How Technology Has Facilitated Cyber-bullying
Info: 10912 words (44 pages) Dissertation
Published: 1st Mar 2022
Tagged: CriminologyTechnology
Abstract
This paper outlines the findings of the research undertaking to establish how technology facilitates Cyber-bullying within a particular secondary school. The key findings demonstrate that teenagers use different technological platforms to abuse and cause harm that leads to distress for many students. The research sample is a whole year group of Year 10 pupils from a Secondary High School. Two analysis strategies have been under taken to ensure that the correct data is obtained upon completion of this study. These include: questionnaires and interviews. Data was analysed and portrayed in different ways such as tables and figures and the use of content analysis. The results suggest that Cyber-Bullying is a very real issue in schools throughout UK and that strong Anti-Bullying Policies are required in Secondary schools in order to protect those students who are on the receiving end of such abuse.
Table of Contents
Click to expand Table of Contents
Introduction
Project Aim and Objectives
Scope and Rationale
Literature Review
Methodologies
- Epistemology
- Paradigm
- Methodology
- Conceptual Framework:
- Conclusion
Methods
- Questionnaires
- Interviews
- Sampling Strategy
- Validity of Data
- Ethical Considerations
Presentation of Results
- Questionnaire Results
- Interview Results
Discussion of Results
Summary and Conclusion
References
List of Figures and Tables
| Figure Number | Title | Page Number |
| 1 | Frequency of Technology Usage | 12 |
| 2 | Conceptual Framework of the Research | 19 |
| Table Number | Title | Page Number |
| 1 | Types of Bullying Comparison | 25 |
| 2 | Common Terminology Identified | 26 |
| 3 | Common Themes Identified | 26 |
Introduction
The focus of this study is to identify how technology has facilitated Cyber-Bullying. The main emphasis is identifying the different types of technology being used against a group of Year 10 pupils in a Secondary High School. Electronic bullying, online bullying and/or Cyber bullying are new methods of bullying involving forms of bullying defined as harassment using technology such as social websites (MySpace, Facebook), email, chat rooms, mobile phone texting and cameras, picture messaging(sexting), IM(Instant Messaging) and blogs.
The following document will analyse the responses from a group of Year 10 pupils in a Secondary High School to identify the various technology being used during Cyber Bullying. The study will compare and contrast the data acquired through questionnaires and interviews with the intention to update the Anti-Bullying Policy of the Secondary High School of the findings from the study. The findings recognise that the number of teenagers who are on the receiving end of Cyber-Bullying is on the increase and recommendations need to be made to schools to stop the ever increasing use of technology to harm, abuse and intimidate other students in order for them to continue with their education.
Project Aim and Objectives
AimExamine how the use of technology has facilitated Cyber-Bullying in a Secondary High School setting and particular focussing on the Year 10 cohort. |
||
| Objectives | Methodology | Validation |
| To establish and gain a clear understanding on what Cyber-Bullying is. | Literature Review | This will clearly define exactly what Cyber-Bullying is |
| To critically analyse the technology used during Cyber-Bullying. | Literature Review
Questionnaires Interviews |
This will analyse and illustrate the technology used during Cyber-Bullying.
The questionnaire gathers primary data from students. The questionnaires and interviews will also gather qualitative and quantitative data |
| To analyse a cohort of Year 10 students | Questionnaires
Interviews |
This will identify and gather all the parameters required to produce the findings of the project |
| To make recommendations for the Anti-Bullying Policy for the Secondary High School | Questionnaires
Interviews |
The qualitative and quantitative data will be compared to the current Anti-Bullying Policy with the findings updating the Policy to be current and relevant for the school. |
Scope and Rationale
The following description will highlight and describe the limitations and boundaries within the research project. The emphasis of the research project is on the technology used when engaging in Cyber-Bullying. Cyber-Bullying is becoming more and more at the forefront in affecting young peoples’ lives in todays’ society. The ability to Cyber-Bully is not only limited to mobile phones, Instant Messaging, chat rooms, email and webcams but websites, video hosting sites, Virtual Learning Environments(VLE’s) and gaming consoles but other advancements in technology are all responsible for engagement in Cyber-Bullying. This research project will aim to prove that technology, when used incorrectly, has a major impact on the lives of a cohort of students in Year 10. The project will only be focussing on the technology used and not the psychological, behaviours or effects as a result of the findings.
The technology industry is a fast growing industry that has both a positive and negative impact on individuals. As technology is a large and vast part of everyday life the way we use this technology and the research gathered through the use of questionnaires and one-to-one interviews will prove the impact that this has on both individuals and groups. The students will all be asked to participate in a questionnaire for the purpose of the project to collect the primary data. In total there are 83 pupils in this year group. The interviews will be conducted with the consent of the students to gain further understanding into the technologies being used during Cyber-bullying. The constraints on the research are that the actual topic of Cyber-Bullying has only been highlighted in the last decade and therefore accurate, concise and relevant information on this topic is in its infancy.
The assumptions of the research project will prove that when young people are able communicate through the use of technology there is no limitation on how, where and when cyber-bullying is taking place. It will be down to the data and research gathered to prove how technology facilitates Cyber-bullying within the group of year 10 pupils.
Literature Review
When trying to understand what Cyber-Bullying is, it is important to break this down further by trying to establish what the definition of bullying is. According to Elliot (2011:02) ’Bullying is deliberately harming someone who is less powerful than you with the intention of causing pain’. When exploring the exact definition of the term ‘bullying’, what emerges is a slight difference of opinion between writers and authors. Askew (1989) follows a theme in his definition of power and a concept of continuum by identifying bullying as behaviour which involves an attempt to gain power and dominance over another. However, when comparing Askew (1989), with writers such as Herbert(1996) who both identify bullying as a way of being horrible and cruel to another child or group of children whereby the victim may find the behaviour embarrassing, hurtful or humiliating, and be frightened or threatened by it and Rigby(1996), who states that bullying is a repeated oppression, psychological or physical, of a less powerful person by a more powerful person or persons. The themes of hurt, intent, repetition, duration, power and provocation are all vocabulary that can be pinned up upon the word bullying.
What is clear in the comparisons between writers and authors is that experts in the field offer a variety of views of the term bullying, however when schools are devising policies in relation to the term bullying, they are encouraged by the Department of Education(2014), to arrive and their own institutional definition.
More recently, research has demonstrated that advances in technology have provided a new means of bullying. Cyber-Bullying can be defined as a form of covert psychological bullying conveyed through the use of electronic media, such as mobile phones and the internet, that is deliberately intended to harm another (Cowie and Jennifer 2007). It includes bullying by text message or mobile phone calling, by instant messenger services and social networking sites, by email, and by images or videos posted on the internet or mobile phones. Cyber bullying is completely different to other forms of bullying, firstly, cyber-bullying creates a sense of anonymity and a hidden identity that serves to distance the bully from the victim. Secondly, cyber-bullying reaches a far wider audience at a greater speed due to the advances of technology and the internet and finally people that are initially bystanders can easily become engaged in the cyber-bullying.
The types of behaviour that bullies exhibit differs between Cyber-bullying and other types of bullying, for example intimidation, threats, harassment, name calling and insults, social exclusion or peer rejection, identity theft and publication of private information or images are all common within Cyber-Bullying. All of the information above establishes and gains what Cyber-Bullying is (objective 1). Despite the differences mentioned it is important to remember that Cyber-Bullying may form part of a relationship that includes offline and face-to-face bullying as well (Smith et al 2008).
There have been several comprehensive studies in which technology and the youth have been the focus. New research from Mintel (2013) informs us of the following of our UK teenagers:
- 15% of 10-15 year olds are afraid to be left out of there social circle if they are not always on Facebook or Twitter
- 22% of children aged between 10 – 15 feel more free to express themselves online
- 60% of all 15 year olds are smart phone owners
- 45% of 10-15 year olds use a tablet device in the home, significantly exceeding the 36% overall household tablet penetration in the UK.
Research from another country identifies similarities to other countries. Last year McAfee (2013) undertook similar research in Australia and found the following:
- 95% of teens are accessing Facebook daily
- 67% are using social media websites
- On average children between the ages of 8–12 are using between 3 to 4 Internet enabled devices including smart phones andtablets.
The extensive technological involvement by youth is supported by the wide and easily availability of such products. ‘Youth in this day and age live in a virtual candy store of technology’ Trolley (2010: 8). The youth have grown up with continuous advancements in technology. Zwick (2005) argues that Desktop Pc’s are being replaced with more increasingly powerful portable computers.
In terms of occurrence, numerous studies have been conducted in the UK and in other countries to investigate Cyber-Bullying. Li (2006) conducted an anonymous questionnaire survey of 264 students from a High School in Canada and found that:
- 25% of participants had been Cyber-Bullied
- 62% were Cyber-Bullied between 1 and 3 times
- 40% were Cyber-Bullied more than three times
A further study conducted by Livingston and Bober (2005) surveyed over 1,500 nine to nineteen year olds which found that older children were more likely to experience online bullying, with 35 percent 12 to 15 year olds and 44 percent of 16 to 19 year olds reporting this. In the UK, the NSPCC (2013) conducted their own research in 2012/13 and found that online bullying amongst 12-18 year olds has increased by 84% than in the previous years. In particular young people mentioned bullying on social networking sites, chat rooms or gaming sites. From December 2012 to March 2013, the NSPCC (2013) heard from 1,098 young people who mentioned these platforms, a third of whom were aged 13-14.
To further highlight the growing issue of Cyber-Bullying in the UK, a five year study of over 15,000 secondary school pupils in 13 different schools, identified that the frequency with which pupils reported being bullied was directly related to the market up-take in mobile technology and internet connectivity (Noret and Rivers, 2010). Patchin and Hinduja (2006) conducted an internet based survey of 384 respondents of specific online bullying behaviours that young people have experienced and found that over half had been ignored by others (60 percent), half had been disrespected by others (50 percent), nearly one third had been called names by others (30 percent), and one fifth had been threatened by others (21 percent), picked on by others (20 percent), been made fun of by others (19 percent) and experienced rumours spread by others (19 percent). Furthermore, the survey revealed that Cyber-Bullying was most prevalent in chat rooms, with 22 percent of victims reporting this, followed by messaging through computers (14 percent) and email (13 percent).
Cyber-Bullying varies greatly in their estimates of prevalence, ranging anywhere from 4% to 36% of the school population (Noret and Rivers, 2010). The figure below conducted in the research of Noret and Rivers (2010) highlights the frequency to which the different types of technologies were used during their research into Cyber-Bullying.
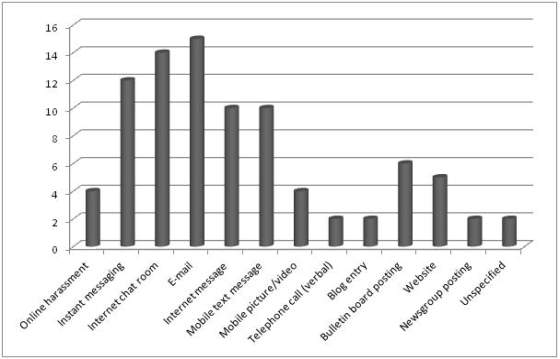
Figure 1: Frequency of technology usage (Noret and Rivers, 2010)
Young people are increasingly using the internet, mobile technology and gaming platforms for a variety of purposes. They offer young people new opportunities in the areas of information, education, social contact and entertainment. Several studies have found that platforms like Instant Messaging (IM), chat boxes and Social Networking Sites(SNS) offer online communication with existing friends and acquaintances (Vandebosch and Heidi 2011). Many teenagers have different technologies that they own, the amount of content they consume and the environment in which they do this. Many teenagers have various devices that resemble pocket media devices, these devices carry meaning as status symbols, for example not owning a trendy mobile phone may be commented on by peers. Mobile phones carry a strong sense of identity and brand and appearance of such devices carry identity and therefore act as a way to differentiate oneself from others. According to teenagers’ cultural frames of reference, the ownership of a communication device is not an individual matter. Rather it is a radically social affair (Caron and Caronia 2007).
The types of Cyber-Environments whereby Cyber-Bullying and harassment are not limited to (objective 2), but include the following:
Instant Messaging (IM) is very similar to emails being past back and forth however the difference is that both parties are online at the same time and are able to send messages back and forth to each other. This dialogue takes place in real time and is usually done through an internet connection. There are many IM programs such as Windows Live Messenger, that are free to use and many of these programs allow ‘chats’ to take place with more than one person. These particular types of programs allow users to create a list of screen contacts and then the program would alert the user when those contacts are online and available to ‘chat’ to. IM’s can only be exchanged between subscribers who have listed each other as contacts (Willard 2006). Users of IM can decide which of their contacts they wish to invite to join a chat, while excluding others. IM is particularly appealing to High School students as students are free to socialize and very familiar with technology.
Chatrooms are also real time written conversations, except that the content is public to everyone in the chat at that time. However, within a chat room, it is possible to ‘move’ to a private chat that is essentially an IM conversation (Willard 2006). This shows how social exclusion can be implemented. Someone in a chat room invites some, but excludes others, from a private chat. This particular form of Cyber-Environment make participants more vulnerable to harmful consequences from Cyber-Bullying. Some chatrooms have features where persons can anonymously post comments for example MUDS (Multi User Dungeons) which is where multiple users are online simultaneously. Unlike chat rooms, people typically do not know each other outside of the environment (Grinter and Palen 2002). In a MUD, participants use avatars to represent themselves to create roles to participate in a fantasy world.
Blogs are similar to diaries, except that they are posted online for public view and comment. Blogs can include both video as well as text. Blogs are very popular in America with 38% of US teens read blogs and 19% have their own blog (Willard 2006). Huffaker and Calvert (2005) observed that 52% of all blogs are those of youth adolescents between ages 13-19. Blogs can be linked to other blogs to create communities of bloggers. These blogs can be platforms for Cyber-Bullies to post comments, thoughts and any other information of others. Many bloggers provide personal information that could be misused by others. Huffaker and Calvert (2005) found that 20% of all teen bloggers provided their real name on blogs and that 44% listed an email address or IM name.
Emails are used to send messages and is more used these days by adults more so than teenagers. It can be employed to send offensive messages to harass and do harm. In research conducted by Tarapdar and Kellett (2011) it was found that the most accessible forms of technology became the most used method of bullying. Abusive emails (26%) were the most popular form of cyber-bullying.
Text Messages are particularly popular in Australia where texting is the preferred method of communicating for teenager between the ages of 14 – 17 (Brown et al 2009). Text messages are short messages using words or abbreviations that can be sent between one mobile phone to any other mobile phones. Most mobile phones these days allow for a digital message to be sent between users.
Happy Slapping was started as a joke in London in 2004 Kraft (2006) and at that time was a particularly nasty form of Cyber-Bullying. Happy Slapping occurs when a target is approached and slapped in the face while a third person captures the incident with the use of a camera. The video then gets uploaded to a website for others to view.
Social Networking Sites such as Facebook, MySpace and Twitter for example include many features as above (email, blogs, chats etc.) and have exactly the same potential to be misused by Cyber-Bullies. The very first incident in the UK whereby a teenager who posted death threats to another teenager received a 3 month sentence in a Youth Offender Institute (Guardian 2009).
Video hosting sites such as YouTube allows users the opportunity to access useful educational, entertaining and original creative video content, however it also provides the user to upload and post embarrassing and humiliating films of someone.
Gaming Sites, Consoles and Virtual Worlds allows users the opportunities to text or voice chat live during online gaming between players across the world, or on handheld devices with people in the same local area. This particular technology allows players to pick on weaker ones by repeatedly name calling, making derogatory remarks and forwarding unwanted messages to other devices in the immediate vicinity.
There are many ways in which society can approach Cyber Bullying; one example of this would be where Rigby and Barrington Thomas (2003) suggest that in schools prevention loomed large in the plans and procedures embraced by most schools. Another way adopted in America according to Phillips and Sianjina (2013) is that agencies within the federal government including the court system and the department of education should assume the responsibility of overseeing the electronic bully policy. Katz (2012) describes in the cycle of bullying intervention, effective bullying prevention is a five stage programme, to be endlessly repeated with tweaks and improvements through constant evaluation and monitoring of its effectiveness. Every single young person in our society should have the right to feel protected by the laws that govern our very own society. For example the Equality Act 2010 (Section 26) states that:
‘Harassment – A person (A) harasses another (B) if –
- A engages in unwanted conduct related to a relevant protected characteristic, and
- The conduct has the purpose or effect of –
- Violating B’s dignity, or
- Creating an intimidating, hostile, degrading, humiliating or offensive environment for B’
Wellfield High School (2014) has its own Anti-Bullying Policy and within this policy it highlights Cyber-Bullying as ‘Cyber-bullying takes different forms: threats and intimidation; harassment or “cyber-stalking” (e.g. repeatedly sending unwanted texts or instant messages); vilification / defamation; exclusion or peer rejection; impersonation; unauthorised publication of private information or images and videos and the manipulation of’.
‘The use of ICT in Cyber-bullying is a fine balance between risks and opportunities’ Katz (2012:26). ‘Experts say that there are missing or shadowy parents and social pressures on kids much earlier than in previous generations. The need to please and be accepted by the peer group that becomes the driving force in teenagers’ lives’ Singh (2007:16). A common theme to the literature states that technology plays an important role in the everyday lives of teenagers. As modern advancements in technology increase, so does the use and the popularity of these technologies and devices, however the way that the technology is used to abuse individuals or groups of people during cyber-bullying creates a major and a common problem for students, parents and professionals.
Methodologies
This section will explain the methodology used to investigate how technology facilitates Cyber-Bullying. The epistemological approach within the document will be justified through the comparison of the researcher’s knowledge and the data acquired through research. The document will also explain approaches to both qualitative and quantitative data collection methods through the use of triangulation methods to gain the desired data and how they will be used in the study. The section will then explore the two different methods adopted during data collection and reference these to the outcomes of the research project.
Epistemology
All research is about knowledge. This research will adopt both a positivist and interpretivist epistemological approach to gain further understanding on how theories on knowledge would reflect upon the evidence gathered by the researcher. Audi (2011) describes that being justified in believing something is having justification for believing it, this narrowed down further means that justified belief is a good backbone for knowledge.
(Fantl et al 2008) describe epistemology as ‘a philosophical enquiry into the nature, conditions and extent of human knowledge’. The approach adopted in this research allowed the researcher to gather data through consultations and interactions with the cohort of students and the interpretations of the researcher to ultimately induce an epistemological approach. This study will allow the research to be gathered, interpreted and the results be published to enable the researcher to understand how technology facilitates Cyber-Bullying.
Paradigm
Lincoln (1998) insists that human behaviour, unlike physical objects, cannot be understood without reference to the meanings and purposes. The researcher adopted approaches in a ‘stand off’ between a ‘qualitative scholar’ and a ‘quantitative scholar’. The ‘qualitative scholar’ will adopt approaches from ethnology, archival research and textual criticism however the ‘quantitative scholar will make use of mathematics, and statistics. By combining elements of quantitative and qualitative paradigms, the validity of the research findings may be enhanced because the different methods being used, questionnaires and interviews will complement each other and the value of the study will be enhanced by using the mixed methodology approach. A pattern and trend that is developing amongst young people is the link drawn with Cyber-Bullying and technology.
Methodology
The type of methodological stand point that this particular piece of research is a combination of both Positivism and Interpretivism. A combination of the researcher interacting with the students during the interview process, highlights the cross over into Interpretivism. However the true hard data that is required for this research requires the methodological approach to encompass elements of Positivism. The use of questionnaires to gather the data shows that elements of positivism will be required to acquiring the primary data, but is not the only methodological approach to the research. Della and Keating (2008) state that ‘Methodological debates are often framed as a confrontation between the quantitative methodologies used by positivists and the qualitative ones used by constructivists and interpretivists. According to Cresswell (2011) the complexity of our research problems calls for answers beyond simple numbers in a quantitative sense or words in a qualitative sense.
Newman (1998:43) states that ‘multivariate research is based on the complexities of most human and social science research. More than one variable is always operating in the questions researchers ask’. Triangulation is restricted to the use of multiple data gathering techniques, usually three, to investigate the same phenomenon (Berg and Lune 2014). The research methodology conducted through the use of primary qualitative studies does not exclude the quantitative data gathering techniques adopted. The gathering of data in a school setting would describe the ethnography as being distinctive as the researcher would be required to engage with the group on its own ground. The role of the researcher varies according to the level of involvement. During the gathering of the primary data through the use of questionnaires, the researcher would be unobtrusive, however the engagement level during the interview stage may vary and therefore the researcher becomes more involved. Ethnography is an ideal method for deriving meaning from social lives that might otherwise go hidden or unnoticed (Berg and Lune 2014), however this approach would not be adopted as the method of collection does not involve participant observation by the researcher. According to Meyerhoff and Schleef (2010) the researcher develops personal associations with members of community and then becomes a member of it.
Conceptual Framework:
A conceptual framework has been derived to show the theory that underpins the research project. The framework has been used to show the factors and relationships that occur between the topics, which are all key in this study. All the topics are directly and/or indirectly linked to each other and must be considered through the research.
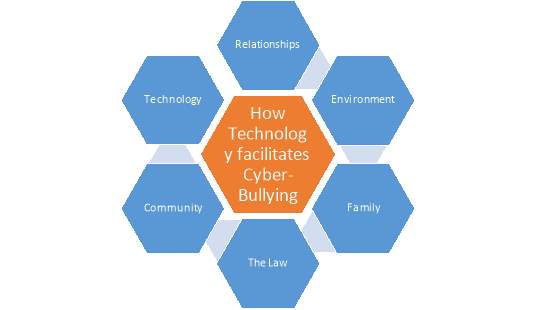
Figure 2: Conceptual Framework of the Research
Conclusion
The purpose of the research methodology is to capture the voices of the Year 10 students who have been Cyber-Bullied. The methodology uses a mixed methods approach that involves both positivist and interpretivist elements that will provide the research with clarity and specific data from the implementation of multivariate research undertaken. The collection of data through the use of questionnaires and interviews will add to the researcher’s knowledge of the topic and therefore justifying the epistemological approach and reasoning behind the paradigms adopted when conducting research into Cyber-Bullying.
Methods
The methods adopted for the research project will vary between questionnaires and interviews. The focus will be on a group of Year 10 students that will include a mix of high/low achievers and pupils with SEND (Special Educational Needs and Disabilities). Focus groups were looked at as an alternative method for information gathering. According to Creswell (2011) the researcher engages in a sampling procedure that involves determining the location or site for the research, identifies the participants who will provide data in the study and how they will be sampled. Cresswell (2011) also ascertains the number of participants needed to answer the research and the recruitment procedures for participants to engage in the research.
Questionnaires
A Questionnaire is a method of issuing participants with a series of questions to gain data. The ways in which the questions are structured are essential to the quality of the data. If questions are worded poorly, this will reflect in the quality of the data that has been gathered (Proctor and Van Zandt, 2011). It is also very important when working with young people, to take into account their understanding of words and therefore the questions within the questionnaire would need to be worded and phrased accordingly. Proctor and Van Zandt (2011) highlight that a common issue when conducting questionnaires is their unreliability, if people do complete them, then they may forget to return them or ultimately they may ignore the questionnaire completely. The nature of anonymity granted through the completion of questionnaires has its positives, as suggested by Gilham (2000), results obtained are likely to be more accurate as a result of anonymity. This method has been chosen to collect both quantitative and qualitative data whereby the use of both open ended and closed questions will provide the grouping of data that is required to critically analyse the technology used during Cyber-Bullying (objective 1), and to analyse the cohort of year 10 students (objective 2). The distribution of the questionnaires was on paper during an assembly morning to 84 students. This method is important because a large amount of data will be gained. The final aspect that the use of this method will enable the researcher to make recommendations for the Anti-Bullying Policy of the Secondary High School (objective 3). A copy of the questionnaire is available in the appendix.
Interviews
Interviewing may be defined simply as a conversation with a purpose. Specifically, the purpose is to gather information (Berg 2014). There are three different types of interviews, the standardised interview, the semi-standardised interview and the un-standardised interview. Merriam (2002) agrees with Berg (2014) as interviews range from highly structured, where specific questions and the order in which they are asked are determined ahead of time, to unstructured, where one has topic areas to explore but neither the questions nor the order are predetermined. For the purpose of this research and the group of young people that will be researched, the standardised interview will be used. The rationale behind this decision is that to gain the relevant information, the questions will be simple enough to understand which allows the subjects to understand clearly what they are being asked.
The sequencing, phrasing and level of language adopted in the interview will be considered accordingly and adopted for the purpose of gaining the relevant information. The interviewer will need to be aware that the topic could be sensitive to some young people and may result in those feeling manipulated by the questions being asked. The risk involved with the sensitive nature of the topic could be that the young people will drop out from the interview and the researcher would not be able to use the data. The benefits from those young people that do complete the interview will be deliberate, knowledgeable and unforced. The researcher will ask the pupils to self-nominate to participate in the interview in order to identify and gather the parameters for the project. The researcher has conducted an interview with two participants, one who has been bullied and another who was the bullying order for there to be consistency with the results obtained during the collection and analyses of the cohort of Year 10 students (objective 3). The data that will be collected during the interviews will also allow the researcher to focus specifically on the technology used during Cyber-Bullying (objective 2). A copy of the interview questions are available in the appendix.
Sampling Strategy
The sampling strategy that has been employed by the researcher took into account many considerations. One of the methodological issues that needed to be recognised first, was the actual sample size using questionnaires. The researcher specifically did not want to sample the whole school, however the researcher understood that the likelihood of the precision sample may increase the number of errors. Bryman (2008) states that the less sampling error one is willing to tolerate, the larger a sample will need to be. However, Fowler (1993) argues against this point by declaring that in practice researchers do not base their decisions about sample size on a single estimate of a variable. He also observes that it is not normal for survey researchers to be in a position to specify in advance an ‘a desired level of precision’ (Fowler,1993: 34).
Another consideration that the researcher needed to take into account was non-response, this did not occur within this research as all the students that were present on the day of the data collection, completed the questionnaire. The only issue that did occur, which was out of the control of the researcher, was absenteeism. A good response rate from the questionnaires that were handed out was based on the non-probability sample and specifically convenience sampling. A convenience sample is ‘one that is simply available to the researcher by virtue of its accessibility’ Bryman (2008: 183). As a convenience strategy was employed, the researcher also considered a quota sample of a non-probability sample however this particular sample would represent students within different categories. The researcher conducted a standardised interview in order to collect the qualitative data required. The reasoning behind the decision is that it would entail far more accuracy in processing the answers compared to questionnaires, with many questions being closed or closed ended. These type of questions allow for the respondents to reply with limited answers and therefore variability is reduced.
Validity of Data
Validity is a function of the correlation between the response and that true value Groves et al (2009). This research implemented the three standards that all surveys should meet, content standards, cognitive standards and usability standards. The students themselves could provide data that is inaccurate when they complete the questionnaires as they may get bored and feel that the topic is not relevant to them if they have not been Cyber-Bullied. Absenteeism on the day may not provide the project with sufficient data however the year group as a whole has 97% attendance for the year thus far.
Ethical Considerations
To correctly adhere to the ethical standards, permission from the Secondary High School’s Headmaster (refer to Appendix 3) and the parents or guardians of the young people participating in the research was obtained. The researcher adhered to the ethical guidelines for educational research (refer to Appendix 2).
Technology can have a huge impact on young people being Cyber-Bullied, however it is important to show that no bias is shown in the research, this is done by directing a participant to give the result or answer other than their own. Bias is known to distort results Page et al (2012) and therefore must be avoided. This puts more emphasis on the phrasing of questions and especially during interviews, the researcher will need to prompt for more information. ‘It is vitally important to remember that all participants within the research project are voluntary’ Polonsky (2004) and therefore the participants must be given the opportunity to withdraw from the research process. Two key terms, anonymity and confidentiality, must not be confused when conducting the research. Confidentiality according to Nation (1997) denotes an implicit or explicit arrangement that no record of a participant’s data will be disclosed. Anonymity is a condition, according to Weiss (2000) in which the researcher does not know the identity of a participant.
Presentation of Results
This section will discuss the results that have been obtained whilst conducting the research. A large sample, a whole year group, of students were selected and questionnaires were handed out to these students. Interviews were also conducted with two students who volunteered to be interviewed.
Questionnaire Results
Questionnaires were given out to 83 students from a year group of which 74 students completed the questionnaire. All the students had the option of not completing the questionnaire or to complete it in their own time. For the purpose of anonymity all students were requested not to add their name to the questionnaire.
The key results of the questionnaire are as follows:
- 19% of students have either been bullied at school or at home in the past year.
- Of those students that have been bullied at school, 88% of students have been bullied through Cyber-Bullying while at school.
- Text Messaging, Pictures or Video Clips and Instant Messaging are the most common ways that Cyber-Bullying is taking place.
- Of all the students that have been victims of Cyber-Bullying, the most common place that this occurs is in the same class as the Cyber-Bully with 60% of students confirming this.
- 70% of all Cyber-Bullies are Female.
- 59% of students stated that Cyber-Bullying lasts approximately for 6 months.
- 44% of all students believe that banning mobile phones in school will not stop Cyber-Bullying with another 38% believing that students will continue with the Cyber-Bullying after school.
- 70% of students have informed an adult at school that they are being Cyber-Bullied.
The table below further highlights the key results of the questionnaire.
| Types of Bullying | During School | Outside of school |
| Text Messaging | 11% | 16% |
| Pictures or Video Clips | 7% | 8% |
| Phone Call | 7% | 1% |
| Emailing | 0% | 1% |
| Chat Room | 5% | 1% |
| Instant Messaging | 7% | 4% |
| Website Bullying | 3% | 1% |
| Any other Forms | 7% | 0% |
Table 1: Types of bullying comparison
Interview Results
The results gathered from the questionnaires enabled the researcher to gain an overall perspective of Cyber-Bullying within the Year 10 student group, however for more finite, accurate and specific information, then an interview would need to take place in order to gather further detailed information. The interviewer asked the group of Year 10 students for two volunteers to complete in the interview process. The interviews were conducted with both a victim of bullying and a bully present as more of a discussion. This would enable the researcher to focus on the schism that exists between both individuals with the intention to identify specifics required to meet the overall aims objectives of the study. The researcher adopted the process of coding qualitative data. According to the Center for Evaluation and Research (2012), coding is the process of organising and sorting your data. When the researcher conducted the interviews, the students involved in the process were very limited in their answers, even when prompted further. With the data that was collected, the researcher was able to summarise and synthesize as seen below in Table 2.
The data in column three below highlights common terminology that was mentioned when the interview was conducted. From this common terminology, it then became apparent that four main themes could be deduced, these included technology, reasoning, venue and information sharing.
| Pre-Set Code Number | Common Themes | Terminology related to the Theme |
| 1 | Technology | Texts, Mobiles, Computers, Facebook, Online Gaming |
| 2 | Reasoning | Around others, Easy, Fall outs |
| 3 | Venue | School, Outside School |
| 4 | Information Sharing | Teacher |
Table 2: Common Terminology identified
The transcript was then broken down again, to summarise the common themes according to their use from the bully and the victim.
| Common Themes | The Bully | The Victim |
| Technology | Texts, Mobiles, Computers, Facebook and Online Gaming | Facebook, Computers, Social Media and Mobiles |
| Reasoning | Easy to do, disagreements and around many | Easy Targets |
| Venue | When able to | Both during and Outside school |
| Information Sharing | School and Teacher |
Table 3: Common Themes identified
The process of breaking down the transcript according to the individuals involved enabled the researcher to identify any emerging themes, no emerging themes existed in this research. A combination of qualitative data and quantitative data through the use of interviews and questionnaires, enabled the researcher to arrive at the following conclusions from the data gathered:
- 100% of students have an electronic media device.
- The victims of Cyber-Bullying all agree that the bullies will find a way to bully using any technology available to them.
- 7% of male students now believe that online gaming is rapidly becoming the next generation of Cyber-Bullying.
- Only 14% students informed their parents that they were Cyber-Bullied, fearing repercussions in school if they told their parents.
The method that was not used in the validation of data was focus groups. During the cross checking of the data obtained through triangulation, it was felt that this method may be counterproductive as a risk to compromising the unique contribution of the individuals involved in the process.
Discussion of Results
As identified in the key literature (e.g. Katz 2012, Singh 2007), it was stated that the use of technology is vitally important in the way teenagers communicate. It was also highlighted in previous studies conducted (e.g. Noret and Rivers 2010, Mintel 2013 and Mcafee 2013) that Cyber-Bullying is fast becoming an issue that is affecting teenagers, not only in this country, but other countries too. Through the analysis of the data, the vast majority of students in Year 10 within the Secondary High School are not or have not been Cyber-Bullied. However, of those that are currently being bullied through Cyber-Bullying, text messaging, picture messaging and instant messaging are by far the most commonly used method. The key results obtained from the questionnaire do raise some very interesting and thought provoking questions. The results suggest that 88% of students that have been bullied, have been a victim of Cyber Bullying while at school. This in itself is a very high figure especially when the current Anti-Bullying Policy stipulates that any student caught committing the bullying will face certain sanctions. The underlying question that exists is, is the current policy strong enough to deter those that engage in the harassment. Livingston and Bober (2009) conducted research for 9 – 19 year olds highlighting the fact the older students are more likely to be Cyber-Bullied, however contradicting this research is McAfee (2013) who found that on average children between the ages of 8-12 year olds are using between 3-4 internet abled devices including smart phones and tablets which potentially leaves them vulnerable to becoming Cyber-Bullied. The analysis of results clearly shows that when students are Cyber-Bullied it lasts for between one month and six months, with six months being the most common timeframe. The main focus of the research was to understand how technology has facilitated Cyber-Bullying, the data that has been collected uniquely identifies that there is no real differences to the technology being used either by a bully or through which means the victim is being reached during Cyber-Bullying, the key differences that do exist are the impact that this has on the individuals, however this research does not delve into the complexities of the emotional behaviours of the individuals. Technological advances allow for communication between individuals and groups to be more prominent than in previous years, however certain technologies appear both in this research and in research conducted 5 years ago. It is clear from the literature review and the study conducted by Noret and Rivers (2010) that Instant Messaging is prevalent throughout, this coincides with the research gathered in this study whereby this type of technology appears again and used continuously both during and after school.
The data that has been gathered has enabled the researcher to make recommendations to the Secondary High School concerned and in particular its Anti-Bullying Policy. The recommendations are as follows:
- Creating a specific e-Safety Charter to the School.
- Not allowing any students to enter school with any mobile phone.
- Educate pupils through assemblies on a half termly basis of the impact of Cyber-Bullying.
- Greater sanctions for pupils found to be Cyber-Bullying.
- Encouraging parents to monitor their Sons/Daughters internet activity.
The students also make various recommendations to try and stop the Cyber-Bullying when it begins, changing phone numbers, switching off the device and informing members of staff at the school are all methods that they feel will enable them to stop becoming victims of Cyber-Bullies.
Summary and Conclusion
The research conducted has frequently challenged the thoughts and feelings that have been collected through the key literature. Research has been obtained and gathered that has questioned beliefs from authors and professionals that have been questioned and disproved. In some instances, the research that has been gathered has corresponded with beliefs and the research has acted to support the claims made by the authors. The aim of the research is to examine how the use of technology has facilitated Cyber-Bullying in a Secondary High School setting and particular focussing on the Year 10 cohort within a Secondary High School. The aim has been thoroughly met through the extensive research conducted in the literature review by comparing the literature of authors and professionals, using data that has been collected through other organisations and critically analysing this against the data collected at the Secondary High School. A concise definition of Cyber-Bullying still remains open for debate amongst authors. Common themes do exist between well-established authors (e.g. Askew 1989, Herbert 1996 and Rigby 1996) however what is consistent is that Cyber-Bullying is repetitive, hurtful and deliberate acts towards the victims (objective 1). The opportunity to critically analyse the technology used during Cyber-Bullying (objective 2) provided prospects to use real-life data and compare this data against organisations (McAfee 2013, Mintel 2013, NSPCC 2013) and results of data collected in Canada (Li 2006) and other authors (Livingston and Bober 2005, Patchin and Hiduja 2006). A common theme that occurs throughout is that as different technologies are being introduced to young people, the Cyber-Bullies are making use of these technologies. Through the use of questionnaires and interviews, primary data was collected to analyse a cohort of Year 10 students (objective 3). The comparison of results and data from various means and sources would allow the research conducted to make recommendation for the Anti-Bullying Policy for the Secondary High School (objective 4). This recommendation would hopefully restrict the opportunities for Cyber-Bullying to take place at school as an update on the current policy would be implemented in preparation for the new academic year in 2015.
Throughout the completion of this research project, questions have arisen that need to be investigated further. The questions identified are:
- Do all Secondary High Schools have a strong enough Anti-Bullying Policy in place to protect their students?
- Are teachers and staff doing enough in the classroom to deal with and stop Cyber-Bullying from occurring?
- Does the organisations that develop communication enabled technology protect young people of all ages from being Cyber-Bullied?
- Are the laws that govern our society strong enough to halt the continuous misuse of technology in relation to Cyber-Bullying?
This has been a very valuable research project and one that has highlighted the greater need to educate students, parents and school staff on an issue that sometimes goes unnoticed for periods of time. In an era when students are bombarded with the pressures of achieving good results, we sometimes miss the impact that Cyber-Bullying can have on individuals and those around them such as families, friends and the communities they represent. Alongside the pressures of achieving well, students also have to deal with looking good in their social circles, this includes having the latest technology or gadgets. As the research has suggested, we live in a world whereby technology plays an important role in our everyday lives and in particular from a social point of view, however what sometimes occurs when this technology is abused and misused results in negative behaviours towards others. These negative behaviours are either occurring in school or at home and what has been learnt from the research is that nowhere is safe for the victim if the bully is able to access any form of technology.
References
Askew, S. 1989. Aggressive behaviour in Boys: to what extent is it institutionalised. Stoke on Trent : Trentham Books.
Audi R., 2011. EPISTOMOLOGY: A Contemporary Introduction to the theory of knowledge. Abingdon: Routledge.
Belsey, B. 2014. Cyberbullying [online]. Available from: http://www.cyberbullying.ca/ [accessed 9 October 2014].
Berg B., Lune, H. 2014. Qualitative Research Methods for the Social Sciences. Harlow : Pearson Education Limited.
Brown, K., Jackson M. and Cassidy, W. 2009. Sticks and Stones Can Break My Bones, But How Can Pixels Hurt Me? Journal of School Psychology International [online]. 30 (4), pp. 383 – 402. Available from: http://spi.sagepub.com/content/30/4/383.refs [Accessed 30 December 2014].
Bryman, A. 2008. Social Research Methods. NY, US: Oxford University Press.
Caron, A.H and Caronia, L. 2007. Moving cultures. Mobile Communication in everyday life. Montreal, Canada : McGill – Queens University Press.
Center for Evaluation and Research. 2012. Coding Qualitative Data [online]. Available from: http://tobaccoeval.ucdavis.edu/analysis-reporting/documents/CodingQualitativeData.pdf [Accessed: 13 March 2015].
Cowie, H and Jennifer, D. 2007. Managing Violence in Schools: A Whole School Approach to Best Practice. London:Sage Publications.
Creswell J.,2011. Designing and conducting mixed methods research. Thousand Oaks, CA: Sage.
Della Porta D., Keating M., 2008. Approaches and Methodologies in the Social Sciences. Cambridge, UK : University Press.
DEPARTMENT OF EDUCATION. 2014. Preventing and Tackling Bullying [online]. Available from: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/368340/preventing_and_tackling_bullying_october14.pdf [Accessed 22 December 2014].
Edmunds H., (2000). The Focus Group Research Handbook. Thousand Oaks, CA: Sage.
Elliott, M. 2011. The Essential Guide to Tackling Bullying. Harlow:Pearson Education Ltd.
Fantl J., Kim J.,McGrath M., Sosa E,. 2008. Epistemology An Anthology. Oxford: Blackwell.
Flick, U. 2014. An introduction to Qualitative Research. London : Sage Publications.
Fowler, F.J. 1993. Survey Research Methods. Newbury Park, California : Sage.
Gillham B., 2000. Developing a Questionnaire. London:Continum.
GREAT BRITAIN. PARLIAMENT, 2010. Equality Act 2010, Chapter 26. London: HMSO.
Grinter, R.E. and Palen, L. 2002. Instant Messaging in Teen Life [online]. Available from: https://www.cs.colorado.edu/~palen/Papers/grinter-palen-IM.pdf [Accessed 30 December 2012].
Groves, R., Fowler, F., Couper, M., Lepkowski, J., Singer, E., Tourangeau, R. 2009. Survey Methodology. NJ, US : John Wiley & Sons.
Herbert, C. 1996. Stop the Bullying. Cambridge:Carrie Herbert Press.
Huffaker,D.A. and Calvert, S.L. 2005. Gender, Identity and Language Use in Teenage Blogs. Journal of Computer-Mediated Communication [online]. 10 (2), pp. 00. Available from: http://onlinelibrary.wiley.com/doi/10.1111/j.1083-6101.2005.tb00238.x/full [Accessed 30 December 2014].
Hunter,N.,2012. Hot Topics Cyber Bullying. London:Raintree.
Katz, A., 2012.Cyberbullying and e-safety: what educators and other professionals need to know. London: Jessica Kingsley Publishers.
Kraft, E. 2006. Cyberbullying in a Rural Intermediate School: An Exploratory Study. Journal of Early Adolescence [online]. 30 (6), pp. 803 – 833. Available from: http://jea.sagepub.com/content/30/6/803.full.pdf+html [Accessed 30 December 2014].
Li, Q. 2006. Cyber bullying in schools : a research of gender differences. Journal of School Psychology International [online]. 27 (2), pp. 157 – 170. Available from: http://spi.sagepub.com/content/27/2/157.short [Accessed 23 December 2014].
Lincoln,D. 1998. The landscape of qualitative research. London: Sage.
Livingstone, S and Bober, M. 2005. UK Children Go Online : final report of key project findings [online]. London : LSE Research Online. Available from : http://eprints.lse.ac.uk/399/1/UKCGO_Final_report.pdf [Accessed 23 December 2014].
McAFEE Blog Central, 2013. Australian Tweens, Teens and Technology [online]. Available from: http://blogs.mcafee.com/consumer/australian-tweens-teens-and-technology [accessed 09 October 2014].
Merriam S., 2002. Qualitative Research in Practice. San Francisco, CA : Jossey-Bass.
Meyerhoff M., Schleef, E. 2010. The Routledge sociolinguistics Reader. NY, US : Routledge.
MINTEL, 2013. Half a million children aged 10-15 afraid to be left out of their social circle if not “always on” Facebook or Twitter [online]. Available from: http://www.mintel.com/press-centre/technology-press-centre/social-media-and-teenagers [Accessed 09 October 2014].
Nation J., 1997. Research Methods. NJ : Prentice – Hall.
Newman I., 1998. Qualitative Quantitative Research Methodology. Southern Illinois University,USA: Southern Illinois University Press.
NSPCC, 2013. What’s affecting children in 2013 [online]. Available from: http://www.nspcc.org.uk/globalassets/documents/research-reports/childline-review-2012-2013.pdf [Accessed 23 December 2014].
Ong, R.Y.C., 2010. Mobile Communication and the Protection of Children [ebook]. Amsterdam, NLD: Leiden University Press. Available from: http://0-site.ebrary.com.library.edgehill.ac.uk/lib/edgehill/detail.action?docID=10493666 [Accessed 18 October 2014].
Page P., Carr J., Eardley W., Chadwick D., Porter K. 2012. An Introduction to Clinical Research. London : Oxford University Press.
Patchin, J.W and Hiduja, S. 2006. Bullies Move Beyond the Schoolyard : A Preliminary Look at Cyberbullying. Journal of Youth Violence and Juvenile Justice [online]. 4 (2), pp 148 – 169. Available from: http://yvj.sagepub.com/content/4/2/148.abstract [Accessed 23 December 2014].
Phillip,P and Sianjina,R.,2013. Cyber Security for Educational Leaders. New York: Routledge.
Polonsky, M.J., 1998. Incorporating ethics into business students’ research projects: A process approach. Journal of Business Ethics [online]. 17(11), pp 1227 – 1241. Available from: http://download.springer.com/static/pdf/790/art%253A10.1023%252FA%253A1005843400352.pdf?auth66=1422612985_b7532cc6cfebc7b766816baf34a86980&ext=.pdf [Accessed 30 January 2015].
Proctor R., Van Zandt T., (2011). Human Factors in Simple and Complex Systems. Second Edition. UK:CRC Press.
Richards L., 2013. Qualitative Methods. Thousand Oaks, CA : Sage.
Rigby, K. 1996. Bullying in Schools and What to Do About It. London : Jessica Kingsley.
Rigby, K., Barrington Thomas, E. 2003. How Schools Counter Bullying. Victoria: Australian Council for Educational Research Limited.
Rivers, I., Noret, N. 2010. ‘I h 8 u’ : Findings from a five-year study of text and email bullying. British Educational Research Journal [online]. 36 (4), pp. 643 – 671. Available from: http://ianrivers.files.wordpress.com/2011/11/cyberbullying1.pdf [Accessed 23 December 2014].
Smith, P.K., Mahdavi, J., Carvalho, M., Fisher, S., Russell, S., and Tippett, N. 2008. Cyberbullying: Its nature and impact in secondary school pupils. Journal of Child Psychology and Psychiatry[online]. 49(4), pp. 376 – 385. Available from: https://www.gold.ac.uk/media/SmithJCPP.pdf [Accessed 24 January 2015].
Singh, P., 2007. Laws on Cyber Crimes : Alongwith It Act and Relevant Rules [ebook]. Jaipur, IND: Book Enclave. Available from: http://0-site.ebrary.com.library.edgehill.ac.uk/lib/edgehill/detail.action?docID=10415573 [Accessed18 October 2014].
Tarapdar, S., Kellett, M., 2011. Young people’s voices on cyber bullying: what can age comparisons tell us [online]. Available from: http://oro.open.ac.uk/32271/1/Diana_-_Young_Peoples_Voices_Report.pdf [Accessed 24 January 2015].
The Guardian. 2009. Teenage girl is first to be jailed for bullying on Facebook [online]. Available from: http://www.theguardian.com/uk/2009/aug/21/facebook-bullying-sentence-teenage-girl [Accessed 24 January 2015].
Trolley, B. 2010. Cyber kids, Cyber bullying, Cyber balance. California: Corwin
Vandebosch, H. 2011. eYouth : Balancing between Opportunities and Risks [online]. ProQuest ebrary. http://0-site.ebrary.com.library.edgehill.ac.uk/lib/edgehill/reader.action?docID=10600380 [Accessed 23 December 2014].
WELLFIELD HIGH SCHOOL, 2014. Anti-bullyingPolicy [online]. Available from: http://www.wellfield-high.lancsngfl.ac.uk/download/file/Anti%20Bullying%20Policy%20WHS.pdf [Accessed 23 October 2014]
Weiss D., 2000. Journal of Applied Social Psychology. UK: V.H. Winston & Sons.
Willard, N. 2006. Cyberbullying and Cyberthreats [online]. Available from: http://bcloud.marinschools.org/SafeSchools/Documents/BP-CyberBandT.pdf [Accessed 30 December 2014].
Zwick,C.,2005.Designing for small screens : mobile phones, smart phones, PDAs, pocket PCs, navigation systems, MP3. Switzerland: AVA Publishing.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Technology"
Technology can be described as the use of scientific and advanced knowledge to meet the requirements of humans. Technology is continuously developing, and is used in almost all aspects of life.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




