Approaches to Applying Defence in Depth to Web Applications
Info: 3646 words (15 pages) Dissertation
Published: 9th Dec 2019
Tagged: Cyber Security
Vulnerabilities and Defences
NET512: Database and Web Security
2.1 Server and Database paradigms
3.2 Database Permissions (Least Privilege)
List of Figures
Figure 1. Defence in Depth Overview………………………………………
Figure 2. Defence in Depth for Web Applications……………………………..
Figure 3. Fortification of host nodes……………………………………….
Figure 4. Session Spoofing……………………………………………..
Figure 5. Http Headers………………………………………………..
Figure 6. OSfuscate – Before…………………………………………….
Figure 7. OSfuscate – After……………………………………………..
Figure 8. URLScan – Before……………………………………………..
Figure 9. URLScan – After………………………………………………
Figure 10. SQL Injection Attack…………………………………………..
Figure 11. SQL Injection Result…………………………………………..
List of Tables
Table 1. Microsoft Server 2019 vs Ubuntu Server 18.04 (2/11/18)………………..16
Table 2. Microsoft IIS 7.5 vs Apache 2.4 (2/11/18)…………………………..16
Table 3. A comparative study of attacks against Corporate IIS and Apache………….16
Introduction
The premise for this report is to provide the client with a deeper understanding of the security landscape, by delivering a more comprehensive overview of Defence in Depth, security vulnerabilities in the server and application layers and finally, security recommendations for the client’s website.
1 DEFENCE IN DEPTH
Originally defined as a military strategy, in the 1976 thesis ‘The grand strategy of the Roman Empire from the first century A.D. to the third’ by Edward Luttwak (Luttwak, 1976); the concept ‘Defence in Depth’ was later adopted by the National Security Agency (NSA, 2010), as a suitable ‘best practice’ paradigm for achieving information assurance.
Luttwak elucidates that the basic principle of the strategy is to implement layers of defence around the target of an attacker, rather than to defeat an attack with a single, strong defensive line. The objective is to slow an advance because, over time, attrition will force the attack to lose momentum, and therefore, will not be as effective.
In terms of information security, Straub (2003) describes that this layered defensive posture (Appendix, Figure. 1) is leveraged by using redundant security mechanisms, so that if one defensive measure fails there are more behind it to continue to protect the data, systems, networks, and users, by buying time. Time, which can then be utilised, to respond to an incident, minimising the risk of an attack (Shamim, Fayyaz and Balakrishnan, 2014).
An essential principle of the Defence in Depth strategy, develops Skoglund (2014), is a balanced focus on three primary elements: People, Technology and Operations, which can be applied within each layer.
However, it is essential to understand, that implementing a secure defence is always a “best effort”. No system can ever be 100% secure, affirms Langer and Yorks (2018, p.222) because factors outside of the controls, might introduce vulnerabilities. An example of this is that software in use may contain 0-day bugs; unknown application vulnerabilities that could be exploited by an attacker.
When considering the primary elements, often overlapping, three types of control can be applied: Physical, Technical, and Administrative.
LO1: Evaluate approaches to applying defence in depth to web applications
1.1 Physical Controls
[84 words max] Describe one area.
Physical controls are anything that physically limits or prevents access to an IT asset for example, fences, guards, dogs, locks, and CCTV systems.
Locks
Often underutilised, most modern computer cases incorporate a holed tab at the rear, to permit the fitting of a lock, thereby delaying the removal of the case cover, denying access to and the removal of, the systems hard drives.
1.2 Technical Controls
[84 words max] Describe one area.
Web Application Firewalls
DSS-PCI Card Transactions
OSI Layer 7, deep packet inspection. Reverse proxy (Proxy interrogates application, not client)
Technical controls are hardware or software whose purpose is to protect systems and resources. Examples of technical controls would be disk encryption, fingerprint readers, and Windows Active Directory. Hardware technical controls differ from physical controls in that they prevent access to the contents of a system, but not the physical systems themselves.
1.3 Administrative Controls
[84 words max] Describe one area.
Security Awareness Training
Administrative controls are an organisation’s policies and procedures. Their purpose is to ensure that there is proper guidance available regarding security and that regulations are met. They include things such as hiring practices, data handling procedures, and security requirements.
2 SECURITY VULNERABILITIES
Your task is to compare, and contrast, a range of vulnerabilities and their potential effect on your client’s business.
LO2: Compare and contrast security vulnerabilities in dynamic web environments using different development paradigms
This section should cover: –
• Features and comparison of Windows IIS/SQL and Apache/MySQL
• Comparing and contrasting key elements of vulnerabilities in dynamic web environments using different development paradigms
• Definition and analysis of the vulnerabilities listed in the scenario
2.1 Server and Database paradigms
[180 words max] Firstly compare, and contrast, the two main server and database paradigms; i.e. Windows IIS/SQL (WISA) and Apache/MySQL (WAMP) regarding vulnerabilities.
2.2 Generic Vulnerabilities
Secondly, discuss the generic vulnerabilities listed below (additional vulnerabilities could be considered).
2.2.1 Session spoofing
[100 words max] Text goes here.
2.2.2 Injection attacks
[100 words max] Text goes here.
SQL Injection (SQLi) can be used in a range of ways to cause serious problems. By levering SQL Injection, an attacker could bypass authentication, access, modify and delete data within a database. In some cases, SQL Injection can even be used to execute commands on the operating system, potentially allowing an attacker to escalate to more damaging attacks inside of a network that sits behind a firewall.
SQL Injection can be classified into three major categories – In-band SQLi, Inferential SQLi and Out-of-band SQLi.
Both fields, ‘ or 1=1–
Password field, 1’or’1’=’1
(GAO, 2018) Equifax 2017 SQL Injection
(ICO, 2015) TalkTalk – DDoS + SQL Injection
2.2.3 Cross-site scripting
[100 words max] Text goes here.
Vulnerabilities persists in many Web applications due to developers lack of expertise in the problem identification and their unfamiliarity with the current mechanisms (Venkat et al., 2012)
(Mutton, 2017) eBay 2017
3 SECURITY RECOMMENDATIONS
You have previously undertaken some analysis of the static vulnerabilities of the website using penetration testing tools. You are now required to extend this analysis to the susceptibility of the Lanconnnectors site to the vulnerabilities discussed in section 2, and other threats specific to this configuration that you may have identified or discovered.
LO3: Critically analyse the potential security risks for a given web deployment scenario and recommend security mechanisms
This section should cover: –
• Analysis of threats from section 2 contextualised to the client website
• Security recommendations to mitigate threats from section 2
• Analysis of additional areas listed in scenario
• Security recommendations to mitigate threats from additional areas listed in the scenario.
3.1 Developer Skill
[160 words max] Text goes here. Full stack vs Coder? Security through validation? Do not offer the ability to delete a record.
Password sniffing, spoofing, buffer overflows, and denial of service: these are only a few of the attacks on today’s computer systems and networks. At the root of this epidemic is poorly written, poorly tested, and insecure code that puts everyone at risk. Developers today need help figuring out how to write code that attackers will not be able to exploit. However, writing such code is surprisingly difficult (Viega and Messier, 2003).
Front End developer + Backend developer = Full Stack developer
3.2 Database Permissions (Least Privilege)
[160 words max] Text goes here. Default permissions?
(Barnum and Gegick, 2005) Explain that only the minimum necessary rights should be assigned to a subject that requests access to a resource and should be in effect for the shortest duration necessary (remember to relinquish privileges). Granting permissions to a user beyond the scope of the necessary rights of action can allow that user to obtain or change information in unwanted ways. Therefore, a careful delegation of access rights can limit attackers from damaging a system.
3.3 Security Obscurity
[160 words max] Text goes here.
Gleaning information, by undertaking passive reconnaissance using a product such as Burp Suite (PortSwigger, 2018), helps to narrow the field of possible exploits, thereby saving an attacker time and effort, explains (Skoglund, 2014b). Figure 5. Illustrates that the Http Headers are exposing
Therefore, understanding that if a web server’s known to be running Apache 2.2 a hacker, or a script that the hacker’s running, knows to look for security holes in Apache 2.2. If the web server software is unknown, they must try everything. So you want to limit exposed information. Don’t report any more information than is absolutely necessary. It’s similar to the idea of least privilege, but this is least information.
It is possible to obscure the identification of the operating system, by anyone using active reconnaissance tools, using an application such as OSfuscate 0.3 (Crenshaw, 2016)
Performing this task prevents a potential hacker from focusing an attack against the known vulnerabilities of a known operating system.
A comparative study of attacks against Corporate IIS and Apache (Wright, 2011)
Figure 5. Illustrates that the Http Headers are exposing ,,,,,,,,,,,,,,,,,,,
To frustrate the attacker
3.4 Password Usage/Storage
[160 words max] Text goes here.
2 step authentication
Hashing/salting
References
Barnum, S. and Gegick, M. (2005) Least privilege.
Cleghorn, L. (2013) ‘Network Defense Methodology: A Comparison of Defense in Depth and Defense in Breadth’, Journal of Information Security, Vol:4, pp. 144–149. doi: 10.4236/jis.2013.43017.
Crenshaw, A. (2016) ‘OSfuscate’. Louisville: IronGeek.
Darknet (2017) Defence In Depth For Web Applications [Image], Countermeasures. Available at: https://www.darknet.org.uk/2016/03/defence-depth-web-applications/ (Accessed: 30 October 2018).
GAO (2018) Actions Taken by Equifax and Federal Agencies in Response to the 2017 Breach.
ICO (2015) TalkTalk cyber attack – how the ICO’s investigation unfolded, News and Events. Available at: https://ico.org.uk/about-the-ico/news-and-events/talktalk-cyber-attack-how-the-ico-investigation-unfolded/ (Accessed: 25 October 2018).
Langer, A. M. and Yorks, L. (2018) Strategic Information Technology : Best practices to drive digital transformation. 2nd edn. John Wiley & Sons.
Luttwak, E. (1976) The grand strategy of the Roman Empire from the first century A.D. to the third. Johns Hopkins University Press.
Matrix Computer Consulting (2018) Cyber Security 101 [Image], Cyber Security Practice. Available at: http://www.matrixcc.net/cyber-security/ (Accessed: 30 October 2018).
Mitre (2018a) Apache 2.4 Search Results, Common Vulnerabilities and Exposures (CVE) List. Available at: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=apache+2.4 (Accessed: 2 November 2018).
Mitre (2018b) IIS 7.5 Search Results, Common Vulnerabilities and Exposures (CVE) List. Available at: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=iis+7.5 (Accessed: 2 November 2018).
Mitre (2018c) Microsoft Server 2019 Search Results, Common Vulnerabilities and Exposures (CVE) List. Available at: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Microsoft+Server+2019 (Accessed: 2 November 2018).
Mitre (2018d) Ubuntu Server 18.04 Search Results, Common Vulnerabilities and Exposures (CVE) List. Available at: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Ubuntu+Server+18.04 (Accessed: 2 November 2018).
Mrd, D. (2018) Redirect someone to a different website (ARP spoofing). [Image], Pentest Tips. Available at: http://pentestfreak.blogspot.com/2013/05/redirect-someone-to-different-website.html (Accessed: 1 November 2018).
Mutton, P. (2017) Hackers still exploiting eBay’s stored XSS vulnerabilities in 2017, Security. Available at: https://news.netcraft.com/archives/2017/02/17/hackers-still-exploiting-ebays-stored-xss-vulnerabilities-in-2017.html (Accessed: 28 October 2018).
NSA (2010) Defense in Depth. Fort Meade.
PortSwigger (2018) ‘Burp Suite Professional’.
Shamim, A., Fayyaz, B. and Balakrishnan, V. (2014) ‘Layered Defense in Depth Model for IT Organizations’, in 2nd International Conference on Innovations in Engineering and Technology. Penang, p. 4. doi: 10.15242/IIE.E0914047.
Skoglund, K. (2014a) ‘Defense in depth’, in Programming Foundations: Web Security. Lynda.com. Available at: https://www.lynda.com/Web-Development-tutorials/Defense-depth/133330/163841-4.html (Accessed: 27 October 2018).
Skoglund, K. (2014b) ‘Security through obscurity’, in Programming Foundations: Web Security. Lynda.com. Available at: https://www.lynda.com/Web-Development-tutorials/Security-through-obscurity/133330/163842-4.html (Accessed: 27 October 2018).
Straub, K. R. (2003) Information Security : Managing Risk with Defense in Depth.
Venkat, T., Rao, N., Tejaswini, V. and Preethi, K. (2012) ‘Defending against Web Vulnerabilities and Cross-Site Scripting’, Journal of Global Research in Computer Science, Vol:3(5), p. 4.
Viega, J. and Messier, M. (2003) Secure programming cookbook for C and C++. O’Reilly.
Wright, C. S. (2011) A comparative study of attacks against Corporate IIS and Apache Web Servers.
Appendix
Figure 1. Defence in Depth Overview
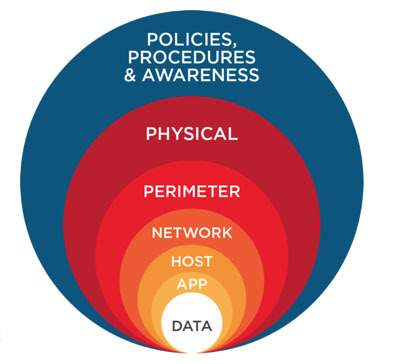
(Matrix Computer Consulting, 2018)
Figure 2. Defence in Depth for Web Applications
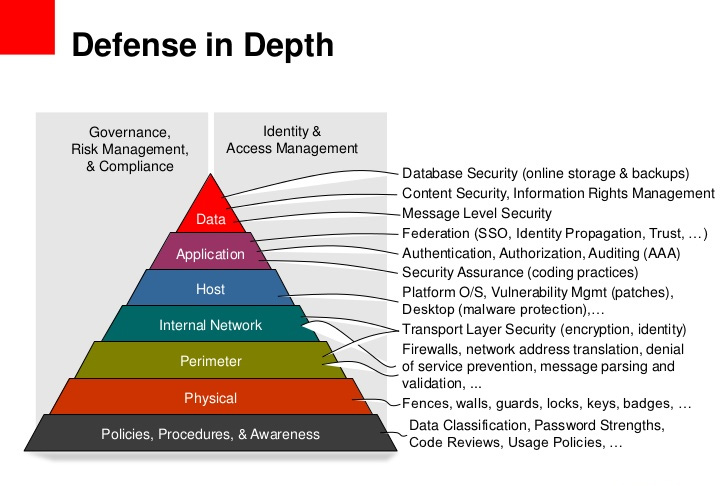
(Darknet, 2017)
Figure 3. Fortification of host nodes
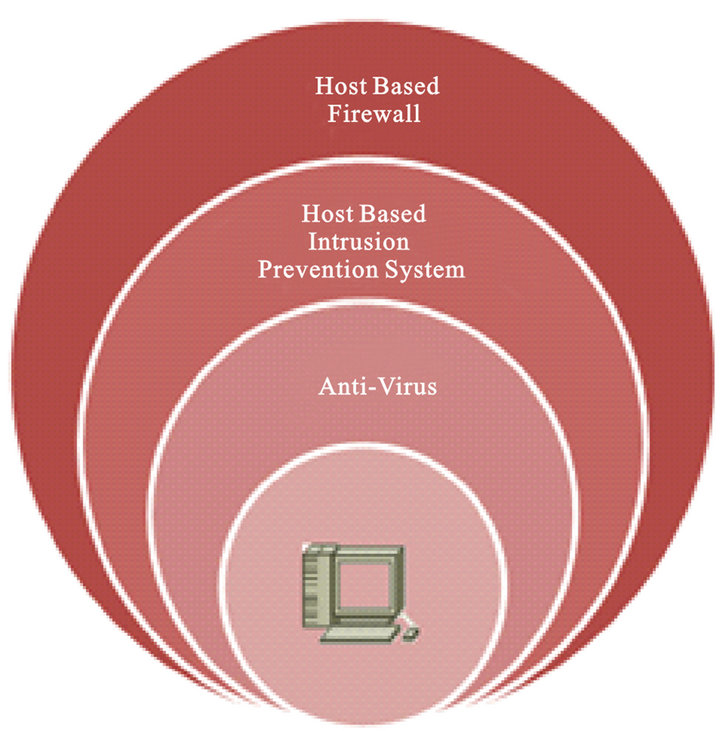
(Cleghorn, 2013)
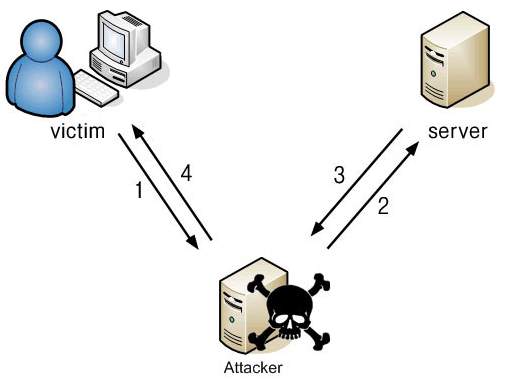
(Mrd, 2018)
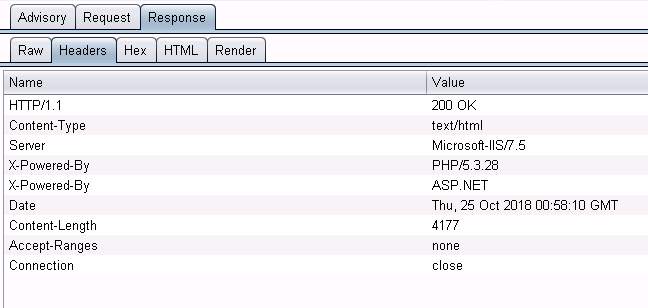

Figure 10. SQL Injection Attack
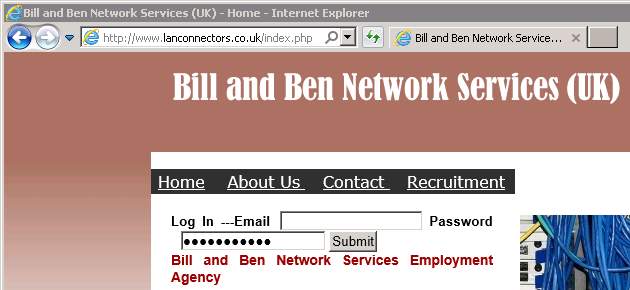
Figure 11. SQL Injection Result
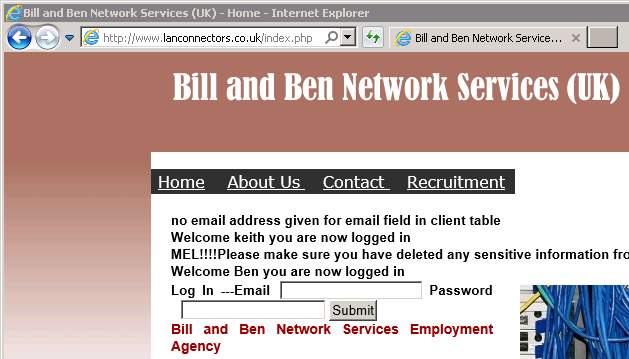
Table 1. Microsoft Server 2019 vs Ubuntu Server 18.04 (2/11/18)
| CVE O/S Vulnerabilities | |
| Microsoft Server 2019 (Mitre, 2018c) | 6 |
| Ubuntu Server 18.04 (Mitre, 2018d) | 3 |
Table 2. Microsoft IIS 7.5 vs Apache 2.4 (2/11/18)
| CVE Web Server Vulnerabilities | |
| Microsoft IIS 7.5 (Mitre, 2018b) | 7 |
| Apache 2.4 (Mitre, 2018a) | 3 |
Table 3. A comparative study of attacks against Corporate IIS and Apache
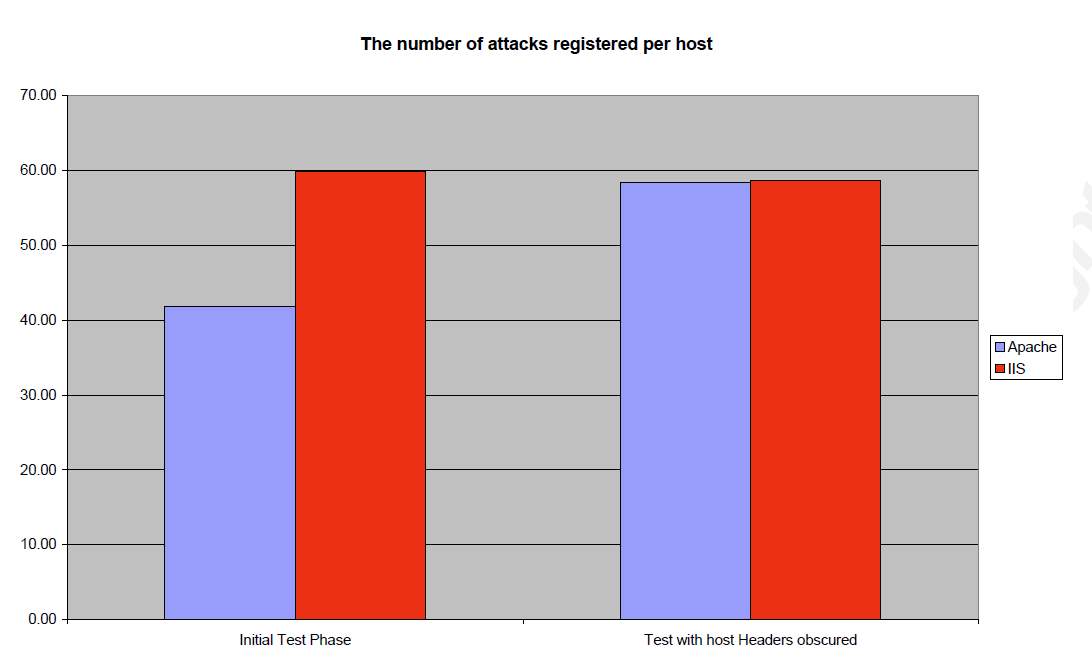
(Wright, 2011)
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




