The Rise of Fileless Malware and Attack Techniques
Info: 8958 words (36 pages) Dissertation
Published: 23rd Dec 2021
Tagged: Cyber Security
Abstract
This is a research report into all aspects of Fileless Attack Malware. It provides the reader with concise information regarding what a Fileless Malware Threat is, how it infiltrates a machine, how it penetrates through a system, and how to prevent attacks of such kind.
This report also highlights why fileless attacks is the fan favourite among attackers in today’s environment. It explores the stealth, and precision of fileless malware, and how it can manipulate built-in system vulnerabilities.
This report was initially intended to be a supportive document to a practical demonstration of Fileless Attack Malware. However, it was not possible in the time allotted to source a fileless malware threat to explore, modify, test or run. As a result, the author investigated the complete theoretical journey of Fileless Attack Malware.
Table of Contents
Click to expand Table of Contents
1 Introduction
1.1 Research questions
1.2 Research Methodology
2 Literature Review
2.1 JS_POWMET – Trojan Malware
2.2 Kovter – Click Fraud Malware
2.3 SOREBRECT – Code Injection Ransomware
2.4 Dridex – Credential Theft Malware
2.5 NotPetya Using EternalBlue Exploit
3 Fileless Malware
3.1 How Fileless Attacks Work
3.2 PowerShell Scripts
3.3 History of Fileless Malware
3.3.1 Code Red and Code Red II
3.3.2 SQL Slammer Worm
3.3.3 Lurk Trojan
3.3.4 Powerliks
3.3.5 Kovter
3.3.6 PowerWare
3.3.7 Poshspy
3.4 Fileless Malware Attacks Facts
3.5 Reason behind Fileless Malware Attacks
4 Antivirus Software Limitations
4.1 Pattern Matching
4.2 Heuristic Analysis
4.3 Behavioural Analysis
4.4 Hash Matching
5 Typical Attack Chain
5.1 Incursion
5.2 Persistence
5.3 Payload
6 Fileless Attack Categories
6.1 Memory Only attack
6.2 Fileless Persistence Methods
6.2.1 Windows Registry
6.2.2 Windows Management Instrumentation
6.2.3 Group Policy Objects
6.2.4 Scheduled Tasks
6.3 Non-PE file Attacks
6.4 Dual-Use Tools
6.4.1 Dual-use Tool Purpose
7 Fileless Malware Attack Prevention
7.1 Apply Patches
7.2 Least Privilege principle
7.3 Content Blocking
7.4 Disable Unnecessary Tools
7.5 Disable Macros
7.6 Logging
7.7 Maintaining Upgrades
7.8 User Awareness
8 Conclusion
8.1 Personal Reflections on the Project Experience
9 Bibliography
Table of Figures
Figure 2‑1 JS_POWMET Process
Figure 2‑2 Random file and opening shell commands
Figure 2‑3 Run and execute of payload
Figure 2‑4 Restart with shortcut and .bat files
Figure 2‑5 SOREBRECT process
Figure 2‑6 Payload execution vis svchost.exe
Figure 2‑7 Dridex process
Figure 2‑8 DLL files to gain system privileges
Figure 2‑9 NotPetya replacing MBR
Figure 2‑10 Response request
Figure 3‑1 6 steps for a fileless malware attack
Figure 6‑1 Dual-use tools, grouped by purpose
1 Introduction
Fileless Malware is currently one of the leading targeted cyber-attacks trends. (Korolov, 2017) Attackers are making use of existing tool on targeted devices, or utilising a simple script of shellcode directly to the device memory. Detection of these Fileless attacks is difficult as it does not create new software onto the device and, therefore, minimizes the effectiveness of antivirus tools to recognise the threat. According to The State of Endpoint Security Risk report, by Ponemon Institute, “77% of compromised attacks in 2017 were Fileless” (Ponemon Institute, 2018).
For fileless malware to penetrates the security of the device, malicious scripts are hidden inside the registry, or Windows Management Instrumentation (WMI) (Microsoft, 2018). By doing this, the malware achieves a persistent fileless infiltration on the targeted device.
System tools are dual-use tools are frequently used to gather information about a freshly compromised system. These tools also help to exfiltrate stolen data. This action is undetectable in most cases as it blends with the normal system administration duties.
Attackers are reverting to these simpler methods of attack as it is proving most cost intensive to find reliable, exploitable vulnerabilities. Often a spear-phishing attack with some social engineering can be just as successful at achieving the attackers’ goals.
There are four main categories for fileless malware techniques. They include
- Memory-only threats
- Fileless persistence
- Dual-use tools
- Non-PE attacks
Cyber criminals are adopting these tactics to spread threats like ransomware and financial Trojans, but nation-state targeted attack groups also make use of them. This was apparent during the Kaspersky Enterprise Network attack, in February 2017. The recent attack by a well-established hacking group, called FIN7, launched an attack against restaurants in the United States is an example of how effective these tactics can be (ars TECHNICA, 2017).
This document will discuss what a Fileless Malware attack is, the motivation for the attacks, the vulnerabilities and limitations of Antivirus software against such attacks, and suggested prevention techniques.
1.1 Research questions
- What are the different variations of Fileless Malware attacks?
- How do Fileless Malware attacks work?
- How do attack affect a system?
- What prevention measures are available?
- Why are Fileless Malware attacks so stealthy and dangerous?
1.2 Research Methodology
- Whitepaper reports
- Technical Blogs
- Digital journals
- Archives
- Security specific websites
2 Literature Review
This chapter is the findings of an investigation into the different fileless malwares that the author discovered in the current market. In each case the author describes the technical processes for each version.
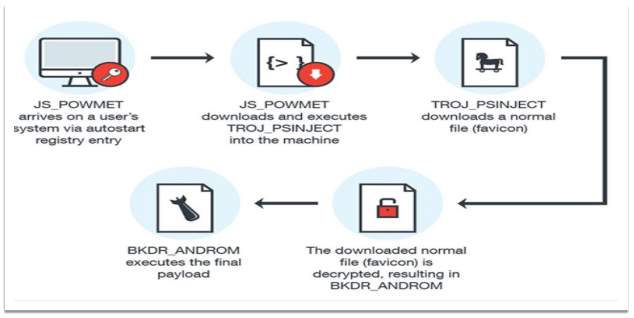
2.1 JS_POWMET – Trojan Malware
An Extensible Mark-up Language (XML) file (Fisher, 2018) is delivered to the targeted device either by user download, or dropped by another malware with an AutoStart registry. The malware is executed on the system through user interaction with malicious URL.
Once is executed it downloads another file called TROJ_PSINJECT which in fact is a script that runs under the PowerShell process. Next, the malicious file connects to a domain and downloads a file named favicon and proceeds to decrypts it. The result is a DLL file called BKDR_ANDROM which is injected into powershell.exe process. The whole process is achieved without saving any files on the machine disk (Zorz, 2017).
The malware gathers data such as operating system version, IP address and administrator credentials and sends it to a remote C&C server.
2.2 Kovter – Click Fraud Malware
This click-fraud persistent ransomware arrives through an email document attachment, and requires Macro features to be enabled. This permits the downloading of Kovter from a specific domain.
This ransomware will achieve persistence by generating new random file and open a shell command (Microsoft Secure, 2016).
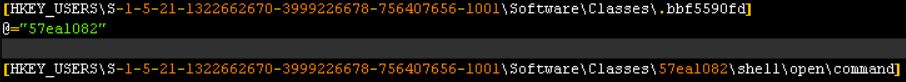
Figure 2‑2 Random file and opening shell commands
Every time the file with extension .bbf5590ftd is opened the command will run the malicious JavaScript. This will execute the payload from another registry key.
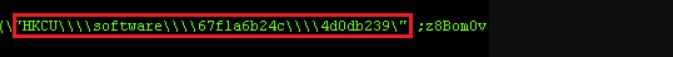
Figure 2‑3 Run and execute of payload
The restart mechanism is assured by using a shortcut file and a bat file. The .bat file contains the file with extension .bbf5590ftd.
Once the .bat file runs, the malicious shell open will execute. All the Kovter malicious code is kept into the registry.
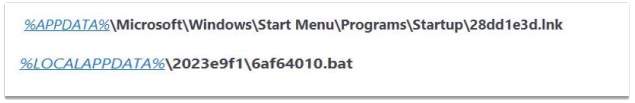
Figure 2‑4 Restart with shortcut and .bat files
2.3 SOREBRECT – Code Injection Ransomware
Because of its huge financial potential, this ransomware was advertised as a service where cyber criminals get a commission for every successful attack.
After user account is compromised using administration privileges, the malware is using the psexec process to inject the code. Alternatively, a legit Windows utility that allow administration to run executable files is targeted (Tancio, 2017).
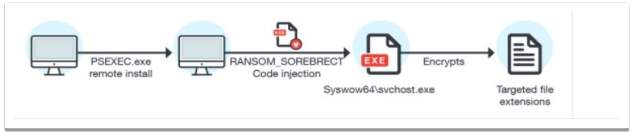
After injection, another Windows service-hosting system process, svchost.exe, executes the payload resulting in encrypted files.

Figure 2‑6 Payload execution vis svchost.exe
The malware takes advantage of wevtutil.exe ,a Windows event command line utility to delete the event log files, and vssadmin, to delete system shadow copies. As a result, any evidence of malicious activity is removed from the system.
For hiding connections to C&C servers, the malware is using Tor Network Protocols.
2.4 Dridex – Credential Theft Malware
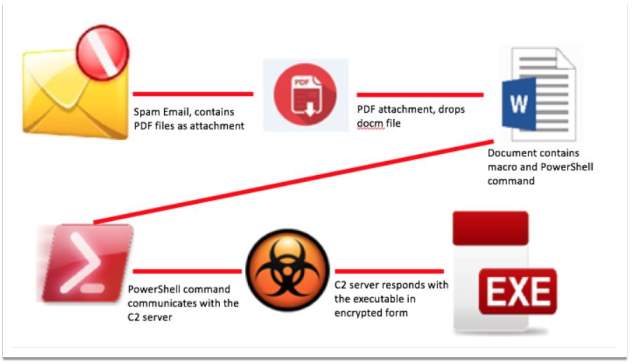
Dridex is another known malware that has become popular with cybercriminals, especially for executing large infection campaigns in 2016.
Attackers start executing a spam email campaign by using malicious PDF files as an attachment.
Once the user clicks on the .pdf, a document file, that contains macros, is executed. A PowerShell script is run. This script requests the encrypted binary file from C&C server. The binary is decrypted and executed. This launches the malicious payload.
2.5 NotPetya Using EternalBlue Exploit
NotPetya is a well-known malware that affected many systems, especially in Ukraine using Eternalblue SMBv1 exploit. Other locations such as US, UK, India, China, Australia, South Africa, Korea have been affected since the malware spread started in 2017.
The Server Message Block (SMB) is a network protocol using for sharing files or printers by many companies (Microsoft, 2018). Because of the file sharing, the malware can easily infected so many systems.
An interesting note about this malware family is once it gains access to a machine, the malicious file programs a reboot, rather than forcing one, and then presents the user with different interface.
Before getting administration privileges, the malware must get access to several system privileges as seen in the example below (Pirozzi, 2017).
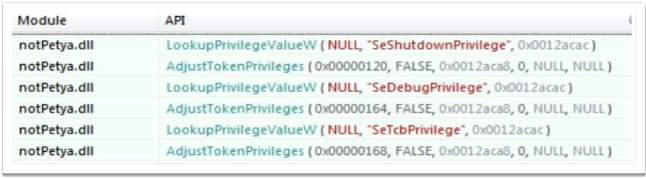
Figure 2‑8 DLL files to gain system privileges
Actions taken by the malware:
- In first stage malicious file looks for an identifiable marker on the machine C: drive to avoid secondary infection.
- Next, the malware replaces the system Master Boot Record (MBR) with its own boot loader for loading the micro kernel at reboot (TechNet, 2018). See Figure 2-9.
- After reboot, malware steals user credentials by using a custom Mimikatz tool (Offensive Security, 2018)
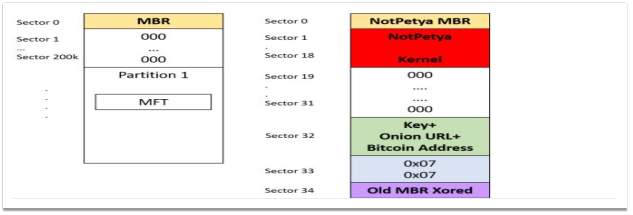
Figure 2‑9 NotPetya replacing MBR
- Identifying the windows machine is next step for lateral movement inside the company network. The response request between two windows machines is shown in Figure 2-10.
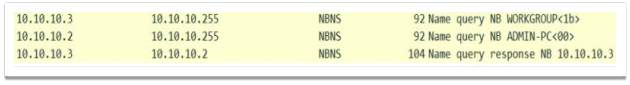
- Once the windows machines are identified the malware attempts to infect them using the SMB exploit Eternalblue (Burgess, 2017).
- Finally, the malicious file is executed, and the malware is installed on the victim machine.
3 Fileless Malware
Fileless malware goes by many names, including ‘non-malware’, ‘memory-based malware’. This section will explore the history of fileless malware, why it is becoming a favourite among hackers, and some interesting facts relating to fileless malware.
The reason it is called ‘fileless’ is that, unlike traditional malware that use files to infiltrate a host, fileless malware do not create additional files. Alternatively, fileless malware resides in the RAM, or the registry. As no addition software is created, antivirus software can fail to detect the attack. This makes fileless attacks very affective in its role.
Considered an Advanced Volatile Threat (AVT), fileless malware is capable of exploiting vulnerabilities in a system or application without writing files to the local hard drive (Waterson, 2013). It typically requires administrative rights to the target device, which may be obtained by exploiting a vulnerability or other attack for privilege escalation.
3.1 How Fileless Attacks Work
Fileless malware attacks use valid tools available on the compromised system.
The following is a list of six typical steps taken to achieve unauthorised access to a system (Korolov, 2017).
- Users receive spam message with a link to a malicious site
- Users click on the link
- The malicious website loads Flash which has known vulnerabilities on user computer
- Flash opens the Windows PowerShell tool which can execute instructions in command line
- PowerShell downloads and executes a script from command and control server
- The script locates and sends user’s data to the attacker
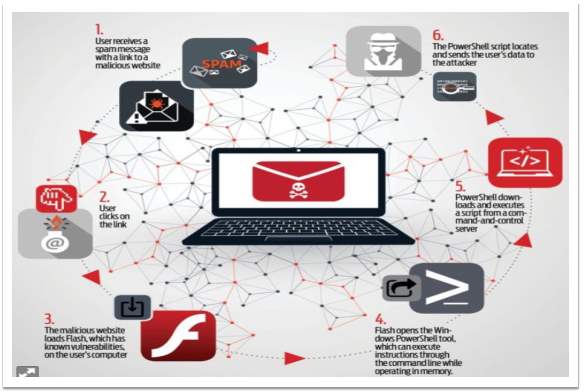
Figure 3‑1 6 steps for a fileless malware attack
3.2 PowerShell Scripts
Another tool of infiltration is through use of carefully constructed scripts, such as PowerShell (Cybereason, 2017) ,where payloads can be injected into the memory of an existing application/software, or by running scripts within a whitelisted application.
Malicious PowerShell scripts are a key ingredient to many fileless malware attacks. Windows PowerShell is a built-in tool based on the .NET framework (Microsoft, 2017) comprising of a command-line shell, an interface that lets users access services of the operating system (OS), and a programming language that can be used to create scripts.
PowerShell is designed to automate system administration tasks, such as view all USB devices, drives, and services installed in the system, schedule a series of commands and set it in the background, or terminate processes. To the user it functions just as the system’s Task Manager. PowerShell is also designed to enable administrators to seamlessly manage the configurations of systems and servers, as well as the software or services and the environments they run on.
3.3 History of Fileless Malware
This section will highlight some of the more relevant occurrences since Fileless Malware was discovered.
3.3.1 Code Red and Code Red II
The first fileless malware was detected in July 2001. It was a worm-type attack known as Code Red Worm, and affected Microsoft ||S web server Windows systems. This was closely followed by a secondary variation called Code Red II. Symantec Security Response were responsible for designing a removal tool to assess the device and remove both variations of Code Red by August 10th, 2001.
Subsequently, Kaspersky Labs published an announcement in response to the Code Red attacks, where Eugene Kaspersky stated:
“We predict that in the very near future, such ‘fileless’ worms as Code Red will become one of the most widespread forms of malicious programs, and an anti-virus’ ineffectiveness in the face of such a threat simply invites danger.”
(Zeltser, 2015)
3.3.2 SQL Slammer Worm
On January 25th, 2003, an aggressive scan, by SQL Slammer Worm, disrupted internet traffic. This attack was made easier by the fact that Microsoft issued a patch in 2002 that removed the buffer overflow vulnerability for SQL 2000 servers. This allowed the worm to spread rapidly throughout the internet (Vamosi, 2003).
This worm can be removed by rebooting the infected system. However, this does not protect the system from further, similar attacks. The worm can be blocked using adequate firewall/ gateway at the ports. Alternatively, McAfee, Symantec and Trend Micro have since developed removal tools for infected system of an SQL Slammer attack.
3.3.3 Lurk Trojan
Moving forward to 2012, Sergey Golovanov, at the Kaspersky Labs, reported on a bot that used a fileless technique. In his findings, he stated that
“We are dealing with a very rare kind of malware — the so-called fileless malicious programs that do not exist as files on the hard drive but operate only in the infected computers RAM.”
(Golovanov, 2012)
This bot did not save any files to the hard drive. Instead, it exploited the client-side Java by affecting the javaw.exe process
3.3.4 Powerliks
This form of malware attack is different to the above attack. By 2014, Powerliks arrived, and is described as a persistent malware without a file”. This translates as a malware which resides in the registry only, and does not generate any files on the infected system (Rascagnères, 2014).
Powerliks uses the following steps to infiltrate a system
- It exploits a weakness in MS Word via a crafted Word document that has been circulated through the user email
- An encoded auto-start registry key is created to ensure the malicious activity survives a system re-boot
- The decoding is established by a script that ensures the system has PowerShell installed.
- Additional code is a PowerShell script, Base64-encoded. This code executes the shellcode.
- This shellcode runs a Windows binary. The binary connects to the IP address to access further commands.
- All actions are stored without file creation in the registry.
3.3.5 Kovter
In mid-2015, Kovter arrived, showing a lot of similarities with Powerliks. This attack involves infection via a malicious executable, and storing it in the registry in an encrypted format. This is most recognisable in report by Andrew Dove of Airbus. In this report, Dove outlines a lab setup to show the lifecycle of the Kovter attack (Dove, 2016) .
3.3.6 PowerWare
2016 saw the introduction of PowerWare. Rico Valdez and Mike Sconzo reported for Carbon Black (Carbon Black, 2018) in this threat. This ransomware uses a systems’ native tools to infiltrate the core of the system by leveraging PowerShell to do all the work. This edition of fileless malware is showcasing the hackers’ ability and need to think outside the box.
The PowerWare is delivered to the targeted system using a macro-enabled Word document. This document uses the macros to generate executable files such a “cmd.exe”. This .exe requests action from PowerShell, which, in turn, downloads and executes the PowerWare code (Rico, 2016).
3.3.7 Poshspy
In April of 2017, a security specialist at Mandiant (Mandiant, 2018), Matthew Dunwoody, reported on a fileless malware, named Poshspy, which uses WMI process of the Operating System to gain a persistence. It is supported by PowerShell as its payload.
Dunwoody refers to Poshspy as “living-off-the-land” as it uses the built-in infrastructure of the system. By using PowerShell, it is virtually undetectable, especially to any user not familiar with the finer details of WMI.
In his report, Dunwoody states,
By “living off the land” they were able to make an extremely discrete backdoor that they can deploy alongside their more conventional and noisier backdoor families, in order to help ensure persistence even after remediation
(Dunwoody, 2017)
3.4 Fileless Malware Attacks Facts
The following is a list of some of the more fascinating facts about fileless as found in the Barkley Fileless Attack Survival Guide published in February 2018. (Barkley, 2018).
- 42% of organisations face one or more fileless attacks, resulting in the data being compromised.
- 77% of all successful attacks in 2017 involved fileless malware.
- Because of new tools in the field of fileless attacks, these occurrences are becoming more available, and easier to apply, to the common cybercriminal.
- These techniques are less likely to be detected as there is no files being generated. Therefore, damage can go undisturbed for some time.
- Fileless attack techniques allow initial access to the system, when it then could cause a wide range of subsequent activities.
- Antivirus software have not full developed to detect the fileless attack. The ordinary user cannot recognise the intricate activities of the WMI.
- Fileless attacks can result in persistence by storing the malicious codes in the registry.
- A successful attack can compromise sensitive data, and incur a huge monetary cost to the company.
3.5 Reason behind Fileless Malware Attacks
The author identifies why the use of fileless attacks is so appealing to cybercriminals.
- Easy: due to the development of pen testing frameworks in recent years, fileless attacks are, for the most part, pre-packaged.
- Reliable: three quarters of all successful penetrations were fileless attacks.
- Convenient: it uses built-in software to mitigate to where it wants to go. There is no overheads associated with it.
- Stealth: fileless attack are difficult to detect, even with an elaborate antivirus software system
- Evasive: attacks of this calibre are difficult to identify or reverse engineer. This make progress in prevention development inadequate.
4 Antivirus Software Limitations
This chapter investigates the limitations the current antivirus software has in combatting the latest trends of fileless malware attacks.
Traditionally, antivirus software detects an attack by comparing signatures of the malware present on the hard disk. Since fileless malware does not leave residual files, most antivirus software cannot detect the attack. The malware penetrates by injecting itself directly into the RAM, or the registry (Cylance, 2017).
There are four main tradition approaches which existing antivirus software uses to detect malware (Zeltser, 2018) .
- Pattern Matching
- Heuristic Analysis
- Behavioural Analysis
- Hash Matching
4.1 Pattern Matching
A signature is the digital fingerprint of a piece of malware. It’s a unique string of bits, a binary pattern representing the malware. Each time a traditional Anti-Virus (AV) product encounters a new file, the AV product looks through its signature list and asks, “does this byte in the signature match this byte in the file?” If it does, it moves on and checks the next byte. It continues through the whole file in this way. If every byte of the file matches every byte in one of its signatures, exactly, it flags the file as malware.
However, attackers easily bypass signatures by mutating, obfuscating, or otherwise changing up the code in their malware. Herein lays the biggest weakness of signatures: if so much as a single byte is changed in any of the signature’s important values, then the signature no longer matches the malware.
4.2 Heuristic Analysis
The Antivirus (AV) looks at loose properties of the file, such as how big the file is, whether it looks like it’s using a set of dangerous functions, or whether it has abnormal permissions. With heuristic approaches, the AV matches things that aren’t in the code directly (Thomas, 2018).
One example of how this might work is by asking the following questions of the file:
- Does the executable import VirtualAlloc (Kath, 1993)?
- Is the executable greater than 30KB and less than 75KB?
- Does the executable have a section whose permissions are read, write and execute?
If all of the above are true, then it is malware!
With heuristic matches, there may be up to ten rules in place, but it’s no more complicated than having more rules than the above illustrates in the real world. Traditional AV relies heavily on this set of rules in order to convict a sample. This is where the cybercriminals get the last laugh. For an attacker, bypassing AV products, that use heuristics, requires knowledge of just a single feature. Changing that one feature breaks the entire detection.
4.3 Behavioural Analysis
A third approach is behavioural analysis, which is like heuristics and targets the actual behaviour exhibited by malware (Cloonan, 2017).
Behavioural analysis looks at questions such as:
- What is the file doing on a file system level?
- What is the file doing on a registry level?
- What is the file doing on a process level?
- What is the file doing on a network level?
The trouble with this approach is that the malware must run first before the AV product can detect it.
4.4 Hash Matching
The forth approach is hash matching.
The AV calculates hashes over different parts of the file, and does the following:
- Takes a hash over a certain area of the executable (MD5, SHA256, CRC32)
- Asks, does the hash match the hash of a known piece of malware?
If yes, then it is malware!
The problem with hashes is, once again, if a single bit gets changed in any of the areas used to generate the hashes, the hashes produced are wildly different.
An attacker only needs to change one bit of the file, and it renders the AV useless.
5 Typical Attack Chain
This chapter looks into the different methods of “Living off the Land” attack chains typically used in current security environments (Wueest, 2018).
5.1 Incursion
Incursion can be achieved through remote code execution vulnerabilities.
Examples include:
- Exploit in memory – SMB EthernalBlue
- Email – Document macro
- Stolen credentials – Remote Desk Protocol password guess
- Remote PowerShell dropper from a cloud
5.2 Persistence
This is the second stage of the attack, and depends on the attacker’s goal. Once the computer is compromised, stage two may or may not be fileless regarding the persistence method.
Examples include:
- Memory only malware – SQL slammer
- JavaScript in the registry
5.3 Payload
The payload is injected through dual-use of tools.
Examples include:
- Dual-use tools – Mimkatz, PWDUMP
- Memory only payload – Mirai DDOS
- Non-PE file payload – PowerShell script
6 Fileless Attack Categories
The following categories attacks are specific to fileless malware attack:
- Memory only threats
- Fileless persistence
- Dual-use tools
- Non-PE file attacks
In this chapter, the author will look into each of these techniques in more detail (Wueest, 2018).
6.1 Memory Only attack
Earlier examples of this were the Code Red, and SQL Slammer attacks in 2001 and 2003 respectively. A more recent example was the EthernalBlue exploit. This attack deployed the DoublePulsar backdoor as used by the WannaCry ransomware (Symantec Security Response, 2017).
It is relatively easy for an attacker to use shellcode to load the payload directly to the memory or registry without any residual file remaining if they target the Remote Code Execution vulnerabilities (Ophtek, 2015).
This needs to be done in conjunction with detecting this behaviour in the web attack toolkits. In 2013, the Angular exploit kit was seen using Trojan.Snifula (Morparia, 2013). It was clear that the shellcode was loaded directly to the memory rather than generating files.
To clear the system of this malware, a simple reboot is adequate. Rebooting is something companies with core servers need to apply more often. If the core server is not rebooted regularly, the attack can infiltrate throughout the system, undetected.
6.2 Fileless Persistence Methods
This is the term used when describing how an attacker can obtain a persistent hold on a Windows device without leaving malicious payload on the hard disk. Normally it requires the existence of malicious code on the system post-infection. An example is VBS in the registry.
The following are examples of the more common variations of infiltration.
6.2.1 Windows Registry
Usually referred to as registry, it contains a database of settings configurations in the Windows Operating System.
There was a series of threats which appeared, starting in 2014. First came TrojanPoweliks (F-Secure, 2018), which was a simple registry key embedded in the Windows registry. This opened the system to the risk of downloading additional malware on the susceptible machine, remotely.
This was closely followed by two similar threats called Trojan.Kotver and Trojan.Bedep. seeing the success of these methods, it fast became the attackers’ favourite method.
A normal call to rundll32 takes in the following arguments:
RUNDLL32.EXE
The value used by the threat looks like this:
rundll32.exe javascript:”.. mshtml,RunHTMLApplication “;alert(‘payload’)
6.2.2 Windows Management Instrumentation
The Windows Management Instrumentation (WMI) is internal infrastructure for the data management, operations, and administration on a Windows OS, locally and remotely (Microsoft, 2018).
Through command line (wmic.exe), or PowerShell, the WMI can control processes, execute scripts and query system settings.
Due to the accessibility of WMI to privileged areas, attackers can construct a filter for an event. The attacker then provides a user trigger to activate the malicious script. This can be as simple as the time on the device.
The following are a few examples of these attacks discussed in the 2015 Black Hat Report by Matt Graeber (Graeber, 2015).
- PowerShell is an extremely powerful scripting language
- wmic.exe s used commonly by attackers to perform lateral movement
- wbemtest.exe is a powerful GUI tool that was designed primarily as a diagnostic tool
- WMI Explorer is a commercial tool from Sapien that is great for discovering WMI classes
- CIM Studio is a free, legacy tool from Microsoft that allows you to easily browse the WMI repository
- Windows Script Host (WSH) languages – The two WSH language provided by Microsoft are VBScript and JScript
6.2.3 Group Policy Objects
Windows Group Policy Objects (GPOs) is a collection of policies and settings for a system. It is vulnerable as it can be used to add a load point for a backdoor (Microsoft, 2017).
A registry run key can be generated using PowerShell script. When permission is granted, the malware is created by the system through the command line.
It is also possible to use existing tools, such as PowerShell Empire Framework, which has a built-in persistence module. This can generate new GPOs, or modify existing GPOs.
This method is not as common as most, as GPOs are not on most home computers, so the threat is concentrated on the corporate world.
6.2.4 Scheduled Tasks
According to Pieter Arntz of MalwareLabs in 2015,
“The Windows Task Scheduler is like an alarm clock that you can set, to start a procedure under specified circumstances.”
(Arntz, 2015)
If an attacker creates a schedule task using a PowerShell script, malicious activity can be triggered at a specified time.
A scheduled attack can also bypass the User Account Control (UAC) giving an attacker privileges.
6.3 Non-PE file Attacks
A non-PE file is a non-portable executable file. And attack on a non-PE file usually involve scripts and tools. Essentially, it is a subclass of most dual-tools attacks. The host tool is basically a payload location for the malware. Such tools include PowerShell, CScript, JavaScript, or WScript.
While this is not exactly a fileless attack, as it uses script files. However, this fact becomes obsolete when it is realised that these script files are obscure, and can avoid detection easily.
For example, a user must install Microsoft Office onto their machine. The Office document or PDF file contains script. If this is targeted, and corrupted or modifies, an attacker can gain access to the OS by requesting the user triggers the malware, and proceed to alter permissions. This exposes the entire system.
Zip files are also a fan favourite for this method. Script files can be triggered by extensions like .LNK, .HTA or .SCT. the malicious script can be hidden among genuine scripts. Once unzipped, the malware is inside the system. This can be also achieved by self-extracting archives and installation files. The malicious file can then be routed to the machines path to the cloud, so it can work undetected even if a user was looking for it on the machine.
In 2017, Google started blocking .js files in Gmail transactions. However, this proved futile as it did not expose the true number of malicious JavaScript files passing through its service.
For example, in February 2017 Google began blocking .js files in Gmail but this did not have a significant effect on the number of malicious JavaScript file detection (Davenport, 2017).
6.4 Dual-Use Tools
Dual-use tools are ubiquitous, meaning that the attacker is hidden in plain sight. The attacker uses existing system tools, hides among its native script, and worms its way through the system without triggering any alarms.
Legitimate commands can be used by attackers as back doors. Example would be the simple command to create a new user, and give the new user administration group access.
- net user /add [username] [password]
- net localgroup administrators [username] /add
the attacker has learned to pass specific arguments through the command line at the tool launch, so that the tool will ‘listen’ to the command.
Because the commands are clean, the attacker has the advantage of bypassing the majority of the whitelisting approaches, and many security tools. If the arguments look like normal activity, it is unlikely that any antivirus tool will detect it.
6.4.1 Dual-use Tool Purpose
This table illustrates the purpose of several of the current Dual-use Tools. (Wueest, 2018)
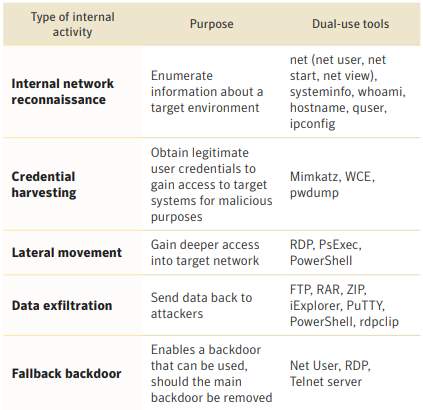
Figure 6‑1 Dual-use tools, grouped by purpose
7 Fileless Malware Attack Prevention
This chapter gives a list of potential preventative measure that can be taken to combat a malware infiltration threat. Using multilayer techniques is best to minimize infection threats.
Common strategies to protects against malware involves three general steps:
- Prevent: Block the incursion or infection and prevent the damage from occurring.
- Containment: Limit the spread of an attack in the event of a successful infection.
- Respond: Have an incident response process, learn from the attack, and improve the defences
7.1 Apply Patches
A vulnerable machine, is only waiting to be attacked. This can be made more difficult by having protocols in place to assess, test, and roll out patches. It is important to have strong first-defences against attacks. Patching is vital, but not easy. Isolated systems you can’t patch quickly by restricting network access.
7.2 Least Privilege principle
As best practice, users should be given the bare minimum of access and privileges necessary, limiting the damage they can do if compromised (Vogel, 2013). Removing Users from the Local Administrators Group can also help prevent privilege escalation attempts.
7.3 Content Blocking
Using common sense, it is in the interest of the user to block any unnecessary, or unrecognisable file attachments. Some of the more obvious ones include .EXE, .BAT. Extend this blocking practice to script files (.JS, .VBS, etc.), archive files (.ZIP, .SFX, .7z), and even Office files (.DOC, .DOCX, etc.) and PDFs (Symantec, 2017).
7.4 Disable Unnecessary Tools
Windows PowerShell is a native Microsoft tool used for task automation and configuration management. Unfortunately, fileless malware often exploits certain vulnerabilities in PowerShell. If you don’t need to use PowerShell disable it.
7.5 Disable Macros
Block macros in Office files downloaded from the Internet. Macros are abused to download malware and launch malicious scripts (National Cyber Security Centre, 2016).
Disable “Update Automatic Links At Open” in Microsoft Word is excellent advice.
7.6 Logging
- Avoid Credential Overlap Across systems. This can help prevent lateral movement opportunities if valid credentials are obtained.
- Disable Anonymous Login for Read and Write Access to Network File Shares (NFS)
- Disable Anonymous Login for Read and Write Access to File Transfer Protocol (FTP)
- Use Strong Passwords or two factor authentication (2FA) when possible – can help keep attackers out even if they’ve successfully stolen passwords.
- Ensure there is adequate Firewall to help track logs.
7.7 Maintaining Upgrades
One of the most effective ways to keep your system safe from malware is to simply keep all your software up to date with the latest security patches. For the ultimate peace of mind, ensure auto updates are enabled in the settings of your applications.
7.8 User Awareness
Conduct User Awareness Training Many attacks still initially require users clicking something they should not. Train and inform end-users about attacks that rely on deception and social engineering (BSI, 2018).
8 Conclusion
Using fileless attack techniques and malicious scripts is an obvious choice for attackers, one which is made easier by various, widely available tools. So, it’s no surprise that many cyber criminals and targeted attack groups have embraced fileless tactics.
Attackers are relying on existing tools to blend in with everyday system activities, and not raise additional alarms. Misusing clean system tools can bypass many protection mitigations like application whitelisting. It is very common to steal credentials and misuse them for lateral movement inside a network. Also, any scripts used in attacks can be obfuscated by trivial techniques making them as good as invisible to traditional static signature detection methods. For the attackers, scripts bear the advantage that they can be updated and adapted quickly without a huge development cycle, making them more flexible and individually tailored for their environmental purpose. These points combined lead to many traditional security solutions having issues reliably blocking fileless attack techniques.
Malware are designed to detect and avoid sandboxes-which are often not configured to handle script attacks and may let them pass through unblocked. One of the best methods for detection is a combination of memory scanning with heuristics and behaviour-based detection which also monitors system tools. The attackers trying to hinder behavioural detection by splitting the code into multiple modules and distributing it over multiple command calls to break a simple chain of events. Fileless or dual-use tool attacks either use a remote code execution (RCE) vulnerability (Ophtek, 2015), stolen or guessed credentials, or a non-PE file like a script during the initial incursion phase. Hence, they can be detected at the incursion phase before any further damage can be done.
Techniques and tactics need to be shared to be able to filter how these tools are used in context.
8.1 Personal Reflections on the Project Experience
- This is research paper. It is different from final project as the original idea about fileless malware was not achievable. It was not within my resources to find a fileless malware which could be used and tested in a practical way for demonstration purposes.
- The author learned about a new malware family that has proven to be extremely hard to detect by Antivirus software. It is apparent that this format of malware is more dangerous than traditional malicious files designed to write itself onto the hard drive
- The author was exposed to many malware fileless attack techniques.
- The importance of having legitimate system tools like psexe, wmic.exe, PowerShell, RDP that misused can inflict damage to victim machines
- Prevention methods can be easy if the user is aware of such threats. And being aware seems to be the best way to detect, and avoid fileless attacks.
9 Bibliography
Arntz, P., 2015. Scheduled Tasks. [Online] Available at: https://blog.malwarebytes.com/cybercrime/2015/03/scheduled-tasks/ [Accessed 05 02 2018].
ars TECHNICA, 2017. Fileless malware targeting US restaurants went undetected by most AV. [Online] Available at: https://arstechnica.com/information-technology/2017/06/fileless-malware-attack-against-us-restaurants-went-undetected-by-most-av/ [Accessed 12 02 2018].
Barkley, 2018. Fileless Attack Survival Guide, Boston: Barkley.
BSI, 2018. End user security awareness training. [Online] Available at: https://www.bsigroup.com/en-IE/our-services/Cybersecurity-Information-Resilience/Technology-solutions/End-User-Security-Awareness-Training/ [Accessed 27 02 2018].
Burgess, M., 2017. Everything you need to know about EternalBlue. [Online] Available at: http://www.wired.co.uk/article/what-is-eternal-blue-exploit-vulnerability-patch [Accessed 27 02 2018].
Carbon Black, 2018. [Online] Available at: https://www.carbonblack.com/ [Accessed 21 02 2018].
Cloonan, J., 2017. Advanced Malware Detection. [Online] Available at: https://www.infosecurity-magazine.com/opinions/malware-detection-signatures/ [Accessed 17 02 2018].
Cybereason, 2017. WHAT YOU NEED TO KNOW ABOUT POWERSHELL ATTACKS. [Online] Available at: https://www.cybereason.com/blog/fileless-malware-powershell [Accessed 12 02 2018].
Cylance, 2017. How Traditional Antivirus Works. [Online] Available at: https://www.cylance.com/en_us/blog/how-traditional-antivirus-works.html [Accessed 05 02 2018].
Davenport, C., 2017. Gmail won’t allow JavaScript file attachments starting February 13. [Online] Available at: https://www.androidpolice.com/2017/01/25/gmail-wont-allow-javascript-file-attachments-starting-february-13/ [Accessed 01 02 2018].
Dove, A., 2016. Fileless Malware – A Behavioural Analysis Of Kovter Persistence. [Online] Available at: http://blog.airbuscybersecurity.com/post/2016/03/FILELESS-MALWARE-%E2%80%93-A-BEHAVIOURAL-ANALYSIS-OF-KOVTER-PERSISTENCE [Accessed 06 02 2018].
Dunwoody, M., 2017. Dissecting One of APT29’s Fileless WMI and PowerShell Backdoors (POSHSPY). [Online] Available at: https://www.fireeye.com/blog/threat-research/2017/03/dissecting_one_ofap.html [Accessed 16 02 2018].
Fisher, T., 2018. What Is an XML File?. [Online] Available at: https://www.lifewire.com/what-is-an-xml-file-2622560 [Accessed 05 02 2018].
F-Secure, 2018. Trojan:W32/Poweliks. [Online] Available at: https://www.f-secure.com/v-descs/trojan_w32_poweliks.shtml [Accessed 06 02 2008].
Golovanov, S., 2012. A unique ‘fileless’ bot attacks news site visitors. [Online] Available at: https://web.archive.org/web/20121115032711/http://www.securelist.com/en/blog/687/A_unique_fileless_bot_attacks_news_site_visitors [Accessed 20 02 2018].
Graeber, M., 2015. Abusing Windows Management…. [Online] Available at: https://www.blackhat.com/docs/us-15/materials/us-15-Graeber-Abusing-Windows-Management-Instrumentation-WMI-To-Build-A-Persistent%20Asynchronous-And-Fileless-Backdoor-wp.pdf [Accessed 27 02 2018].
Kath, R., 1993. Managing Virtual Memory. [Online] Available at: https://msdn.microsoft.com/en-us/library/ms810627.aspx [Accessed 01 02 2018].
Korolov, M., 2017. What is a fileless attack?. [Online] Available at: https://www.csoonline.com/article/3227046/malware/what-is-a-fileless-attack-how-hackers-invade-systems-without-installing-software.html [Accessed 20 02 2018].
Korolov, M., 2017. What is a fileless attack? …. [Online] Available at: https://www.csoonline.com/article/3227046/malware/what-is-a-fileless-attack-how-hackers-invade-systems-without-installing-software.html [Accessed 22 01 2018].
Mandiant, A. F. C., 2018. Mandiant Consulting Services. [Online] Available at: https://www.fireeye.com/content/dam/fireeye-www/global/en/services/pdfs/ds-mandiant-consulting-services.pdf [Accessed 22 02 2018].
Microsoft Secure, 2016. Kovter becomes almost fileless, creates a new file type…. [Online] Available at: https://cloudblogs.microsoft.com/microsoftsecure/2016/07/22/kovter-becomes-almost-file-less-creates-a-new-file-type-and-gets-some-new-certificates/?source=mmpc [Accessed 06 02 2018].
Microsoft, 2017. Group Policy Objects. [Online] Available at: https://msdn.microsoft.com/en-us/library/aa374162(v=vs.85).aspx [Accessed 14 02 2018].
Microsoft, 2017. Overview of the .NET Framework. [Online] Available at: https://docs.microsoft.com/en-us/dotnet/framework/get-started/overview [Accessed 15 02 2018].
Microsoft, 2018. Microsoft SMB Protocol and CIFS Protocol Overview. [Online] Available at: https://msdn.microsoft.com/en-us/library/windows/desktop/aa365233(v=vs.85).aspx [Accessed 28 02 2018].
Microsoft, 2018. Windows Management Instrumentation. [Online] Available at: https://msdn.microsoft.com/en-us/library/aa394582(v=vs.85).aspx [Accessed 17 02 2018].
Microsoft, 2018. Windows Management Instrumentation. [Online] Available at: https://msdn.microsoft.com/en-us/library/aa394582(v=vs.85).aspx [Accessed 02 02 2018].
Morparia, J., 2013. Trojan.Snifula. [Online] Available at: https://www.symantec.com/security_response/writeup.jsp?docid=2013-112803-2524-99 [Accessed 12 02 2018].
National Cyber Security Centre, 2016. Macro Security for Microsoft Office. [Online] Available at: https://www.ncsc.gov.uk/guidance/macro-security-microsoft-office [Accessed 09 02 2018].
Offensive Security, 2018. Mimikatz. [Online] Available at: https://www.offensive-security.com/metasploit-unleashed/mimikatz/ [Accessed 28 02 2018].
Ophtek, 2015. What is Remote Code Execution?. [Online] Available at: https://www.ophtek.com/remote-code-execution-used/ [Accessed 01 02 2018].
Pirozzi, F. M., 2017. Malware Analysis Report: NotPetya, Rome, Italy: CSE CyberSec Enterprise SPA.
Ponemon Institute, 2018. The 2017 State of Endpoint Security Risk Report, Boston: Barkly Protects, Inc.
Rascagnères, P., 2014. Poweliks: the persistent malware without a file. [Online] Available at: https://www.gdatasoftware.com/blog/2014/07/23947-poweliks-the-persistent-malware-without-a-file [Accessed 01 02 2018].
Rico, S., 2016. Threat Alert: “PowerWare,” New Ransomware Written in PowerShell, Targets Organizations via Microsoft Word. [Online] Available at: https://www.carbonblack.com/2016/03/25/threat-alert-powerware-new-ransomware-written-in-powershell-targets-organizations-via-microsoft-word/ [Accessed 05 02 2018].
Symantec Security Response, 2017. What you need to know about the WannaCry Ransomware. [Online] Available at: https://www.symantec.com/blogs/threat-intelligence/wannacry-ransomware-attack [Accessed 09 02 2018].
Symantec, 2017. File extensions and types that are common threat vectors for email. [Online] Available at: https://support.symantec.com/en_US/article.INFO3768.html [Accessed 06 02 2018].
Tancio, B., 2017. Analyzing the Fileless, Code-injecting SOREBRECT Ransomware. [Online] Available at: https://blog.trendmicro.com/trendlabs-security-intelligence/analyzing-fileless-code-injecting-sorebrect-ransomware/ [Accessed 16 02 2018].
TechNet, 2018. Master Boot Record. [Online] Available at: https://technet.microsoft.com/en-us/library/cc976786.aspx [Accessed 01 03 2018].
Thomas, T., 2018. What is Heuristic Antivirus Detection?. [Online] Available at: http://www.toptenreviews.com/software/articles/what-is-heuristic-antivirus-detection/ [Accessed 04 02 2018].
Vamosi, R., 2003. SQL Slammer: How it works–prevent it. [Online] Available at: http://www.zdnet.com/article/sql-slammer-how-it-works-prevent-it/ [Accessed 18 02 2018].
Vogel, D., 2013. How to successfully implement the principle of least privilege. [Online] Available at: https://www.techrepublic.com/blog/it-security/how-to-successfully-implement-the-principle-of-least-privilege/ [Accessed 27 02 2018].
Waterson, D., 2013. Advanced Volatile Threats (AVTs). [Online] Available at: https://dwaterson.com/2013/03/11/advanced-volatile-threats-avts/ [Accessed 10 02 2018].
Wueest, C., 2018. Living off the land and fileless attack techniques, California: Internet Security Threat Report.
Zeltser, L., 2015. Looking Beyond the Buzzword. [Online] Available at: https://zeltser.com/fileless-malware-beyond-buzzword/ [Accessed 03 02 2018].
Zeltser, l., 2018. …Virus detection techniques. [Online] Available at: http://searchsecurity.techtarget.com/tip/How-antivirus-software-works-Virus-detection-techniques [Accessed 15 02 2018].
Zorz, Z., 2017. The anatomy of a completely fileless attack. [Online] Available at: https://www.helpnetsecurity.com/2017/08/03/anatomy-completely-fileless-attack/ [Accessed 18 02 2018].
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allRelated Content
All TagsContent relating to: "Cyber Security"
Cyber security refers to technologies and practices undertaken to protect electronics systems and devices including computers, networks, smartphones, and the data they hold, from malicious damage, theft or exploitation.
Related Articles
DMCA / Removal Request
If you are the original writer of this dissertation and no longer wish to have your work published on the UKDiss.com website then please:




