Literature Review on Personal Data Online and Data Privacy
Info: 3231 words (13 pages) Example Literature Review
Published: 12th Apr 2021
Tagged: MediaCyber Security
Contents
Online Services and Personal Data
Introduction
This literature review will determine the current issues surrounding privacy and the use of personal data online. The information gathered will show how relevant a solution to the highlighted issues will be – also an understanding of previous or current potential solutions will be beneficial to this project. There also be a small section of information regarding the technologies used to make this project viable in its solution – the software defined technologies will include: ReactJS and Solid. ReactJS is a JavaScript framework which eases the creation of user interfaces (UI) with constantly changing data (usually user dependant data). Solid which is a very new technology, introduced to provide a system which allows the ability to store a user’s data in one or multiple locations, then allow it to communicate with various online services – whilst specific online services will not have any control over the user data it receives.
Context
This project aims to create and implement a solution to solve current issues surrounding privacy and the use of personal data online. The solution aims to be a de-centralised web in theory, with user’s personal data never being stored on third-parties’ filesystems, resulting in the user having full control over their data. Many organisations have become victim to cybercrime, resulting in their user’s personal data being stolen – so a potential solution means that users will have to be responsible for their own personal data.
Online Services and Personal Data
With more users than ever online, rising from 738 million in 2000, to over 3 billion people as of 2015 (Davidson, 2015). Online services are now more common than ever, with a number of organisations considering moving their services entirely online – such as the UK Government who are planning to make their Tax system online only by October 2019 (Overview of Making Tax Digital – GOV.UK, n.d.). The rise of online services has resulted in people storing more personal data online than ever seen before, with the average UK email address being associated with 118 different online accounts (Le Bras, 2015). The higher number of online accounts results in a greater probability of becoming a victim to a data breach, with each of those service providers needing to provide an adequate level of security to protect personal data.
A recent cybercrime report has shown that 43% of UK businesses experience a cyber security breach or attack within a 12 month period (Department for Digital, Culture, 2018). These high probabilities of a cyber-attack show that personal data stored online is very vulnerable. Using online services is not something companies or individuals can avoid, with 98% of businesses relying on some form of online communication such as company emails, websites, or VoIP systems; 92% of companies using emails, 83% of companies using a website or blog; and 56% of companies holding information about customers electronically (Department for Digital, Culture, 2018). Findings by the IT Governance have shown that cybercrime is on the rise; in 2010 there were 3.8 million records breached, in comparison with 2016 where 3.1 billion records were breached. (Graham, 2018)
As seen many organisations are moving online resulting in a rise of online only services, which is also rising alongside cybercrime – dramatically increasing the chances of people becoming victim to a data breach. As of November 2018, according to the Identity Theft Resource Centre there has been 57,667,911 separate online records stolen in 1027 data breaches (Data Breach Category YTD Summary, 2018).
Even organisations as large as Facebook fall victim to cyber-attacks, as seen in 2018 when hackers were able to gain access to over 50 million user accounts (Solon, 2018; Wong Carrie, 2018). If Facebook; one of the world’s largest companies couldn’t protect user’s data, smaller companies would find it near impossible to protect against any type of data breach. Some online services may collect real-time data, such as location tracking which was present in Fitness app PolarFlow, which offers users the ability to see their running history – this type of data resulted in PolarFlow leaking the secret locations of military personnel in active service (Burgess, 2018).
New laws are now being implemented such as the General Data Protection Regulation (GDPR), which will fine organisations up to €20 million or 4% of global annual turnover, if they fail to adequately protect user’s personal data (Key Changes with the General Data Protection Regulation – EUGDPR, 2018). If complete new laws are being introduced it shows that there is a clear motive to solve the current issues with online privacy and the use of personal data.
Data mishandling has evidently been prevalent in various online services, showing that organisations aren’t competently implementing adequate security measures to protect their user’s data. Despite cybersecurity becoming increasingly important people and organisations are still lacking an apparent understanding in how it works (Singer W. and Friedman, 2013). This clear misunderstanding of cybersecurity shows that organisations cannot be trusted to protect user’s data when it is stored on their internal systems. If online service providers can’t protect user’s data a solution needs to be found to enable functionality of these online services, whilst taking away the responsibility of organisations needing to store various sensitive user data.
This project will hope to achieve a potential solution to enable a system to be developed which allows online services to remain functional, by using a user’s personal data, however they shall not be required to store the data on their own internal systems. These findings have shown a definite problem with the use and storage of user’s personal data online; which is made extremely vulnerable by the current issues within cybersecurity. This project will use the information gathered to understand the potential solutions which are currently being developed to solve these issues, with this the project can have greater relevancy in a potential solution.
Online Privacy
The massive losses of personal data in various data breaches has led to concerns surrounding people’s privacy online, with personal data falling into cyber criminal’s hands. Once personal data is stolen users can become victims of identity theft; with cyber criminals seeking financial gain, from making illegal transfers to applying for credit in a victim’s name (Sysnet, n.d.).
Recently, people have become increasingly concerned about their data; as shown by the Information Commission’s Office with a 14.5% rise in data protection complaints (Afifi-Sabet, 2018). This that people are aware there is a rising issue with the use of their data online, which shows a demand for a solution to solve online privacy issues – resulting from the consequences of their data falling into to the wrong hands.
An email address is considered personal data, which can identify a person (Jucan, 2017). The number of email accounts is expected to reach 5.594 billion by the end of 2019 (The Radicati Group Inc, 2015), this is a massive number of users who can be potentially impacted by their email address being victim of a data breach, resulting in serious online privacy issues. There are already 103,446,520 spam emails sent every minute (Hale, 2017), a result of people not being data responsible or organisations leaking the email addresses in a data breach.
Many people became significantly more aware of online privacy after the massive media coverage surrounding Edward Snowden’s whistleblowing, leaking National Security Agency information in 2013 (Preibusch, 2015). There are now 91% of adults in a survey conducted by GfK Group agreeing that consumers have lost control of how their personal information is collected and used by companies (Madden, 2014).
All the statistics and information gathered show there is a clear link between personal data and online privacy. After widespread media coverage regarding online privacy people are now aware of issues, meaning a solution will be extremely important to many users. There have been active attempts to solve online privacy issues, mainly seen from a client side, meaning a user has taken it into their own hands to try and protect their data. This list includes: firewalls, proxy-based anonymisers, routing-based anonymisers, mix-based anonymisers and peer-to-peer anonymisers (Understanding Privacy, 2003). Although this research is not recent computing terms, it remains relevant as many issues raised are still prevalent in recent times. The solutions identified are all potentially viable to the issues found, however they are only successful in hiding identities on the web during any type of communication, but as soon as a user enters any personal information they are putting their online privacy at risk because their identity is then shown to the destination service. This project aims to make the personal data usable by a web service, so it remains functional, however the personal data used will never be stored on a third-parties filesystem. This means the user’s personal data will not be vulnerable during a data breach.
Solid
Solid (Social Linked Data) is a platform which allows users to have complete control over their data online, taking control away from massive corporations; by potentially de-centralising the web, if the Solid project is successful (Wikipedia, 2018).
Solid was introduced by Sir Tim Berners-Lee, inventor of the World Wide Web. To fix many current issues found on the web. He also sees Solid as a step to repair the current state of the internet. (Wikipedia, 2018)
There have also been different potential solutions introduced, as such as the InterPlanetary File System (IPFS), which follows an idea that a single server offering a service is too centralised (Weinberger, 2016). For example, a website would be hosted on many different devices; all delivering their own part of the website (or parts of any other service). This achieves the goal of a de-centralised system to deliver various online services, however once a user enters any personal information their identity would potentially be revealed to more than one device. Therefore, Solid is the superior choice, it will allow for a de-centralised method of using online services whilst restricting online services storing any user’s personal information.
Alongside the IPFS, there has been other methods attempted, some of the solutions found range from proxy anonymisers to peer-to-peer anonymisers, they achieve a goal of making the client’s device anonymous. Although, these solutions do not restrict any web services storing personal data about their client, which would be the point that the user loses their anonymity online. This is another solution which has been considered but falls short as it does not address online privacy issues. Solid enables users to protect their personal data, whilst still being able to use web services as before – and therefore it is the favourable option for this project.
The Solid platform will aid this project in becoming successful and viable as a solution to online privacy issues, by serving as a system to allow de-centralised data to be used on a functional web service.
ReactJS
ReactJS is a JavaScript framework to assist in the creation of user interfaces (UI) used on web services, such as social media platforms, which contain constantly changing user information (e.g. status updates, comments and likes). ReactJS will break these different sections of changing information into components, which are self-contained pieces of code – reducing the resource usage of computers.
ReactJS was chosen as it is used by many popular online services which contain user information; these services include Facebook, Instagram and Airbnb amongst many others (Miller, 2017). If this project enables ReactJS to be functional with Solid it will set a path for other web services to follow. Also, recently Solid has expressed their desire to become compatible with the ReactJS framework (Solid Inrupt, 2018).
Conclusion
This literature review has enabled this project to discover its relevance to find a solution to many apparent issues with the use of personal data and privacy online. It shows that online services need personal data for various reasons, however they are clearly not competent in protecting it; which is what this project is trying to achieve a solution for.
The technologies used set a base to enable users to protect their data online, whilst still being able to use online services. Solid allows online services to communicate with personal data hosted via a pod, they can then use it, but they will not need to be responsible for storing it. Then ReactJS will allow this project to become even more relevant, as many popular online services have been found using ReactJS (Coder Academy, n.d.).
The two technologies will communicate as seen in the diagram below, which is adapted from the official Solid GitHub pages.
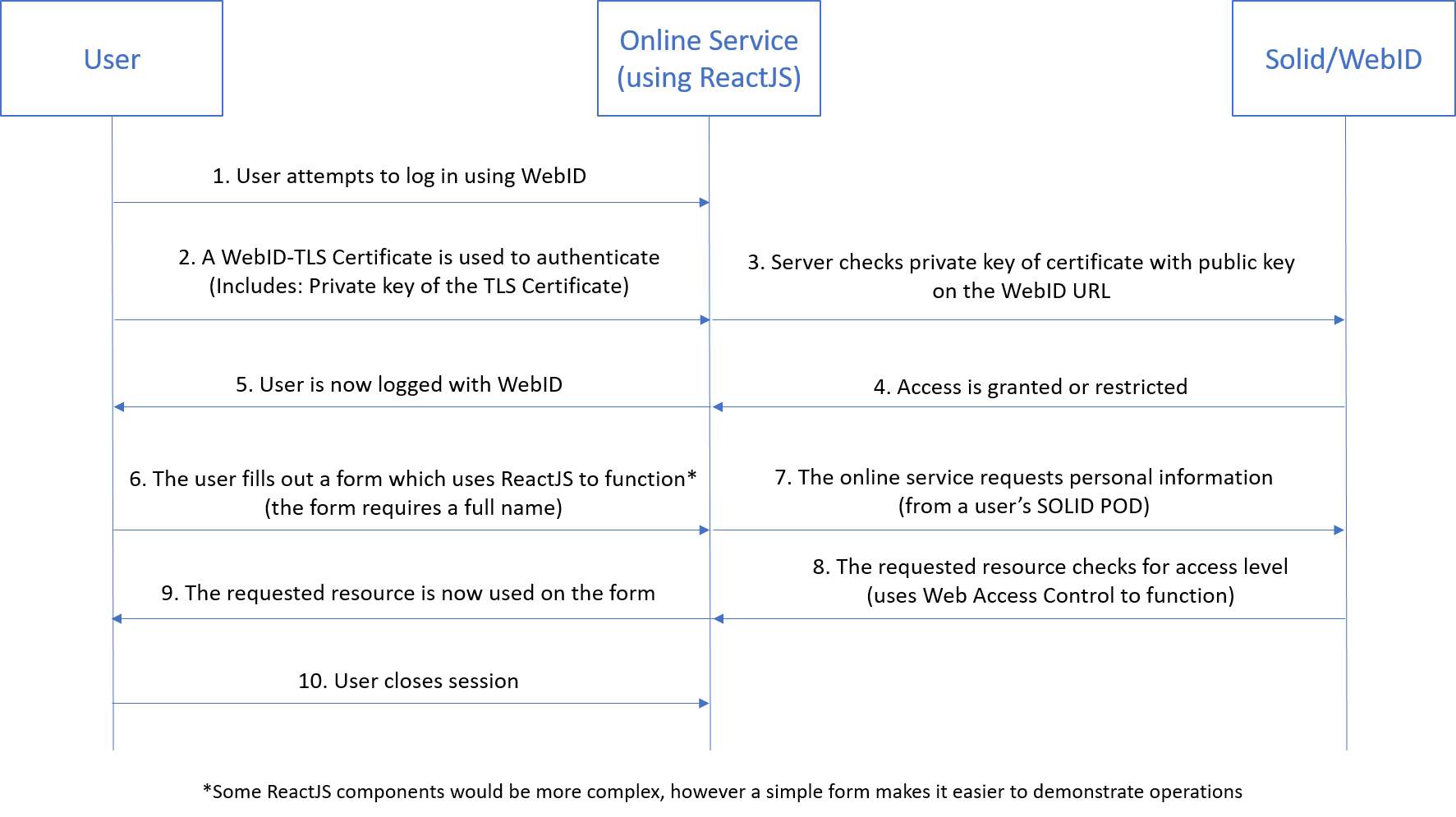
Figure 1 – Adapted from spec guides on GitHub – https://github.com/solid/solid-spec
References
Afifi-Sabet, K. (2018) People are more aware of their data rights than ever before, says ICO | IT PRO. Available at: https://www.itpro.co.uk/information-commissioner/31565/people-are-more-aware-of-their-data-rights-than-ever-before-says-ico (Accessed: 3 December 2018).
Le Bras, T. (2015) Do we have too many passwords? — Blog Dashlane. Available at: https://blog.dashlane.com/infographic-online-overload-its-worse-than-you-thought/ (Accessed: 26 November 2018).
Burgess, M. (2018) The British Airways hack is impressively bad | WIRED UK. Available at: https://www.wired.co.uk/article/hacks-data-breaches-in-2018 (Accessed: 27 November 2018).
Coder Academy (n.d.) Top 32 Sites Built With ReactJS – Coder Academy – Medium. Available at: https://medium.com/@coderacademy/32-sites-built-with-reactjs-172e3a4bed81 (Accessed: 3 December 2018).
Data Breach Category YTD Summary (2018). Available at: https://www.idtheftcenter.org/wp-content/uploads/2018/11/2018-October-Data-Breach-Package.pdf (Accessed: 27 November 2018).
Davidson, J. (2015) 3.2 Billion People Now Using Internet Worldwide | Money. Available at: http://time.com/money/3896219/internet-users-worldwide/ (Accessed: 25 November 2018).
Department for Digital, Culture, M.& S. (2018) Cyber Security Breaches Survey 2018. Available at: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/702074/Cyber_Security_Breaches_Survey_2018_-_Main_Report.pdf (Accessed: 27 November 2018).
Graham, A. (2018) The rise of cyber crime – IT Governance Blog. Available at: https://www.itgovernance.co.uk/blog/the-rise-of-cyber-crime/ (Accessed: 30 October 2018).
Hale, T. (2017) How Much Data Does The World Generate Every Minute? | IFLScience. Available at: https://www.iflscience.com/technology/how-much-data-does-the-world-generate-every-minute/ (Accessed: 3 December 2018).
Jucan, M. (2017) Expert GDPR QA: The material scope of personal data and legal implications – IT Governance Blog. Available at: https://www.itgovernance.eu/blog/en/expert-gdpr-qa-the-material-scope-of-personal-data-and-legal-implications (Accessed: 3 December 2018).
Key Changes with the General Data Protection Regulation – EUGDPR (2018). Available at: https://eugdpr.org/the-regulation/ (Accessed: 27 November 2018).
Madden, M. (2014) Public Perceptions of Privacy and Security in the Post-Snowden Era | Pew Research Center. Available at: http://www.pewinternet.org/2014/11/12/public-privacy-perceptions/ (Accessed: 3 December 2018).
Miller, H.B. (2017) What is Design Thinking? (And What Are The 5 Stages Associated With it?). Available at: https://medium.com/@bhmiller0712/what-is-design-thinking-and-what-are-the-5-stages-associated-with-it-d628152cf220 (Accessed: 30 October 2018).
Overview of Making Tax Digital – GOV.UK (n.d.). Available at: https://www.gov.uk/government/publications/making-tax-digital/overview-of-making-tax-digital (Accessed: 25 November 2018).
Preibusch, S. (2015) Despite continuing media coverage, the public’s privacy behaviors have hardly changed. COMMUNICATIONS OF THE ACM, 58 (5). doi:10.1145/2663341.
Singer W., P. and Friedman, A. (2013) Cybersecurity and Cyberwar : What Everyone Needs to Know. Available at: https://ebookcentral.proquest.com/lib/bcu/reader.action?docID=1538365 (Accessed: 28 November 2018).
Solid Inrupt (2018) Make a Solid app on your lunch break | Solid. Available at: https://solid.inrupt.com/docs/app-on-your-lunch-break (Accessed: 6 December 2018).
Solon, O. (2018) Facebook faces $1.6bn fine and formal investigation over massive data breach | Technology | The Guardian. Available at: https://www.theguardian.com/technology/2018/oct/03/facebook-data-breach-latest-fine-investigation (Accessed: 2 November 2018).
Sysnet (n.d.) What They Do with the Data They Steal. Available at: https://sysnetgs.com/2018/06/what-do-cybercriminals-do-with-the-data-they-steal/ (Accessed: 29 November 2018).
The Radicati Group Inc (2015) Email Statistics Report, 2015-2019. Available at: http://www.radicati.comhttp//www.radicati.com. (Accessed: 3 December 2018).
Understanding Privacy (2003). Available at: http://computer.org/security/ (Accessed: 3 December 2018).
Weinberger, D. (2016) Tim Berners-Lee and Solid Want to Protect Your Data | Digital Trends. Available at: https://www.digitaltrends.com/web/ways-to-decentralize-the-web/ (Accessed: 3 December 2018).
Wikipedia (2018) Solid (web decentralization project). Available at: https://en.wikipedia.org/wiki/Solid_(web_decentralization_project).
Wong Carrie, J. (2018) Facebook says nearly 50m users compromised in huge security breach | Technology | The Guardian. Available at: https://www.theguardian.com/technology/2018/sep/28/facebook-50-million-user-accounts-security-berach (Accessed: 26 November 2018).
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this literature review and no longer wish to have your work published on the UKDiss.com website then please:




