Cyber-Physical Systems Applications and Features Literature Review
Info: 10724 words (43 pages) Example Literature Review
Published: 9th Dec 2019
Tagged: Information Systems
2 Chapter 2
Past decades witnessed great success and advances in the field of information and communication technology (ICT) which is expected to grow much more in the close future and attract so many attentions. Among the variety of applications in Information Technology field, ICT Embedded components in different devices have become an important component playing a significant role in different aspects of our life.
Embedded systems are defined as computer systems which are designed to perform specific functions, usually in real-time and are embedded as part of a complete system. Embedded systems include different types of devices such as portable devices (e.g. smart phones and MP3 players) and large systems (e.g. plant control systems) [1].
Nowadays, the relation between the cyber world and the physical world has distinguished CPS from traditional embedded systems. CPS main characteristic is the integration of computation and physical processes [1]. In these systems, different devices with computational components are working together in a network and are monitoring, sensing and actuating the elements in the physical world.
There are many different examples and applications of CPS. They include large-scale systems such as health care, automation, transportation and smart grid system. In addition, a new concept is coming up for mobile cyber-physical applications using smart phones and mobile Internet devices that employ multiple sensors [1]. In all different types of CPS, the most important issue is properly understanding and resolving the complicated interaction between physical and computational elements [1]. In these systems, the cyber section is set of control logic and sensor units and the physical section is a set of actuator units [10].
Term “Cyber-Physical Systems” has emerged as an important and critical research topic is the combination of computations, communications and control. Although it is difficult to have one specific definition for this term because of its vast span, it can be depicted as a physical engineering system that its operation is being controlled, monitored and integrated by a computational core.
In CPS, understanding physical and computational processes separately is not enough and sufficient. CPS is about the intersection and it is important to understand the interaction of physical and computation components. [4]
As the connection diagram demonstrates in Figure 2-1, sensors capture and transmit the physical world’s status to CPS and the computational components process the received information. The system then decides which action should be taken based on the result given by computational components and the actions are performed by the actuators. The following steps have been defined by Eric Ke Wang showing the main steps in CPS workflow: [5]
- Monitoring: This is the fundamental function which monitors the physical environment and its processes. Using this function CPS can send feedbacks on previous actions and make sure that operations are correctly done in the future.
- Networking: This function is responsible for aggregating data received from sensors. There are many sensors networked in CPS which are generating data in real-time. Meanwhile, different services need to interact and communicate with the network.
- Computing: The data monitored in step one and aggregated in step two should be analyzed in step three which is computing step. This function is responsible for checking the criteria which are defined previously and decide if the result coming from analysis satisfies that. If not, the computing section executes corrective actions. As an example, the temperature rise can be detected using a data-center CPS.
- Actuation: The results coming from computing elements are sent and executed by actuators. The actions that can be taken by actuators are different types of activities such as correcting the cyber behavior and modifying the physical process. For example, shutting down a system before a probable explosion.
CPS have much more functions, capabilities and services which could not be included in embedded systems. Users can not influence embedded systems. Embedded systems can just help with automated tasks and they are not usually visible to the user. Any possible action needed in embedded systems would be performed under complete control of the user [7]. In opposite to embedded systems, CPS acts based on the data gathered from the physical world in real-time and reacts to this data through predefined orders while cooperating with services, local systems, Internet of Services (IoS) and Internet of Things (IoT) [7].
In summary, CPS focuses on the connection between the physical world and the cyber world while traditional embedded systems concentrate on computational elements. Figure 2-2 shows the structure of a CPS more clearly.
CPS exceeds embedded systems in different aspects. CPS are more reliable, safe, efficient, robust and adaptable [1]. As an instance, with help of a fast response captured from the sensors, the damages of an explosion in gas stations or in a car accident can be avoided. These systems can also help in having more precise robotic surgeries and result in less pain, blood loss etc. As a result, research on CPS is growing faster and is significantly important nowadays. Considering the unlimited applications CPS can enhance humans’ life quality.
1.1. CPS characteristics
Key characteristics of CPS can be summarized as follows:
- System of systems: In contrast to embedded systems, CPS is a complex system, consisting of many subsystems that interact with each other and can also stand-alone. Therefore, the CPS complexity is much more than a traditional individual embedded system [1].
- Interactions between control, communication and computation: CPS should be automated and non-technical factors (human factors) should be all omitted in the control loop. Therefore, the control, communication and computing element should be considered in parallel while designing the system. [1]
- Coupled cyber and physical world: The physical world in CPS should be tightly coupled with the cyber world. Consequently, large-scale wireless and wired networks become significantly important. [1]
1.2. CPS background
In 2008, in the US, President’s Council of Advisors on Science and Technology (PCAST) organization has prioritized CPS as a top federal research investment. Because of the recommendations coming from PCAST about CPS importance, the CPS program was started at the National Science Foundation (NSF) in 2009 [1]. The NSF CPS program concentrates on fundamental issues concerning different sectors such as health care, automotive, energy, transportation and aerospace.
In addition, this program supports developing different components including methods, hardware, software and tools to accelerate the realization and the usage of CPS in different domains. The NFS CPS program also further implemented the CPS Virtual Organization[1] to prepare and increase research and education community for emerging innovations and applications of CPS.
In 2010, several workshops and conferences started regarding CPS and their applications. These conferences were mainly initiated by the cooperation of the ACM and the IEEE. The first conference on CPS (ICCPS), was successful with many interesting paper and sessions. A timeline of CPS history is shown in Figure 2-3.
1.3. CPS applications
Nowadays CPS are being used in various domains including health care systems, assisted living, advanced automotive systems, traffic control and safety, energy conservation, environmental control, critical infrastructure (e.g. power, water), robotics and manufacturing [6]. In this section, three examples of CPS applications, health care and medicine, aerospace, electric power grid and automotive systems are explained.
1.3.1. Health care and medicine
The health care domain consists of home care, operating room, robotic surgery, national health data, electronic patient record, etc. These systems which are mostly controlled by computer systems and some work in real-time require too much safety and accuracy in timing [3].
Health care domain in CPS that is usually called Medical CPS (MCPS) helps doctors and patients to interact with each other easier using the cyber section in CPS to receive better treatment [3]. With the help of MCPS, doctors can monitor patients from far away on remote systems rather than the local stand-alone systems.
The wireless technology significantly improves the safety of health care systems; current complicated massive connections between systems using wires in health care environments often results in a crisscross of cables named ‘‘malignant spaghetti’’, which is a serious vulnerability that puts patients’ lives in danger [1]. Systems’ reliability is of high importance in MCPS and it is one of the researchers’ priorities to enhance the overall reliability by bringing new technologies and theories.
1.3.2. Aerospace
CPS research has a significant impact on the design of aircraft as well as on air traffic management with the aim to significantly improving aviation safety. Some key research issues in aerospace CPS are as follows:
(i) New functionalities to achieve higher capacity, greater safety and more efficiency as well as tradeoffs among their possibly conflicting goals; (ii) integrated flight deck systems, moving from displays and concepts for pilots to future autonomous systems; (iii) vehicle health monitoring and management; (iv) safety research relative to aircraft control systems.
One of the main challenges is design verification and validation of extremely complex flight systems. Since the complexity of flight systems is constantly increasing, the cost of verification and validation also increases. The research on verification and validation of aviation flight-critical systems includes how to provide methodologies for rigorous and systematic high-level validation of various system safety properties and requirements. This is evaluated in all phases ranging from initial design through implementation, maintenance and modification; it is also highly required to understand tradeoffs between.
1.3.3. Power grid
A power grid CPS is formed from the power electronics, power grid and embedded control software. Designing this type of CPS requires a high-level of security, fault tolerance and decentralized control [6]. Recently, research on smart power grid has gained tremendous interests. Development of smart power grids has been of great public interest, which results in a high priority for policymakers. It is a top priority to protect the energy infrastructure from failure as well as outside attacks. For example, under certain unexpected situations, a failure in one location of the electric power grid can propagate across the grid, which leads to plenty of failures and blackouts.
The key objective is to design a robust power grid network by introducing real-time control in the composition of cyber and physical elements in the grid. In particular, security policy, intrusion detection and mitigation must deal with possible outside attacks and should be carefully considered.
1.3.4. Automotive systems
Nowadays vehicle systems are way more advanced than pure mechanical systems. Automotive systems are being used everywhere. Around 30-90 processors are embedded and networked in each car in different sections such as brake system, engine control, airbag system and door locks. [1]. Furthermore, cars may connect to each other and communicate using the Internet, vehicle-to-vehicle networks, or cellular networks [1]. In this situation, safety and security of systems become highly critical. These systems should guarantee reliability for complex networked software.
Automotive CPS has one of the most usages in our everyday life and is one of the most critical ones that should be highly secured as a small accident can damage a lot and take many lives. In the US, currently, almost 42,000 fatal accidents happen each year which could dramatically be reduced using more intelligent systems to help the drivers. Current technologies for collision avoidance are passive and heavily depend on driver’s interaction. Consequently, the automation of collision avoidance is of great interest. With advanced technologies for onboard sensing and in-vehicle computation, as well as with global positioning systems (GPS) and inter-vehicle information exchange, it is expected that near-zero automotive traffic fatalities and significantly reduced traffic congestion are achieved. With the growing development of CPS, some new solutions can be applied to unmanned vehicles. Researchers are working on a program to integrate unmanned vehicles and intelligent roads as a CPS. [6]
1.4. SCADA
SCADA is one type of industrial control systems (ICS) that help to monitor and control operation remotely via communication channels [2]. Existing industrial processes in the physical world can be monitored by ICSs. SCADA is cooperating with many various types of CPS. It can be employed to acquire raw data about the remote equipment’s status and it usually uses different communication channel for each remote station.
SCADA is the core of different industries such as transportation, manufacturing, power, gas, oil, water and many other areas. It cooperates well with many different types of CPS since they can range from simple to complex large configurations and projects. SCADA can be found in our daily life nowadays almost everywhere. It is not easily seen because it is used behind the scenes. You can find SCADA at your local supermarket, wastewater treatment plant, or more importantly the gas stations [2]. SCADA systems employ many software/hardware elements allowing industrial organizations to: [2]
- Aggregate, control, monitor and process data.
- Control devices and interact with them. Devices are connected through human-machine interfaces (HMI).
- Store all events in log files.
In SCADA, PLCs (Programmable Logic Controllers) and/or RTUs (Remote Terminal Units) receive data from sensors and/or manual inputs and send these data to computers which have SCADA software on them. These computers then analyze the data and display the result. SCADA reduces the wasting time and improves efficiency the manufacturing process and may result in significant savings of money and time. Figure 2-4 shows SCADA architecture and the connection between sensors, RTUs, PLC and SCADA system.
1.4.1. Security challenge in SCADA
In contrast to ICSs, SCADA systems are used in large distances for large-scale processes including multiple sites [2]. Many security attacks have been reported against utility assets. Security vulnerabilities in critical systems can lead to fatal disruptions and they may disclose sensitive information. An attacker can execute an attack in less than one hour as soon as system vulnerability is known and its security is compromised. The growing usage of the Internet helps attackers to form an attack from multiple locations. The most dangerous type of attack is when attackers gain access to the supervisory control access and execute disruptive commands [2].
1.5. Architectural topology
There are three main topologies for CPS:
- Centralized topology: In this topology, data is collected from distributed sensors and all sensors and actuators are monitored using one deployed middleware [11]. In this topology, it is easier to manage and control CPS and a more secure environment is provided. However, there are more devices being added every day and it makes every system more complex, therefore, it would be problematic to use this tightly coupled centralized topology.
- Distributed topology: In this topology, a very small “middleware” is implemented on each physical device. This middleware is responsible for controlling the physical part and connecting with other peer-to-peer sections. For instance, a middleware may consist of agents and actors. These entities provide adaptive load balancing and monitoring while moving across networked sensors. As the name of this topology shows it provides scalable systems as it is possible to add as many as physical devices and computing elements are needed without any interference with other elements. On one hand, this topology can minimize the network congestion as there is no bottleneck point in it. But on the other hand, it is not possible to execute complex computation since the physical devices have limited resources and managing the devices gets harder. [11]
- Nested topology: If combine both previous topologies are combined, we get nested topology. The cyber-physical system in this topology can contain more than one local CPS networks which can be either centralized or distributed [11].
1.6. Three-Tiers CPS architecture
Three-tiers CPS architecture includes the following parts: [8]
- Service Tiers: The service tier employs different services such as CC (Cloud Computing) and builds a computing environment.
- Environmental Tiers: Includes physical devices and it is in contact with end-users which are the target environment.
- Control Tiers: Makes controlling decisions based on the monitored information that has been aggregated from sensors. This tier finds the right services with service tier consultant and provides the services which have been requested by physical devices. The three-tiers architecture is shown in Figure 2-5.
1.7. CPS Challenges
CPS is a very active and critical research subject nowadays and researchers need to solve many various questions including architecture layers, the systems design and most importantly physical and cyber worlds’ integration. There are six main challenges discussed in CPS: [6]
- Control and hybrid systems. An updated mathematical theory is required to integrate time-based and event-based systems for feedback control. The theory should suit hybrid systems with different geographic scopes and timescales.
- Sensor and mobile networks. Information gathering and aggregating out of huge amount of unprocessed data is one of the critical steps in CPS. Therefore, a self-organizing and reorganizing mobile network is required for CPS.
- Abstractions. New resource allocation scheme is required for real-time embedded systems and computational abstractions, to make sure that system can achieve scalability, fault tolerance, optimization etc. Therefore, with emerging new technologies and new needs, new distributed real-time computing and communication methods are required.
- Model-based development. Though there are several existing model-based development methods, they are far from meeting demands in CPS. Abstraction and modeling are needed for computing and communications and physical dynamics for a variety of scales, localities and time scopes.
- Verification, validation and certification. Formal methods in different sections should be able to interact easily and safely. Testing methods and compositional verification should be applied to the system.
- Robustness, reliability, safety and security. The most critical issue in CPS concentrates on its safety and security. System safety, robustness, reliability and security, should be guaranteed in uncertain environments, security attacks and errors coming from the physical world and physical devices. The mechanisms in CPS should be time-based, location-based and tag-based to be able to solve and mitigate security problems.
Haung-Ming Haung in [9] has brought up and discussed three important fundamental connected issues in developing and evaluating real-time hybrid CPS:
- Integration of physical and simulated version of components using a reusable middleware architecture;
- Achieving predictable timing over available hardware and software platforms; and
- Interchanging physical versus components’ simulated versions within a system with high accuracy.
Security of CPS can be categorized into three main aspects:
- Perception security, which is to ensure the security and accuracy of the information collected from physical environment;
- Transport security, which is to prevent the data from being destroyed during the transmission processes;
- Processing center security, such as physical security and safety procedures in servers or workstations [8].
1.7.1. CPS intrusion detection
In conclusion, the most important CPS issues are availability, reliability and security. The first two can be affected by security issue. Security is the most significant challenge in critical infrastructures like CPS which is highly integrated into today’s world. As this integration increases, securing CPS becomes more and more important. Compromised sub-system, sensor or node can disrupt the CPS functionality. Therefore, it is of high importance to increase the security in CPS and to decrease the possibility of attacks and intrusions. The best security solutions nowadays are designed with IDS. CPS intrusion detection system has one of the highest priorities in security research in different companies all around the world. This thesis aims to do a survey on challenges of CPS intrusion detection, compare the existing techniques and improve one of the common intrusion detection techniques used in CPS to increase CPS security against cyber-attacks. In the next chapter, a comprehensive survey of the existing CPS intrusion detection techniques is provided. In addition, a classification tree is introduced to organize existing CPS intrusion detection schemes.
3 Chapter 3
Nowadays with increasing speed, efficiency, number and communications of computer systems in critical infrastructure systems, the urge of having more reliable security systems has been significantly increased. During years 1984 to 1986, Peter Neumann and Dorotty Denning, were doing research on the security of systems in real-time, which resulted to produce an IDS based on expert systems. This system was named IDES (Intrusion Detection Expert System) [12]. The idea in their project became the foundation of many IDSs produced after.
CERT (Computer Emergency Response Team) reports that with the daily rise in computer systems and Internet, the number of intrusions has extremely increased [17]. NIST (The National Institute of Standards and Technology) defines intrusion as an effort of an attacker to compromise confidentiality, integration and availability (CIA) or to escape security rules. It also defines intrusion detection as the process of monitoring and analyzing running events to find out if they have signs of efforts for the intrusion. In addition, as programming cannot be done without any mistakes, the rapid change of software application leaves behind too many exploitable vulnerabilities. These issues show the necessity for having IDS as a stronger wall to protect networks against attacks. This necessity is more observable in infrastructural systems such as CPS since they have critical missions and they are connected to the physical world and any damages in these systems may cause huge financial and life loss. IDSs analyze network data to detect and record suspicious events in real-time. IDS are systems which automate the process of detection [13]. In addition, intrusion detection system (IPS) is similar to IDS but can also stop possible attacks [13]. In some articles, the term of intrusion detection and prevention systems (IDPS) is a synonym to IPS, but the term IDPS is rarely used.
Although the traditional prevention methods including user authentication, access control, using firewall and encryption are used in the first step of defense for network security, they are not enough. If users use a weak password, user authentication can be compromised. Firewalls, on the other hand, are vulnerable to error in their configurations and they cannot check the content of the packet. They also can be bypassed by tunnels and are unable to detect malicious mobile code or insider attacks. There are three groups of attackers:
- Attackers that are getting access to the network from the Internet connections;
- Valid users who are trying to get privileged access, however, they are not allowed;
- Valid users that have complete access but they abuse that.
In the following, IDS’s compliments, computer attack taxonomy, potential attacks to CPS and different types of IDSs are examined.
2.1. Complements
IDSs are used as one of the steps to secure computer networks. In other words, IDSs are one of the security systems to protect the networks and other security systems should cooperate with them as complements. These systems have different positions and responsibilities in the network. Some of these compliments are introduced in this section.
2.1.1. Security policy
Security policy is a significantly important step in every security project. Security policy’s aim is to specify the rules that define privileges for users and the security properties which should be satisfied. There are several default standards to be used for designing system frameworks such as ISO 17,799 and ISO 27001. ISO security standards enforce companies for specific norms and requirements [16].
2.1.2. Firewall
The main goal of firewall systems is protecting the network behind it. It is significantly important to have appropriately configured firewalls on every network. Firewalls are capable of checking inside each packet and detect any known attack which matched with the rules inside their table. Firewalls should be configured very carefully by security engineers based on appropriate security policies for the requirements of the organization. A Firewall can restrict malicious access from outside the network. It examines information on the network layer (IP Address), transport layer (port address, multiplexing) and application layer (application) [15].
2.1.3. Authentication and encryption
Encryption is one of the most common and effective ways to retain information. This mechanism has the capability to provide a reliable point to point transmission. It can transfer data between clients, servers and routers. However, encryption cannot be the only way to maintain security. With discovering a vulnerability in the network, the attacker could threaten critical information or the system can be defenseless against DoS attacks. Authentication mechanisms that use username and passwords also cannot be an enough security mechanism, especially when the majority of the users are using weak passwords.
2.1.4. Access control list
Firewalls use a set of rules named access control lists which are written and defined based on security policies of each organization separately. These lists are used to restrict malicious traffics or to define permissions. Attacks cannot be hindered by this list only and they should be enforced to firewalls. As an example, it is possible to restrict access to specific services by a predefined range of IP addresses.
2.2. Computer attack taxonomy
A well-defined taxonomy classifies attacks into categories that have mutual properties. Groups should not overlap since putting an attack into one category excludes it from other categories. Existing and probable attacks to CPS are categorized into four main groups: Probing, denial of service, user to root and remote to user. [18]
2.2.1. Probing
An attack is in the class of probing attacks if an attacker or intruder tries to find information or detect systems’ vulnerabilities in the network by scanning the network. An intruder that can access to a map showing devices on the network can easily scan the vulnerabilities and exploit them. There are various kinds of probes. As an example, some of the probes use social engineering methods and some abuse the features on the device. Probing is one of the most common classes of attack since the attacker does not need to be a technical expert. Attacks in probing class are written in Table 3-1. [18]
2.2.2. Denial of service (DoS) attacks
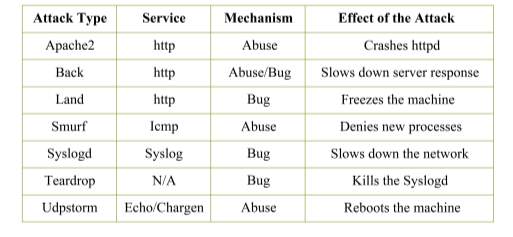
In DoS attack, the intruder spends a lot of memory or computing resources to make server and network occupied so it will not be able to handle other requests for any other services. This stops legitimate users from accessing the system and using services. DoS attacks can be done in different ways:
- To abuse legitimate user’s system features;
- To target implementation bugs;
- To exploit system’s vulnerabilities.
These groups of attacks are categorized based on the services that become unavailable during the attack and authorized user cannot use them anymore. Table 3-2 presents some types of DoS attacks and their impacts.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Information Systems"
Information Systems relates to systems that allow people and businesses to handle and use data in a multitude of ways. Information Systems can assist you in processing and filtering data, and can be used in many different environments.
Related Articles
DMCA / Removal Request
If you are the original writer of this literature review and no longer wish to have your work published on the UKDiss.com website then please:




