Logic_bomb (Accessed: 26.03.2017)
Kaspersky (2017). What is a Botnet? Available at: https://usa.kaspersky.com/resource-center/threats/botnet-attacks (Accessed: 26.03.2017)
Wikipedia (2017). Ransomware. Available at: https://en.wikipedia.org/wiki/Ransomware (Accessed: 26.03.2017)
Rouse, M. (no date). Polymorphic malware. Available at: http://searchsecurity.techtarget.com/definition/polymorphic-malware (Accessed: 26.03.2017)
Beal, V. (2017). Armored Virus. Available at: http://www.webopedia.com/TERM/A/Armored_Virus.html (Accessed: 27.03.2017)
Wikipedia (2017). Man-in-the-middle attack. Available at: https://en.wikipedia.org/wiki/Man-in-the-middle_attack (Accessed: 27.03.2017)
Wikipedia (2017). Denial-of-service attack. Available at: https://en.wikipedia.org/wiki/Denial-of-service_attack (Accessed: 27.03.2017)
Wikipedia (2017). Replay attack. Available at: https://en.wikipedia.org/wiki/Replay_attack (Accessed: 27.03.2017)
Techopedia (2017). Spoofing. Available at: https://www.techopedia.com/definition/5398/ spoofing (Accessed: 27.03.2017)
Beal, V. (2017). Spam. Available at: http://www.webopedia.com/TERM/S/spam.html (Accessed: 27.03.2017)
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html#anc14
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Compliance and Operational Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Part-2-Compliance-Operational-Security/433938-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Network Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Part-1-Network-Security/433937-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Threats and Vulnerabilities. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Threats-Vulnerabilities/415404-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Application Data and Host Security. Available at: https://www.lynda.com/Security-tutorials/CompTIA-Security-Exam-Prep-SY0-401-Application-Data-Host-Security/433940-2.html (Accessed: 15.05.2017)
Chapple, M. (2016). CompTIA Security+ (SY0-401) Cert Prep: Access Control and Identity Management. Available at: https://www.lynda.com/IT-Infrastructure-tutorials/CompTIA-Security-SY0-401-Cert-Prep-Access-Control-Identity-Management/415405-2.html (Accessed: 15.05.2017)
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please: